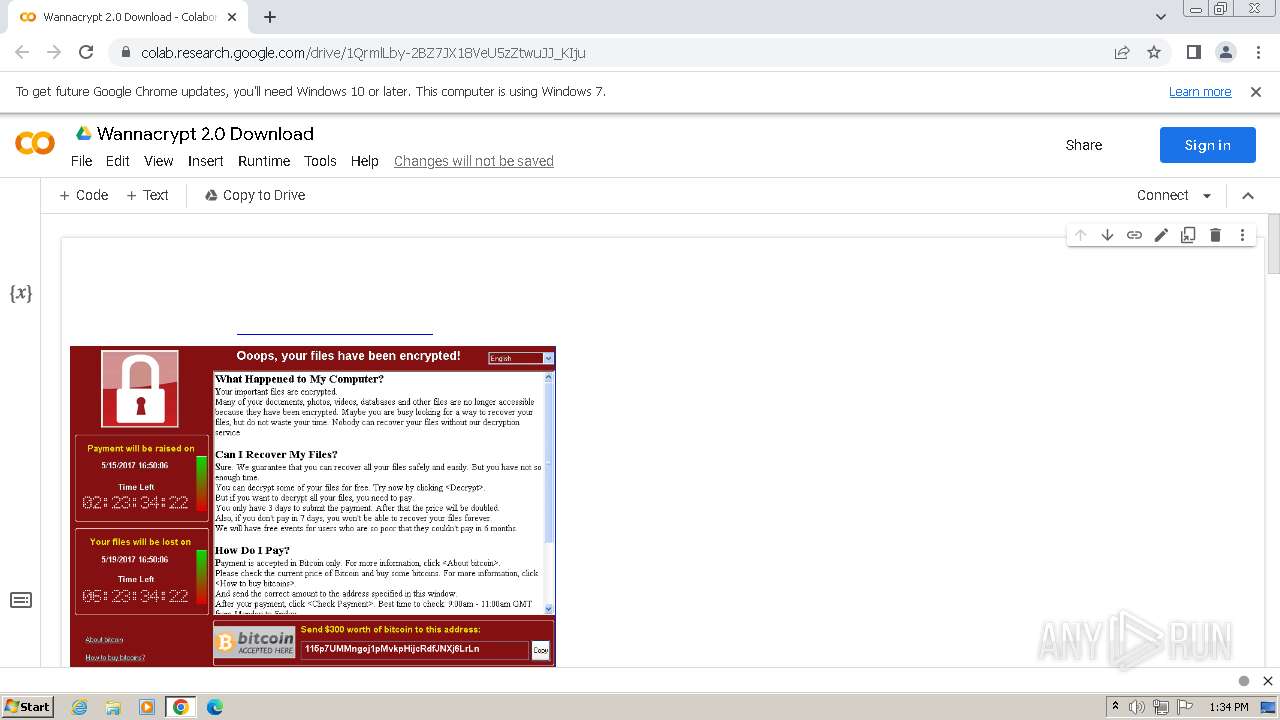
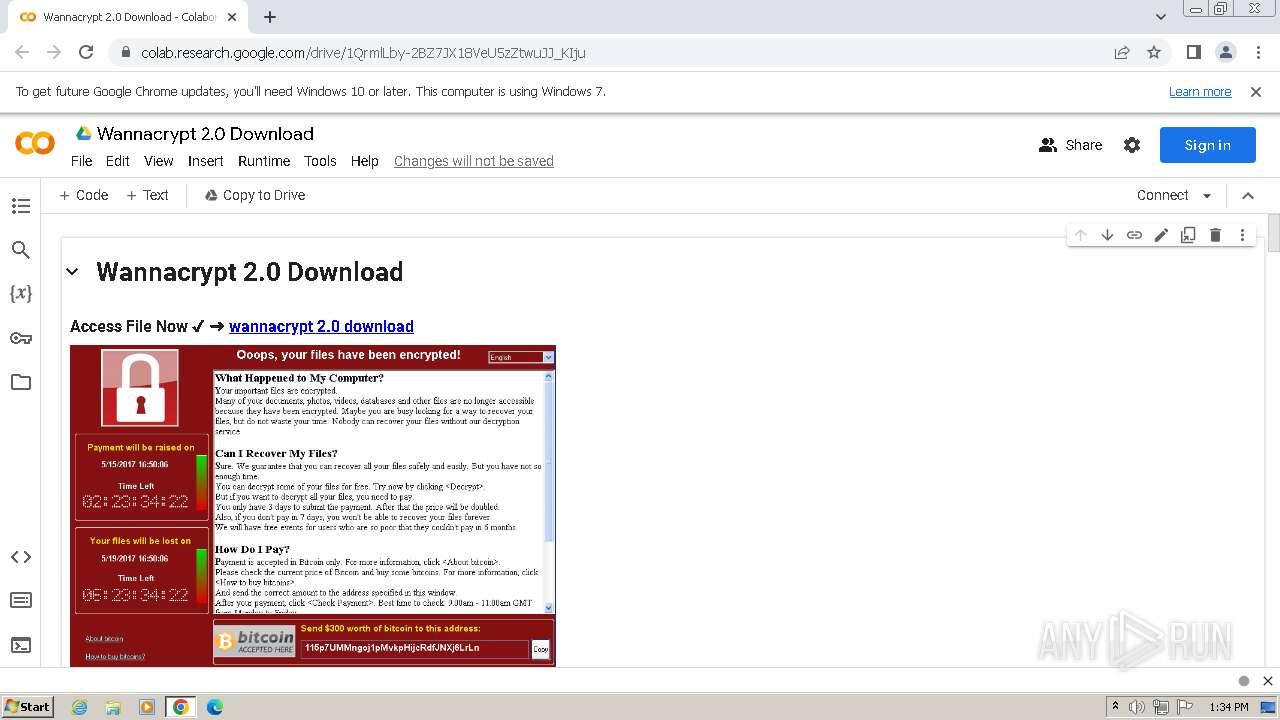
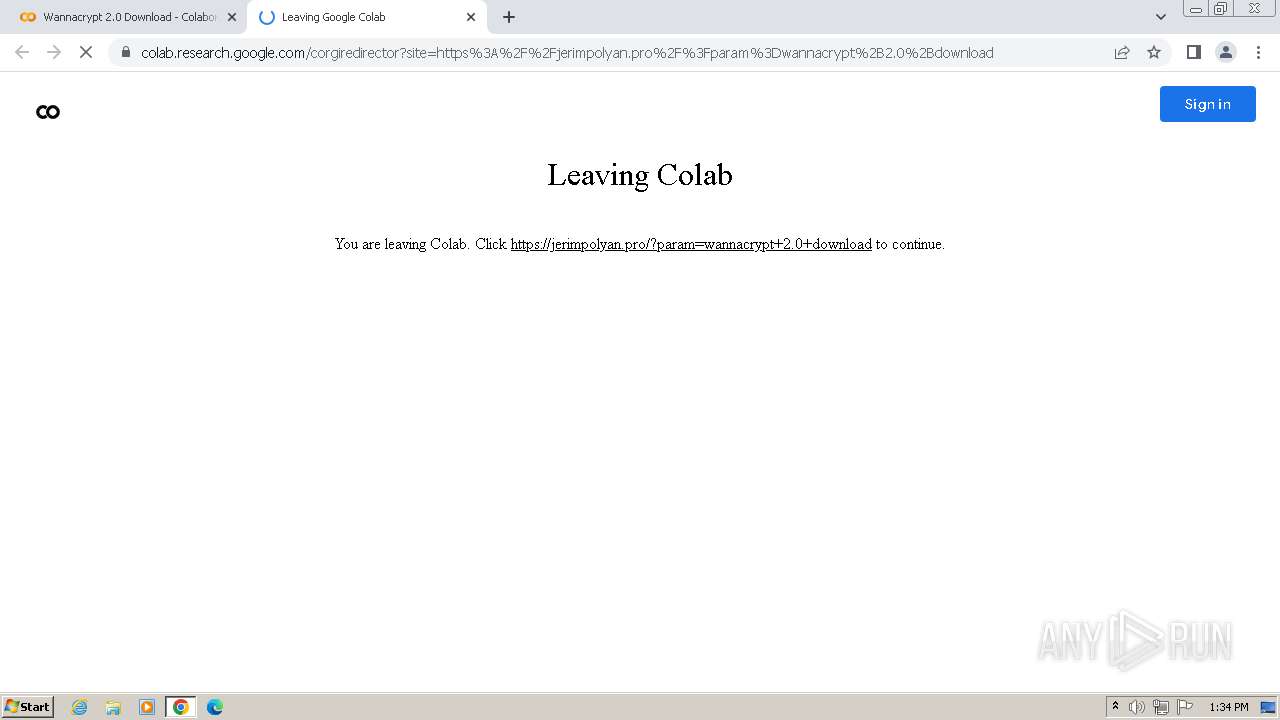
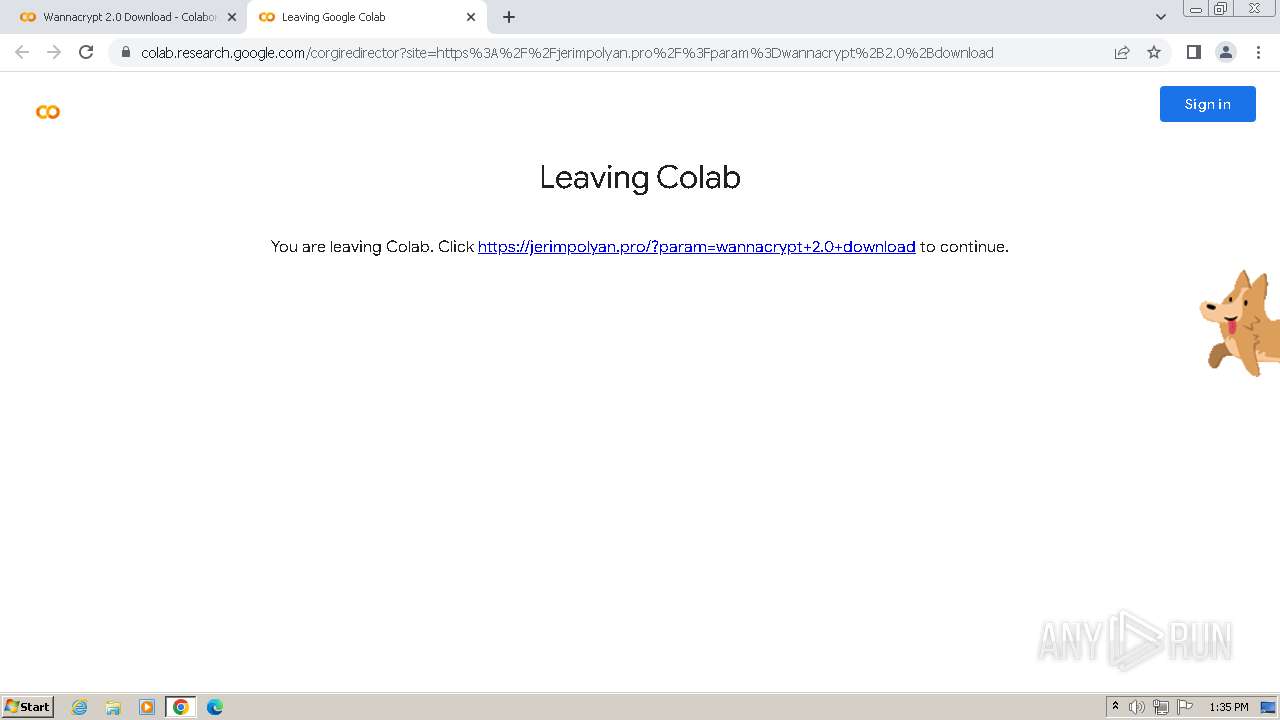
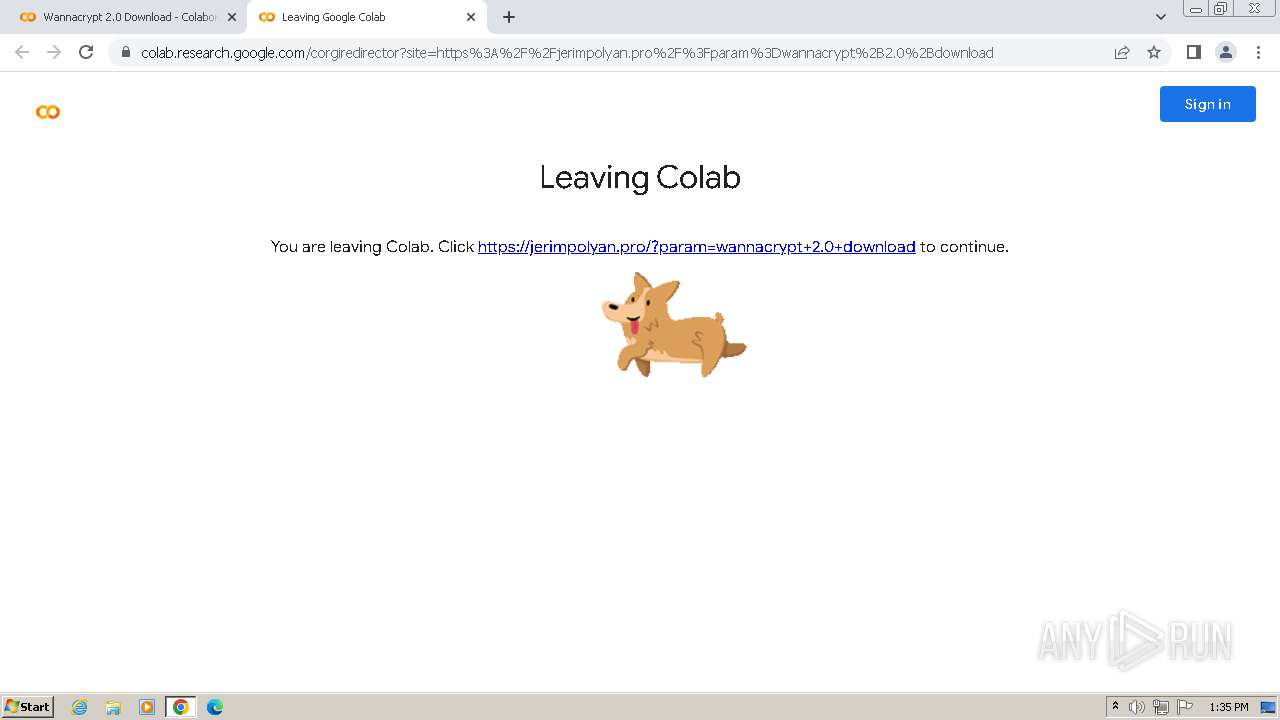
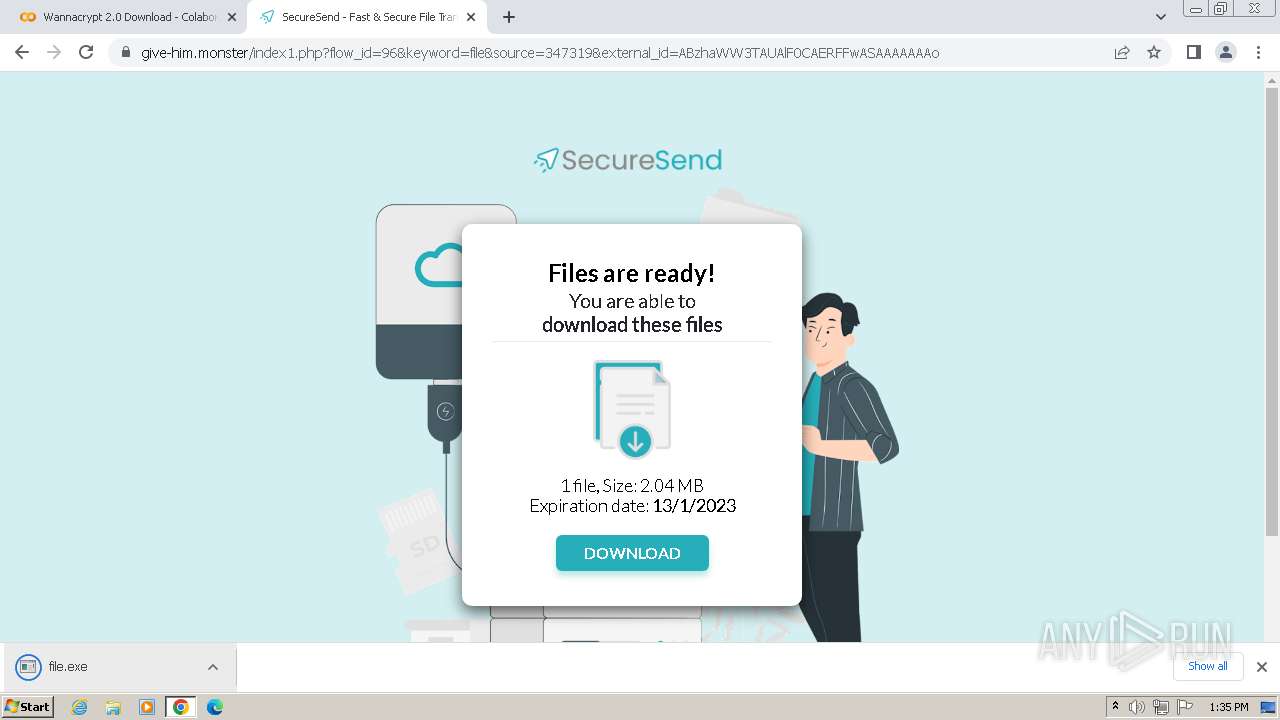
| URL: | https://colab.research.google.com/drive/1QrmlLby-2BZ7JX18VeU5zZtwuJJ_KIju |
| Full analysis: | https://app.any.run/tasks/2fa50eaf-91c0-4f4f-a86e-fe5a13c01d18 |
| Verdict: | Malicious activity |
| Threats: | Rhadamanthys is a C++ information-stealing malware that extracts sensitive data from infiltrated machines. Its layered operational chain and advanced evasion tactics make it a major risk in cybersecurity landscapes. |
| Analysis date: | December 01, 2023, 13:34:20 |
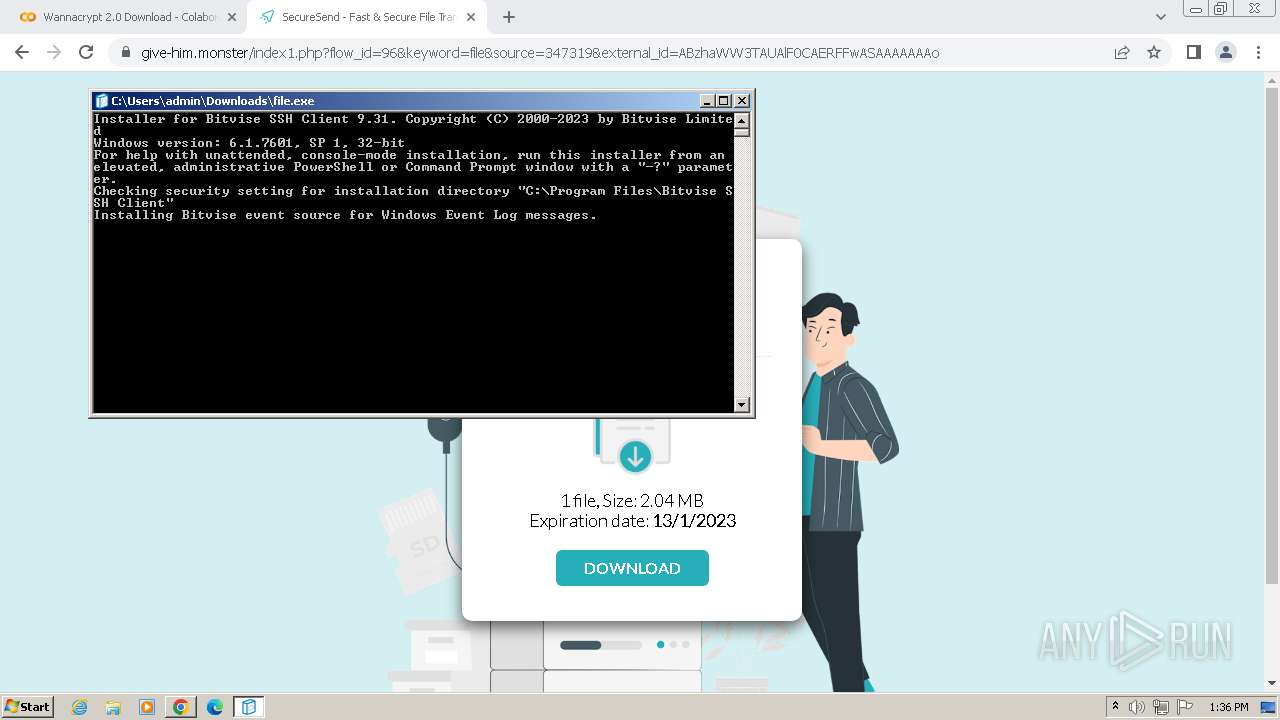
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 1EDF2883377538AD189874D1F3418ED6 |
| SHA1: | 6112ED9B6BD5F4975E3844146518B31E18217A1E |
| SHA256: | DFDE313F639251B97F581A9634EB80977D006525DFC1E3B75E7F49229029D506 |
| SSDEEP: | 3:N8XKHHPvnXj0XIJp8Oc6zAlf/Bi8n:26HHPvjJp8O3z6XBl |
MALICIOUS
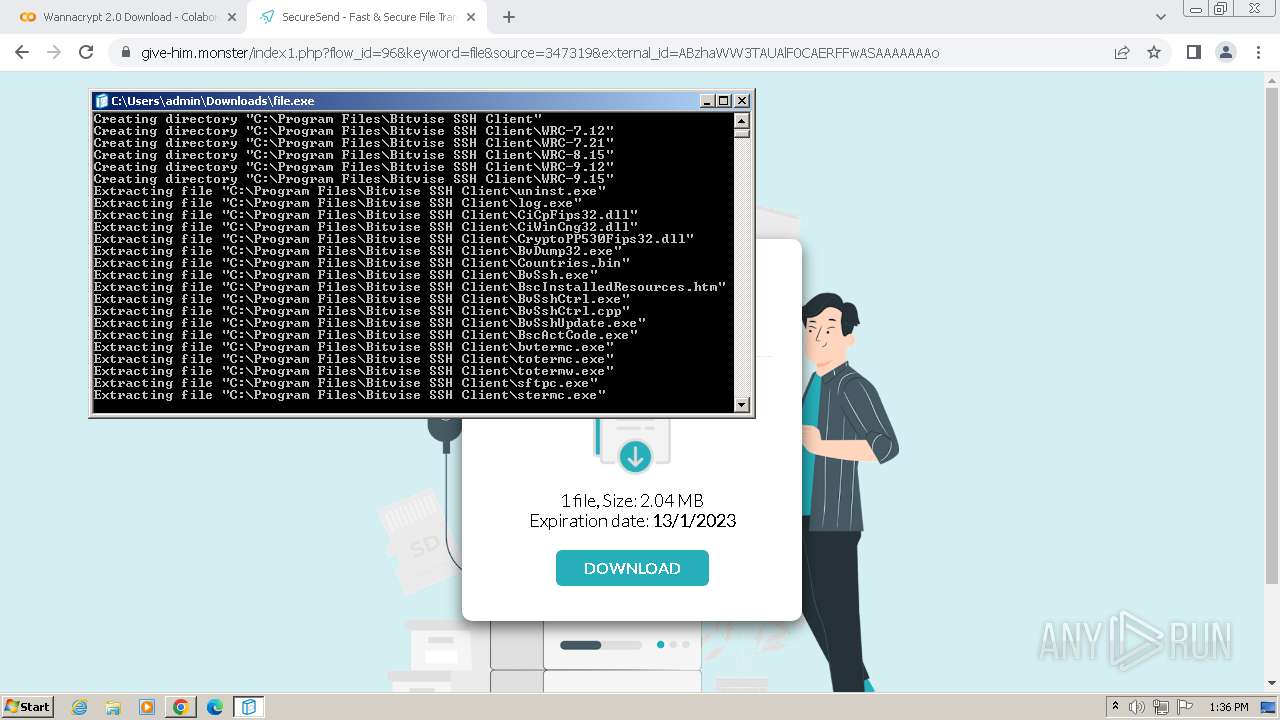
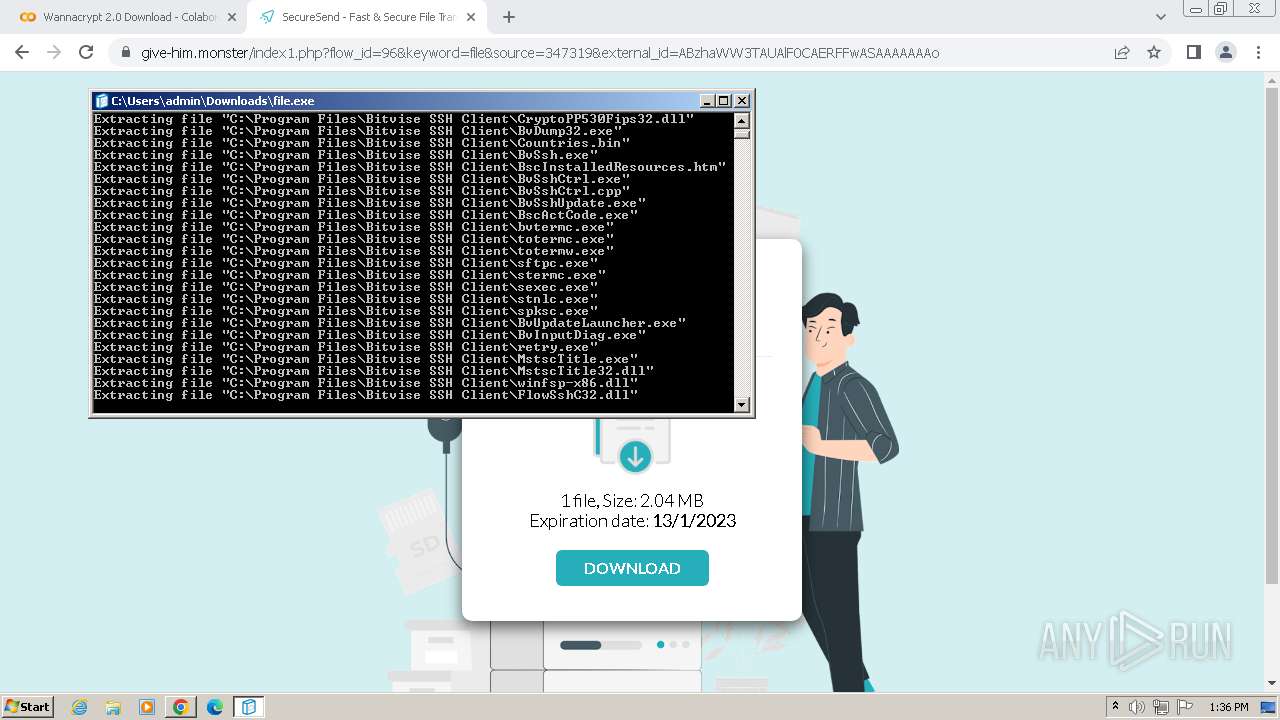
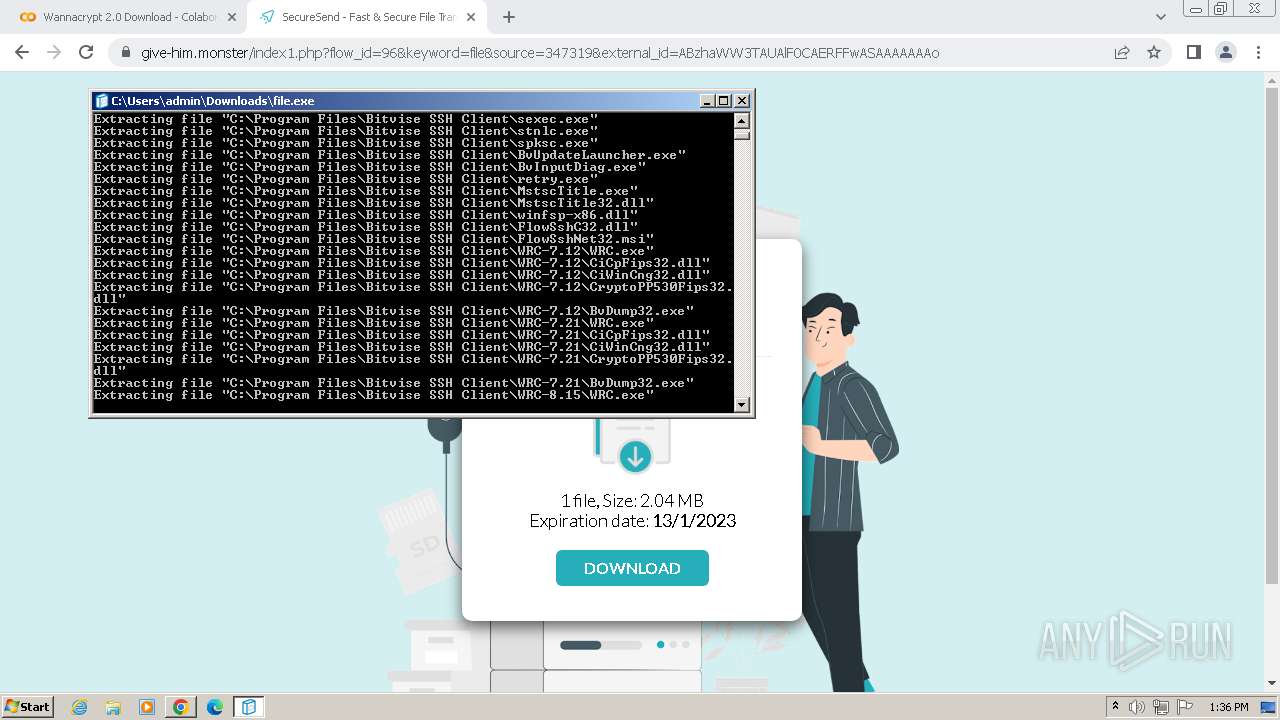
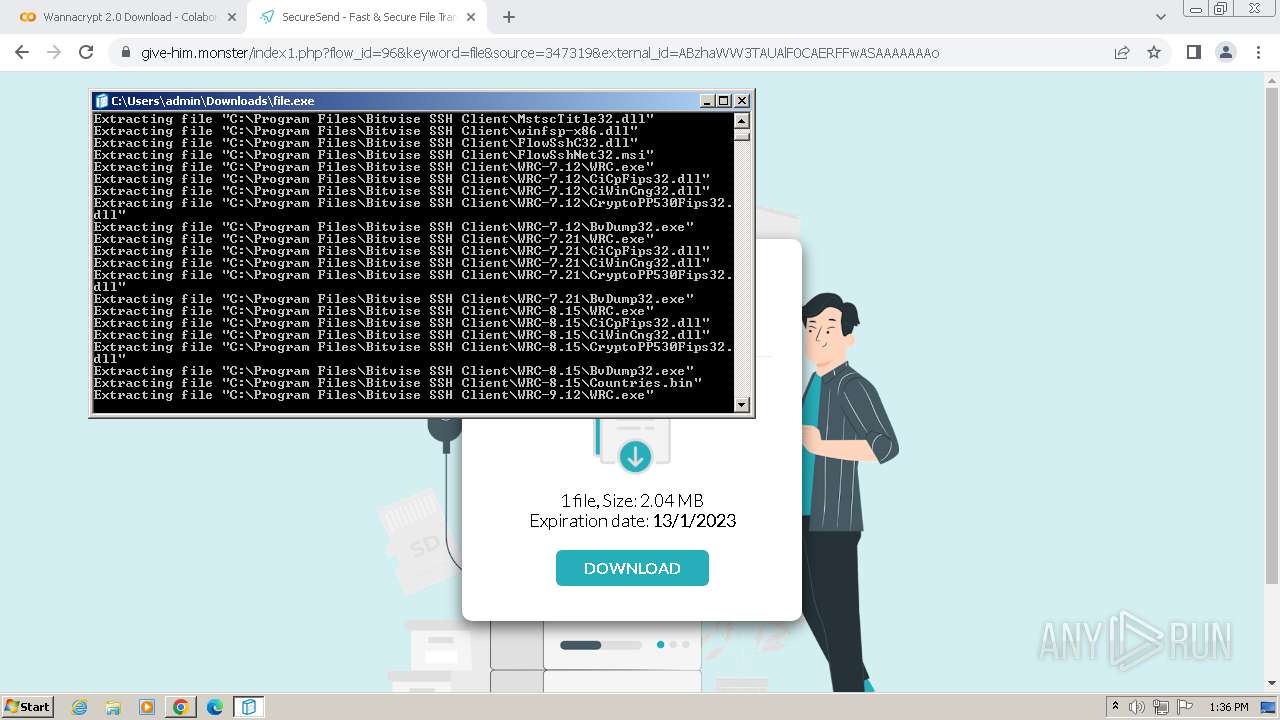
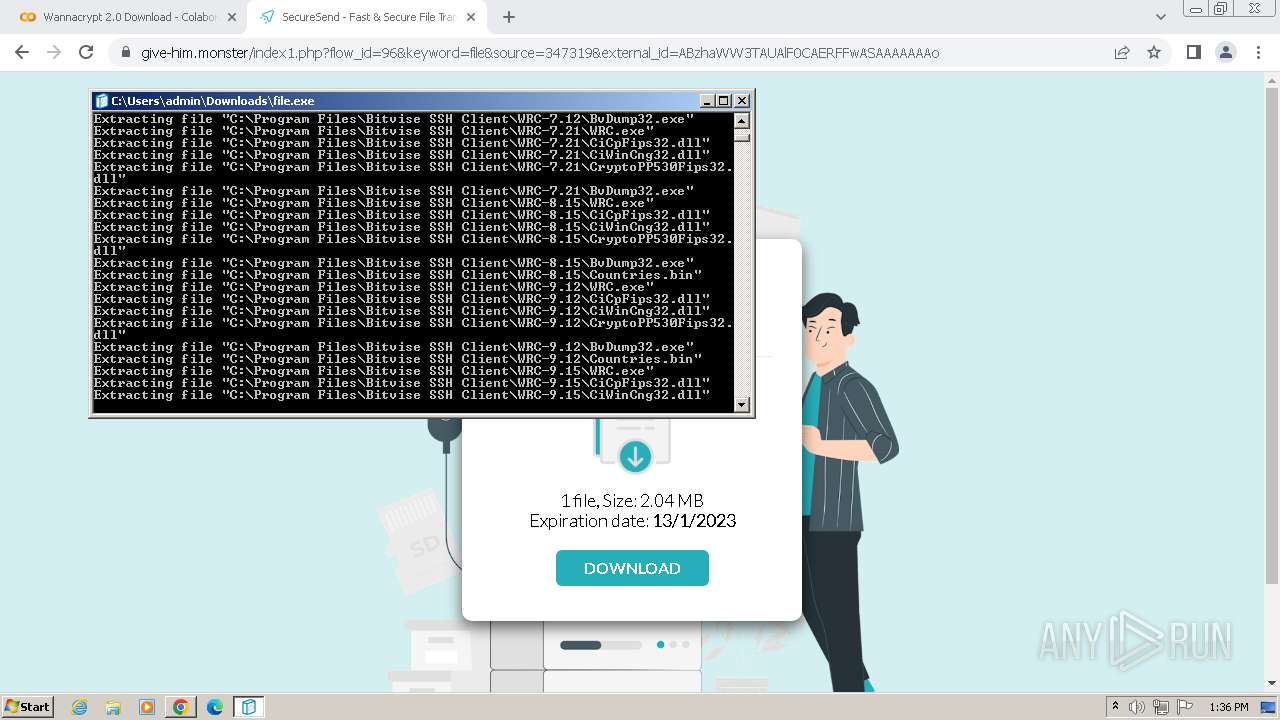
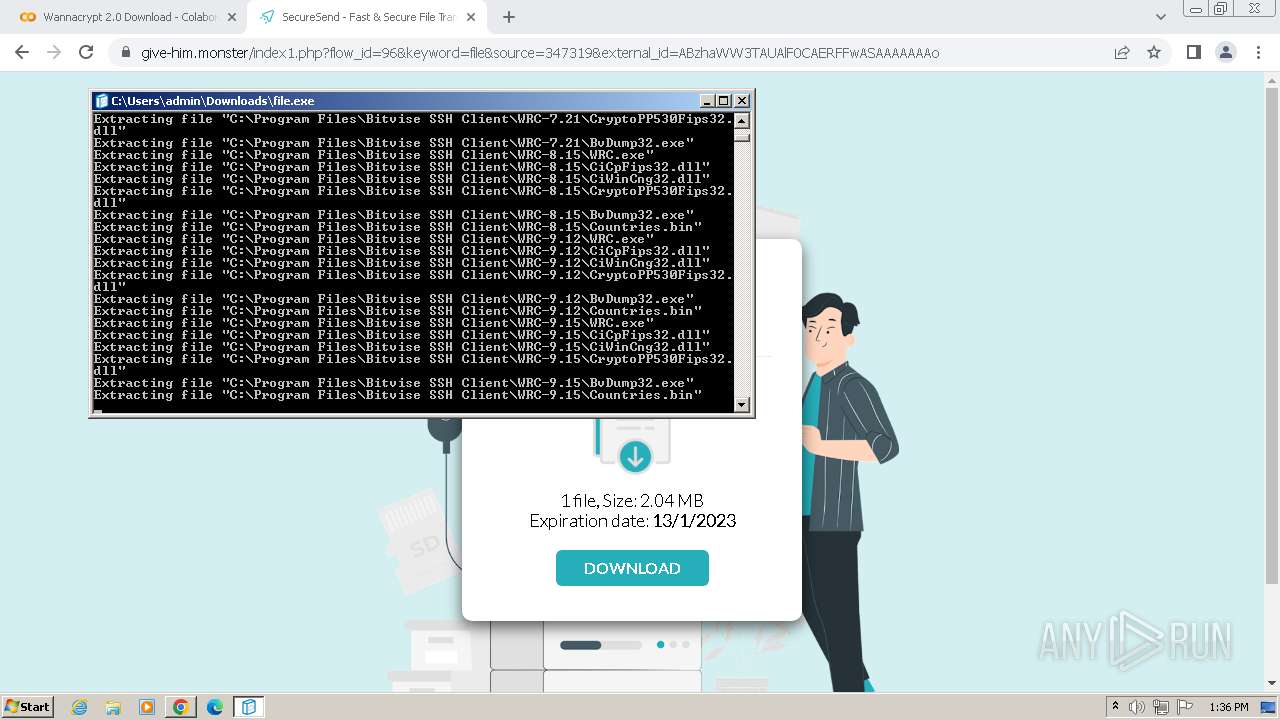
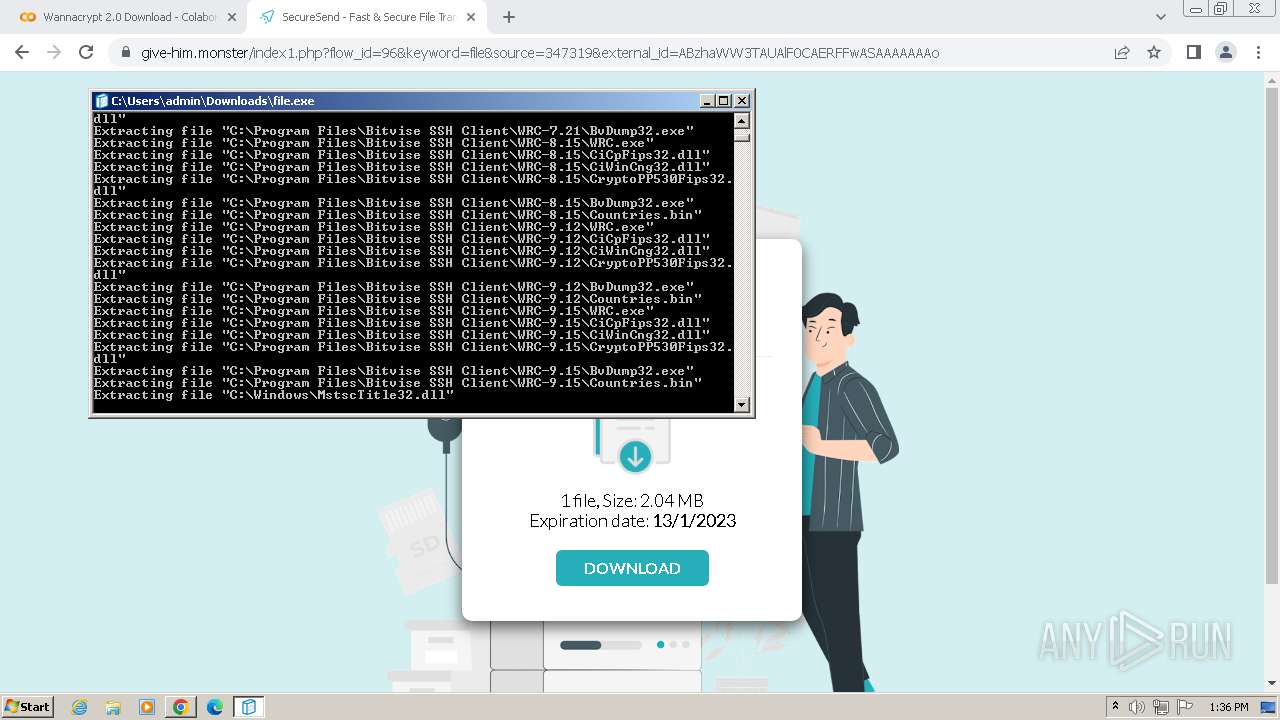
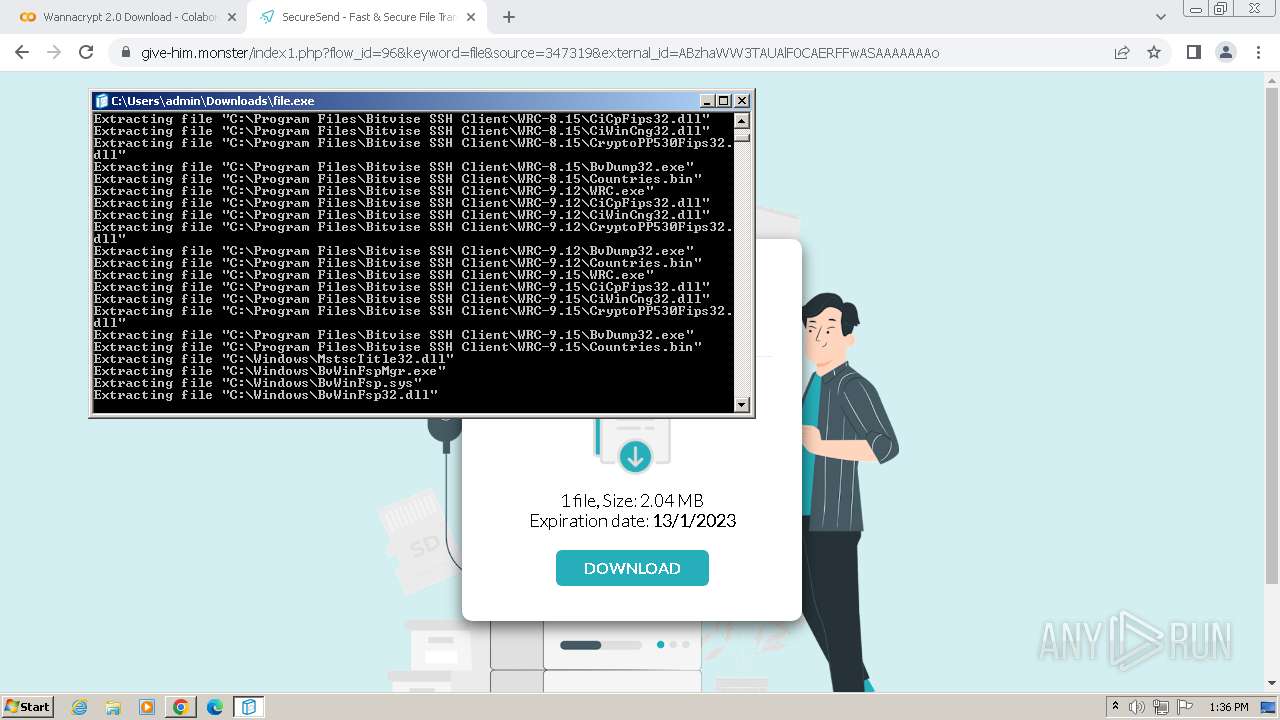
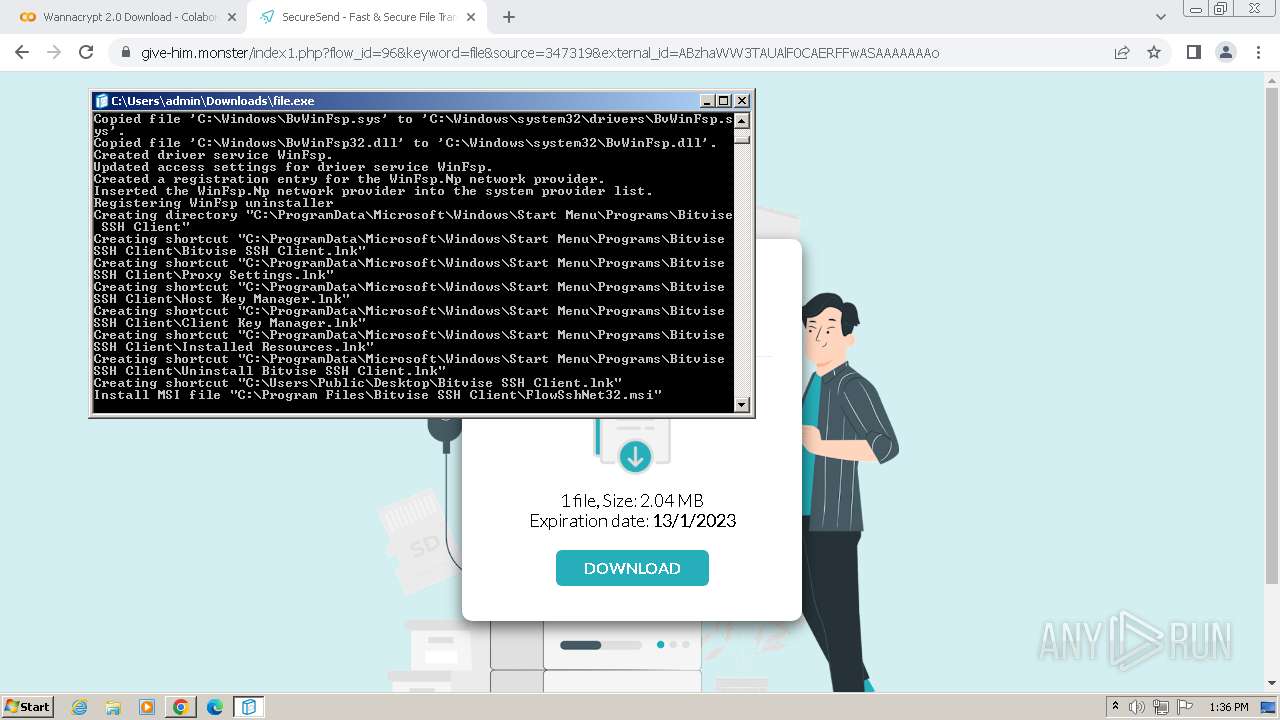
Creates a writable file in the system directory
- file.exe (PID: 1656)
- BvWinFspMgr.exe (PID: 3616)
Drops the executable file immediately after the start
- file.exe (PID: 1656)
- BvWinFspMgr.exe (PID: 3616)
- msiexec.exe (PID: 2152)
RHADAMANTHYS has been detected (YARA)
- BvSsh.exe (PID: 128)
SUSPICIOUS
Process drops legitimate windows executable
- chrome.exe (PID: 888)
Drops a system driver (possible attempt to evade defenses)
- file.exe (PID: 1656)
- BvWinFspMgr.exe (PID: 3616)
Creates files in the driver directory
- BvWinFspMgr.exe (PID: 3616)
Checks Windows Trust Settings
- msiexec.exe (PID: 2152)
- BvSsh.exe (PID: 128)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2152)
Searches for installed software
- BvSsh.exe (PID: 128)
Reads the Internet Settings
- BvSsh.exe (PID: 128)
Reads security settings of Internet Explorer
- BvSsh.exe (PID: 128)
Reads settings of System Certificates
- BvSsh.exe (PID: 128)
Adds/modifies Windows certificates
- msiexec.exe (PID: 2152)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 2536)
- wmpnscfg.exe (PID: 2692)
- BvSsh.exe (PID: 128)
Checks supported languages
- wmpnscfg.exe (PID: 2536)
- wmpnscfg.exe (PID: 2692)
- file.exe (PID: 1656)
- BvEventSource.exe (PID: 1808)
- BvWinFspMgr.exe (PID: 3616)
- msiexec.exe (PID: 2152)
- BvSsh.exe (PID: 128)
Reads the computer name
- wmpnscfg.exe (PID: 2536)
- wmpnscfg.exe (PID: 2692)
- file.exe (PID: 1656)
- BvWinFspMgr.exe (PID: 3616)
- msiexec.exe (PID: 2152)
- BvSsh.exe (PID: 128)
The process uses the downloaded file
- chrome.exe (PID: 3604)
- chrome.exe (PID: 3360)
- chrome.exe (PID: 3620)
- chrome.exe (PID: 3660)
- chrome.exe (PID: 888)
- file.exe (PID: 1656)
Drops the executable file immediately after the start
- chrome.exe (PID: 888)
Creates files in the program directory
- file.exe (PID: 1656)
Application launched itself
- chrome.exe (PID: 888)
Reads the machine GUID from the registry
- file.exe (PID: 1656)
- msiexec.exe (PID: 2152)
- BvSsh.exe (PID: 128)
Create files in a temporary directory
- msiexec.exe (PID: 2152)
Creates files or folders in the user directory
- BvSsh.exe (PID: 128)
Checks proxy server information
- BvSsh.exe (PID: 128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
89
Monitored processes
46
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
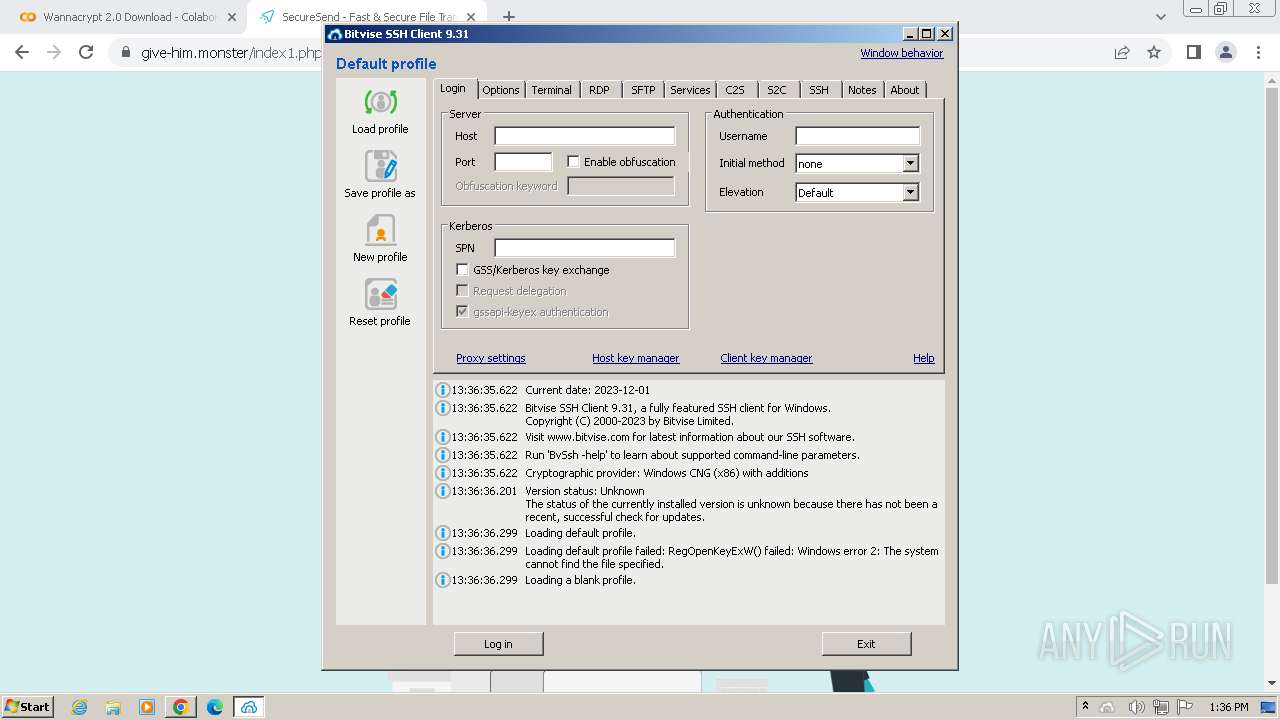
| 128 | "C:\Program Files\Bitvise SSH Client\BvSsh.exe" | C:\Program Files\Bitvise SSH Client\BvSsh.exe | explorer.exe | ||||||||||||
User: admin Company: Bitvise Limited Integrity Level: MEDIUM Description: Bitvise SSH Client Exit code: 0 Version: 9.31.0.0 Modules
| |||||||||||||||
| 276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=4836 --field-trial-handle=1148,i,3841157696482164589,11816311039485976665,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 844 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6a7a8b38,0x6a7a8b48,0x6a7a8b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 888 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking "https://colab.research.google.com/drive/1QrmlLby-2BZ7JX18VeU5zZtwuJJ_KIju" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1368 --field-trial-handle=1148,i,3841157696482164589,11816311039485976665,131072 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=23 --mojo-platform-channel-handle=4092 --field-trial-handle=1148,i,3841157696482164589,11816311039485976665,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1452 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3624 --field-trial-handle=1148,i,3841157696482164589,11816311039485976665,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1640 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=4376 --field-trial-handle=1148,i,3841157696482164589,11816311039485976665,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
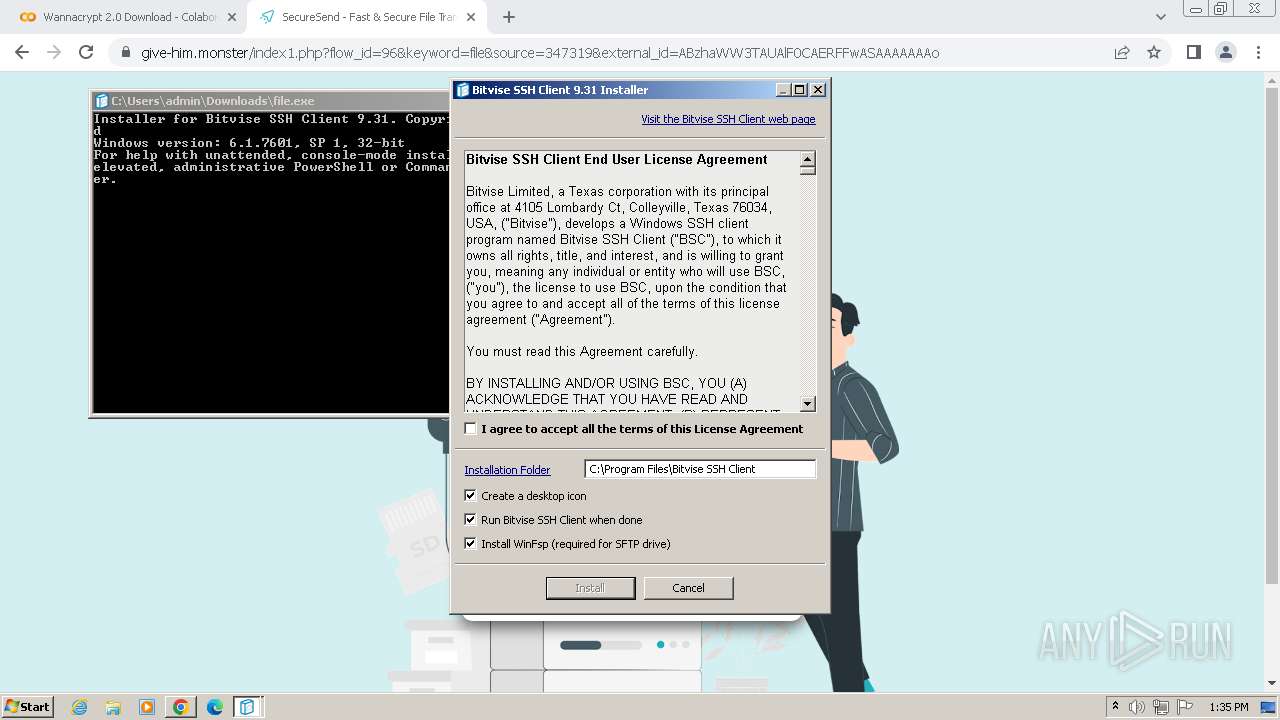
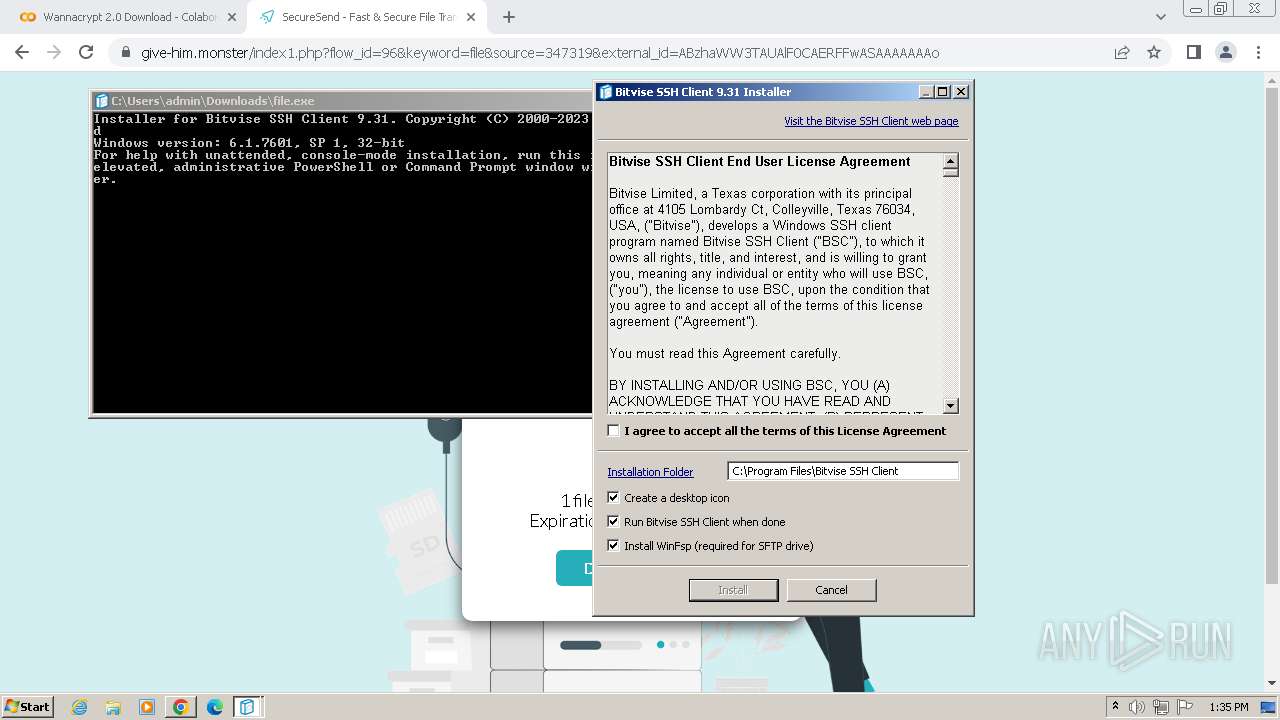
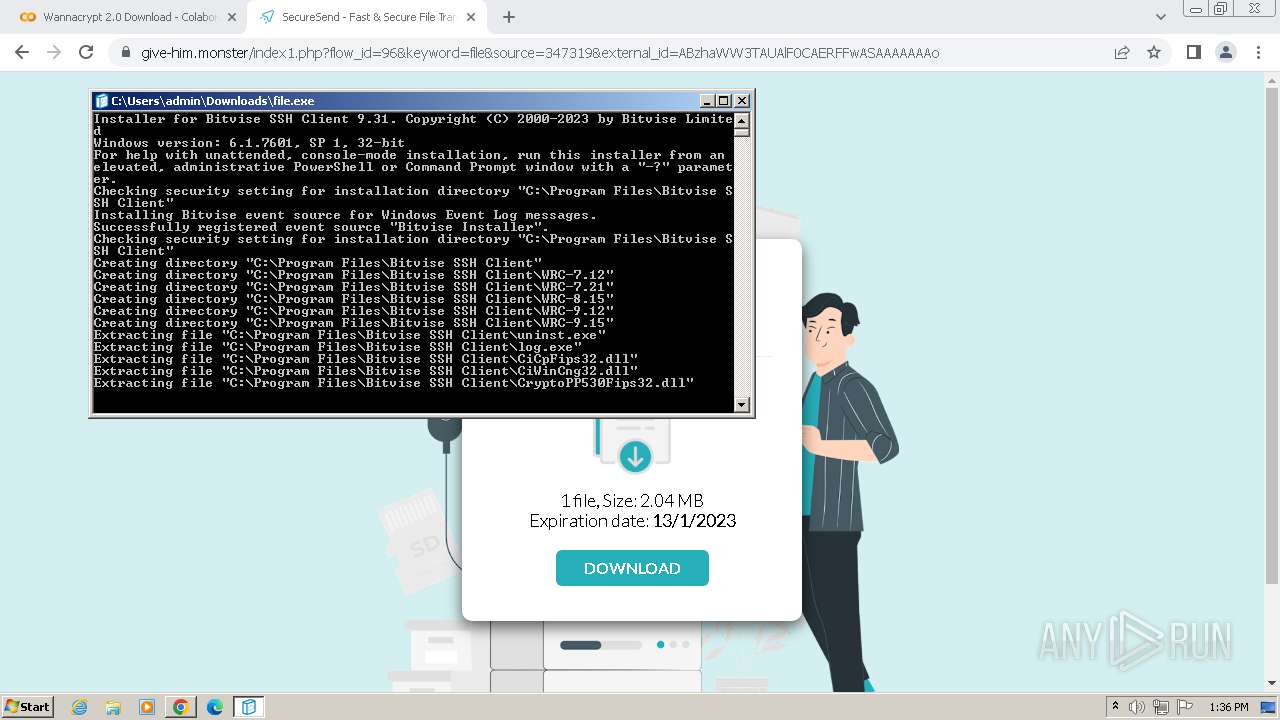
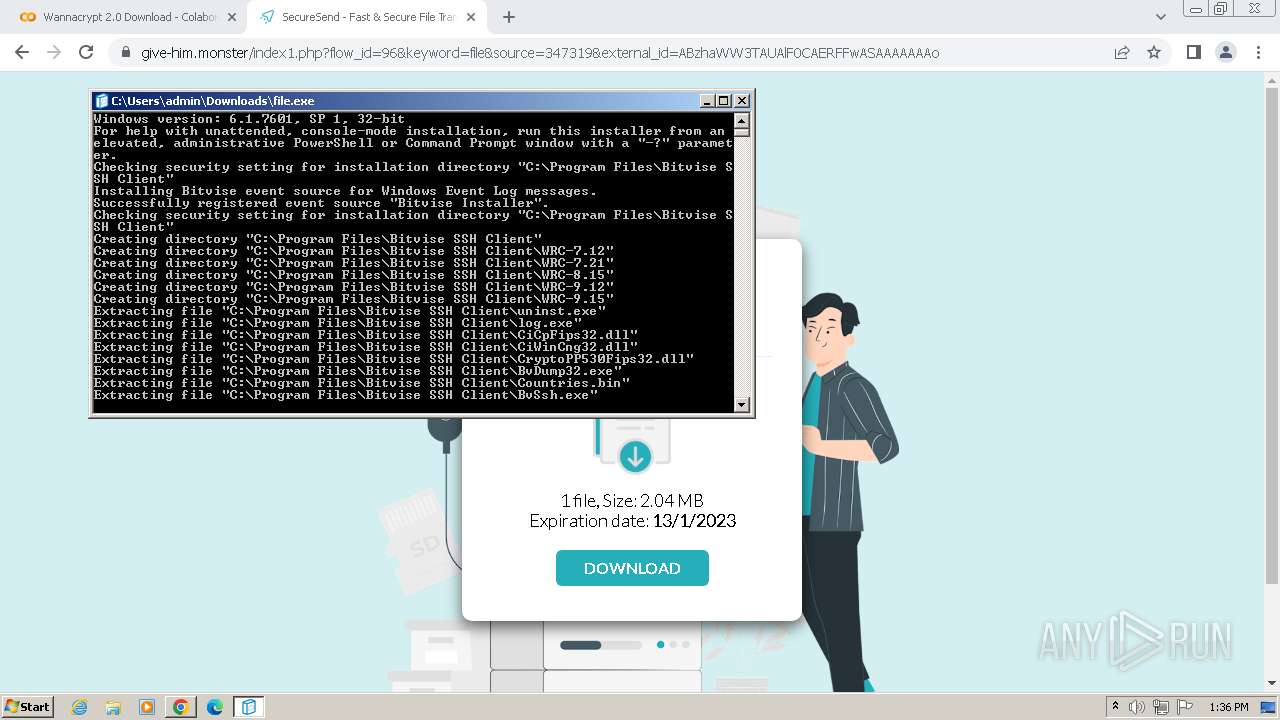
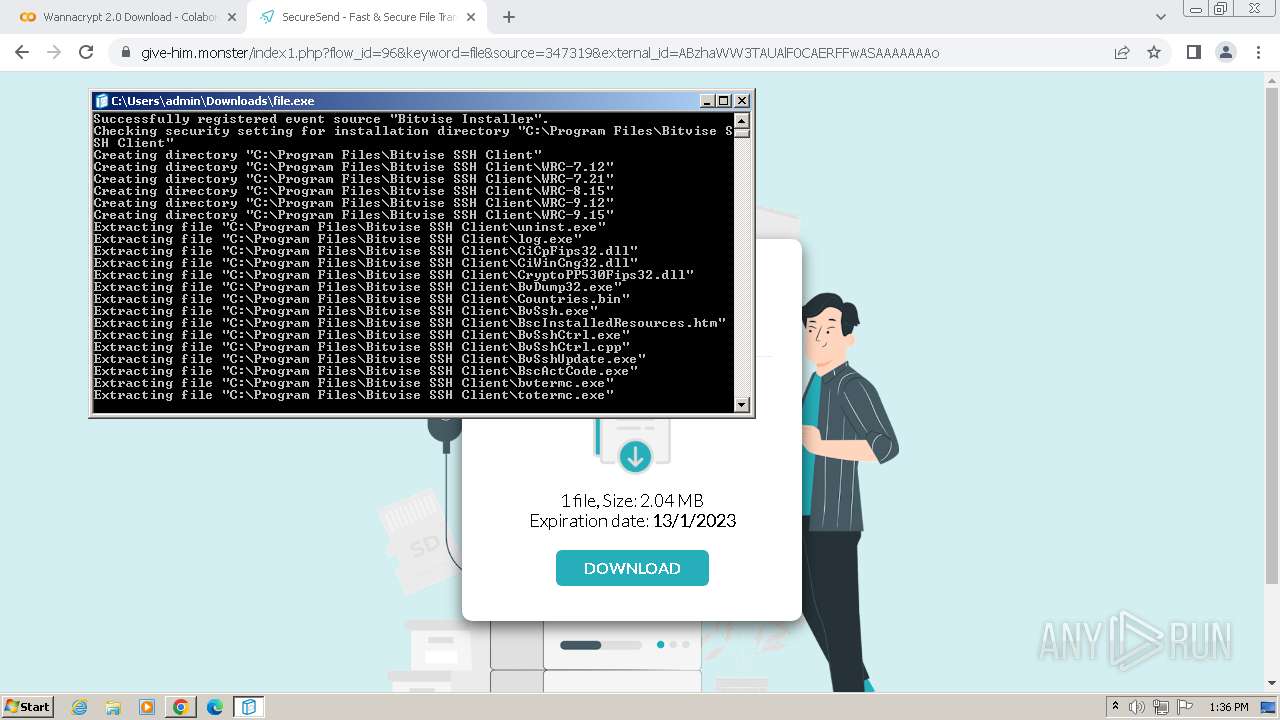
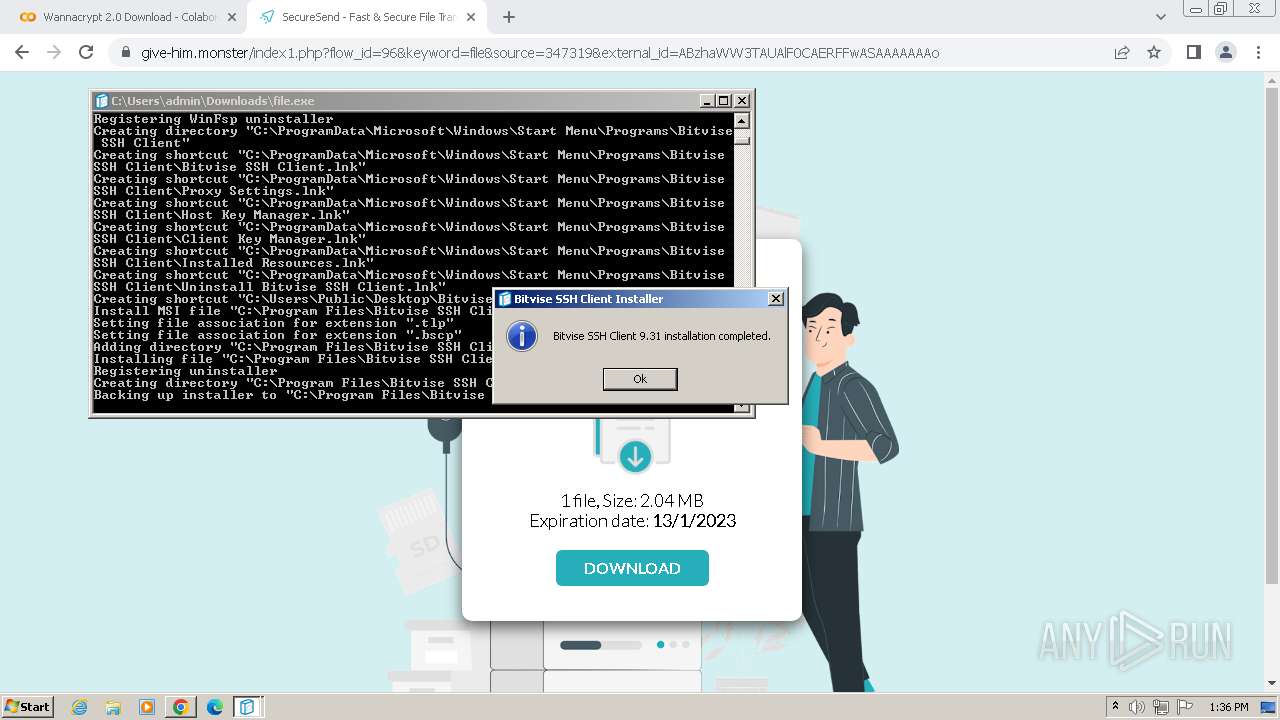
| 1656 | "C:\Users\admin\Downloads\file.exe" | C:\Users\admin\Downloads\file.exe | chrome.exe | ||||||||||||
User: admin Company: Bitvise Limited Integrity Level: HIGH Description: Bitvise SSH Client Installer Exit code: 0 Version: 9.31.0.0 Modules
| |||||||||||||||
| 1808 | "C:\Windows\system32\BvEventSource.exe" register | C:\Windows\System32\BvEventSource.exe | — | file.exe | |||||||||||
User: admin Company: Bitvise Limited Integrity Level: HIGH Description: Bitvise Log Event Source Utility Exit code: 0 Version: 1.02 Modules
| |||||||||||||||
Total events
19 523
Read events
19 318
Write events
194
Delete events
11
Modification events
| (PID) Process: | (888) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (888) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (888) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (888) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (888) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (888) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (888) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (888) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (888) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (888) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
72
Suspicious files
194
Text files
38
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 888 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF20830f.TMP | — | |
MD5:— | SHA256:— | |||
| 888 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 888 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF20830f.TMP | text | |
MD5:513218482935B0D388C0A990D868387A | SHA256:8E39CBAAF4AACC3A01AFA74EA8C30FB24FE69A22B8B30728AFB1614FD68809D9 | |||
| 888 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 888 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\optimization_guide_model_metadata_store\LOG.old~RF20983d.TMP | — | |
MD5:— | SHA256:— | |||
| 888 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\optimization_guide_model_metadata_store\LOG.old | — | |
MD5:— | SHA256:— | |||
| 888 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\optimization_guide_hint_cache_store\LOG.old~RF20983d.TMP | — | |
MD5:— | SHA256:— | |||
| 888 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\optimization_guide_hint_cache_store\LOG.old | — | |
MD5:— | SHA256:— | |||
| 888 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOG.old~RF20984c.TMP | — | |
MD5:— | SHA256:— | |||
| 888 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
74
DNS requests
109
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | — | — | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 5.40 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 9.82 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 17.2 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 9.84 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 28.0 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 13.1 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 118 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 235 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | binary | 58.3 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
868 | svchost.exe | 23.35.228.137:80 | — | AKAMAI-AS | DE | unknown |
888 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1996 | chrome.exe | 142.250.186.77:443 | accounts.google.com | GOOGLE | US | unknown |
1996 | chrome.exe | 142.250.74.206:443 | colab.research.google.com | GOOGLE | US | whitelisted |
888 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
1996 | chrome.exe | 172.217.18.4:443 | www.google.com | GOOGLE | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 184.30.20.134:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1996 | chrome.exe | 172.217.18.106:443 | optimizationguide-pa.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
colab.research.google.com |
| whitelisted |
www.google.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
optimizationguide-pa.googleapis.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1996 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |