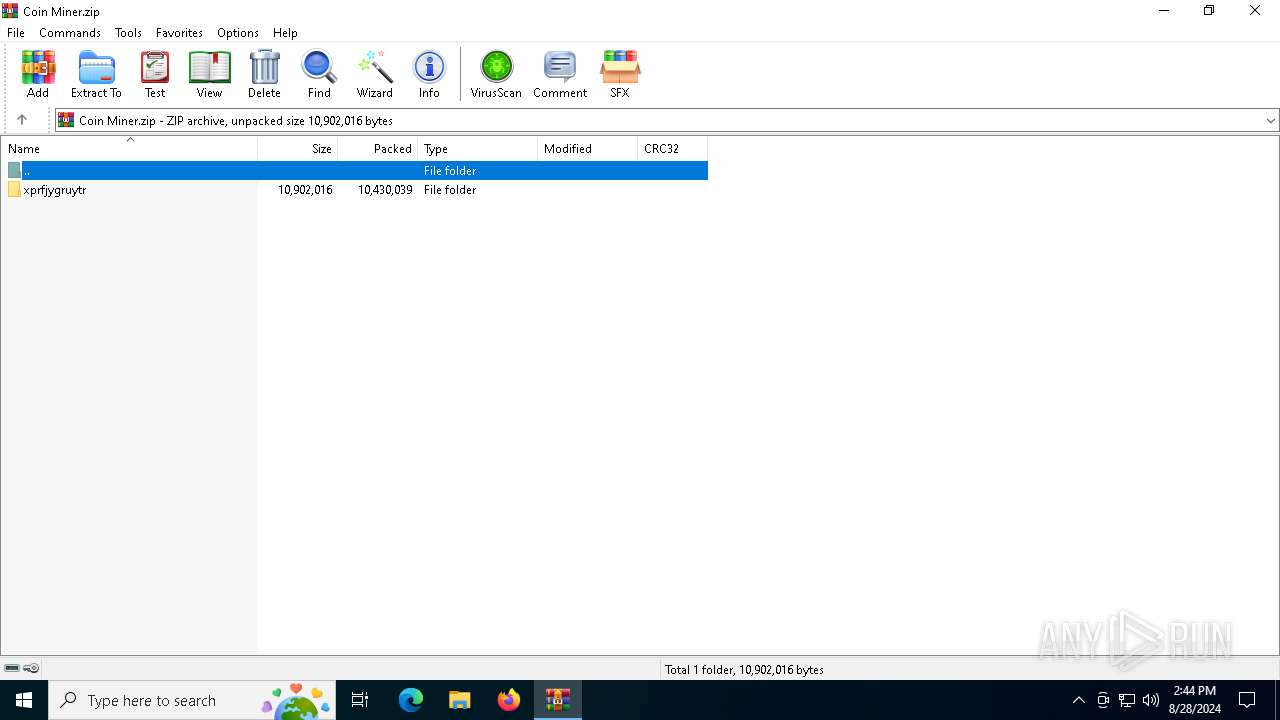
| File name: | Coin Miner.zip |
| Full analysis: | https://app.any.run/tasks/0b79cd9d-e078-47ee-9067-da8590adf248 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | August 28, 2024, 14:44:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 1F640A6D75EEFEF4ABEEB45EDC4406E4 |
| SHA1: | F34E6FB4D075ADD235F81D3D3B9B6BCBE1025468 |
| SHA256: | DFF074379AAF466C4C0D8EB06235320F4866B7385804836BBF21A26223DCF779 |
| SSDEEP: | 98304:/N6dfnDwnj1nTOvpCe6P3y7tie96jW7mgExvwDaSgdYKWfiC+4BI/Mw9ByJFZZia:/UWWN+u7FBWh9kqiAwKYrF |
MALICIOUS
Changes the autorun value in the registry
- reg.exe (PID: 1452)
- reg.exe (PID: 5944)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2256)
SUSPICIOUS
Uses powercfg.exe to modify the power settings
- etzpikspwykg.exe (PID: 5692)
- etzpikspwykg.exe (PID: 1332)
Executable content was dropped or overwritten
- etzpikspwykg.exe (PID: 1332)
- etzpikspwykg.exe (PID: 5692)
Uses REG/REGEDIT.EXE to modify registry
- etzpikspwykg.exe (PID: 1332)
- etzpikspwykg.exe (PID: 5692)
Starts itself from another location
- etzpikspwykg.exe (PID: 1332)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6188)
- etzpikspwykg.exe (PID: 1332)
- etzpikspwykg.exe (PID: 5692)
Drops a system driver (possible attempt to evade defenses)
- etzpikspwykg.exe (PID: 5692)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2256)
INFO
Manual execution by a user
- etzpikspwykg.exe (PID: 1332)
Creates files or folders in the user directory
- etzpikspwykg.exe (PID: 1332)
Checks supported languages
- etzpikspwykg.exe (PID: 1332)
- etzpikspwykg.exe (PID: 5692)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6188)
Create files in a temporary directory
- etzpikspwykg.exe (PID: 5692)
Reads the software policy settings
- slui.exe (PID: 5140)
- slui.exe (PID: 6212)
Checks proxy server information
- slui.exe (PID: 6212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:27 16:30:38 |
| ZipCRC: | 0x8a574462 |
| ZipCompressedSize: | 10430039 |
| ZipUncompressedSize: | 10902016 |
| ZipFileName: | xprfjygruytr/etzpikspwykg.exe |
Total processes
158
Monitored processes
30
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 964 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1292 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1332 | "C:\Users\admin\Desktop\Coin Miner\xprfjygruytr\etzpikspwykg.exe" | C:\Users\admin\Desktop\Coin Miner\xprfjygruytr\etzpikspwykg.exe | explorer.exe | ||||||||||||
User: admin Company: Google Chrome Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 127,0,6533,89 Modules
| |||||||||||||||
| 1452 | C:\WINDOWS\system32\reg.exe add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "VIFLJRPW" /t REG_SZ /f /d "C:\Users\admin\AppData\Roaming\xprfjygruytr\etzpikspwykg.exe" | C:\Windows\System32\reg.exe | etzpikspwykg.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | C:\WINDOWS\system32\powercfg.exe /x -standby-timeout-ac 0 | C:\Windows\System32\powercfg.exe | — | etzpikspwykg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2112 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | svchost.exe | C:\Windows\System32\svchost.exe | etzpikspwykg.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2624 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2768 | C:\WINDOWS\system32\powercfg.exe /x -standby-timeout-dc 0 | C:\Windows\System32\powercfg.exe | — | etzpikspwykg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 552
Read events
9 541
Write events
11
Delete events
0
Modification events
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Coin Miner.zip | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6188) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
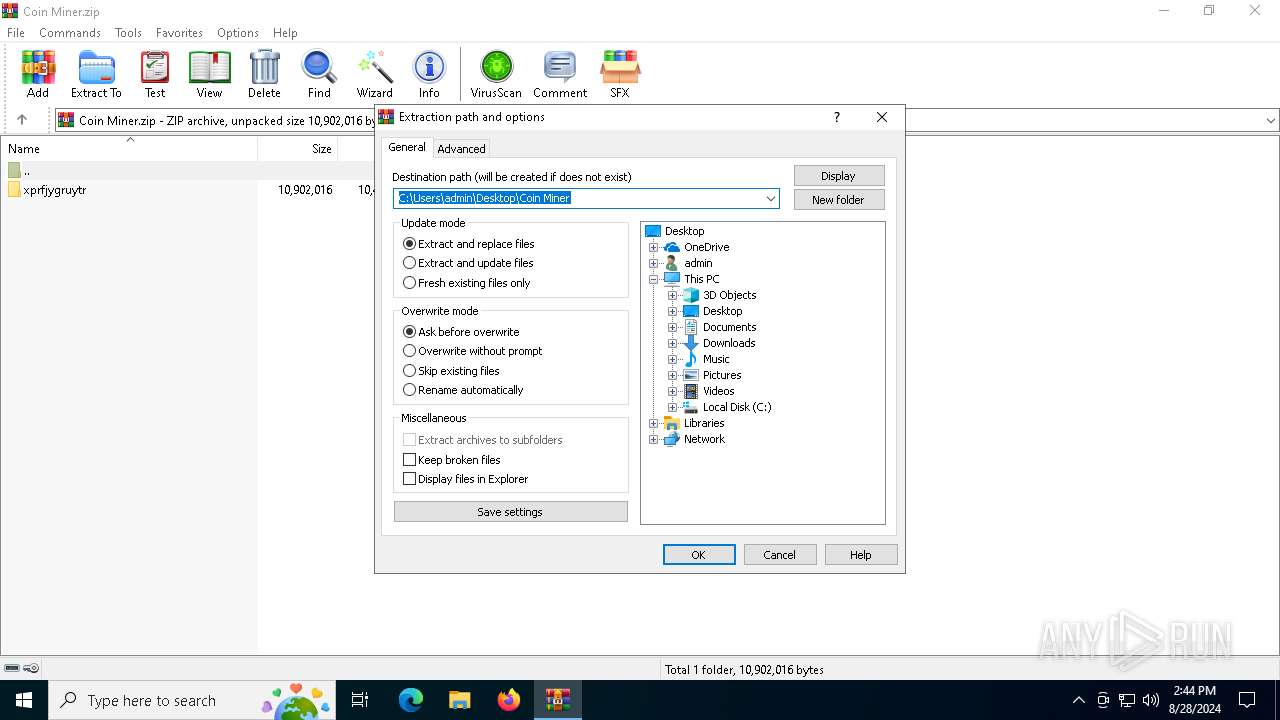
Value: C:\Users\admin\Desktop\Coin Miner | |||
| (PID) Process: | (1452) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | VIFLJRPW |
Value: C:\Users\admin\AppData\Roaming\xprfjygruytr\etzpikspwykg.exe | |||
Executable files
3
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5692 | etzpikspwykg.exe | C:\Users\admin\AppData\Local\Temp\cofhaqkdwqvn.sys | executable | |
MD5:0C0195C48B6B8582FA6F6373032118DA | SHA256:11BD2C9F9E2397C9A16E0990E4ED2CF0679498FE0FD418A3DFDAC60B5C160EE5 | |||
| 1332 | etzpikspwykg.exe | C:\Users\admin\AppData\Roaming\xprfjygruytr\etzpikspwykg.exe | executable | |
MD5:025EBE0A476FE1A27749E6DA0EEA724F | SHA256:2A51D50F42494C6AB6027DBD35F8861BDD6FE1551F5FB30BF10138619F4BC4B2 | |||
| 6188 | WinRAR.exe | C:\Users\admin\Desktop\Coin Miner\xprfjygruytr\etzpikspwykg.exe | executable | |
MD5:025EBE0A476FE1A27749E6DA0EEA724F | SHA256:2A51D50F42494C6AB6027DBD35F8861BDD6FE1551F5FB30BF10138619F4BC4B2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
37
DNS requests
19
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4164 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2816 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2816 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
236 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6248 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6164 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6164 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4164 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4164 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
pool.hashvault.pro |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Crypto Currency Mining Activity Detected | ET COINMINER CoinMiner Domain in DNS Lookup (pool .hashvault .pro) |