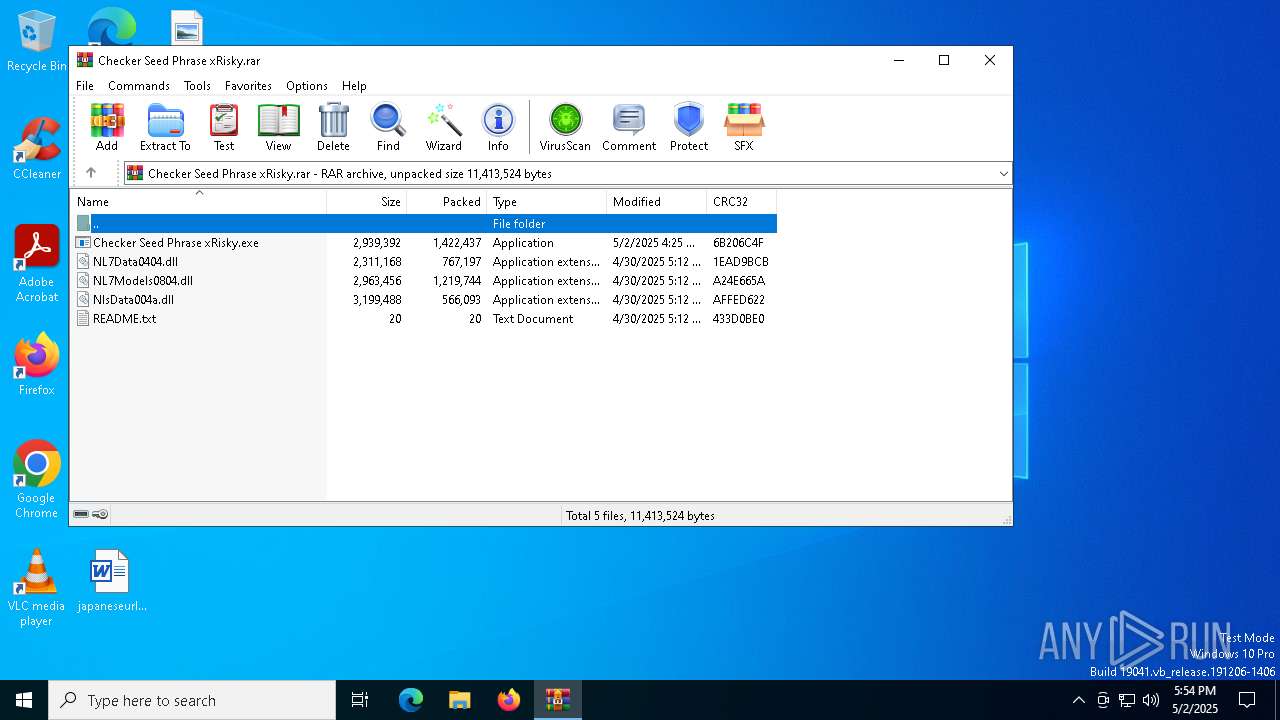
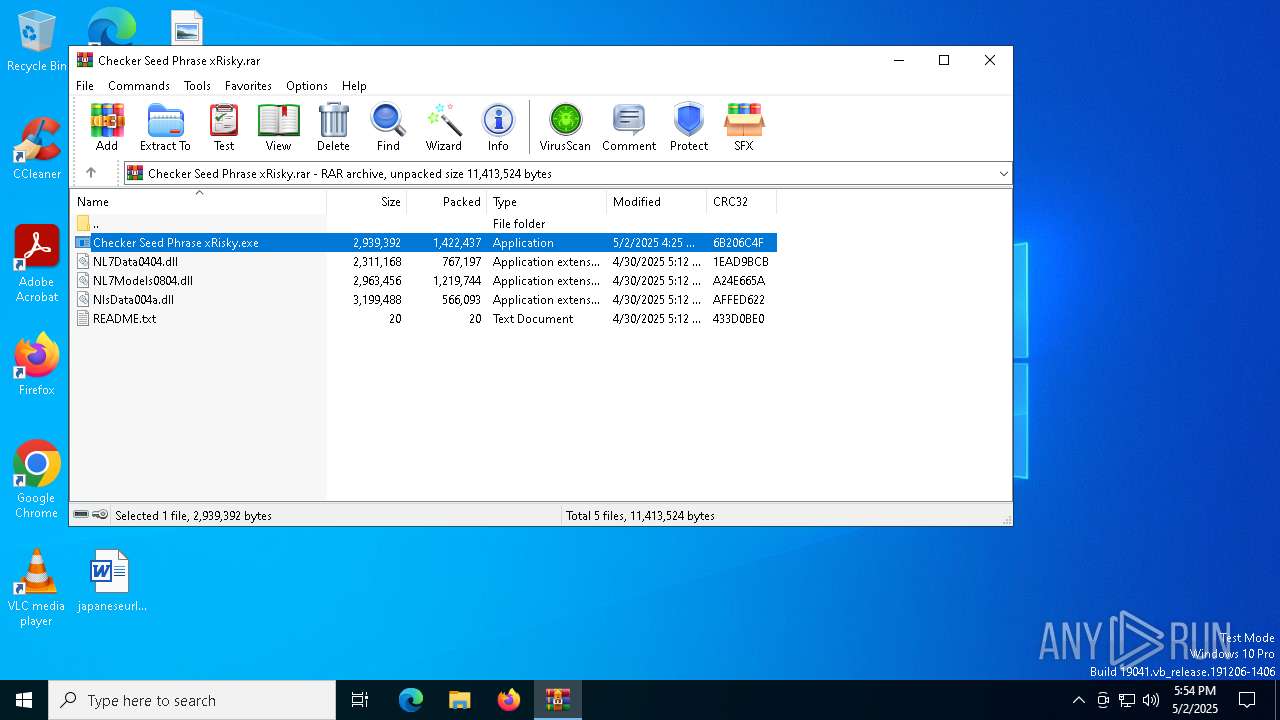
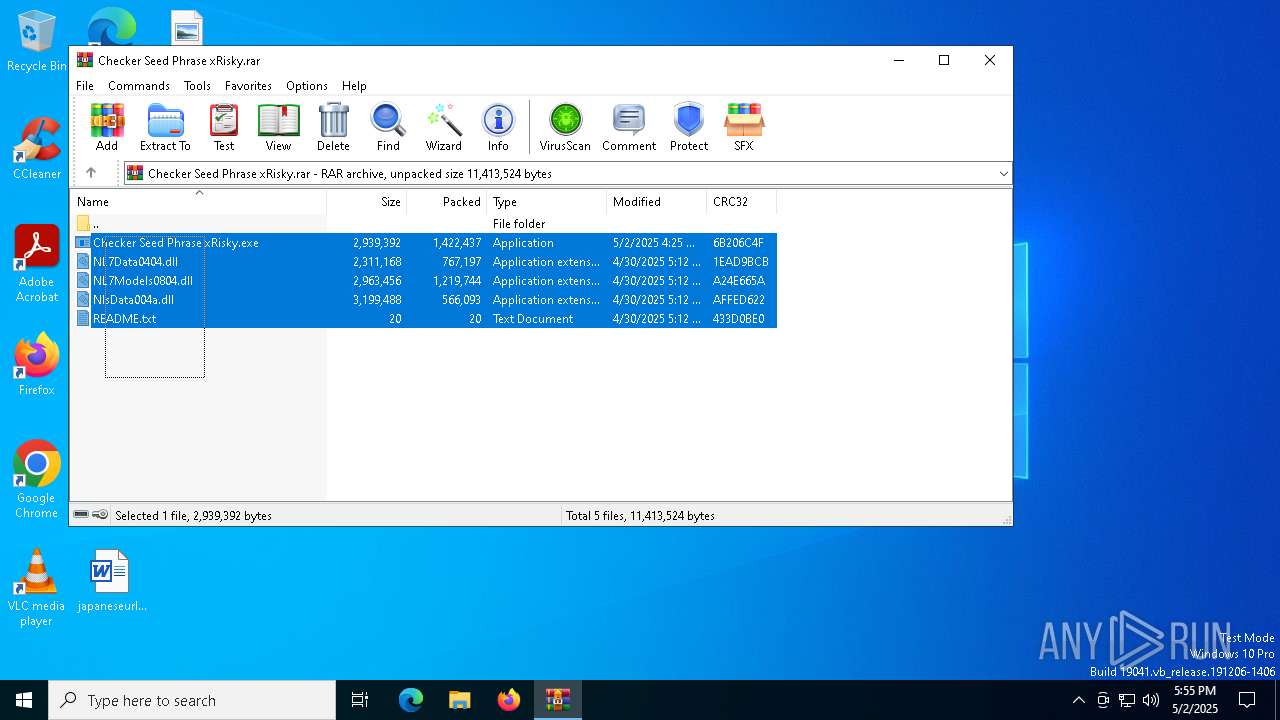
| File name: | Checker Seed Phrase xRisky.rar |
| Full analysis: | https://app.any.run/tasks/cbdd3597-ca0c-4b27-8124-9c4635640426 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | May 02, 2025, 17:54:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 2DAC4ECE52C5FE09EE22EEC0C2F9E475 |
| SHA1: | 7A5EC0E6BE66B8173413A35313E0E81BFB1DBCE5 |
| SHA256: | DF67FD814FC60CC4831729366D4D98D15BDA6C6F92CA2ADC7C2606C71D371BE4 |
| SSDEEP: | 98304:N3mESIOjii2q2hjLRtAc4NNpPElpsSQYAswoTyW8Jb0/YP9PmZmjnqXeWBvKU7ct:Ky8BZwc |
MALICIOUS
Create files in the Startup directory
- ikiBdzvtRI.exe (PID: 5868)
LUMMA mutex has been found
- MSBuild.exe (PID: 2908)
- ikiBdzvtRI.exe (PID: 5868)
- JBnTlvLT3i.exe (PID: 6564)
- MSBuild.exe (PID: 4424)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 2908)
- MSBuild.exe (PID: 4424)
Steals credentials from Web Browsers
- MSBuild.exe (PID: 2908)
- MSBuild.exe (PID: 4424)
LUMMA has been detected (YARA)
- MSBuild.exe (PID: 4424)
SUSPICIOUS
Starts a Microsoft application from unusual location
- Checker Seed Phrase xRisky.exe (PID: 864)
- Checker Seed Phrase xRisky.exe (PID: 2344)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5072)
- MSBuild.exe (PID: 2236)
- MSBuild.exe (PID: 1328)
Process drops legitimate windows executable
- WinRAR.exe (PID: 5072)
- MSBuild.exe (PID: 2236)
- MSBuild.exe (PID: 1328)
Executable content was dropped or overwritten
- MSBuild.exe (PID: 2236)
- ikiBdzvtRI.exe (PID: 5868)
- MSBuild.exe (PID: 1328)
The process creates files with name similar to system file names
- ikiBdzvtRI.exe (PID: 5868)
Found regular expressions for crypto-addresses (YARA)
- ikiBdzvtRI.exe (PID: 5868)
Searches for installed software
- MSBuild.exe (PID: 2908)
- MSBuild.exe (PID: 4424)
There is functionality for taking screenshot (YARA)
- MSBuild.exe (PID: 4424)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5072)
Creates files or folders in the user directory
- MSBuild.exe (PID: 2236)
- ikiBdzvtRI.exe (PID: 5868)
- MSBuild.exe (PID: 1328)
Checks supported languages
- MSBuild.exe (PID: 2236)
- Checker Seed Phrase xRisky.exe (PID: 864)
- Mn4T59674h.exe (PID: 2088)
- ikiBdzvtRI.exe (PID: 5868)
- MSBuild.exe (PID: 2908)
- Checker Seed Phrase xRisky.exe (PID: 2344)
- MSBuild.exe (PID: 1328)
- fPn6luXr9s.exe (PID: 4688)
- JBnTlvLT3i.exe (PID: 6564)
- MSBuild.exe (PID: 4424)
The sample compiled with english language support
- WinRAR.exe (PID: 5072)
- MSBuild.exe (PID: 2236)
- MSBuild.exe (PID: 1328)
Reads the computer name
- MSBuild.exe (PID: 2236)
- ikiBdzvtRI.exe (PID: 5868)
- MSBuild.exe (PID: 2908)
- JBnTlvLT3i.exe (PID: 6564)
- MSBuild.exe (PID: 4424)
- MSBuild.exe (PID: 1328)
Process checks computer location settings
- MSBuild.exe (PID: 2236)
- MSBuild.exe (PID: 1328)
Reads the software policy settings
- MSBuild.exe (PID: 2908)
- slui.exe (PID: 1132)
- MSBuild.exe (PID: 4424)
- slui.exe (PID: 5084)
Manual execution by a user
- Checker Seed Phrase xRisky.exe (PID: 2344)
Checks proxy server information
- slui.exe (PID: 5084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(4424) MSBuild.exe
C2 (8)orijinalecza.org/jub
orjinalecza.net/lxaz
eczakozmetik.net/qop
tortoisgfe.top/paxk
snakejh.top/adsk
eczamedikal.org/vax
medicalbitkisel.net/juj
orijinalecza.net/kazd
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 1422437 |
| UncompressedSize: | 2939392 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Checker Seed Phrase xRisky.exe |
Total processes
150
Monitored processes
16
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5072.30034\Checker Seed Phrase xRisky.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5072.30034\Checker Seed Phrase xRisky.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | Checker Seed Phrase xRisky.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2088 | "C:\Users\admin\AppData\Roaming\Mn4T59674h.exe" | C:\Users\admin\AppData\Roaming\Mn4T59674h.exe | — | MSBuild.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | Checker Seed Phrase xRisky.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2344 | "C:\Users\admin\Desktop\Checker Seed Phrase xRisky.exe" | C:\Users\admin\Desktop\Checker Seed Phrase xRisky.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2908 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | Mn4T59674h.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 3332 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4068 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | Mn4T59674h.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4424 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | fPn6luXr9s.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
Lumma(PID) Process(4424) MSBuild.exe C2 (8)orijinalecza.org/jub orjinalecza.net/lxaz eczakozmetik.net/qop tortoisgfe.top/paxk snakejh.top/adsk eczamedikal.org/vax medicalbitkisel.net/juj orijinalecza.net/kazd | |||||||||||||||
Total events
4 608
Read events
4 590
Write events
18
Delete events
0
Modification events
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Checker Seed Phrase xRisky.rar | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
13
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5072.30034\NL7Data0404.dll | executable | |
MD5:81B14FD1C9D2B830E55C93C4C38AFA2F | SHA256:878E2DBAC4B6A6BCCE54742F3C7BFD87AA93A6637CCCC1E5D18AB65215D81BEE | |||
| 1328 | MSBuild.exe | C:\Users\admin\AppData\Roaming\fPn6luXr9s.exe | executable | |
MD5:CB7947BB3CECB618E00A27E6F2747822 | SHA256:FD23ED3598671A78339696A462722B1295792315BDEAC3CF76493DD2DCC6546D | |||
| 5072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5072.34385\README.txt | text | |
MD5:229BFB07694F123E2CB4986F47100A62 | SHA256:8DF26B1F550C80646F01D25B8AAFCABB1342BBB2BE1CD335CDB8D254BE8C4090 | |||
| 5868 | ikiBdzvtRI.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svhost.exe | executable | |
MD5:3A96573C06D0D2479145387C10A27082 | SHA256:ED6731C5D5DE872E56816984FAF9BB056E4D3E3282862F2F626D2DF75B38D6DA | |||
| 1328 | MSBuild.exe | C:\Users\admin\AppData\Roaming\JBnTlvLT3i.exe | executable | |
MD5:3A96573C06D0D2479145387C10A27082 | SHA256:ED6731C5D5DE872E56816984FAF9BB056E4D3E3282862F2F626D2DF75B38D6DA | |||
| 2236 | MSBuild.exe | C:\Users\admin\AppData\Roaming\Mn4T59674h.exe | executable | |
MD5:CB7947BB3CECB618E00A27E6F2747822 | SHA256:FD23ED3598671A78339696A462722B1295792315BDEAC3CF76493DD2DCC6546D | |||
| 5072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5072.30034\README.txt | text | |
MD5:229BFB07694F123E2CB4986F47100A62 | SHA256:8DF26B1F550C80646F01D25B8AAFCABB1342BBB2BE1CD335CDB8D254BE8C4090 | |||
| 5072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5072.30034\NlsData004a.dll | executable | |
MD5:BE007B645B9D1332E3346107727320D9 | SHA256:7B128BE8D77398CBC3BB789A34E21AFC984C2E87276907A01326F8FB4504E9DA | |||
| 5072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5072.30034\NL7Models0804.dll | executable | |
MD5:65525C7B89204D241120B7638934A0D2 | SHA256:18F7F52F14986133F9A9676D5AB959349377A53C0936CEA6EB9880E72F85BC54 | |||
| 5072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5072.34385\NlsData004a.dll | executable | |
MD5:BE007B645B9D1332E3346107727320D9 | SHA256:7B128BE8D77398CBC3BB789A34E21AFC984C2E87276907A01326F8FB4504E9DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
38
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1628 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1628 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
medicalbitkisel.net |
| unknown |