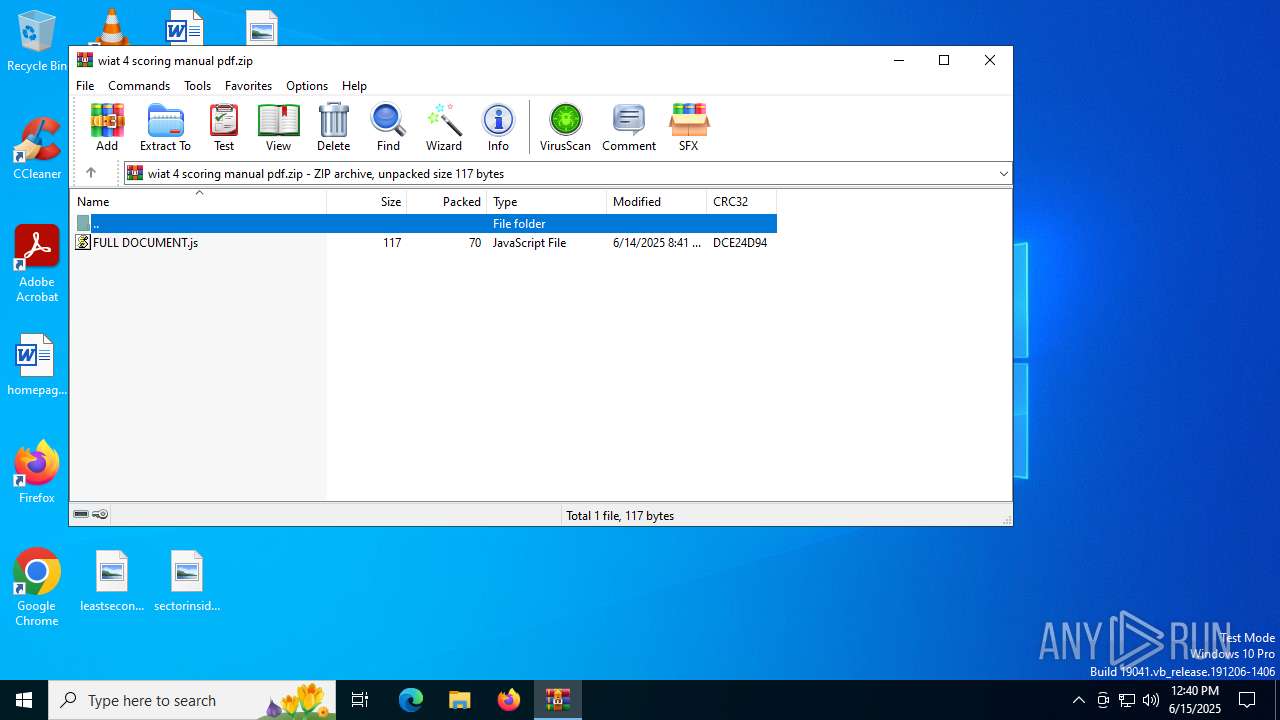
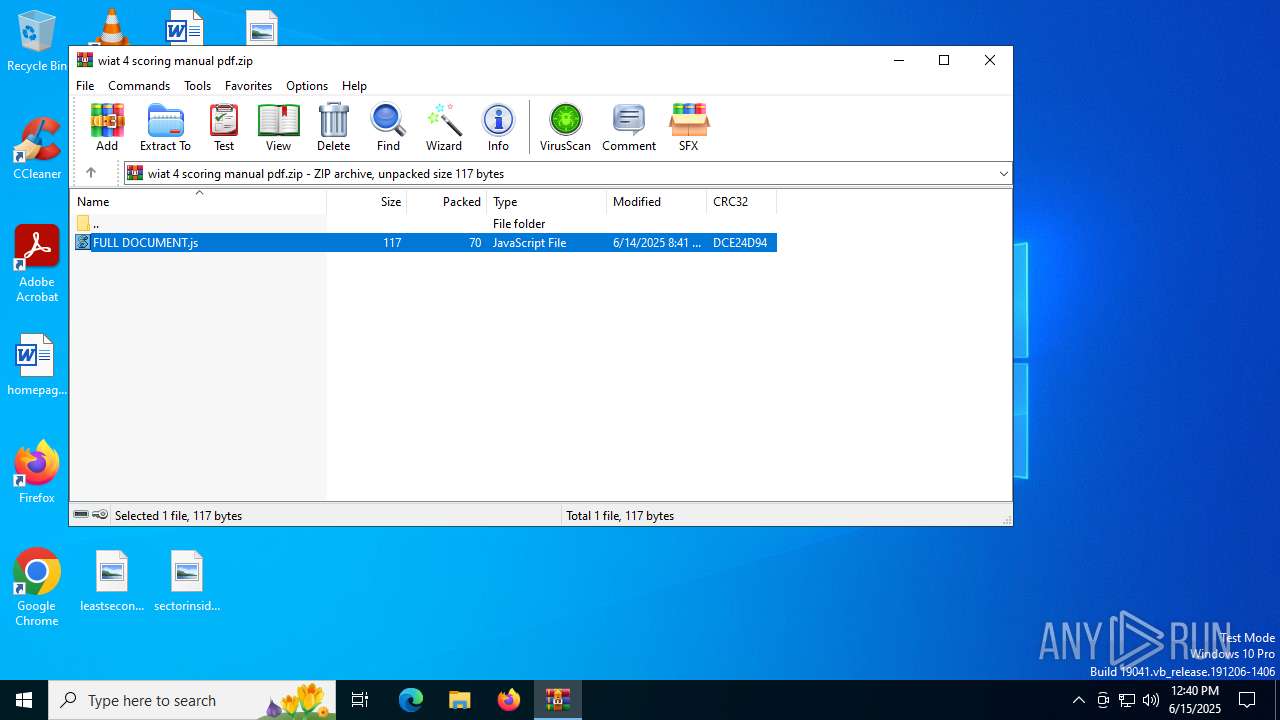
| File name: | wiat 4 scoring manual pdf.zip |
| Full analysis: | https://app.any.run/tasks/73ad881b-3712-4da1-bdb6-88847043ab4e |
| Verdict: | Malicious activity |
| Threats: | A botnet is a group of internet-connected devices that are controlled by a single individual or group, often without the knowledge or consent of the device owners. These devices can be used to launch a variety of malicious attacks, such as distributed denial-of-service (DDoS) attacks, spam campaigns, and data theft. Botnet malware is the software that is used to infect devices and turn them into part of a botnet. |
| Analysis date: | June 15, 2025, 12:40:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 8999DE451327701ADB1048E207C59CA0 |
| SHA1: | 3AF09B23AF495CF583C0141F1093C132A3F6516D |
| SHA256: | DE5BF4A9FEB84084F193D8C4F09D5CF3BC93675D71AB8A1BA721F12D19CE6C5E |
| SSDEEP: | 6:5jYKEmvPBYRZFKaAJFtlfmKXKik3Y8svB+lK:5jYK7vPBYRZlGTl+u1l5vBaK |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6536)
May hide the program window using WMI (SCRIPT)
- wscript.exe (PID: 5172)
ANDROMEDA mutex has been found
- powershell.exe (PID: 3668)
Bypass execution policy to execute commands
- powershell.exe (PID: 3668)
Gets information about running processes via WMI (SCRIPT)
- wscript.exe (PID: 5172)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 5172)
The process executes JS scripts
- WinRAR.exe (PID: 6536)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6536)
Executed via WMI
- powershell.exe (PID: 3668)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 5172)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 3668)
Connects to the server without a host name
- wscript.exe (PID: 5172)
- powershell.exe (PID: 3668)
Creates an object to access WMI (SCRIPT)
- wscript.exe (PID: 5172)
Reverses array data (POWERSHELL)
- powershell.exe (PID: 3668)
Converts a string into array of characters (POWERSHELL)
- powershell.exe (PID: 3668)
INFO
Checks proxy server information
- wscript.exe (PID: 5172)
- powershell.exe (PID: 3668)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6536)
Creates files in the program directory
- wscript.exe (PID: 5172)
Disables trace logs
- powershell.exe (PID: 3668)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:14 20:41:36 |
| ZipCRC: | 0xdce24d94 |
| ZipCompressedSize: | 70 |
| ZipUncompressedSize: | 117 |
| ZipFileName: | FULL DOCUMENT.js |
Total processes
140
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3668 | powershell.exe -ep bypass -file "C:\ProgramData\yqsuenn.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4832 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5172 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa6536.3566\FULL DOCUMENT.js" | C:\Windows\System32\wscript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5600 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6536 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\wiat 4 scoring manual pdf.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
7 437
Read events
7 424
Write events
13
Delete events
0
Modification events
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\wiat 4 scoring manual pdf.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.js\OpenWithProgids |
| Operation: | write | Name: | JSFile |
Value: | |||
| (PID) Process: | (5172) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
0
Suspicious files
0
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5172 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\zso[1].htm | html | |
MD5:FBB1E60643DB3F6F40526AB548DEAD34 | SHA256:A813E5C3B58011322C4796FD0584794E5667173FCE0F151BD4119949C5C3118B | |||
| 3668 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ii10f1i1.0rj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6536.3566\FULL DOCUMENT.js | text | |
MD5:E289AF2B8FF598E138E9B43F4049519A | SHA256:F87619A204C52F134BF0DB874D1483C4F59E52FFC4260171AE4C2E776FC9560D | |||
| 3668 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mktarr2k.meu.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5172 | wscript.exe | C:\ProgramData\yqsuenn.ps1 | text | |
MD5:3AC07E04C0904534D2CD0241A62CB348 | SHA256:86D4A3DF79A5601856BB127F6C6952CD29A83AF6F55FB7BF5080070A52358CAB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
26
DNS requests
14
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5172 | wscript.exe | GET | 200 | 181.174.164.170:80 | http://181.174.164.170/zso | unknown | — | — | unknown |
2288 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2632 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3668 | powershell.exe | GET | 404 | 181.174.164.170:80 | http://181.174.164.170/649566714 | unknown | — | — | unknown |
2632 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3668 | powershell.exe | GET | 404 | 181.174.164.170:80 | http://181.174.164.170/649566714 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5900 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5172 | wscript.exe | 181.174.164.170:80 | — | Offshore Racks S.A | PA | unknown |
2336 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2288 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2288 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5172 | wscript.exe | Misc activity | ET INFO Observed UA-CPU Header |