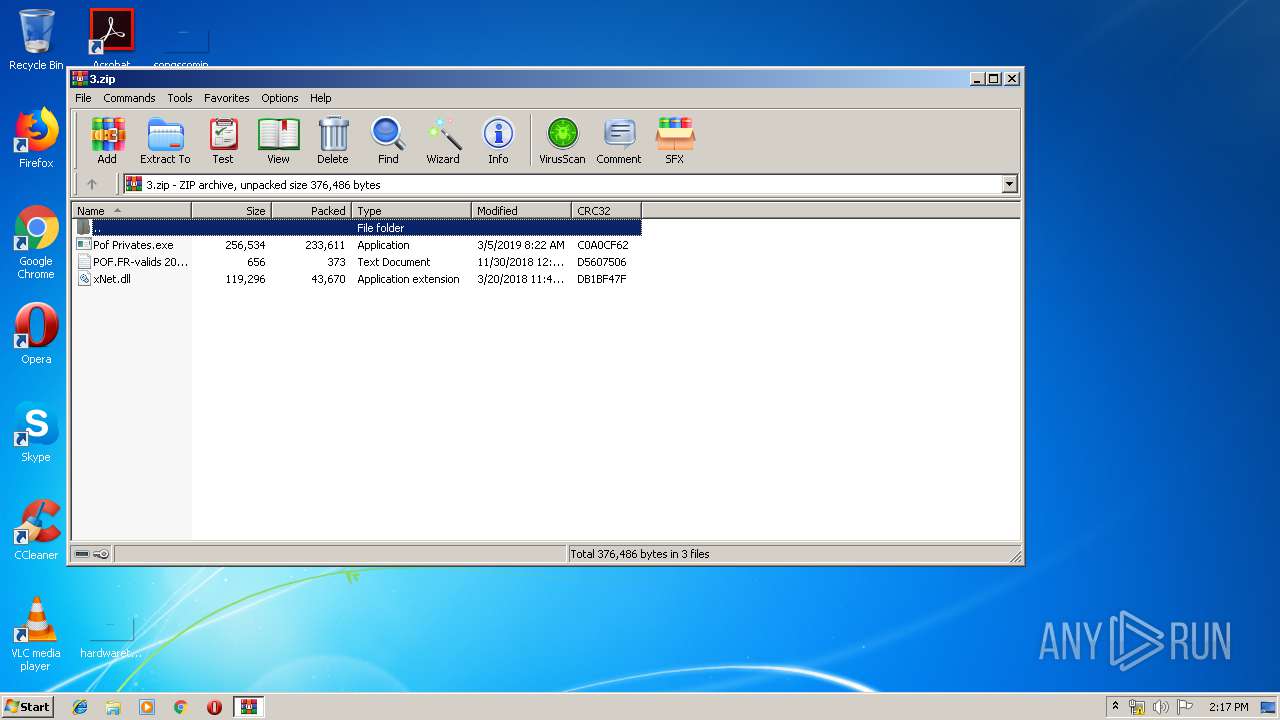
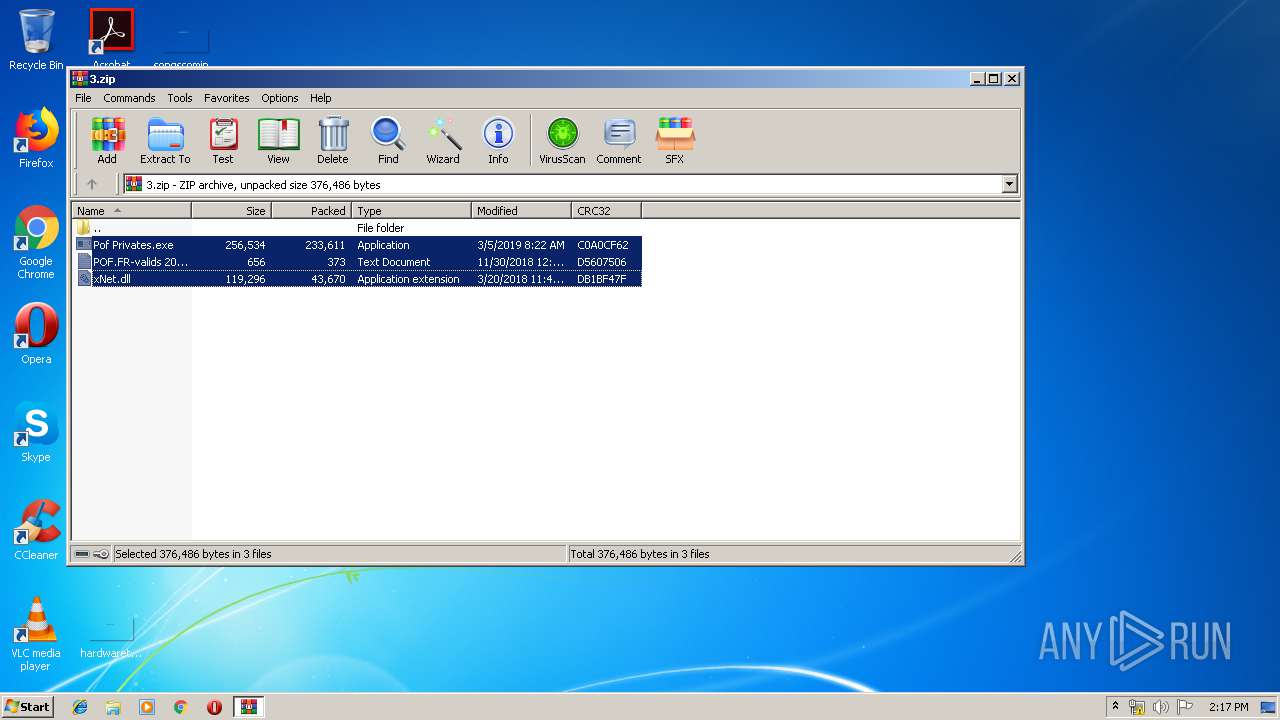
| File name: | 3.zip |
| Full analysis: | https://app.any.run/tasks/fc0c4916-3c37-4854-8115-74762e93110f |
| Verdict: | Malicious activity |
| Threats: | njRAT is a remote access trojan. It is one of the most widely accessible RATs on the market that features an abundance of educational information. Interested attackers can even find tutorials on YouTube. This allows it to become one of the most popular RATs in the world. |
| Analysis date: | May 20, 2019, 13:16:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 2187AE324F7CD40746B3E73651F0F74F |
| SHA1: | 5E487E3BC9AD707952535D04182DEF16ECB028E0 |
| SHA256: | E13B60C09B77CB861AC82818869204D222EF9C2ED5C3F1C219CF1C1D839C8044 |
| SSDEEP: | 6144:HQMBSuIDvyU0uavh6z26YzbQL/7WaDgArsb5051G0:HLEuIDvQrh60b0Lsb5Z0 |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1692)
Application was dropped or rewritten from another process
- Pof Privates.exe (PID: 3580)
- Google Chrome.exe (PID: 2924)
- Google Chrome.exe (PID: 3536)
- Pof Private.exe (PID: 3396)
- svchost.com (PID: 3640)
- Chrome.exe (PID: 2620)
- svchost.com (PID: 1892)
- svchost.com (PID: 3916)
Changes settings of System certificates
- Pof Private.exe (PID: 3396)
Writes to a start menu file
- Chrome.exe (PID: 2620)
Connects to CnC server
- Chrome.exe (PID: 2620)
Changes the autorun value in the registry
- Chrome.exe (PID: 2620)
NJRAT was detected
- Chrome.exe (PID: 2620)
SUSPICIOUS
Creates files in the user directory
- Pof Privates.exe (PID: 3580)
- Pof Private.exe (PID: 3396)
- Google Chrome.exe (PID: 3536)
- Chrome.exe (PID: 2620)
Executable content was dropped or overwritten
- Pof Privates.exe (PID: 3580)
- Google Chrome.exe (PID: 2924)
- Pof Private.exe (PID: 3396)
- Google Chrome.exe (PID: 3536)
- Chrome.exe (PID: 2620)
Creates files in the Windows directory
- Google Chrome.exe (PID: 2924)
- svchost.com (PID: 3640)
Modifies the open verb of a shell class
- Google Chrome.exe (PID: 2924)
Reads Environment values
- Pof Private.exe (PID: 3396)
Adds / modifies Windows certificates
- Pof Private.exe (PID: 3396)
Starts application with an unusual extension
- Google Chrome.exe (PID: 3536)
Uses NETSH.EXE for network configuration
- Chrome.exe (PID: 2620)
Removes files from Windows directory
- svchost.com (PID: 3640)
Application launched itself
- chrome.exe (PID: 4084)
Reads the cookies of Google Chrome
- chrome.exe (PID: 4084)
INFO
Manual execution by user
- Pof Privates.exe (PID: 3580)
- svchost.com (PID: 1892)
- svchost.com (PID: 3916)
Reads settings of System Certificates
- chrome.exe (PID: 4084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:03:20 04:41:16 |
| ZipCRC: | 0xdb1bf47f |
| ZipCompressedSize: | 43670 |
| ZipUncompressedSize: | 119296 |
| ZipFileName: | xNet.dll |
Total processes
63
Monitored processes
26
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | "C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe" --type=utility --field-trial-handle=948,9216681174630342674,7877295993969436981,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16668114753455058385 --mojo-platform-channel-handle=3896 --ignored=" --type=renderer " /prefetch:8 | C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 772 | C:\Windows\regedit.exe | C:\Windows\regedit.exe | — | svchost.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 836 | "C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe" --type=renderer --field-trial-handle=948,9216681174630342674,7877295993969436981,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=5141035378816544806 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5141035378816544806 --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2196 /prefetch:1 | C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 920 | netsh firewall add allowedprogram "C:\Users\admin\AppData\Roaming\Chrome.exe" "Chrome.exe" ENABLE | C:\Windows\system32\netsh.exe | — | Chrome.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1096 | "C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe" --type=watcher --main-thread-id=4052 --on-initialized-event-handle=300 --parent-handle=304 /prefetch:6 | C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1444 | "C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe" --type=utility --field-trial-handle=948,9216681174630342674,7877295993969436981,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15142638054429353941 --mojo-platform-channel-handle=2140 --ignored=" --type=renderer " /prefetch:8 | C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 | |||||||||||||||
| 1692 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1892 | "C:\Windows\svchost.com" "C:\Windows\regedit.exe" | C:\Windows\svchost.com | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2148 | "C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe" --type=renderer --field-trial-handle=948,9216681174630342674,7877295993969436981,131072 --enable-features=PasswordImport --service-pipe-token=14154157070223734015 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14154157070223734015 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2276 /prefetch:1 | C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2244 | "C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe" --type=renderer --field-trial-handle=948,9216681174630342674,7877295993969436981,131072 --enable-features=PasswordImport --service-pipe-token=5428713702737295868 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5428713702737295868 --renderer-client-id=3 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2284 /prefetch:1 | C:\PROGRA~1\Google\Chrome\APPLIC~1\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
2 336
Read events
1 616
Write events
717
Delete events
3
Modification events
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\3.zip | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (1692) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
15
Suspicious files
21
Text files
44
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3280.23760\xNet.dll | — | |
MD5:— | SHA256:— | |||
| 3280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3280.23760\POF.FR-valids 2018-11-29_14_14_16.txt | — | |
MD5:— | SHA256:— | |||
| 3280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3280.23760\Pof Privates.exe | — | |
MD5:— | SHA256:— | |||
| 3396 | Pof Private.exe | C:\Users\admin\AppData\Local\Temp\Cab3764.tmp | — | |
MD5:— | SHA256:— | |||
| 3396 | Pof Private.exe | C:\Users\admin\AppData\Local\Temp\Tar3765.tmp | — | |
MD5:— | SHA256:— | |||
| 3396 | Pof Private.exe | C:\Users\admin\AppData\Local\Temp\Cab3785.tmp | — | |
MD5:— | SHA256:— | |||
| 3396 | Pof Private.exe | C:\Users\admin\AppData\Local\Temp\Tar3786.tmp | — | |
MD5:— | SHA256:— | |||
| 3396 | Pof Private.exe | C:\Users\admin\AppData\Local\Temp\Cab3797.tmp | — | |
MD5:— | SHA256:— | |||
| 3396 | Pof Private.exe | C:\Users\admin\AppData\Local\Temp\Tar3798.tmp | — | |
MD5:— | SHA256:— | |||
| 3396 | Pof Private.exe | C:\Users\admin\AppData\Local\Temp\Cab3854.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
18
DNS requests
19
Threats
25
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4084 | chrome.exe | GET | 200 | 173.194.183.201:80 | http://r4---sn-aigl6nl7.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=217.147.89.18&mm=28&mn=sn-aigl6nl7&ms=nvh&mt=1558358423&mv=m&pl=22&shardbypass=yes | US | crx | 842 Kb | whitelisted |
3396 | Pof Private.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.1 Kb | whitelisted |
3396 | Pof Private.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/DF3C24F9BFD666761B268073FE06D1CC8D4F82A4.crt | US | der | 914 b | whitelisted |
4084 | chrome.exe | GET | 302 | 172.217.22.46:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 504 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3396 | Pof Private.exe | 145.14.145.144:443 | pandikeypu.000webhostapp.com | Hostinger International Limited | US | shared |
2620 | Chrome.exe | 51.68.120.162:5552 | d3co4r.duckdns.org | — | GB | malicious |
4084 | chrome.exe | 172.217.22.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
— | — | 172.217.18.99:443 | www.gstatic.com | Google Inc. | US | whitelisted |
4084 | chrome.exe | 172.217.16.206:443 | apis.google.com | Google Inc. | US | whitelisted |
3396 | Pof Private.exe | 93.184.221.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 172.217.22.33:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
4084 | chrome.exe | 172.217.22.33:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
— | — | 172.217.22.46:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
4084 | chrome.exe | 172.217.22.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pandikeypu.000webhostapp.com |
| shared |
www.download.windowsupdate.com |
| whitelisted |
d3co4r.duckdns.org |
| malicious |
clientservices.googleapis.com |
| whitelisted |
www.google.com.ua |
| whitelisted |
accounts.google.com |
| shared |
clients1.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
clients2.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |
3396 | Pof Private.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
1056 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2620 | Chrome.exe | A Network Trojan was detected | MALWARE [PTsecurity] njRAT.Gen RAT outbound connection |
2620 | Chrome.exe | A Network Trojan was detected | ET TROJAN Bladabindi/njRAT CnC Command (ll) |
1056 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2620 | Chrome.exe | A Network Trojan was detected | MALWARE [PTsecurity] njRAT.Gen RAT outbound connection |
2620 | Chrome.exe | A Network Trojan was detected | ET TROJAN Bladabindi/njRAT CnC Command (ll) |
— | — | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
— | — | A Network Trojan was detected | MALWARE [PTsecurity] njRAT.Gen RAT outbound connection |
15 ETPRO signatures available at the full report