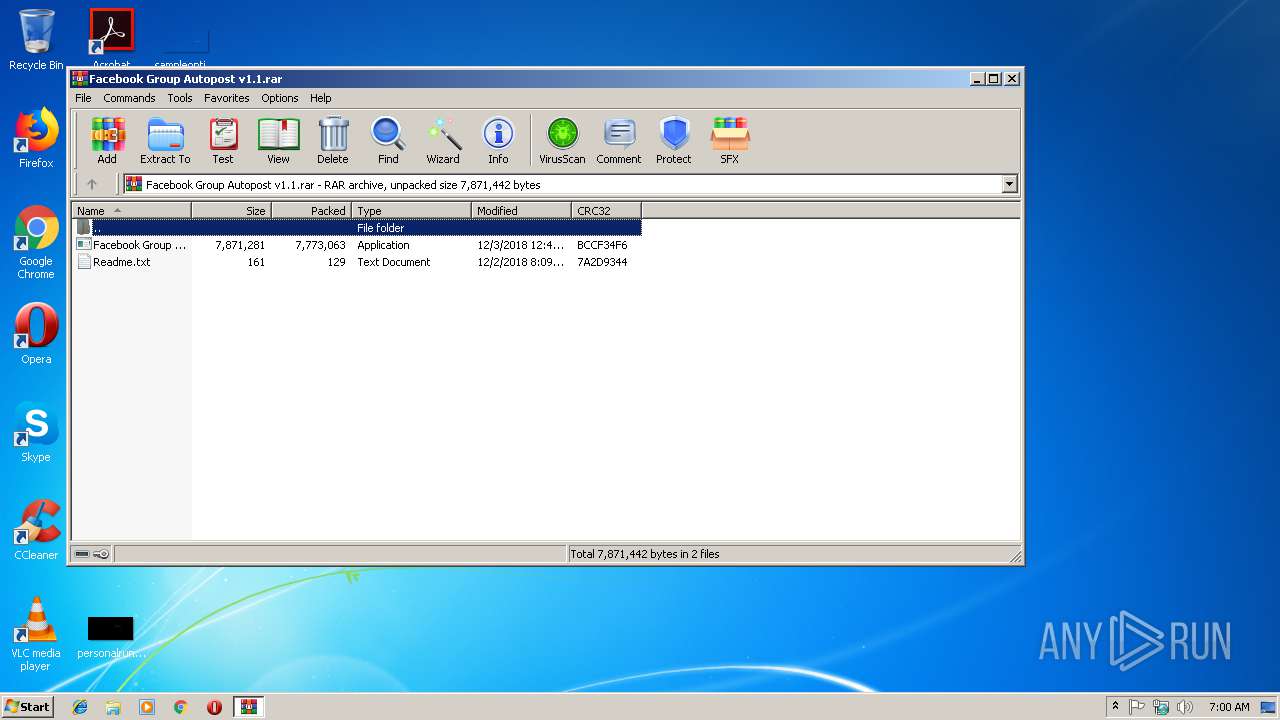
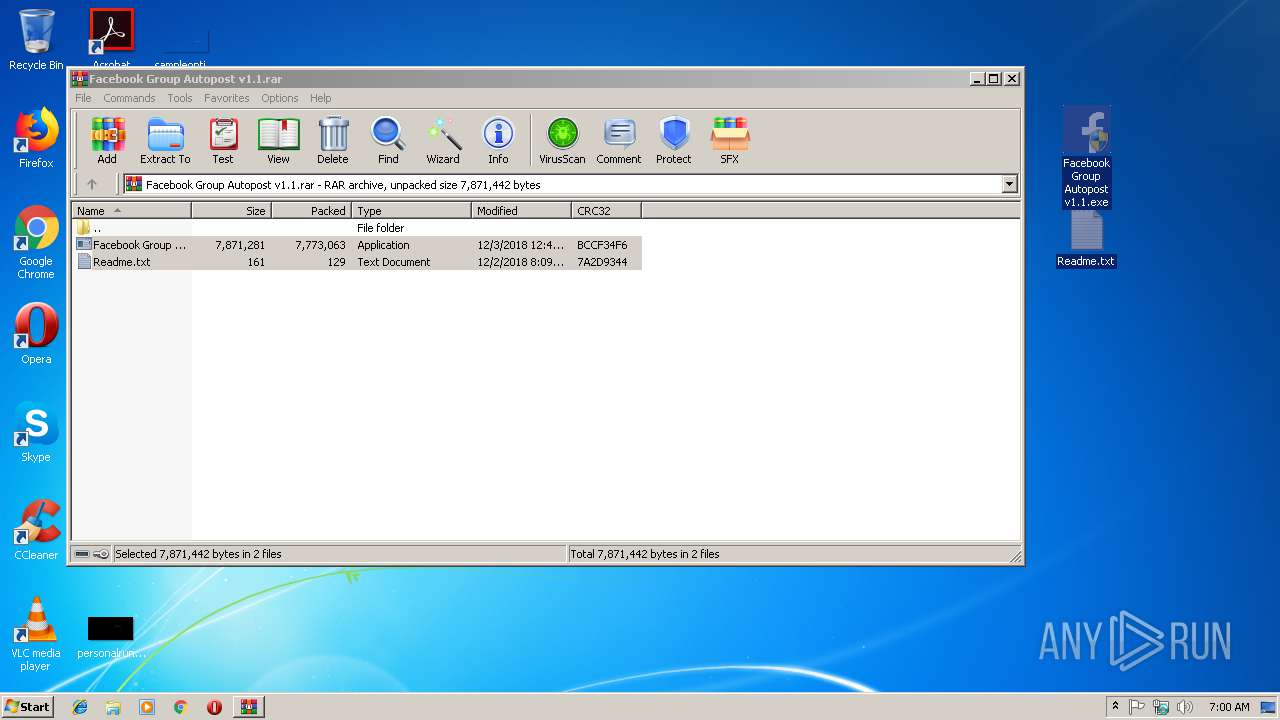
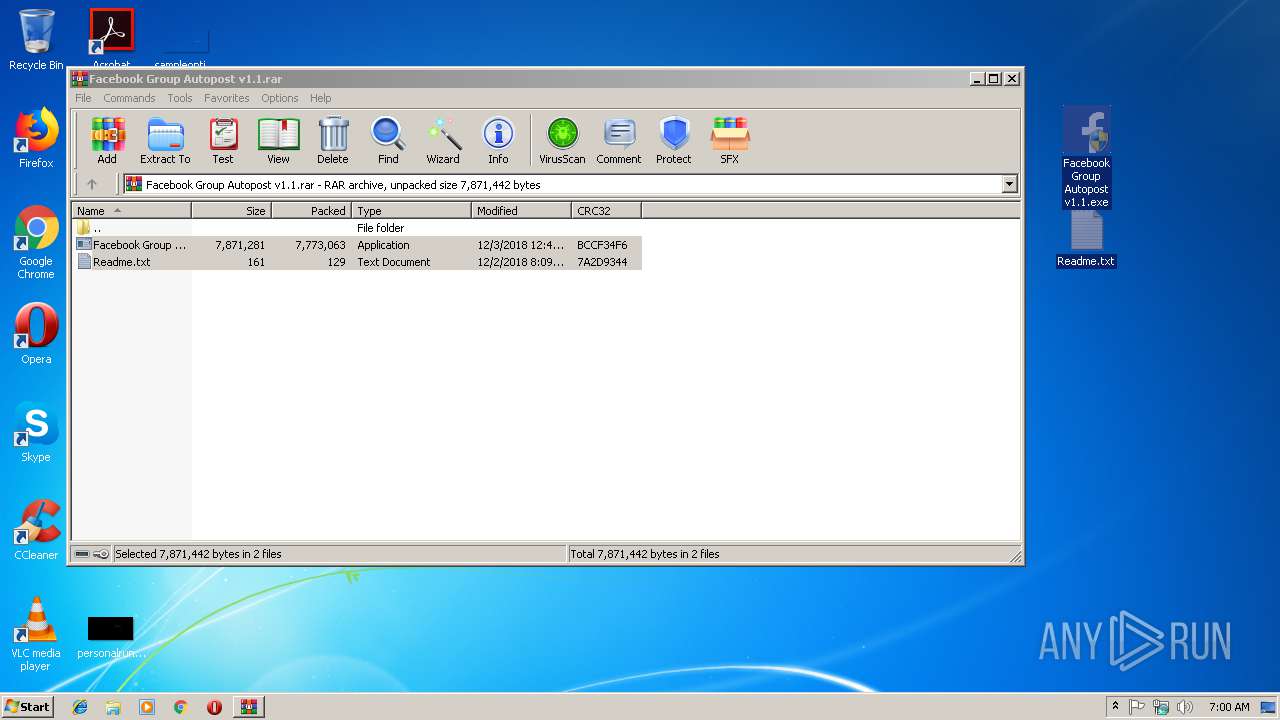
| File name: | Facebook Group Autopost v1.1.rar |
| Full analysis: | https://app.any.run/tasks/e7bdab26-bebc-4176-9275-138778fdda4f |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | December 06, 2018, 07:00:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 9BB097AE7D83BEBE8CD745B357C23E36 |
| SHA1: | AD1AB5272D33765CB9E5B936F4B49DD9A3093764 |
| SHA256: | DF6A1E642512DDB0693B138E3F12F25EFC61EED55502F4F22BDBF3F4AED50639 |
| SSDEEP: | 196608:1gy23DDZEM1TdSJLo+ASFtkPu1wCHfIBwDqQtNR03sxRbJHy:ey23DRdH+wurHww9b379Hy |
MALICIOUS
Changes the autorun value in the registry
- bohemian.exe (PID: 2980)
- data.exe (PID: 1660)
Application was dropped or rewritten from another process
- Facebook Group Autopost v1.1.exe (PID: 2548)
- bohemian.sfx.exe (PID: 3800)
- data.exe (PID: 1660)
- ILCADXLAX.exe (PID: 3832)
- n.exe (PID: 2788)
- L.exe (PID: 2976)
- nj.exe (PID: 3324)
- LL.exe (PID: 2352)
- Facebook Group Autopost v1.1.exe (PID: 3872)
- bohemian.exe (PID: 2980)
- service.exe (PID: 3616)
Uses Task Scheduler to run other applications
- bohemian.exe (PID: 2980)
- L.exe (PID: 2976)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3068)
- schtasks.exe (PID: 3204)
- schtasks.exe (PID: 4092)
MINER was detected
- ILCADXLAX.exe (PID: 3832)
Connects to CnC server
- ILCADXLAX.exe (PID: 3832)
NJRAT was detected
- data.exe (PID: 1660)
Writes to a start menu file
- data.exe (PID: 1660)
SUSPICIOUS
Executable content was dropped or overwritten
- bohemian.sfx.exe (PID: 3800)
- Facebook Group Autopost v1.1.exe (PID: 2548)
- WinRAR.exe (PID: 3280)
- bohemian.exe (PID: 2980)
- nj.exe (PID: 3324)
- L.exe (PID: 2976)
- data.exe (PID: 1660)
Creates files in the user directory
- nj.exe (PID: 3324)
- L.exe (PID: 2976)
- data.exe (PID: 1660)
Starts itself from another location
- nj.exe (PID: 3324)
- L.exe (PID: 2976)
Uses NETSH.EXE for network configuration
- data.exe (PID: 1660)
Connects to unusual port
- ILCADXLAX.exe (PID: 3832)
- data.exe (PID: 1660)
INFO
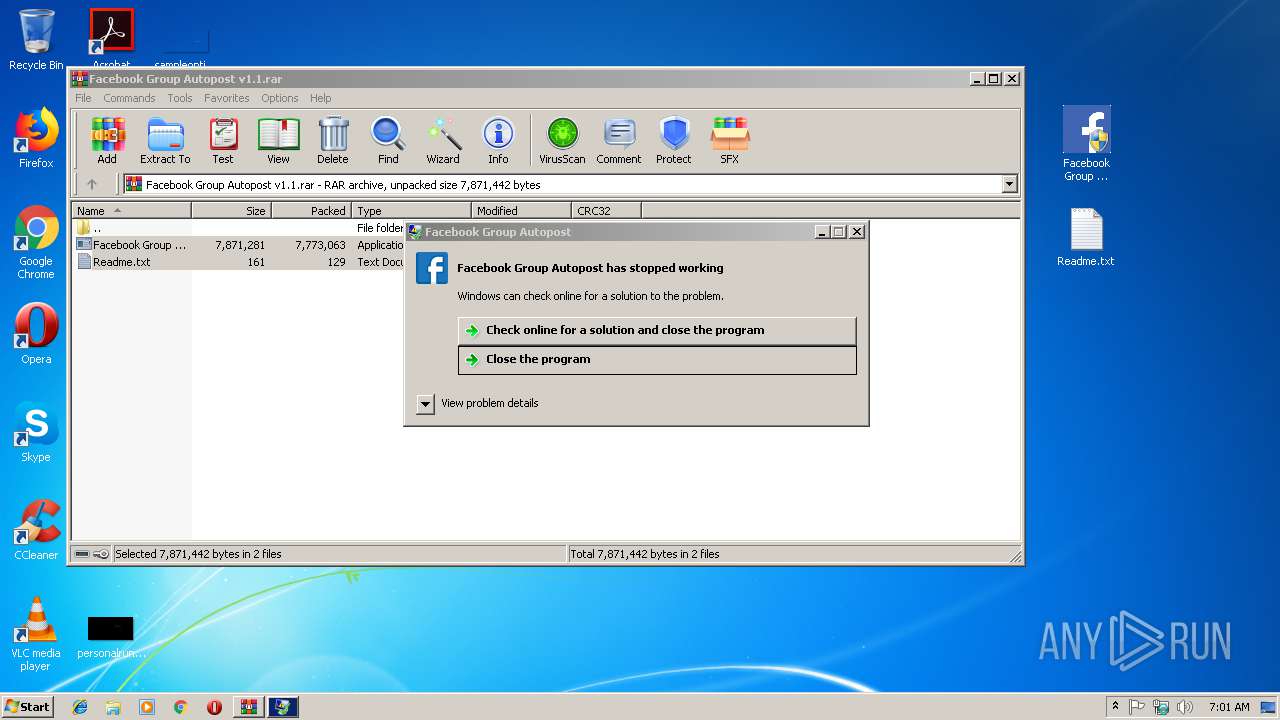
Application was crashed
- Facebook Group Autopost v1.1.exe (PID: 3872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
57
Monitored processes
16
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1660 | "C:\Users\admin\AppData\Roaming\data.exe" | C:\Users\admin\AppData\Roaming\data.exe | nj.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Winx Exit code: 0 Version: 1.3.1.1 Modules
| |||||||||||||||
| 2352 | "C:\Users\admin\AppData\Local\Temp\LL.exe" | C:\Users\admin\AppData\Local\Temp\LL.exe | — | Facebook Group Autopost v1.1.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Winx Exit code: 0 Version: 1.3.1.1 Modules
| |||||||||||||||
| 2548 | "C:\Users\admin\Desktop\Facebook Group Autopost v1.1.exe" | C:\Users\admin\Desktop\Facebook Group Autopost v1.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2788 | "C:\Users\admin\AppData\Local\Temp\n.exe" | C:\Users\admin\AppData\Local\Temp\n.exe | — | Facebook Group Autopost v1.1.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Vis Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2976 | "C:\Users\admin\AppData\Local\Temp\L.exe" | C:\Users\admin\AppData\Local\Temp\L.exe | Facebook Group Autopost v1.1.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Vis Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2980 | "C:\Users\admin\AppData\Local\Temp\bohemian.exe" | C:\Users\admin\AppData\Local\Temp\bohemian.exe | bohemian.sfx.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3068 | schtasks.exe /create /tn VFFWUNWSNPLW /tr C:\Users\admin\AppData\Local\XGCQDOKWGZNZKZR\SystemProcess.exe /sc minute /mo 1 | C:\Windows\system32\schtasks.exe | — | bohemian.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3204 | schtasks.exe /create /tn VFFWUNWSNPLW /tr C:\Users\admin\AppData\Local\XGCQDOKWGZNZKZR\SystemProcess.exe /sc onidle /i 1 | C:\Windows\system32\schtasks.exe | — | bohemian.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3280 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Facebook Group Autopost v1.1.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3324 | "C:\Users\admin\AppData\Local\Temp\nj.exe" | C:\Users\admin\AppData\Local\Temp\nj.exe | Facebook Group Autopost v1.1.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Winx Exit code: 0 Version: 1.3.1.1 Modules
| |||||||||||||||
Total events
2 128
Read events
2 010
Write events
118
Delete events
0
Modification events
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Facebook Group Autopost v1.1.rar | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2548) Facebook Group Autopost v1.1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2548) Facebook Group Autopost v1.1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
13
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2548 | Facebook Group Autopost v1.1.exe | C:\Users\admin\AppData\Local\Temp\L.exe | executable | |
MD5:— | SHA256:— | |||
| 2548 | Facebook Group Autopost v1.1.exe | C:\Users\admin\AppData\Local\Temp\bohemian.sfx.exe | executable | |
MD5:— | SHA256:— | |||
| 3280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3280.15466\Facebook Group Autopost v1.1.exe | executable | |
MD5:— | SHA256:— | |||
| 3280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3280.15466\Readme.txt | text | |
MD5:— | SHA256:— | |||
| 2548 | Facebook Group Autopost v1.1.exe | C:\Users\admin\AppData\Local\Temp\LL.exe | executable | |
MD5:— | SHA256:— | |||
| 2976 | L.exe | C:\Users\admin\AppData\Roaming\System32\service.exe | executable | |
MD5:— | SHA256:— | |||
| 1660 | data.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\da3434d6f617c5d897806b653bcb0ded.exe | executable | |
MD5:— | SHA256:— | |||
| 2548 | Facebook Group Autopost v1.1.exe | C:\Users\admin\AppData\Local\Temp\n.exe | executable | |
MD5:— | SHA256:— | |||
| 2548 | Facebook Group Autopost v1.1.exe | C:\Users\admin\AppData\Local\Temp\nj.exe | executable | |
MD5:— | SHA256:— | |||
| 2548 | Facebook Group Autopost v1.1.exe | C:\Users\admin\AppData\Local\Temp\Facebook Group Autopost v1.1.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
2
Threats
6
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3832 | ILCADXLAX.exe | 80.188.53.27:5555 | xmr.bohemianpool.com | O2 Czech Republic, a.s. | CZ | suspicious |
1660 | data.exe | 79.159.172.236:5553 | redlocal.hopto.org | Telefonica De Espana | ES | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
xmr.bohemianpool.com |
| suspicious |
redlocal.hopto.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3832 | ILCADXLAX.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
3832 | ILCADXLAX.exe | Misc activity | MINER [PTsecurity] CoinMiner CryptoNight XMRig JSON_RPC Client Login |
3832 | ILCADXLAX.exe | Misc activity | MINER [PTsecurity] Riskware/CoinMiner JSON_RPC Response |
3832 | ILCADXLAX.exe | Misc activity | MINER [PTsecurity] Risktool.W32.coinminer!c |
3832 | ILCADXLAX.exe | Misc activity | MINER [PTsecurity] Riskware/CoinMiner JSON_RPC Response |
3832 | ILCADXLAX.exe | Misc activity | MINER [PTsecurity] Risktool.W32.coinminer!c |