| File name: | random.exe |
| Full analysis: | https://app.any.run/tasks/14ab12a2-a3cf-4a7f-8024-7d1322b7a72b |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 20, 2025, 01:37:41 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 572C2EF520F73C55A1A75CBF57D466C1 |
| SHA1: | DAA81B7B9E86EE8CB5BF8790B6B4683A40914655 |
| SHA256: | E04FD3D23B9BFC7E468BE3E70D244C763777B7CDB9C8523B76E0C66BFBCA7186 |
| SSDEEP: | 49152:kPPkzemqoSut3Jh4+QQ/btosJwIA4hHmZlKH2Tw/Pq83zw0bCjvk9G661QGtBEXo:OP/mp7t3T4+B/btosJwIA4hHmZlKH2TE |
MALICIOUS
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6036)
- cmd.exe (PID: 5344)
Run PowerShell with an invisible window
- powershell.exe (PID: 7224)
- powershell.exe (PID: 7816)
- powershell.exe (PID: 7628)
- powershell.exe (PID: 7696)
AMADEY mutex has been found
- TempJTJ33BDQIHTUAIBYKMYHZB9HVRCUNGQV.EXE (PID: 7772)
- ramez.exe (PID: 7976)
- ramez.exe (PID: 8140)
- TempJTJ33BDQIHTUAIBYKMYHZB9HVRCUNGQV.EXE (PID: 2140)
Request from PowerShell that ran from MSHTA.EXE
- powershell.exe (PID: 7224)
- powershell.exe (PID: 7816)
- powershell.exe (PID: 7628)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7816)
- powershell.exe (PID: 7224)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 7976)
Connects to the CnC server
- ramez.exe (PID: 7976)
- svchost.exe (PID: 2196)
- dwm.exe (PID: 3760)
- dwm.exe (PID: 8448)
- explorer.exe (PID: 5492)
- cmd.exe (PID: 8608)
AMADEY has been detected (YARA)
- ramez.exe (PID: 7976)
Executing a file with an untrusted certificate
- 07c099764d.exe (PID: 7236)
- 8RypWDs.exe (PID: 9604)
- 8RypWDs.exe (PID: 8628)
- XEIxGFE.exe (PID: 8812)
- cSyRrCk.exe (PID: 9856)
- HRnxr8j.exe (PID: 5728)
VIDAR mutex has been found
- MSBuild.exe (PID: 6644)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- 22993beae5.exe (PID: 5256)
- 22993beae5.exe (PID: 4212)
- MSBuild.exe (PID: 8592)
Changes the autorun value in the registry
- ramez.exe (PID: 7976)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 6644)
- 22993beae5.exe (PID: 5256)
Steals credentials from Web Browsers
- MSBuild.exe (PID: 6644)
VIDAR has been detected (YARA)
- MSBuild.exe (PID: 6644)
LUMMA mutex has been found
- 22993beae5.exe (PID: 5256)
GCLEANER has been detected (SURICATA)
- cvtres.exe (PID: 4920)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 6324)
- cmd.exe (PID: 5800)
- NSudoLG.exe (PID: 7900)
- NSudoLG.exe (PID: 7996)
Changes Windows Defender settings
- NSudoLG.exe (PID: 7900)
- NSudoLG.exe (PID: 7996)
- WinTemp-v4.exe (PID: 9180)
LUMMA has been detected (YARA)
- 22993beae5.exe (PID: 5256)
Known privilege escalation attack
- dllhost.exe (PID: 9412)
- dllhost.exe (PID: 744)
GENERIC has been found (auto)
- cvtres.exe (PID: 4920)
DARKCRYSTAL has been detected (SURICATA)
- dwm.exe (PID: 3760)
- dwm.exe (PID: 8448)
Adds process to the Windows Defender exclusion list
- WinTemp-v4.exe (PID: 9180)
Starts SC.EXE for service management
- cmd.exe (PID: 6324)
- cmd.exe (PID: 5800)
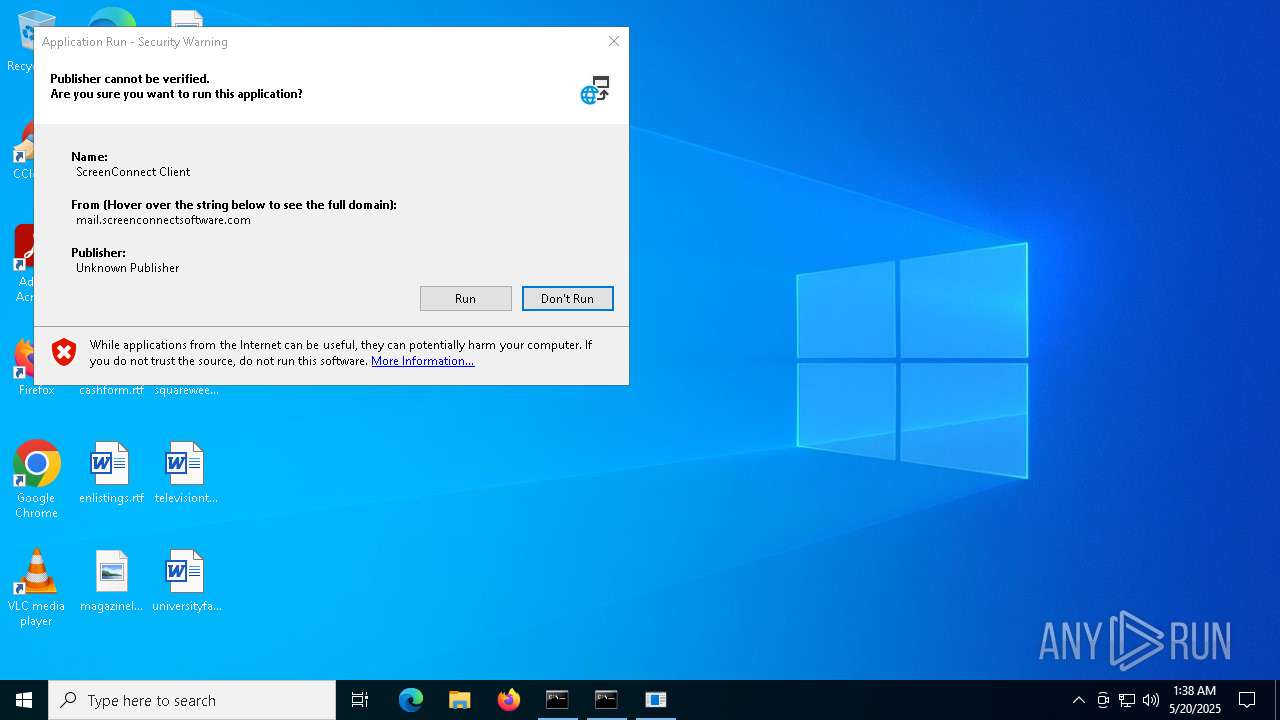
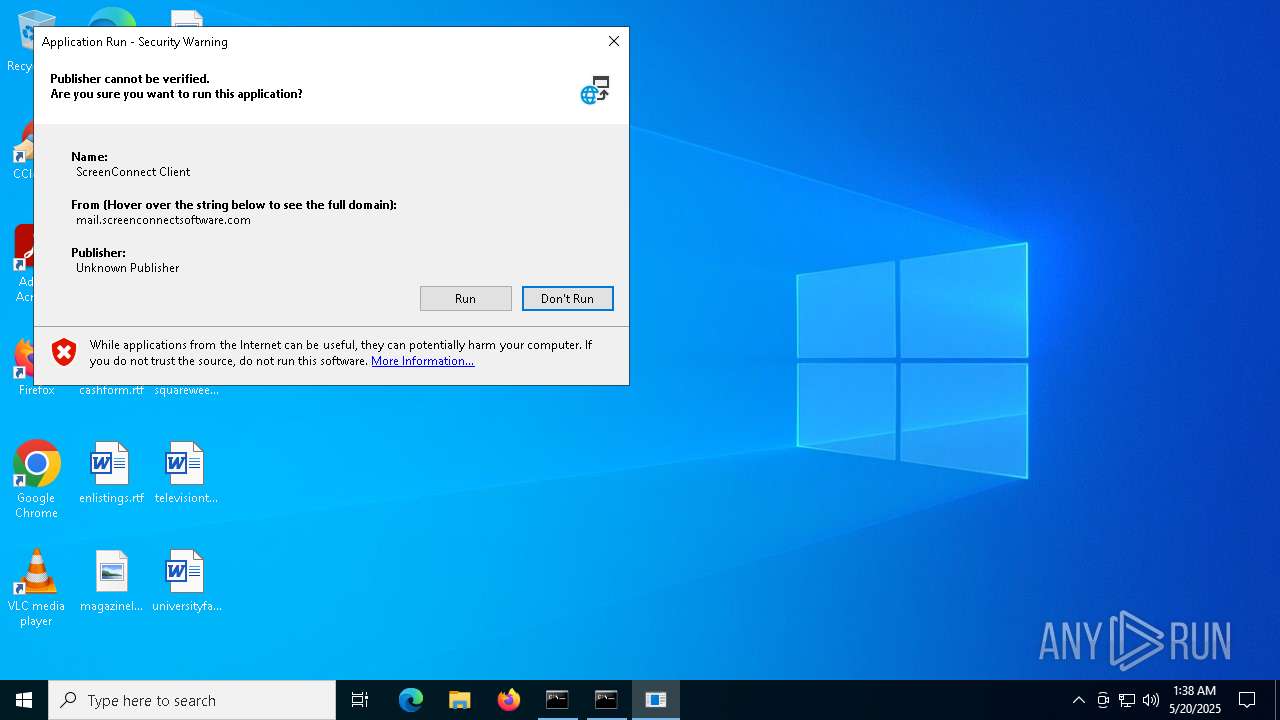
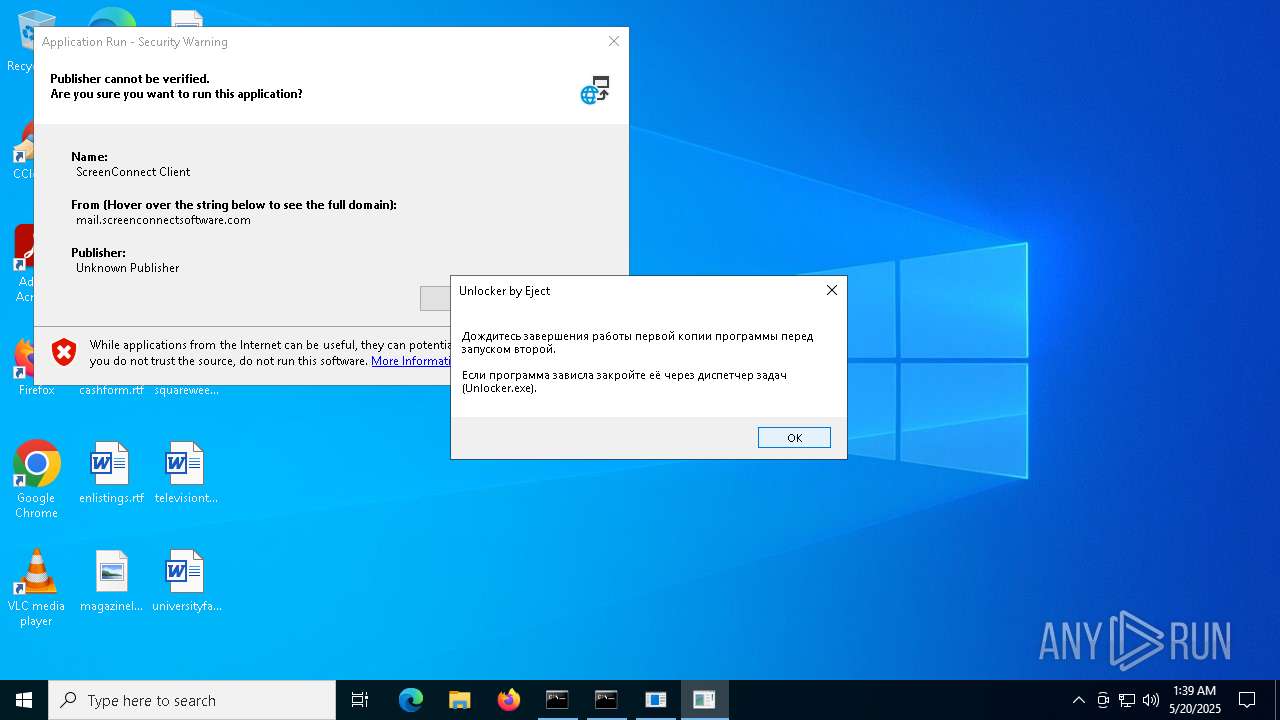
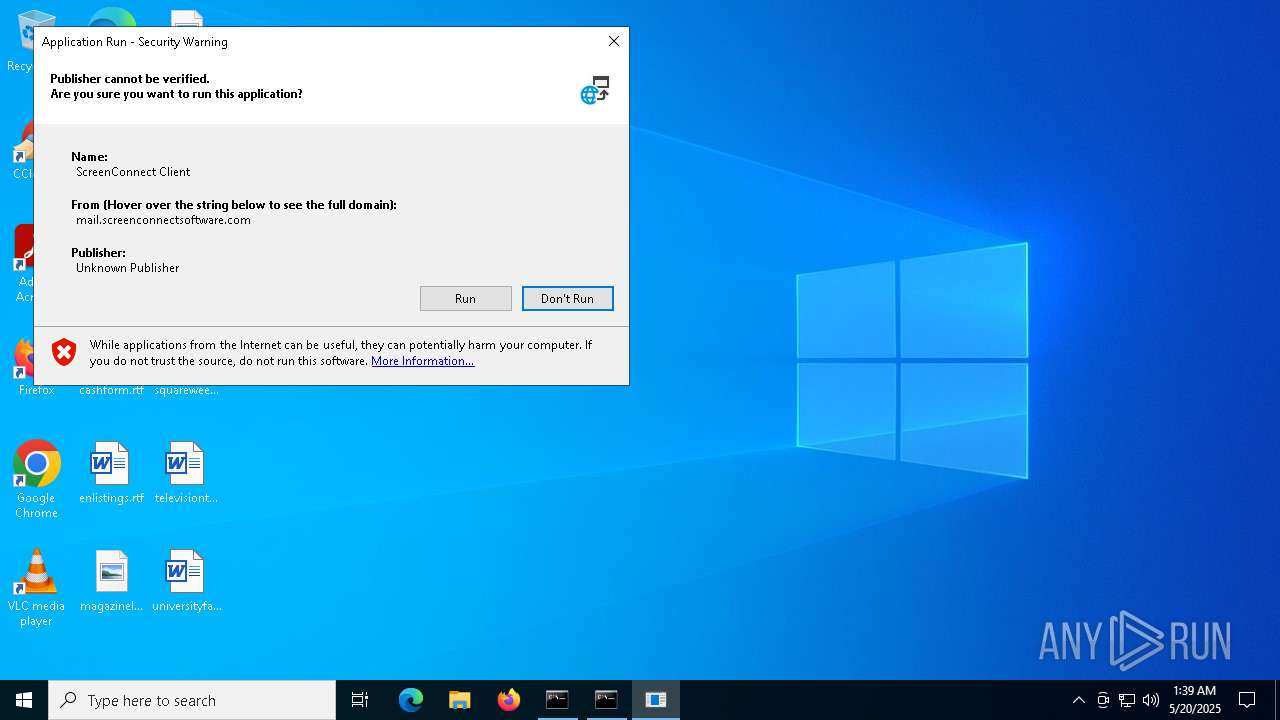
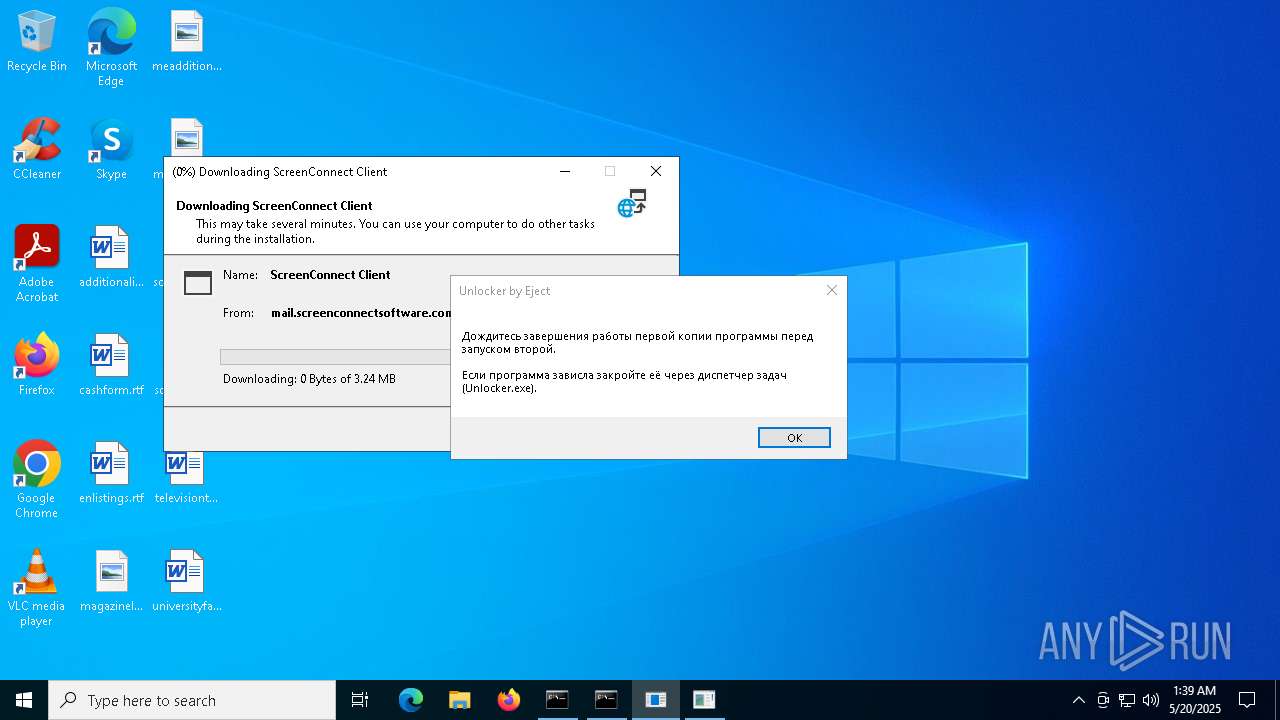
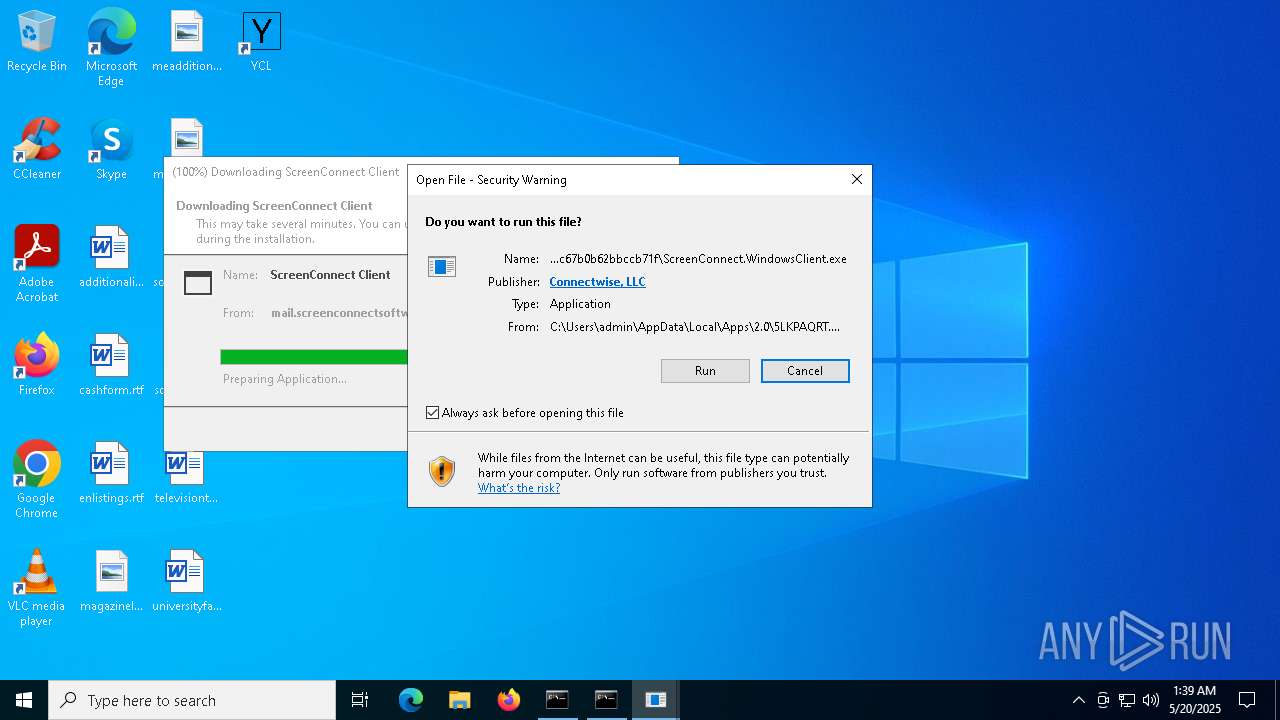
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.ClientService.exe (PID: 8668)
Starts REAGENTC.EXE to disable the Windows Recovery Environment
- ReAgentc.exe (PID: 7736)
MINER has been detected (SURICATA)
- cmd.exe (PID: 8608)
SUSPICIOUS
Starts CMD.EXE for commands execution
- random.exe (PID: 2320)
- cmd.exe (PID: 7428)
- 649f5ebdb0.exe (PID: 7632)
- nircmd.exe (PID: 7964)
- cmd.exe (PID: 7876)
- f855b79cb5.exe (PID: 7224)
- 649f5ebdb0.exe (PID: 5216)
- cmd.exe (PID: 7916)
- NSudoLG.exe (PID: 6192)
- nircmd.exe (PID: 2908)
- cmd.exe (PID: 7732)
- cmd.exe (PID: 3024)
- cmd.exe (PID: 5800)
- cmd.exe (PID: 5544)
- NSudoLG.exe (PID: 7792)
- cmd.exe (PID: 6324)
- Unlocker.exe (PID: 8072)
- Unlocker.exe (PID: 9292)
- Unlocker.exe (PID: 920)
- 8RypWDs.exe (PID: 9604)
- Unlocker.exe (PID: 8976)
- Unlocker.exe (PID: 7600)
- wscript.exe (PID: 744)
- Unlocker.exe (PID: 2664)
- Comreviewdriver.exe (PID: 4284)
- Unlocker.exe (PID: 8680)
- Unlocker.exe (PID: 8892)
- Unlocker.exe (PID: 9036)
- WinTemp-v4.exe (PID: 9180)
- Unlocker.exe (PID: 9020)
Starts process via Powershell
- powershell.exe (PID: 7224)
- powershell.exe (PID: 7816)
- powershell.exe (PID: 7628)
- powershell.exe (PID: 7696)
Probably download files using WebClient
- mshta.exe (PID: 3332)
- mshta.exe (PID: 7708)
- mshta.exe (PID: 6372)
- mshta.exe (PID: 7084)
Found IP address in command line
- powershell.exe (PID: 7224)
- powershell.exe (PID: 7816)
- powershell.exe (PID: 7628)
- powershell.exe (PID: 7696)
Manipulates environment variables
- powershell.exe (PID: 7224)
- powershell.exe (PID: 7816)
- powershell.exe (PID: 7628)
- powershell.exe (PID: 7696)
Executable content was dropped or overwritten
- powershell.exe (PID: 7224)
- TempJTJ33BDQIHTUAIBYKMYHZB9HVRCUNGQV.EXE (PID: 7772)
- ramez.exe (PID: 7976)
- 97a61b4446.exe (PID: 744)
- 97a61b4446.tmp (PID: 1764)
- 649f5ebdb0.exe (PID: 7632)
- csc.exe (PID: 3140)
- powershell.exe (PID: 7628)
- csc.exe (PID: 9536)
- csc.exe (PID: 9392)
- csc.exe (PID: 9628)
- csc.exe (PID: 9692)
- csc.exe (PID: 10088)
- csc.exe (PID: 9508)
- csc.exe (PID: 10184)
- csc.exe (PID: 9292)
- csc.exe (PID: 7956)
- csc.exe (PID: 6080)
- csc.exe (PID: 10012)
- csc.exe (PID: 7912)
- csc.exe (PID: 10008)
- csc.exe (PID: 9996)
- 22993beae5.exe (PID: 5256)
- 7z.exe (PID: 9536)
- L7m5WH3.exe (PID: 7220)
- 22993beae5.exe (PID: 4212)
- 8RypWDs.exe (PID: 9604)
- Comreviewdriver.exe (PID: 4284)
- csc.exe (PID: 7156)
- csc.exe (PID: 9092)
- csc.exe (PID: 9996)
- csc.exe (PID: 9640)
- dwm.exe (PID: 3760)
- Unlocker.exe (PID: 8680)
- dfsvc.exe (PID: 7272)
- cvtres.exe (PID: 4920)
- oxDU0MW.exe (PID: 8244)
- dwm.exe (PID: 8448)
- cmd.exe (PID: 6324)
- WinTemp-v4.exe (PID: 9180)
- explorer.exe (PID: 5492)
Process requests binary or script from the Internet
- powershell.exe (PID: 7224)
- powershell.exe (PID: 7816)
- ramez.exe (PID: 7976)
- powershell.exe (PID: 7628)
- powershell.exe (PID: 7696)
- 22993beae5.exe (PID: 5256)
- 22993beae5.exe (PID: 4212)
Connects to the server without a host name
- powershell.exe (PID: 7224)
- ramez.exe (PID: 7976)
- powershell.exe (PID: 7816)
- cvtres.exe (PID: 4920)
- powershell.exe (PID: 7628)
- powershell.exe (PID: 7696)
- 22993beae5.exe (PID: 5256)
- 22993beae5.exe (PID: 4212)
- MSBuild.exe (PID: 9072)
- dwm.exe (PID: 3760)
- dwm.exe (PID: 8448)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 7708)
- mshta.exe (PID: 3332)
- MSBuild.exe (PID: 6644)
- mshta.exe (PID: 6372)
- mshta.exe (PID: 7084)
- NSudoLG.exe (PID: 7900)
- NSudoLG.exe (PID: 7996)
- WinTemp-v4.exe (PID: 9180)
Starts itself from another location
- TempJTJ33BDQIHTUAIBYKMYHZB9HVRCUNGQV.EXE (PID: 7772)
The process executes via Task Scheduler
- ramez.exe (PID: 8140)
- ramez.exe (PID: 6248)
Reads security settings of Internet Explorer
- ramez.exe (PID: 7976)
- TempJTJ33BDQIHTUAIBYKMYHZB9HVRCUNGQV.EXE (PID: 7772)
- 97a61b4446.tmp (PID: 1764)
- MSBuild.exe (PID: 6644)
- cvtres.exe (PID: 4920)
- 649f5ebdb0.exe (PID: 7632)
- nircmd.exe (PID: 7964)
Contacting a server suspected of hosting an CnC
- ramez.exe (PID: 7976)
- svchost.exe (PID: 2196)
- 22993beae5.exe (PID: 5256)
- 22993beae5.exe (PID: 4212)
- MSBuild.exe (PID: 8592)
- explorer.exe (PID: 5492)
Potential Corporate Privacy Violation
- powershell.exe (PID: 7816)
- ramez.exe (PID: 7976)
- powershell.exe (PID: 7224)
- powershell.exe (PID: 7628)
- 22993beae5.exe (PID: 5256)
- 22993beae5.exe (PID: 4212)
- cvtres.exe (PID: 4920)
- ScreenConnect.ClientService.exe (PID: 8668)
- cmd.exe (PID: 8608)
There is functionality for enable RDP (YARA)
- ramez.exe (PID: 7976)
There is functionality for taking screenshot (YARA)
- ramez.exe (PID: 7976)
- MSBuild.exe (PID: 6644)
Reads the Windows owner or organization settings
- 97a61b4446.tmp (PID: 1764)
Reads the BIOS version
- 22993beae5.exe (PID: 5256)
- 22993beae5.exe (PID: 4212)
Executes application which crashes
- core.exe (PID: 5800)
- Unlocker.exe (PID: 920)
- Unlocker.exe (PID: 8976)
- Unlocker.exe (PID: 2664)
- Win-v42.exe (PID: 5232)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 6644)
- MSBuild.exe (PID: 7188)
- MSBuild.exe (PID: 7680)
Drops 7-zip archiver for unpacking
- 649f5ebdb0.exe (PID: 7632)
Searches for installed software
- MSBuild.exe (PID: 6644)
Executing commands from a ".bat" file
- 649f5ebdb0.exe (PID: 7632)
- cmd.exe (PID: 7428)
- nircmd.exe (PID: 7964)
- cmd.exe (PID: 7876)
- cmd.exe (PID: 7916)
- 649f5ebdb0.exe (PID: 5216)
- cmd.exe (PID: 7732)
- NSudoLG.exe (PID: 6192)
- cmd.exe (PID: 5544)
- nircmd.exe (PID: 2908)
- cmd.exe (PID: 3024)
- NSudoLG.exe (PID: 7792)
- wscript.exe (PID: 744)
- Comreviewdriver.exe (PID: 4284)
Application launched itself
- cmd.exe (PID: 7428)
- cmd.exe (PID: 7876)
- cmd.exe (PID: 7916)
- cmd.exe (PID: 7732)
- cmd.exe (PID: 5544)
- cmd.exe (PID: 3024)
- cmd.exe (PID: 5800)
- cmd.exe (PID: 6324)
- 8RypWDs.exe (PID: 9604)
Starts application with an unusual extension
- cmd.exe (PID: 7800)
- cmd.exe (PID: 6488)
- cmd.exe (PID: 7964)
- cmd.exe (PID: 5344)
- cmd.exe (PID: 5800)
- cmd.exe (PID: 6324)
- cmd.exe (PID: 8308)
The process bypasses the loading of PowerShell profile settings
- MSBuild.exe (PID: 6644)
The process creates files with name similar to system file names
- 649f5ebdb0.exe (PID: 7632)
The executable file from the user directory is run by the CMD process
- nircmd.exe (PID: 7964)
- nircmd.exe (PID: 2908)
- NSudoLG.exe (PID: 7792)
- NSudoLG.exe (PID: 6192)
- NSudoLG.exe (PID: 7900)
- NSudoLG.exe (PID: 7996)
- 7z.exe (PID: 9536)
- 7z.exe (PID: 6044)
- Unlocker.exe (PID: 9292)
- Unlocker.exe (PID: 8072)
- Unlocker.exe (PID: 920)
- Unlocker.exe (PID: 8976)
- Unlocker.exe (PID: 7600)
- Comreviewdriver.exe (PID: 4284)
- Unlocker.exe (PID: 2664)
- Unlocker.exe (PID: 8680)
- Unlocker.exe (PID: 8892)
- Unlocker.exe (PID: 9020)
- Unlocker.exe (PID: 9036)
Reads the date of Windows installation
- nircmd.exe (PID: 7964)
Base64-obfuscated command line is found
- MSBuild.exe (PID: 6644)
The process hide an interactive prompt from the user
- MSBuild.exe (PID: 6644)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7912)
Multiple wallet extension IDs have been found
- MSBuild.exe (PID: 6644)
CSC.EXE is used to compile C# code
- csc.exe (PID: 3140)
- csc.exe (PID: 9692)
- csc.exe (PID: 9392)
- csc.exe (PID: 9536)
- csc.exe (PID: 9628)
- csc.exe (PID: 9996)
- csc.exe (PID: 10008)
- csc.exe (PID: 10088)
- csc.exe (PID: 9292)
- csc.exe (PID: 9508)
- csc.exe (PID: 7956)
- csc.exe (PID: 6080)
- csc.exe (PID: 7912)
- csc.exe (PID: 10012)
- csc.exe (PID: 10184)
BASE64 encoded PowerShell command has been detected
- MSBuild.exe (PID: 6644)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6488)
- cmd.exe (PID: 5344)
- cmd.exe (PID: 5800)
- cmd.exe (PID: 6324)
Get information on the list of running processes
- cmd.exe (PID: 7296)
- cmd.exe (PID: 6324)
- cmd.exe (PID: 7752)
- cmd.exe (PID: 5800)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 7708)
Script adds exclusion path to Windows Defender
- NSudoLG.exe (PID: 7900)
- NSudoLG.exe (PID: 7996)
- WinTemp-v4.exe (PID: 9180)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5800)
- cmd.exe (PID: 6324)
Starts SC.EXE for service management
- cmd.exe (PID: 9072)
- cmd.exe (PID: 9064)
- cmd.exe (PID: 6576)
- cmd.exe (PID: 6324)
- cmd.exe (PID: 9972)
- cmd.exe (PID: 5800)
- cmd.exe (PID: 7524)
- cmd.exe (PID: 10196)
- cmd.exe (PID: 9020)
- cmd.exe (PID: 8452)
- cmd.exe (PID: 8652)
- cmd.exe (PID: 1272)
- cmd.exe (PID: 9412)
- cmd.exe (PID: 5868)
Windows service management via SC.EXE
- sc.exe (PID: 6724)
- sc.exe (PID: 1568)
- sc.exe (PID: 1116)
- sc.exe (PID: 9628)
- sc.exe (PID: 7956)
- sc.exe (PID: 6960)
- sc.exe (PID: 8312)
- sc.exe (PID: 2908)
- sc.exe (PID: 6228)
- sc.exe (PID: 8076)
- sc.exe (PID: 1128)
- sc.exe (PID: 8916)
- sc.exe (PID: 7940)
- sc.exe (PID: 7268)
- sc.exe (PID: 7844)
- sc.exe (PID: 9460)
- sc.exe (PID: 1660)
- sc.exe (PID: 7544)
- sc.exe (PID: 2616)
- sc.exe (PID: 8524)
- sc.exe (PID: 9788)
- sc.exe (PID: 7416)
- sc.exe (PID: 7888)
- sc.exe (PID: 8884)
- sc.exe (PID: 1128)
- sc.exe (PID: 10036)
- sc.exe (PID: 2144)
- sc.exe (PID: 5736)
- sc.exe (PID: 2580)
- sc.exe (PID: 3848)
- sc.exe (PID: 7224)
- sc.exe (PID: 8956)
- sc.exe (PID: 5892)
- sc.exe (PID: 6184)
- sc.exe (PID: 6388)
- sc.exe (PID: 10152)
- sc.exe (PID: 6640)
- sc.exe (PID: 1132)
- sc.exe (PID: 672)
- sc.exe (PID: 8836)
- sc.exe (PID: 7904)
- sc.exe (PID: 1580)
- sc.exe (PID: 6148)
- sc.exe (PID: 5176)
- sc.exe (PID: 9916)
- sc.exe (PID: 8916)
- sc.exe (PID: 10132)
- sc.exe (PID: 8016)
- sc.exe (PID: 9628)
- sc.exe (PID: 5740)
- sc.exe (PID: 8624)
- sc.exe (PID: 10164)
- sc.exe (PID: 9972)
- sc.exe (PID: 9804)
- sc.exe (PID: 7204)
- sc.exe (PID: 9884)
- sc.exe (PID: 8984)
- sc.exe (PID: 7280)
- sc.exe (PID: 3192)
- sc.exe (PID: 900)
- sc.exe (PID: 9576)
- sc.exe (PID: 1616)
- sc.exe (PID: 4212)
- sc.exe (PID: 7220)
- sc.exe (PID: 7208)
- sc.exe (PID: 1276)
- sc.exe (PID: 8372)
- sc.exe (PID: 7000)
- sc.exe (PID: 7316)
- sc.exe (PID: 7780)
- sc.exe (PID: 5344)
- sc.exe (PID: 7696)
- sc.exe (PID: 2444)
- sc.exe (PID: 4284)
- sc.exe (PID: 7844)
- sc.exe (PID: 5260)
- sc.exe (PID: 8724)
- sc.exe (PID: 9080)
- sc.exe (PID: 7860)
- sc.exe (PID: 7840)
- sc.exe (PID: 7732)
- sc.exe (PID: 4200)
- sc.exe (PID: 640)
- sc.exe (PID: 8148)
- sc.exe (PID: 8636)
- sc.exe (PID: 8508)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6644)
- cmd.exe (PID: 9140)
- cmd.exe (PID: 9980)
- cmd.exe (PID: 3016)
- cmd.exe (PID: 10192)
- cmd.exe (PID: 5188)
- cmd.exe (PID: 8300)
Uses WMIC.EXE to obtain BIOS management information
- cmd.exe (PID: 8616)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 8532)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6324)
- cmd.exe (PID: 5800)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 4220)
Executed via WMI
- schtasks.exe (PID: 9016)
- schtasks.exe (PID: 8756)
- schtasks.exe (PID: 10108)
- schtasks.exe (PID: 6828)
- schtasks.exe (PID: 5408)
- schtasks.exe (PID: 10204)
- schtasks.exe (PID: 7584)
- schtasks.exe (PID: 7644)
- schtasks.exe (PID: 9344)
- schtasks.exe (PID: 7560)
- schtasks.exe (PID: 3176)
- schtasks.exe (PID: 2616)
- schtasks.exe (PID: 6032)
- schtasks.exe (PID: 5600)
- schtasks.exe (PID: 7264)
- schtasks.exe (PID: 4212)
- schtasks.exe (PID: 5020)
- schtasks.exe (PID: 4428)
Likely accesses (executes) a file from the Public directory
- schtasks.exe (PID: 9016)
- schtasks.exe (PID: 8756)
- schtasks.exe (PID: 10108)
- schtasks.exe (PID: 5408)
- schtasks.exe (PID: 10204)
- schtasks.exe (PID: 7584)
- schtasks.exe (PID: 2616)
- schtasks.exe (PID: 6032)
- dwm.exe (PID: 3760)
- dllhost.exe (PID: 7620)
- schtasks.exe (PID: 4428)
- cvtres.exe (PID: 2064)
- dwm.exe (PID: 8448)
Process drops legitimate windows executable
- Comreviewdriver.exe (PID: 4284)
- cmd.exe (PID: 6324)
- ramez.exe (PID: 7976)
- explorer.exe (PID: 5492)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 8308)
Drops a system driver (possible attempt to evade defenses)
- Unlocker.exe (PID: 8680)
Stops a currently running service
- sc.exe (PID: 8312)
- sc.exe (PID: 9620)
- sc.exe (PID: 4112)
- sc.exe (PID: 8620)
- sc.exe (PID: 9384)
- sc.exe (PID: 10124)
- sc.exe (PID: 3364)
- sc.exe (PID: 2488)
- sc.exe (PID: 9608)
- sc.exe (PID: 8264)
- sc.exe (PID: 2400)
- sc.exe (PID: 2772)
- sc.exe (PID: 9896)
- sc.exe (PID: 8076)
- sc.exe (PID: 4528)
- sc.exe (PID: 7504)
- sc.exe (PID: 856)
- sc.exe (PID: 140)
- sc.exe (PID: 1600)
- sc.exe (PID: 8060)
- sc.exe (PID: 10024)
- sc.exe (PID: 8572)
- sc.exe (PID: 7104)
- sc.exe (PID: 9992)
- sc.exe (PID: 5124)
- sc.exe (PID: 8460)
- sc.exe (PID: 6620)
- sc.exe (PID: 8340)
- sc.exe (PID: 7500)
- sc.exe (PID: 8064)
- sc.exe (PID: 9692)
- sc.exe (PID: 8428)
- sc.exe (PID: 2420)
- sc.exe (PID: 10040)
Script adds exclusion process to Windows Defender
- WinTemp-v4.exe (PID: 9180)
Executes as Windows Service
- ScreenConnect.ClientService.exe (PID: 8668)
Connects to unusual port
- ScreenConnect.ClientService.exe (PID: 8668)
- WinTemp-v4.exe (PID: 9180)
- cmd.exe (PID: 8608)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 8788)
- schtasks.exe (PID: 3620)
- schtasks.exe (PID: 2632)
- schtasks.exe (PID: 1012)
- schtasks.exe (PID: 456)
- schtasks.exe (PID: 7644)
- schtasks.exe (PID: 6248)
- schtasks.exe (PID: 3804)
- schtasks.exe (PID: 1544)
- schtasks.exe (PID: 9428)
Starts a Microsoft application from unusual location
- HRnxr8j.exe (PID: 5728)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 3956)
Checks for external IP
- svchost.exe (PID: 2196)
- WinTemp-v4.exe (PID: 9180)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2088)
- cmd.exe (PID: 3176)
Uses powercfg.exe to modify the power settings
- WinTemp-v4.exe (PID: 9180)
Hides command output
- cmd.exe (PID: 976)
INFO
Reads mouse settings
- random.exe (PID: 2320)
- f855b79cb5.exe (PID: 7224)
Checks supported languages
- random.exe (PID: 2320)
- TempJTJ33BDQIHTUAIBYKMYHZB9HVRCUNGQV.EXE (PID: 7772)
- ramez.exe (PID: 7976)
- ramez.exe (PID: 8140)
- TempJTJ33BDQIHTUAIBYKMYHZB9HVRCUNGQV.EXE (PID: 2140)
- 07c099764d.exe (PID: 7236)
- 97a61b4446.exe (PID: 744)
- 97a61b4446.tmp (PID: 1764)
- info.exe (PID: 5124)
- core.exe (PID: 5800)
- 22993beae5.exe (PID: 5256)
- cvtres.exe (PID: 4920)
- MSBuild.exe (PID: 6644)
- chcp.com (PID: 7724)
- 649f5ebdb0.exe (PID: 7632)
- nircmd.exe (PID: 7964)
- 22993beae5.exe (PID: 4212)
- f855b79cb5.exe (PID: 7224)
- 649f5ebdb0.exe (PID: 5216)
Reads the computer name
- random.exe (PID: 2320)
- TempJTJ33BDQIHTUAIBYKMYHZB9HVRCUNGQV.EXE (PID: 7772)
- ramez.exe (PID: 7976)
- 97a61b4446.tmp (PID: 1764)
- 07c099764d.exe (PID: 7236)
- MSBuild.exe (PID: 6644)
- 22993beae5.exe (PID: 5256)
- cvtres.exe (PID: 4920)
- 649f5ebdb0.exe (PID: 7632)
- nircmd.exe (PID: 7964)
- f855b79cb5.exe (PID: 7224)
- 649f5ebdb0.exe (PID: 5216)
Auto-launch of the file from Task Scheduler
- cmd.exe (PID: 6036)
- cmd.exe (PID: 5344)
Create files in a temporary directory
- random.exe (PID: 2320)
- TempJTJ33BDQIHTUAIBYKMYHZB9HVRCUNGQV.EXE (PID: 7772)
- ramez.exe (PID: 7976)
- 97a61b4446.exe (PID: 744)
- 97a61b4446.tmp (PID: 1764)
- 649f5ebdb0.exe (PID: 7632)
- MSBuild.exe (PID: 6644)
- f855b79cb5.exe (PID: 7224)
- powershell.exe (PID: 7912)
- 649f5ebdb0.exe (PID: 5216)
The sample compiled with english language support
- random.exe (PID: 2320)
- ramez.exe (PID: 7976)
- 649f5ebdb0.exe (PID: 7632)
- 8RypWDs.exe (PID: 9604)
- Comreviewdriver.exe (PID: 4284)
- Unlocker.exe (PID: 8680)
- cmd.exe (PID: 6324)
- explorer.exe (PID: 5492)
Reads Internet Explorer settings
- mshta.exe (PID: 3332)
- mshta.exe (PID: 7708)
- mshta.exe (PID: 6372)
Checks proxy server information
- powershell.exe (PID: 7224)
- ramez.exe (PID: 7976)
- powershell.exe (PID: 7816)
- MSBuild.exe (PID: 6644)
- cvtres.exe (PID: 4920)
Manual execution by a user
- mshta.exe (PID: 7708)
- cvtres.exe (PID: 4920)
- 22993beae5.exe (PID: 4212)
- 649f5ebdb0.exe (PID: 5216)
- mshta.exe (PID: 7084)
- dwm.exe (PID: 3760)
- dllhost.exe (PID: 7620)
- Comreviewdriver.exe (PID: 7508)
- fPbjy1Q.exe (PID: 8420)
- fontdrvhost.exe (PID: 8500)
- cvtres.exe (PID: 2064)
- Win-v42.exe (PID: 5232)
The executable file from the user directory is run by the Powershell process
- TempJTJ33BDQIHTUAIBYKMYHZB9HVRCUNGQV.EXE (PID: 7772)
- TempJTJ33BDQIHTUAIBYKMYHZB9HVRCUNGQV.EXE (PID: 2140)
- Temp02TNIN0ANV4TH9XT9HCW0CMUBVHFW7KB.EXE (PID: 6816)
- Temp02TNIN0ANV4TH9XT9HCW0CMUBVHFW7KB.EXE (PID: 8788)
Process checks computer location settings
- TempJTJ33BDQIHTUAIBYKMYHZB9HVRCUNGQV.EXE (PID: 7772)
- ramez.exe (PID: 7976)
- 97a61b4446.tmp (PID: 1764)
- 649f5ebdb0.exe (PID: 7632)
- nircmd.exe (PID: 7964)
Disables trace logs
- powershell.exe (PID: 7816)
- powershell.exe (PID: 7224)
Creates files or folders in the user directory
- ramez.exe (PID: 7976)
- 97a61b4446.tmp (PID: 1764)
- WerFault.exe (PID: 1240)
- MSBuild.exe (PID: 6644)
- cvtres.exe (PID: 4920)
Creates a software uninstall entry
- 97a61b4446.tmp (PID: 1764)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
- powershell.exe (PID: 7912)
Reads the machine GUID from the registry
- 07c099764d.exe (PID: 7236)
- 22993beae5.exe (PID: 5256)
- MSBuild.exe (PID: 6644)
- cvtres.exe (PID: 4920)
Creates files in the program directory
- MSBuild.exe (PID: 6644)
- svchost.exe (PID: 6676)
Reads the software policy settings
- MSBuild.exe (PID: 6644)
- 22993beae5.exe (PID: 5256)
- cvtres.exe (PID: 4920)
- powershell.exe (PID: 7912)
Auto-launch of the file from Registry key
- ramez.exe (PID: 7976)
Reads CPU info
- MSBuild.exe (PID: 6644)
Reads product name
- MSBuild.exe (PID: 6644)
Reads Environment values
- MSBuild.exe (PID: 6644)
Changes the display of characters in the console
- cmd.exe (PID: 7800)
- cmd.exe (PID: 7964)
- cmd.exe (PID: 6488)
- cmd.exe (PID: 5344)
- cmd.exe (PID: 6324)
- cmd.exe (PID: 5800)
- cmd.exe (PID: 8308)
NirSoft software is detected
- nircmd.exe (PID: 7964)
- nircmd.exe (PID: 2908)
Application launched itself
- chrome.exe (PID: 7712)
- chrome.exe (PID: 8364)
- chrome.exe (PID: 8700)
- chrome.exe (PID: 8544)
- chrome.exe (PID: 8900)
- chrome.exe (PID: 9204)
- chrome.exe (PID: 8740)
- chrome.exe (PID: 8444)
- chrome.exe (PID: 7300)
- chrome.exe (PID: 7228)
- chrome.exe (PID: 8212)
- chrome.exe (PID: 8792)
- chrome.exe (PID: 8504)
- chrome.exe (PID: 8196)
- chrome.exe (PID: 8112)
Checks operating system version
- cmd.exe (PID: 5800)
- cmd.exe (PID: 6324)
Starts MODE.COM to configure console settings
- mode.com (PID: 6516)
- mode.com (PID: 6824)
Themida protector has been detected
- 22993beae5.exe (PID: 5256)
Attempting to use instant messaging service
- MSBuild.exe (PID: 7188)
- MSBuild.exe (PID: 7680)
Uses Task Scheduler to autorun other applications (AUTOMATE)
- WinTemp-v4.exe (PID: 9180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(7976) ramez.exe
C2185.156.72.96
URLhttp://185.156.72.96/te4h2nus/index.php
Version5.34
Options
Drop directoryd610cf342e
Drop nameramez.exe
Strings (125)lv:
msi
Kaspersky Lab
av:
|
#
"
\App
00000422
dm:
Powershell.exe
ProgramData\
ps1
rundll32
http://
Content-Disposition: form-data; name="data"; filename="
SOFTWARE\Microsoft\Windows NT\CurrentVersion
dll
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
id:
VideoID
cred.dll|clip.dll|
0000043f
cmd
00000423
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
-executionpolicy remotesigned -File "
2022
------
2016
og:
\0000
CurrentBuild
2019
:::
S-%lu-
" && timeout 1 && del
ProductName
Panda Security
ESET
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/k
+++
?scr=1
Doctor Web
GET
SYSTEM\ControlSet001\Services\BasicDisplay\Video
/quiet
.jpg
d610cf342e
vs:
sd:
rundll32.exe
"taskkill /f /im "
pc:
random
=
360TotalSecurity
<d>
wb
Content-Type: multipart/form-data; boundary=----
Startup
Norton
&& Exit"
os:
https://
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
2025
Avira
%-lu
zip
POST
"
Content-Type: application/octet-stream
Rem
/te4h2nus/index.php
------
5.34
<c>
clip.dll
AVAST Software
\
shell32.dll
" && ren
e3
ramez.exe
kernel32.dll
DefaultSettings.XResolution
d1
DefaultSettings.YResolution
185.156.72.96
r=
cred.dll
--
GetNativeSystemInfo
-%lu
ComputerName
&unit=
Keyboard Layout\Preload
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
ar:
Sophos
%USERPROFILE%
exe
e1
e2
st=s
Programs
0123456789
un:
rb
bi:
abcdefghijklmnopqrstuvwxyz0123456789-_
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
cmd /C RMDIR /s/q
Bitdefender
-unicode-
AVG
WinDefender
&&
shutdown -s -t 0
Comodo
00000419
Content-Type: application/x-www-form-urlencoded
/Plugins/
Main
Vidar
(PID) Process(6644) MSBuild.exe
C2https://t.me/eom25h
URLhttps://steamcommunity.com/profiles/76561199855598339
RC43333333333333333UUUUUUUUUUUUUUUU
Strings (1)
Lumma
(PID) Process(5256) 22993beae5.exe
C2 (10)btcgeared.live/lbak
clarmodq.top/qoxo
buzzarddf.live/ktnt
techguidet.digital/apdo
timertvey.top/ldak
bearjk.live/benj
parakehjet.run/kewk
zenithcorde.top/auid
techsyncq.run/riid
fishgh.digital/tequ
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:20 01:03:48+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 633856 |
| InitializedDataSize: | 326144 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20577 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
Total processes
807
Monitored processes
665
Malicious processes
49
Suspicious processes
22
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 140 | sc stop "SgrmAgent" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | C:\WINDOWS\system32\WerFault.exe -u -p 920 -s 1464 | C:\Windows\System32\WerFault.exe | — | Unlocker.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | schtasks /Delete /TN "Microsoft\Windows\Windows Defender\Windows Defender Cache Maintenance" /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Task Scheduler Configuration Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | reg query "HKLM\System\CurrentControlSet\Services\MsSecWfp" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | sc query IObitUnlocker | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | reg delete "HKLM\System\CurrentControlset\Control\WMI\Autologger\DefenderApiLogger" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | timeout /t 2 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | sc config "webthreatdefusersvc" start= disabled | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | "C:\Users\admin\AppData\Local\Apps\2.0\5LKPAQRT.N4P\6HYHP8OH.M65\scre..tion_25b0fbb6ef7eb094_0019.0002_c67b0b62bbccb71f\ScreenConnect.WindowsClient.exe" | C:\Users\admin\AppData\Local\Apps\2.0\5LKPAQRT.N4P\6HYHP8OH.M65\scre..tion_25b0fbb6ef7eb094_0019.0002_c67b0b62bbccb71f\ScreenConnect.WindowsClient.exe | — | dfsvc.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Version: 25.2.4.9229 Modules
| |||||||||||||||
| 744 | "C:\Users\admin\AppData\Local\Temp\10154530101\97a61b4446.exe" | C:\Users\admin\AppData\Local\Temp\10154530101\97a61b4446.exe | ramez.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: MyApp Setup Exit code: 0 Version: Modules
| |||||||||||||||
Total events
311 420
Read events
310 733
Write events
425
Delete events
262
Modification events
| (PID) Process: | (3332) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3332) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3332) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000050294 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000050294 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7224) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7224) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7224) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7224) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7224) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
125
Suspicious files
164
Text files
194
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2320 | random.exe | C:\Users\admin\AppData\Local\Temp\0aQYqcAlr.hta | html | |
MD5:DD147151E600EDF9524E03E39A102E5C | SHA256:1365F657276D95ABA90FF62337CB27B2A55A0FBD899CBE1FB2334E6F7DFD89C8 | |||
| 7224 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_34bktumv.jqe.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7976 | ramez.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\random[1].exe | executable | |
MD5:ECE1D1507B62C20327E999C6936A95A7 | SHA256:8EB08322033F193A5E7EA16D83C0CD324EFAAAB628FB245BDB27F6977C2A6D86 | |||
| 7224 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:EEB9D818B8044D606F0DD4929D7AF543 | SHA256:15FC1AD8E2DF2AF33957AD8845C632F854C650C8029A88B472AB1CA3AF959969 | |||
| 7224 | powershell.exe | C:\Users\admin\AppData\Local\TempJTJ33BDQIHTUAIBYKMYHZB9HVRCUNGQV.EXE | executable | |
MD5:26CC5A6CFD8E8ECC433337413C14CDDB | SHA256:2D904D576B46236BAF504DBA21775F6EBBBD0F65272A9C2FCA1C6798184FA4E8 | |||
| 7816 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_v2ekscl2.tza.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7772 | TempJTJ33BDQIHTUAIBYKMYHZB9HVRCUNGQV.EXE | C:\Windows\Tasks\ramez.job | binary | |
MD5:1C098D0946ABDECFAD49B6FC833731E9 | SHA256:12ABAEAF8971270220BA79D1918C39F3866BB58157B9F4AF2BAF55BAF89150BF | |||
| 7976 | ramez.exe | C:\Users\admin\AppData\Local\Temp\10154520101\07c099764d.exe | executable | |
MD5:ECE1D1507B62C20327E999C6936A95A7 | SHA256:8EB08322033F193A5E7EA16D83C0CD324EFAAAB628FB245BDB27F6977C2A6D86 | |||
| 744 | 97a61b4446.exe | C:\Users\admin\AppData\Local\Temp\is-OFM7A.tmp\97a61b4446.tmp | executable | |
MD5:E4C43138CCB8240276872FD1AEC369BE | SHA256:46BE5E3F28A5E4ED63D66B901D927C25944B4DA36EFFEA9C97FB05994360EDF5 | |||
| 1764 | 97a61b4446.tmp | C:\Users\admin\AppData\Roaming\MyApp\unins000.exe | executable | |
MD5:4134EC81A9D645602B1FA265F98FBF35 | SHA256:69966257CE41717F2121EA1F03F8BFA1486423ACECFCC977DD9F1E157C911AD4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
124
TCP/UDP connections
129
DNS requests
62
Threats
130
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7224 | powershell.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/testmine/random.exe | unknown | — | — | unknown |
7976 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
7816 | powershell.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/testmine/random.exe | unknown | — | — | unknown |
7976 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
7976 | ramez.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/unique2/random.exe | unknown | — | — | unknown |
7976 | ramez.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/unique1/random.exe | unknown | — | — | unknown |
5124 | info.exe | GET | — | 45.155.69.47:80 | http://pub-stat-999.twilightparadox.com/api/record?t=p3 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7224 | powershell.exe | 185.156.72.2:80 | — | Tov Vaiz Partner | RU | unknown |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
t.me |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7224 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7224 | powershell.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7224 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
7224 | powershell.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
7224 | powershell.exe | Misc activity | ET INFO Packed Executable Download |
7976 | ramez.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
7816 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7816 | powershell.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7816 | powershell.exe | Misc activity | ET INFO Packed Executable Download |
7816 | powershell.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
1 ETPRO signatures available at the full report