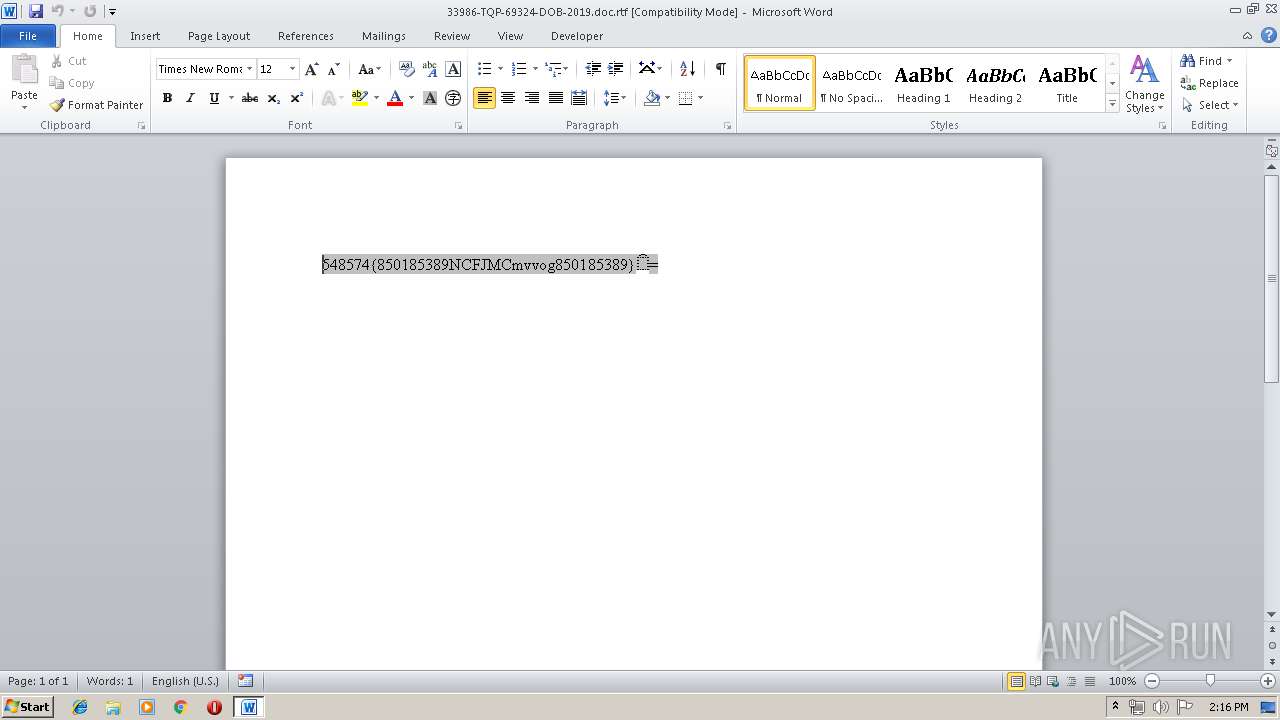
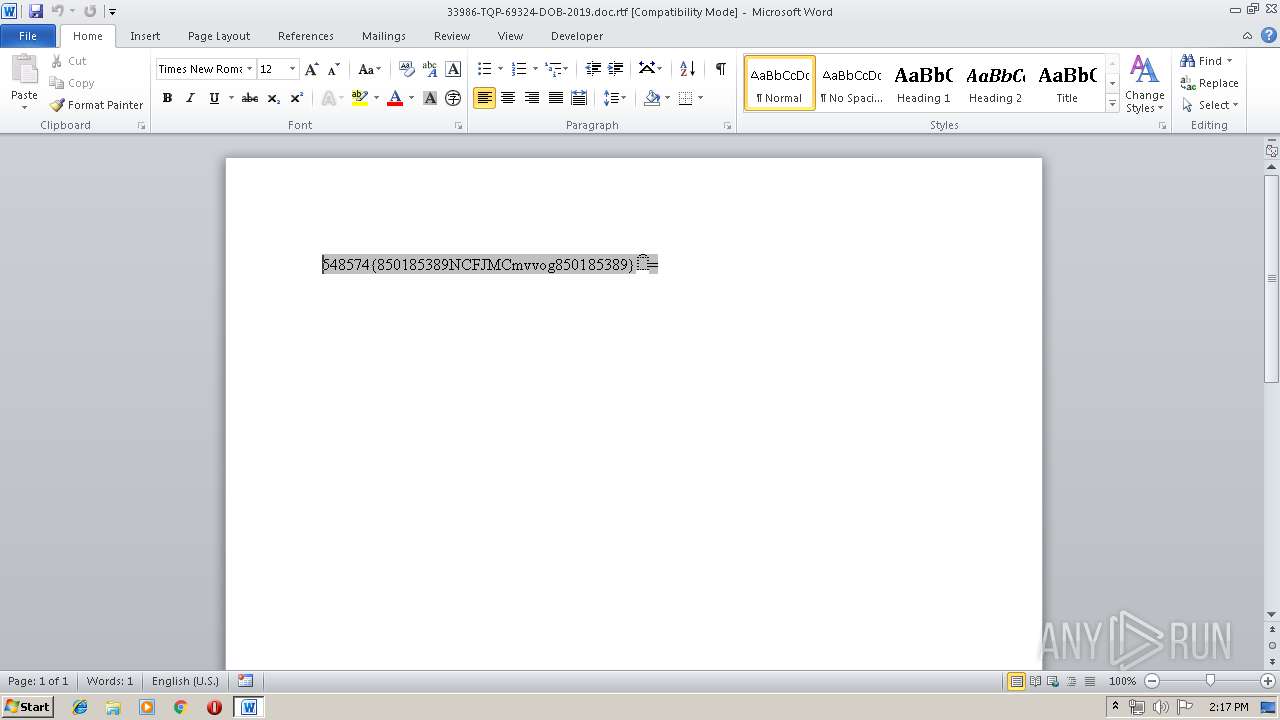
| File name: | 33986-TQP-69324-DOB-2019.doc |
| Full analysis: | https://app.any.run/tasks/5729de00-44c4-4672-ba31-2a1dc8f0c152 |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | December 06, 2019, 14:12:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, unknown version |
| MD5: | 447F2F4430E7EFA9E165DA6CE6FAE601 |
| SHA1: | 5B352D12E3AF7C10CB3C741A2E416E614C0502A4 |
| SHA256: | DEF4E0EE3F787D867DAFE6FEBB68E9BA356AF66332FEFA18F0730B6F836749DD |
| SSDEEP: | 24576:kff+8U1/WoJtMOz5oi9r5kvZR0BdetJpe3mWi1n+OBoTk30/2OhJRnHsLVmDTqn4:L |
MALICIOUS
Changes the autorun value in the registry
- pop.exe (PID: 2880)
- KUQJUC.exe (PID: 2280)
- OJOHPW.exe (PID: 2888)
- RegAsm.exe (PID: 392)
- TFIMUM.exe (PID: 1740)
Downloads executable files from the Internet
- EQNEDT32.EXE (PID: 2212)
Application was dropped or rewritten from another process
- TFIMUM.exe (PID: 1740)
- OJOHPW.exe (PID: 2888)
- RegAsm.exe (PID: 392)
- RegAsm.exe (PID: 884)
- RegAsm.exe (PID: 944)
- KUQJUC.exe (PID: 2280)
- RegAsm.exe (PID: 332)
- pop.exe (PID: 2880)
Starts Visual C# compiler
- TFIMUM.exe (PID: 1740)
- KUQJUC.exe (PID: 2280)
- pop.exe (PID: 2880)
- OJOHPW.exe (PID: 2888)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 2212)
Suspicious connection from the Equation Editor
- EQNEDT32.EXE (PID: 2212)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 944)
- vbc.exe (PID: 776)
- vbc.exe (PID: 2848)
- vbc.exe (PID: 3708)
- vbc.exe (PID: 1516)
Detected Hawkeye Keylogger
- RegAsm.exe (PID: 884)
- RegAsm.exe (PID: 332)
HAWKEYE was detected
- RegAsm.exe (PID: 332)
Stealing of credential data
- vbc.exe (PID: 776)
- vbc.exe (PID: 1516)
- vbc.exe (PID: 2848)
- vbc.exe (PID: 3708)
Uses NirSoft utilities to collect credentials
- vbc.exe (PID: 776)
- vbc.exe (PID: 1516)
- vbc.exe (PID: 2848)
- vbc.exe (PID: 3708)
SUSPICIOUS
Executable content was dropped or overwritten
- pop.exe (PID: 2880)
- TFIMUM.exe (PID: 1740)
- EQNEDT32.EXE (PID: 2212)
- RegAsm.exe (PID: 392)
- KUQJUC.exe (PID: 2280)
- OJOHPW.exe (PID: 2888)
Connects to unusual port
- EQNEDT32.EXE (PID: 2212)
Creates files in the user directory
- RegAsm.exe (PID: 392)
Executed via COM
- EQNEDT32.EXE (PID: 2212)
Uses RUNDLL32.EXE to load library
- RegAsm.exe (PID: 392)
Reads Internet Cache Settings
- rundll32.exe (PID: 520)
Loads DLL from Mozilla Firefox
- RegAsm.exe (PID: 944)
- vbc.exe (PID: 1516)
Checks for external IP
- RegAsm.exe (PID: 944)
Connects to SMTP port
- RegAsm.exe (PID: 944)
- RegAsm.exe (PID: 332)
- RegAsm.exe (PID: 884)
Executes scripts
- RegAsm.exe (PID: 884)
- RegAsm.exe (PID: 332)
Reads Environment values
- RegAsm.exe (PID: 332)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2796)
Creates files in the user directory
- WINWORD.EXE (PID: 2796)
Reads settings of System Certificates
- RegAsm.exe (PID: 944)
- RegAsm.exe (PID: 332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
Total processes
63
Monitored processes
23
Malicious processes
13
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES1989.tmp" "c:\Users\admin\AppData\Local\Temp\CSCACC9498ECBC342EA8D52FED567765A94.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52519.0 built by: VSWINSERVICING Modules
| |||||||||||||||
| 332 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | KUQJUC.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 392 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | pop.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 520 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | RegAsm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 776 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe" /stext "C:\Users\admin\AppData\Local\Temp\tmp529A.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | RegAsm.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 884 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | OJOHPW.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 944 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | TFIMUM.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 1044 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESDB1.tmp" "c:\Users\admin\AppData\Local\Temp\CSC9BC112F9660B44248080D4CC79B8CD61.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52519.0 built by: VSWINSERVICING Modules
| |||||||||||||||
| 1516 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe" /stext "C:\Users\admin\AppData\Local\Temp\tmp4D6A.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | RegAsm.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 1724 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES1D42.tmp" "c:\Users\admin\AppData\Local\Temp\CSC92006EE63854855A2E97A25101F2D21.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52519.0 built by: VSWINSERVICING Modules
| |||||||||||||||
Total events
2 421
Read events
1 662
Write events
623
Delete events
136
Modification events
| (PID) Process: | (2796) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | w"e |
Value: 77226500EC0A0000010000000000000000000000 | |||
| (PID) Process: | (2796) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2796) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2796) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2796) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2796) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2796) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2796) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2796) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2796) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1334181950 | |||
Executable files
9
Suspicious files
0
Text files
23
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2796 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRB6A8.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2880 | pop.exe | C:\Users\admin\DocumentsBinaryObjectWithMapTyped | — | |
MD5:— | SHA256:— | |||
| 2880 | pop.exe | C:\Users\admin\AppData\Local\Temp\h0y0c5b5.0.cs | — | |
MD5:— | SHA256:— | |||
| 1044 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESDB1.tmp | — | |
MD5:— | SHA256:— | |||
| 2572 | csc.exe | C:\Users\admin\AppData\Local\Temp\h0y0c5b5.dll | — | |
MD5:— | SHA256:— | |||
| 2572 | csc.exe | C:\Users\admin\AppData\Local\Temp\h0y0c5b5.out | — | |
MD5:— | SHA256:— | |||
| 392 | RegAsm.exe | C:\Users\admin\AppData\Local\Temp\aut1310.tmp | — | |
MD5:— | SHA256:— | |||
| 392 | RegAsm.exe | C:\Users\admin\AppData\Local\Temp\aut16F9.tmp | — | |
MD5:— | SHA256:— | |||
| 392 | RegAsm.exe | C:\Users\admin\AppData\Local\Temp\aut17B6.tmp | — | |
MD5:— | SHA256:— | |||
| 236 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES1989.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
11
DNS requests
5
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
332 | RegAsm.exe | GET | 200 | 66.171.248.178:80 | http://bot.whatismyipaddress.com/ | US | text | 13 b | shared |
332 | RegAsm.exe | GET | 200 | 66.171.248.178:80 | http://bot.whatismyipaddress.com/ | US | text | 13 b | shared |
332 | RegAsm.exe | GET | 200 | 66.171.248.178:80 | http://bot.whatismyipaddress.com/ | US | text | 13 b | shared |
884 | RegAsm.exe | GET | 200 | 66.171.248.178:80 | http://bot.whatismyipaddress.com/ | US | text | 13 b | shared |
2212 | EQNEDT32.EXE | GET | 200 | 52.47.207.162:82 | http://52.47.207.162:82/po.exe | FR | executable | 5.96 Mb | suspicious |
944 | RegAsm.exe | GET | 200 | 131.186.113.70:80 | http://checkip.dyndns.org/ | US | html | 105 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2212 | EQNEDT32.EXE | 52.47.207.162:82 | — | Amazon.com, Inc. | FR | suspicious |
944 | RegAsm.exe | 131.186.113.70:80 | checkip.dyndns.org | — | US | malicious |
392 | RegAsm.exe | 104.26.8.44:443 | ipapi.co | Cloudflare Inc | US | malicious |
332 | RegAsm.exe | 66.171.248.178:80 | bot.whatismyipaddress.com | Alchemy Communications, Inc. | US | malicious |
944 | RegAsm.exe | 185.61.137.171:587 | mail.bandaichemical.com | Dotsi, Unipessoal Lda. | NL | suspicious |
332 | RegAsm.exe | 185.61.137.171:587 | mail.bandaichemical.com | Dotsi, Unipessoal Lda. | NL | suspicious |
884 | RegAsm.exe | 66.171.248.178:80 | bot.whatismyipaddress.com | Alchemy Communications, Inc. | US | malicious |
884 | RegAsm.exe | 185.61.137.171:587 | mail.bandaichemical.com | Dotsi, Unipessoal Lda. | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ipapi.co |
| shared |
checkip.dyndns.org |
| shared |
mail.bandaichemical.com |
| unknown |
maxcoop1.ddns.net |
| malicious |
bot.whatismyipaddress.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2212 | EQNEDT32.EXE | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
2212 | EQNEDT32.EXE | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
2212 | EQNEDT32.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2212 | EQNEDT32.EXE | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1080 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup Domain (ipapi .co in DNS lookup) |
1080 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.dyndns. Domain |
1080 | svchost.exe | Misc activity | AV INFO Query to checkip.dyndns. Domain |
944 | RegAsm.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup - checkip.dyndns.org |
944 | RegAsm.exe | Potentially Bad Traffic | ET POLICY DynDNS CheckIp External IP Address Server Response |
944 | RegAsm.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
8 ETPRO signatures available at the full report