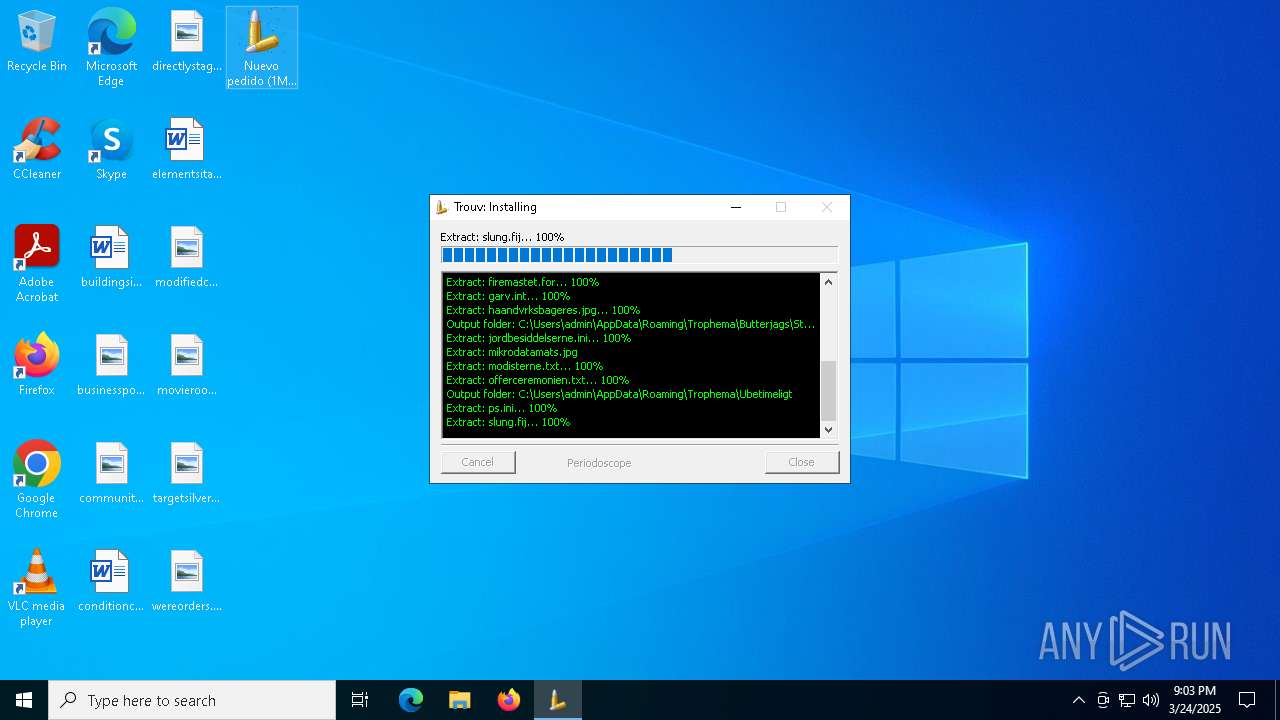
| File name: | Nuevo pedido (1M85700).exe |
| Full analysis: | https://app.any.run/tasks/fc953097-96ac-4bc3-a064-522ff883ce84 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | March 24, 2025, 21:02:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 666231157A1AA72B467C82C7ABA16653 |
| SHA1: | 1FED551514389221DD64979A4F705804D0D6F660 |
| SHA256: | DDE6B5B337FBB0C75BA9198962DEDC4EB0A1C0D33372096033E995379ACA7E60 |
| SSDEEP: | 49152:ivCj8fW1Y6cA6XxBxOS+zd+DjcBi0U/IBn4qKBn7Z4crX0GtXirk3zkzcAHbjOL1:j1sA6BBxAd+DjcM00DJBn7qGt8kjmcAu |
MALICIOUS
Executing a file with an untrusted certificate
- Nuevo pedido (1M85700).exe (PID: 5988)
- Nuevo pedido (1M85700).exe (PID: 1164)
- Nuevo pedido (1M85700).exe (PID: 5324)
- Nuevo pedido (1M85700).exe (PID: 5576)
GULOADER SHELLCODE has been detected (YARA)
- Nuevo pedido (1M85700).exe (PID: 5988)
- Nuevo pedido (1M85700).exe (PID: 5324)
- Nuevo pedido (1M85700).exe (PID: 1164)
GULOADER has been detected (YARA)
- Nuevo pedido (1M85700).exe (PID: 5988)
- Nuevo pedido (1M85700).exe (PID: 5324)
- Nuevo pedido (1M85700).exe (PID: 1164)
Scans artifacts that could help determine the target
- Nuevo pedido (1M85700).exe (PID: 5324)
- Nuevo pedido (1M85700).exe (PID: 5576)
Actions looks like stealing of personal data
- Nuevo pedido (1M85700).exe (PID: 5324)
- Nuevo pedido (1M85700).exe (PID: 5576)
Steals credentials from Web Browsers
- Nuevo pedido (1M85700).exe (PID: 5324)
- Nuevo pedido (1M85700).exe (PID: 5576)
PURELOGS has been detected (SURICATA)
- Nuevo pedido (1M85700).exe (PID: 5324)
PURECRYPTER has been detected (SURICATA)
- Nuevo pedido (1M85700).exe (PID: 5324)
- Nuevo pedido (1M85700).exe (PID: 5576)
SUSPICIOUS
The process creates files with name similar to system file names
- Nuevo pedido (1M85700).exe (PID: 5988)
- Nuevo pedido (1M85700).exe (PID: 1164)
Executable content was dropped or overwritten
- Nuevo pedido (1M85700).exe (PID: 5988)
- Nuevo pedido (1M85700).exe (PID: 1164)
Malware-specific behavior (creating "System.dll" in Temp)
- Nuevo pedido (1M85700).exe (PID: 5988)
- Nuevo pedido (1M85700).exe (PID: 1164)
There is functionality for taking screenshot (YARA)
- Nuevo pedido (1M85700).exe (PID: 5988)
- Nuevo pedido (1M85700).exe (PID: 5324)
- Nuevo pedido (1M85700).exe (PID: 1164)
Application launched itself
- Nuevo pedido (1M85700).exe (PID: 5988)
- Nuevo pedido (1M85700).exe (PID: 1164)
Reads security settings of Internet Explorer
- Nuevo pedido (1M85700).exe (PID: 5324)
- Nuevo pedido (1M85700).exe (PID: 5576)
- ShellExperienceHost.exe (PID: 1748)
Connects to the server without a host name
- Nuevo pedido (1M85700).exe (PID: 5324)
- Nuevo pedido (1M85700).exe (PID: 5576)
Connects to unusual port
- Nuevo pedido (1M85700).exe (PID: 5576)
- Nuevo pedido (1M85700).exe (PID: 5324)
INFO
Reads the computer name
- Nuevo pedido (1M85700).exe (PID: 5988)
- Nuevo pedido (1M85700).exe (PID: 5324)
- ShellExperienceHost.exe (PID: 1748)
Checks supported languages
- Nuevo pedido (1M85700).exe (PID: 5988)
- Nuevo pedido (1M85700).exe (PID: 1164)
- Nuevo pedido (1M85700).exe (PID: 5324)
- Nuevo pedido (1M85700).exe (PID: 5576)
- ShellExperienceHost.exe (PID: 1748)
The sample compiled with english language support
- Nuevo pedido (1M85700).exe (PID: 5988)
Creates files or folders in the user directory
- Nuevo pedido (1M85700).exe (PID: 5988)
- BackgroundTransferHost.exe (PID: 6592)
Create files in a temporary directory
- Nuevo pedido (1M85700).exe (PID: 5988)
- Nuevo pedido (1M85700).exe (PID: 1164)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 6592)
- Nuevo pedido (1M85700).exe (PID: 5324)
- Nuevo pedido (1M85700).exe (PID: 5576)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 3888)
- BackgroundTransferHost.exe (PID: 6592)
- BackgroundTransferHost.exe (PID: 4608)
- BackgroundTransferHost.exe (PID: 4756)
- BackgroundTransferHost.exe (PID: 6044)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 6592)
Manual execution by a user
- Nuevo pedido (1M85700).exe (PID: 1164)
Reads Microsoft Office registry keys
- Nuevo pedido (1M85700).exe (PID: 5324)
- Nuevo pedido (1M85700).exe (PID: 5576)
Reads the machine GUID from the registry
- Nuevo pedido (1M85700).exe (PID: 5576)
- Nuevo pedido (1M85700).exe (PID: 5324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:08:01 02:41:11+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 3805696 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x34a2 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.5.0.0 |
| ProductVersionNumber: | 2.5.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | Federal Express Corp. |
| FileDescription: | Jones Apparel Group Inc. |
| LegalTrademarks: | ACT Manufacturing Inc. |
| OriginalFileName: | tsarrigets.exe |
| ProductName: | Greif Bros. Corporation |
Total processes
149
Monitored processes
13
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | "C:\Users\admin\Desktop\Nuevo pedido (1M85700).exe" | C:\Users\admin\Desktop\Nuevo pedido (1M85700).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Jones Apparel Group Inc. Exit code: 0 Modules
| |||||||||||||||
| 1748 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2980 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3888 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4608 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4756 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5324 | "C:\Users\admin\Desktop\Nuevo pedido (1M85700).exe" | C:\Users\admin\Desktop\Nuevo pedido (1M85700).exe | Nuevo pedido (1M85700).exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Jones Apparel Group Inc. Exit code: 0 Modules
| |||||||||||||||
| 5576 | "C:\Users\admin\Desktop\Nuevo pedido (1M85700).exe" | C:\Users\admin\Desktop\Nuevo pedido (1M85700).exe | Nuevo pedido (1M85700).exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Jones Apparel Group Inc. Exit code: 0 Modules
| |||||||||||||||
| 5968 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5988 | "C:\Users\admin\Desktop\Nuevo pedido (1M85700).exe" | C:\Users\admin\Desktop\Nuevo pedido (1M85700).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Jones Apparel Group Inc. Exit code: 0 Modules
| |||||||||||||||
Total events
8 192
Read events
7 613
Write events
579
Delete events
0
Modification events
| (PID) Process: | (5988) Nuevo pedido (1M85700).exe | Key: | HKEY_CURRENT_USER\fancies\onionskin\propositionise |
| Operation: | write | Name: | sneryddendes |
Value: 211939 | |||
| (PID) Process: | (5988) Nuevo pedido (1M85700).exe | Key: | HKEY_CURRENT_USER\Giddyhead211\nectarised\defineredes |
| Operation: | write | Name: | Sidewards |
Value: %Nstedes%\skandere.but | |||
| (PID) Process: | (3888) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3888) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3888) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6592) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6592) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6592) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4608) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4608) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
2
Suspicious files
13
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5988 | Nuevo pedido (1M85700).exe | C:\Users\admin\AppData\Roaming\Trophema\Butterjags\barkarolernes.mis | — | |
MD5:— | SHA256:— | |||
| 5988 | Nuevo pedido (1M85700).exe | C:\Users\admin\AppData\Roaming\Trophema\Butterjags\Stalemated\garv.int | — | |
MD5:— | SHA256:— | |||
| 5988 | Nuevo pedido (1M85700).exe | C:\Users\admin\AppData\Roaming\Trophema\Ubetimeligt\slung.fij | — | |
MD5:— | SHA256:— | |||
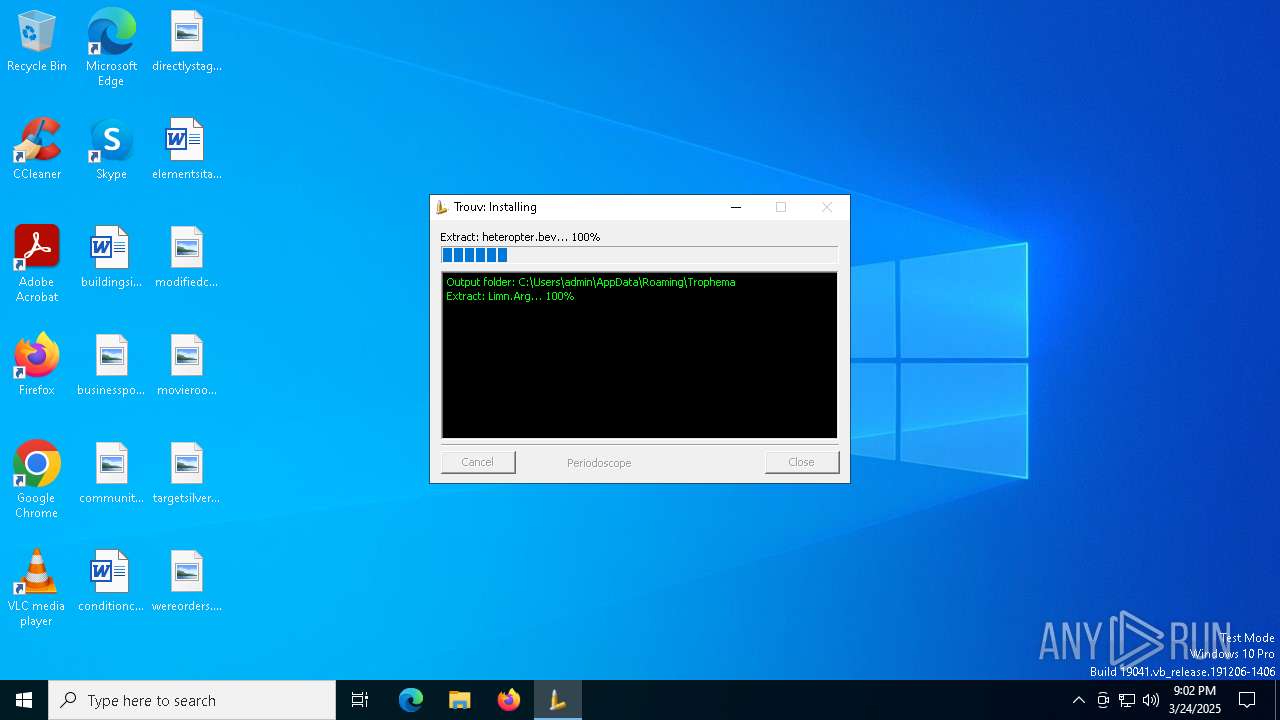
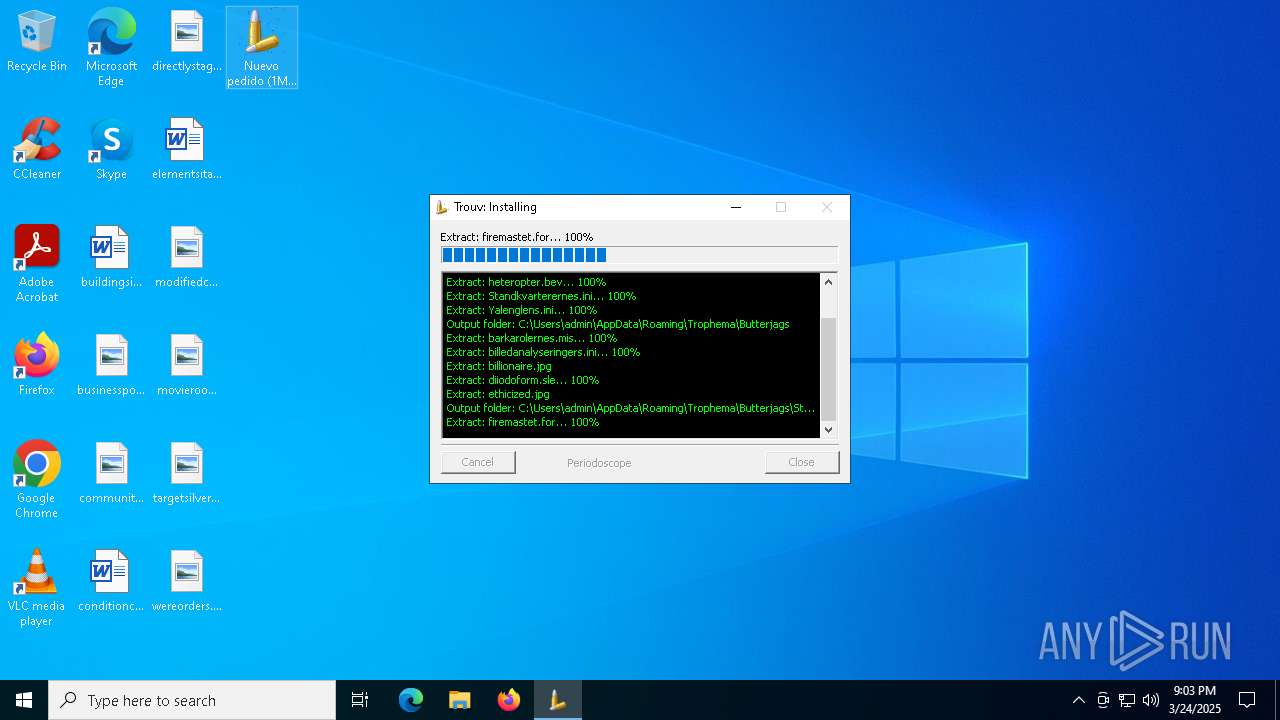
| 5988 | Nuevo pedido (1M85700).exe | C:\Users\admin\AppData\Roaming\Trophema\heteropter.bev | binary | |
MD5:E2D4792D90735883CAA9462B13736361 | SHA256:00A7269EF92D9DEFCA170CA92E24AC36168A312F46152DC6A8D3557095911C85 | |||
| 6592 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\5b798eea-8327-44df-bd1a-591cd9d6da39.down_data | — | |
MD5:— | SHA256:— | |||
| 5988 | Nuevo pedido (1M85700).exe | C:\Users\admin\AppData\Roaming\Trophema\Limn.Arg | binary | |
MD5:A3939DB7578DB6868308CFD393506933 | SHA256:AC83BACEDE6CDE31C58D14CE46C60359739AD47FAEE766BDD93704F9EB3CF9B1 | |||
| 5988 | Nuevo pedido (1M85700).exe | C:\Users\admin\AppData\Roaming\Trophema\Yalenglens.ini | text | |
MD5:FFFBE2929C7CDEFD4036FC90E2E8D30E | SHA256:C380368254FF79885EC48C925DE1CB9550C8272E013C936036873AC63FBC4A08 | |||
| 5988 | Nuevo pedido (1M85700).exe | C:\Users\admin\AppData\Roaming\Trophema\Blges.ini | text | |
MD5:CB27AD0B84B3385E6D5DDF46656CBAE9 | SHA256:A5C299F01AE8B67AF45384AE89B904F91C7EB411E040F8C1326D122E4165FB0B | |||
| 5988 | Nuevo pedido (1M85700).exe | C:\Users\admin\AppData\Roaming\Trophema\Standkvarterernes.ini | text | |
MD5:827D8C5EA33745A9878F57586D86B5C1 | SHA256:19FE1C65C967AD3260FAC631DC6F10E5435A7263005B866E21CC44C8EB893892 | |||
| 5988 | Nuevo pedido (1M85700).exe | C:\Users\admin\AppData\Roaming\Trophema\Butterjags\diiodoform.sle | binary | |
MD5:5CD6EEF3DA2E17CEE9D6B925E993082E | SHA256:B7BA0F86054684942B652875EFBDC8A5AB4A6B9729D62E1019A8F51A395F2E46 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
34
DNS requests
18
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6592 | BackgroundTransferHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
976 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5436 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5436 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5324 | Nuevo pedido (1M85700).exe | GET | 200 | 135.148.3.78:80 | http://135.148.3.78/cfr/nYhQFF15.bin | unknown | — | — | malicious |
5576 | Nuevo pedido (1M85700).exe | GET | 200 | 135.148.3.78:80 | http://135.148.3.78/cfr/nYhQFF15.bin | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.48.23.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
976 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5324 | Nuevo pedido (1M85700).exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
5324 | Nuevo pedido (1M85700).exe | A Network Trojan was detected | LOADER [ANY.RUN] PureLogs Download Attempt (LOAD) |
5324 | Nuevo pedido (1M85700).exe | STEALER [ANY.RUN] PureLogs Stealer Exfiltration | |
5324 | Nuevo pedido (1M85700).exe | A Network Trojan was detected | STEALER [ANY.RUN] PureLogs Stealer Exfiltration |
5576 | Nuevo pedido (1M85700).exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
5576 | Nuevo pedido (1M85700).exe | A Network Trojan was detected | LOADER [ANY.RUN] PureLogs Download Attempt (LOAD) |