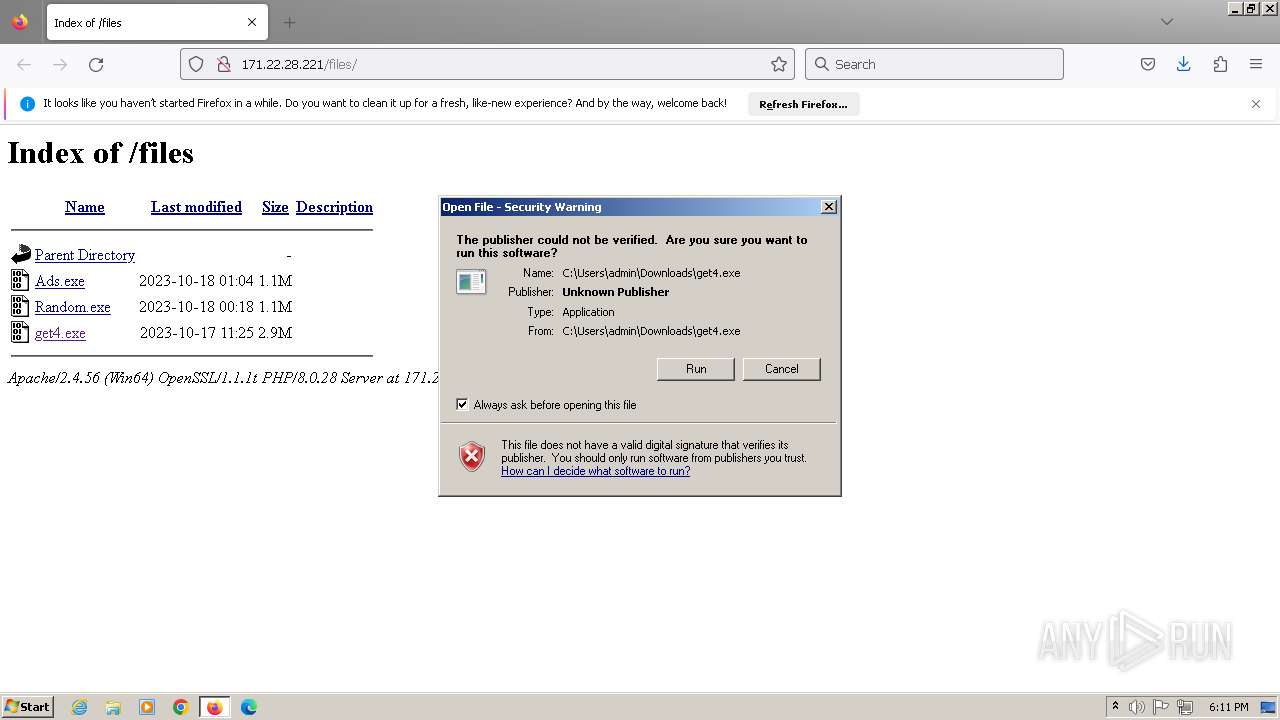
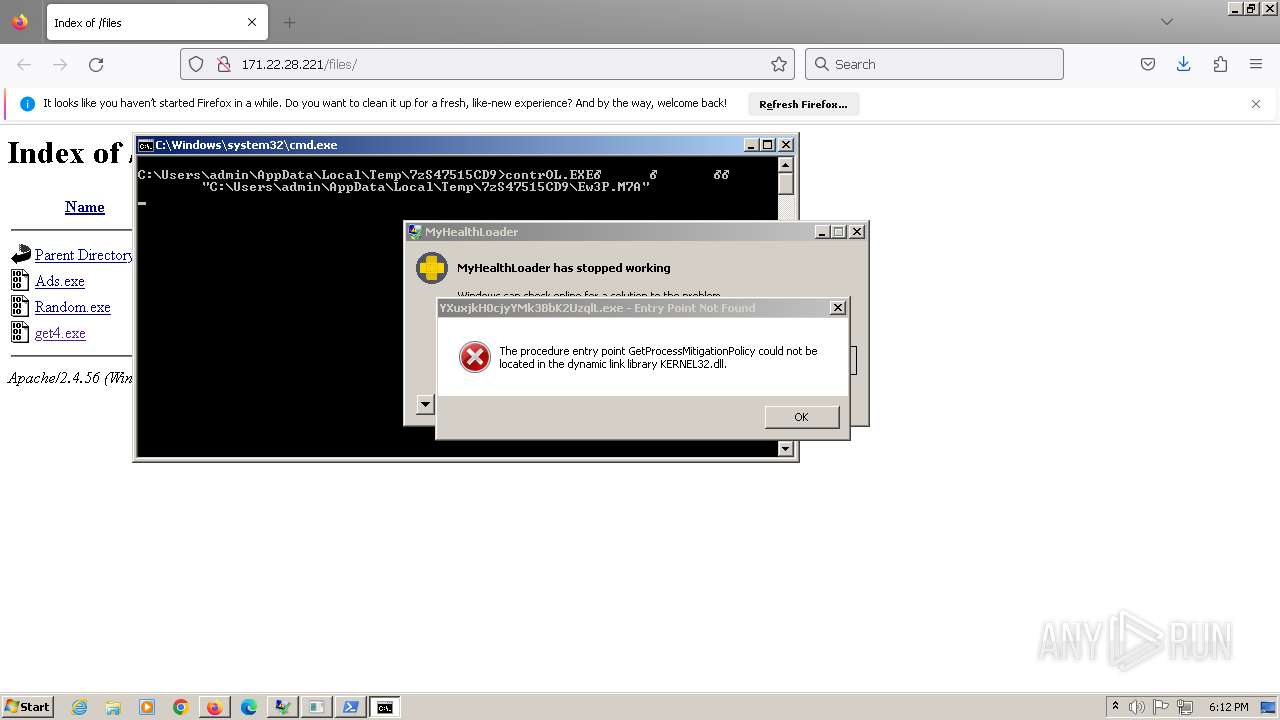
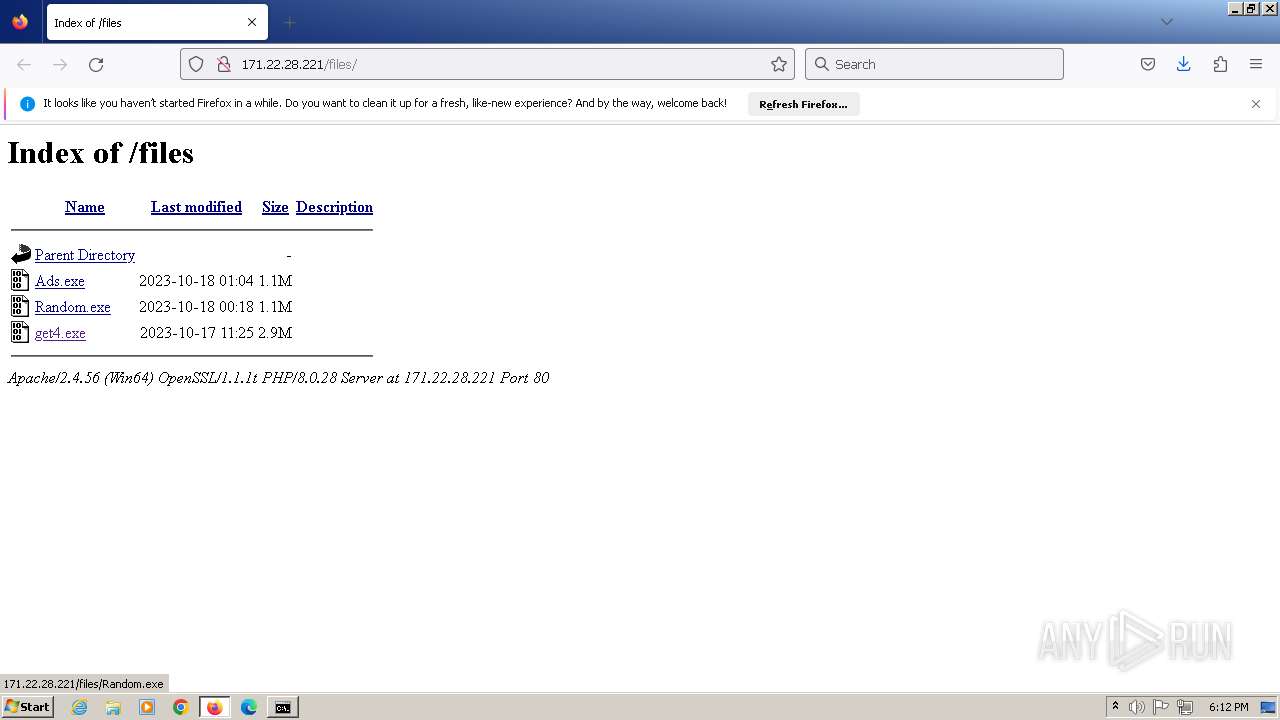
| URL: | http://171.22.28.221/files/ |
| Full analysis: | https://app.any.run/tasks/f4296b37-eeae-4b4b-b7c7-ad83b1fceed3 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | October 18, 2023, 18:11:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| SHA1: | 56BB406B0086B232A6681527E1E178754D621007 |
| SHA256: | DEE1B6C955BAE4A3316D3510944A4CE5B32F9257C043D476AE893CC9933CA371 |
| SSDEEP: | 3:N1KqUfl0Kn:CqUflz |
MALICIOUS
Application was dropped or rewritten from another process
- get4.exe (PID: 1296)
- q8OSAEnVHW3WkRgcmKQ0dUXZ.exe (PID: 3412)
- nhdues.exe (PID: 3728)
- AOdgduFToChPmaTfjl8Ph3R4.exe (PID: 3420)
- arriveprospect.exe (PID: 3012)
- 66vC2gAXVfk27a5wEcwAlQ4t.exe (PID: 3776)
- 3npwZ06l6txlO5EG5bEFIhXC.exe (PID: 3468)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- K3AidViq3fu5I0UKoDhvimK1.exe (PID: 3520)
- Lmr41oZWb1ZPiV772JIaAFkT.exe (PID: 2092)
- K3AidViq3fu5I0UKoDhvimK1.exe (PID: 3620)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 2460)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- YXuxjkH0cjyYMk3BbK2UzqlL.exe (PID: 792)
- zsWklsWnSwufAN7TKspgweE3.exe (PID: 2436)
- zsWklsWnSwufAN7TKspgweE3.exe (PID: 2180)
- mmUi7viccv48sJD1w9k4AuDs.exe (PID: 3140)
- Install.exe (PID: 904)
- mmUi7viccv48sJD1w9k4AuDs.exe (PID: 3400)
- Install.exe (PID: 3964)
- Zbxppt0pzqdS7E2romHwKpef.exe (PID: 2504)
- LhzwzpX5CoXjD1kfEk3zTdEj.exe (PID: 2476)
- RZbl0lR98O6Qhs7pebM5pNhE.exe (PID: 3796)
- vAjmiB170tl4bIKZ5xUDpfrl.exe (PID: 1396)
- nF6mOdhRMpN3SGbQlrPIZdiL.exe (PID: 3980)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- lYUgfzizvypmRH9zJmFjirkj.exe (PID: 2240)
- ukAyKHLGhoX80UWXzKQoVPOa.exe (PID: 1296)
- Tf5ss65.exe (PID: 4628)
- nb5XL55.exe (PID: 4784)
- rg1qP67.exe (PID: 684)
- arriveprospect.exe (PID: 5056)
- RzHhsHIvDvaCDn8gf5Vfq60U.exe (PID: 1076)
- ix0VkCfPyhYNXlHNcxjuBwtF.exe (PID: 1828)
- arriiveprospect.exe (PID: 2244)
- srMgMKR14ZrJXhtxiFzFfjto.exe (PID: 3764)
- vt2VgJ1wjzh9p8Ki58YN65JU.exe (PID: 984)
- QIPR1ptbkPFZQ5thhYbsDOLW.exe (PID: 5024)
- Vx9XK71.exe (PID: 1620)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 3876)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 4592)
- gWrsw8QB73u2AInEN7hC0wty.exe (PID: 3424)
- loEwvzzf5f4P5czVnTz5lu61.exe (PID: 3912)
- himeffectively.exe (PID: 3012)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- 1lP68aL0.exe (PID: 3356)
- OBezVevHKAJ2UV1nNQKZcbBI.exe (PID: 4940)
- untilmathematicspro.exe (PID: 4152)
- untilmathematics.exe (PID: 4852)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- QIPR1ptbkPFZQ5thhYbsDOLW.exe (PID: 4396)
- cgKIS14C6q1NoChphhrRLrDB.exe (PID: 4908)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 6072)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 5456)
- nhdues.exe (PID: 6004)
- CjzLhIoubU6EOrERGzOsnpeU.exe (PID: 5148)
- 2pr5983.exe (PID: 5128)
- uhxRUj5DV1cfZSEfD3bMoZUr.exe (PID: 5556)
- IEUpdater1.exe (PID: 3808)
- updater.exe (PID: 5892)
- Install.exe (PID: 6056)
- oneetx.exe (PID: 5916)
- FFvUvYbdQ3pjTyFDA4WuM6Yr.exe (PID: 4988)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- 1vaFjymLZSPVW3YztXJvLowK.exe (PID: 5944)
- a8XgakQfmwwdkpVYBMRsJHzX.exe (PID: 4608)
- _tTuyuRtejceJx8gkDzE6lOi.exe (PID: 4212)
- m_fh9IkGRfZ7B0XBXkKo84dt.exe (PID: 2220)
- ffUbNlFyy94bJxTL_5Ig97z6.exe (PID: 1076)
- RgZJOtfo_D0hS8k6QbNV4q4k.exe (PID: 4208)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5284)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- 3Vj72Hw.exe (PID: 3764)
- build2.exe (PID: 5124)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5472)
- Install.exe (PID: 3340)
- Tf5ss65.exe (PID: 4128)
- build3.exe (PID: 6040)
- 4WD828Ic.exe (PID: 5668)
- RE82WtvebfRpLAO0phRIy4wQ.exe (PID: 3748)
- ysGi5iID3g53tlkzaQbgcJJD.exe (PID: 5788)
- SNeCBREnHZIC1szciY1ex3XV.exe (PID: 4140)
- KibI8idbFuOXtShsGGds6DF3.exe (PID: 5856)
- bXbjU3cr8ZJeNPvCflnP7NAd.exe (PID: 5804)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- 5zPBjjonT4oS1cZTmbyogig9.exe (PID: 2960)
- ngMvND4PvkhwkTVzYV5xsqwh.exe (PID: 4740)
- hkfMTElbgBduYQ60cv15ysFv.exe (PID: 5480)
- ueFUGKtfr8db8yUkRinZ2Yqv.exe (PID: 5268)
- BOkUTx0iwlgh3MRNoF7OvgaQ.exe (PID: 5880)
- 0X2VWPeOtWsJzActynA8jUp3.exe (PID: 4596)
- build2.exe (PID: 2476)
- BGiqV6xWxTEIyg12Uj1Y35gg.exe (PID: 1760)
- SKDGRzQaLrdorjBgweAuc5lQ.exe (PID: 5636)
- 5cHcitxg53pwem26My5QgTVo.exe (PID: 5872)
- aLiYFgBKzaENPeFMTzSmeIxG.exe (PID: 6072)
- ZPd8ckjQ4bbYp0Ib7vkamPaC.exe (PID: 4552)
- untilmathematics.exe (PID: 5924)
- 0X2VWPeOtWsJzActynA8jUp3.exe (PID: 3400)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- untilmathematics.exe (PID: 5140)
- TskS7iTuF1rMl02JwXmqAncH.exe (PID: 6296)
- untilmathematiics.exe (PID: 4572)
- fvSjc99mxBf23smnXhkyisRs.exe (PID: 5104)
- ovIFc9bI6zb75QUIvz2wnNDT.exe (PID: 5404)
- Install.exe (PID: 5116)
- nb5XL55.exe (PID: 6228)
- YAqVpZrY6VsUD5ENN6oY797A.exe (PID: 6368)
- fMh25VTHm9OryG9HeJyynLMm.exe (PID: 6468)
- BqsrfKeKClGgpr7HLZodSKqw.exe (PID: 2932)
- vDx1uwIwCvhCxlbFOC2kkWGc.exe (PID: 6052)
- Kj3JVsuQJB2IvbWqvZdsn4f7.exe (PID: 2548)
- JEwIXxkYI0wHPvLLaqPI7yVM.exe (PID: 5900)
- Install.exe (PID: 6940)
- fMh25VTHm9OryG9HeJyynLMm.exe (PID: 6900)
- Install.exe (PID: 6492)
- Uue0d0frXqEkX6JcnasnNNbd.exe (PID: 6952)
- 0yKb1qQOjVPpU6xlr56TaqHo.exe (PID: 6948)
- 1jQgxQsXN1wKyFlyav53jSeF.exe (PID: 6764)
- ULRKwx3iR5VJqNbLaeyIW54j.exe (PID: 6976)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- QeNz3MywCODuOxaYk85AqaYo.exe (PID: 5924)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- nhdues.exe (PID: 6608)
- Install.exe (PID: 6808)
- xqRPslL.exe (PID: 5592)
- O6d4NgNKLYPx1lNE6j84Gr_k.exe (PID: 3948)
- Al7cTMQlqsfdhc54yHwz1zKD.exe (PID: 7060)
- rg1qP67.exe (PID: 4668)
- Vx9XK71.exe (PID: 7548)
- Tf5ss65.exe (PID: 4016)
- j1QJP0Aa5KqR0gKRmEqWQuN8.exe (PID: 7312)
- Ns6hO16rUCgFiQNe6HvHSI5W.exe (PID: 7316)
- 7BZn5RFuIM945dYaLrkreCCh.exe (PID: 7256)
- sYUFFPSWg8DtFkB2iv0yZAKN.exe (PID: 4112)
- x0RPFql2zaxOzeAaN8s3QFfO.exe (PID: 7344)
- xNfkGmGmIqUGxtSpqcUgU8oC.exe (PID: 5264)
- n8u8MnM4FzEZFJsDGpjlpz9v.exe (PID: 7736)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
- CnU05d0R1X160oSaoMyxrsaD.exe (PID: 7176)
- sYUFFPSWg8DtFkB2iv0yZAKN.exe (PID: 8156)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5068)
- UTpHoSqwV4zPYqFspLsVQn5B.exe (PID: 7696)
- iWbQMIE_UejHCbAVoXKzSsCs.exe (PID: 8040)
- k2xOQaxpXLSuIZ1xwmjXa2Vz.exe (PID: 7716)
- gByeecmMjiYL8_DIUhNulyQz.exe (PID: 5508)
- ZwKhMo_6j7LHpjAFGyW48J0z.exe (PID: 7036)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 8104)
- IYEq8bDdA5b9aTNdGrlAV9OY.exe (PID: 4700)
- rsMRDHH5EHOGkhtLr7DcGPWp.exe (PID: 5864)
- lHeL4Ck2v9Hjsjc6L2Pb2eGZ.exe (PID: 7972)
- P3jb1n2rFq0ez3JUkuovAZXe.exe (PID: 7188)
- 1lP68aL0.exe (PID: 2688)
- nb5XL55.exe (PID: 7328)
- xzAyOwQKSF8_vOdFe_6ZM0Dm.exe (PID: 5632)
- fyuhvPv42QHuU13Up4YJsw8l.exe (PID: 7072)
- UvzI3kSiZhAk8YCjLL4eOV41.exe (PID: 5192)
- updater.exe (PID: 8836)
- 8QQnvSudgWkiVzXWct9iPrdG.exe (PID: 8288)
- HNXZXKK.exe (PID: 6028)
- Install.exe (PID: 8532)
- himeffectively.exe (PID: 9156)
- 2pr5983.exe (PID: 6848)
- Install.exe (PID: 8372)
Create files in the Startup directory
- InstallUtil.exe (PID: 2556)
Drops the executable file immediately after the start
- AOdgduFToChPmaTfjl8Ph3R4.exe (PID: 3420)
- InstallUtil.exe (PID: 2556)
- q8OSAEnVHW3WkRgcmKQ0dUXZ.exe (PID: 3412)
- YXuxjkH0cjyYMk3BbK2UzqlL.exe (PID: 792)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- Install.exe (PID: 904)
- mmUi7viccv48sJD1w9k4AuDs.exe (PID: 3140)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- vAjmiB170tl4bIKZ5xUDpfrl.exe (PID: 1396)
- lYUgfzizvypmRH9zJmFjirkj.exe (PID: 2240)
- nb5XL55.exe (PID: 4784)
- rg1qP67.exe (PID: 684)
- InstallUtil.exe (PID: 4828)
- ix0VkCfPyhYNXlHNcxjuBwtF.exe (PID: 1828)
- Vx9XK71.exe (PID: 1620)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 4592)
- Tf5ss65.exe (PID: 4628)
- himeffectively.exe (PID: 3012)
- untilmathematicspro.exe (PID: 4152)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- OBezVevHKAJ2UV1nNQKZcbBI.exe (PID: 4940)
- Install.exe (PID: 3964)
- cgKIS14C6q1NoChphhrRLrDB.exe (PID: 4908)
- cgKIS14C6q1NoChphhrRLrDB.tmp (PID: 4104)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- zsWklsWnSwufAN7TKspgweE3.exe (PID: 2180)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- uhxRUj5DV1cfZSEfD3bMoZUr.exe (PID: 5556)
- CjzLhIoubU6EOrERGzOsnpeU.exe (PID: 5148)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 5456)
- 1vaFjymLZSPVW3YztXJvLowK.exe (PID: 5944)
- a8XgakQfmwwdkpVYBMRsJHzX.exe (PID: 4608)
- InstallUtil.exe (PID: 924)
- Install.exe (PID: 6056)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- ysGi5iID3g53tlkzaQbgcJJD.exe (PID: 5788)
- InstallUtil.exe (PID: 2436)
- SKDGRzQaLrdorjBgweAuc5lQ.exe (PID: 5636)
- ZPd8ckjQ4bbYp0Ib7vkamPaC.exe (PID: 4552)
- Tf5ss65.exe (PID: 4128)
- updater.exe (PID: 5892)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- KibI8idbFuOXtShsGGds6DF3.exe (PID: 5856)
- TskS7iTuF1rMl02JwXmqAncH.exe (PID: 6296)
- Install.exe (PID: 5116)
- Kj3JVsuQJB2IvbWqvZdsn4f7.exe (PID: 2548)
- BqsrfKeKClGgpr7HLZodSKqw.exe (PID: 2932)
- Install.exe (PID: 6492)
- QeNz3MywCODuOxaYk85AqaYo.exe (PID: 5924)
- nb5XL55.exe (PID: 6228)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- rsMRDHH5EHOGkhtLr7DcGPWp.exe (PID: 5864)
- ULRKwx3iR5VJqNbLaeyIW54j.exe (PID: 6976)
- rg1qP67.exe (PID: 4668)
- InstallUtil.exe (PID: 4916)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- Vx9XK71.exe (PID: 7548)
- CnU05d0R1X160oSaoMyxrsaD.exe (PID: 7176)
- x0RPFql2zaxOzeAaN8s3QFfO.exe (PID: 7344)
- Tf5ss65.exe (PID: 4016)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- xqRPslL.exe (PID: 5592)
- InstallUtil.exe (PID: 3880)
- P3jb1n2rFq0ez3JUkuovAZXe.exe (PID: 7188)
- fyuhvPv42QHuU13Up4YJsw8l.exe (PID: 7072)
- 8QQnvSudgWkiVzXWct9iPrdG.exe (PID: 8288)
- Install.exe (PID: 8532)
- HNXZXKK.exe (PID: 6028)
- nb5XL55.exe (PID: 7328)
- himeffectively.exe (PID: 9156)
Changes the autorun value in the registry
- nhdues.exe (PID: 3728)
- oneetx.exe (PID: 5916)
Uses Task Scheduler to run other applications
- nhdues.exe (PID: 3728)
- Install.exe (PID: 3964)
- explorer.exe (PID: 1944)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- oneetx.exe (PID: 5916)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- xqRPslL.exe (PID: 5592)
- Install.exe (PID: 3340)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- HNXZXKK.exe (PID: 6028)
Creates a writable file the system directory
- svchost.exe (PID: 884)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- XPcwXmnXG4RB07G5BG31ozqo.exe (PID: 4120)
- lsass.exe (PID: 500)
- TrustedInstaller.exe (PID: 5012)
- services.exe (PID: 484)
- powershell.exe (PID: 2932)
Steals credentials from Web Browsers
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- AppLaunch.exe (PID: 3112)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
- HNXZXKK.exe (PID: 6028)
Steals credentials
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- explorer.exe (PID: 5536)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
ARKEI was detected
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
Loads dropped or rewritten executable
- YXuxjkH0cjyYMk3BbK2UzqlL.exe (PID: 792)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- rundll32.exe (PID: 4584)
- OBezVevHKAJ2UV1nNQKZcbBI.exe (PID: 4940)
- cgKIS14C6q1NoChphhrRLrDB.tmp (PID: 4104)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- SKDGRzQaLrdorjBgweAuc5lQ.exe (PID: 5636)
- BqsrfKeKClGgpr7HLZodSKqw.exe (PID: 2932)
Starts CMD.EXE for self-deleting
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- untilmathematics.exe (PID: 5140)
Application was injected by another process
- explorer.exe (PID: 1944)
- svchost.exe (PID: 780)
- wmpnetwk.exe (PID: 1104)
- svchost.exe (PID: 608)
- svchost.exe (PID: 884)
- svchost.exe (PID: 1056)
- spoolsv.exe (PID: 1028)
- svchost.exe (PID: 324)
- svchost.exe (PID: 852)
- IMEDICTUPDATE.EXE (PID: 1244)
- svchost.exe (PID: 1956)
- winlogon.exe (PID: 448)
- lsass.exe (PID: 500)
- services.exe (PID: 484)
- lsm.exe (PID: 508)
- svchost.exe (PID: 692)
- svchost.exe (PID: 824)
- dllhost.exe (PID: 2052)
- taskeng.exe (PID: 4000)
- dwm.exe (PID: 1884)
- svchost.exe (PID: 1184)
- conhost.exe (PID: 4696)
- conhost.exe (PID: 6116)
- svchost.exe (PID: 3160)
- conhost.exe (PID: 5212)
- TrustedInstaller.exe (PID: 5012)
- conhost.exe (PID: 6372)
- conhost.exe (PID: 6864)
- taskeng.exe (PID: 6716)
- conhost.exe (PID: 2504)
- conhost.exe (PID: 2900)
- conhost.exe (PID: 7044)
- conhost.exe (PID: 3912)
- svchost.exe (PID: 1708)
- conhost.exe (PID: 6740)
- conhost.exe (PID: 4528)
- conhost.exe (PID: 5168)
- conhost.exe (PID: 4332)
- conhost.exe (PID: 6932)
- conhost.exe (PID: 4028)
- conhost.exe (PID: 7932)
- conhost.exe (PID: 8172)
- conhost.exe (PID: 7804)
- conhost.exe (PID: 7448)
- conhost.exe (PID: 8048)
- conhost.exe (PID: 7836)
- conhost.exe (PID: 8004)
- conhost.exe (PID: 7160)
- conhost.exe (PID: 7064)
- conhost.exe (PID: 4312)
- conhost.exe (PID: 7964)
- conhost.exe (PID: 6012)
- conhost.exe (PID: 6772)
- conhost.exe (PID: 3024)
- conhost.exe (PID: 3704)
- conhost.exe (PID: 8016)
- conhost.exe (PID: 6960)
- conhost.exe (PID: 2004)
- conhost.exe (PID: 7392)
- conhost.exe (PID: 7620)
- conhost.exe (PID: 7072)
- conhost.exe (PID: 6044)
- conhost.exe (PID: 2336)
- conhost.exe (PID: 3108)
- conhost.exe (PID: 6960)
- conhost.exe (PID: 6604)
- conhost.exe (PID: 7472)
- conhost.exe (PID: 7680)
- conhost.exe (PID: 7564)
- conhost.exe (PID: 7880)
- conhost.exe (PID: 4324)
- conhost.exe (PID: 6148)
- conhost.exe (PID: 6488)
- conhost.exe (PID: 4776)
- conhost.exe (PID: 7764)
- conhost.exe (PID: 8108)
- conhost.exe (PID: 4804)
- conhost.exe (PID: 6284)
- conhost.exe (PID: 6196)
- conhost.exe (PID: 4284)
- conhost.exe (PID: 4780)
- conhost.exe (PID: 1984)
- conhost.exe (PID: 8096)
- conhost.exe (PID: 3664)
- conhost.exe (PID: 7572)
- conhost.exe (PID: 7808)
- conhost.exe (PID: 7492)
- conhost.exe (PID: 8368)
- conhost.exe (PID: 8912)
- conhost.exe (PID: 9208)
- conhost.exe (PID: 9108)
- conhost.exe (PID: 7776)
- conhost.exe (PID: 5996)
- conhost.exe (PID: 8528)
- conhost.exe (PID: 8616)
- conhost.exe (PID: 8124)
- conhost.exe (PID: 8272)
- conhost.exe (PID: 8404)
- conhost.exe (PID: 2904)
- conhost.exe (PID: 8972)
- conhost.exe (PID: 5068)
- conhost.exe (PID: 7832)
- conhost.exe (PID: 7608)
- conhost.exe (PID: 7560)
- conhost.exe (PID: 4776)
- conhost.exe (PID: 8012)
- conhost.exe (PID: 9052)
- conhost.exe (PID: 7588)
- conhost.exe (PID: 8224)
- conhost.exe (PID: 4264)
- conhost.exe (PID: 7728)
- conhost.exe (PID: 7588)
Runs injected code in another process
- K3AidViq3fu5I0UKoDhvimK1.exe (PID: 3620)
- LhzwzpX5CoXjD1kfEk3zTdEj.exe (PID: 2476)
- QIPR1ptbkPFZQ5thhYbsDOLW.exe (PID: 4396)
- FFvUvYbdQ3pjTyFDA4WuM6Yr.exe (PID: 4988)
- 0X2VWPeOtWsJzActynA8jUp3.exe (PID: 3400)
- dialer.exe (PID: 4208)
PRIVATELOADER was detected
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- XPcwXmnXG4RB07G5BG31ozqo.exe (PID: 4120)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- 39FAQZKOIFCH_3zOZOXG9Eit.exe (PID: 5396)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- Ovhlx8nFAQOOvWEVPt74gNgq.exe (PID: 8080)
Actions looks like stealing of personal data
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- vbc.exe (PID: 4964)
- CeXhyH7QAVA1fsMjxdS_ql2i.exe (PID: 2176)
- explorer.exe (PID: 5536)
- AppLaunch.exe (PID: 4672)
- AppLaunch.exe (PID: 3112)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- AppLaunch.exe (PID: 4892)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- certreq.exe (PID: 4984)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- untilmathematics.exe (PID: 5140)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- xqRPslL.exe (PID: 5592)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- VX6MxNHHzpIMgwuLaadgabw3.exe (PID: 5500)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- AppLaunch.exe (PID: 6396)
- AppLaunch.exe (PID: 6444)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- HNXZXKK.exe (PID: 6028)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
Connects to the CnC server
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- vbc.exe (PID: 4964)
- explorer.exe (PID: 1944)
- CeXhyH7QAVA1fsMjxdS_ql2i.exe (PID: 2176)
- AppLaunch.exe (PID: 4672)
- RZbl0lR98O6Qhs7pebM5pNhE.exe (PID: 3796)
- AppLaunch.exe (PID: 3112)
- AppLaunch.exe (PID: 4892)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- XPcwXmnXG4RB07G5BG31ozqo.exe (PID: 4120)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- explorer.exe (PID: 5076)
- 2pr5983.exe (PID: 5128)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- explorer.exe (PID: 5536)
- VX6MxNHHzpIMgwuLaadgabw3.exe (PID: 5500)
- ffUbNlFyy94bJxTL_5Ig97z6.exe (PID: 1076)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- 39FAQZKOIFCH_3zOZOXG9Eit.exe (PID: 5396)
- vbc.exe (PID: 3144)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- 4WD828Ic.exe (PID: 5668)
- untilmathematics.exe (PID: 5140)
- AppLaunch.exe (PID: 6444)
- Uue0d0frXqEkX6JcnasnNNbd.exe (PID: 6952)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- AppLaunch.exe (PID: 2344)
- AppLaunch.exe (PID: 6396)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- oneetx.exe (PID: 5916)
- vbc.exe (PID: 4124)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- 45SOoUJQUZuPF31kWHwCDbqW.exe (PID: 6936)
- Ovhlx8nFAQOOvWEVPt74gNgq.exe (PID: 8080)
Run PowerShell with an invisible window
- powershell.EXE (PID: 1364)
- powershell.EXE (PID: 3756)
Adds path to the Windows Defender exclusion list
- explorer.exe (PID: 1944)
AMADEY has been detected (YARA)
- nhdues.exe (PID: 3728)
- oneetx.exe (PID: 5916)
OSKI has been detected (YARA)
- RZbl0lR98O6Qhs7pebM5pNhE.exe (PID: 3796)
- ffUbNlFyy94bJxTL_5Ig97z6.exe (PID: 1076)
STEALC has been detected (YARA)
- RZbl0lR98O6Qhs7pebM5pNhE.exe (PID: 3796)
- ffUbNlFyy94bJxTL_5Ig97z6.exe (PID: 1076)
PRIVATELOADER has been detected (YARA)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
RISEPRO was detected
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- IEUpdater1.exe (PID: 3808)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
REDLINE has been detected (YARA)
- CeXhyH7QAVA1fsMjxdS_ql2i.exe (PID: 2176)
- vbc.exe (PID: 4964)
- AppLaunch.exe (PID: 4892)
- VX6MxNHHzpIMgwuLaadgabw3.exe (PID: 5500)
- vbc.exe (PID: 3144)
RISEPRO has been detected (YARA)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- IEUpdater1.exe (PID: 3808)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
REDLINE has been detected (SURICATA)
- vbc.exe (PID: 4964)
Creates or modifies Windows services
- services.exe (PID: 484)
SMOKE was detected
- explorer.exe (PID: 1944)
- explorer.exe (PID: 5076)
- explorer.exe (PID: 5536)
REDLINE was detected
- CeXhyH7QAVA1fsMjxdS_ql2i.exe (PID: 2176)
- AppLaunch.exe (PID: 4672)
- AppLaunch.exe (PID: 3112)
- AppLaunch.exe (PID: 4892)
- VX6MxNHHzpIMgwuLaadgabw3.exe (PID: 5500)
- vbc.exe (PID: 3144)
- 4WD828Ic.exe (PID: 5668)
- AppLaunch.exe (PID: 6444)
- AppLaunch.exe (PID: 6396)
- AppLaunch.exe (PID: 2344)
- vbc.exe (PID: 4124)
- 45SOoUJQUZuPF31kWHwCDbqW.exe (PID: 6936)
Modifies hosts file to block updates
- zsWklsWnSwufAN7TKspgweE3.exe (PID: 2180)
- fvSjc99mxBf23smnXhkyisRs.exe (PID: 5104)
Disables Windows Defender
- 1lP68aL0.exe (PID: 3356)
- 1lP68aL0.exe (PID: 2688)
Unusual connection from system programs
- vbc.exe (PID: 4964)
- explorer.exe (PID: 5536)
- vbc.exe (PID: 3144)
- vbc.exe (PID: 4124)
STEALC was detected
- RZbl0lR98O6Qhs7pebM5pNhE.exe (PID: 3796)
- 2pr5983.exe (PID: 5128)
- ffUbNlFyy94bJxTL_5Ig97z6.exe (PID: 1076)
- Uue0d0frXqEkX6JcnasnNNbd.exe (PID: 6952)
Uses Task Scheduler to autorun other applications
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- powershell.exe (PID: 6900)
- HNXZXKK.exe (PID: 6028)
ARKEI has been detected (YARA)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- build2.exe (PID: 2476)
- BOkUTx0iwlgh3MRNoF7OvgaQ.exe (PID: 5880)
RHADAMANTHYS was detected
- arriveprospect.exe (PID: 5056)
Stop is detected
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 5456)
VODKAGATS was detected
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 5456)
LUMMA was detected
- untilmathematics.exe (PID: 5140)
AMADEY was detected
- oneetx.exe (PID: 5916)
Changes the Windows auto-update feature
- 1lP68aL0.exe (PID: 2688)
SUSPICIOUS
Reads settings of System Certificates
- InstallUtil.exe (PID: 2556)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- InstallUtil.exe (PID: 4828)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 4592)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- XPcwXmnXG4RB07G5BG31ozqo.exe (PID: 4120)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 5456)
- cgKIS14C6q1NoChphhrRLrDB.tmp (PID: 4104)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- InstallUtil.exe (PID: 924)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5472)
- 39FAQZKOIFCH_3zOZOXG9Eit.exe (PID: 5396)
- InstallUtil.exe (PID: 2436)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- InstallUtil.exe (PID: 4916)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
- InstallUtil.exe (PID: 3880)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 8104)
- Ovhlx8nFAQOOvWEVPt74gNgq.exe (PID: 8080)
Reads the Internet Settings
- InstallUtil.exe (PID: 2556)
- q8OSAEnVHW3WkRgcmKQ0dUXZ.exe (PID: 3412)
- nhdues.exe (PID: 3728)
- arriveprospect.exe (PID: 3012)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- Install.exe (PID: 3964)
- InstallUtil.exe (PID: 4828)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 4592)
- control.exe (PID: 4572)
- powershell.exe (PID: 2900)
- RZbl0lR98O6Qhs7pebM5pNhE.exe (PID: 3796)
- cmd.exe (PID: 4856)
- arriiveprospect.exe (PID: 2244)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- untilmathematics.exe (PID: 4852)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- cgKIS14C6q1NoChphhrRLrDB.tmp (PID: 4104)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 5456)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- powershell.EXE (PID: 1364)
- uhxRUj5DV1cfZSEfD3bMoZUr.exe (PID: 5556)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- explorer.exe (PID: 5536)
- InstallUtil.exe (PID: 924)
- 2pr5983.exe (PID: 5128)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5472)
- ffUbNlFyy94bJxTL_5Ig97z6.exe (PID: 1076)
- oneetx.exe (PID: 5916)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- InstallUtil.exe (PID: 2436)
- Install.exe (PID: 3340)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- untilmathematics.exe (PID: 5140)
- untilmathematiics.exe (PID: 4572)
- Uue0d0frXqEkX6JcnasnNNbd.exe (PID: 6952)
- InstallUtil.exe (PID: 4916)
- Install.exe (PID: 6940)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- Install.exe (PID: 6808)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- cmd.exe (PID: 6004)
- control.exe (PID: 6224)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- InstallUtil.exe (PID: 3880)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 8104)
- control.exe (PID: 4676)
- control.exe (PID: 8492)
Adds/modifies Windows certificates
- services.exe (PID: 484)
- InstallUtil.exe (PID: 2556)
- nF6mOdhRMpN3SGbQlrPIZdiL.exe (PID: 3980)
Starts itself from another location
- q8OSAEnVHW3WkRgcmKQ0dUXZ.exe (PID: 3412)
- mmUi7viccv48sJD1w9k4AuDs.exe (PID: 3140)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- uhxRUj5DV1cfZSEfD3bMoZUr.exe (PID: 5556)
- CjzLhIoubU6EOrERGzOsnpeU.exe (PID: 5148)
- TskS7iTuF1rMl02JwXmqAncH.exe (PID: 6296)
- Kj3JVsuQJB2IvbWqvZdsn4f7.exe (PID: 2548)
- fyuhvPv42QHuU13Up4YJsw8l.exe (PID: 7072)
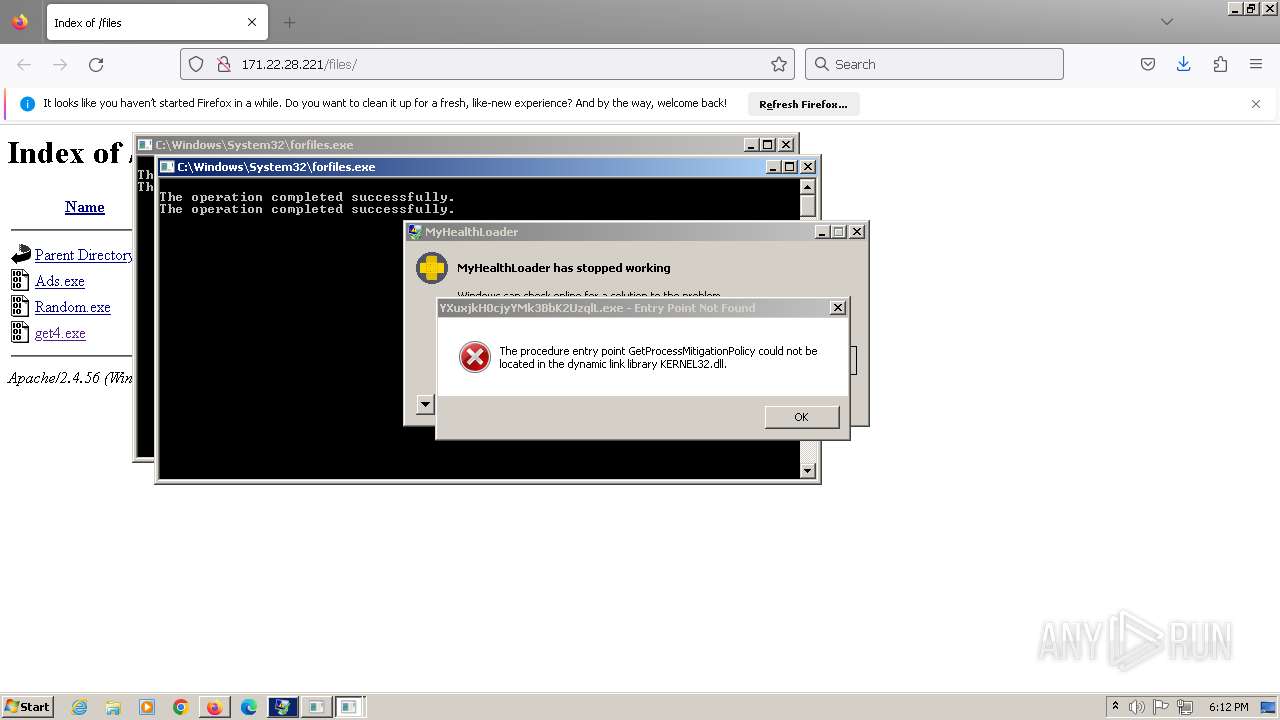
Starts CMD.EXE for commands execution
- nhdues.exe (PID: 3728)
- cmd.exe (PID: 2180)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- forfiles.exe (PID: 2652)
- forfiles.exe (PID: 3780)
- vAjmiB170tl4bIKZ5xUDpfrl.exe (PID: 1396)
- ix0VkCfPyhYNXlHNcxjuBwtF.exe (PID: 1828)
- explorer.exe (PID: 1944)
- a8XgakQfmwwdkpVYBMRsJHzX.exe (PID: 4608)
- ysGi5iID3g53tlkzaQbgcJJD.exe (PID: 5788)
- KibI8idbFuOXtShsGGds6DF3.exe (PID: 5856)
- oneetx.exe (PID: 5916)
- QeNz3MywCODuOxaYk85AqaYo.exe (PID: 5924)
- untilmathematics.exe (PID: 5140)
- cmd.exe (PID: 4052)
- xqRPslL.exe (PID: 5592)
- x0RPFql2zaxOzeAaN8s3QFfO.exe (PID: 7344)
- forfiles.exe (PID: 6872)
- P3jb1n2rFq0ez3JUkuovAZXe.exe (PID: 7188)
- HNXZXKK.exe (PID: 6028)
Application launched itself
- cmd.exe (PID: 2180)
- K3AidViq3fu5I0UKoDhvimK1.exe (PID: 3520)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 3876)
- arriveprospect.exe (PID: 3012)
- QIPR1ptbkPFZQ5thhYbsDOLW.exe (PID: 5024)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 4592)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 6072)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5284)
- build2.exe (PID: 5124)
- untilmathematics.exe (PID: 4852)
- 0X2VWPeOtWsJzActynA8jUp3.exe (PID: 4596)
- fMh25VTHm9OryG9HeJyynLMm.exe (PID: 6468)
- cmd.exe (PID: 4052)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5472)
- sYUFFPSWg8DtFkB2iv0yZAKN.exe (PID: 4112)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5068)
Connects to the server without a host name
- InstallUtil.exe (PID: 2556)
- arriveprospect.exe (PID: 3012)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- InstallUtil.exe (PID: 4828)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- untilmathematics.exe (PID: 4852)
- arriiveprospect.exe (PID: 2244)
- XPcwXmnXG4RB07G5BG31ozqo.exe (PID: 4120)
- 2pr5983.exe (PID: 5128)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- InstallUtil.exe (PID: 924)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- 39FAQZKOIFCH_3zOZOXG9Eit.exe (PID: 5396)
- InstallUtil.exe (PID: 2436)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- untilmathematiics.exe (PID: 4572)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- InstallUtil.exe (PID: 4916)
- oneetx.exe (PID: 5916)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- InstallUtil.exe (PID: 3880)
- Ovhlx8nFAQOOvWEVPt74gNgq.exe (PID: 8080)
Process requests binary or script from the Internet
- InstallUtil.exe (PID: 2556)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- InstallUtil.exe (PID: 4828)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 5456)
- InstallUtil.exe (PID: 924)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- InstallUtil.exe (PID: 2436)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- InstallUtil.exe (PID: 4916)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- InstallUtil.exe (PID: 3880)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2180)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 4592)
- cmd.exe (PID: 4052)
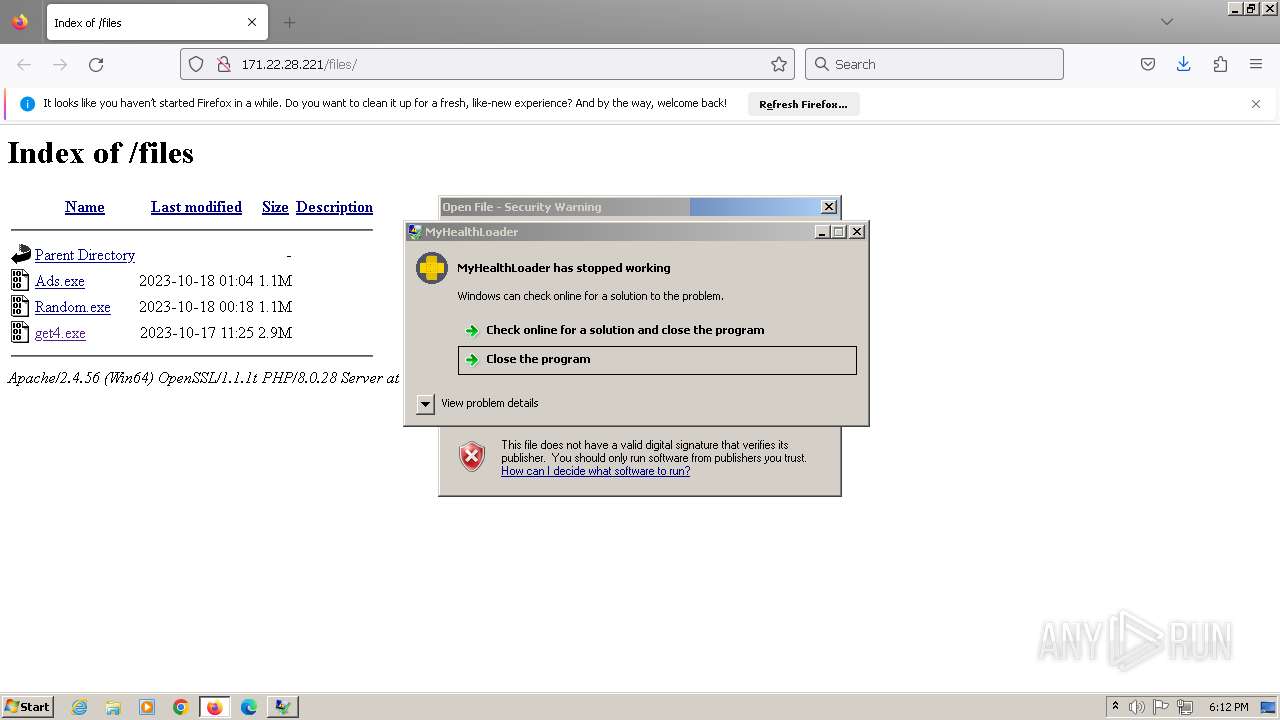
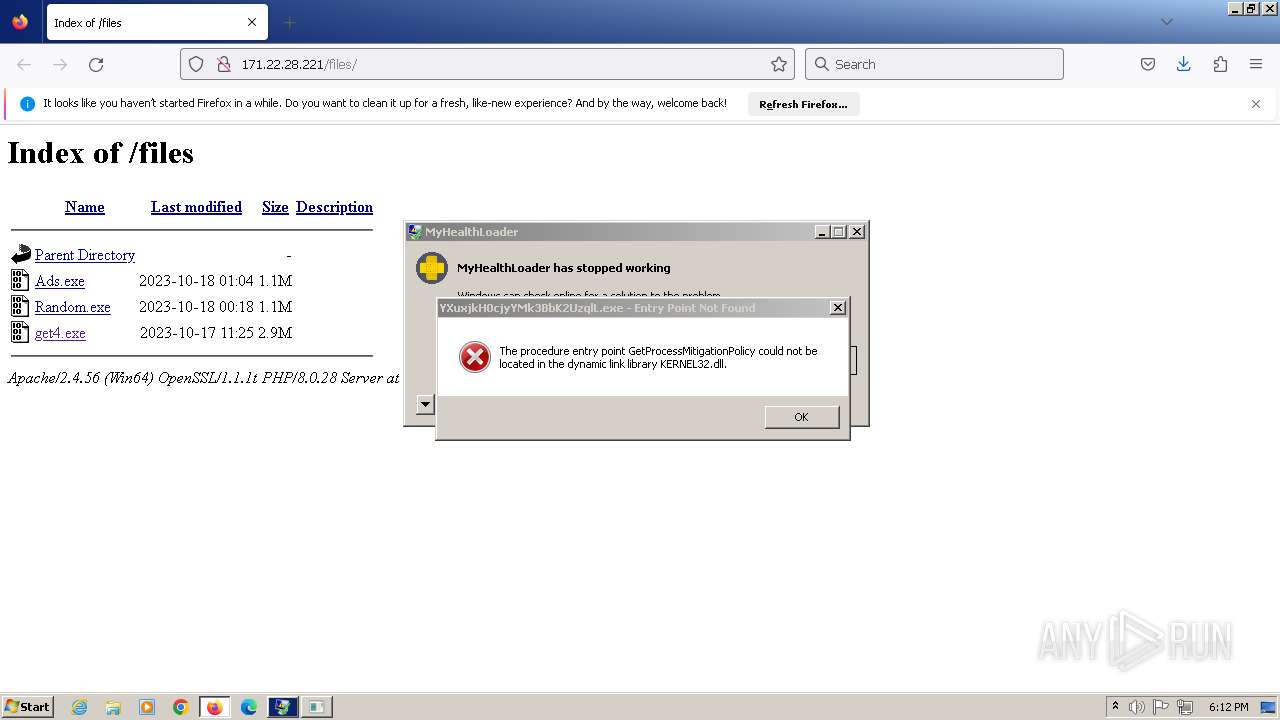
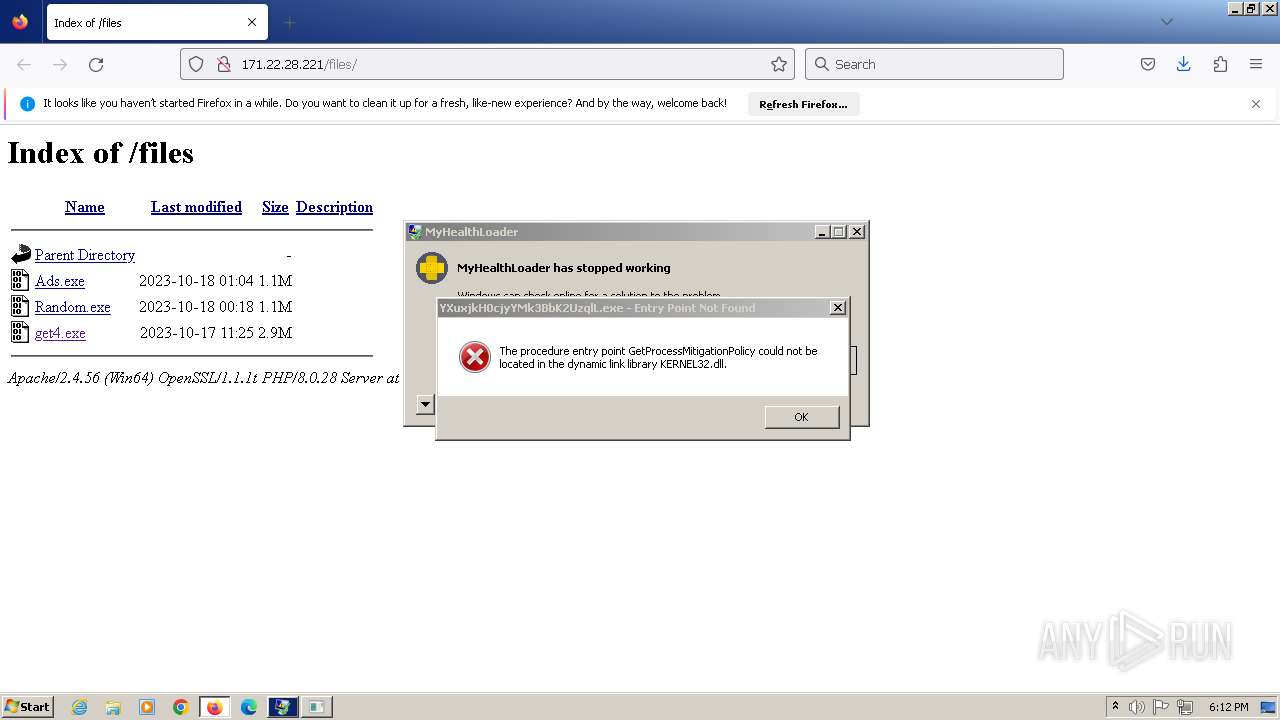
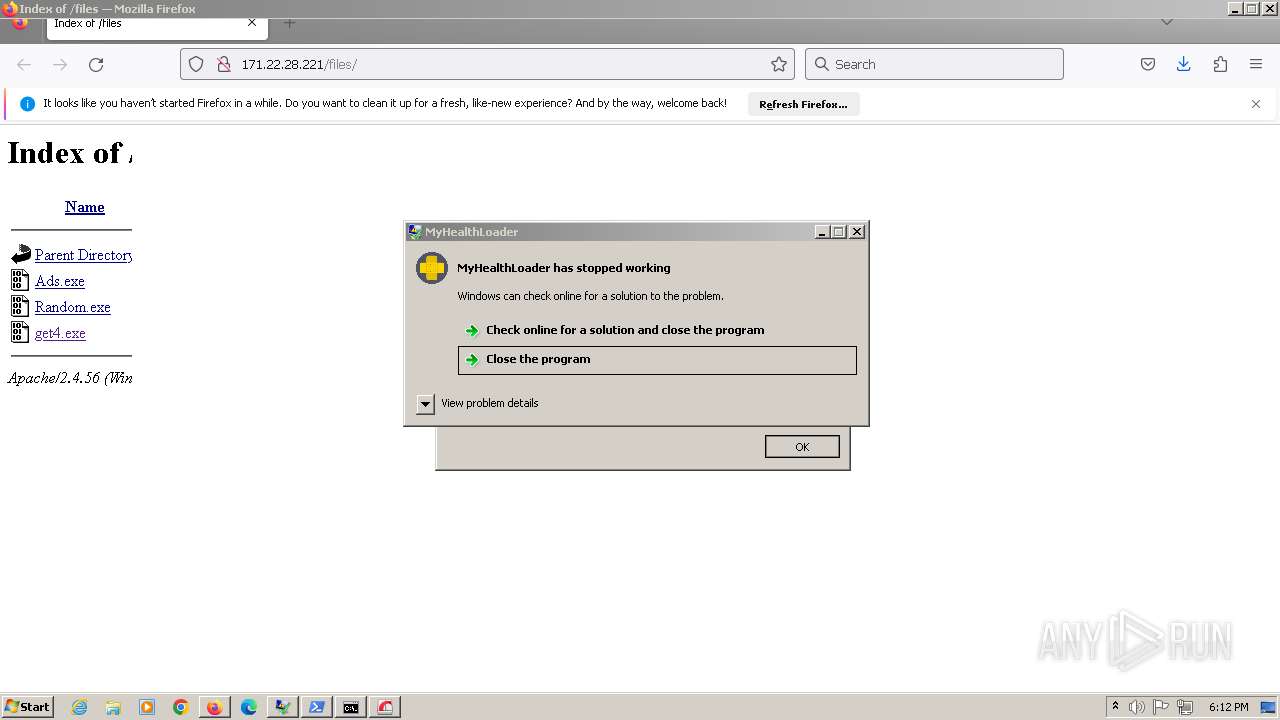
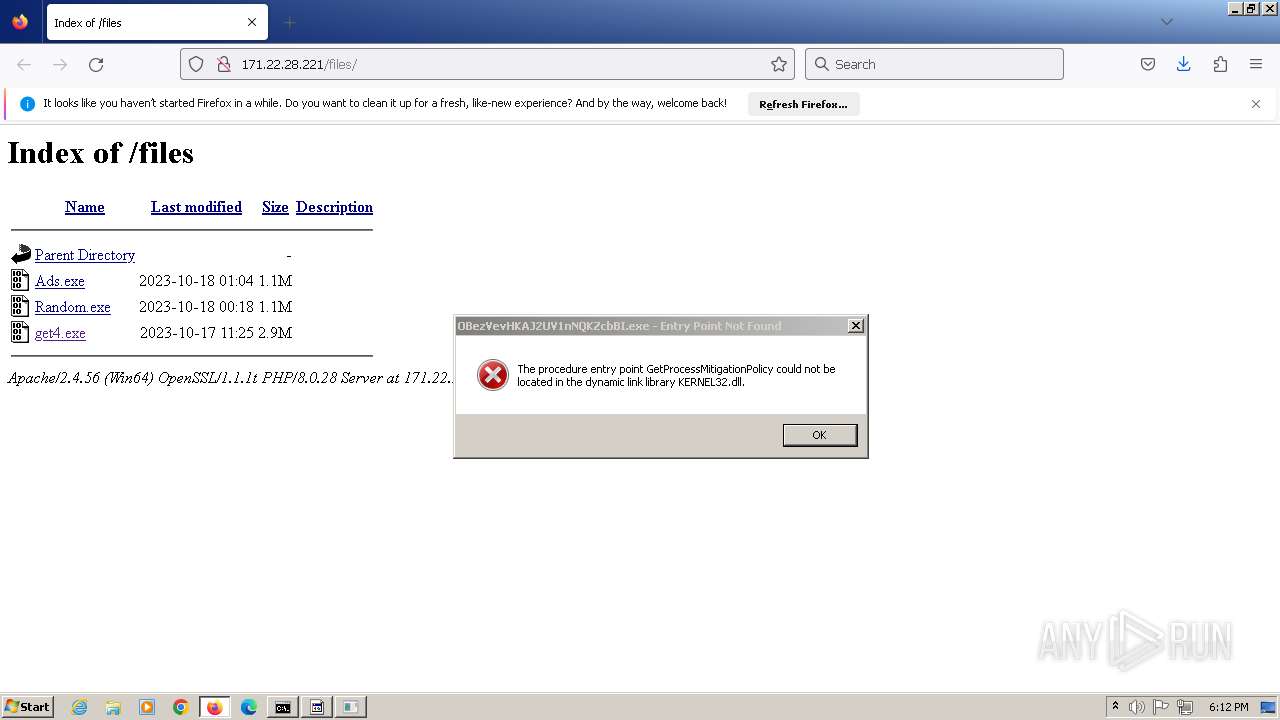
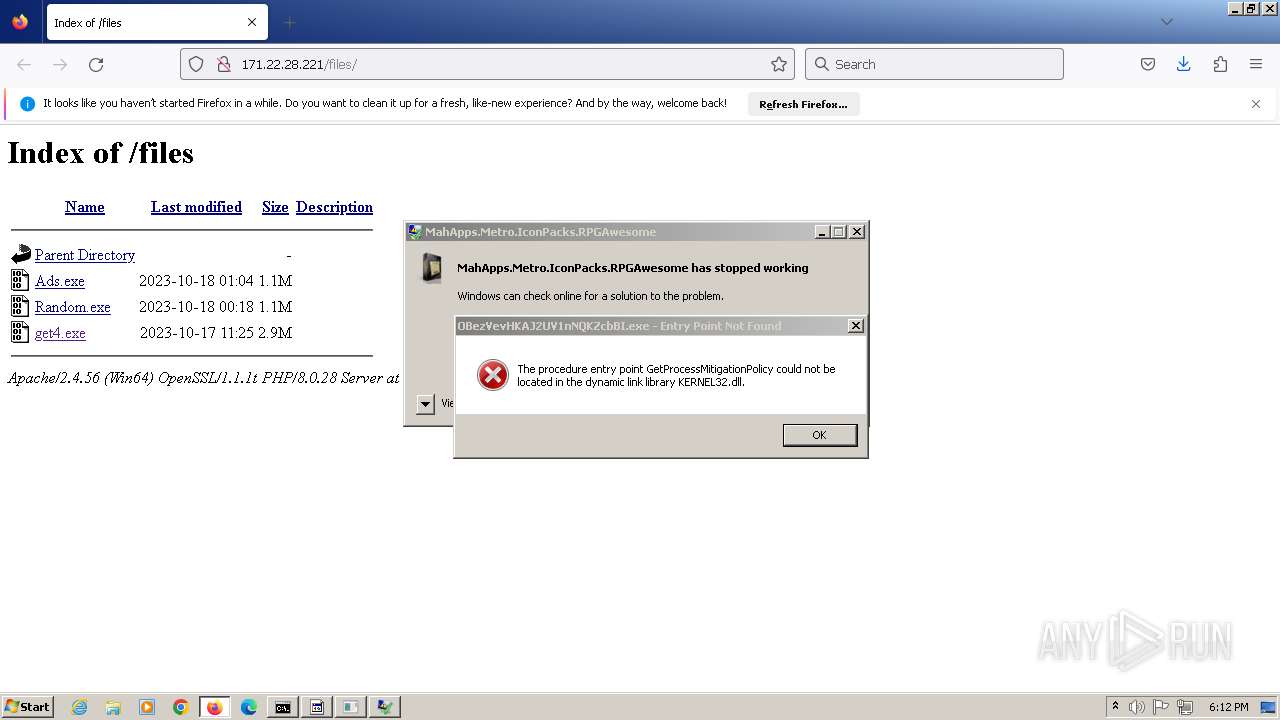
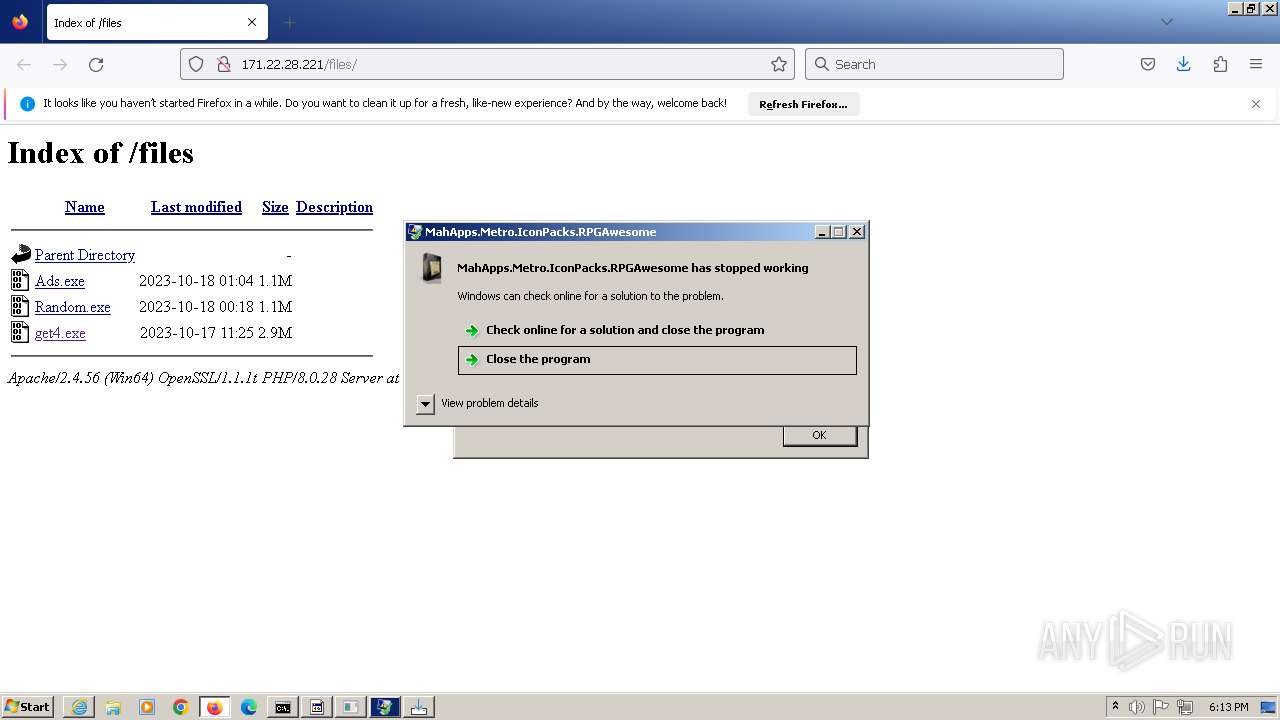
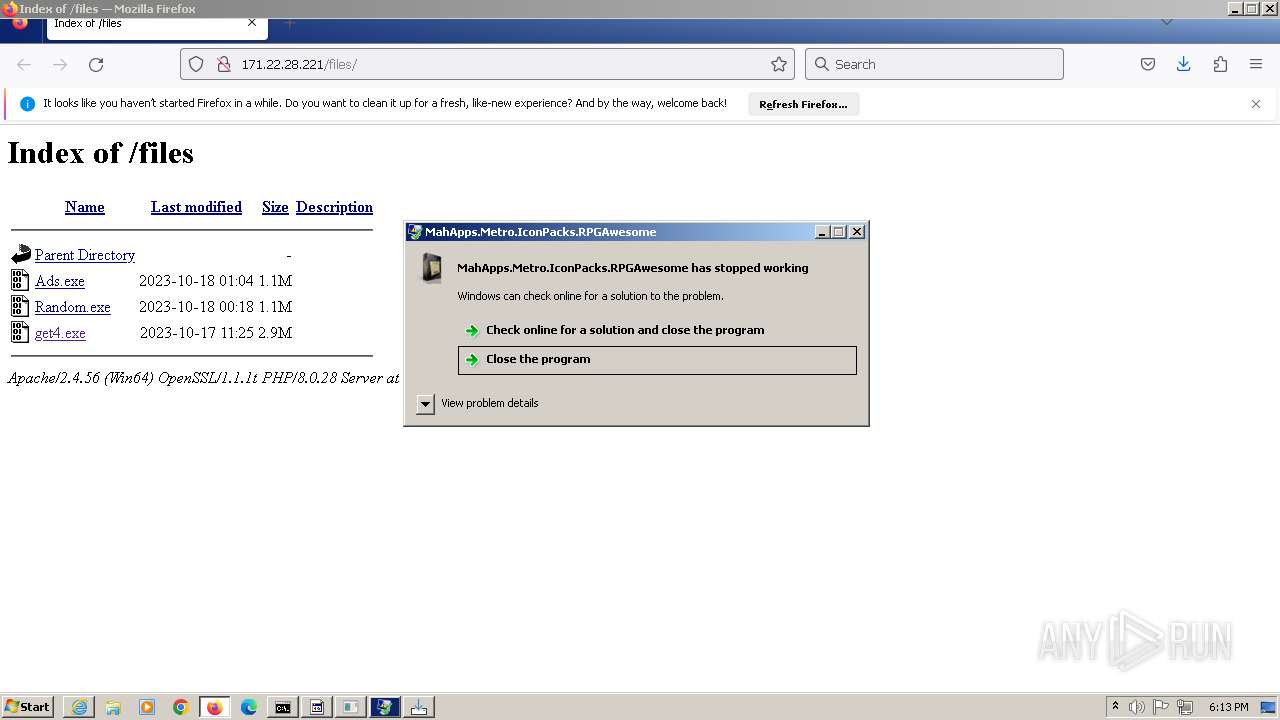
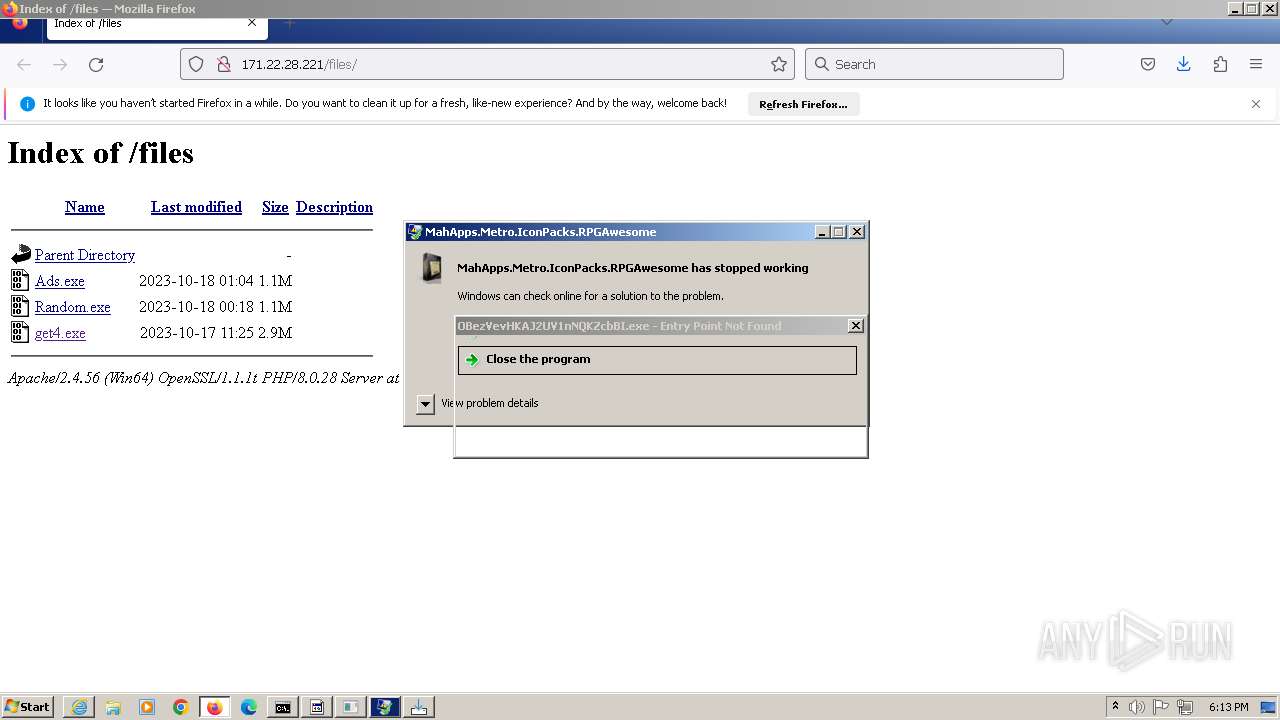
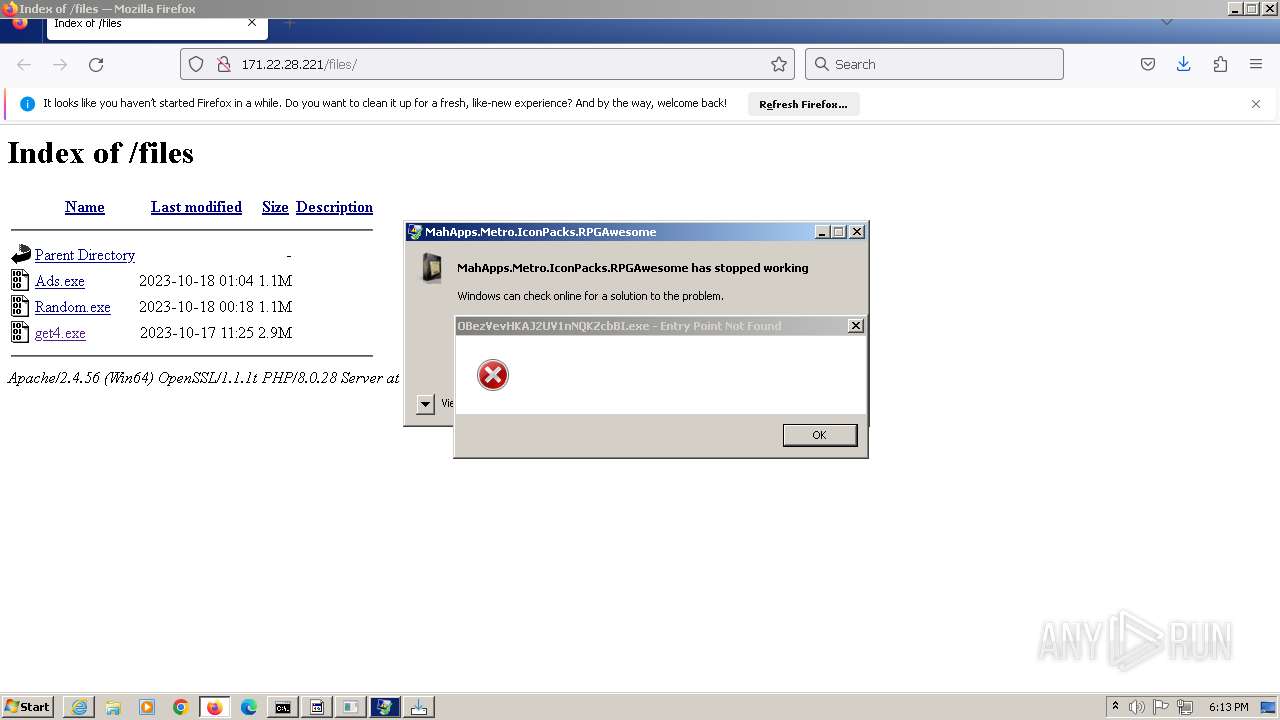
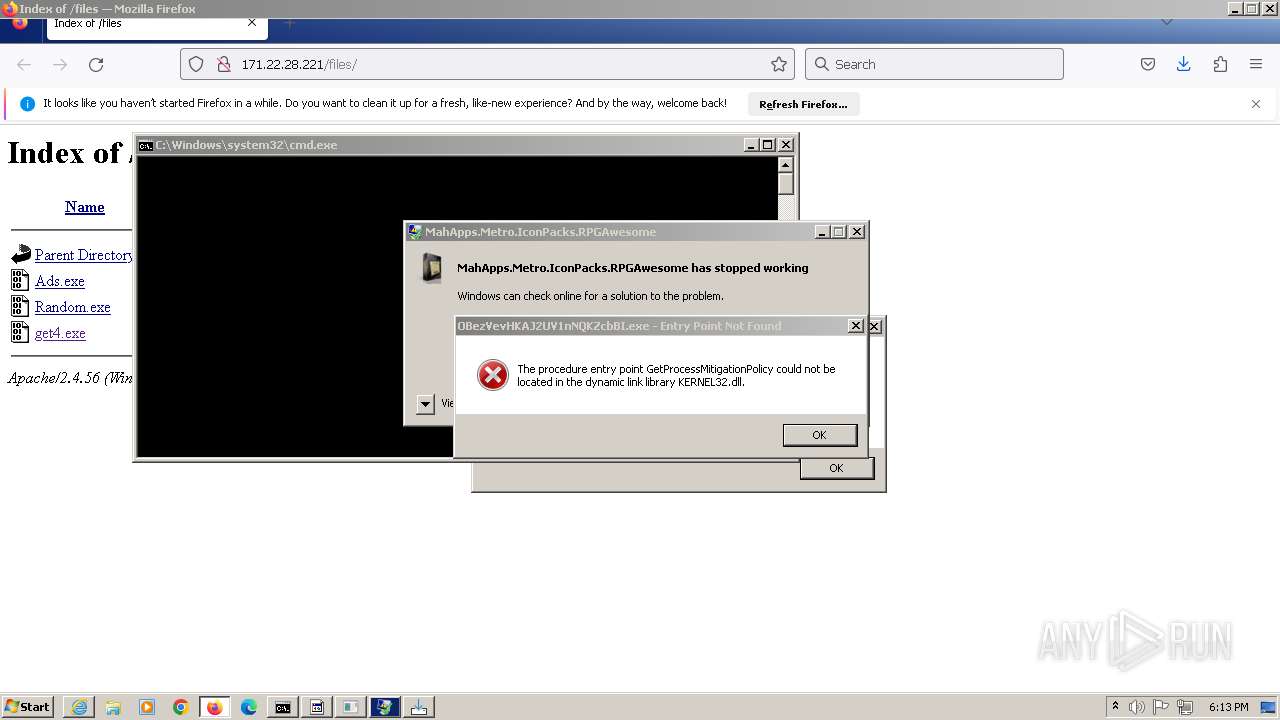
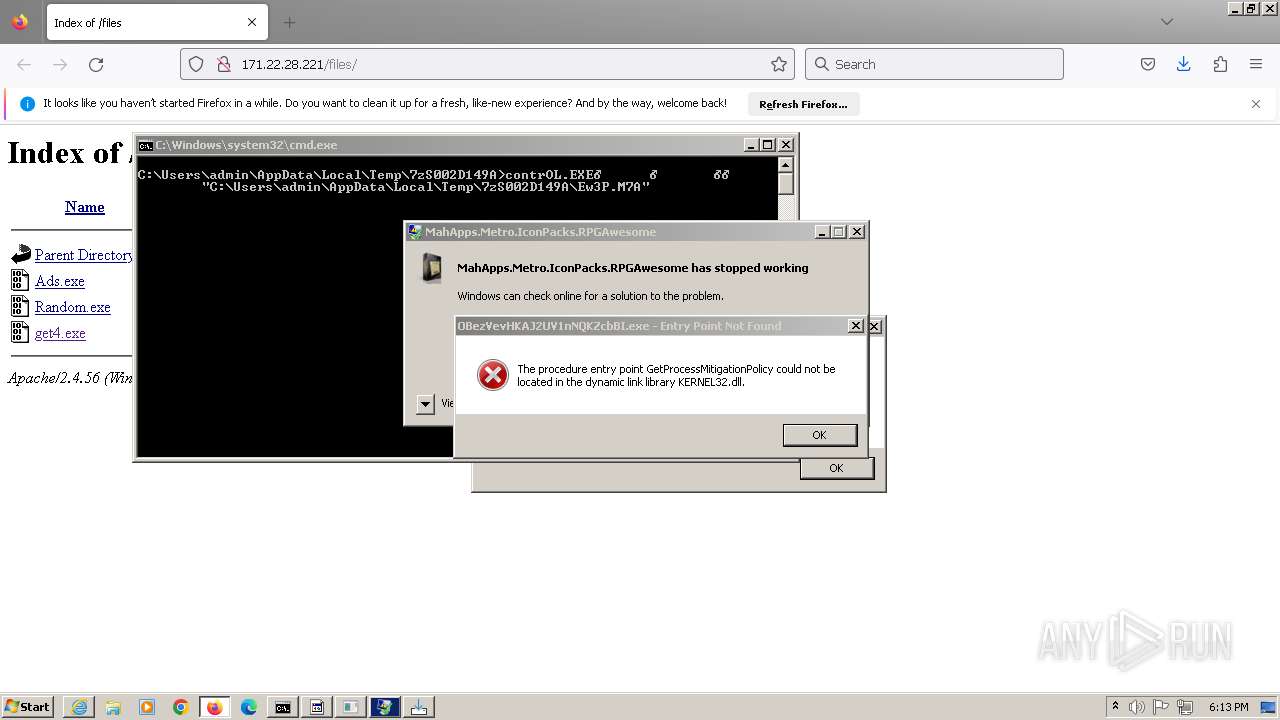
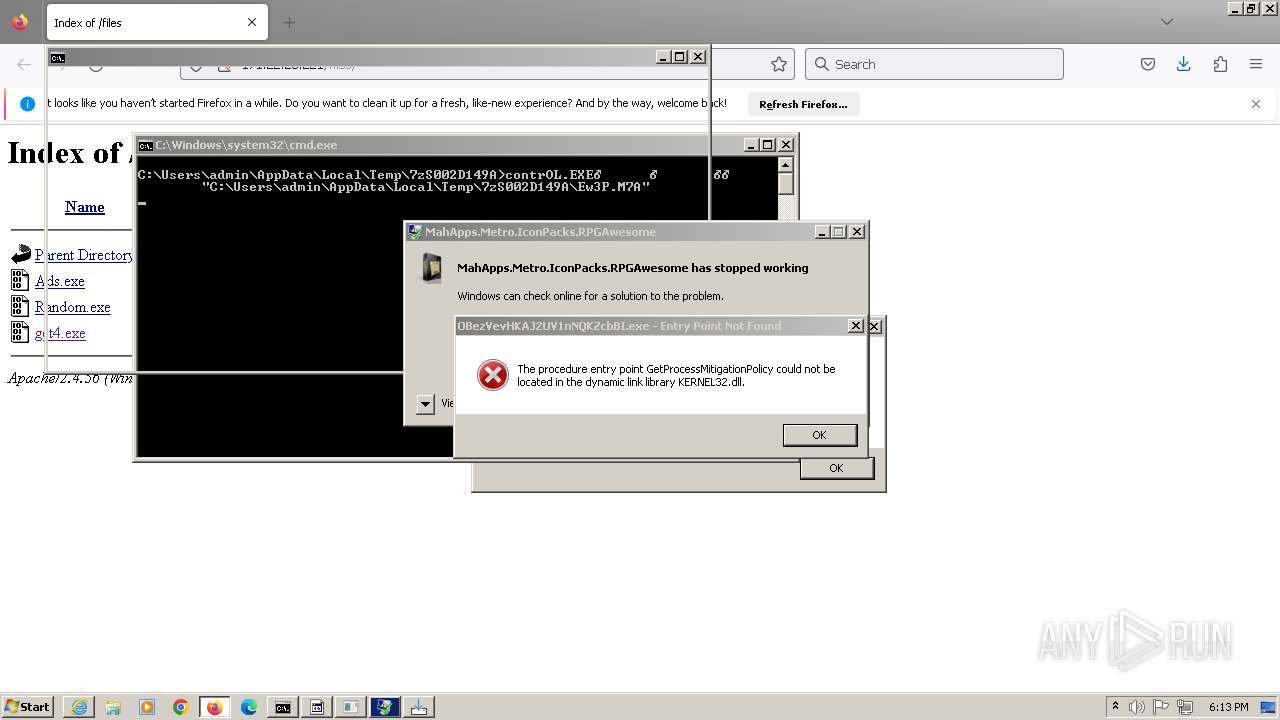
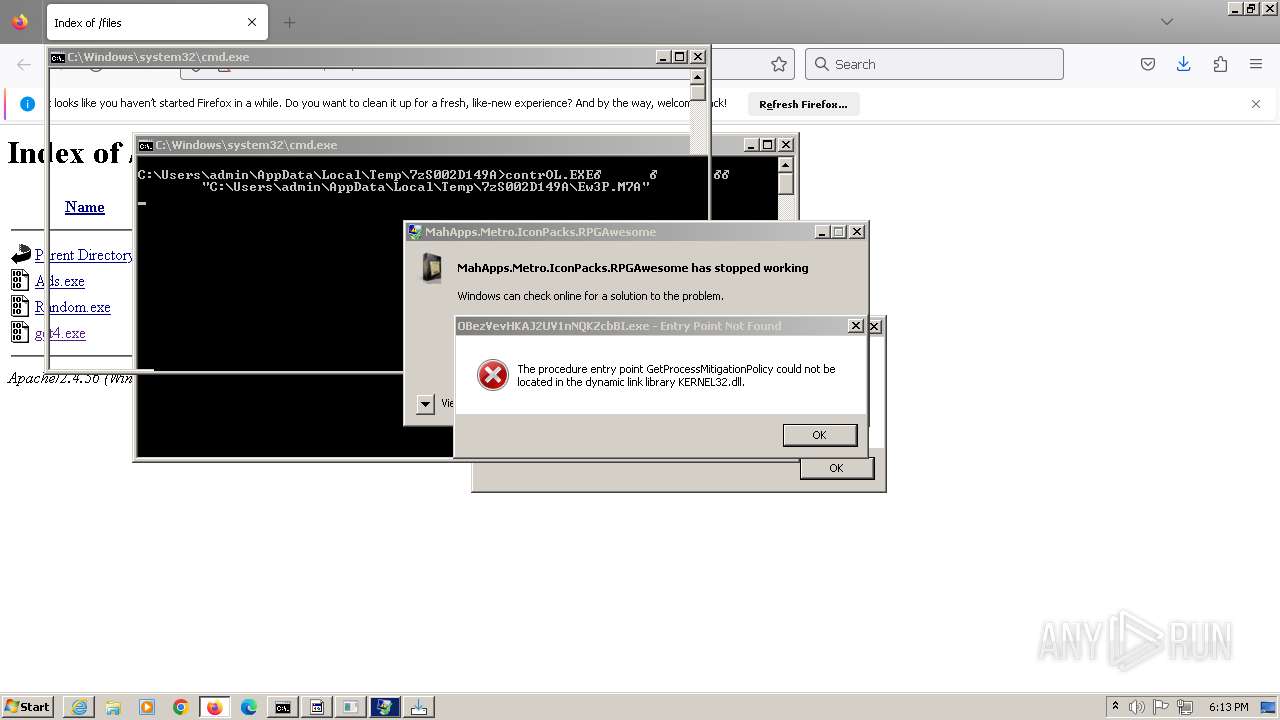
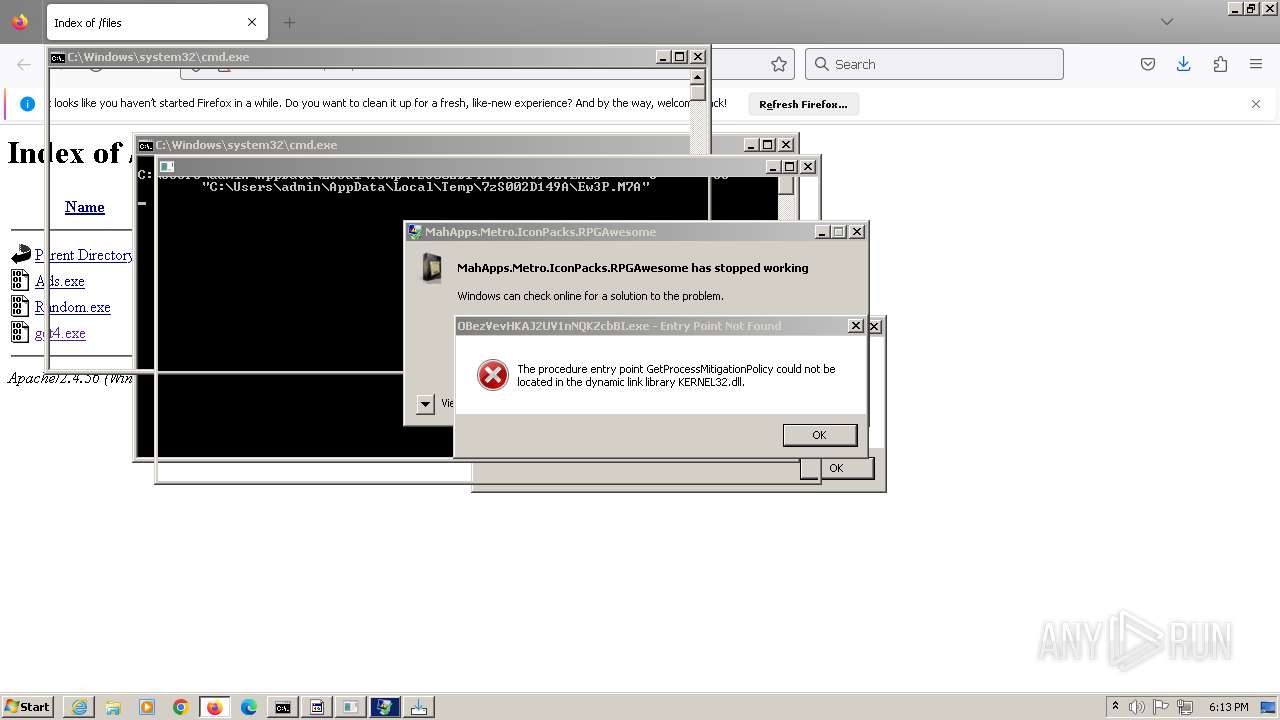
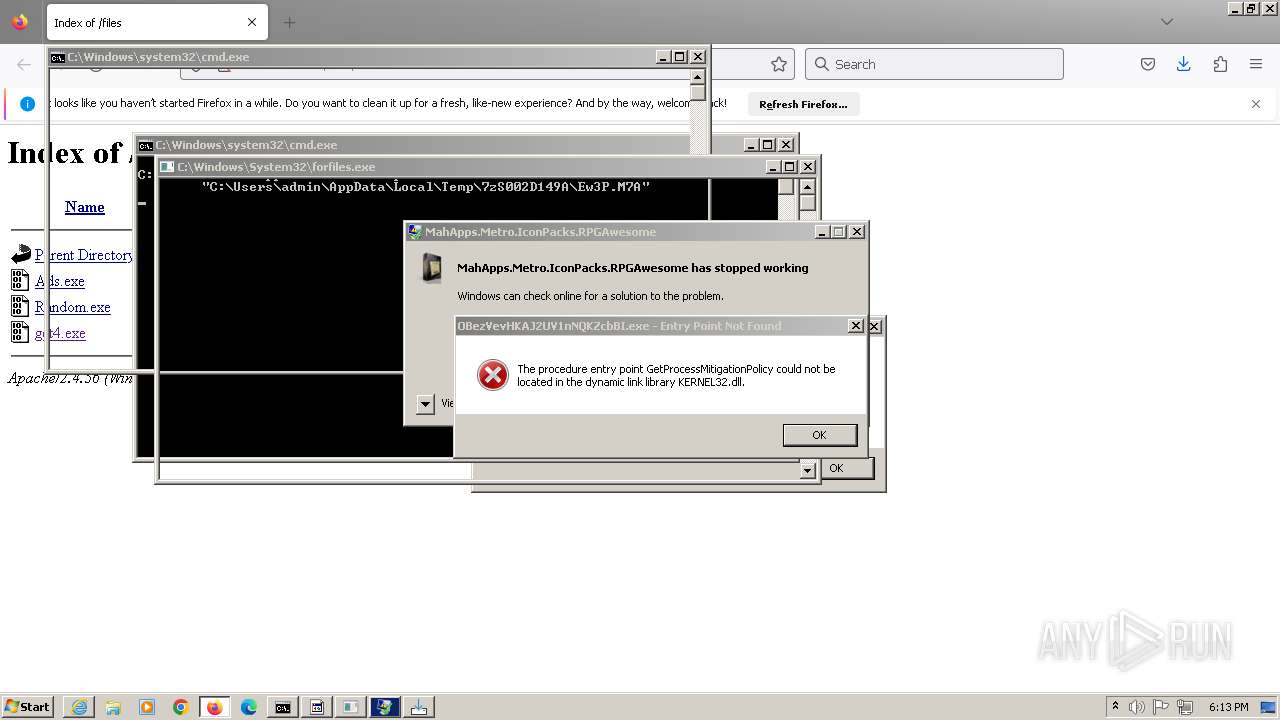
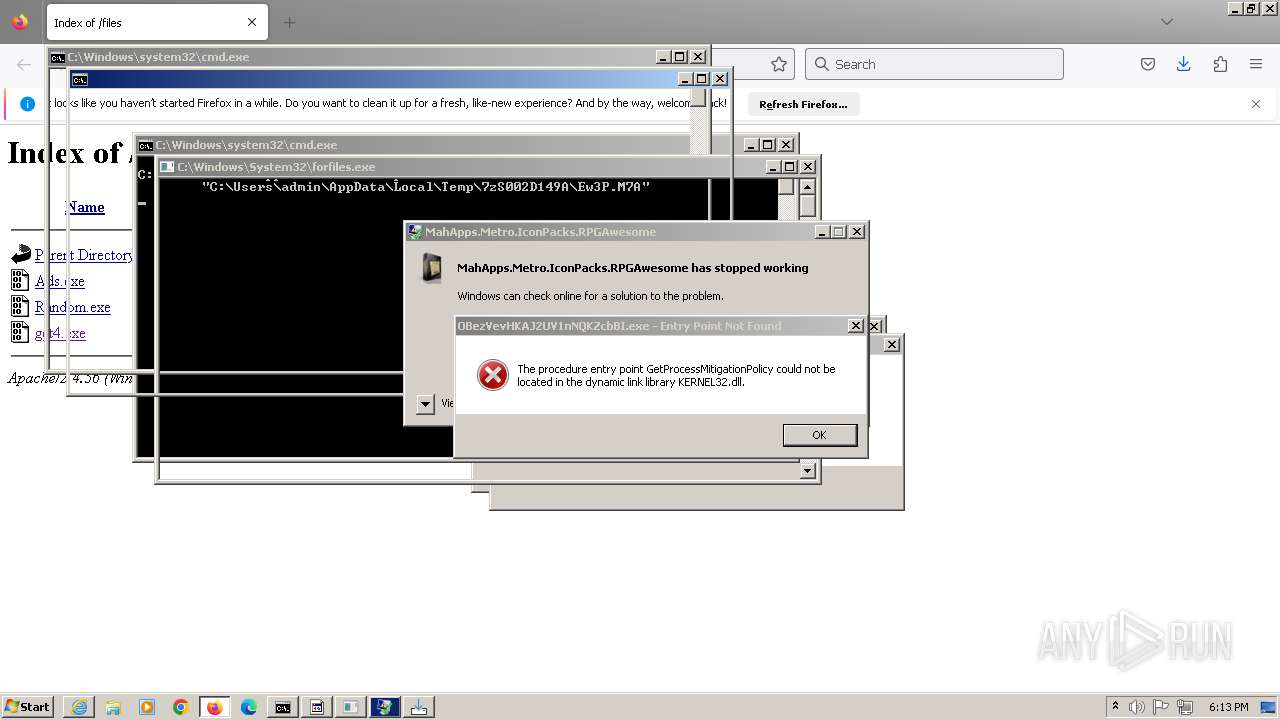
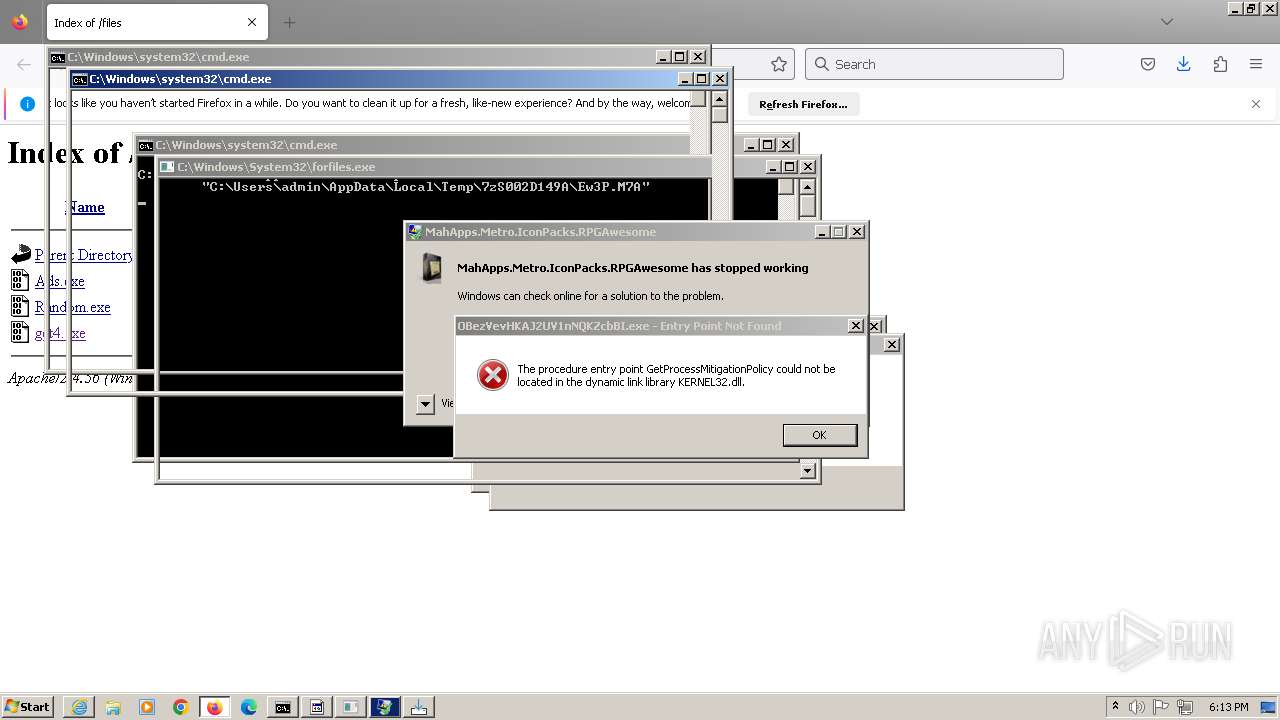
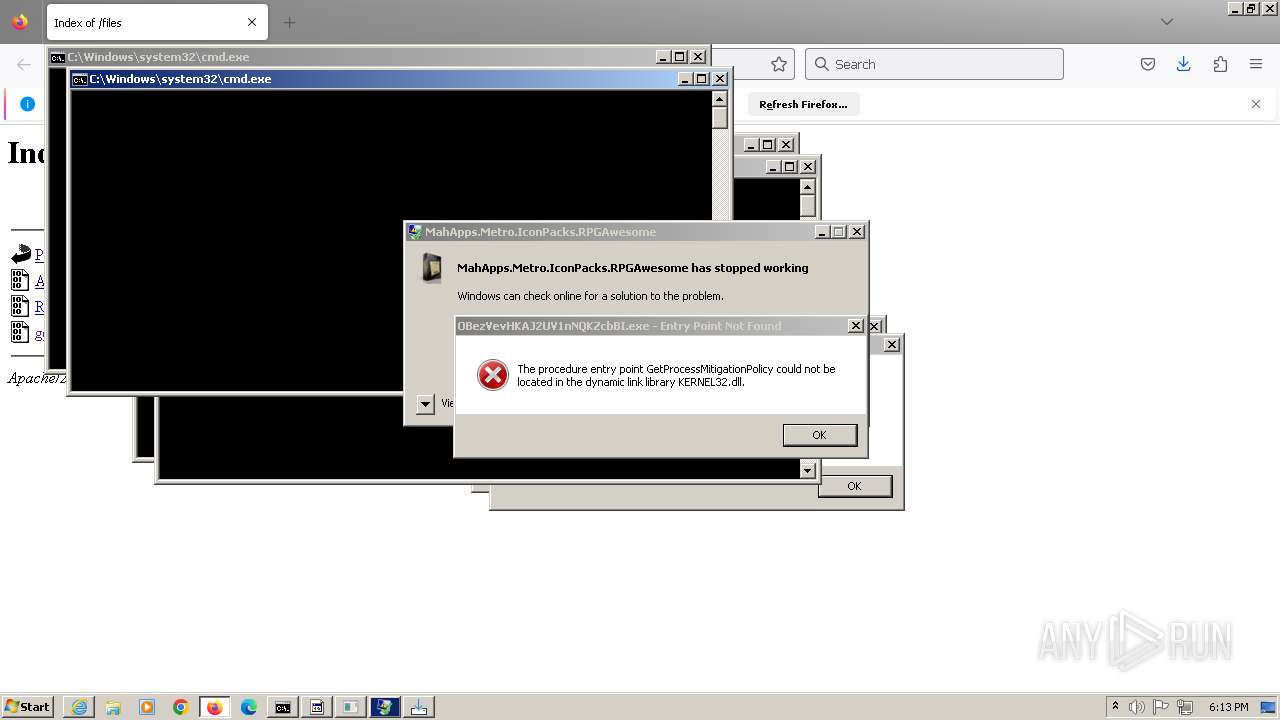
Executes application which crashes
- svchost.exe (PID: 3160)
Checks Windows Trust Settings
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 4592)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- cgKIS14C6q1NoChphhrRLrDB.tmp (PID: 4104)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 5456)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5472)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 8104)
Reads security settings of Internet Explorer
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 4592)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- cgKIS14C6q1NoChphhrRLrDB.tmp (PID: 4104)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 5456)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5472)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 8104)
The process drops C-runtime libraries
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
The process drops Mozilla's DLL files
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
Process drops legitimate windows executable
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- vAjmiB170tl4bIKZ5xUDpfrl.exe (PID: 1396)
- lYUgfzizvypmRH9zJmFjirkj.exe (PID: 2240)
- Tf5ss65.exe (PID: 4628)
- nb5XL55.exe (PID: 4784)
- rg1qP67.exe (PID: 684)
- ix0VkCfPyhYNXlHNcxjuBwtF.exe (PID: 1828)
- himeffectively.exe (PID: 3012)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- 1vaFjymLZSPVW3YztXJvLowK.exe (PID: 5944)
- a8XgakQfmwwdkpVYBMRsJHzX.exe (PID: 4608)
- ysGi5iID3g53tlkzaQbgcJJD.exe (PID: 5788)
- Tf5ss65.exe (PID: 4128)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- KibI8idbFuOXtShsGGds6DF3.exe (PID: 5856)
- QeNz3MywCODuOxaYk85AqaYo.exe (PID: 5924)
- nb5XL55.exe (PID: 6228)
- ULRKwx3iR5VJqNbLaeyIW54j.exe (PID: 6976)
- rg1qP67.exe (PID: 4668)
- x0RPFql2zaxOzeAaN8s3QFfO.exe (PID: 7344)
- Tf5ss65.exe (PID: 4016)
- P3jb1n2rFq0ez3JUkuovAZXe.exe (PID: 7188)
- nb5XL55.exe (PID: 7328)
Loads DLL from Mozilla Firefox
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- explorer.exe (PID: 5076)
- certreq.exe (PID: 4984)
Searches for installed software
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- vbc.exe (PID: 4964)
- AppLaunch.exe (PID: 4672)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- certreq.exe (PID: 4984)
- untilmathematics.exe (PID: 5140)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- AppLaunch.exe (PID: 6396)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
Connects to unusual port
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- CeXhyH7QAVA1fsMjxdS_ql2i.exe (PID: 2176)
- vbc.exe (PID: 4964)
- AppLaunch.exe (PID: 4672)
- AppLaunch.exe (PID: 4892)
- AppLaunch.exe (PID: 3112)
- arriveprospect.exe (PID: 5056)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- VX6MxNHHzpIMgwuLaadgabw3.exe (PID: 5500)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- IEUpdater1.exe (PID: 3808)
- vbc.exe (PID: 3144)
- certreq.exe (PID: 4984)
- 4WD828Ic.exe (PID: 5668)
- AppLaunch.exe (PID: 6444)
- AppLaunch.exe (PID: 6396)
- AppLaunch.exe (PID: 2344)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- nULU3RVg3gPZdJRvhEdXll12.exe (PID: 1448)
- vbc.exe (PID: 4124)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
- 45SOoUJQUZuPF31kWHwCDbqW.exe (PID: 6936)
Checks for external IP
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- svchost.exe (PID: 324)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- XPcwXmnXG4RB07G5BG31ozqo.exe (PID: 4120)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- 39FAQZKOIFCH_3zOZOXG9Eit.exe (PID: 5396)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
- Ovhlx8nFAQOOvWEVPt74gNgq.exe (PID: 8080)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3672)
- cmd.exe (PID: 6832)
Drops 7-zip archiver for unpacking
- mmUi7viccv48sJD1w9k4AuDs.exe (PID: 3140)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- InstallUtil.exe (PID: 2556)
- InstallUtil.exe (PID: 4828)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- CjzLhIoubU6EOrERGzOsnpeU.exe (PID: 5148)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- InstallUtil.exe (PID: 924)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- InstallUtil.exe (PID: 2436)
- TskS7iTuF1rMl02JwXmqAncH.exe (PID: 6296)
- Kj3JVsuQJB2IvbWqvZdsn4f7.exe (PID: 2548)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- InstallUtil.exe (PID: 4916)
- fyuhvPv42QHuU13Up4YJsw8l.exe (PID: 7072)
Reads the BIOS version
- Install.exe (PID: 3964)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- Install.exe (PID: 3340)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- Install.exe (PID: 6940)
- Install.exe (PID: 6808)
- xzAyOwQKSF8_vOdFe_6ZM0Dm.exe (PID: 5632)
Found strings related to reading or modifying Windows Defender settings
- forfiles.exe (PID: 3780)
- forfiles.exe (PID: 2652)
- xqRPslL.exe (PID: 5592)
- forfiles.exe (PID: 6872)
- HNXZXKK.exe (PID: 6028)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3244)
- cmd.exe (PID: 1268)
- cmd.exe (PID: 8096)
- cmd.exe (PID: 7716)
- cmd.exe (PID: 416)
- cmd.exe (PID: 7400)
- wscript.exe (PID: 4328)
- cmd.exe (PID: 9040)
- cmd.exe (PID: 4652)
- cmd.exe (PID: 8220)
Base64-obfuscated command line is found
- taskeng.exe (PID: 4000)
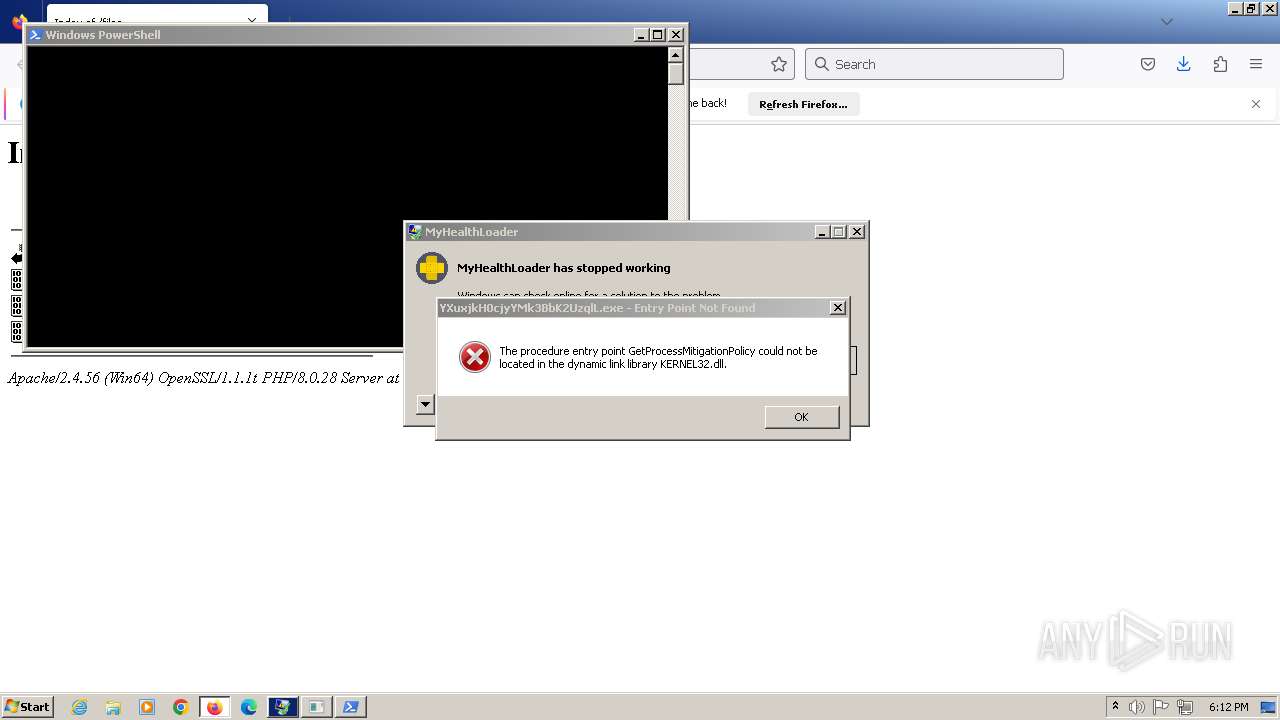
Starts POWERSHELL.EXE for commands execution
- taskeng.exe (PID: 4000)
- explorer.exe (PID: 1944)
BASE64 encoded PowerShell command has been detected
- taskeng.exe (PID: 4000)
The process executes via Task Scheduler
- powershell.EXE (PID: 1364)
- nhdues.exe (PID: 6004)
- nhdues.exe (PID: 6608)
- xqRPslL.exe (PID: 5592)
- powershell.EXE (PID: 3756)
- updater.exe (PID: 8836)
- HNXZXKK.exe (PID: 6028)
- oneetx.exe (PID: 4060)
Script adds exclusion path to Windows Defender
- explorer.exe (PID: 1944)
Executing commands from a ".bat" file
- vAjmiB170tl4bIKZ5xUDpfrl.exe (PID: 1396)
- ix0VkCfPyhYNXlHNcxjuBwtF.exe (PID: 1828)
- a8XgakQfmwwdkpVYBMRsJHzX.exe (PID: 4608)
- ysGi5iID3g53tlkzaQbgcJJD.exe (PID: 5788)
- KibI8idbFuOXtShsGGds6DF3.exe (PID: 5856)
- QeNz3MywCODuOxaYk85AqaYo.exe (PID: 5924)
- x0RPFql2zaxOzeAaN8s3QFfO.exe (PID: 7344)
- P3jb1n2rFq0ez3JUkuovAZXe.exe (PID: 7188)
The process checks if it is being run in the virtual environment
- rundll32.exe (PID: 4584)
- arriveprospect.exe (PID: 5056)
- SNeCBREnHZIC1szciY1ex3XV.exe (PID: 4140)
- rundll32.exe (PID: 5220)
The process executes VB scripts
- oIG1jnrpbxpgV9UQqYXO_y0e.exe (PID: 3076)
- OvUB1xP1YS1GBZpQ665SSkBm.exe (PID: 6012)
- 5zPBjjonT4oS1cZTmbyogig9.exe (PID: 2960)
Executes as Windows Service
- raserver.exe (PID: 3876)
- raserver.exe (PID: 5276)
- updater.exe (PID: 5892)
- raserver.exe (PID: 5448)
- raserver.exe (PID: 5236)
- raserver.exe (PID: 7044)
- raserver.exe (PID: 6644)
- raserver.exe (PID: 6536)
- raserver.exe (PID: 7340)
- raserver.exe (PID: 5972)
Reads browser cookies
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- AppLaunch.exe (PID: 4672)
- AppLaunch.exe (PID: 3112)
- vbc.exe (PID: 4964)
- CeXhyH7QAVA1fsMjxdS_ql2i.exe (PID: 2176)
- certreq.exe (PID: 4984)
- AppLaunch.exe (PID: 4892)
- VX6MxNHHzpIMgwuLaadgabw3.exe (PID: 5500)
- AppLaunch.exe (PID: 6444)
Accesses Microsoft Outlook profiles
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- explorer.exe (PID: 5536)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- certreq.exe (PID: 4984)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
Starts SC.EXE for service management
- cmd.exe (PID: 4412)
- cmd.exe (PID: 6052)
- cmd.exe (PID: 6252)
- cmd.exe (PID: 2212)
- cmd.exe (PID: 2516)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 4780)
- cmd.exe (PID: 5900)
- cmd.exe (PID: 6600)
- cmd.exe (PID: 7284)
- cmd.exe (PID: 2284)
Reads the Windows owner or organization settings
- cgKIS14C6q1NoChphhrRLrDB.tmp (PID: 4104)
Reads the date of Windows installation
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 4592)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5472)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
Unusual connection from system programs
- powershell.exe (PID: 2932)
The Powershell connects to the Internet
- powershell.exe (PID: 2932)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 5892)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 4584)
INFO
Drops the executable file immediately after the start
- firefox.exe (PID: 2612)
- explorer.exe (PID: 1944)
Application launched itself
- firefox.exe (PID: 2612)
Reads the computer name
- get4.exe (PID: 1296)
- InstallUtil.exe (PID: 2556)
- arriveprospect.exe (PID: 3012)
- q8OSAEnVHW3WkRgcmKQ0dUXZ.exe (PID: 3412)
- nhdues.exe (PID: 3728)
- 66vC2gAXVfk27a5wEcwAlQ4t.exe (PID: 3776)
- 3npwZ06l6txlO5EG5bEFIhXC.exe (PID: 3468)
- Lmr41oZWb1ZPiV772JIaAFkT.exe (PID: 2092)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- Install.exe (PID: 3964)
- CeXhyH7QAVA1fsMjxdS_ql2i.exe (PID: 2176)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 4592)
- InstallUtil.exe (PID: 4828)
- RZbl0lR98O6Qhs7pebM5pNhE.exe (PID: 3796)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- vbc.exe (PID: 4964)
- AppLaunch.exe (PID: 4672)
- arriveprospect.exe (PID: 5056)
- AppLaunch.exe (PID: 3112)
- RzHhsHIvDvaCDn8gf5Vfq60U.exe (PID: 1076)
- AppLaunch.exe (PID: 4892)
- arriiveprospect.exe (PID: 2244)
- 1lP68aL0.exe (PID: 3356)
- TrustedInstaller.exe (PID: 5012)
- XPcwXmnXG4RB07G5BG31ozqo.exe (PID: 4120)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- vt2VgJ1wjzh9p8Ki58YN65JU.exe (PID: 984)
- untilmathematics.exe (PID: 4852)
- gWrsw8QB73u2AInEN7hC0wty.exe (PID: 3424)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- cgKIS14C6q1NoChphhrRLrDB.tmp (PID: 4104)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 5456)
- 2pr5983.exe (PID: 5128)
- uhxRUj5DV1cfZSEfD3bMoZUr.exe (PID: 5556)
- IEUpdater1.exe (PID: 3808)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- VX6MxNHHzpIMgwuLaadgabw3.exe (PID: 5500)
- InstallUtil.exe (PID: 924)
- ffUbNlFyy94bJxTL_5Ig97z6.exe (PID: 1076)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5472)
- vbc.exe (PID: 3144)
- 4WD828Ic.exe (PID: 5668)
- oneetx.exe (PID: 5916)
- 39FAQZKOIFCH_3zOZOXG9Eit.exe (PID: 5396)
- Install.exe (PID: 3340)
- SNeCBREnHZIC1szciY1ex3XV.exe (PID: 4140)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- hkfMTElbgBduYQ60cv15ysFv.exe (PID: 5480)
- InstallUtil.exe (PID: 2436)
- BGiqV6xWxTEIyg12Uj1Y35gg.exe (PID: 1760)
- bXbjU3cr8ZJeNPvCflnP7NAd.exe (PID: 5804)
- build2.exe (PID: 2476)
- BOkUTx0iwlgh3MRNoF7OvgaQ.exe (PID: 5880)
- ueFUGKtfr8db8yUkRinZ2Yqv.exe (PID: 5268)
- untilmathematics.exe (PID: 5140)
- AppLaunch.exe (PID: 6444)
- untilmathematiics.exe (PID: 4572)
- JEwIXxkYI0wHPvLLaqPI7yVM.exe (PID: 5900)
- vDx1uwIwCvhCxlbFOC2kkWGc.exe (PID: 6052)
- AppLaunch.exe (PID: 2344)
- ovIFc9bI6zb75QUIvz2wnNDT.exe (PID: 5404)
- YAqVpZrY6VsUD5ENN6oY797A.exe (PID: 6368)
- AppLaunch.exe (PID: 6396)
- Install.exe (PID: 6940)
- 1jQgxQsXN1wKyFlyav53jSeF.exe (PID: 6764)
- Uue0d0frXqEkX6JcnasnNNbd.exe (PID: 6952)
- nULU3RVg3gPZdJRvhEdXll12.exe (PID: 1448)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- InstallUtil.exe (PID: 4916)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- Install.exe (PID: 6808)
- vbc.exe (PID: 4124)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- ZPd8ckjQ4bbYp0Ib7vkamPaC.tmp (PID: 4708)
- j1QJP0Aa5KqR0gKRmEqWQuN8.exe (PID: 7312)
- xNfkGmGmIqUGxtSpqcUgU8oC.exe (PID: 5264)
- 45SOoUJQUZuPF31kWHwCDbqW.exe (PID: 6936)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- n8u8MnM4FzEZFJsDGpjlpz9v.exe (PID: 7736)
- IYEq8bDdA5b9aTNdGrlAV9OY.exe (PID: 4700)
- Ns6hO16rUCgFiQNe6HvHSI5W.exe (PID: 7316)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
- InstallUtil.exe (PID: 3880)
- Ovhlx8nFAQOOvWEVPt74gNgq.exe (PID: 8080)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 8104)
- 9jQg9ghWh15yCL361uCzjJTq.exe (PID: 6440)
- 1lP68aL0.exe (PID: 2688)
- AppLaunch.exe (PID: 900)
- k2xOQaxpXLSuIZ1xwmjXa2Vz.exe (PID: 7716)
- AppLaunch.exe (PID: 2692)
- HNXZXKK.exe (PID: 6028)
- xzAyOwQKSF8_vOdFe_6ZM0Dm.exe (PID: 5632)
Checks supported languages
- InstallUtil.exe (PID: 2556)
- get4.exe (PID: 1296)
- AOdgduFToChPmaTfjl8Ph3R4.exe (PID: 3420)
- q8OSAEnVHW3WkRgcmKQ0dUXZ.exe (PID: 3412)
- arriveprospect.exe (PID: 3012)
- nhdues.exe (PID: 3728)
- 66vC2gAXVfk27a5wEcwAlQ4t.exe (PID: 3776)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- K3AidViq3fu5I0UKoDhvimK1.exe (PID: 3520)
- 3npwZ06l6txlO5EG5bEFIhXC.exe (PID: 3468)
- Lmr41oZWb1ZPiV772JIaAFkT.exe (PID: 2092)
- K3AidViq3fu5I0UKoDhvimK1.exe (PID: 3620)
- YXuxjkH0cjyYMk3BbK2UzqlL.exe (PID: 792)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- zsWklsWnSwufAN7TKspgweE3.exe (PID: 2180)
- mmUi7viccv48sJD1w9k4AuDs.exe (PID: 3140)
- Install.exe (PID: 904)
- LhzwzpX5CoXjD1kfEk3zTdEj.exe (PID: 2476)
- vAjmiB170tl4bIKZ5xUDpfrl.exe (PID: 1396)
- nF6mOdhRMpN3SGbQlrPIZdiL.exe (PID: 3980)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- lYUgfzizvypmRH9zJmFjirkj.exe (PID: 2240)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 3876)
- CeXhyH7QAVA1fsMjxdS_ql2i.exe (PID: 2176)
- ukAyKHLGhoX80UWXzKQoVPOa.exe (PID: 1296)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- oIG1jnrpbxpgV9UQqYXO_y0e.exe (PID: 3076)
- Zbxppt0pzqdS7E2romHwKpef.exe (PID: 2504)
- InstallUtil.exe (PID: 4828)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 4592)
- SsUbG5aDCpzJve6jGVmV73Bs.exe (PID: 1480)
- Tf5ss65.exe (PID: 4628)
- XPcwXmnXG4RB07G5BG31ozqo.exe (PID: 4120)
- nb5XL55.exe (PID: 4784)
- Install.exe (PID: 3964)
- rg1qP67.exe (PID: 684)
- vbc.exe (PID: 4964)
- RZbl0lR98O6Qhs7pebM5pNhE.exe (PID: 3796)
- arriveprospect.exe (PID: 5056)
- ix0VkCfPyhYNXlHNcxjuBwtF.exe (PID: 1828)
- RzHhsHIvDvaCDn8gf5Vfq60U.exe (PID: 1076)
- AppLaunch.exe (PID: 3112)
- Vx9XK71.exe (PID: 1620)
- AppLaunch.exe (PID: 4672)
- AppLaunch.exe (PID: 4892)
- arriiveprospect.exe (PID: 2244)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- TrustedInstaller.exe (PID: 5012)
- 1lP68aL0.exe (PID: 3356)
- srMgMKR14ZrJXhtxiFzFfjto.exe (PID: 3764)
- himeffectively.exe (PID: 3012)
- untilmathematicspro.exe (PID: 4152)
- QIPR1ptbkPFZQ5thhYbsDOLW.exe (PID: 5024)
- vt2VgJ1wjzh9p8Ki58YN65JU.exe (PID: 984)
- untilmathematics.exe (PID: 4852)
- gWrsw8QB73u2AInEN7hC0wty.exe (PID: 3424)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- loEwvzzf5f4P5czVnTz5lu61.exe (PID: 3912)
- OBezVevHKAJ2UV1nNQKZcbBI.exe (PID: 4940)
- QIPR1ptbkPFZQ5thhYbsDOLW.exe (PID: 4396)
- cgKIS14C6q1NoChphhrRLrDB.exe (PID: 4908)
- cgKIS14C6q1NoChphhrRLrDB.tmp (PID: 4104)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 6072)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 5456)
- 2pr5983.exe (PID: 5128)
- uhxRUj5DV1cfZSEfD3bMoZUr.exe (PID: 5556)
- nhdues.exe (PID: 6004)
- rsMRDHH5EHOGkhtLr7DcGPWp.exe (PID: 5864)
- CjzLhIoubU6EOrERGzOsnpeU.exe (PID: 5148)
- updater.exe (PID: 5892)
- IEUpdater1.exe (PID: 3808)
- FFvUvYbdQ3pjTyFDA4WuM6Yr.exe (PID: 4988)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- a8XgakQfmwwdkpVYBMRsJHzX.exe (PID: 4608)
- 1vaFjymLZSPVW3YztXJvLowK.exe (PID: 5944)
- ffUbNlFyy94bJxTL_5Ig97z6.exe (PID: 1076)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5284)
- oneetx.exe (PID: 5916)
- _tTuyuRtejceJx8gkDzE6lOi.exe (PID: 4212)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- 39FAQZKOIFCH_3zOZOXG9Eit.exe (PID: 5396)
- VX6MxNHHzpIMgwuLaadgabw3.exe (PID: 5500)
- Install.exe (PID: 6056)
- m_fh9IkGRfZ7B0XBXkKo84dt.exe (PID: 2220)
- OvUB1xP1YS1GBZpQ665SSkBm.exe (PID: 6012)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- build2.exe (PID: 5124)
- RgZJOtfo_D0hS8k6QbNV4q4k.exe (PID: 4208)
- InstallUtil.exe (PID: 924)
- 3Vj72Hw.exe (PID: 3764)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5472)
- build3.exe (PID: 6040)
- Tf5ss65.exe (PID: 4128)
- Install.exe (PID: 3340)
- vbc.exe (PID: 3144)
- 4WD828Ic.exe (PID: 5668)
- aZuvvaBqmC0LA2eaWFOjl4T9.exe (PID: 5428)
- SNeCBREnHZIC1szciY1ex3XV.exe (PID: 4140)
- RE82WtvebfRpLAO0phRIy4wQ.exe (PID: 3748)
- ysGi5iID3g53tlkzaQbgcJJD.exe (PID: 5788)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- KibI8idbFuOXtShsGGds6DF3.exe (PID: 5856)
- hkfMTElbgBduYQ60cv15ysFv.exe (PID: 5480)
- bXbjU3cr8ZJeNPvCflnP7NAd.exe (PID: 5804)
- ngMvND4PvkhwkTVzYV5xsqwh.exe (PID: 4740)
- 0X2VWPeOtWsJzActynA8jUp3.exe (PID: 4596)
- BGiqV6xWxTEIyg12Uj1Y35gg.exe (PID: 1760)
- build2.exe (PID: 2476)
- InstallUtil.exe (PID: 2436)
- ueFUGKtfr8db8yUkRinZ2Yqv.exe (PID: 5268)
- aLiYFgBKzaENPeFMTzSmeIxG.exe (PID: 6072)
- BOkUTx0iwlgh3MRNoF7OvgaQ.exe (PID: 5880)
- 5cHcitxg53pwem26My5QgTVo.exe (PID: 5872)
- SKDGRzQaLrdorjBgweAuc5lQ.exe (PID: 5636)
- ZPd8ckjQ4bbYp0Ib7vkamPaC.exe (PID: 4552)
- 0X2VWPeOtWsJzActynA8jUp3.exe (PID: 3400)
- untilmathematics.exe (PID: 5140)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- TskS7iTuF1rMl02JwXmqAncH.exe (PID: 6296)
- untilmathematiics.exe (PID: 4572)
- AppLaunch.exe (PID: 6444)
- fvSjc99mxBf23smnXhkyisRs.exe (PID: 5104)
- nb5XL55.exe (PID: 6228)
- ovIFc9bI6zb75QUIvz2wnNDT.exe (PID: 5404)
- Install.exe (PID: 5116)
- BqsrfKeKClGgpr7HLZodSKqw.exe (PID: 2932)
- fMh25VTHm9OryG9HeJyynLMm.exe (PID: 6468)
- Kj3JVsuQJB2IvbWqvZdsn4f7.exe (PID: 2548)
- vDx1uwIwCvhCxlbFOC2kkWGc.exe (PID: 6052)
- YAqVpZrY6VsUD5ENN6oY797A.exe (PID: 6368)
- JEwIXxkYI0wHPvLLaqPI7yVM.exe (PID: 5900)
- ZPd8ckjQ4bbYp0Ib7vkamPaC.tmp (PID: 4708)
- AppLaunch.exe (PID: 6396)
- AppLaunch.exe (PID: 2344)
- Install.exe (PID: 6940)
- Install.exe (PID: 6492)
- fMh25VTHm9OryG9HeJyynLMm.exe (PID: 6900)
- QeNz3MywCODuOxaYk85AqaYo.exe (PID: 5924)
- Uue0d0frXqEkX6JcnasnNNbd.exe (PID: 6952)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- nULU3RVg3gPZdJRvhEdXll12.exe (PID: 1448)
- 1jQgxQsXN1wKyFlyav53jSeF.exe (PID: 6764)
- ULRKwx3iR5VJqNbLaeyIW54j.exe (PID: 6976)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- Al7cTMQlqsfdhc54yHwz1zKD.exe (PID: 7060)
- xqRPslL.exe (PID: 5592)
- InstallUtil.exe (PID: 4916)
- Install.exe (PID: 6808)
- 5zPBjjonT4oS1cZTmbyogig9.exe (PID: 2960)
- rg1qP67.exe (PID: 4668)
- vbc.exe (PID: 4124)
- O6d4NgNKLYPx1lNE6j84Gr_k.exe (PID: 3948)
- 0yKb1qQOjVPpU6xlr56TaqHo.exe (PID: 6948)
- Tf5ss65.exe (PID: 4016)
- Vx9XK71.exe (PID: 7548)
- x0RPFql2zaxOzeAaN8s3QFfO.exe (PID: 7344)
- j1QJP0Aa5KqR0gKRmEqWQuN8.exe (PID: 7312)
- 7BZn5RFuIM945dYaLrkreCCh.exe (PID: 7256)
- sYUFFPSWg8DtFkB2iv0yZAKN.exe (PID: 4112)
- xNfkGmGmIqUGxtSpqcUgU8oC.exe (PID: 5264)
- Ns6hO16rUCgFiQNe6HvHSI5W.exe (PID: 7316)
- CnU05d0R1X160oSaoMyxrsaD.exe (PID: 7176)
- Ovhlx8nFAQOOvWEVPt74gNgq.exe (PID: 8080)
- n8u8MnM4FzEZFJsDGpjlpz9v.exe (PID: 7736)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
- sYUFFPSWg8DtFkB2iv0yZAKN.exe (PID: 8156)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5068)
- 45SOoUJQUZuPF31kWHwCDbqW.exe (PID: 6936)
- lHeL4Ck2v9Hjsjc6L2Pb2eGZ.exe (PID: 7972)
- IYEq8bDdA5b9aTNdGrlAV9OY.exe (PID: 4700)
- gByeecmMjiYL8_DIUhNulyQz.exe (PID: 5508)
- AppLaunch.exe (PID: 2692)
- 1lP68aL0.exe (PID: 2688)
- 9jQg9ghWh15yCL361uCzjJTq.exe (PID: 6440)
- xzAyOwQKSF8_vOdFe_6ZM0Dm.exe (PID: 5632)
- InstallUtil.exe (PID: 3880)
- P3jb1n2rFq0ez3JUkuovAZXe.exe (PID: 7188)
- AppLaunch.exe (PID: 900)
- k2xOQaxpXLSuIZ1xwmjXa2Vz.exe (PID: 7716)
- nb5XL55.exe (PID: 7328)
- iWbQMIE_UejHCbAVoXKzSsCs.exe (PID: 8040)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 8104)
- UvzI3kSiZhAk8YCjLL4eOV41.exe (PID: 5192)
- fyuhvPv42QHuU13Up4YJsw8l.exe (PID: 7072)
- 8QQnvSudgWkiVzXWct9iPrdG.exe (PID: 8288)
- HNXZXKK.exe (PID: 6028)
- Install.exe (PID: 8532)
- nhdues.exe (PID: 6608)
- himeffectively.exe (PID: 9156)
- 2pr5983.exe (PID: 6848)
- Install.exe (PID: 8372)
The process uses the downloaded file
- firefox.exe (PID: 2612)
Reads the machine GUID from the registry
- InstallUtil.exe (PID: 2556)
- nhdues.exe (PID: 3728)
- arriveprospect.exe (PID: 3012)
- 3npwZ06l6txlO5EG5bEFIhXC.exe (PID: 3468)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- Lmr41oZWb1ZPiV772JIaAFkT.exe (PID: 2092)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- Install.exe (PID: 3964)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- CeXhyH7QAVA1fsMjxdS_ql2i.exe (PID: 2176)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 4592)
- vbc.exe (PID: 4964)
- RZbl0lR98O6Qhs7pebM5pNhE.exe (PID: 3796)
- InstallUtil.exe (PID: 4828)
- arriveprospect.exe (PID: 5056)
- AppLaunch.exe (PID: 4672)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- AppLaunch.exe (PID: 3112)
- AppLaunch.exe (PID: 4892)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- RzHhsHIvDvaCDn8gf5Vfq60U.exe (PID: 1076)
- XPcwXmnXG4RB07G5BG31ozqo.exe (PID: 4120)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- arriiveprospect.exe (PID: 2244)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- gWrsw8QB73u2AInEN7hC0wty.exe (PID: 3424)
- untilmathematics.exe (PID: 4852)
- TrustedInstaller.exe (PID: 5012)
- cgKIS14C6q1NoChphhrRLrDB.tmp (PID: 4104)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 5456)
- 2pr5983.exe (PID: 5128)
- uhxRUj5DV1cfZSEfD3bMoZUr.exe (PID: 5556)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- IEUpdater1.exe (PID: 3808)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- InstallUtil.exe (PID: 924)
- VX6MxNHHzpIMgwuLaadgabw3.exe (PID: 5500)
- ffUbNlFyy94bJxTL_5Ig97z6.exe (PID: 1076)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5472)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- 39FAQZKOIFCH_3zOZOXG9Eit.exe (PID: 5396)
- Install.exe (PID: 3340)
- build2.exe (PID: 2476)
- vbc.exe (PID: 3144)
- InstallUtil.exe (PID: 2436)
- SNeCBREnHZIC1szciY1ex3XV.exe (PID: 4140)
- BOkUTx0iwlgh3MRNoF7OvgaQ.exe (PID: 5880)
- hkfMTElbgBduYQ60cv15ysFv.exe (PID: 5480)
- bXbjU3cr8ZJeNPvCflnP7NAd.exe (PID: 5804)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- 4WD828Ic.exe (PID: 5668)
- ueFUGKtfr8db8yUkRinZ2Yqv.exe (PID: 5268)
- untilmathematics.exe (PID: 5140)
- vDx1uwIwCvhCxlbFOC2kkWGc.exe (PID: 6052)
- untilmathematiics.exe (PID: 4572)
- ovIFc9bI6zb75QUIvz2wnNDT.exe (PID: 5404)
- YAqVpZrY6VsUD5ENN6oY797A.exe (PID: 6368)
- Install.exe (PID: 6940)
- AppLaunch.exe (PID: 6444)
- AppLaunch.exe (PID: 2344)
- AppLaunch.exe (PID: 6396)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- InstallUtil.exe (PID: 4916)
- Uue0d0frXqEkX6JcnasnNNbd.exe (PID: 6952)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- Install.exe (PID: 6808)
- nULU3RVg3gPZdJRvhEdXll12.exe (PID: 1448)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- oneetx.exe (PID: 5916)
- vbc.exe (PID: 4124)
- xNfkGmGmIqUGxtSpqcUgU8oC.exe (PID: 5264)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- Ns6hO16rUCgFiQNe6HvHSI5W.exe (PID: 7316)
- IYEq8bDdA5b9aTNdGrlAV9OY.exe (PID: 4700)
- n8u8MnM4FzEZFJsDGpjlpz9v.exe (PID: 7736)
- 45SOoUJQUZuPF31kWHwCDbqW.exe (PID: 6936)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
- InstallUtil.exe (PID: 3880)
- k2xOQaxpXLSuIZ1xwmjXa2Vz.exe (PID: 7716)
- Ovhlx8nFAQOOvWEVPt74gNgq.exe (PID: 8080)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 8104)
- HNXZXKK.exe (PID: 6028)
Reads Environment values
- InstallUtil.exe (PID: 2556)
- arriveprospect.exe (PID: 3012)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- InstallUtil.exe (PID: 4828)
- CeXhyH7QAVA1fsMjxdS_ql2i.exe (PID: 2176)
- arriiveprospect.exe (PID: 2244)
- untilmathematics.exe (PID: 4852)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- AppLaunch.exe (PID: 3112)
- vbc.exe (PID: 4964)
- AppLaunch.exe (PID: 4892)
- AppLaunch.exe (PID: 4672)
- InstallUtil.exe (PID: 924)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- InstallUtil.exe (PID: 2436)
- untilmathematiics.exe (PID: 4572)
- VX6MxNHHzpIMgwuLaadgabw3.exe (PID: 5500)
- vbc.exe (PID: 3144)
- InstallUtil.exe (PID: 4916)
- 4WD828Ic.exe (PID: 5668)
- AppLaunch.exe (PID: 2344)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- AppLaunch.exe (PID: 6444)
- AppLaunch.exe (PID: 6396)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
- InstallUtil.exe (PID: 3880)
Creates files or folders in the user directory
- InstallUtil.exe (PID: 2556)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- explorer.exe (PID: 1944)
- InstallUtil.exe (PID: 4828)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 4592)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- lsass.exe (PID: 500)
- nhdues.exe (PID: 3728)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 5456)
- cgKIS14C6q1NoChphhrRLrDB.tmp (PID: 4104)
- InstallUtil.exe (PID: 924)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5472)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- InstallUtil.exe (PID: 2436)
- dllhost.exe (PID: 2052)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- InstallUtil.exe (PID: 4916)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- InstallUtil.exe (PID: 3880)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 8104)
- HNXZXKK.exe (PID: 6028)
Create files in a temporary directory
- AOdgduFToChPmaTfjl8Ph3R4.exe (PID: 3420)
- q8OSAEnVHW3WkRgcmKQ0dUXZ.exe (PID: 3412)
- nhdues.exe (PID: 3728)
- YXuxjkH0cjyYMk3BbK2UzqlL.exe (PID: 792)
- Install.exe (PID: 904)
- mmUi7viccv48sJD1w9k4AuDs.exe (PID: 3140)
- vAjmiB170tl4bIKZ5xUDpfrl.exe (PID: 1396)
- lYUgfzizvypmRH9zJmFjirkj.exe (PID: 2240)
- Tf5ss65.exe (PID: 4628)
- nb5XL55.exe (PID: 4784)
- rg1qP67.exe (PID: 684)
- ix0VkCfPyhYNXlHNcxjuBwtF.exe (PID: 1828)
- Vx9XK71.exe (PID: 1620)
- himeffectively.exe (PID: 3012)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- untilmathematicspro.exe (PID: 4152)
- OBezVevHKAJ2UV1nNQKZcbBI.exe (PID: 4940)
- zsWklsWnSwufAN7TKspgweE3.exe (PID: 2180)
- Install.exe (PID: 3964)
- cgKIS14C6q1NoChphhrRLrDB.exe (PID: 4908)
- cgKIS14C6q1NoChphhrRLrDB.tmp (PID: 4104)
- explorer.exe (PID: 5536)
- uhxRUj5DV1cfZSEfD3bMoZUr.exe (PID: 5556)
- a8XgakQfmwwdkpVYBMRsJHzX.exe (PID: 4608)
- 1vaFjymLZSPVW3YztXJvLowK.exe (PID: 5944)
- Install.exe (PID: 6056)
- InstallUtil.exe (PID: 924)
- CjzLhIoubU6EOrERGzOsnpeU.exe (PID: 5148)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- Tf5ss65.exe (PID: 4128)
- ysGi5iID3g53tlkzaQbgcJJD.exe (PID: 5788)
- KibI8idbFuOXtShsGGds6DF3.exe (PID: 5856)
- InstallUtil.exe (PID: 2436)
- SKDGRzQaLrdorjBgweAuc5lQ.exe (PID: 5636)
- ZPd8ckjQ4bbYp0Ib7vkamPaC.exe (PID: 4552)
- TskS7iTuF1rMl02JwXmqAncH.exe (PID: 6296)
- Install.exe (PID: 5116)
- nb5XL55.exe (PID: 6228)
- BqsrfKeKClGgpr7HLZodSKqw.exe (PID: 2932)
- Kj3JVsuQJB2IvbWqvZdsn4f7.exe (PID: 2548)
- Install.exe (PID: 6492)
- QeNz3MywCODuOxaYk85AqaYo.exe (PID: 5924)
- ULRKwx3iR5VJqNbLaeyIW54j.exe (PID: 6976)
- InstallUtil.exe (PID: 4916)
- rsMRDHH5EHOGkhtLr7DcGPWp.exe (PID: 5864)
- rg1qP67.exe (PID: 4668)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- Tf5ss65.exe (PID: 4016)
- Vx9XK71.exe (PID: 7548)
- x0RPFql2zaxOzeAaN8s3QFfO.exe (PID: 7344)
- CnU05d0R1X160oSaoMyxrsaD.exe (PID: 7176)
- fvSjc99mxBf23smnXhkyisRs.exe (PID: 5104)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
- nb5XL55.exe (PID: 7328)
- fyuhvPv42QHuU13Up4YJsw8l.exe (PID: 7072)
- P3jb1n2rFq0ez3JUkuovAZXe.exe (PID: 7188)
- InstallUtil.exe (PID: 3880)
- 8QQnvSudgWkiVzXWct9iPrdG.exe (PID: 8288)
- Install.exe (PID: 8532)
Checks proxy server information
- nhdues.exe (PID: 3728)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 4592)
- RZbl0lR98O6Qhs7pebM5pNhE.exe (PID: 3796)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- cgKIS14C6q1NoChphhrRLrDB.tmp (PID: 4104)
- JdVTmNQlPY6hhjFqqPxGrMIP.exe (PID: 5456)
- 2pr5983.exe (PID: 5128)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- ffUbNlFyy94bJxTL_5Ig97z6.exe (PID: 1076)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 5472)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- untilmathematics.exe (PID: 5140)
- Uue0d0frXqEkX6JcnasnNNbd.exe (PID: 6952)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- oneetx.exe (PID: 5916)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
- EeJ1jfccZPIn6SPEFp5hni2N.exe (PID: 8104)
Creates files in the program directory
- svchost.exe (PID: 884)
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- lsass.exe (PID: 500)
- HfBbiQ5JHrhsuHIsvEd0hpUA.exe (PID: 3260)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- zsWklsWnSwufAN7TKspgweE3.exe (PID: 2180)
- VC2YEgro4cHXWrr3zBMAPM40.exe (PID: 2104)
- hYmVKq29CP_wOpmXXx9U8Ccz.exe (PID: 4888)
- FT7cAVxcVP_ghYG9VRFCLQMh.exe (PID: 7112)
- HNXZXKK.exe (PID: 6028)
Reads product name
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
Process checks computer location settings
- 0JazsvHOAs2E5Ybf0mbia6YU.exe (PID: 3460)
- 6FLFwbgm21UWnX9KQFFdvkSR.exe (PID: 4308)
- KkwhyOnqqRY9UkJUJOcXKnTS.exe (PID: 4652)
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- dHYx9AWax7mCnkNxe82ZbSBK.exe (PID: 5408)
- BRVXzxsOX8TAC1QhW8H03yED.exe (PID: 2460)
- 8sOQ0Kvx1emlaYf_g0v3uMv9.exe (PID: 6316)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- SF7IJm9FNqOPwCgM3zGG6YVU.exe (PID: 7656)
Reads CPU info
- dDqTuH6URaVCl9h3HLE1hiNu.exe (PID: 460)
- 9gE0j5bNvsV28fzOtwWdMJDa.exe (PID: 4272)
- K5zCueztXozkzOF624lgClot.exe (PID: 5336)
- ixnNFjMDSAAiex6PLzHgS6u6.exe (PID: 6868)
- ZvYCW83t5FVPWfobptLKffdI.exe (PID: 7720)
Manual execution by a user
- powershell.exe (PID: 2900)
- cmd.exe (PID: 4412)
- cmd.exe (PID: 4780)
- schtasks.exe (PID: 2196)
- schtasks.exe (PID: 4480)
- certreq.exe (PID: 4984)
- explorer.exe (PID: 5536)
- explorer.exe (PID: 5076)
- schtasks.exe (PID: 5188)
- powershell.exe (PID: 5732)
- powershell.exe (PID: 2932)
- cmd.exe (PID: 6052)
- cmd.exe (PID: 5900)
- schtasks.exe (PID: 2548)
- conhost.exe (PID: 6744)
- explorer.exe (PID: 6460)
- cmd.exe (PID: 6252)
- powershell.exe (PID: 4600)
Reads the Internet Settings
- explorer.exe (PID: 1944)
- explorer.exe (PID: 5076)
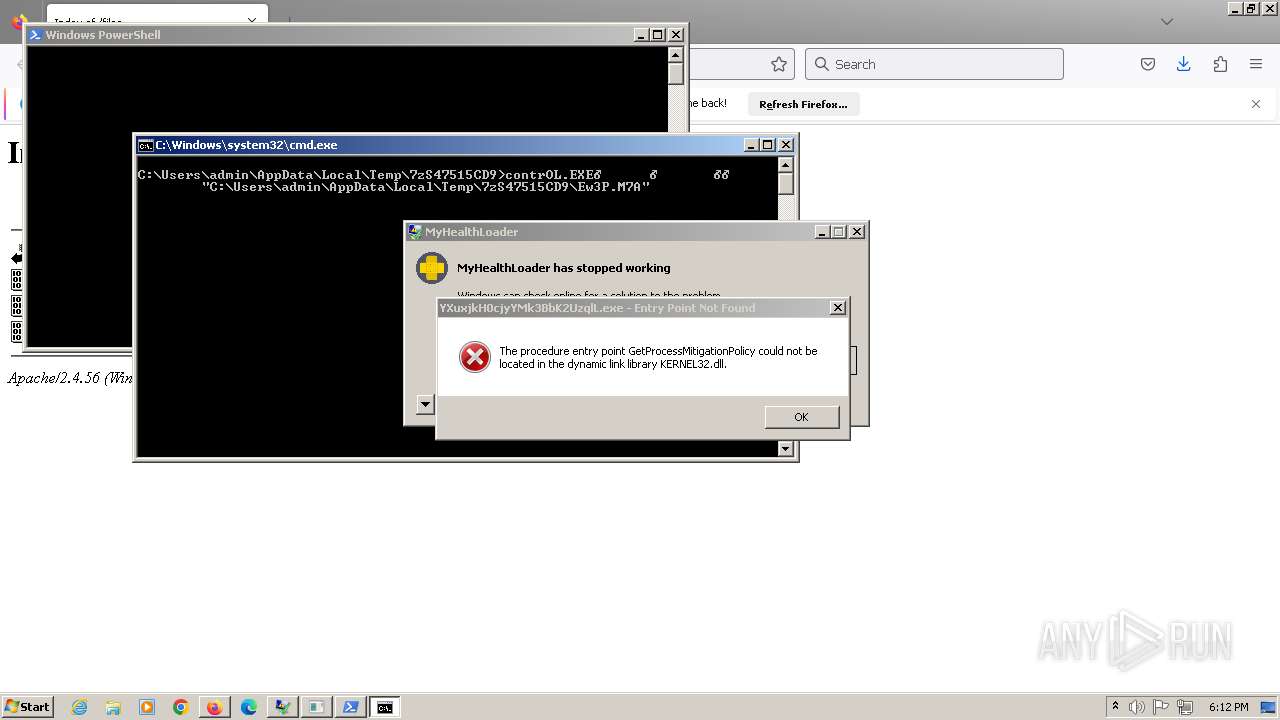
Application was dropped or rewritten from another process
- cgKIS14C6q1NoChphhrRLrDB.tmp (PID: 4104)
- ZPd8ckjQ4bbYp0Ib7vkamPaC.tmp (PID: 4708)
Process checks are UAC notifies on
- vWYKsChzFbsrKVlOTC_BGZsS.exe (PID: 3284)
- sxgeORlz9H9FCqZnM_6qDanu.exe (PID: 6176)
- xzAyOwQKSF8_vOdFe_6ZM0Dm.exe (PID: 5632)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(3728) nhdues.exe
C2 (1)http://193.42.32.29
Version3.89
Options
Drop directoryS-%lu-
Drop name%-lu
Strings (120)-%lu
1ff8bec27e
nhdues.exe
SCHTASKS
/Create /SC MINUTE /MO 1 /TN
/TR "
" /F
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Startup
Rem
cmd /C RMDIR /s/q
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
rundll32
/Delete /TN "
Programs
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
%USERPROFILE%
\App
POST
GET
id=
&vs=
&sd=
&os=
&bi=
&ar=
&pc=
&un=
&dm=
&av=
&lv=
&og=
cred.dll|clip.dll|
d1
e1
e0
Main
http://
https://
exe
dll
cmd
ps1
<c>
<d>
Plugins/
+++
#
|
&unit=
=
shell32.dll
kernel32.dll
GetNativeSystemInfo
ProgramData\
AVAST Software
Avira
Kaspersky Lab
ESET
Panda Security
Doctor Web
AVG
360TotalSecurity
Bitdefender
Norton
Sophos
Comodo
WinDefender
0123456789
rb
wb
Content-Type: multipart/form-data; boundary=----
------
Content-Disposition: form-data; name="data"; filename="
"
Content-Type: application/octet-stream
------
--
?scr=1
.jpg
Content-Type: application/x-www-form-urlencoded
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
ComputerName
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
SYSTEM\ControlSet001\Services\BasicDisplay\Video
VideoID
\0000
DefaultSettings.XResolution
DefaultSettings.YResolution
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
2019
2022
2016
CurrentBuild
&&
echo Y|CACLS "
" /P "
:N"
CACLS "
" /P "
:R" /E
:F" /E
&&Exit
..\
\
:::
rundll32.exe
/k
"taskkill /f /im "
" && timeout 1 && del
&& Exit"
" && ren
&&
Powershell.exe
-executionpolicy remotesigned -File "
"
shutdown -s -t 0
(PID) Process(5916) oneetx.exe
C2 (1)http://45.9.74.80
Version3.83
Options
Drop directory207aa4515d
Drop nameoneetx.exe
Strings (116)SCHTASKS
/Create /SC MINUTE /MO 1 /TN
/TR "
" /F
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Startup
Rem
cmd /C RMDIR /s/q
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
rundll32
/Delete /TN "
Programs
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
%USERPROFILE%
\App
POST
GET
id=
&vs=
&sd=
&os=
&bi=
&ar=
&pc=
&un=
&dm=
&av=
&lv=
&og=
cred.dll|clip.dll|
d1
e1
e0
Main
http://
https://
exe
dll
cmd
ps1
<c>
<d>
Plugins/
+++
#
|
&unit=
=
shell32.dll
kernel32.dll
GetNativeSystemInfo
ProgramData\
AVAST Software
Avira
Kaspersky Lab
ESET
Panda Security
Doctor Web
AVG
360TotalSecurity
Bitdefender
Norton
Sophos
Comodo
WinDefender
0123456789
rb
wb
Content-Type: multipart/form-data; boundary=----
------
Content-Disposition: form-data; name="data"; filename="
"
Content-Type: application/octet-stream
------
--
?scr=1
.jpg
Content-Type: application/x-www-form-urlencoded
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
ComputerName
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
SYSTEM\ControlSet001\Services\BasicDisplay\Video
VideoID
\0000
DefaultSettings.XResolution
DefaultSettings.YResolution
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
2019
2022
2016
CurrentBuild
&&
echo Y|CACLS "
" /P "
:N"
CACLS "
" /P "
:R" /E
:F" /E
&&Exit
..\
\
:::
rundll32.exe
/k
"taskkill /f /im "
" && timeout 1 && del
&& Exit"
" && ren
&&
Powershell.exe
-executionpolicy remotesigned -File "
"
Stealc
(PID) Process(3796) RZbl0lR98O6Qhs7pebM5pNhE.exe
C2http://kevinrobinson.top/e9c345fc99a4e67e.php
Keys
RC49478689687193229132746546166
Strings (346)" & del "C:\ProgramData\*.dll"" & exit
#ea6@I?!KP
%08lX%04lX%lu
%APPDATA%
%DESKTOP%
%DOCUMENTS%
%LOCALPPDATA%
%PROGRMFILES%
%PROGRMFILES_86%
%RECENT%
%USERPROFILE%
%d/%d/%d %d:%d:%d
%hu/%hu/%hu
*.ini
*.lnk
*.tox
- Architecture:
- CPU:
- Computer Name:
- Cores:
- Country: ISO?
- Display Resolution:
- GPU:
- HWID:
- IP: IP?
- Keyboards:
- Language:
- Laptop:
- Local Time:
- OS:
- RAM:
- Running Path:
- Threads:
- UTC:
- UserName:
.exe
.txt
/412a0310f85f16ad/
/c start
/c timeout /t 5 & del /f /q "
/e9c345fc99a4e67e.php
00000001
00000002
00000003
00000004
A7FDF864FBC10B77*
A92DAA6EA6F891F2*
ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890
All Users:
BCryptCloseAlgorithmProvider
BCryptDecrypt
BCryptDestroyKey
BCryptGenerateSymmetricKey
BCryptOpenAlgorithmProvider
BCryptSetProperty
BitBlt
C:\ProgramData\
C:\ProgramData\nss3.dll
C:\Windows\system32\cmd.exe
CURRENT
CharToOemW
CloseHandle
CloseWindow
CoCreateInstance
CoInitialize
CoUninitialize
Content-Disposition: form-data; name="
Content-Type: multipart/form-data; boundary=----
Cookies
CopyFileA
CreateCompatibleBitmap
CreateCompatibleDC
CreateDCA
CreateEventA
CreateFileA
CreateStreamOnHGlobal
CreateToolhelp32Snapshot
CryptBinaryToStringA
CryptStringToBinaryA
CryptUnprotectData
Current User:
D877F783D5D3EF8C*
DD5$R)Z
DISPLAY
DeleteFileA
DeleteObject
DialogConfig.vdf
DialogConfigOverlay*.vdf
DisplayName
DisplayVersion
EnumDisplayDevicesA
ExitProcess
F8806DD0C461824F*
FALSE
FindClose
FindFirstFileA
FindNextFileA
FreeLibrary
GdipCreateBitmapFromHBITMAP
GdipDisposeImage
GdipFree
GdipGetImageEncodrs
GdipGetImageEncodrsSize
GdipSaveImageoStream
GdiplusShutdown
GdiplusStartup
GetComputerNameA
GetCurrentProcess
GetCurrentProcessId
GetDC
GetDesktopWindow
GetDeviceCaps
GetEnvironmentVariableA
GetFileAttributesA
GetFileSize
GetFileSizeEx
GetHGlobalFromStram
GetKeyboardLayoutList
GetLastError
GetLocalTime
GetLocaleInfoA
GetLogicalProcessorInformationEx
GetModuleFileNameA
GetModuleFileNameExA
GetProcAddress
GetProcessHeap
GetSystemInfo
GetSystemPowerStatus
GetSystemTime
GetTimeZoneInformation
GetUserDefaultLangID
GetUserDefaultLocaleName
GetUserNameA
GetVolumeInformationA
GetWindowRect
GetWindowsDirectoryA
GlobalFree
GlobalLock
GlobalMemoryStatusEx
GlobalSize
Globallloc
HAL9TH
HARDWARE\DESCRIPTION\System\CentralProcessor\0
HTTP/1.1
HeapAlloc
HeapFree
History
HttpOpenRequestA
HttpSendRequestA
IndexedDB
Installed Apps:
InternetCloseHandle
InternetConnectA
InternetCrackUrlA
InternetOpenA
InternetOpenUrlA
InternetReadFile
IsWow64Process
JohnDoe
LoadLibraryA
Local Extension Sttings
Local State
LocalAlloc
LocalFree
Login Data
MultiByteToWideChar
NSS_Init
NSS_Shutdown
Network
Network Info:
OpenEventA
OpenProcess
Opera
Opera GX Stable
Opera Stable
OperaGX
P#0xH r
PATH
PK11SDR_Decrypt
PK11_Authenticate
PK11_FreeSlot
PK11_GetInternalKySlot
POST
Password
PathMatchSpecA
Pidgin
Process List:
Process32First
Process32Next
ProcessorNameString
ProductName
ReadFile
RegCloseKey
RegEnumKeyExA
RegEnumValueA
RegOpenKeyExA
RegQuerValueExA
ReleaseDC
RmEndSession
RmGetList
RmRegisterResourcs
RmStartSession
SELECT HOST_KEY, is_httponly, path, is_secure, (expires_utc/1000000)-1164480800, name, encrypted_value from cookies
SELECT fieldname, value FROM moz_formhistory
SELECT host, isHttpOnly, path, isSecure, expiry, name, value FROM moz_cookies
SELECT name, valu FROM autofill
SELECT name_on_card, expiration_month, expiration_year, card_number_encrypted FROM credit_cards
SELECT origin_url, username_value, password_value FROM logins
SELECT url FROM moz_places LIMIT 1000
SELECT url FROM urls LIMIT 1000
SHGetFolderPathA
SOFTWARE\Microsoft\Windows NT\CurrentVersion
SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
SelectObject
SetEnvironmentVariableA
SetFilePointer
ShellExecuteExA
Sleep
Software\Microsoft\Office\13.0\Outlook\Profiles\Outlo\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office\14.0\Outlook\Profiles\Outlo\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office\15.0\Outlook\Profiles\Outlo\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office\16.0\Outlook\Profiles\Outlo\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
Software\Valve\Stam
SteamPath
StrCmpCA
StrCmpCW
StrStr
Sync Extension Settings
System Summary:
SystemTimeToFileTime
TRUE
Telegram
TerminateProcess
User Agents:
VMwareVMware
VirtualAlloc
VirtualAllocExNuma
VirtualFree
VirtualProtect
Web Data
WideCharToMultiByte
WriteFile
\.purple\
\?jQhsa
\Discord\tokens.txt
\Local Storage\leveldb
\Local Storage\leveldb\CURRENT
\Outlook\accounts.txt
\Steam\
\Telegram Desktop\
\Temp\
\config\
\discord\
_0.indexeddb.leveldb
accounts.xml
advapi32.dll
autofill
bcrypt.dll
browser:
browsers
build
card:
chrome
chrome-extension_
config.vdf
cookies
cookies.sqlite
crypt32.dll
dQw4w9WgXcQ
default
done
encryptedPassword
encryptedUsername
encrypted_key
file
file_name
files
firefox
formSubmitURL
formhistory.sqlit
freebl3.dll
gdi2.dll
gdiplus.dll
guid
history
http://kevinrobinson.top
https
hwid
key_datas
libraryfolders.vdf
login:
logins.json
loginusers.vdf
lstrcatA
lstrcpyA
lstrcpynA
lstrlenA
map*
message
month:
mozglue.dll
msvcp140.dll
name:
nss.dll
ntdll.dll
oftware\Microsoft\Windows Messaging Subsystem\Profiles\9375CFF0413111d3B88A00104B2A6676\
ole2.dll
open
opera
password:
places.sqlite
plugins
profile:
profiles.ini
psapi.dll
rstrtmgr.dll
runas
screenshot.jpg
shell32.dll
shlwapi.dll
soft
softokn3.dll
sqlite3.dll
sqlite3_close
sqlite3_column_blob
sqlite3_column_bytes
sqlite3_column_text
sqlite3_finalize
sqlite3_open
sqlite3_prepare_v2
sqlite3_step
sscanf
ssfn*
system_info.txt
token
token:
url:
user32.dll
usernameField
vcruntime140.dll
wallets
wininet.dll
wsprintfA
wsprintfW
year:
(PID) Process(1076) ffUbNlFyy94bJxTL_5Ig97z6.exe
C2http://kevinrobinson.top/e9c345fc99a4e67e.php
Keys
RC49478689687193229132746546166
Strings (346)" & del "C:\ProgramData\*.dll"" & exit
#ea6@I?!KP
%08lX%04lX%lu
%APPDATA%
%DESKTOP%
%DOCUMENTS%
%LOCALPPDATA%
%PROGRMFILES%
%PROGRMFILES_86%
%RECENT%
%USERPROFILE%
%d/%d/%d %d:%d:%d
%hu/%hu/%hu
*.ini
*.lnk
*.tox
+E+@_W
- Architecture:
- CPU:
- Computer Name:
- Cores:
- Country: ISO?
- Display Resolution:
- GPU:
- HWID:
- IP: IP?
- Keyboards:
- Language:
- Laptop:
- Local Time:
- OS:
- RAM:
- Running Path:
- Threads:
- UTC:
- UserName:
.exe
.txt
/412a0310f85f16ad/
/c start
/c timeout /t 5 & del /f /q "
/e9c345fc99a4e67e.php
00000001
00000002
00000003
00000004
A7FDF864FBC10B77*
A92DAA6EA6F891F2*
ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890
All Users:
BCryptCloseAlgorithmProvider
BCryptDecrypt
BCryptDestroyKey
BCryptGenerateSymmetricKey
BCryptOpenAlgorithmProvider
BCryptSetProperty
BitBlt
C:\ProgramData\
C:\ProgramData\nss3.dll
C:\Windows\system32\cmd.exe
CURRENT
CharToOemW
CloseHandle
CloseWindow
CoCreateInstance
CoInitialize
CoUninitialize
Content-Disposition: form-data; name="
Content-Type: multipart/form-data; boundary=----
Cookies
CopyFileA
CreateCompatibleBitmap
CreateCompatibleDC
CreateDCA
CreateEventA
CreateFileA
CreateStreamOnHGlobal
CreateToolhelp32Snapshot
CryptBinaryToStringA
CryptStringToBinaryA
CryptUnprotectData
Current User:
D877F783D5D3EF8C*
DD5$R)Z
DISPLAY
DeleteFileA
DeleteObject
DialogConfig.vdf
DialogConfigOverlay*.vdf
DisplayName
DisplayVersion
EnumDisplayDevicesA
ExitProcess
F8806DD0C461824F*
FALSE
FindClose
FindFirstFileA
FindNextFileA
FreeLibrary
GdipCreateBitmapFromHBITMAP
GdipDisposeImage
GdipFree
GdipGetImageEncodrs
GdipGetImageEncodrsSize
GdipSaveImageoStream
GdiplusShutdown
GdiplusStartup
GetComputerNameA
GetCurrentProcess
GetCurrentProcessId
GetDC
GetDesktopWindow
GetDeviceCaps
GetEnvironmentVariableA
GetFileAttributesA
GetFileSize
GetFileSizeEx
GetHGlobalFromStram
GetKeyboardLayoutList
GetLastError
GetLocalTime
GetLocaleInfoA
GetLogicalProcessorInformationEx
GetModuleFileNameA
GetModuleFileNameExA
GetProcAddress
GetProcessHeap
GetSystemInfo
GetSystemPowerStatus
GetSystemTime
GetTimeZoneInformation
GetUserDefaultLangID
GetUserDefaultLocaleName
GetUserNameA
GetVolumeInformationA
GetWindowRect
GetWindowsDirectoryA
GlobalFree
GlobalLock
GlobalMemoryStatusEx
GlobalSize
Globallloc
HAL9TH
HARDWARE\DESCRIPTION\System\CentralProcessor\0
HTTP/1.1
HeapAlloc
HeapFree
History
HttpOpenRequestA
HttpSendRequestA
IndexedDB
Installed Apps:
InternetCloseHandle
InternetConnectA
InternetCrackUrlA
InternetOpenA
InternetOpenUrlA
InternetReadFile
IsWow64Process
JohnDoe
LoadLibraryA
Local Extension Sttings
Local State
LocalAlloc
LocalFree
Login Data
MultiByteToWideChar
NSS_Init
NSS_Shutdown
Network
Network Info:
OpenEventA
OpenProcess
Opera
Opera GX Stable
Opera Stable
OperaGX
P#0xH r
PATH
PK11SDR_Decrypt
PK11_Authenticate
PK11_FreeSlot
PK11_GetInternalKySlot
POST
Password
PathMatchSpecA
Pidgin
Process List:
Process32First
Process32Next
ProcessorNameString
ProductName
ReadFile
RegCloseKey
RegEnumKeyExA
RegEnumValueA
RegOpenKeyExA
RegQuerValueExA
ReleaseDC
RmEndSession
RmGetList
RmRegisterResourcs
RmStartSession
SELECT HOST_KEY, is_httponly, path, is_secure, (expires_utc/1000000)-1164480800, name, encrypted_value from cookies
SELECT fieldname, value FROM moz_formhistory
SELECT host, isHttpOnly, path, isSecure, expiry, name, value FROM moz_cookies
SELECT name, valu FROM autofill
SELECT name_on_card, expiration_month, expiration_year, card_number_encrypted FROM credit_cards
SELECT origin_url, username_value, password_value FROM logins
SELECT url FROM moz_places LIMIT 1000
SELECT url FROM urls LIMIT 1000
SHGetFolderPathA
SOFTWARE\Microsoft\Windows NT\CurrentVersion
SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
SelectObject
SetEnvironmentVariableA
SetFilePointer
ShellExecuteExA
Sleep
Software\Microsoft\Office\13.0\Outlook\Profiles\Outlo\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office\14.0\Outlook\Profiles\Outlo\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office\15.0\Outlook\Profiles\Outlo\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office\16.0\Outlook\Profiles\Outlo\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
Software\Valve\Stam
SteamPath
StrCmpCA
StrCmpCW
StrStr
Sync Extension Settings
System Summary:
SystemTimeToFileTime
TRUE
Telegram
TerminateProcess
User Agents:
VMwareVMware
VirtualAlloc
VirtualAllocExNuma
VirtualFree
VirtualProtect
Web Data
WideCharToMultiByte
WriteFile
\.purple\
\Discord\tokens.txt
\Local Storage\leveldb
\Local Storage\leveldb\CURRENT
\Outlook\accounts.txt
\Steam\
\Telegram Desktop\
\Temp\
\config\
\discord\
_0.indexeddb.leveldb
accounts.xml
advapi32.dll
autofill
bcrypt.dll
browser:
browsers
build
card:
chrome
chrome-extension_
config.vdf
cookies
cookies.sqlite
crypt32.dll
dQw4w9WgXcQ
default
done
encryptedPassword
encryptedUsername
encrypted_key
file
file_name
files
firefox
formSubmitURL
formhistory.sqlit
freebl3.dll
gdi2.dll
gdiplus.dll
guid
history
http://kevinrobinson.top
https
hwid
key_datas
libraryfolders.vdf
login:
logins.json
loginusers.vdf
lstrcatA
lstrcpyA
lstrcpynA
lstrlenA
map*
message
month:
mozglue.dll
msvcp140.dll
name:
nss.dll
ntdll.dll
oftware\Microsoft\Windows Messaging Subsystem\Profiles\9375CFF0413111d3B88A00104B2A6676\
ole2.dll
open
opera
password:
places.sqlite
plugins
profile:
profiles.ini
psapi.dll
rstrtmgr.dll
runas
screenshot.jpg
shell32.dll
shlwapi.dll
soft
softokn3.dll
sqlite3.dll
sqlite3_close
sqlite3_column_blob
sqlite3_column_bytes
sqlite3_column_text
sqlite3_finalize
sqlite3_open
sqlite3_prepare_v2
sqlite3_step
sscanf
ssfn*
system_info.txt
token
token:
url:
user32.dll
usernameField
vcruntime140.dll
wallets
wininet.dll
wsprintfA
wsprintfW
year:
PrivateLoader
(PID) Process(3260) HfBbiQ5JHrhsuHIsvEd0hpUA.exe
C2 (4)193.42.32.118
94.142.138.131
94.142.138.113
208.67.104.60
Strings (62)Unknown
SOFTWARE\Microsoft\Cryptography
MachineGuid
telegram.org
twitter.com
yandex.ru
google.com
/api/tracemap.php
http://
15.5pnp.10.lock
data=
/api/firecom.php
ipinfo.io/widget
country
db-ip.com
data-api-key="
/self
countryCode
www.maxmind.com/geoip/v2.1/city/me
iso_code
GetIP
api.ipgeolocation.io/ipgeo?include=hostname&ip=
country_code2
PowerControl
\PowerControl
\PowerControl_Svc.exe
Power monitoring service for your device.
WININET.dll
WINHTTP.dll
193.42.32.118
94.142.138.131
94.142.138.113
208.67.104.60
GetVersion|
GetUpdateLink
https://
Later
" /tn "PowerControl HR" /sc HOURLY /rl HIGHEST
schtasks /create /f /RU "
" /tn "PowerControl LG" /sc ONLOGON /rl HIGHEST
WinHttpConnect
WinHttpQueryHeaders
WinHttpOpen
WinHttpOpenRequest
WinHttpQueryDataAvailable
WinHttpSendRequest
WinHttpReceiveResponse
WinHttpReadData
WinHttpCloseHandle
WinHttpSetTimeouts
CharNextA
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3729.169 Safari/537.36
InternetOpenA
InternetSetOptionA
HttpOpenRequestA
InternetConnectA
InternetOpenUrlA
HttpQueryInfoA
InternetQueryOptionA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
(PID) Process(4888) hYmVKq29CP_wOpmXXx9U8Ccz.exe
C2 (4)193.42.32.118
94.142.138.131
94.142.138.113
208.67.104.60
Strings (62)Unknown
SOFTWARE\Microsoft\Cryptography
MachineGuid
telegram.org
twitter.com
yandex.ru
google.com
/api/tracemap.php
http://
15.5pnp.10.lock
data=
/api/firecom.php
ipinfo.io/widget
country
db-ip.com
data-api-key="
/self
countryCode
www.maxmind.com/geoip/v2.1/city/me
iso_code
GetIP
api.ipgeolocation.io/ipgeo?include=hostname&ip=
country_code2
PowerControl
\PowerControl
\PowerControl_Svc.exe
Power monitoring service for your device.
WININET.dll
WINHTTP.dll
193.42.32.118
94.142.138.131
94.142.138.113
208.67.104.60
GetVersion|
GetUpdateLink
https://
Later
" /tn "PowerControl HR" /sc HOURLY /rl HIGHEST
schtasks /create /f /RU "
" /tn "PowerControl LG" /sc ONLOGON /rl HIGHEST
WinHttpConnect
WinHttpQueryHeaders
WinHttpOpen
WinHttpOpenRequest
WinHttpQueryDataAvailable
WinHttpSendRequest
WinHttpReceiveResponse
WinHttpReadData
WinHttpCloseHandle
WinHttpSetTimeouts
CharNextA
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3729.169 Safari/537.36
InternetOpenA
InternetSetOptionA
HttpOpenRequestA
InternetConnectA
InternetOpenUrlA
HttpQueryInfoA
InternetQueryOptionA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
Arkei
(PID) Process(2104) VC2YEgro4cHXWrr3zBMAPM40.exe
C2 (2)https://t.me/twowheelfun
https://steamcommunity.com/profiles/76561199563297648
Strings (531)kernel32.dll
GetUserNameA
advapi32.dll
GetComputerNameA
LocalAlloc
lstrcmpiW
VirtualFree
VirtualAlloc
VirtualAllocExNuma
GetCurrentProcess
ExitProcess
GetSystemTime
Sleep
GetProcAddress
lstrcatA
LoadLibraryA
JohnDoe
HAL9TH
Ledger Live
\Raven\
Raven Core
\Dogecoin\
Dogecoin
*wallet*.dat
wallet.dat
\Bitcoin\
Bitcoin Core Old
\Bitcoin\wallets\
Bitcoin Core
.finger-print.fp
simple-storage.json
Binance Desktop
loginusers.vdf
libraryfolders.vdf
DialogConfigOverlay*.vdf
DialogConfig.vdf
config.vdf
ssfn*
SteamPath
Software\Valve\Steam
C:\\\Windows\
C:\\Windows\
C:\Windows\
*%DRIVE_REMOVABLE%*
*%DRIVE_FIXED%*
*%RECENT%*
%DRIVE_REMOVABLE%
%DRIVE_FIXED%
%RECENT%
%PROGRAMFILES_86%
%PROGRAMFILES%
%DOCUMENTS%
%DESKTOP%
%USERPROFILE%
%LOCALAPPDATA%
%APPDATA%
\information.txt
[Software]
[Processes]
VideoCard:
RAM:
CPU Count:
Processor:
[Hardware]
TimeZone:
Local Time:
Keyboard Languages:
Display Language:
Display Resolution:
User Name:
Computer Name:
Windows:
Work Dir: In memory
Path:
HWID:
GUID:
MachineID:
Date:
Version:
sqlite3.dll
RoninWalletEdge
kjmoohlgokccodicjjfebfomlbljgfhk
IndexedDB
Sync Extension Settings
Local Extension Settings
UseMasterPassword
Security
Password
UserName
PortNumber
HostName
Soft: WinSCP
\Soft\Authy Desktop\
\Authy Desktop\Local Storage\leveldb\
\Soft\Authy Desktop Old\
\Authy Desktop\Local Storage\
*.localstorage
places.sqlite
formhistory.sqlite
cookies.sqlite
History
SELECT fieldname, value FROM moz_formhistory
SELECT url FROM moz_places
SELECT host, isHttpOnly, path, isSecure, expiry, name, value FROM moz_cookies
Network
Password:
Login:
Host:
Soft:
"os_crypt":{"encrypted_key":"
\passwords.txt
\Soft\Telegram\
F8806DD0C461824F*
A92DAA6EA6F891F2*
A7FDF864FBC10B77*
D877F783D5D3EF8C*
key_datas
\Telegram Desktop\
Thunderbird
\Thunderbird\Profiles\
Brave
\BraveSoftware\Brave-Browser\User Data\
CryptoTab Browser
\CryptoTab Browser\User Data\
\Opera GX Stable\
\Opera Stable\
\Opera Software\
sqlite3_column_blob
sqlite3_column_bytes
sqlite3_close
sqlite3_finalize
sqlite3_column_text
sqlite3_step
sqlite3_prepare_v2
sqlite3_open
GdipFree
GdipDisposeImage
GdipSaveImageToStream
GdiplusShutdown
GdiplusStartup
GdipCreateBitmapFromHBITMAP
GdipGetImageEncoders
GdipGetImageEncodersSize
SymMatchString
PathFindFileNameA
StrStrA
StrCmpCW
StrCmpCA
PathMatchSpecA
PathMatchSpecW
SHGetFolderPathA
SHFileOperationA
ShellExecuteExA
CloseWindow
GetWindowDC
GetWindowRect
GetHGlobalFromStream
CreateStreamOnHGlobal
CoInitialize
InternetCrackUrlA
AccessCheck
MapGenericMask
DuplicateToken
OpenProcessToken
GetFileSecurityA
RegEnumValueA
CryptBinaryToStringA
gdiplus.dll
dbghelp.dll
shlwapi.dll
shell32.dll
GetVolumeInformationA
GetWindowsDirectoryA
Process32Next
Process32First
CreateToolhelp32Snapshot
CreateEventA
OpenEventA
GetTickCount
SetEnvironmentVariableA
GetEnvironmentVariableA
GetFileInformationByHandle
CreateFileMappingA
FileTimeToSystemTime
UnmapViewOfFile
MapViewOfFile
LocalFileTimeToFileTime
GetFileAttributesA
WriteFile
SetFileTime
GetLocalTime
SystemTimeToFileTime
HeapFree
SetFilePointer
GetCurrentDirectoryA
DeleteFileA
CopyFileA
TzSpecificLocalTimeToSystemTime
GetTimeZoneInformation
GetFileSizeEx
OpenProcess
GetCurrentProcessId
GetLocaleInfoA
FreeLibrary
GlobalSize
GlobalLock
lstrcpynA
GetLastError
FindClose
FindNextFileA
FindFirstFileA
MultiByteToWideChar
lstrcpyA
GetDriveTypeA
lstrlenA
GetLogicalDriveStringsA
CloseHandle
ReadFile
GetFileSize
CreateFileA
GetProcessHeap
HeapAlloc
LocalFree
WideCharToMultiByte
GetSystemInfo
GetUserDefaultLocaleName
IsWow64Process
GlobalMemoryStatusEx
CreateThread
Discord Token:
dQw4w9WgXcQ:
\Soft\Discord\discord_tokens.txt
Session Storage
leveldb
Local Storage
Discord
\discord\
Wasabi Wallet
\WalletWasabi\Client\Wallets\
Blockstream Green
\Blockstream\Green\wallets\
she*.sqlite
Daedalus Mainnet
\Daedalus Mainnet\wallets\
Jaxx_Desktop
\com.liberty.jaxx\IndexedDB\file__0.indexeddb.leveldb\
GAuth Authenticator
ilgcnhelpchnceeipipijaljkblbcobl
EOS Authenticator
oeljdldpnmdbchonielidgobddffflal
Authy
gaedmjdfmmahhbjefcbgaolhhanlaolb
Authenticator
bhghoamapcdpbohphigoooaddinpkbai
jnkelfanjkeadonecabehalmbgpfodjm
Temple
ookjlbkiijinhpmnjffcofjonbfbgaoc
TezBox
mnfifefkajgofkcjkemidiaecocnkjeh
hcflpincpppdclinealmandijcmnkbgn
CyanoWallet
dkdedlpgdmmkkfjabffeganieamfklkm
Solflare
bhhhlbepdkbapadjdnnojkbgioiodbic
WavesKeeper
lpilbniiabackdjcionkobglmddfbcjo
MaiarDeFiWallet
dngmlblcodfobpdpecaadgfbcggfjfnm
NamiWallet
lpfcbjknijpeeillifnkikgncikgfhdo
XdefiWallet
hmeobnfnfcmdkdcmlblgagmfpfboieaf
BoltX
aodkkagnadcbobfpggfnjeongemjbjca
PaliWallet
mgffkfbidihjpoaomajlbgchddlicgpn
Oxygen (Atomic)
fhilaheimglignddkjgofkcbgekhenbh
BraveWallet
odbfpeeihdkbihmopkbjmoonfanlbfcl
ejbalbakoplchlghecdalmeeeajnimhm
Phantom
bfnaelmomeimhlpmgjnjophhpkkoljpa
Rabby
acmacodkjbdgmoleebolmdjonilkdbch
Trezor Password Manager
imloifkgjagghnncjkhggdhalmcnfklk
KardiaChain
pdadjkfkgcafgbceimcpbkalnfnepbnk
EVER Wallet
cgeeodpfagjceefieflmdfphplkenlfk
Coin98
aeachknmefphepccionboohckonoeemg
Harmony
fnnegphlobjdpkhecapkijjdkgcjhkib
ICONex
flpiciilemghbmfalicajoolhkkenfel
PolymeshWallet
jojhfeoedkpkglbfimdfabpdfjaoolaf
AuroWallet
cnmamaachppnkjgnildpdmkaakejnhae
Sollet
fhmfendgdocmcbmfikdcogofphimnkno
Keplr
dmkamcknogkgcdfhhbddcghachkejeap
Terra_Station
aiifbnbfobpmeekipheeijimdpnlpgpp
LiqualityWallet
kpfopkelmapcoipemfendmdcghnegimn
CloverWallet
nhnkbkgjikgcigadomkphalanndcapjk
NeoLine
cphhlgmgameodnhkjdmkpanlelnlohao
RoninWallet
fnjhmkhhmkbjkkabndcnnogagogbneec
GuildWallet
nanjmdknhkinifnkgdcggcfnhdaammmj
MewCx
nlbmnnijcnlegkjjpcfjclmcfggfefdm
Wombat
amkmjjmmflddogmhpjloimipbofnfjih
iWallet
kncchdigobghenbbaddojjnnaogfppfj
BitAppWallet
fihkakfobkmkjojpchpfgcmhfjnmnfpi
JaxxLiberty
cjelfplplebdjjenllpjcblmjkfcffne
EQUALWallet
blnieiiffboillknjnepogjhkgnoapac
Guarda
hpglfhgfnhbgpjdenjgmdgoeiappafln
Coinbase
hnfanknocfeofbddgcijnmhnfnkdnaad
MathWallet
afbcbjpbpfadlkmhmclhkeeodmamcflc
NiftyWallet
jbdaocneiiinmjbjlgalhcelgbejmnid
Yoroi
ffnbelfdoeiohenkjibnmadjiehjhajb
BinanceChainWallet
fhbohimaelbohpjbbldcngcnapndodjp
MetaMask
nkbihfbeogaeaoehlefnkodbefgpgknn
TronLink
ibnejdfjmmkpcnlpebklmnkoeoihofec
EnumProcessModules
GetModuleBaseNameA
GetModuleFileNameExA
GetSystemMetrics
EnumDisplayDevicesA
wsprintfA
GetDC
CharToOemA
GetKeyboardLayoutList
ReleaseDC
GetDesktopWindow
CoUninitialize
CoCreateInstance
CreateCompatibleDC
GetDeviceCaps
CreateDCA
DeleteObject
BitBlt
SelectObject
CreateCompatibleBitmap
DeleteUrlCacheEntry
InternetSetOptionA
InternetOpenUrlA
InternetSetFilePointer
HttpQueryInfoA
HttpAddRequestHeadersA
InternetOpenA
InternetConnectA
HttpOpenRequestA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
wininet.dll
RegGetValueA
RegGetValueW
RegOpenKeyExW
RegCloseKey
RegQueryValueExA
RegOpenKeyExA
PK11SDR_Decrypt
PK11_Authenticate
PK11_FreeSlot
PK11_GetInternalKeySlot
NSS_Shutdown
NSS_Init
C:\ProgramData\nss3.dll
CryptStringToBinaryA
CryptUnprotectData
CRYPT32.DLL
BCryptDecrypt
BCryptGenerateSymmetricKey
BCryptSetProperty
BCryptOpenAlgorithmProvider
BCryptDestroyKey
BCryptCloseAlgorithmProvider
BCRYPT.DLL
psapi.dll
user32.dll
ole32.dll
gdi32.dll
FALSE
Cookies
Local State
\Opera Software\Opera GX Stable\
OperaGX
\Opera Software\Opera Stable\
Opera
\Tencent\QQBrowser\User Data\
QQBrowser
\360Browser\Browser\User Data\
360 Browser
\Microsoft\Edge\User Data\
Microsoft Edge
\7Star\7Star\User Data\
7Star
\brave\
Brave_Old
\Chedot\User Data\
Chedot Browser
\TorBro\Profile\
TorBro Browser
\CentBrowser\User Data\
Cent Browser
\CocCoc\Browser\User Data\
CocCoc
\Vivaldi\User Data\
Vivaldi
\Epic Privacy Browser\User Data\
Epic Privacy Browser
\Comodo\Dragon\User Data\
Comodo Dragon
\Torch\User Data\
Torch
\Amigo\User Data\
Amigo
\Chromium\User Data\
Chromium
\Google\Chrome\User Data\
Google Chrome
\Moonchild Productions\Pale Moon\Profiles\
Pale Moon
\Mozilla\Firefox\Profiles\
Mozilla Firefox
Soft: FileZilla
<Pass encoding="base64">
<User>
<Port>
<Host>
\AppData\Roaming\FileZilla\recentservers.xml
SELECT HOST_KEY, is_httponly, path, is_secure, (expires_utc/1000000)-11644480800, name, encrypted_value from cookies
SELECT url FROM urls
SELECT target_path, tab_url from downloads
SELECT name_on_card, expiration_month, expiration_year, card_number_encrypted FROM credit_cards
SELECT name, value FROM autofill
SELECT origin_url, username_value, password_value FROM logins
encryptedPassword
encryptedUsername
usernameField
formSubmitURL
logins.json
Web Data
Cookies
Login Data
netfulfilled
mnpayments
mncache
governance
banlist
mempool
peers
fee_estimates
Local\Microsoft
Roaming\WinRAR
Local\NuGet
Local\Packages
MicrosoftEdge\Cookies
Recycle.Bin
Local\Temp
Recovery
msdownld.tmp
System Volume Information
Config.Msi
RECYCLE.BIN
C:\ProgramData\
\Monero\
SOFTWARE\monero-project\monero-core
wallet_path
*.config
*.wallet
\Coinomi\Coinomi\wallets\
Coinomi
app-store.json
\Binance\
Binance
0000*
MANIFEST-000001
CURRENT
*.log
\atomic\Local Storage\leveldb\
Atomic
file__0.localstorage
\jaxx\Local Storage\
Jaxx_Desktop_Old
multidoge.wallet
\MultiDoge\
MultiDoge
default_wallet
\ElectronCash\wallets\
ElectronCash
info.seco
seed.seco
passphrase.json
\Exodus\exodus.wallet\
window-state.json
exodus.conf.json
\Exodus\
Exodus
\Electrum-LTC\wallets\
ElectrumLTC
\Electrum\wallets\
Electrum
\Ethereum\
Ethereum"
keystore
Plugins
Wallets
(PID) Process(2476) build2.exe
C2 (2)https://t.me/twowheelfun
https://steamcommunity.com/profiles/76561199563297648
Strings (531)kernel32.dll
GetUserNameA
advapi32.dll
GetComputerNameA
LocalAlloc
lstrcmpiW
VirtualFree
VirtualAlloc
VirtualAllocExNuma
GetCurrentProcess
ExitProcess
GetSystemTime
Sleep
GetProcAddress
lstrcatA
LoadLibraryA
JohnDoe
HAL9TH
Ledger Live
\Raven\
Raven Core
\Dogecoin\
Dogecoin
*wallet*.dat
wallet.dat
\Bitcoin\
Bitcoin Core Old
\Bitcoin\wallets\
Bitcoin Core
.finger-print.fp
simple-storage.json
Binance Desktop
loginusers.vdf
libraryfolders.vdf
DialogConfigOverlay*.vdf
DialogConfig.vdf
config.vdf
ssfn*
SteamPath
Software\Valve\Steam
C:\\\Windows\
C:\\Windows\
C:\Windows\
*%DRIVE_REMOVABLE%*
*%DRIVE_FIXED%*
*%RECENT%*
%DRIVE_REMOVABLE%
%DRIVE_FIXED%
%RECENT%
%PROGRAMFILES_86%
%PROGRAMFILES%
%DOCUMENTS%
%DESKTOP%
%USERPROFILE%
%LOCALAPPDATA%
%APPDATA%
\information.txt
[Software]
[Processes]
VideoCard:
RAM:
CPU Count:
Processor:
[Hardware]
TimeZone:
Local Time:
Keyboard Languages:
Display Language:
Display Resolution:
User Name:
Computer Name:
Windows:
Work Dir: In memory
Path:
HWID:
GUID:
MachineID:
Date:
Version:
sqlite3.dll
RoninWalletEdge
kjmoohlgokccodicjjfebfomlbljgfhk
IndexedDB
Sync Extension Settings
Local Extension Settings
UseMasterPassword
Security
Password
UserName
PortNumber
HostName
Soft: WinSCP
\Soft\Authy Desktop\
\Authy Desktop\Local Storage\leveldb\
\Soft\Authy Desktop Old\
\Authy Desktop\Local Storage\
*.localstorage
places.sqlite
formhistory.sqlite
cookies.sqlite
History
SELECT fieldname, value FROM moz_formhistory
SELECT url FROM moz_places
SELECT host, isHttpOnly, path, isSecure, expiry, name, value FROM moz_cookies
Network
Password:
Login:
Host:
Soft:
"os_crypt":{"encrypted_key":"
\passwords.txt
\Soft\Telegram\
F8806DD0C461824F*
A92DAA6EA6F891F2*
A7FDF864FBC10B77*
D877F783D5D3EF8C*
key_datas
\Telegram Desktop\
Thunderbird
\Thunderbird\Profiles\
Brave
\BraveSoftware\Brave-Browser\User Data\
CryptoTab Browser
\CryptoTab Browser\User Data\
\Opera GX Stable\
\Opera Stable\
\Opera Software\
sqlite3_column_blob
sqlite3_column_bytes
sqlite3_close
sqlite3_finalize
sqlite3_column_text
sqlite3_step
sqlite3_prepare_v2
sqlite3_open
GdipFree
GdipDisposeImage
GdipSaveImageToStream
GdiplusShutdown
GdiplusStartup
GdipCreateBitmapFromHBITMAP
GdipGetImageEncoders
GdipGetImageEncodersSize
SymMatchString
PathFindFileNameA
StrStrA
StrCmpCW
StrCmpCA
PathMatchSpecA
PathMatchSpecW
SHGetFolderPathA
SHFileOperationA
ShellExecuteExA
CloseWindow
GetWindowDC
GetWindowRect
GetHGlobalFromStream
CreateStreamOnHGlobal
CoInitialize
InternetCrackUrlA
AccessCheck
MapGenericMask
DuplicateToken
OpenProcessToken
GetFileSecurityA
RegEnumValueA
CryptBinaryToStringA
gdiplus.dll
dbghelp.dll
shlwapi.dll
shell32.dll
GetVolumeInformationA
GetWindowsDirectoryA
Process32Next
Process32First
CreateToolhelp32Snapshot
CreateEventA
OpenEventA
GetTickCount
SetEnvironmentVariableA
GetEnvironmentVariableA
GetFileInformationByHandle
CreateFileMappingA
FileTimeToSystemTime
UnmapViewOfFile
MapViewOfFile
LocalFileTimeToFileTime
GetFileAttributesA
WriteFile
SetFileTime
GetLocalTime
SystemTimeToFileTime
HeapFree
SetFilePointer
GetCurrentDirectoryA
DeleteFileA
CopyFileA
TzSpecificLocalTimeToSystemTime
GetTimeZoneInformation
GetFileSizeEx
OpenProcess
GetCurrentProcessId
GetLocaleInfoA
FreeLibrary
GlobalSize
GlobalLock
lstrcpynA
GetLastError
FindClose
FindNextFileA
FindFirstFileA
MultiByteToWideChar
lstrcpyA
GetDriveTypeA
lstrlenA
GetLogicalDriveStringsA
CloseHandle
ReadFile
GetFileSize
CreateFileA
GetProcessHeap
HeapAlloc
LocalFree
WideCharToMultiByte
GetSystemInfo
GetUserDefaultLocaleName
IsWow64Process
GlobalMemoryStatusEx
CreateThread
Discord Token:
dQw4w9WgXcQ:
\Soft\Discord\discord_tokens.txt
Session Storage
leveldb
Local Storage
Discord
\discord\
Wasabi Wallet
\WalletWasabi\Client\Wallets\
Blockstream Green
\Blockstream\Green\wallets\
she*.sqlite
Daedalus Mainnet
\Daedalus Mainnet\wallets\
Jaxx_Desktop
\com.liberty.jaxx\IndexedDB\file__0.indexeddb.leveldb\
GAuth Authenticator
ilgcnhelpchnceeipipijaljkblbcobl
EOS Authenticator
oeljdldpnmdbchonielidgobddffflal
Authy
gaedmjdfmmahhbjefcbgaolhhanlaolb
Authenticator
bhghoamapcdpbohphigoooaddinpkbai
jnkelfanjkeadonecabehalmbgpfodjm
Temple
ookjlbkiijinhpmnjffcofjonbfbgaoc
TezBox
mnfifefkajgofkcjkemidiaecocnkjeh
hcflpincpppdclinealmandijcmnkbgn
CyanoWallet
dkdedlpgdmmkkfjabffeganieamfklkm
Solflare
bhhhlbepdkbapadjdnnojkbgioiodbic
WavesKeeper
lpilbniiabackdjcionkobglmddfbcjo
MaiarDeFiWallet
dngmlblcodfobpdpecaadgfbcggfjfnm
NamiWallet
lpfcbjknijpeeillifnkikgncikgfhdo
XdefiWallet
hmeobnfnfcmdkdcmlblgagmfpfboieaf
BoltX
aodkkagnadcbobfpggfnjeongemjbjca
PaliWallet
mgffkfbidihjpoaomajlbgchddlicgpn
Oxygen (Atomic)
fhilaheimglignddkjgofkcbgekhenbh
BraveWallet
odbfpeeihdkbihmopkbjmoonfanlbfcl
ejbalbakoplchlghecdalmeeeajnimhm
Phantom
bfnaelmomeimhlpmgjnjophhpkkoljpa
Rabby
acmacodkjbdgmoleebolmdjonilkdbch
Trezor Password Manager
imloifkgjagghnncjkhggdhalmcnfklk
KardiaChain
pdadjkfkgcafgbceimcpbkalnfnepbnk
EVER Wallet
cgeeodpfagjceefieflmdfphplkenlfk
Coin98
aeachknmefphepccionboohckonoeemg
Harmony
fnnegphlobjdpkhecapkijjdkgcjhkib
ICONex
flpiciilemghbmfalicajoolhkkenfel
PolymeshWallet
jojhfeoedkpkglbfimdfabpdfjaoolaf
AuroWallet
cnmamaachppnkjgnildpdmkaakejnhae
Sollet
fhmfendgdocmcbmfikdcogofphimnkno
Keplr
dmkamcknogkgcdfhhbddcghachkejeap
Terra_Station
aiifbnbfobpmeekipheeijimdpnlpgpp
LiqualityWallet
kpfopkelmapcoipemfendmdcghnegimn
CloverWallet
nhnkbkgjikgcigadomkphalanndcapjk
NeoLine
cphhlgmgameodnhkjdmkpanlelnlohao
RoninWallet
fnjhmkhhmkbjkkabndcnnogagogbneec
GuildWallet
nanjmdknhkinifnkgdcggcfnhdaammmj
MewCx
nlbmnnijcnlegkjjpcfjclmcfggfefdm
Wombat
amkmjjmmflddogmhpjloimipbofnfjih
iWallet
kncchdigobghenbbaddojjnnaogfppfj
BitAppWallet
fihkakfobkmkjojpchpfgcmhfjnmnfpi
JaxxLiberty
cjelfplplebdjjenllpjcblmjkfcffne
EQUALWallet
blnieiiffboillknjnepogjhkgnoapac
Guarda
hpglfhgfnhbgpjdenjgmdgoeiappafln
Coinbase
hnfanknocfeofbddgcijnmhnfnkdnaad
MathWallet
afbcbjpbpfadlkmhmclhkeeodmamcflc
NiftyWallet
jbdaocneiiinmjbjlgalhcelgbejmnid
Yoroi
ffnbelfdoeiohenkjibnmadjiehjhajb
BinanceChainWallet
fhbohimaelbohpjbbldcngcnapndodjp
MetaMask
nkbihfbeogaeaoehlefnkodbefgpgknn
TronLink
ibnejdfjmmkpcnlpebklmnkoeoihofec
EnumProcessModules
GetModuleBaseNameA
GetModuleFileNameExA
GetSystemMetrics
EnumDisplayDevicesA
wsprintfA
GetDC
CharToOemA
GetKeyboardLayoutList
ReleaseDC
GetDesktopWindow
CoUninitialize
CoCreateInstance
CreateCompatibleDC
GetDeviceCaps
CreateDCA
DeleteObject
BitBlt
SelectObject
CreateCompatibleBitmap
DeleteUrlCacheEntry
InternetSetOptionA
InternetOpenUrlA
InternetSetFilePointer
HttpQueryInfoA
HttpAddRequestHeadersA
InternetOpenA
InternetConnectA
HttpOpenRequestA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
wininet.dll
RegGetValueA
RegGetValueW
RegOpenKeyExW
RegCloseKey
RegQueryValueExA
RegOpenKeyExA
PK11SDR_Decrypt
PK11_Authenticate
PK11_FreeSlot
PK11_GetInternalKeySlot
NSS_Shutdown
NSS_Init
C:\ProgramData\nss3.dll
CryptStringToBinaryA
CryptUnprotectData
CRYPT32.DLL
BCryptDecrypt
BCryptGenerateSymmetricKey
BCryptSetProperty
BCryptOpenAlgorithmProvider
BCryptDestroyKey
BCryptCloseAlgorithmProvider
BCRYPT.DLL
psapi.dll
user32.dll
ole32.dll
gdi32.dll
FALSE
Cookies
Local State
\Opera Software\Opera GX Stable\
OperaGX
\Opera Software\Opera Stable\
Opera
\Tencent\QQBrowser\User Data\
QQBrowser
\360Browser\Browser\User Data\
360 Browser
\Microsoft\Edge\User Data\
Microsoft Edge
\7Star\7Star\User Data\
7Star
\brave\
Brave_Old
\Chedot\User Data\
Chedot Browser
\TorBro\Profile\
TorBro Browser
\CentBrowser\User Data\
Cent Browser
\CocCoc\Browser\User Data\
CocCoc
\Vivaldi\User Data\
Vivaldi
\Epic Privacy Browser\User Data\
Epic Privacy Browser
\Comodo\Dragon\User Data\
Comodo Dragon
\Torch\User Data\
Torch
\Amigo\User Data\
Amigo
\Chromium\User Data\
Chromium
\Google\Chrome\User Data\
Google Chrome
\Moonchild Productions\Pale Moon\Profiles\
Pale Moon
\Mozilla\Firefox\Profiles\
Mozilla Firefox
Soft: FileZilla
<Pass encoding="base64">
<User>
<Port>
<Host>
\AppData\Roaming\FileZilla\recentservers.xml
SELECT HOST_KEY, is_httponly, path, is_secure, (expires_utc/1000000)-11644480800, name, encrypted_value from cookies
SELECT url FROM urls
SELECT target_path, tab_url from downloads
SELECT name_on_card, expiration_month, expiration_year, card_number_encrypted FROM credit_cards
SELECT name, value FROM autofill
SELECT origin_url, username_value, password_value FROM logins
encryptedPassword
encryptedUsername
usernameField
formSubmitURL
logins.json
Web Data
Cookies
Login Data
netfulfilled
mnpayments
mncache
governance
banlist
mempool
peers
fee_estimates
Local\Microsoft
Roaming\WinRAR
Local\NuGet
Local\Packages
MicrosoftEdge\Cookies
Recycle.Bin
Local\Temp
Recovery
msdownld.tmp
System Volume Information
Config.Msi
RECYCLE.BIN
C:\ProgramData\
\Monero\
SOFTWARE\monero-project\monero-core
wallet_path
*.config
*.wallet
\Coinomi\Coinomi\wallets\
Coinomi
app-store.json
\Binance\
Binance
0000*
MANIFEST-000001
CURRENT
*.log
\atomic\Local Storage\leveldb\
Atomic
file__0.localstorage
\jaxx\Local Storage\
Jaxx_Desktop_Old
multidoge.wallet
\MultiDoge\
MultiDoge
default_wallet
\ElectronCash\wallets\
ElectronCash
info.seco
seed.seco
passphrase.json
\Exodus\exodus.wallet\
window-state.json
exodus.conf.json
\Exodus\
Exodus
\Electrum-LTC\wallets\
ElectrumLTC
\Electrum\wallets\
Electrum
\Ethereum\
Ethereum"
keystore
Plugins
Wallets
(PID) Process(5880) BOkUTx0iwlgh3MRNoF7OvgaQ.exe
C2 (2)https://t.me/twowheelfun
https://steamcommunity.com/profiles/76561199563297648
Strings (531)kernel32.dll
GetUserNameA
advapi32.dll
GetComputerNameA
LocalAlloc
lstrcmpiW
VirtualFree
VirtualAlloc
VirtualAllocExNuma
GetCurrentProcess
ExitProcess
GetSystemTime
Sleep
GetProcAddress
lstrcatA
LoadLibraryA
JohnDoe
HAL9TH
Ledger Live
\Raven\
Raven Core
\Dogecoin\
Dogecoin
*wallet*.dat
wallet.dat
\Bitcoin\
Bitcoin Core Old
\Bitcoin\wallets\
Bitcoin Core
.finger-print.fp
simple-storage.json
Binance Desktop
loginusers.vdf
libraryfolders.vdf
DialogConfigOverlay*.vdf
DialogConfig.vdf
config.vdf
ssfn*
SteamPath
Software\Valve\Steam
C:\\\Windows\
C:\\Windows\
C:\Windows\
*%DRIVE_REMOVABLE%*
*%DRIVE_FIXED%*
*%RECENT%*
%DRIVE_REMOVABLE%
%DRIVE_FIXED%
%RECENT%
%PROGRAMFILES_86%
%PROGRAMFILES%
%DOCUMENTS%
%DESKTOP%
%USERPROFILE%
%LOCALAPPDATA%
%APPDATA%
\information.txt
[Software]
[Processes]
VideoCard:
RAM:
CPU Count:
Processor:
[Hardware]
TimeZone:
Local Time:
Keyboard Languages:
Display Language:
Display Resolution:
User Name:
Computer Name:
Windows:
Work Dir: In memory
Path:
HWID:
GUID:
MachineID:
Date:
Version:
sqlite3.dll
RoninWalletEdge
kjmoohlgokccodicjjfebfomlbljgfhk
IndexedDB
Sync Extension Settings
Local Extension Settings
UseMasterPassword
Security
Password
UserName
PortNumber
HostName
Soft: WinSCP
\Soft\Authy Desktop\
\Authy Desktop\Local Storage\leveldb\
\Soft\Authy Desktop Old\
\Authy Desktop\Local Storage\
*.localstorage
places.sqlite
formhistory.sqlite
cookies.sqlite
History
SELECT fieldname, value FROM moz_formhistory
SELECT url FROM moz_places
SELECT host, isHttpOnly, path, isSecure, expiry, name, value FROM moz_cookies
Network
Password:
Login:
Host:
Soft:
"os_crypt":{"encrypted_key":"
\passwords.txt
\Soft\Telegram\
F8806DD0C461824F*
A92DAA6EA6F891F2*
A7FDF864FBC10B77*
D877F783D5D3EF8C*
key_datas
\Telegram Desktop\
Thunderbird
\Thunderbird\Profiles\
Brave
\BraveSoftware\Brave-Browser\User Data\
CryptoTab Browser
\CryptoTab Browser\User Data\
\Opera GX Stable\
\Opera Stable\
\Opera Software\
sqlite3_column_blob
sqlite3_column_bytes
sqlite3_close
sqlite3_finalize
sqlite3_column_text
sqlite3_step
sqlite3_prepare_v2
sqlite3_open
GdipFree
GdipDisposeImage
GdipSaveImageToStream
GdiplusShutdown
GdiplusStartup
GdipCreateBitmapFromHBITMAP
GdipGetImageEncoders
GdipGetImageEncodersSize
SymMatchString
PathFindFileNameA
StrStrA
StrCmpCW
StrCmpCA
PathMatchSpecA
PathMatchSpecW
SHGetFolderPathA
SHFileOperationA
ShellExecuteExA
CloseWindow
GetWindowDC
GetWindowRect
GetHGlobalFromStream
CreateStreamOnHGlobal
CoInitialize
InternetCrackUrlA
AccessCheck
MapGenericMask
DuplicateToken
OpenProcessToken
GetFileSecurityA
RegEnumValueA
CryptBinaryToStringA
gdiplus.dll
dbghelp.dll
shlwapi.dll
shell32.dll
GetVolumeInformationA
GetWindowsDirectoryA
Process32Next
Process32First
CreateToolhelp32Snapshot
CreateEventA
OpenEventA
GetTickCount
SetEnvironmentVariableA
GetEnvironmentVariableA
GetFileInformationByHandle
CreateFileMappingA
FileTimeToSystemTime
UnmapViewOfFile
MapViewOfFile
LocalFileTimeToFileTime
GetFileAttributesA
WriteFile
SetFileTime
GetLocalTime
SystemTimeToFileTime
HeapFree
SetFilePointer
GetCurrentDirectoryA
DeleteFileA
CopyFileA
TzSpecificLocalTimeToSystemTime
GetTimeZoneInformation
GetFileSizeEx
OpenProcess
GetCurrentProcessId
GetLocaleInfoA
FreeLibrary
GlobalSize
GlobalLock
lstrcpynA
GetLastError
FindClose
FindNextFileA
FindFirstFileA
MultiByteToWideChar
lstrcpyA
GetDriveTypeA
lstrlenA
GetLogicalDriveStringsA
CloseHandle
ReadFile
GetFileSize
CreateFileA
GetProcessHeap
HeapAlloc
LocalFree
WideCharToMultiByte
GetSystemInfo
GetUserDefaultLocaleName
IsWow64Process
GlobalMemoryStatusEx
CreateThread
Discord Token:
dQw4w9WgXcQ:
\Soft\Discord\discord_tokens.txt
Session Storage
leveldb
Local Storage
Discord
\discord\
Wasabi Wallet
\WalletWasabi\Client\Wallets\
Blockstream Green
\Blockstream\Green\wallets\
she*.sqlite
Daedalus Mainnet
\Daedalus Mainnet\wallets\
Jaxx_Desktop
\com.liberty.jaxx\IndexedDB\file__0.indexeddb.leveldb\
GAuth Authenticator
ilgcnhelpchnceeipipijaljkblbcobl
EOS Authenticator
oeljdldpnmdbchonielidgobddffflal
Authy
gaedmjdfmmahhbjefcbgaolhhanlaolb
Authenticator
bhghoamapcdpbohphigoooaddinpkbai
jnkelfanjkeadonecabehalmbgpfodjm
Temple
ookjlbkiijinhpmnjffcofjonbfbgaoc
TezBox
mnfifefkajgofkcjkemidiaecocnkjeh
hcflpincpppdclinealmandijcmnkbgn
CyanoWallet
dkdedlpgdmmkkfjabffeganieamfklkm
Solflare
bhhhlbepdkbapadjdnnojkbgioiodbic
WavesKeeper
lpilbniiabackdjcionkobglmddfbcjo
MaiarDeFiWallet
dngmlblcodfobpdpecaadgfbcggfjfnm
NamiWallet
lpfcbjknijpeeillifnkikgncikgfhdo
XdefiWallet
hmeobnfnfcmdkdcmlblgagmfpfboieaf
BoltX
aodkkagnadcbobfpggfnjeongemjbjca
PaliWallet
mgffkfbidihjpoaomajlbgchddlicgpn
Oxygen (Atomic)
fhilaheimglignddkjgofkcbgekhenbh
BraveWallet
odbfpeeihdkbihmopkbjmoonfanlbfcl
ejbalbakoplchlghecdalmeeeajnimhm
Phantom
bfnaelmomeimhlpmgjnjophhpkkoljpa
Rabby
acmacodkjbdgmoleebolmdjonilkdbch
Trezor Password Manager
imloifkgjagghnncjkhggdhalmcnfklk
KardiaChain
pdadjkfkgcafgbceimcpbkalnfnepbnk
EVER Wallet
cgeeodpfagjceefieflmdfphplkenlfk
Coin98
aeachknmefphepccionboohckonoeemg
Harmony
fnnegphlobjdpkhecapkijjdkgcjhkib
ICONex
flpiciilemghbmfalicajoolhkkenfel
PolymeshWallet
jojhfeoedkpkglbfimdfabpdfjaoolaf
AuroWallet
cnmamaachppnkjgnildpdmkaakejnhae
Sollet
fhmfendgdocmcbmfikdcogofphimnkno
Keplr
dmkamcknogkgcdfhhbddcghachkejeap
Terra_Station
aiifbnbfobpmeekipheeijimdpnlpgpp
LiqualityWallet
kpfopkelmapcoipemfendmdcghnegimn
CloverWallet
nhnkbkgjikgcigadomkphalanndcapjk
NeoLine
cphhlgmgameodnhkjdmkpanlelnlohao
RoninWallet
fnjhmkhhmkbjkkabndcnnogagogbneec
GuildWallet
nanjmdknhkinifnkgdcggcfnhdaammmj
MewCx
nlbmnnijcnlegkjjpcfjclmcfggfefdm
Wombat
amkmjjmmflddogmhpjloimipbofnfjih
iWallet
kncchdigobghenbbaddojjnnaogfppfj
BitAppWallet
fihkakfobkmkjojpchpfgcmhfjnmnfpi
JaxxLiberty
cjelfplplebdjjenllpjcblmjkfcffne
EQUALWallet
blnieiiffboillknjnepogjhkgnoapac
Guarda
hpglfhgfnhbgpjdenjgmdgoeiappafln
Coinbase
hnfanknocfeofbddgcijnmhnfnkdnaad
MathWallet
afbcbjpbpfadlkmhmclhkeeodmamcflc
NiftyWallet
jbdaocneiiinmjbjlgalhcelgbejmnid
Yoroi
ffnbelfdoeiohenkjibnmadjiehjhajb
BinanceChainWallet
fhbohimaelbohpjbbldcngcnapndodjp
MetaMask
nkbihfbeogaeaoehlefnkodbefgpgknn
TronLink
ibnejdfjmmkpcnlpebklmnkoeoihofec
EnumProcessModules
GetModuleBaseNameA
GetModuleFileNameExA
GetSystemMetrics
EnumDisplayDevicesA
wsprintfA
GetDC
CharToOemA
GetKeyboardLayoutList
ReleaseDC
GetDesktopWindow
CoUninitialize
CoCreateInstance
CreateCompatibleDC
GetDeviceCaps
CreateDCA
DeleteObject
BitBlt
SelectObject
CreateCompatibleBitmap
DeleteUrlCacheEntry
InternetSetOptionA
InternetOpenUrlA
InternetSetFilePointer
HttpQueryInfoA
HttpAddRequestHeadersA
InternetOpenA
InternetConnectA
HttpOpenRequestA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
wininet.dll
RegGetValueA
RegGetValueW
RegOpenKeyExW
RegCloseKey
RegQueryValueExA
RegOpenKeyExA
PK11SDR_Decrypt
PK11_Authenticate
PK11_FreeSlot
PK11_GetInternalKeySlot
NSS_Shutdown
NSS_Init
C:\ProgramData\nss3.dll
CryptStringToBinaryA
CryptUnprotectData
CRYPT32.DLL
BCryptDecrypt
BCryptGenerateSymmetricKey
BCryptSetProperty
BCryptOpenAlgorithmProvider
BCryptDestroyKey
BCryptCloseAlgorithmProvider
BCRYPT.DLL
psapi.dll
user32.dll
ole32.dll
gdi32.dll
FALSE
Cookies
Local State
\Opera Software\Opera GX Stable\
OperaGX
\Opera Software\Opera Stable\
Opera
\Tencent\QQBrowser\User Data\
QQBrowser
\360Browser\Browser\User Data\
360 Browser
\Microsoft\Edge\User Data\
Microsoft Edge
\7Star\7Star\User Data\
7Star
\brave\
Brave_Old
\Chedot\User Data\
Chedot Browser
\TorBro\Profile\
TorBro Browser
\CentBrowser\User Data\
Cent Browser
\CocCoc\Browser\User Data\
CocCoc
\Vivaldi\User Data\
Vivaldi
\Epic Privacy Browser\User Data\
Epic Privacy Browser
\Comodo\Dragon\User Data\
Comodo Dragon
\Torch\User Data\
Torch
\Amigo\User Data\
Amigo
\Chromium\User Data\
Chromium
\Google\Chrome\User Data\
Google Chrome
\Moonchild Productions\Pale Moon\Profiles\
Pale Moon
\Mozilla\Firefox\Profiles\
Mozilla Firefox
Soft: FileZilla
<Pass encoding="base64">
<User>
<Port>
<Host>
\AppData\Roaming\FileZilla\recentservers.xml
SELECT HOST_KEY, is_httponly, path, is_secure, (expires_utc/1000000)-11644480800, name, encrypted_value from cookies
SELECT url FROM urls
SELECT target_path, tab_url from downloads
SELECT name_on_card, expiration_month, expiration_year, card_number_encrypted FROM credit_cards
SELECT name, value FROM autofill
SELECT origin_url, username_value, password_value FROM logins
encryptedPassword
encryptedUsername
usernameField
formSubmitURL
logins.json
Web Data
Cookies
Login Data
netfulfilled
mnpayments
mncache
governance
banlist
mempool
peers
fee_estimates
Local\Microsoft
Roaming\WinRAR
Local\NuGet
Local\Packages
MicrosoftEdge\Cookies
Recycle.Bin
Local\Temp
Recovery
msdownld.tmp
System Volume Information
Config.Msi
RECYCLE.BIN
C:\ProgramData\
\Monero\
SOFTWARE\monero-project\monero-core
wallet_path
*.config
*.wallet
\Coinomi\Coinomi\wallets\
Coinomi
app-store.json
\Binance\
Binance
0000*
MANIFEST-000001
CURRENT
*.log
\atomic\Local Storage\leveldb\
Atomic
file__0.localstorage
\jaxx\Local Storage\
Jaxx_Desktop_Old
multidoge.wallet
\MultiDoge\
MultiDoge
default_wallet
\ElectronCash\wallets\
ElectronCash
info.seco
seed.seco
passphrase.json
\Exodus\exodus.wallet\
window-state.json
exodus.conf.json
\Exodus\
Exodus
\Electrum-LTC\wallets\
ElectrumLTC
\Electrum\wallets\
Electrum
\Ethereum\
Ethereum"
keystore
Plugins
Wallets
Total processes
630
Monitored processes
559
Malicious processes
174
Suspicious processes
42
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 416 | cmd /C REG ADD "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Paths" /f /v "C:\Windows\Temp\wUBDPVxDQVpvNZiy" /t REG_DWORD /d 0 /reg:64 | C:\Windows\SysWOW64\cmd.exe | — | xqRPslL.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 448 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 460 | "C:\Users\admin\Pictures\dDqTuH6URaVCl9h3HLE1hiNu.exe" | C:\Users\admin\Pictures\dDqTuH6URaVCl9h3HLE1hiNu.exe | InstallUtil.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 484 | C:\Windows\system32\services.exe | C:\Windows\System32\services.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Services and Controller app Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 500 | C:\Windows\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Exit code: 0 Version: 6.1.7601.23915 (win7sp1_ldr.170913-0600) Modules
| |||||||||||||||
| 508 | C:\Windows\system32\lsm.exe | C:\Windows\System32\lsm.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Session Manager Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 572 | sc stop dosvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 608 | C:\Windows\system32\svchost.exe -k DcomLaunch | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 684 | C:\Users\admin\AppData\Local\Temp\IXP003.TMP\rg1qP67.exe | C:\Users\admin\AppData\Local\Temp\IXP003.TMP\rg1qP67.exe | — | nb5XL55.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.17763.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
365 699
Read events
299 411
Write events
3 642
Delete events
62 646
Modification events
| (PID) Process: | (1944) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000088AF72B0747534094337F63DE35C94A000000000200000000001066000000010000200000003A7AE26404D75DF41C31FF40C5EA8CE90BAF74FA9E9BD7A9ACA34C7048350C1E000000000E8000000002000020000000BD2D56D46506C12C41A6A70B10E79EE53CB79EF36FD2BA8CDD2460CB8F4BE86A300000009B5D1418CBF2EB49F3C4BD4C21D58CA55B82FA3D3ED08AF0EF59D6C7ECAFC1055FA323A80FF7C154B1C9B60253392B6640000000DED9FDCC168073324C3013F1BB125E066EB1A2F09FD2C8E7CC7A793AA992E21EF1C942BF7294D04E036428704009B863B1CB981B97312E2530E3E816780CF7C9 | |||
| (PID) Process: | (2612) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 0000000000000000 | |||
| (PID) Process: | (1944) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | 308046O0NS4N39PO |
Value: 000000000D000000150000005F450200000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF800D10ACA1C5D90100000000 | |||
| (PID) Process: | (1944) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000C9000000000100006F706A0015000000070000002A2306007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C0063006D0064002E006500780065000000100300000000B06FD703000000005F4C6D09000000000A000080000000004DBC20FEFE070000000000000000000080DF100300000000D8ED10030000000001000000000000000A0000800000000004FE20FEFE0700000000000000000000D8ED100300000000D8ED10030000000002000000000000007600D4007124807030C22D000000000001100211970250005F4C6D090000000000D3A70200000000B06FD70300000000C0A32B0000000000880000000000000040B35CFEFE0700000000000000000000000000000000000000002B0000000000C803CE77000000000000000000000000D00300000000000000002B0000000000E04AC40300000000280CBF770000000048062B000000000048DDC177000000000000000000000000C103000000000000070095032308000010812B00000000009088DB03000000000000000000000000D0ED10030000000008000000000000004006790900000000207D2B0000000000C8225DFEFE0700001C7F2B0000000000B0E32B00000000005B590EFFFE070000020000000000000028B68707000000004006790900000000A54208FFFE070000C803CE7707000000250000004B7A0B004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000075006C0074000000000000000000010000000000000088E2EA0200000000000000000000000030E0EA020000000028E0EA020000000020E0EA0200000000586705FCFE070000000000000000000040E0EA0200000000000000000000000000000000000000003E00400000000000B0E8EA02000000003053A203000000000000000000000000000000000000000022BBD2FF0000000000003D4A62B00000E000070000000000A210000000000000E0F1EA02000000000000000000000000300B8B0200000000A4768F0200000000D4AF17FEFE070000B0E3EA0200000000200C9C0A000000000100000000000000D46905FCFE0700001500000007000000790E06007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C0063006D0064002E006500780065000000EA02000000000540008000000000542D8CFFFE070000000000000000000068006C02000000005C0001000000000000000000000000000000280000000000EB1A6E770000000068006C020000000000000000FE070000282595FFFE070000A00D33000000000018006C02000000001B000000E8261C007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C007400610073006B006D00670072002E006500780065000000008000000000542DC9FDFE070000000000000000000068009902000000005800010000000000000000000000000000002B0000000000EB1AC07700000000680099020000000000000000FE0700002825D2FDFE070000F099A90200000000180099020000000000000000000000000100000000000000BF1DC9FDFE07000030E010030000000010D1AB020000000000000000000000003B94B8FDFE070000B04EAB020000000008009902000000005800010000000000869AAE7700000000C7F7CF529EC5000082020000000000000000000000000000580001000000000000000000000000008202000000000000020000000000000058000100000000000000000000000000820200000000000080A630FF00000000C81222FF00000000B04EAB020000000001000000000000000F0000C00000000090DFDD0300000000820200000000000001000000000000008202000000000000DB9BAE77000000005800010000000000000000000000000000000000000000000100000000000000000000000000000081020000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2612) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 1 | |||
| (PID) Process: | (2612) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (2612) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (2612) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (2612) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 0 | |||
| (PID) Process: | (2612) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
Executable files
304
Suspicious files
903
Text files
1 752
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\prefs-1.js | text | |
MD5:F42921723A3596D2FA57BE1279C18862 | SHA256:5D6A78D6523693521C6D337C72269B0320B0C5A82D699D74FF2490813574C652 | |||
| 2612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\prefs.js | text | |
MD5:F42921723A3596D2FA57BE1279C18862 | SHA256:5D6A78D6523693521C6D337C72269B0320B0C5A82D699D74FF2490813574C652 | |||
| 2612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\datareporting\glean\db\data.safe.tmp | binary | |
MD5:116BE238A83EF761F2A88C54D53AD0CA | SHA256:27A64E23F02EC9E4CC24E38A32CB10C83DDCAE3A63ACEC05ABAC51DC143CCD5B | |||
| 2612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\datareporting\glean\tmp\e20a7b01-c5b4-4579-a614-e0f3a19ef9fd | text | |
MD5:4B22F96F216F08917362B5D14DD13251 | SHA256:1FDD28854DB987689C55789670B51452CBBC499E79BACEAE8D7D965B34CC9765 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
262
TCP/UDP connections
786
DNS requests
355
Threats
666
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2612 | firefox.exe | GET | 304 | 2.18.121.73:80 | http://ciscobinary.openh264.org/openh264-win64-31c4d2e4a037526fd30d4e5c39f60885986cf865.zip | unknown | — | — | unknown |
2612 | firefox.exe | GET | — | 171.22.28.221:80 | http://171.22.28.221/icons/blank.gif | unknown | — | — | unknown |
2612 | firefox.exe | GET | 200 | 171.22.28.221:80 | http://171.22.28.221/icons/binary.gif | unknown | image | 246 b | unknown |
2612 | firefox.exe | POST | — | 13.32.117.210:80 | http://ocsp.r2m02.amazontrust.com/ | unknown | — | — | unknown |
2612 | firefox.exe | GET | 200 | 171.22.28.221:80 | http://171.22.28.221/favicon.ico | unknown | html | 1.37 Kb | unknown |
2612 | firefox.exe | POST | — | 184.24.77.56:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
2612 | firefox.exe | POST | — | 184.24.77.56:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
2612 | firefox.exe | POST | — | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3 | unknown | — | — | unknown |
2612 | firefox.exe | POST | 200 | 184.24.77.56:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
2612 | firefox.exe | POST | 200 | 184.24.77.56:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2612 | firefox.exe | 171.22.28.221:80 | — | ASN-QUADRANET-GLOBAL | US | unknown |
2612 | firefox.exe | 142.250.184.202:443 | safebrowsing.googleapis.com | — | — | whitelisted |
2612 | firefox.exe | 142.250.181.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2612 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
2612 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
2612 | firefox.exe | 13.32.117.210:80 | ocsp.r2m02.amazontrust.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| shared |
proxyserverecs-1736642167.us-east-1.elb.amazonaws.com |
| shared |
r3.o.lencr.org |
| shared |
content-signature-2.cdn.mozilla.net |
| whitelisted |
a1887.dscq.akamai.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2612 | firefox.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2612 | firefox.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2612 | firefox.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
324 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
324 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2556 | InstallUtil.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2556 | InstallUtil.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2556 | InstallUtil.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2556 | InstallUtil.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2556 | InstallUtil.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
66 ETPRO signatures available at the full report
Process | Message |
|---|---|
arriveprospect.exe | [ERROR] The Roland SoundCanvas Sound Set is licensed under Microsoft's End User License Agreement
|
arriveprospect.exe | [ERROR] All other uses require a separate written license from Roland
|
svchost.exe | base\diagnosis\diagtrack\engine\heartbeat.cpp(199)\diagtrack.dll!000007FEFA51DA84: (caller: 000007FEFA51D257) ReturnHr[PreRelease](59) tid(534) 80070510 The requested file operation failed because the storage policy blocks that type of file. For more information, contact your system administrator.
|
svchost.exe | base\diagnosis\diagtrack\matchengine\asimovuploader.cpp(1592)\diagtrack.dll!000007FEFA54CC77: (caller: 000007FEFA51DA66) ReturnHr[PreRelease](58) tid(534) 80070510 The requested file operation failed because the storage policy blocks that type of file. For more information, contact your system administrator.
|