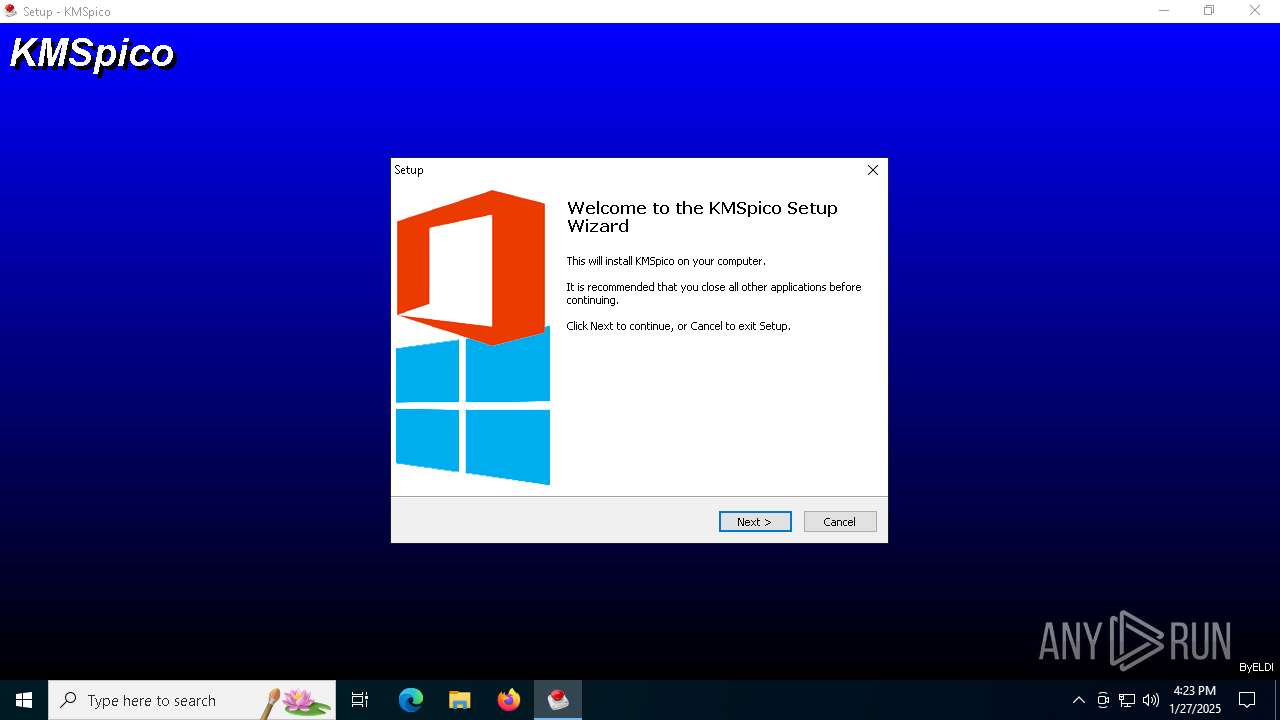
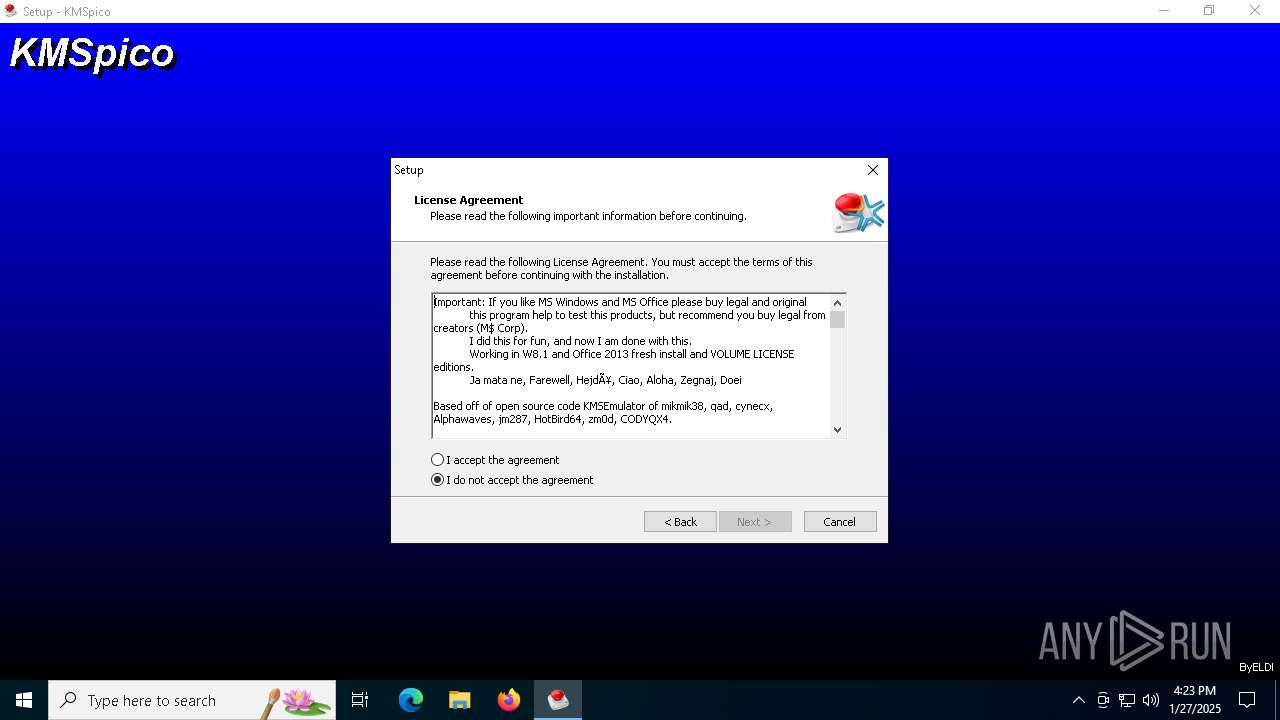
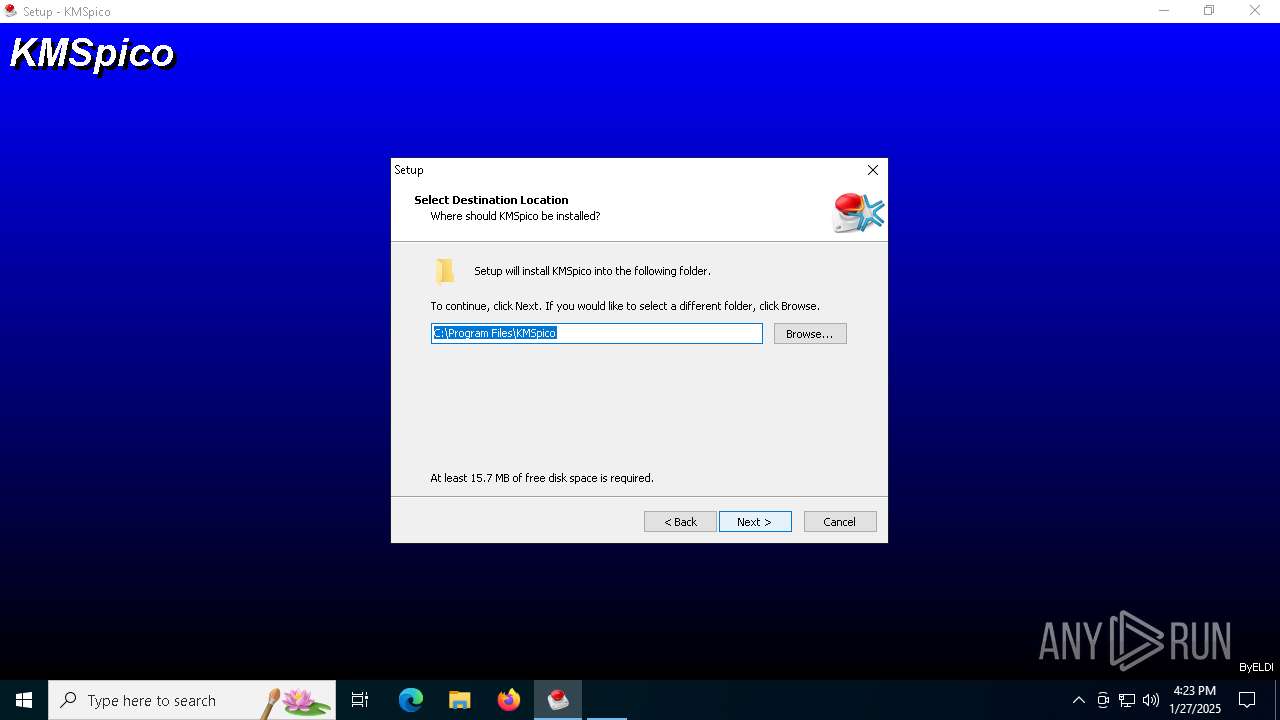
| File name: | KMSpico.exe |
| Full analysis: | https://app.any.run/tasks/76ae4974-69c3-41b9-9151-28f6376db2a5 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | January 27, 2025, 16:22:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | CA48226DF272A89B2D2622EB0EA90E2A |
| SHA1: | 55A245E4D74B6085FBB500474195E01BEA262F68 |
| SHA256: | DEB84EDB1B68CF868BEB0E84E40D06CC101EE1CDE8CA03E112F710DB6CA07BFE |
| SSDEEP: | 98304:H6GavilJmy6ZD/ejjm1+CBviv+0x+ctRYeJ84wr/AYrvy48MnYbY2bz0JqB6yrqA:dhWaE5sV0hFhqYH7q |
MALICIOUS
Executing a file with an untrusted certificate
- KMSpico.exe (PID: 5592)
- core.exe (PID: 4264)
- KMSELDI.exe (PID: 2612)
- AutoPico.exe (PID: 6560)
Actions looks like stealing of personal data
- core.exe (PID: 4264)
Steals credentials from Web Browsers
- core.exe (PID: 4264)
LUMMA mutex has been found
- core.exe (PID: 4264)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3172)
Changes image file execution options
- KMSELDI.exe (PID: 2612)
- AutoPico.exe (PID: 6560)
SUSPICIOUS
Executable content was dropped or overwritten
- KMSpico.exe (PID: 5432)
- KMSpico.tmp (PID: 4704)
- KMSpico.exe (PID: 5592)
- KMSpico.exe (PID: 5256)
- KMSpico.tmp (PID: 2436)
- KMSELDI.exe (PID: 2612)
Reads the Windows owner or organization settings
- KMSpico.tmp (PID: 4704)
- KMSpico.tmp (PID: 2436)
Reads security settings of Internet Explorer
- KMSpico.tmp (PID: 4704)
- KMSpico.tmp (PID: 836)
Process drops legitimate windows executable
- KMSpico.tmp (PID: 2436)
Searches for installed software
- core.exe (PID: 4264)
Modifies the phishing filter of IE
- KMSpico.tmp (PID: 2436)
Starts SC.EXE for service management
- cmd.exe (PID: 2996)
Executing commands from ".cmd" file
- KMSpico.tmp (PID: 2436)
Starts CMD.EXE for commands execution
- KMSpico.tmp (PID: 2436)
Creates a new Windows service
- sc.exe (PID: 5916)
INFO
Checks supported languages
- KMSpico.exe (PID: 5432)
- KMSpico.tmp (PID: 4704)
- KMSpico.exe (PID: 5592)
- KMSpico.tmp (PID: 836)
- KMSpico.exe (PID: 5256)
- KMSpico.tmp (PID: 2436)
- core.exe (PID: 4264)
- UninsHs.exe (PID: 5316)
- KMSELDI.exe (PID: 2612)
- SECOH-QAD.exe (PID: 6840)
- AutoPico.exe (PID: 6560)
Creates files or folders in the user directory
- KMSpico.tmp (PID: 4704)
Create files in a temporary directory
- KMSpico.tmp (PID: 4704)
- KMSpico.exe (PID: 5432)
- KMSpico.exe (PID: 5592)
- KMSpico.exe (PID: 5256)
- KMSpico.tmp (PID: 2436)
- core.exe (PID: 4264)
Compiled with Borland Delphi (YARA)
- KMSpico.exe (PID: 5432)
- KMSpico.tmp (PID: 4704)
- KMSpico.tmp (PID: 2436)
- KMSpico.tmp (PID: 836)
Reads the computer name
- KMSpico.tmp (PID: 4704)
- KMSpico.tmp (PID: 2436)
- KMSpico.tmp (PID: 836)
- core.exe (PID: 4264)
- KMSELDI.exe (PID: 2612)
- AutoPico.exe (PID: 6560)
Detects InnoSetup installer (YARA)
- KMSpico.exe (PID: 5432)
- KMSpico.tmp (PID: 4704)
- KMSpico.exe (PID: 5592)
- KMSpico.tmp (PID: 836)
- KMSpico.exe (PID: 5256)
- KMSpico.tmp (PID: 2436)
Creates a software uninstall entry
- KMSpico.tmp (PID: 4704)
- KMSpico.tmp (PID: 2436)
Process checks computer location settings
- KMSpico.tmp (PID: 4704)
- KMSpico.tmp (PID: 836)
The sample compiled with english language support
- KMSpico.tmp (PID: 2436)
Creates files in the program directory
- KMSpico.tmp (PID: 2436)
- KMSELDI.exe (PID: 2612)
- AutoPico.exe (PID: 6560)
Reads the machine GUID from the registry
- core.exe (PID: 4264)
- KMSELDI.exe (PID: 2612)
- AutoPico.exe (PID: 6560)
Reads the software policy settings
- core.exe (PID: 4264)
Reads product name
- KMSELDI.exe (PID: 2612)
- AutoPico.exe (PID: 6560)
Reads Environment values
- KMSELDI.exe (PID: 2612)
- AutoPico.exe (PID: 6560)
Reads Microsoft Office registry keys
- KMSELDI.exe (PID: 2612)
- AutoPico.exe (PID: 6560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:01:08 15:36:35+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 684032 |
| InitializedDataSize: | 159744 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa7f98 |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | MyApp Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | MyApp |
| ProductVersion: | 1.0 |
Total processes
150
Monitored processes
19
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 836 | "C:\Users\admin\AppData\Local\Temp\is-JPCRF.tmp\KMSpico.tmp" /SL5="$40308,2952592,69120,C:\Users\admin\AppData\Roaming\MyApp\data\KMSpico.exe" | C:\Users\admin\AppData\Local\Temp\is-JPCRF.tmp\KMSpico.tmp | — | KMSpico.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2436 | "C:\Users\admin\AppData\Local\Temp\is-HK2J3.tmp\KMSpico.tmp" /SL5="$602AA,2952592,69120,C:\Users\admin\AppData\Roaming\MyApp\data\KMSpico.exe" /SPAWNWND=$402DE /NOTIFYWND=$40308 | C:\Users\admin\AppData\Local\Temp\is-HK2J3.tmp\KMSpico.tmp | KMSpico.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2612 | "C:\Program Files\KMSpico\KMSELDI.exe" /silent /backup | C:\Program Files\KMSpico\KMSELDI.exe | KMSpico.tmp | ||||||||||||
User: admin Company: @ByELDI Integrity Level: HIGH Description: KMS GUI ELDI Exit code: 4294967295 Version: 37.1.0.0 Modules
| |||||||||||||||
| 2996 | "C:\WINDOWS\system32\cmd.exe" /C ""C:\Program Files\KMSpico\scripts\Install_Service.cmd"" | C:\Windows\System32\cmd.exe | — | KMSpico.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3172 | "C:\WINDOWS\system32\cmd.exe" /C ""C:\Program Files\KMSpico\scripts\Install_Task.cmd"" | C:\Windows\System32\cmd.exe | — | KMSpico.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3532 | SCHTASKS /Create /TN "AutoPico Daily Restart" /TR "'C:\Program Files\KMSpico\AutoPico.exe' /silent" /SC DAILY /ST 23:59:59 /RU "NT AUTHORITY\SYSTEM" /RL Highest /F | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3560 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4264 | "C:\Users\admin\AppData\Roaming\MyApp\core.exe" | C:\Users\admin\AppData\Roaming\MyApp\core.exe | KMSpico.tmp | ||||||||||||
User: admin Company: Raccoonworks - Alan Fletcher Integrity Level: MEDIUM Description: SpeedTest Client Exit code: 0 Version: 2.0.0.69 Modules
| |||||||||||||||
Total events
9 297
Read events
9 214
Write events
72
Delete events
11
Modification events
| (PID) Process: | (4704) KMSpico.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.4.0 | |||
| (PID) Process: | (4704) KMSpico.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Users\admin\AppData\Roaming\MyApp | |||
| (PID) Process: | (4704) KMSpico.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Roaming\MyApp\ | |||
| (PID) Process: | (4704) KMSpico.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: MyApp | |||
| (PID) Process: | (4704) KMSpico.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (4704) KMSpico.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: default | |||
| (PID) Process: | (4704) KMSpico.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | DisplayName |
Value: MyApp version 1.0 | |||
| (PID) Process: | (4704) KMSpico.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Users\admin\AppData\Roaming\MyApp\unins000.exe | |||
| (PID) Process: | (4704) KMSpico.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Users\admin\AppData\Roaming\MyApp\unins000.exe" | |||
| (PID) Process: | (4704) KMSpico.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Users\admin\AppData\Roaming\MyApp\unins000.exe" /SILENT | |||
Executable files
32
Suspicious files
36
Text files
716
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4704 | KMSpico.tmp | C:\Users\admin\AppData\Roaming\MyApp\is-1VGAV.tmp | — | |
MD5:— | SHA256:— | |||
| 4704 | KMSpico.tmp | C:\Users\admin\AppData\Roaming\MyApp\core.exe | — | |
MD5:— | SHA256:— | |||
| 4704 | KMSpico.tmp | C:\Users\admin\AppData\Roaming\MyApp\is-T7NGJ.tmp | executable | |
MD5:4134EC81A9D645602B1FA265F98FBF35 | SHA256:69966257CE41717F2121EA1F03F8BFA1486423ACECFCC977DD9F1E157C911AD4 | |||
| 4704 | KMSpico.tmp | C:\Users\admin\AppData\Local\Temp\is-D1FHV.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 2436 | KMSpico.tmp | C:\Users\admin\AppData\Local\Temp\is-F8V2H.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 5592 | KMSpico.exe | C:\Users\admin\AppData\Local\Temp\is-JPCRF.tmp\KMSpico.tmp | executable | |
MD5:1778C1F66FF205875A6435A33229AB3C | SHA256:95C06ACAC4FE4598840E5556F9613D43AA1039C52DAC64536F59E45A70F79DA6 | |||
| 5256 | KMSpico.exe | C:\Users\admin\AppData\Local\Temp\is-HK2J3.tmp\KMSpico.tmp | executable | |
MD5:1778C1F66FF205875A6435A33229AB3C | SHA256:95C06ACAC4FE4598840E5556F9613D43AA1039C52DAC64536F59E45A70F79DA6 | |||
| 4704 | KMSpico.tmp | C:\Users\admin\AppData\Roaming\MyApp\unins000.dat | binary | |
MD5:6BB968E8217C0267E2F240462E16FFAA | SHA256:5196D926628E813EAB669857FD7E057D9E8DE6F5D87D0DBA5DBDE6793B95AB27 | |||
| 2436 | KMSpico.tmp | C:\Program Files\KMSpico\AutoPico.exe | executable | |
MD5:CFE1C391464C446099A5EB33276F6D57 | SHA256:4A714D98CE40F5F3577C306A66CB4A6B1FF3FD01047C7F4581F8558F0BCDF5FA | |||
| 4704 | KMSpico.tmp | C:\Users\admin\AppData\Roaming\MyApp\unins000.exe | executable | |
MD5:4134EC81A9D645602B1FA265F98FBF35 | SHA256:69966257CE41717F2121EA1F03F8BFA1486423ACECFCC977DD9F1E157C911AD4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
56
TCP/UDP connections
64
DNS requests
18
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 172.67.188.147:443 | https://uniquetopstop.top/api | unknown | text | 2 b | unknown |
— | — | POST | 200 | 104.21.19.193:443 | https://uniquetopstop.top/api | unknown | text | 18.3 Kb | unknown |
— | — | POST | 200 | 172.67.188.147:443 | https://uniquetopstop.top/api | unknown | text | 16 b | unknown |
— | — | POST | 200 | 172.67.188.147:443 | https://uniquetopstop.top/api | unknown | text | 16 b | unknown |
— | — | POST | 200 | 172.67.188.147:443 | https://uniquetopstop.top/api | unknown | text | 16 b | unknown |
— | — | POST | 200 | 172.67.188.147:443 | https://uniquetopstop.top/api | unknown | text | 16 b | unknown |
— | — | POST | 200 | 172.67.188.147:443 | https://uniquetopstop.top/api | unknown | text | 16 b | unknown |
— | — | POST | 204 | 104.126.37.163:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
— | — | POST | 200 | 172.67.188.147:443 | https://uniquetopstop.top/api | unknown | text | 48 b | unknown |
— | — | POST | 400 | 20.190.160.20:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4536 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.19.96.51:443 | — | Akamai International B.V. | DE | unknown |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5780 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5780 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 13.71.55.58:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IN | whitelisted |
3976 | svchost.exe | 13.71.55.58:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IN | whitelisted |
4264 | core.exe | 172.67.188.147:443 | uniquetopstop.top | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
uniquetopstop.top |
| unknown |
2.pool.ntp.org |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |