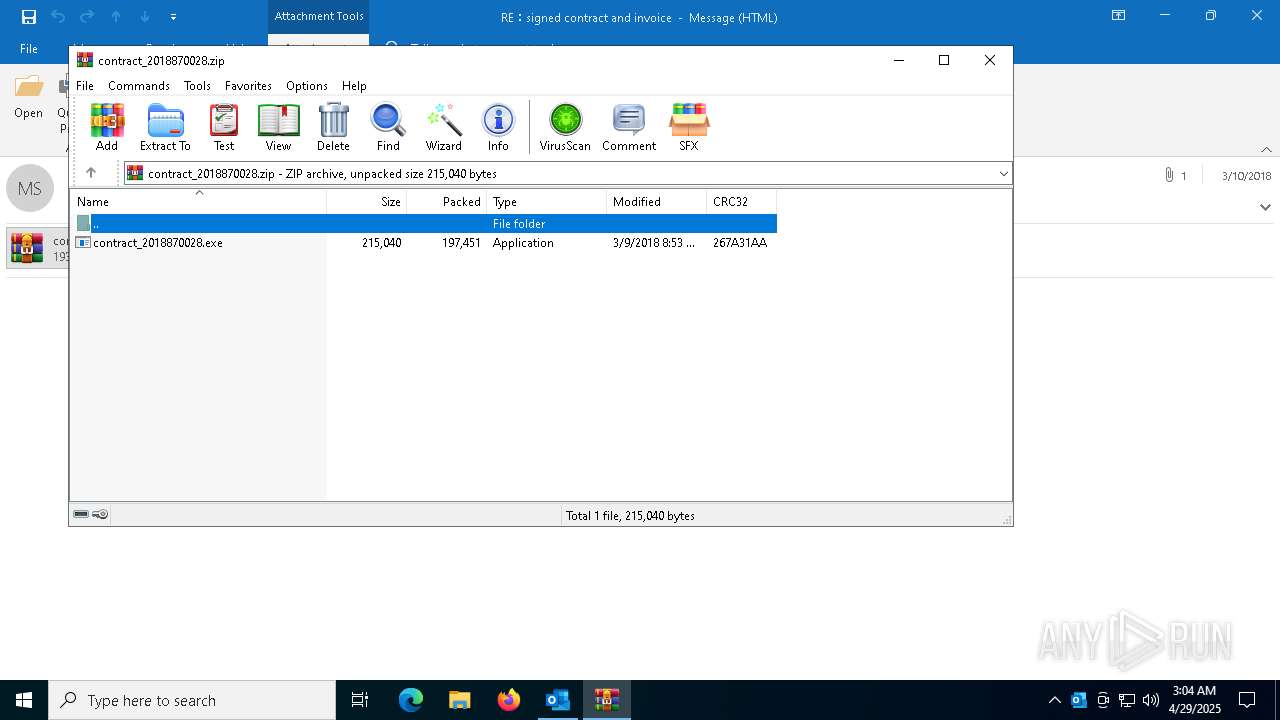
| File name: | 2018-03-09-Lokibot-malspam-1315-UTC.eml |
| Full analysis: | https://app.any.run/tasks/75a4d4c9-3e7d-4b67-afef-f67e0e6f7635 |
| Verdict: | Malicious activity |
| Threats: | LokiBot was developed in 2015 to steal information from a variety of applications. Despite the age, this malware is still rather popular among cybercriminals. |
| Analysis date: | April 29, 2025, 03:04:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF, LF line terminators |
| MD5: | F3AD0F1539D66A23794A97A5C865FEDF |
| SHA1: | A4C80A139EAF112ED4905E2EE0B7AB3A3CA1DC99 |
| SHA256: | DE95CB725A79C22EE33C2BC45958F8FF12E745189CA332F3ACBAA9507CD6D2AD |
| SSDEEP: | 6144:AlHTJoDDcdixuAOO1cJP8evJctBai/WxJjZG:oH1oDDcdibcJUevJ8ai/4pZG |
MALICIOUS
Generic archive extractor
- OUTLOOK.EXE (PID: 896)
Changes the autorun value in the registry
- explorer.exe (PID: 7808)
XORed URL has been found (YARA)
- explorer.exe (PID: 7808)
- explorer.exe (PID: 7852)
LOKIBOT has been detected (YARA)
- explorer.exe (PID: 7808)
- explorer.exe (PID: 7852)
Actions looks like stealing of personal data
- explorer.exe (PID: 7852)
Lokibot is detected
- explorer.exe (PID: 7852)
LOKIBOT mutex has been found
- explorer.exe (PID: 7852)
Scans artifacts that could help determine the target
- explorer.exe (PID: 7852)
LOKIBOT has been detected (SURICATA)
- explorer.exe (PID: 7852)
Connects to the CnC server
- explorer.exe (PID: 7852)
SUSPICIOUS
Executable content was dropped or overwritten
- contract_2018870028.exe (PID: 7672)
- explorer.exe (PID: 7852)
The process creates files with name similar to system file names
- contract_2018870028.exe (PID: 7672)
Reads security settings of Internet Explorer
- contract_2018870028.exe (PID: 7672)
- explorer.exe (PID: 7852)
Application launched itself
- explorer.exe (PID: 7808)
Contacting a server suspected of hosting an CnC
- explorer.exe (PID: 7852)
INFO
Creates files or folders in the user directory
- contract_2018870028.exe (PID: 7672)
- explorer.exe (PID: 7852)
Manual execution by a user
- contract_2018870028.exe (PID: 7672)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7452)
Reads the computer name
- contract_2018870028.exe (PID: 7672)
- explorer.exe (PID: 7808)
- explorer.exe (PID: 7852)
Checks supported languages
- contract_2018870028.exe (PID: 7672)
- explorer.exe (PID: 7808)
- explorer.exe (PID: 7852)
Process checks computer location settings
- contract_2018870028.exe (PID: 7672)
Reads the machine GUID from the registry
- contract_2018870028.exe (PID: 7672)
- explorer.exe (PID: 7808)
- explorer.exe (PID: 7852)
Reads security settings of Internet Explorer
- explorer.exe (PID: 7768)
Reads Microsoft Office registry keys
- explorer.exe (PID: 7852)
Reads the software policy settings
- slui.exe (PID: 1056)
- slui.exe (PID: 7924)
Checks proxy server information
- slui.exe (PID: 7924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(7808) explorer.exe
Decrypted-URLs (1)http://sir-iyke.com/five/fre.php
(PID) Process(7852) explorer.exe
Decrypted-URLs (1)http://sir-iyke.com/five/fre.php
LokiBot
(PID) Process(7808) explorer.exe
C2http://sir-iyke.com/five/fre.php
Decoys (4)kbfvzoboss.bid/alien/fre.php
alphastand.trade/alien/fre.php
alphastand.win/alien/fre.php
alphastand.top/alien/fre.php
(PID) Process(7852) explorer.exe
C2http://sir-iyke.com/five/fre.php
Decoys (4)kbfvzoboss.bid/alien/fre.php
alphastand.trade/alien/fre.php
alphastand.win/alien/fre.php
alphastand.top/alien/fre.php
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
145
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 896 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml C:\Users\admin\AppData\Local\Temp\2018-03-09-Lokibot-malspam-1315-UTC.eml | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1056 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "709BE8D1-6524-438B-83FD-33EADFE182F2" "33FAF2C8-9DE9-4A9D-899E-B79F0F495D29" "896" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 5960 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
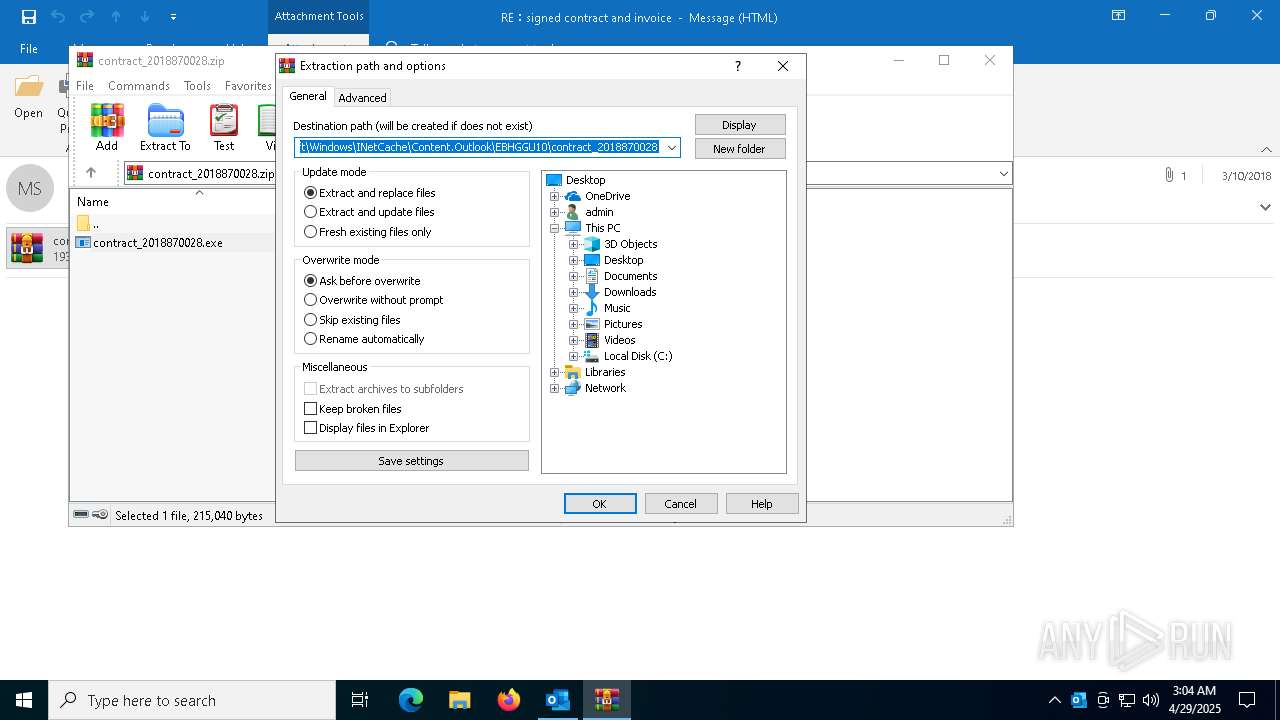
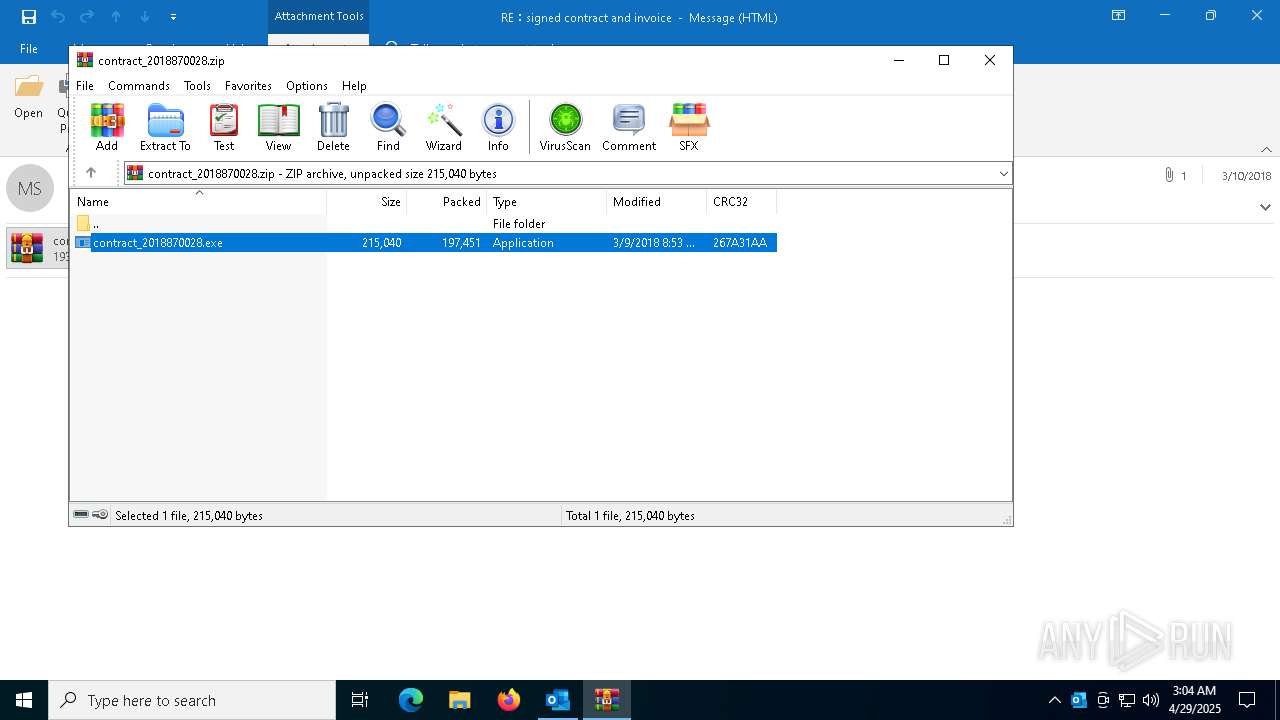
| 7452 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\EBHGGU10\contract_2018870028.zip" | C:\Program Files\WinRAR\WinRAR.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7672 | "C:\Users\admin\Desktop\contract_2018870028.exe" | C:\Users\admin\Desktop\contract_2018870028.exe | explorer.exe | ||||||||||||
User: admin Company: Weyerhauser Company Integrity Level: MEDIUM Description: Recovery Manager for Active Directory Forest Edition Exit code: 0 Version: 4.2.29.2 Modules
| |||||||||||||||
| 7728 | "C:\Windows\System32\explorer.exe" /c select, C:\Users\admin\AppData\Roaming\explorer.exe | C:\Windows\SysWOW64\explorer.exe | — | contract_2018870028.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7768 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7808 | "C:\Users\admin\AppData\Roaming\explorer.exe" | C:\Users\admin\AppData\Roaming\explorer.exe | explorer.exe | ||||||||||||
User: admin Company: Weyerhauser Company Integrity Level: MEDIUM Description: Recovery Manager for Active Directory Forest Edition Exit code: 4294967295 Version: 4.2.29.2 Modules
xor-url(PID) Process(7808) explorer.exe Decrypted-URLs (1)http://sir-iyke.com/five/fre.php LokiBot(PID) Process(7808) explorer.exe C2http://sir-iyke.com/five/fre.php Decoys (4)kbfvzoboss.bid/alien/fre.php alphastand.trade/alien/fre.php alphastand.win/alien/fre.php alphastand.top/alien/fre.php | |||||||||||||||
| 7852 | "C:\Users\admin\AppData\Roaming\explorer.exe" | C:\Users\admin\AppData\Roaming\explorer.exe | explorer.exe | ||||||||||||
User: admin Company: Weyerhauser Company Integrity Level: MEDIUM Description: Recovery Manager for Active Directory Forest Edition Version: 4.2.29.2 Modules
xor-url(PID) Process(7852) explorer.exe Decrypted-URLs (1)http://sir-iyke.com/five/fre.php LokiBot(PID) Process(7852) explorer.exe C2http://sir-iyke.com/five/fre.php Decoys (4)kbfvzoboss.bid/alien/fre.php alphastand.trade/alien/fre.php alphastand.win/alien/fre.php alphastand.top/alien/fre.php | |||||||||||||||
Total events
23 456
Read events
23 156
Write events
210
Delete events
90
Modification events
| (PID) Process: | (896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\896 |
| Operation: | write | Name: | 0 |
Value: 0B0E1060CC92B2EBDDC04BA0F32C82E46CF819230046E0E48DCEB696EEED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5118007D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | m=( |
Value: 6D3D2800800300000400000000000000BE883E6BB3B8DB0196000000010000008E000000430043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C0045006D00610069006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | delete value | Name: | d4( |
Value: 㑤( | |||
| (PID) Process: | (896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
Executable files
3
Suspicious files
10
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 896 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 896 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:3302BCF10D24034BF90B4FD189DF1118 | SHA256:EF6D01E919F2999F19BD920B9D9FCED0F93D322B82044D310139893C0EE996D5 | |||
| 896 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_F1B29A9AEE14A3488E75820257AC0C3D.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 896 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkC267.tmp | binary | |
MD5:64A82896E3188DD300490A2C1F90676F | SHA256:466948171D1AA7EC2CF5EE620013D9C595FF64A46296EA17F20C5C39C2D36746 | |||
| 896 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:8A8882BC9800AB9B7F4DDAC282CF6BE2 | SHA256:A9C9B2ABECDB0EB0E140597391E4E705DE28703CF1EC5D26FC9C24D516EC27C2 | |||
| 7852 | explorer.exe | C:\Users\admin\AppData\Roaming\F3F363\3C28B3.exe | executable | |
MD5:3CED5C4A6A813F2A236D1F910D70FDB7 | SHA256:905C6E5F5C773B7F4E090B892C0E7C2B8F6E11FF01C8CD18435CED36291A235E | |||
| 7852 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1693682860-607145093-2874071422-1001\0f5007522459c86e95ffcc62f32308f1_bb926e54-e3ca-40fd-ae90-2764341e7792 | binary | |
MD5:D898504A722BFF1524134C6AB6A5EAA5 | SHA256:878F32F76B159494F5A39F9321616C6068CDB82E88DF89BCC739BBC1EA78E1F9 | |||
| 7452 | WinRAR.exe | C:\Users\admin\Desktop\contract_2018870028.exe | executable | |
MD5:3CED5C4A6A813F2A236D1F910D70FDB7 | SHA256:905C6E5F5C773B7F4E090B892C0E7C2B8F6E11FF01C8CD18435CED36291A235E | |||
| 7672 | contract_2018870028.exe | C:\Users\admin\AppData\Roaming\explorer.exe | executable | |
MD5:3CED5C4A6A813F2A236D1F910D70FDB7 | SHA256:905C6E5F5C773B7F4E090B892C0E7C2B8F6E11FF01C8CD18435CED36291A235E | |||
| 7852 | explorer.exe | C:\Users\admin\AppData\Roaming\F3F363\3C28B3.hdb | binary | |
MD5:1013079A9BF8FFA458C230EA6AAF8A89 | SHA256:1B1F3BCE8DF0FC7E33B518DAB09D09AF3680E39BCC3C760DADCC50C931007BE8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
69
DNS requests
24
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7852 | explorer.exe | POST | 404 | 49.13.77.253:80 | http://sir-iyke.com/five/fre.php | unknown | — | — | malicious |
7852 | explorer.exe | POST | 404 | 49.13.77.253:80 | http://sir-iyke.com/five/fre.php | unknown | — | — | malicious |
7852 | explorer.exe | POST | 404 | 49.13.77.253:80 | http://sir-iyke.com/five/fre.php | unknown | — | — | malicious |
7852 | explorer.exe | POST | 404 | 49.13.77.253:80 | http://sir-iyke.com/five/fre.php | unknown | — | — | malicious |
7852 | explorer.exe | POST | 404 | 49.13.77.253:80 | http://sir-iyke.com/five/fre.php | unknown | — | — | malicious |
7852 | explorer.exe | POST | 404 | 49.13.77.253:80 | http://sir-iyke.com/five/fre.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
896 | OUTLOOK.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
896 | OUTLOOK.EXE | 52.109.89.19:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
896 | OUTLOOK.EXE | 23.48.23.18:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
nleditor.osi.office.net |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
odc.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7852 | explorer.exe | A Network Trojan was detected | ET MALWARE LokiBot User-Agent (Charon/Inferno) |
7852 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE LokiBot Checkin |
7852 | explorer.exe | A Network Trojan was detected | ET MALWARE LokiBot Application/Credential Data Exfiltration Detected M1 |
7852 | explorer.exe | A Network Trojan was detected | ET MALWARE LokiBot User-Agent (Charon/Inferno) |
7852 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE LokiBot Checkin |
7852 | explorer.exe | A Network Trojan was detected | ET MALWARE LokiBot User-Agent (Charon/Inferno) |
7852 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE LokiBot Checkin |
7852 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE LokiBot Checkin |
7852 | explorer.exe | A Network Trojan was detected | ET MALWARE LokiBot User-Agent (Charon/Inferno) |
7852 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE LokiBot Request for C2 Commands Detected M2 |