| URL: | https://eur02.safelinks.protection.outlook.com/?url=http%3A%2F%2Faccaii.com%2Fksllive%2Fscript%3Fck1%3D1%26xno%3D87c030cc84643ec2%26tz%3D32400%26scr%3D1280.800.24%26inw%3D1143%26dpr%3D1%26ori%3D0%26tch%3D0%26geo%3D1%26nav%3DMozilla%252F5.0%2520(Windows%2520NT%252010.0%253B%2520Win64%253B%2520x64)%2520AppleWebKit%252F537.36%2520(KHTML%252C%2520like%2520Gecko)%2520Chrome%252F64.0.3282.186%2520Safari%252F537.36%26url%3Dbit.ly%252F3yJot1E%26ttl%3D%25E8%25BE%25BB%25E5%2585%2583%25E6%25B8%2585%25E7%25BE%258E%25E3%2581%25A8%25E9%2580%25A3%25E5%25B8%25AF%25E3%2583%25A6%25E3%2583%258B%25E3%2582%25AA%25E3%2583%25B3%25E3%2581%25AE%25E5%2590%258D%25E5%2589%258D%25E3%2581%258C%25E7%25B6%259A%25E3%2580%2585%25EF%25BC%2581%25E6%2597%25A5%25E6%259C%25AC%25E8%25B5%25A4%25E8%25BB%258D%25E6%2594%25AF%25E6%258F%25B4%25E5%258F%25A3%25E5%25BA%25A7%25E9%2596%258B%25E8%25A8%25AD%25E3%2581%25A7%25E9%2580%25AE%25E6%258D%2595%25E3%2581%2595%25E3%2582%258C%25E3%2581%259F%25E5%25AE%25B9%25E7%2596%2591%25E8%2580%2585%25E9%2587%2588%25E6%2594%25BE%25E3%2581%25A8%25E4%25B8%258D%25E8%25B5%25B7%25E8%25A8%25B4%25E3%2582%2592%25E6%25B1%2582%25E3%2582%2581%25E3%2582%258B%25E9%2581%258B%25E5%258B%2595%2520%257C%2520KSL-Live%2521%26mile%3D87c030cc84643ec2.5a9c32a1.5a9c32a1.cf9.1.3.2%26clk%3Dhttps%253A%252F%252F623A30B95F8E597.rincongamer.club%2F.Divine_Indicator%26lbl%3D%25E5%2587%25BA%25E5%2585%25B8%26now%3D1520189444672%26relay%3Don&data=05%7C02%7CAlMubarakS%40sharq.sabic.com%7C1284691cb9284e0b617508dda743ec63%7Ca77c517ce95e435bbbb4cb17e462491f%7C0%7C0%7C638850632348932859%7CUnknown%7CTWFpbGZsb3d8eyJFbXB0eU1hcGkiOnRydWUsIlYiOiIwLjAuMDAwMCIsIlAiOiJXaW4zMiIsIkFOIjoiTWFpbCIsIldUIjoyfQ%3D%3D%7C60000%7C%7C%7C&sdata=jCRUvOg70KbpJIgeCURQQI9DZ0tWDlHXwQoMOq4Y%2Bv4%3D&reserved=0 |
| Full analysis: | https://app.any.run/tasks/fba3b6f1-5d38-4282-8d47-081e467d539b |
| Verdict: | Malicious activity |
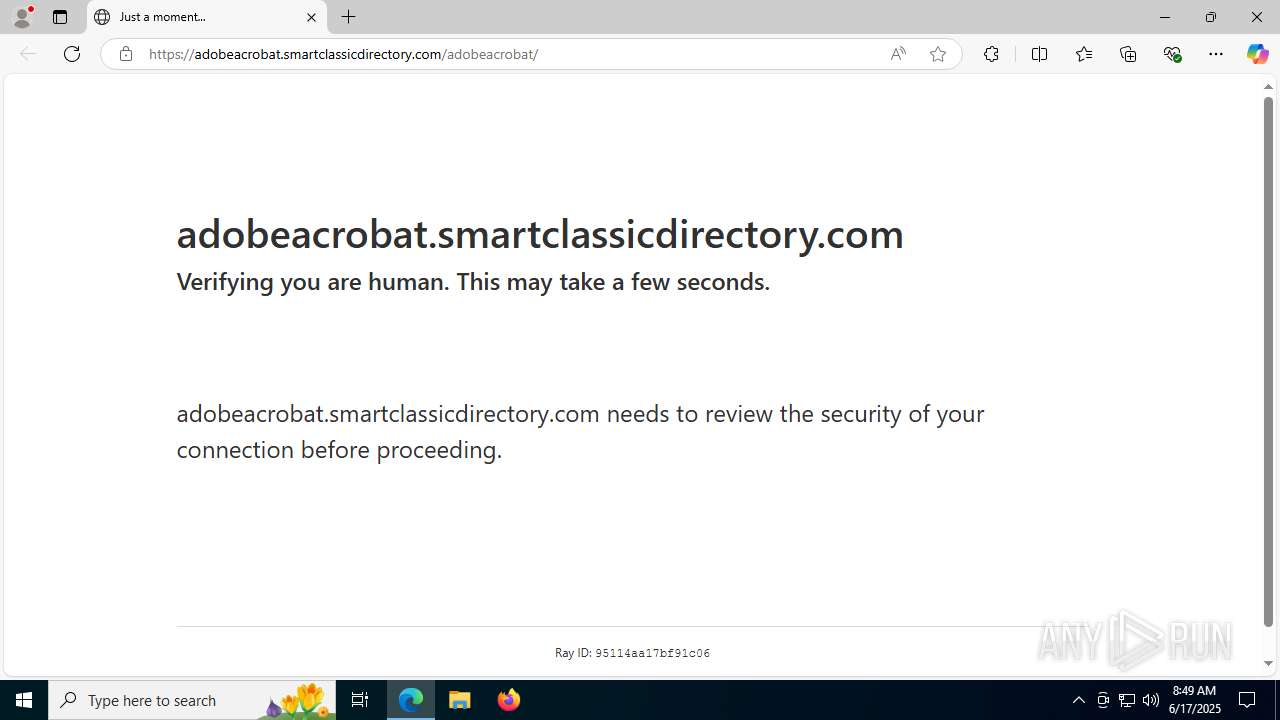
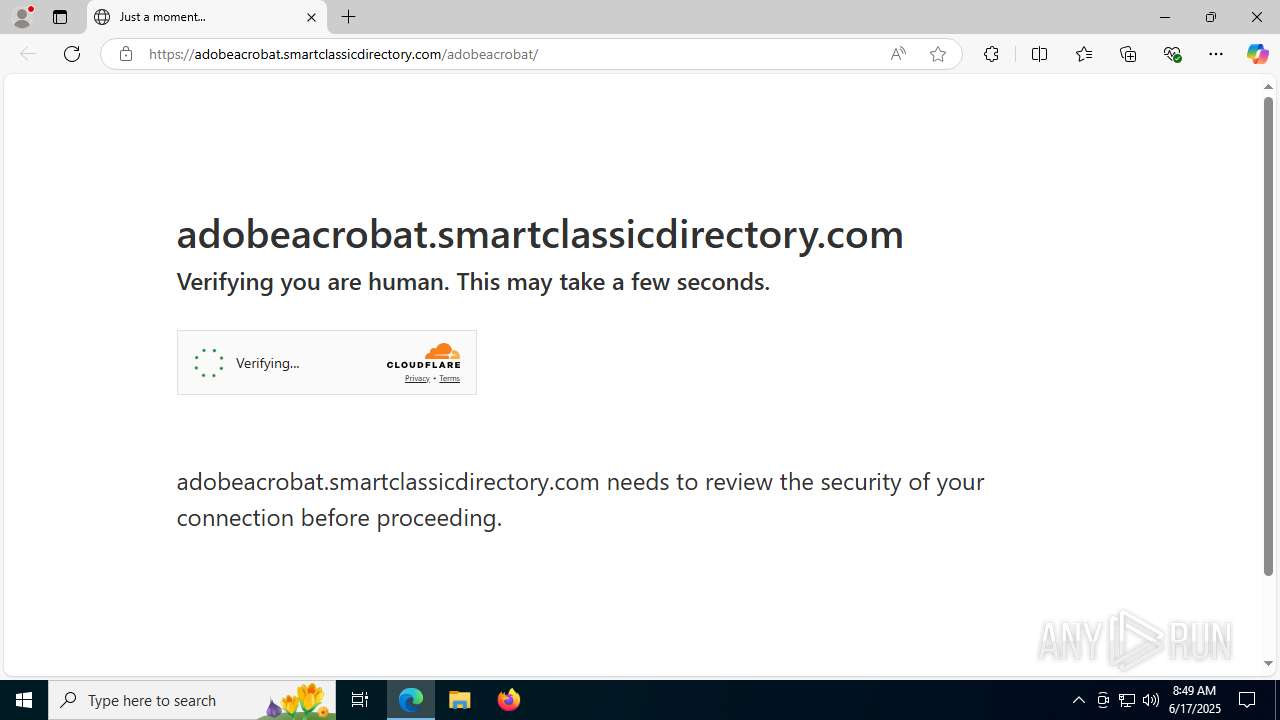
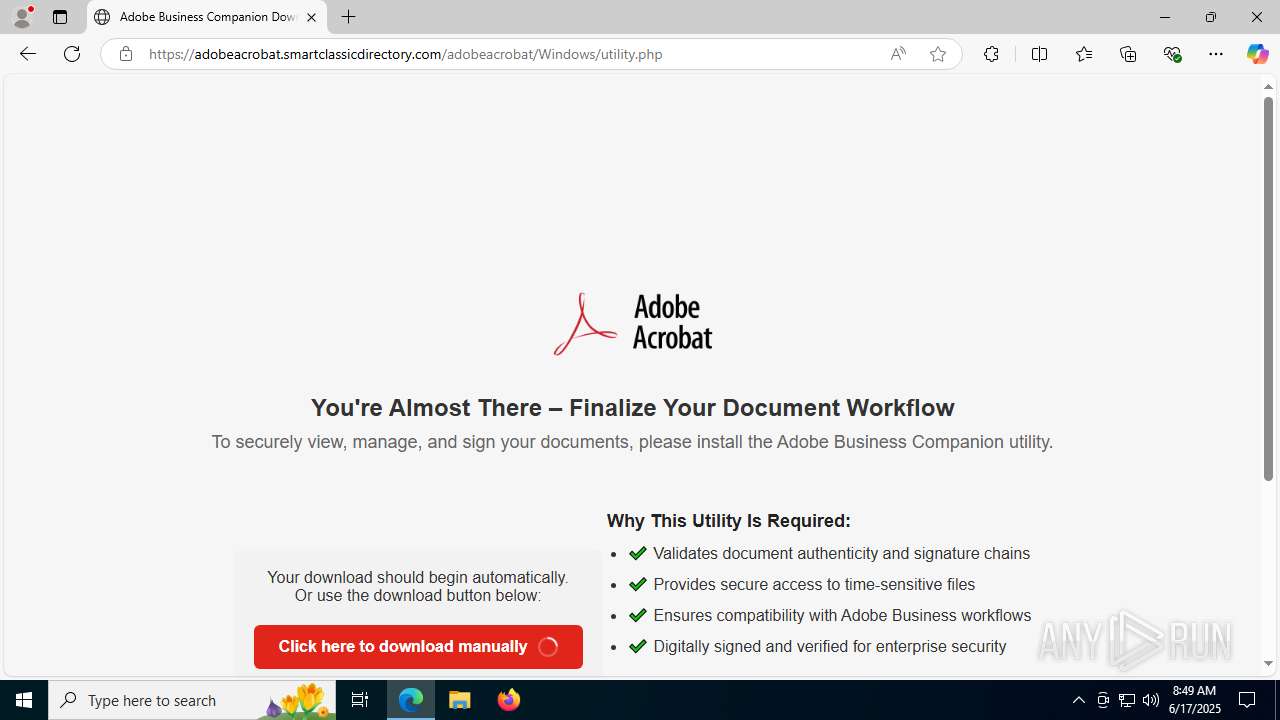
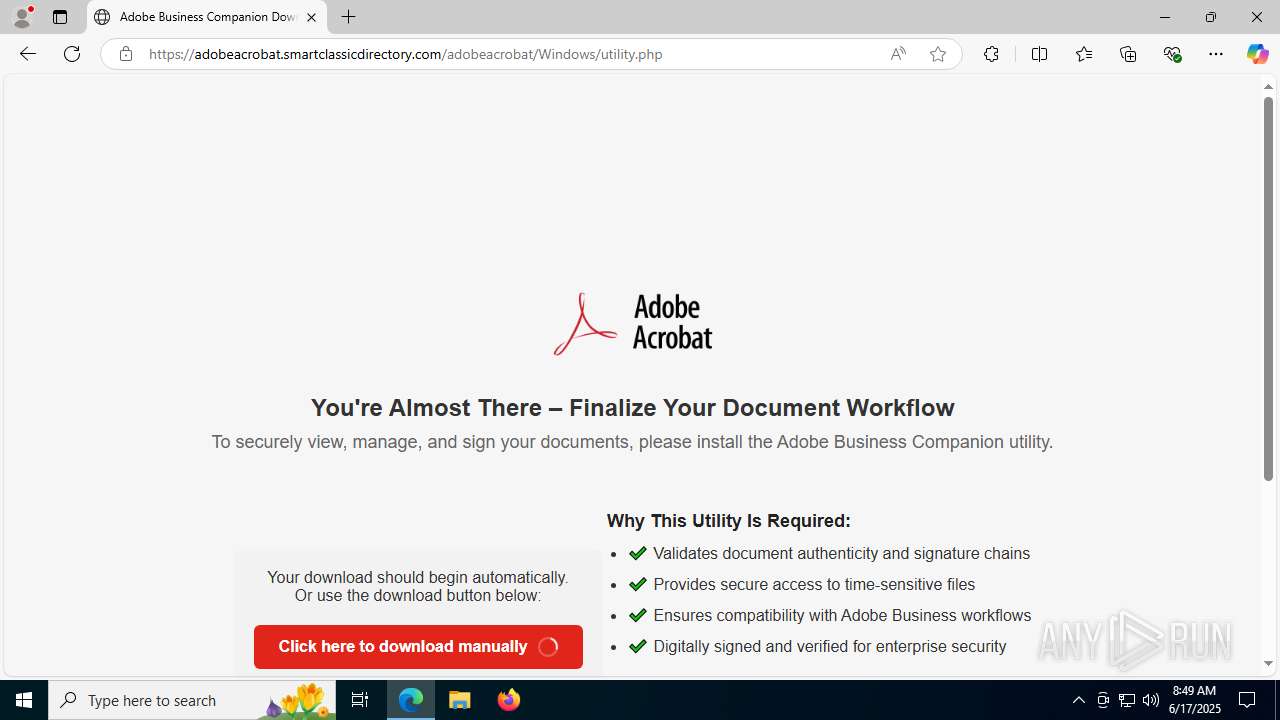
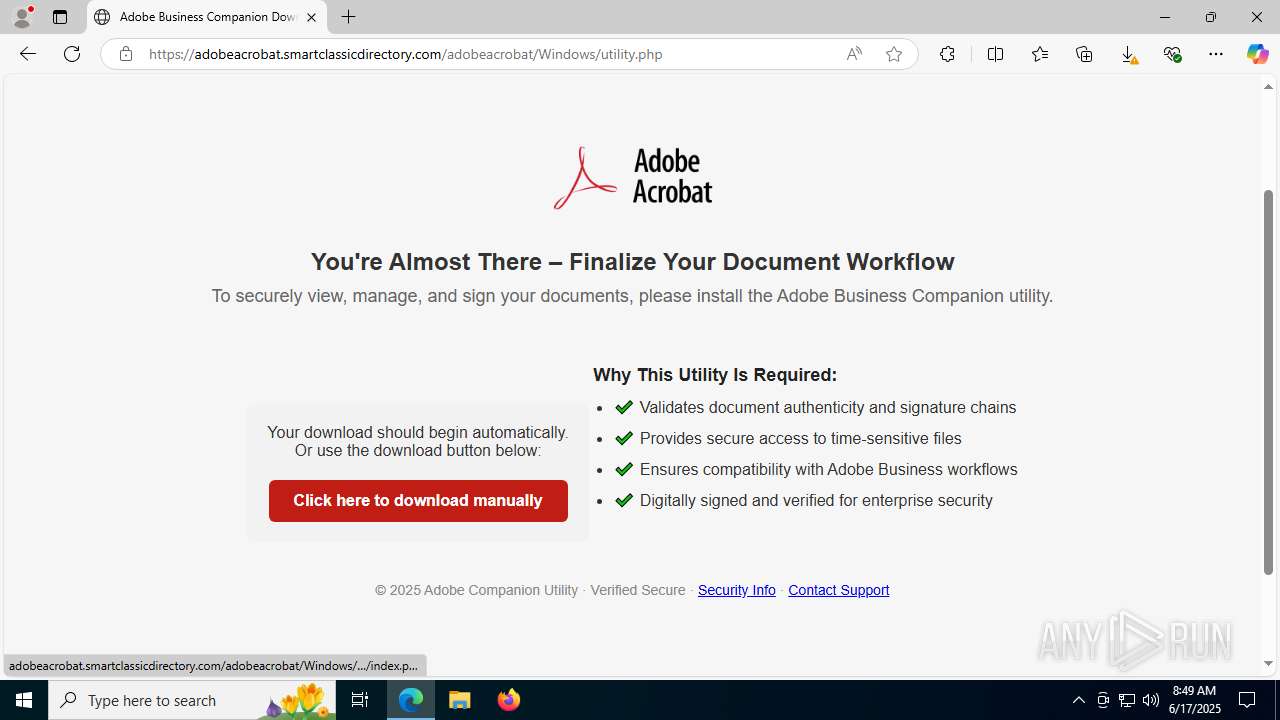
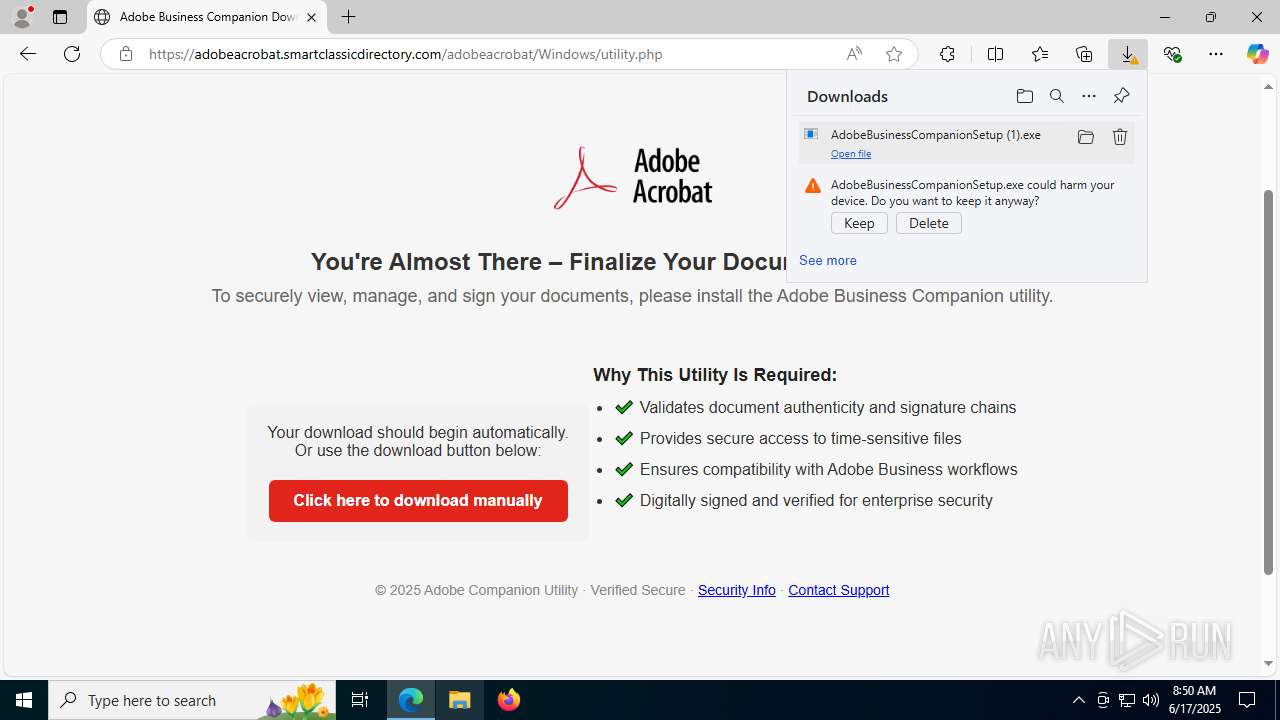
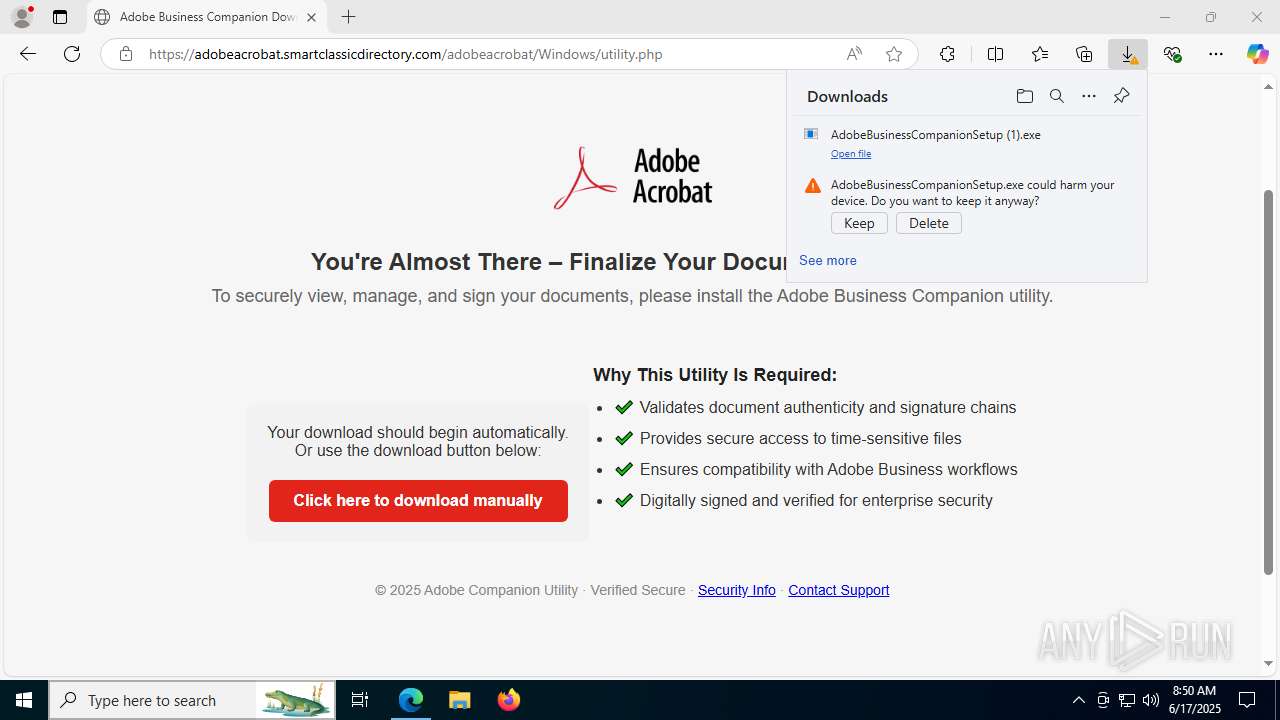
| Threats: | EvilProxy is a phishing-as-a-service (PhaaS) platform that enables cybercriminals to bypass multi-factor authentication (MFA) and hijack user sessions. It leverages reverse proxy techniques to harvest credentials and session cookies, posing a serious threat to both individuals and enterprises. |
| Analysis date: | June 17, 2025, 08:48:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B67CFD8810929772B4F9ABA231A4E6E5 |
| SHA1: | 7B3C0B8E205B11AA966A2488690DF4E11A65E64D |
| SHA256: | DF841482A1A96CC084B0F8D6E615C6F45020310640778F5AD46FFE3F6F751BCD |
| SSDEEP: | 24:2hhqYIbPPhSdUq7L7+CwoqK47uhgwsKrrWubGoCaigFcOS/X7/8feN1Sk1tx:aqYILsdU27aoqKhgPsWuCiTcOSAZknx |
MALICIOUS
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 6216)
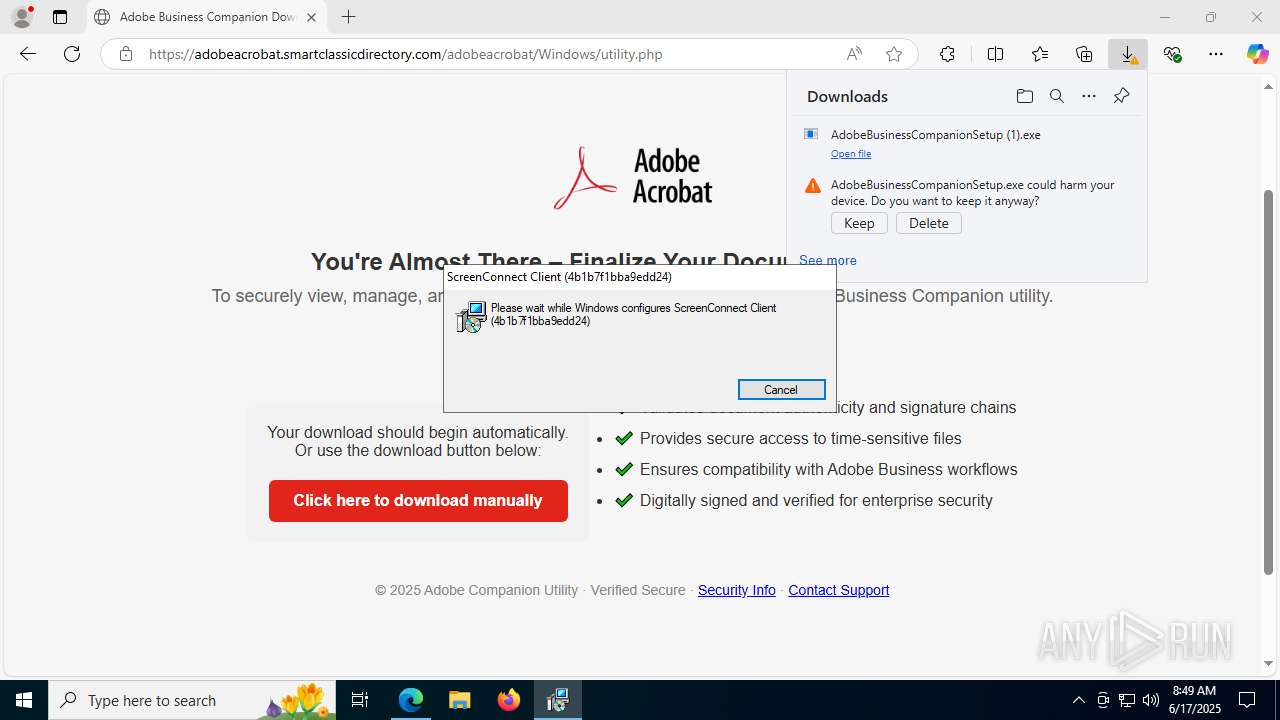
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.ClientService.exe (PID: 7704)
SUSPICIOUS
Reads security settings of Internet Explorer
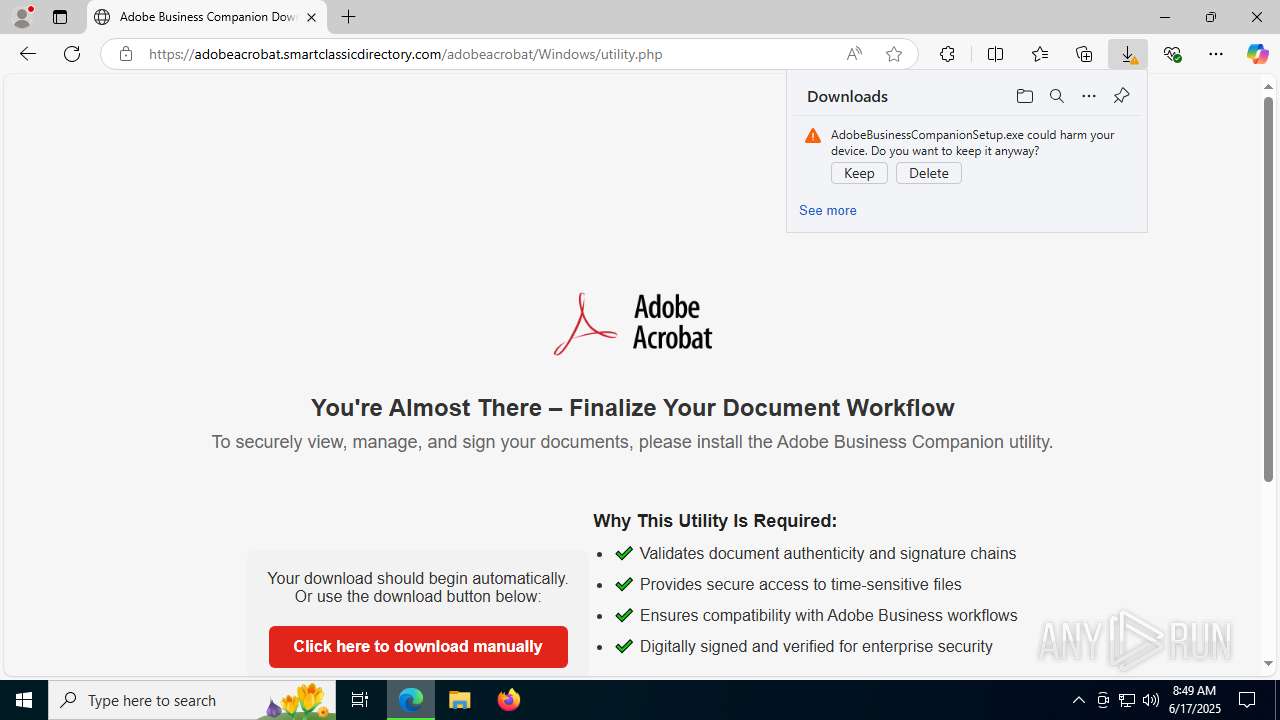
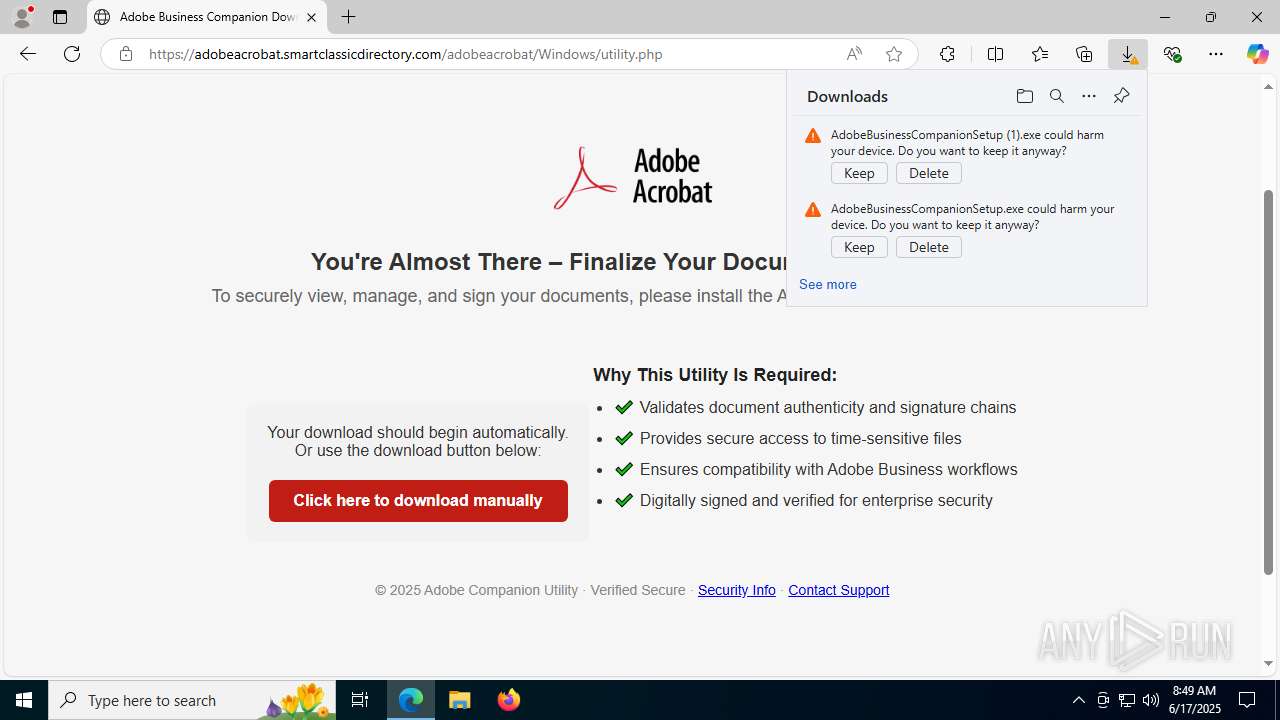
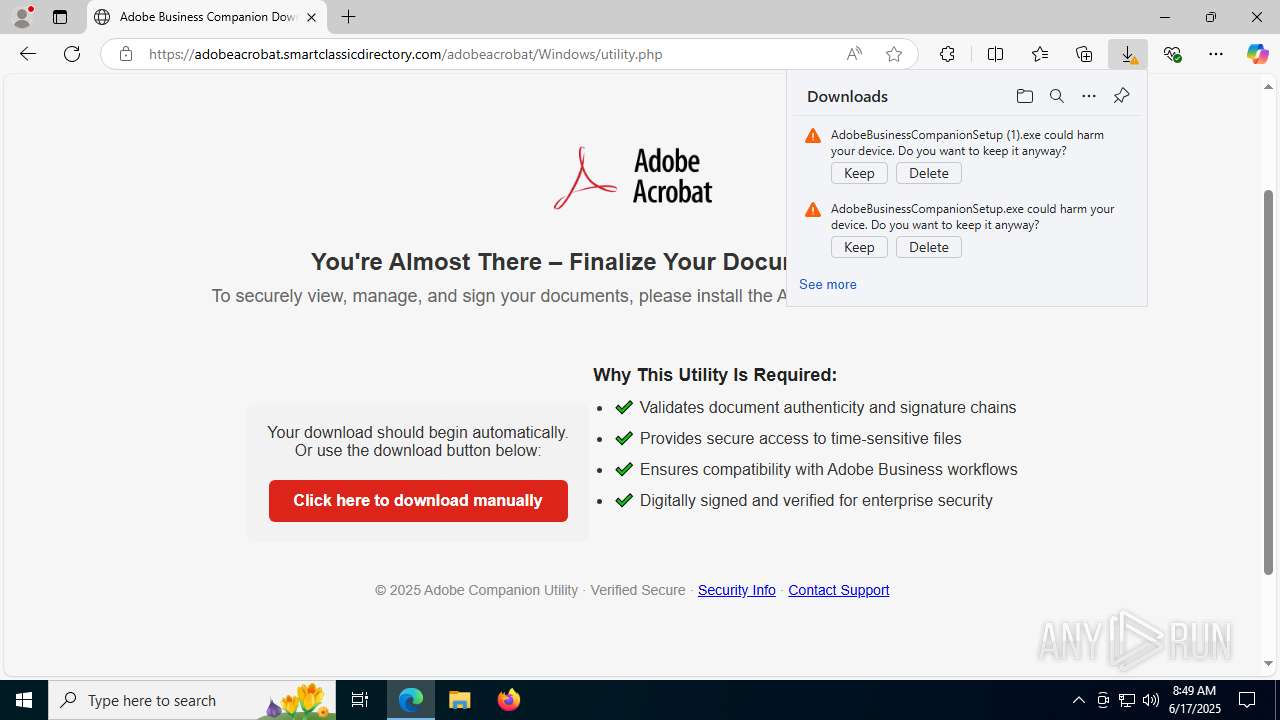
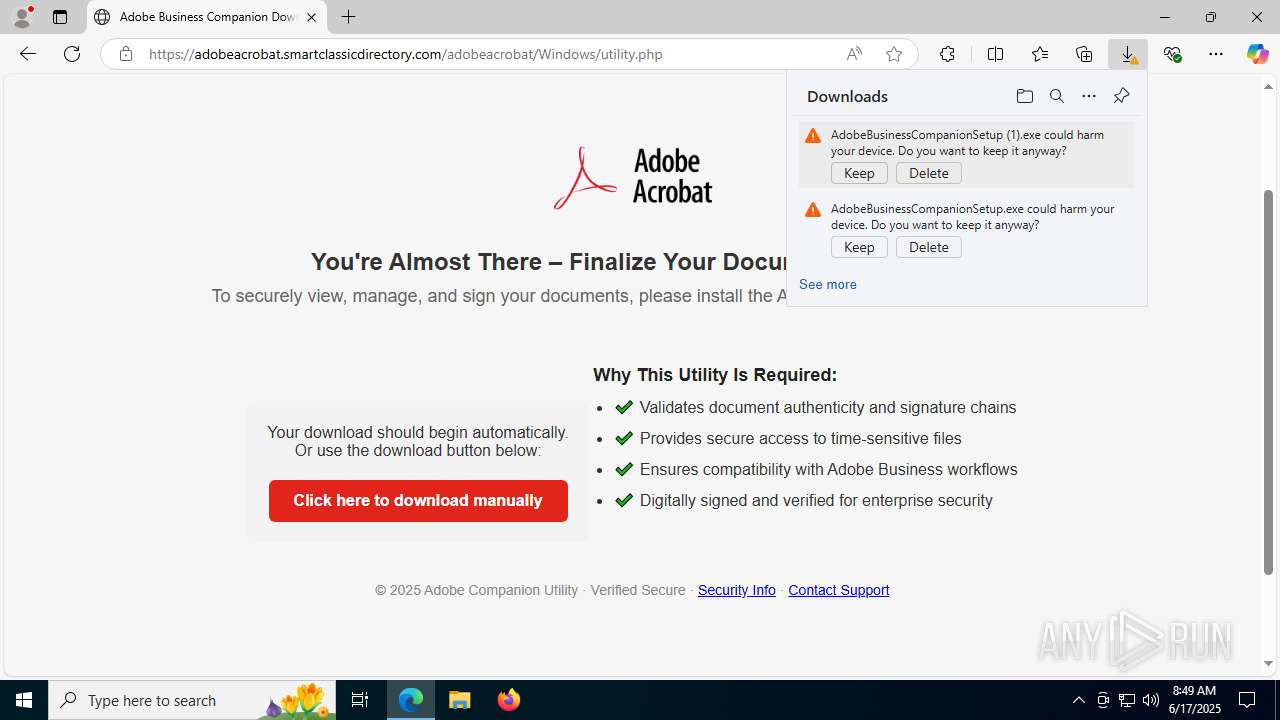
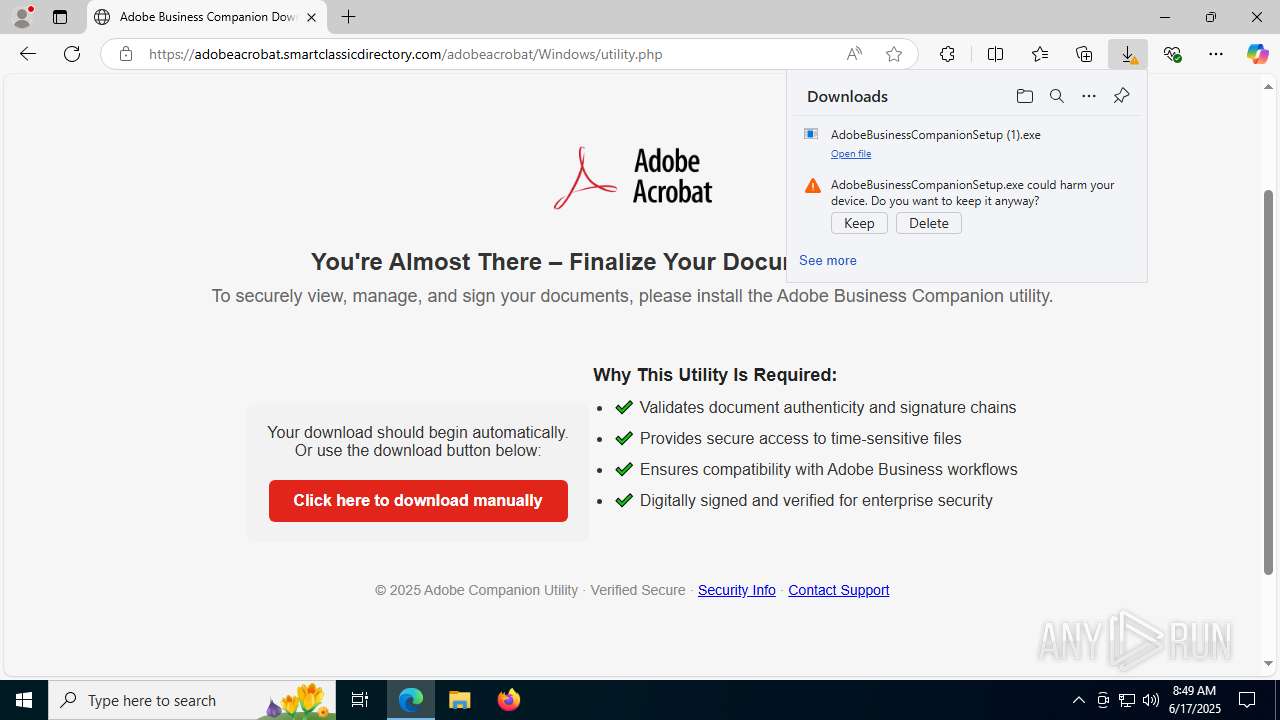
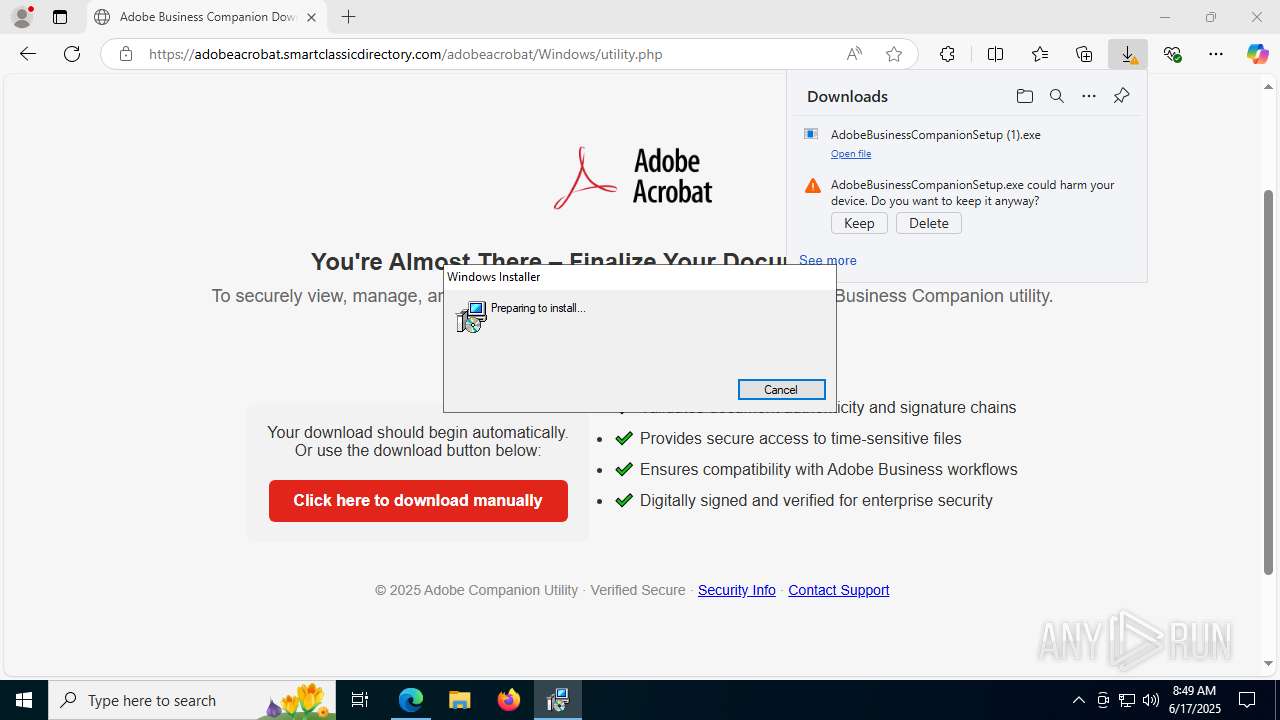
- AdobeBusinessCompanionSetup (1).exe (PID: 1488)
Executable content was dropped or overwritten
- rundll32.exe (PID: 8040)
Connects to unusual port
- ScreenConnect.ClientService.exe (PID: 7704)
Executes as Windows Service
- VSSVC.exe (PID: 3092)
- ScreenConnect.ClientService.exe (PID: 7704)
Screenconnect has been detected
- ScreenConnect.ClientService.exe (PID: 7704)
Potential Corporate Privacy Violation
- ScreenConnect.ClientService.exe (PID: 7704)
INFO
Application launched itself
- msedge.exe (PID: 4808)
Reads Environment values
- identity_helper.exe (PID: 8036)
Reads the computer name
- identity_helper.exe (PID: 8036)
- AdobeBusinessCompanionSetup (1).exe (PID: 1488)
- msiexec.exe (PID: 3048)
- msiexec.exe (PID: 4692)
Checks supported languages
- identity_helper.exe (PID: 8036)
- AdobeBusinessCompanionSetup (1).exe (PID: 1488)
- msiexec.exe (PID: 3048)
- msiexec.exe (PID: 4692)
Executable content was dropped or overwritten
- msedge.exe (PID: 6216)
- msedge.exe (PID: 4808)
- msiexec.exe (PID: 5708)
- msiexec.exe (PID: 3048)
Launching a file from the Downloads directory
- msedge.exe (PID: 4808)
Create files in a temporary directory
- AdobeBusinessCompanionSetup (1).exe (PID: 1488)
- rundll32.exe (PID: 8040)
Reads the machine GUID from the registry
- AdobeBusinessCompanionSetup (1).exe (PID: 1488)
Process checks computer location settings
- AdobeBusinessCompanionSetup (1).exe (PID: 1488)
CONNECTWISE has been detected
- msiexec.exe (PID: 5708)
Manages system restore points
- SrTasks.exe (PID: 7600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
191
Monitored processes
48
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1488 | "C:\Users\admin\Downloads\AdobeBusinessCompanionSetup (1).exe" | C:\Users\admin\Downloads\AdobeBusinessCompanionSetup (1).exe | msedge.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1488 | "C:\Program Files (x86)\ScreenConnect Client (4b1b7f1bba9edd24)\ScreenConnect.WindowsClient.exe" "RunRole" "86fa1ea0-bedc-466f-a3c3-260c35320ab5" "System" | C:\Program Files (x86)\ScreenConnect Client (4b1b7f1bba9edd24)\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: SYSTEM Company: ScreenConnect Software Integrity Level: SYSTEM Description: ScreenConnect Client Exit code: 0 Version: 25.2.4.9229 Modules
| |||||||||||||||
| 1896 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x304,0x308,0x30c,0x2fc,0x314,0x7ffc43a7f208,0x7ffc43a7f214,0x7ffc43a7f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2628 | "C:\Program Files (x86)\ScreenConnect Client (4b1b7f1bba9edd24)\ScreenConnect.WindowsClient.exe" "RunRole" "0ef0830f-1238-4c64-9166-834e4027c4bb" "User" | C:\Program Files (x86)\ScreenConnect Client (4b1b7f1bba9edd24)\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Version: 25.2.4.9229 Modules
| |||||||||||||||
| 3048 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3052 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4984,i,17403900610844337424,12537741843031366762,262144 --variations-seed-version --mojo-platform-channel-handle=1488 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3092 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3760 | C:\Windows\syswow64\MsiExec.exe -Embedding 0298537E8F5F2B48690BBA52A100B314 E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3980 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2016,i,17403900610844337424,12537741843031366762,262144 --variations-seed-version --mojo-platform-channel-handle=2280 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 4036 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4276,i,17403900610844337424,12537741843031366762,262144 --variations-seed-version --mojo-platform-channel-handle=4300 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
11 282
Read events
10 979
Write events
286
Delete events
17
Modification events
| (PID) Process: | (4808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4808) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 1DBDDEDD56962F00 | |||
| (PID) Process: | (4808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\394036 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3D044BD0-92F2-4BA1-9102-12868C8483D5} | |||
| (PID) Process: | (4808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\394036 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {96C6047D-9CF1-4D75-8051-3AC37993421F} | |||
| (PID) Process: | (4808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\394036 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {30EE98C1-6BC7-49D5-8557-9EBF4CB058B8} | |||
| (PID) Process: | (4808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\394036 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {52B38AB4-DBD8-4308-890E-2655C9E4EED6} | |||
| (PID) Process: | (4808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\394036 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {2A3F7B69-7830-47D8-A62B-58AE61611179} | |||
Executable files
27
Suspicious files
83
Text files
51
Unknown types
37
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF176939.TMP | — | |
MD5:— | SHA256:— | |||
| 4808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF176939.TMP | — | |
MD5:— | SHA256:— | |||
| 4808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF176939.TMP | — | |
MD5:— | SHA256:— | |||
| 4808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF176939.TMP | — | |
MD5:— | SHA256:— | |||
| 4808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF176949.TMP | — | |
MD5:— | SHA256:— | |||
| 4808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF176958.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
96
DNS requests
80
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6216 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:X4Zp8ROU76Z0-3wVzAKUjvv2Z8JJUnRBwUr_P-V7FZs&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
6356 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6356 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6220 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750171598&P2=404&P3=2&P4=H9wFktSfCeDzDjgmker%2bftBeg0YUH76eW4SWLDTp1yC9EnabB3Df9iV18UM3uW2qf4q0CsYV4TctmCu2HYZMhA%3d%3d | unknown | — | — | whitelisted |
1380 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6220 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750171598&P2=404&P3=2&P4=H9wFktSfCeDzDjgmker%2bftBeg0YUH76eW4SWLDTp1yC9EnabB3Df9iV18UM3uW2qf4q0CsYV4TctmCu2HYZMhA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6216 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
eur02.safelinks.protection.outlook.com |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
accaii.com |
| unknown |
623a30b95f8e597.rincongamer.club |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6216 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Evilproxy Phishing domain by CrossDomain ( .smartclassicdirectory .com) |
6216 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Evilproxy Phishing domain by CrossDomain ( .smartclassicdirectory .com) |
6216 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6216 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6216 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Evilproxy Phishing domain by CrossDomain ( .smartclassicdirectory .com) |
6216 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Evilproxy Phishing domain by CrossDomain ( .smartclassicdirectory .com) |
6216 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
6216 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
7704 | ScreenConnect.ClientService.exe | Potential Corporate Privacy Violation | REMOTE [ANY.RUN] ScreenConnect Server Response |
6216 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |