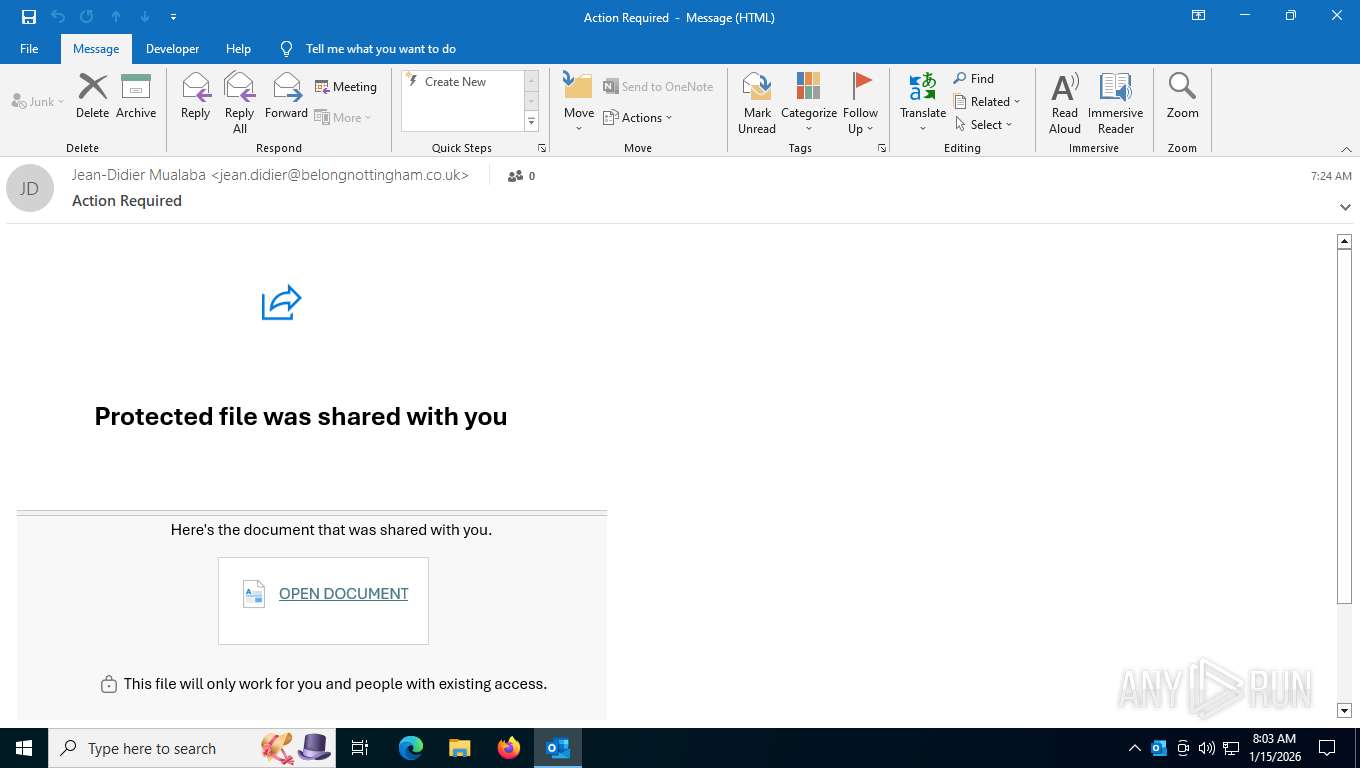
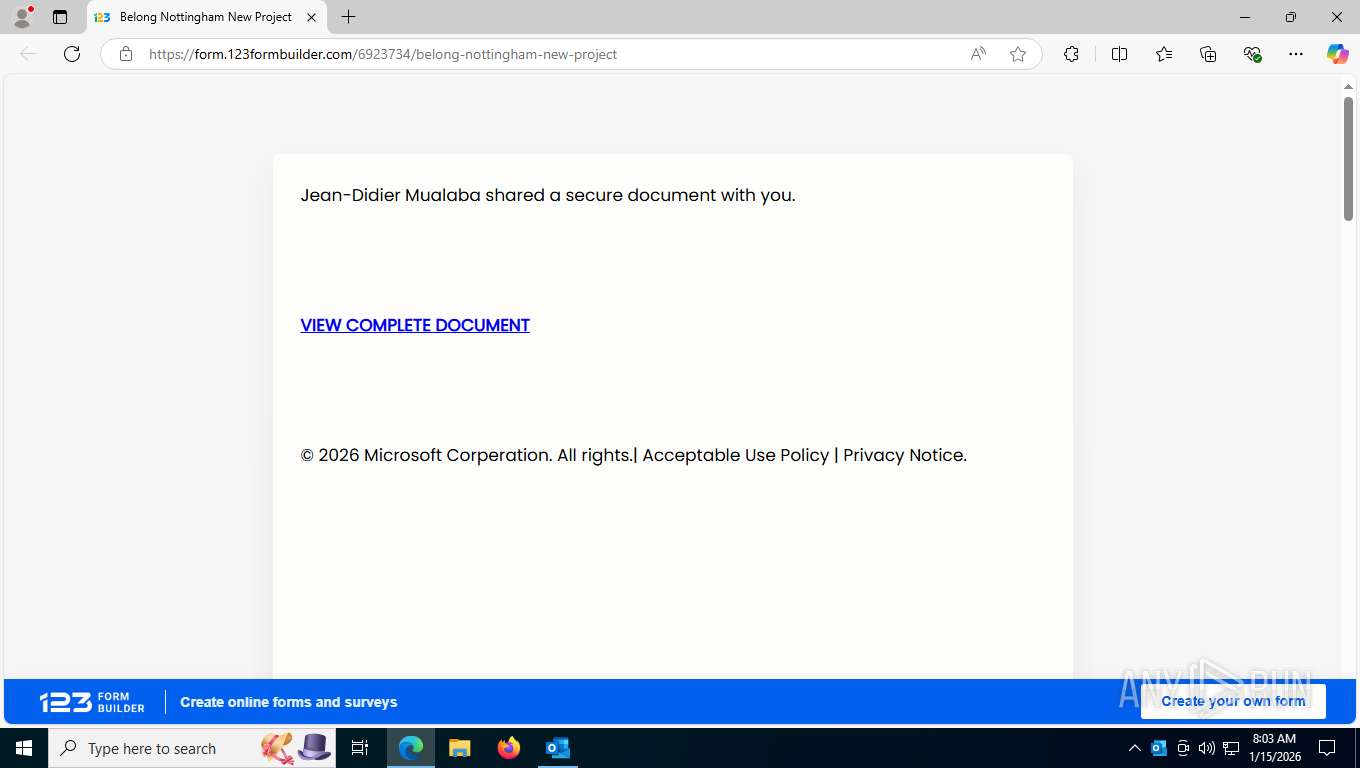
| File name: | Action Required.eml |
| Full analysis: | https://app.any.run/tasks/6b0bb24c-bfdd-40c8-a008-797d25ceff8d |
| Verdict: | Malicious activity |
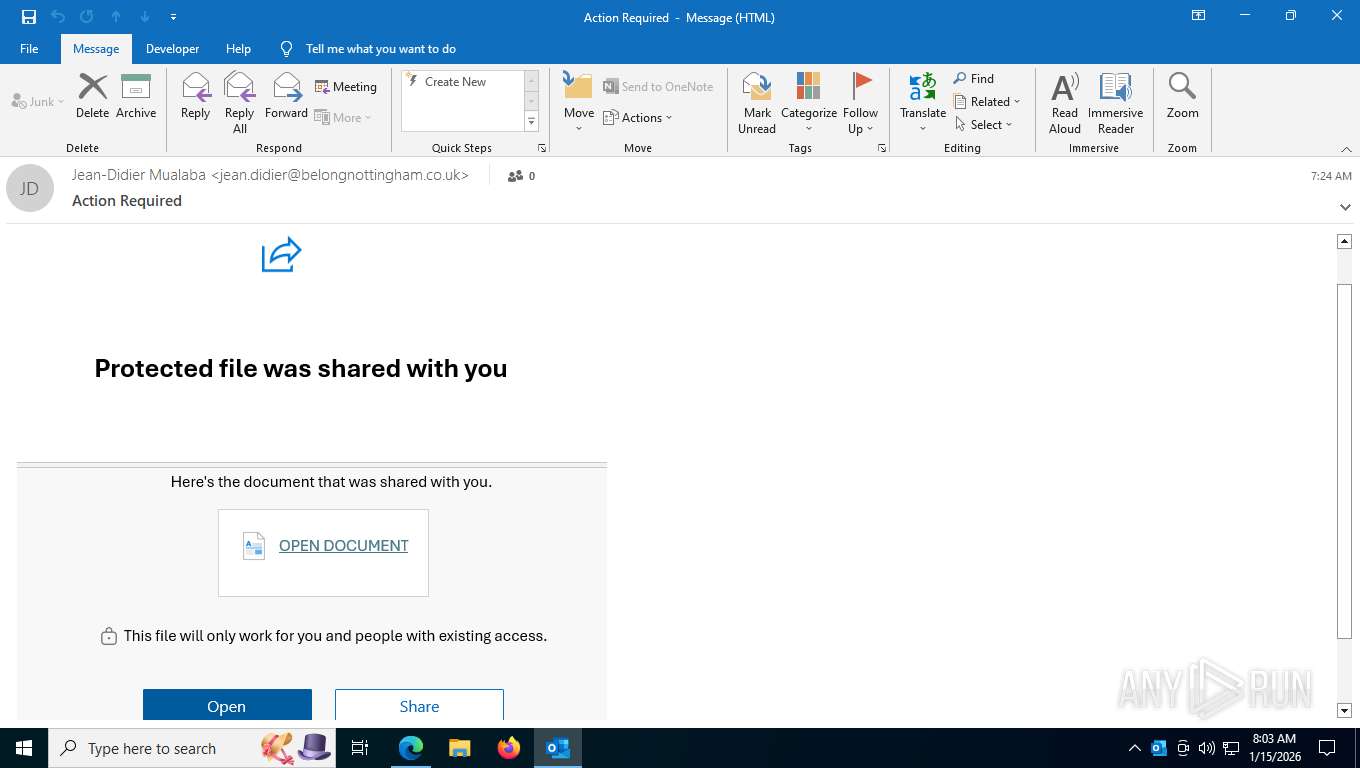
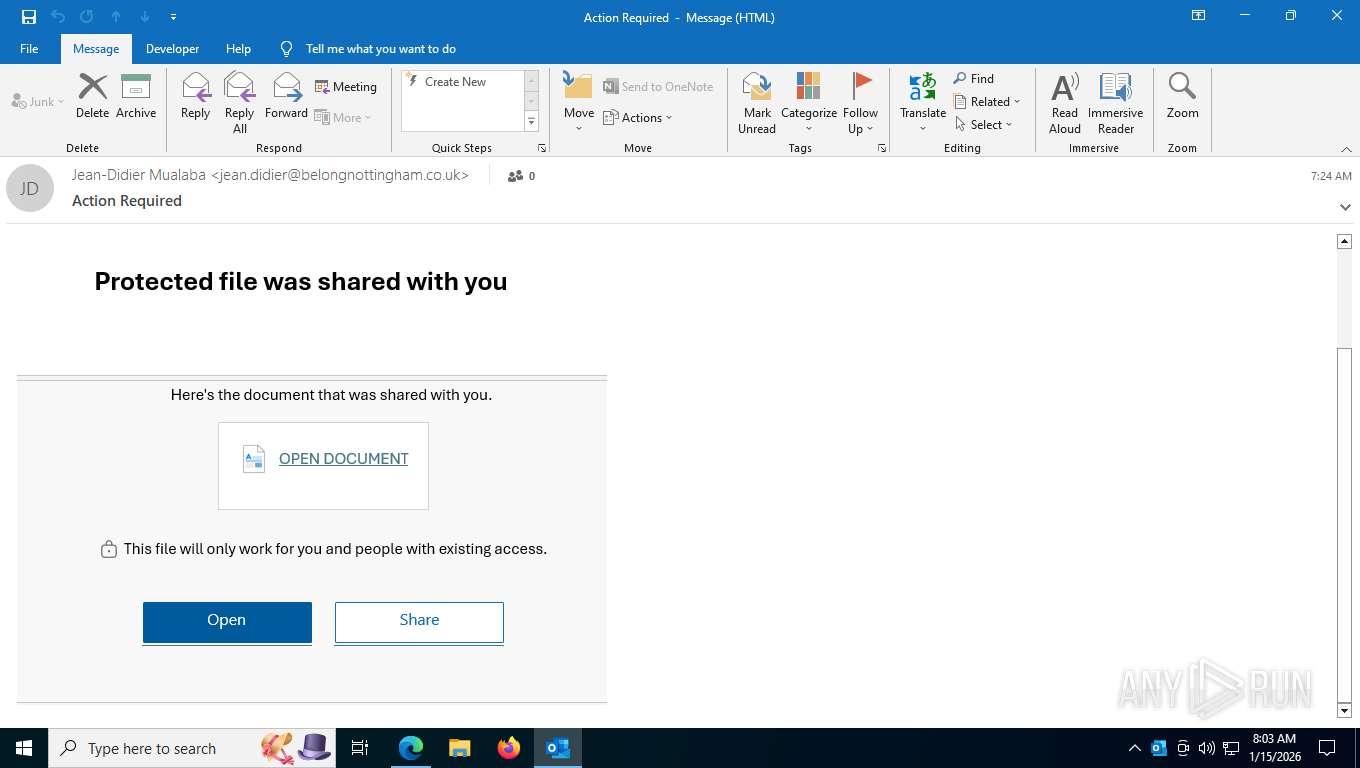
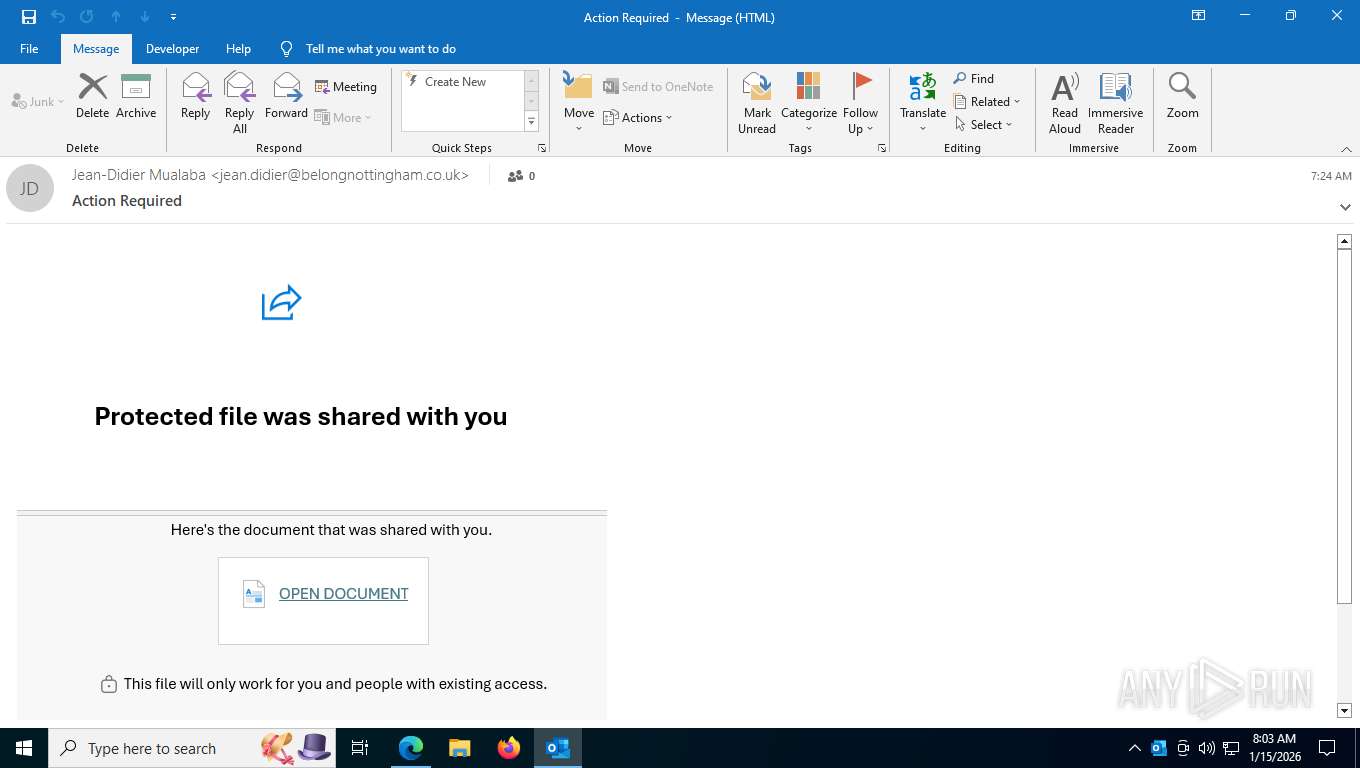
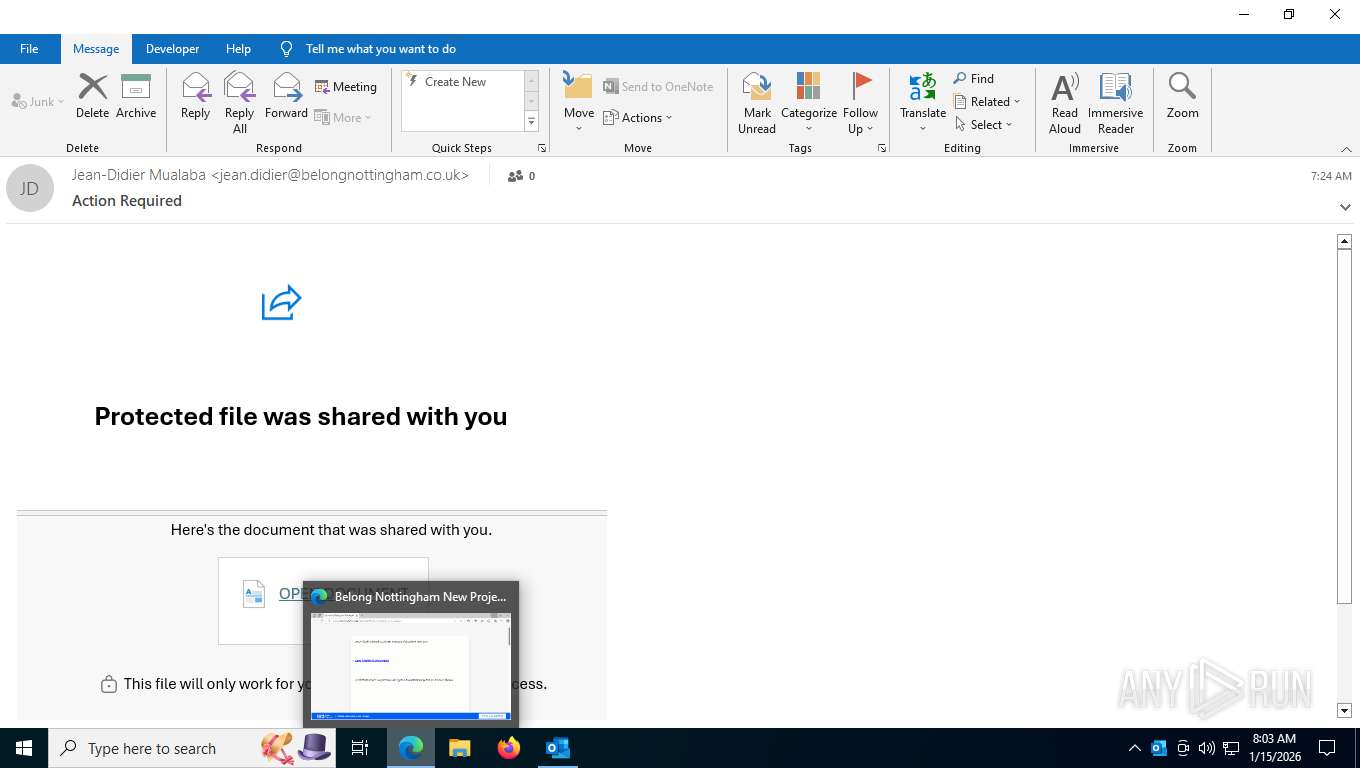
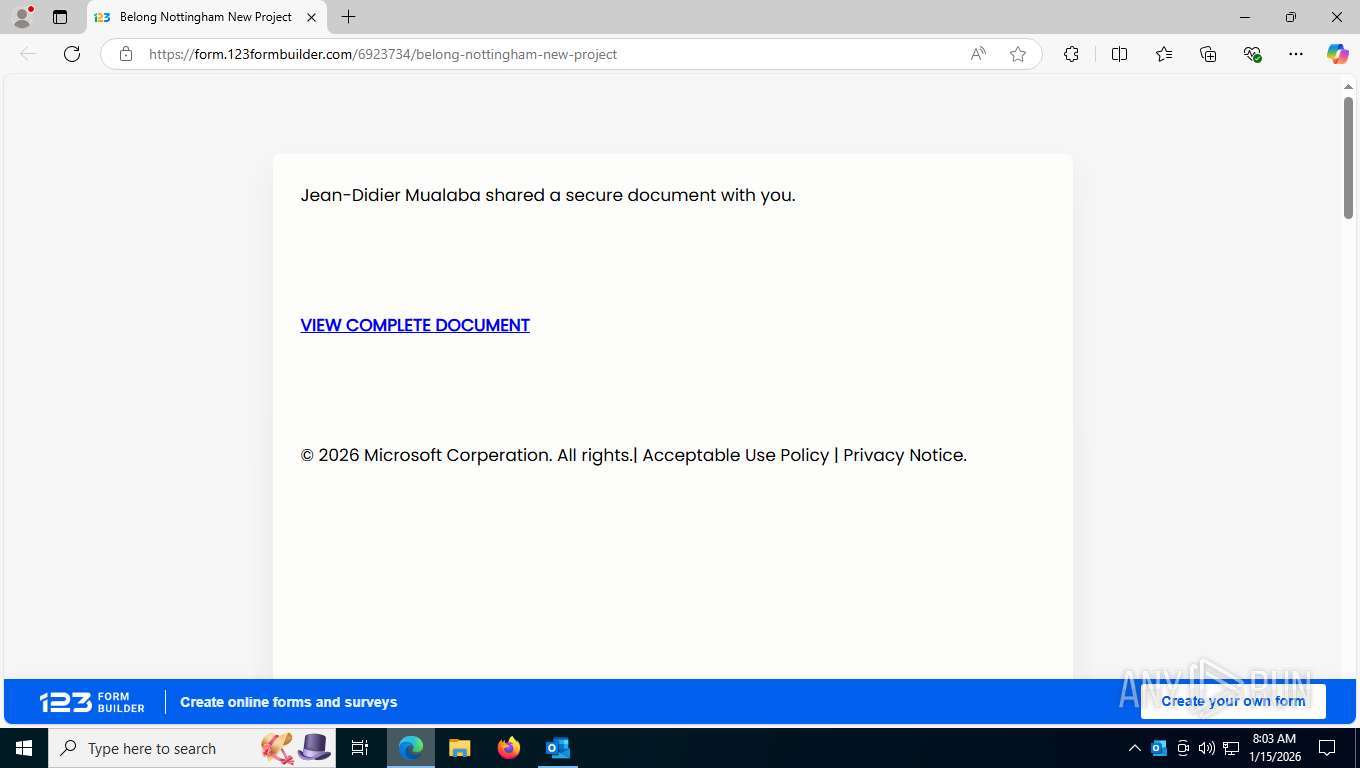
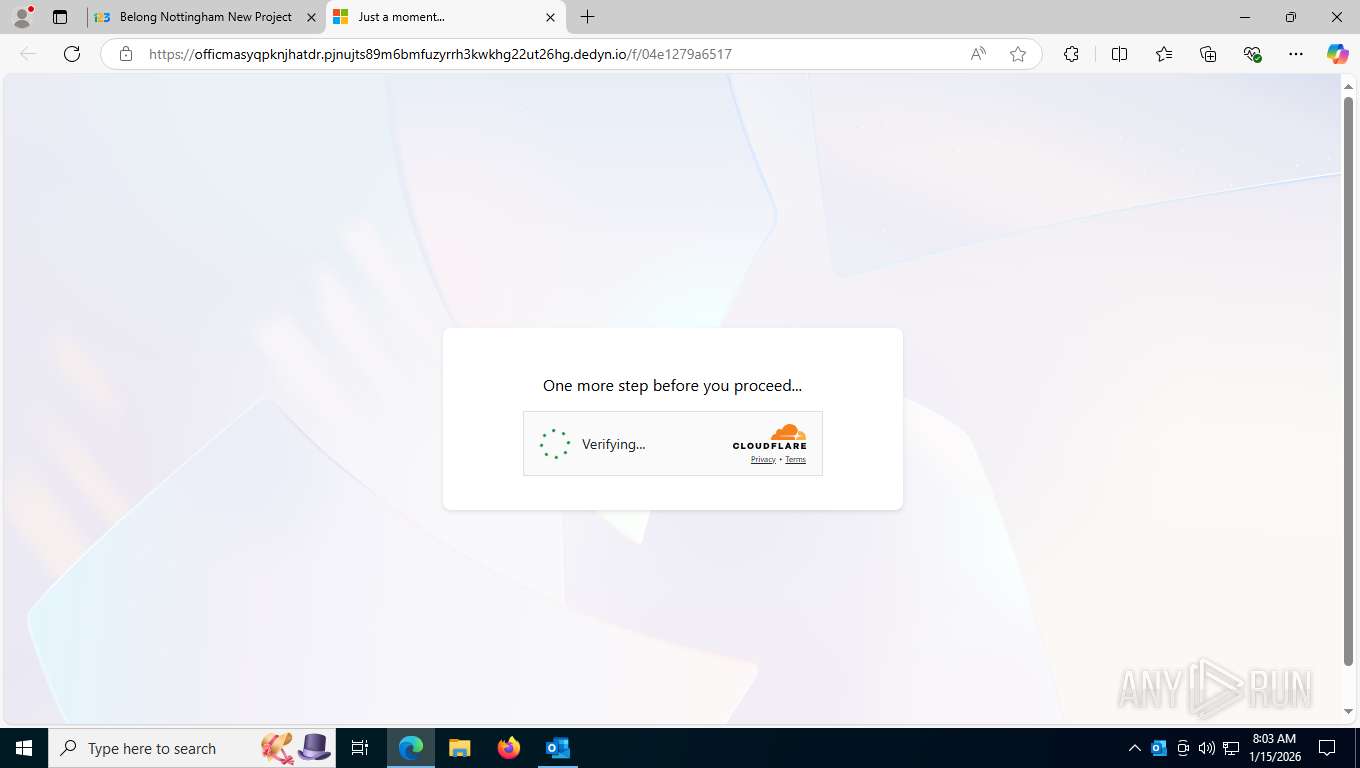
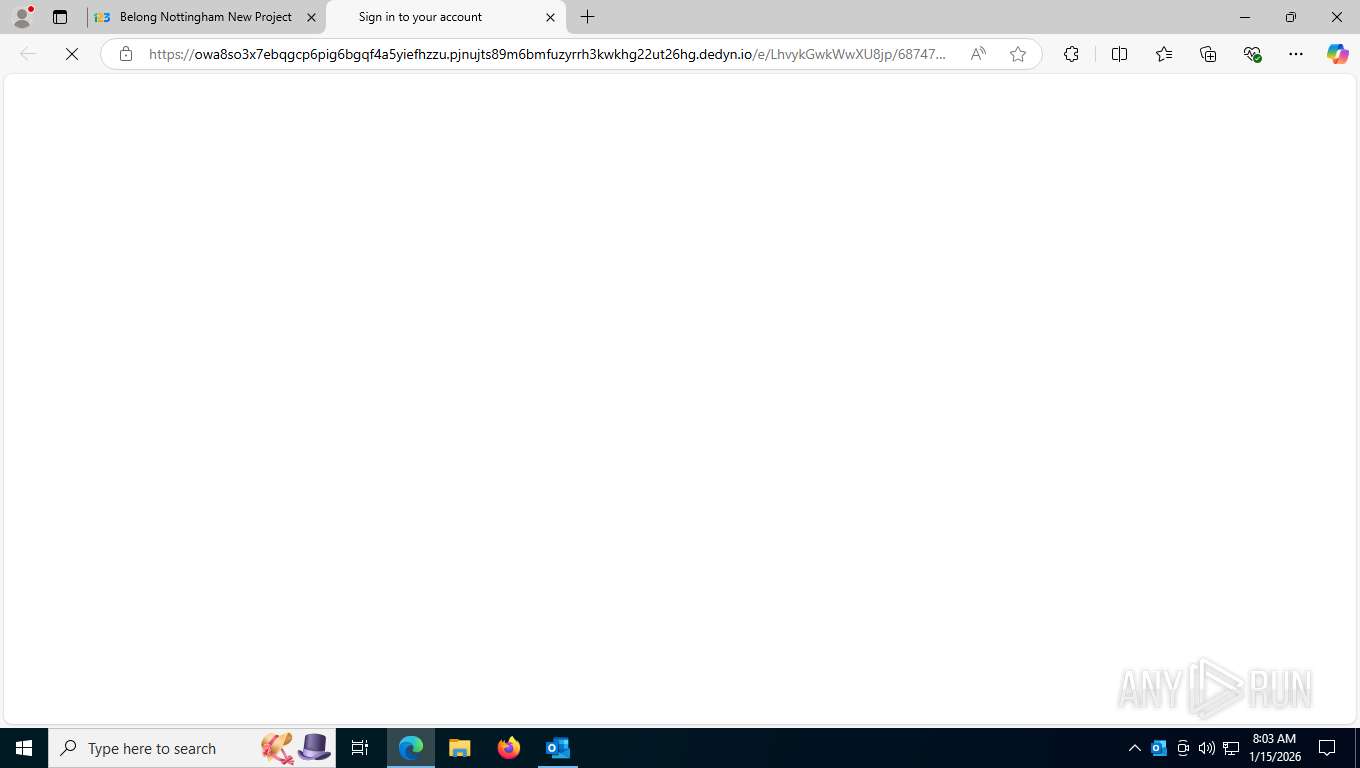
| Threats: | EvilProxy is a phishing-as-a-service (PhaaS) platform that enables cybercriminals to bypass multi-factor authentication (MFA) and hijack user sessions. It leverages reverse proxy techniques to harvest credentials and session cookies, posing a serious threat to both individuals and enterprises. |
| Analysis date: | January 15, 2026, 13:02:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | news or mail, ASCII text, with CRLF line terminators |
| MD5: | C559B855A29C62B2A33948230DAD6D3F |
| SHA1: | 8440B5C8CBC1CDEF1D32F0D5B2F006FD2E631A39 |
| SHA256: | E15E5DD300F2261CDBC1768F6E8D3DF160B323C98E82BEFCA28C9C63886B111E |
| SSDEEP: | 384:Z1KRrRCQBQaw0NE0VHHqo8MVErAenm8HNdJztAcy24uLStyLtKzXe2H3ZzrkE3nz:Z1AwuHHq9BtHNddeH2UyLtQZzzAso4 |
MALICIOUS
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 7372)
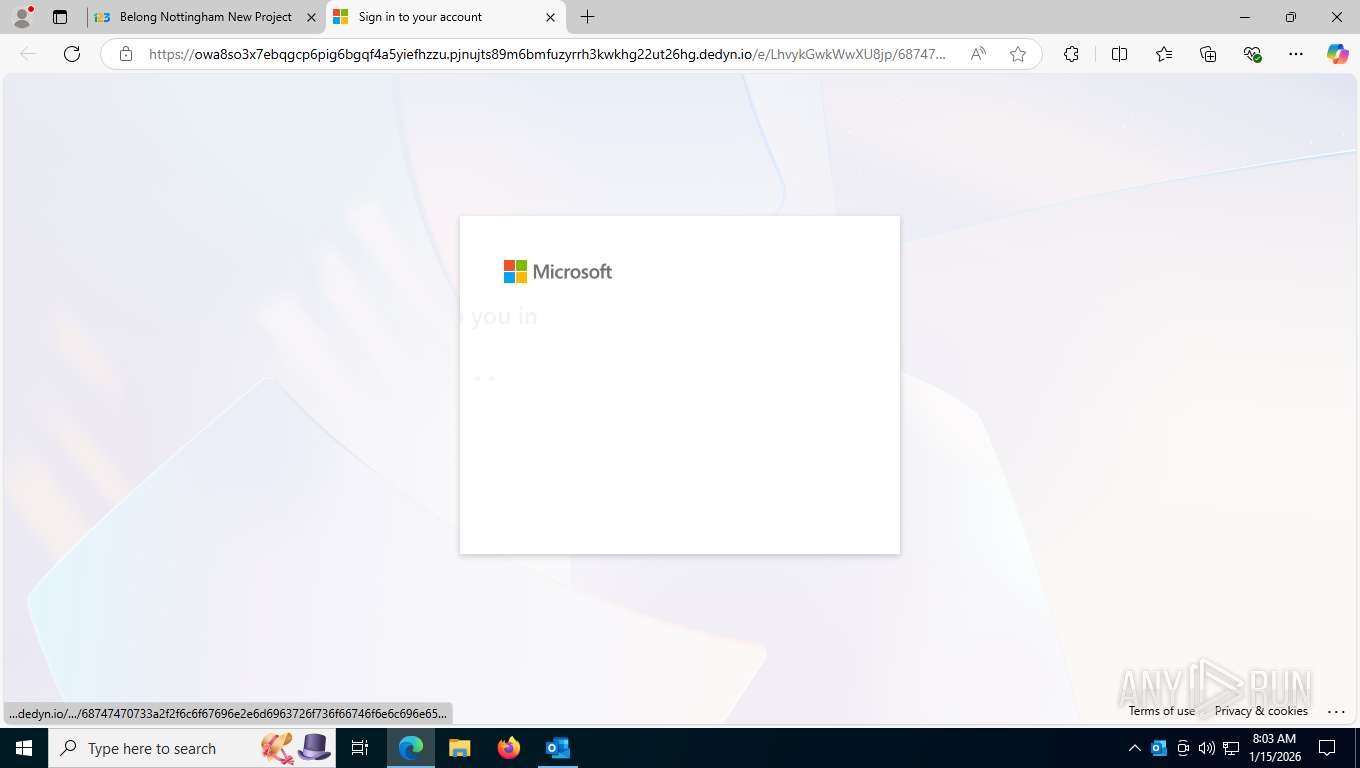
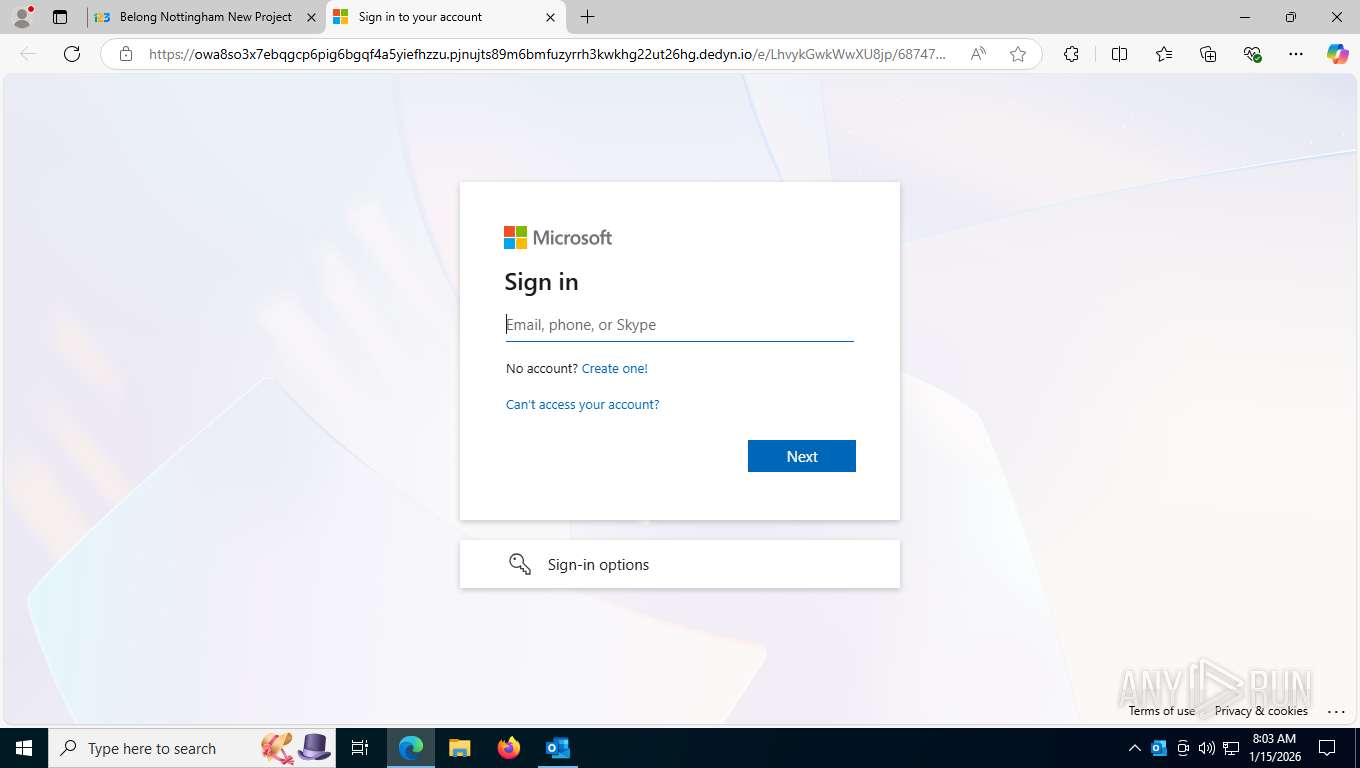
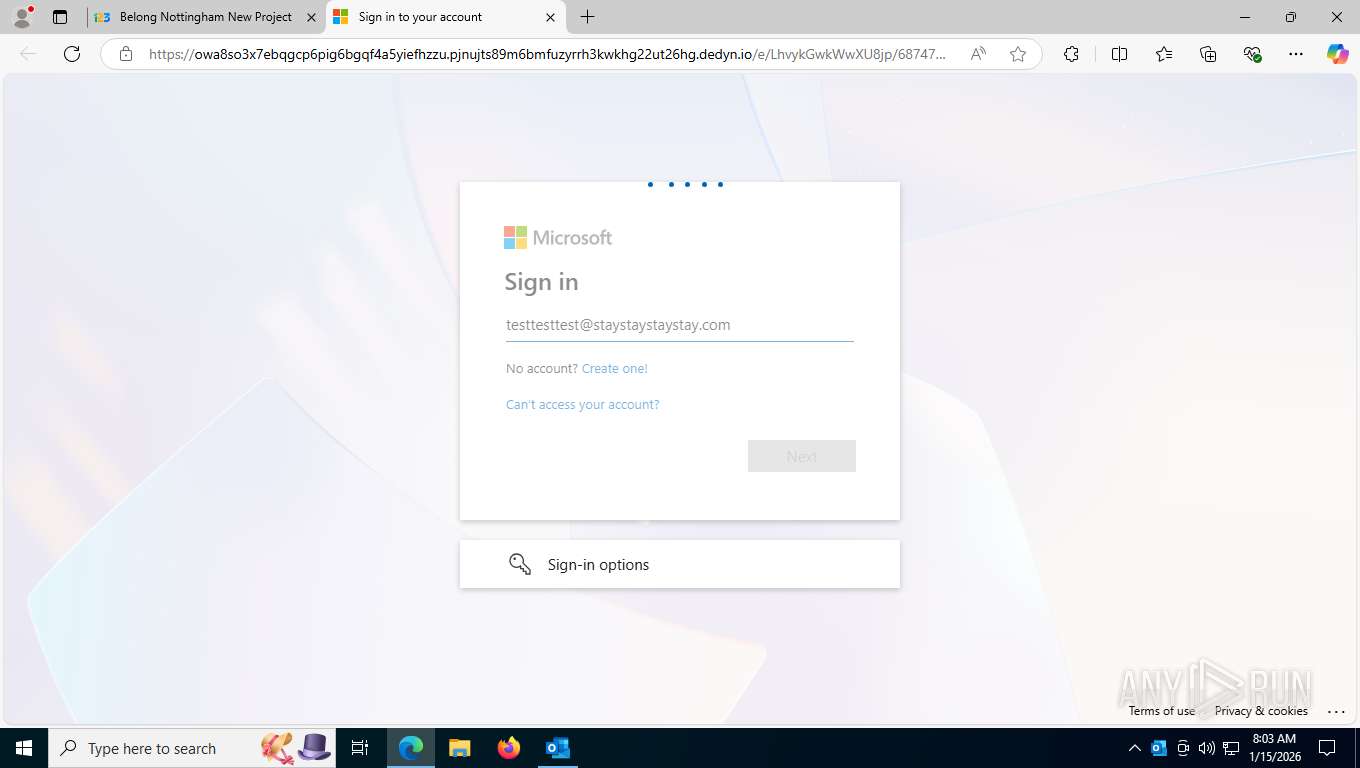
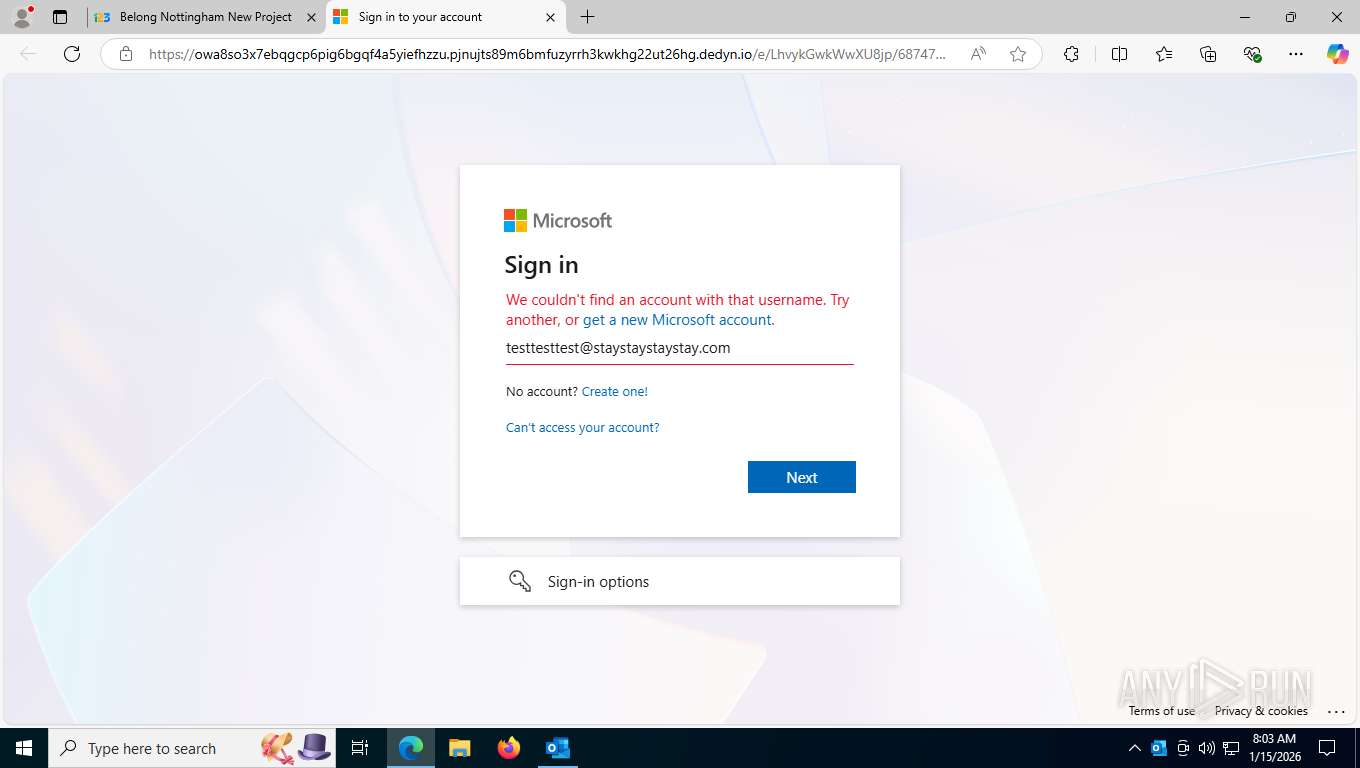
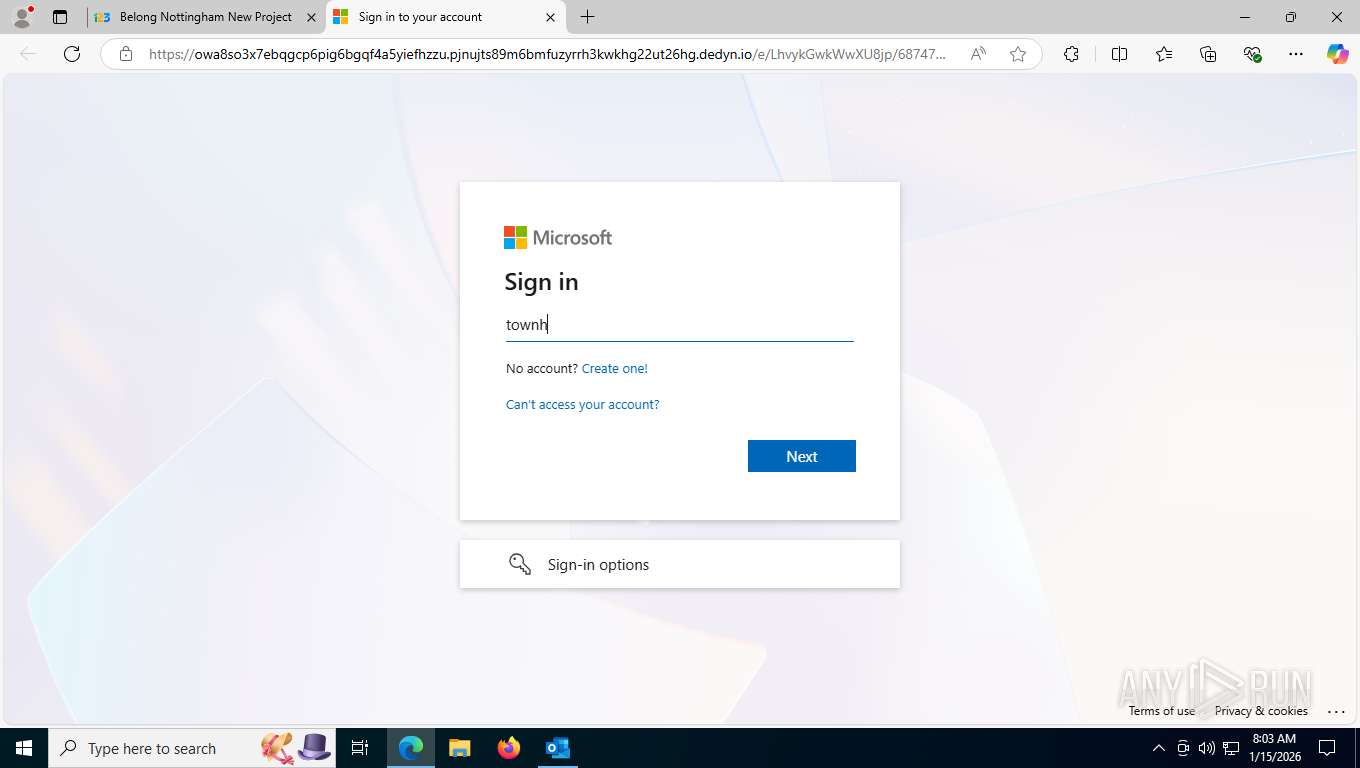
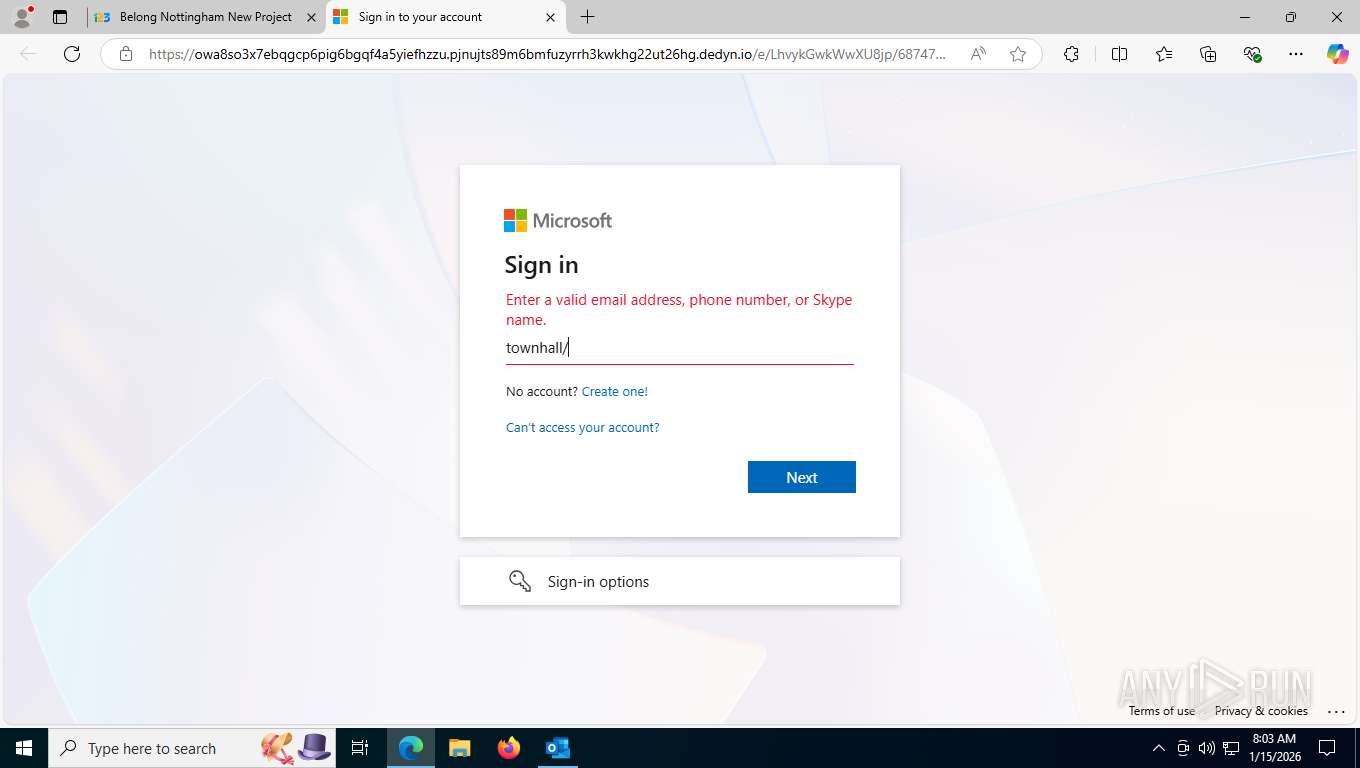
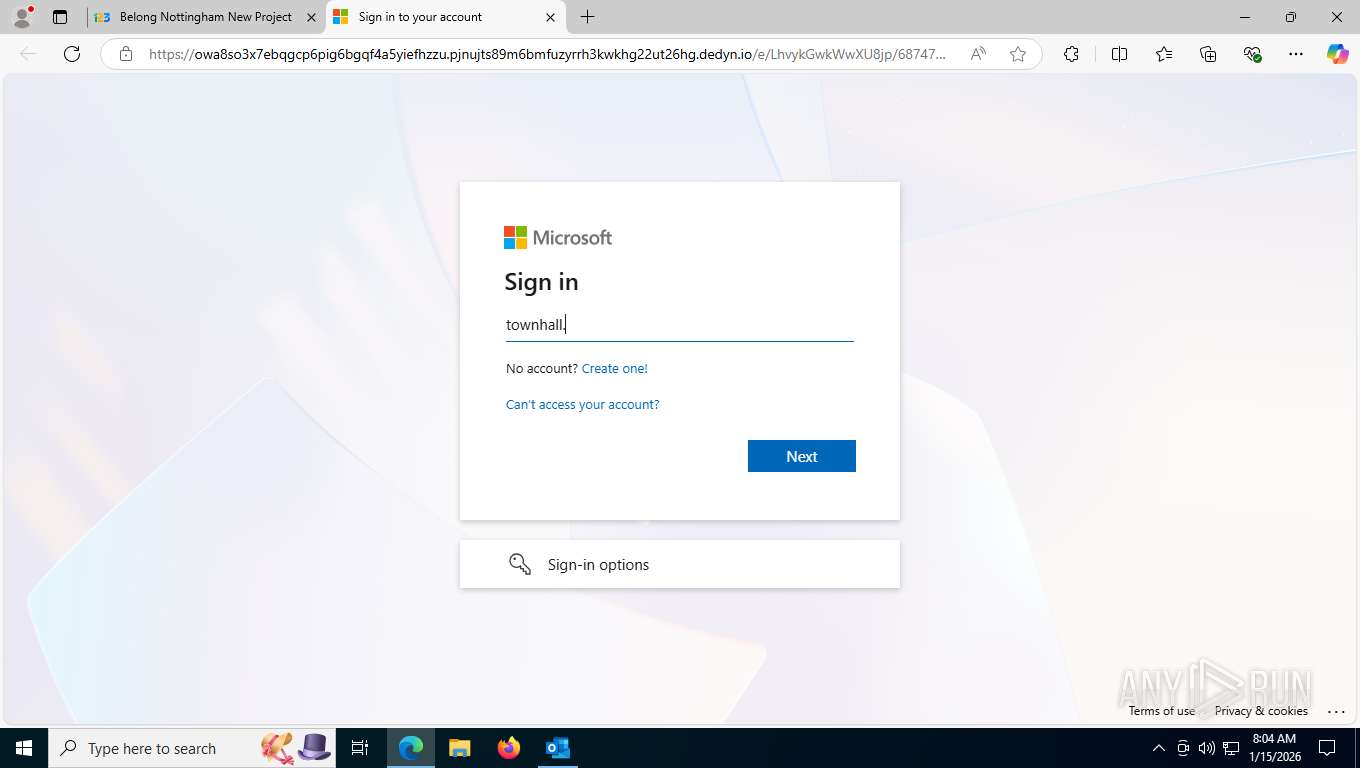
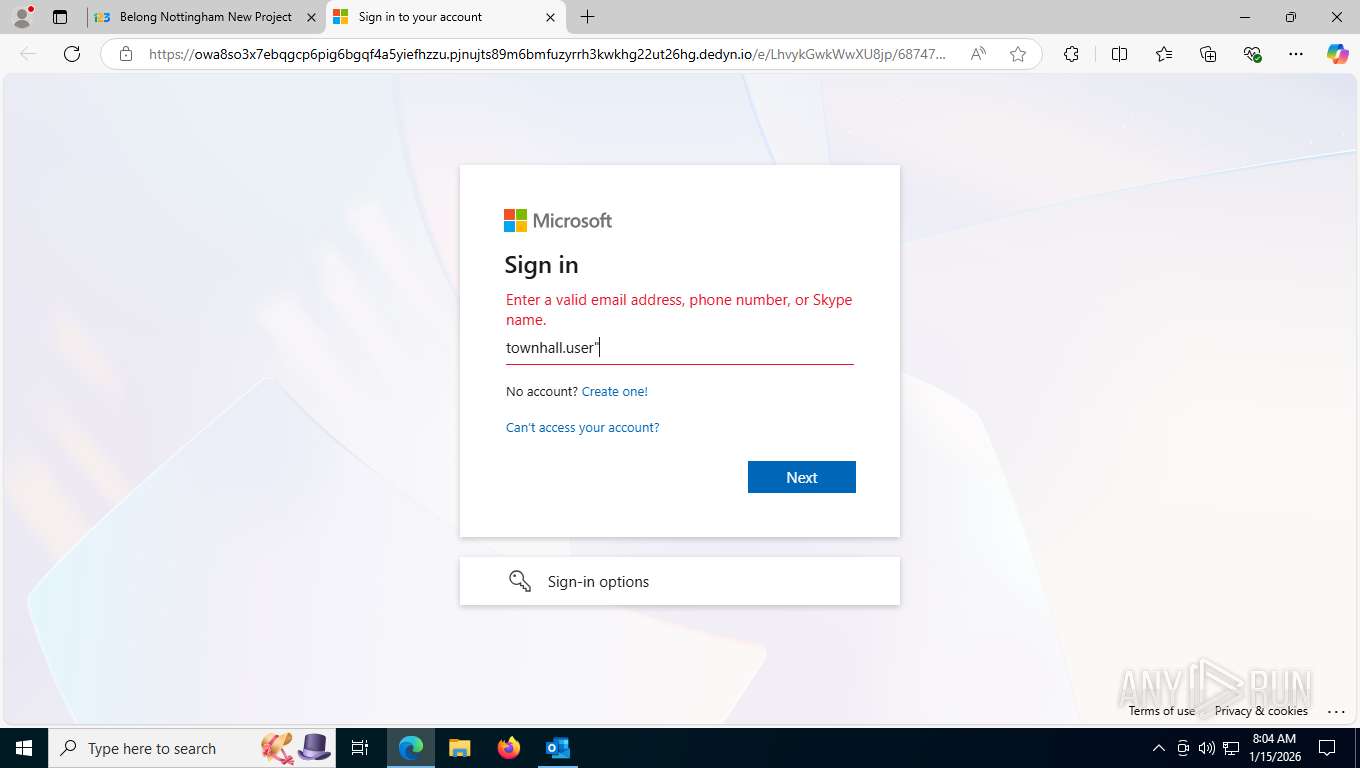
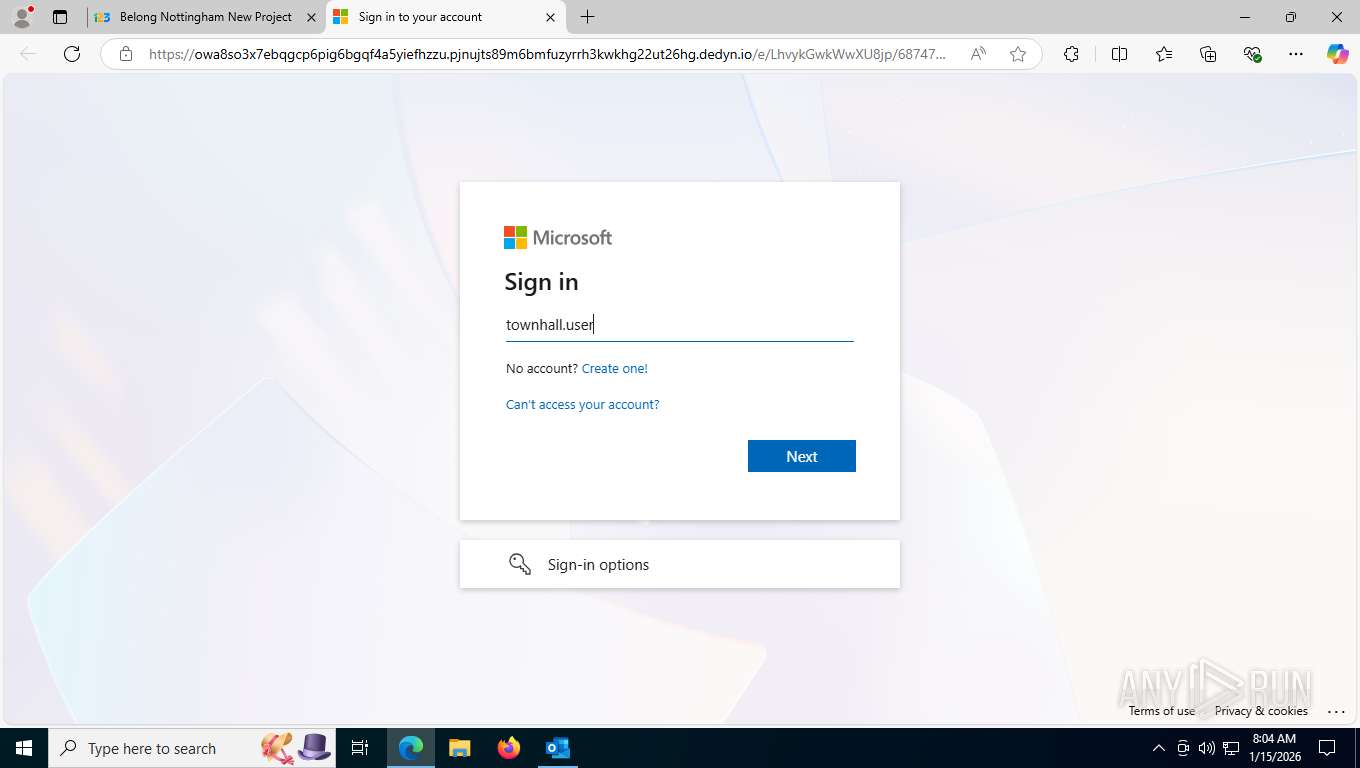
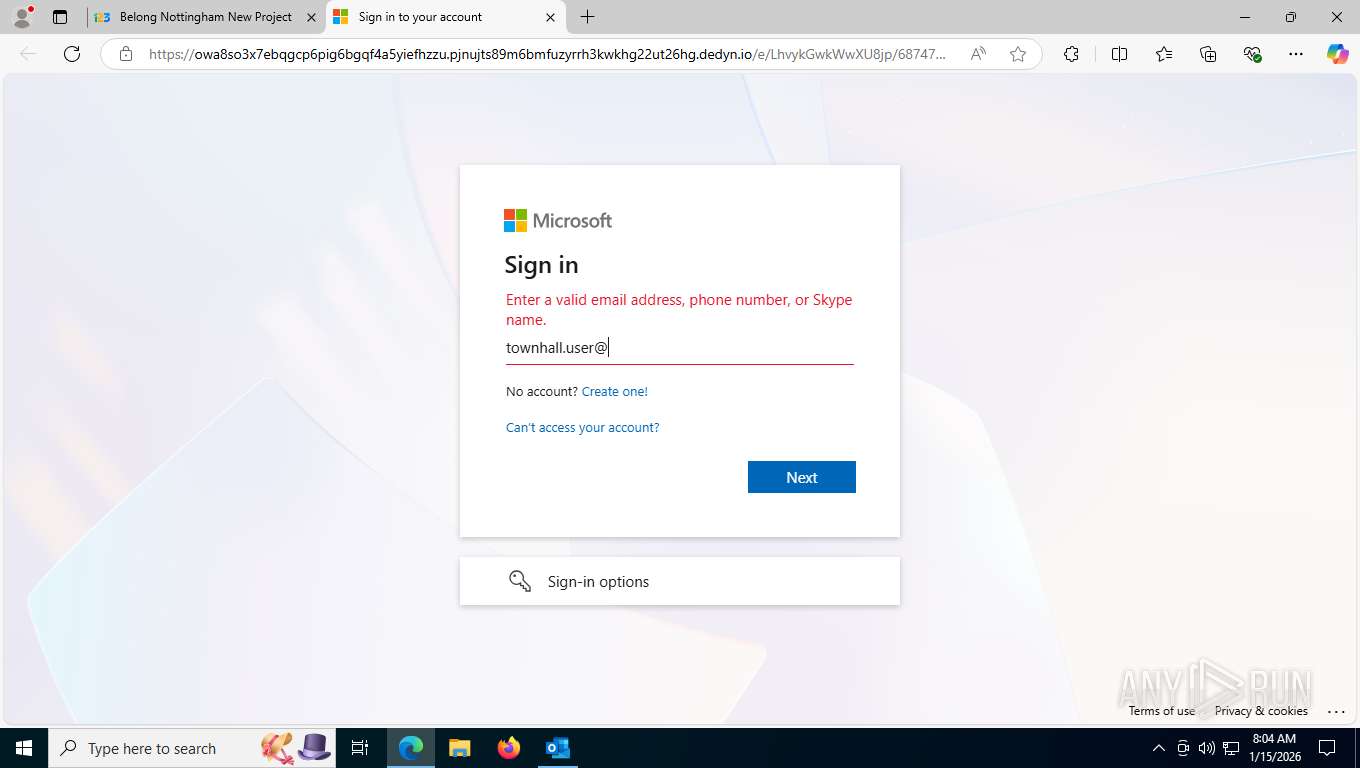
Fake Microsoft Authentication Page has been detected
- msedge.exe (PID: 6296)
EvilProxy phishing kit has been detected
- msedge.exe (PID: 6296)
SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- TextInputHost.exe (PID: 6400)
- identity_helper.exe (PID: 4220)
Checks supported languages
- TextInputHost.exe (PID: 6400)
- identity_helper.exe (PID: 4220)
Application launched itself
- msedge.exe (PID: 6296)
Reads Environment values
- identity_helper.exe (PID: 4220)
Page contains obfuscated JavaScript
- msedge.exe (PID: 6296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 2) (100) |
|---|
Total processes
171
Monitored processes
25
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3368 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=7200,i,16361905094570355208,8005477455621158374,262144 --variations-seed-version --mojo-platform-channel-handle=7384 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 4220 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=7200,i,16361905094570355208,8005477455621158374,262144 --variations-seed-version --mojo-platform-channel-handle=7384 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 6020 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x304,0x308,0x30c,0x2fc,0x314,0x7ffd70f5f208,0x7ffd70f5f214,0x7ffd70f5f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 6296 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://form.123formbuilder.com/6923734/belong-nottingham-new-project | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 6400 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 6404 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=7404,i,16361905094570355208,8005477455621158374,262144 --variations-seed-version --mojo-platform-channel-handle=7464 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 6908 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=3 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4288,i,16361905094570355208,8005477455621158374,262144 --variations-seed-version --mojo-platform-channel-handle=4296 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 7204 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2740,i,16361905094570355208,8005477455621158374,262144 --variations-seed-version --mojo-platform-channel-handle=2772 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 7276 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2268,i,16361905094570355208,8005477455621158374,262144 --variations-seed-version --mojo-platform-channel-handle=2264 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 7288 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=7700,i,16361905094570355208,8005477455621158374,262144 --variations-seed-version --mojo-platform-channel-handle=6752 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
11 396
Read events
11 028
Write events
318
Delete events
50
Modification events
| (PID) Process: | (7564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (7564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\7564 |
| Operation: | write | Name: | 0 |
Value: 0B0E107F35E29C43FB064792888F398467575F230046E0C7EFCDF4C3A1EE016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5118C3BD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (7564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (7564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (7564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (7564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (7564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (7564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (7564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
Executable files
0
Suspicious files
88
Text files
92
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7564 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7564 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:16D488DED32EBAABD892AEAB07228FF4 | SHA256:C432E1F6AD9D93C41479DBB4E6F462D151ECC4D89A3E084845AB33E1CDB030BD | |||
| 7564 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\PreviewFont\flat_officeFontsPreview_4_42.ttf | binary | |
MD5:8BDF396FED21EED0F788CB9A23775A1E | SHA256:BD6575CBCF808C13421BF03886E008624B85B6CE23651949BCFBD10EBD8452BE | |||
| 7564 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\87762AEF-961F-45B0-BB7B-422AA6BD184E | xml | |
MD5:1CB262A29CF9A57D07AE5272CE67F90A | SHA256:336BACFAC940014383660FCB9E908225586640EAC65E5E837F72B567FF196FBD | |||
| 7564 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\Catalog\ListAll.Json | text | |
MD5:7C5578BC58BDE6DC855D5C929CF54232 | SHA256:A48ACBE81F33E5918B096A6B89687E505DA0E79196F74DC48B6E068708378A3F | |||
| 7564 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_WorkHours_1_DBE94A85F8649B4FBBEA7ED958BFE171.dat | xml | |
MD5:9CA1DA1D62A9FF574E63B8946B541C96 | SHA256:B6B10A07FAA634027F3780E77FC3B165DCF7D37E800195BFF5E147CCC492B828 | |||
| 7564 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\9C78843B.dat | image | |
MD5:742C8D629D379733572820DADC7BC903 | SHA256:93CF8E4E1115F75FBB2EB9561D5A4E859231189D0F7415F5D40B8CCD6FC5FB0F | |||
| 6296 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RFffa26.TMP | — | |
MD5:— | SHA256:— | |||
| 6296 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6296 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RFffa35.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
183
TCP/UDP connections
126
DNS requests
119
Threats
63
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7564 | OUTLOOK.EXE | GET | 200 | 52.123.129.14:443 | https://ecs.office.com/config/v2/Office/outlook/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=outlook&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=outlook.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7b9CE2357F-FB43-4706-9288-8F398467575F%7d&LabMachine=false | unknown | text | 128 Kb | unknown |
7564 | OUTLOOK.EXE | GET | 200 | 52.111.246.2:443 | https://messaging.lifecycle.office.com/getcustommessage16?app=6&ui=en-US&src=BizBar&messagetype=BizBar&hwid=04111-083-043729&ver=16.0.16026&lc=en-US&platform=10%3A0%3A19045%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA720%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7B9CE2357F-FB43-4706-9288-8F398467575F%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofsh6c2b1tla1a31%2Cofcrui4yvdulbf31%2Cofhpex3jznepoo31%2Cofpioygfqmufst31%22%7D | unknown | text | 542 b | unknown |
7564 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7564 | OUTLOOK.EXE | GET | 200 | 52.109.28.46:443 | https://officeclient.microsoft.com/config16/?lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3 | unknown | xml | 128 Kb | whitelisted |
7564 | OUTLOOK.EXE | GET | 200 | 104.102.63.189:443 | https://fs.microsoft.com/fs/4.42/flatFontAssets.pkg | unknown | compressed | 128 Kb | whitelisted |
1080 | svchost.exe | POST | 200 | 40.126.32.68:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
7564 | OUTLOOK.EXE | POST | 200 | 135.225.150.15:443 | https://editor.svc.cloud.microsoft/NlEditor/CloudSuggest/V1 | unknown | text | 155 b | unknown |
1080 | svchost.exe | POST | 200 | 40.126.32.68:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
5768 | svchost.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7564 | OUTLOOK.EXE | GET | 200 | 184.86.251.133:443 | https://omex.cdn.office.net/addinclassifier/officesharedentities | unknown | text | 128 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5768 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | Not routed | — | whitelisted |
6768 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3192 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | Not routed | — | whitelisted |
7564 | OUTLOOK.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7564 | OUTLOOK.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3412 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7564 | OUTLOOK.EXE | 104.102.63.189:443 | fs.microsoft.com | AKAMAI-AS | US | whitelisted |
7564 | OUTLOOK.EXE | 52.109.28.47:443 | roaming.svc.cloud.microsoft | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
roaming.svc.cloud.microsoft |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7372 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (ln .run) |
7372 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (ln .run) |
7372 | msedge.exe | Potentially Bad Traffic | ET DYN_DNS Observed DNS Query to Dynamic DNS Domain (dedyn .io) |
7372 | msedge.exe | Potentially Bad Traffic | ET DYN_DNS Observed DNS Query to Dynamic DNS Domain (dedyn .io) |
7372 | msedge.exe | Misc activity | ET INFO Observed Dynamic DNS Domain (dedyn .io in TLS SNI) |
7372 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7372 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7372 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7372 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
7372 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |