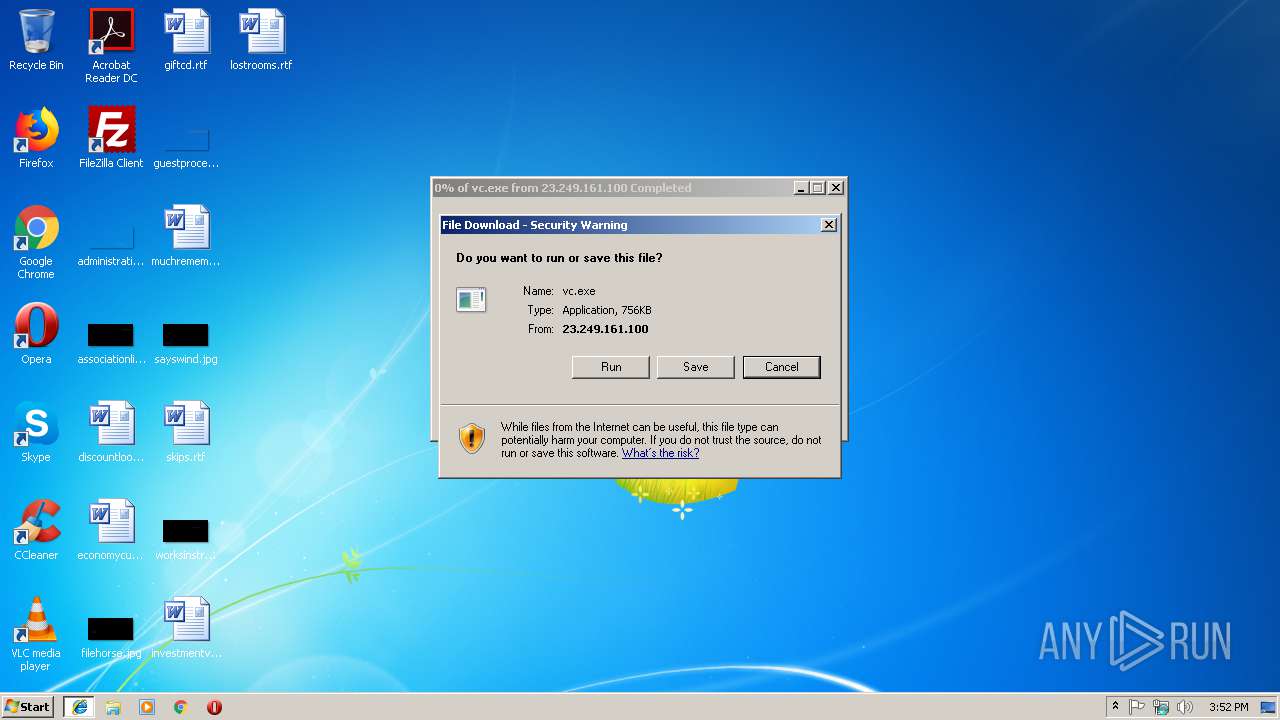
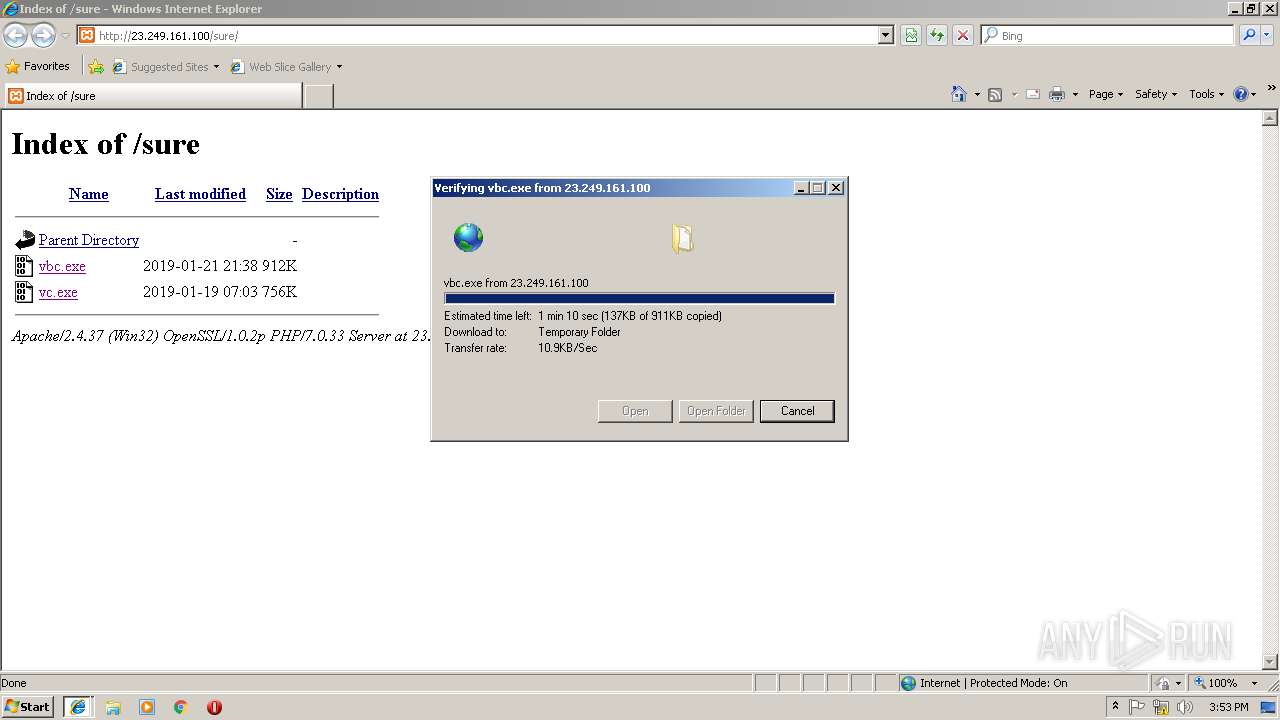
| URL: | http://23.249.161.100/sure/vc.exe |
| Full analysis: | https://app.any.run/tasks/a3f4a4da-b645-4859-a327-0e83f4457900 |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | January 22, 2019, 15:52:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | DD6642788DA9D8C14A5599B91564A7A5 |
| SHA1: | 5DA9029B682B33C518E4445A052409B795754164 |
| SHA256: | E144FF6E8AC7C7D87A65A4D84A09097804D5485E4816F23D784D76FFF14E4912 |
| SSDEEP: | 3:N1KbEMgrk:CIMg4 |
MALICIOUS
Downloads executable files from IP
- iexplore.exe (PID: 3228)
- iexplore.exe (PID: 2284)
- RegAsm.exe (PID: 3936)
Application was dropped or rewritten from another process
- vc[1].exe (PID: 2776)
- vbc[1].exe (PID: 3064)
- vbc[1].exe (PID: 2608)
- Z[1].exe (PID: 3484)
- dmw[1].exe (PID: 916)
- n[1].exe (PID: 1984)
- tmp1850.tmpzna.exe (PID: 3268)
- nisa[1].exe (PID: 3672)
- nsa[1].exe (PID: 2724)
- vbc[1].exe (PID: 2256)
- vbn[1].exe (PID: 3520)
- zah[1].exe (PID: 4076)
- zna[1].exe (PID: 3952)
- zahr[1].exe (PID: 3140)
Downloads executable files from the Internet
- iexplore.exe (PID: 3228)
- iexplore.exe (PID: 2284)
- RegAsm.exe (PID: 3936)
Writes to a start menu file
- dmw[1].exe (PID: 916)
- tmp1850.tmpzna.exe (PID: 3268)
- nisa[1].exe (PID: 3672)
- nsa[1].exe (PID: 2724)
- vbc[1].exe (PID: 2256)
- vbn[1].exe (PID: 3520)
- zah[1].exe (PID: 4076)
- zahr[1].exe (PID: 3140)
- zna[1].exe (PID: 3952)
Detected Hawkeye Keylogger
- vbc[1].exe (PID: 2608)
- RegAsm.exe (PID: 3216)
- RegAsm.exe (PID: 2476)
- RegAsm.exe (PID: 1912)
- RegAsm.exe (PID: 1144)
- RegAsm.exe (PID: 2580)
Actions looks like stealing of personal data
- vbc.exe (PID: 3912)
- vbc.exe (PID: 3556)
- vbc.exe (PID: 576)
- vbc.exe (PID: 3468)
- vbc.exe (PID: 3848)
- vbc.exe (PID: 4000)
- vbc.exe (PID: 348)
- vbc.exe (PID: 3828)
- vbc.exe (PID: 3796)
- vbc.exe (PID: 3544)
- vbc.exe (PID: 2740)
- vbc.exe (PID: 2636)
Stealing of credential data
- vbc.exe (PID: 3912)
- vbc.exe (PID: 3556)
- vbc.exe (PID: 576)
- vbc.exe (PID: 3468)
- vbc.exe (PID: 3848)
- vbc.exe (PID: 4000)
- vbc.exe (PID: 3828)
- vbc.exe (PID: 348)
- vbc.exe (PID: 3544)
- vbc.exe (PID: 3796)
- vbc.exe (PID: 2636)
- vbc.exe (PID: 2740)
Connects to CnC server
- RegAsm.exe (PID: 3936)
NJRAT was detected
- RegAsm.exe (PID: 3936)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 3228)
- iexplore.exe (PID: 3816)
- iexplore.exe (PID: 2964)
- iexplore.exe (PID: 2284)
- dmw[1].exe (PID: 916)
- RegAsm.exe (PID: 3936)
- nisa[1].exe (PID: 3672)
- vbn[1].exe (PID: 3520)
- zahr[1].exe (PID: 3140)
Cleans NTFS data-stream (Zone Identifier)
- vbc[1].exe (PID: 3064)
- dmw[1].exe (PID: 916)
- nisa[1].exe (PID: 3672)
- vbn[1].exe (PID: 3520)
- zahr[1].exe (PID: 3140)
Reads Environment values
- vbc[1].exe (PID: 2608)
Connects to SMTP port
- vbc[1].exe (PID: 2608)
Creates files in the user directory
- dmw[1].exe (PID: 916)
- nisa[1].exe (PID: 3672)
- vbn[1].exe (PID: 3520)
- zahr[1].exe (PID: 3140)
Application launched itself
- vbc[1].exe (PID: 3064)
Connects to unusual port
- RegAsm.exe (PID: 3936)
Executes scripts
- vbc[1].exe (PID: 2608)
- RegAsm.exe (PID: 3216)
- RegAsm.exe (PID: 2476)
- RegAsm.exe (PID: 1912)
- RegAsm.exe (PID: 1144)
- RegAsm.exe (PID: 2580)
Loads DLL from Mozilla Firefox
- vbc.exe (PID: 3912)
- vbc.exe (PID: 4000)
- vbc.exe (PID: 348)
- vbc.exe (PID: 3544)
- vbc.exe (PID: 2740)
- vbc.exe (PID: 576)
INFO
Application launched itself
- iexplore.exe (PID: 2964)
Reads Internet Cache Settings
- iexplore.exe (PID: 2284)
- iexplore.exe (PID: 2964)
- iexplore.exe (PID: 3228)
Changes internet zones settings
- iexplore.exe (PID: 2964)
- iexplore.exe (PID: 3816)
Reads internet explorer settings
- iexplore.exe (PID: 2284)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3816)
- iexplore.exe (PID: 2284)
Reads settings of System Certificates
- RegAsm.exe (PID: 3936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
72
Monitored processes
39
Malicious processes
25
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 348 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe" /stext "C:\Users\admin\AppData\Local\Temp\tmpCAC7.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | RegAsm.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 576 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe" /stext "C:\Users\admin\AppData\Local\Temp\tmp641E.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | RegAsm.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 916 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2YPIJ90\dmw[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2YPIJ90\dmw[1].exe | iexplore.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Setup Exit code: 0 Version: 8.13.0.3 Modules
| |||||||||||||||
| 1144 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | zahr[1].exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 1912 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | vbn[1].exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 1984 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\n[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\n[1].exe | — | iexplore.exe | |||||||||||
User: admin Company: Simon Tatham Integrity Level: MEDIUM Description: SSH, Telnet and Rlogin client Exit code: 0 Version: Release 0.70 Modules
| |||||||||||||||
| 2256 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2YPIJ90\vbc[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2YPIJ90\vbc[1].exe | iexplore.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Setup Exit code: 0 Version: 8.13.0.3 Modules
| |||||||||||||||
| 2284 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3816 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2476 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | nisa[1].exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 2580 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | zna[1].exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
Total events
2 273
Read events
2 091
Write events
178
Delete events
4
Modification events
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {B9727591-1E5D-11E9-AA93-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070100020016000F0034001F008903 | |||
Executable files
29
Suspicious files
1
Text files
71
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2964 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2964 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF62C9E4038CA3E07D.TMP | — | |
MD5:— | SHA256:— | |||
| 2964 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFF6E3C971E85332D0.TMP | — | |
MD5:— | SHA256:— | |||
| 2964 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{B9727591-1E5D-11E9-AA93-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 3816 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2YPIJ90\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3816 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2284 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\sure[1].txt | — | |
MD5:— | SHA256:— | |||
| 3816 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
| 3228 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\JavaDeployReg.log | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
39
DNS requests
14
Threats
64
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2284 | iexplore.exe | GET | — | 23.249.161.100:80 | http://23.249.161.100/sure/ | US | — | — | malicious |
2284 | iexplore.exe | GET | 302 | 23.249.161.100:80 | http://23.249.161.100/ | US | — | — | malicious |
2284 | iexplore.exe | GET | 200 | 23.249.161.100:80 | http://23.249.161.100/sure/vbc.exe | US | executable | 911 Kb | malicious |
2284 | iexplore.exe | GET | 200 | 23.249.161.100:80 | http://23.249.161.100/dashboard/ | US | html | 7.40 Kb | malicious |
2284 | iexplore.exe | GET | 200 | 23.249.161.100:80 | http://23.249.161.100/icons/blank.gif | US | image | 148 b | malicious |
2284 | iexplore.exe | GET | 200 | 23.249.161.100:80 | http://23.249.161.100/icons/binary.gif | US | image | 246 b | malicious |
2964 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
2284 | iexplore.exe | GET | 200 | 23.249.161.100:80 | http://23.249.161.100/icons/back.gif | US | image | 216 b | malicious |
2284 | iexplore.exe | GET | 200 | 104.19.197.151:80 | http://cdnjs.cloudflare.com/ajax/libs/font-awesome/3.1.0/css/font-awesome.min.css | US | text | 4.11 Kb | whitelisted |
3816 | iexplore.exe | GET | 200 | 23.249.161.100:80 | http://23.249.161.100/favicon.ico | US | image | 30.1 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3816 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3228 | iexplore.exe | 23.249.161.100:80 | — | ColoCrossing | US | malicious |
2284 | iexplore.exe | 23.249.161.100:80 | — | ColoCrossing | US | malicious |
3816 | iexplore.exe | 23.249.161.100:80 | — | ColoCrossing | US | malicious |
2284 | iexplore.exe | 157.240.1.35:443 | www.facebook.com | Facebook, Inc. | US | whitelisted |
2284 | iexplore.exe | 104.19.197.151:80 | cdnjs.cloudflare.com | Cloudflare Inc | US | shared |
2284 | iexplore.exe | 31.13.90.6:80 | connect.facebook.net | Facebook, Inc. | IE | whitelisted |
2608 | vbc[1].exe | 157.230.154.9:25 | mail.firstmetalcorp.ml | Joao Carlos de Almeida Silveira trading as Bitcanal | US | unknown |
3936 | RegAsm.exe | 23.249.161.100:80 | — | ColoCrossing | US | malicious |
2284 | iexplore.exe | 31.13.90.6:443 | connect.facebook.net | Facebook, Inc. | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
connect.facebook.net |
| whitelisted |
code.jquery.com |
| whitelisted |
www.facebook.com |
| whitelisted |
bot.whatismyipaddress.com |
| shared |
mail.firstmetalcorp.ml |
| suspicious |
pastebin.com |
| malicious |
hawkeye.sx |
| unknown |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3228 | iexplore.exe | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
3228 | iexplore.exe | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
3228 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3228 | iexplore.exe | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
2284 | iexplore.exe | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
2284 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2284 | iexplore.exe | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
2608 | vbc[1].exe | Misc activity | SUSPICIOUS [PTsecurity] External IP Request (HawkEye) |
1052 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .ml Domain |
2284 | iexplore.exe | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
15 ETPRO signatures available at the full report