| URL: | https://vtsamples.commondatastorage.googleapis.com/7a6ceb6ace388bfb6c1698a723df98ec107e7043e955d64b03fba81cb65627db?GoogleAccessId=758681729565-rc7fgq07icj8c9dm2gi34a4cckv235v1@developer.gserviceaccount.com&Expires=1690225636&Signature=dJywbNr3dJzVEzT6nIe91Lo7btBRsqqdaEqPOiala5wyCtFA%2F6OIfUJ202LRpaRfnsJvphpONFnw%0AExLTG2uB260PEpLWItZPFOSl5mO3KBzQqaNu%2BUVHQEOeQgFpqcVtlzfeR5mb5ZnMFVEJUJs3F%2Fba%0A%2FaJhjIU7bMAvNnsLwv19PBrboSWLr0dABoXQ%2BukTGqmj5NFcGWIMIQCPrJ%2BhtiEX26SRIUbgu%2BqA%0AXuvQ2Bk4Q1EJjmaOYosjopDeJXOzmYxS9ov0By1h3WgmZ72jCIai4VGRrlWxvUFS3YA%2FORfaz%2BGN%0AErra1z8e%2Brp%2BHoTSxzzoAdJ5pqSlONgHC%2Bc33Q%3D%3D&response-content-disposition=attachment%3B%20filename%3D%227a6ceb6ace388bfb6c1698a723df98ec107e7043e955d64b03fba81cb65627db%22&response-content-type=application%2Foctet-stream; |
| Full analysis: | https://app.any.run/tasks/5cb9cdb1-d79c-480a-8d8c-c1938156b167 |
| Verdict: | Malicious activity |
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | July 24, 2023, 18:31:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 2CCB7277D40C165F73BB96965D6AC2F7 |
| SHA1: | C5EFB97D6A871D071D68F08FD8038FBFC7DEE5F3 |
| SHA256: | DDB053A8AEB979B03FEF0C0D5F8C192CEDB660432AEE143080005FD2F9DCEBB4 |
| SSDEEP: | 24:2h2Rx1pKlwIXprxOSzsemlXdiAj7LyiOSUy1ixAIe:vETSyekAj7Ly7G |
MALICIOUS
Application was dropped or rewritten from another process
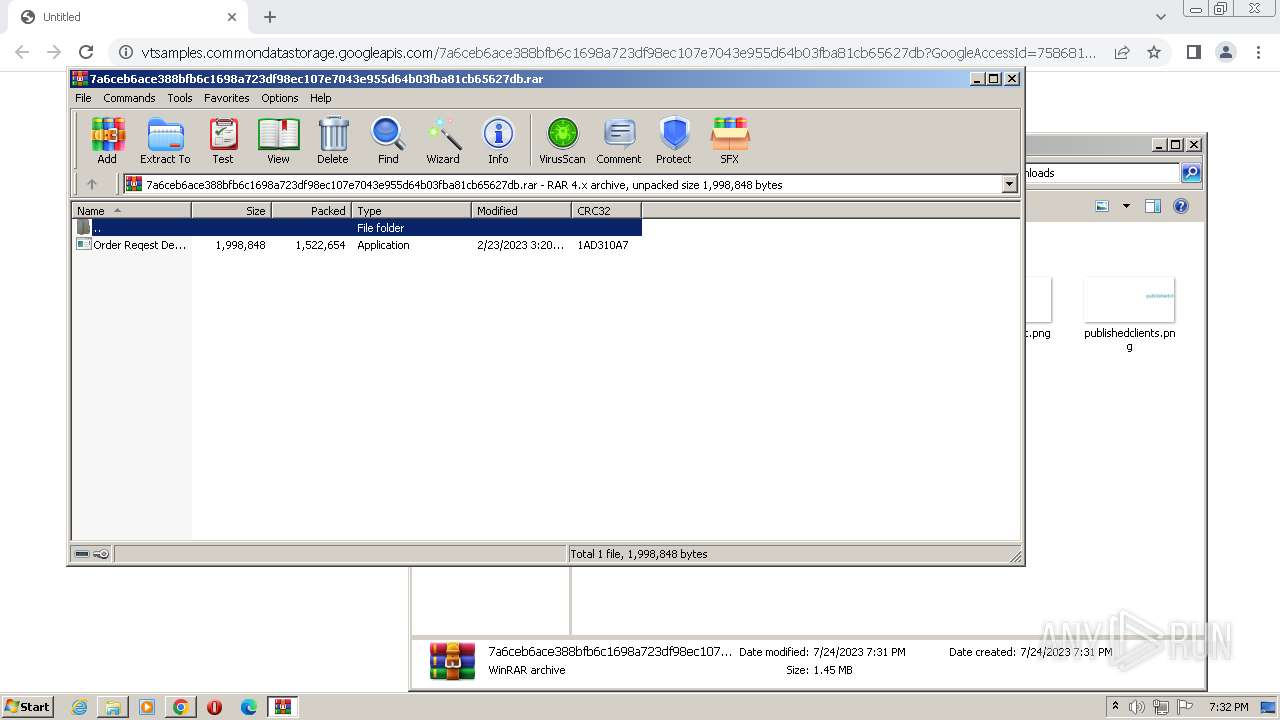
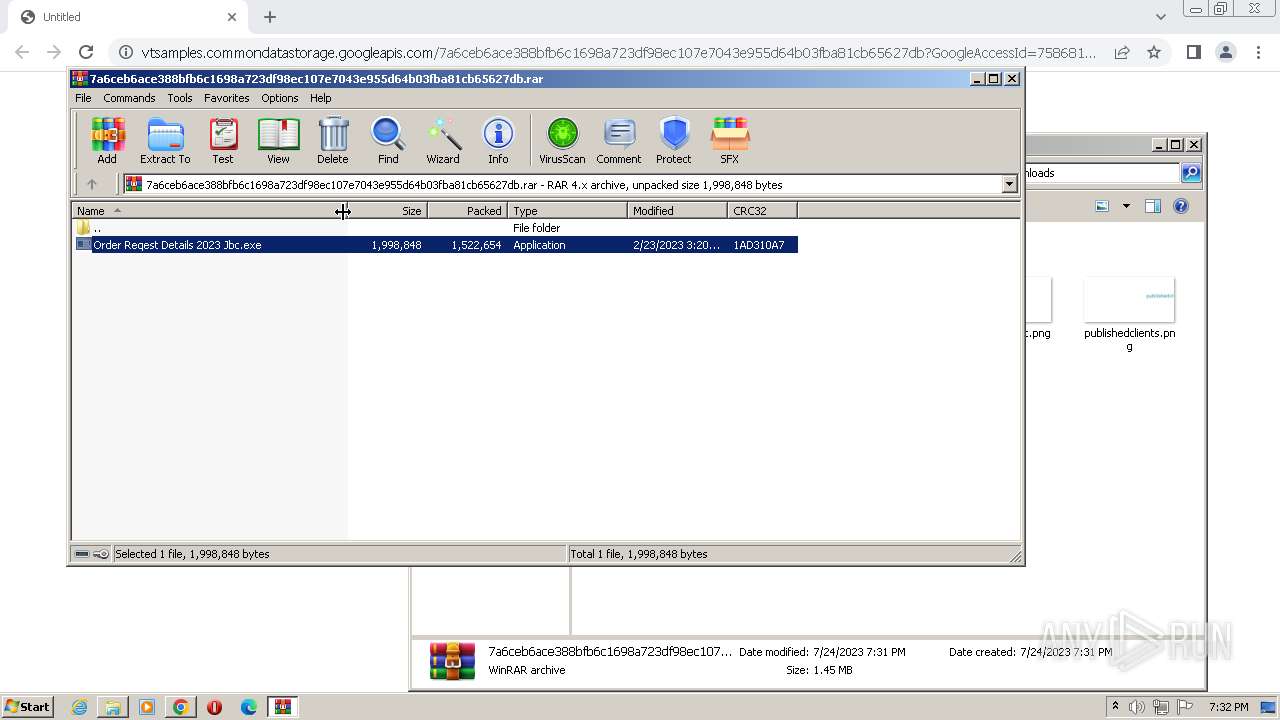
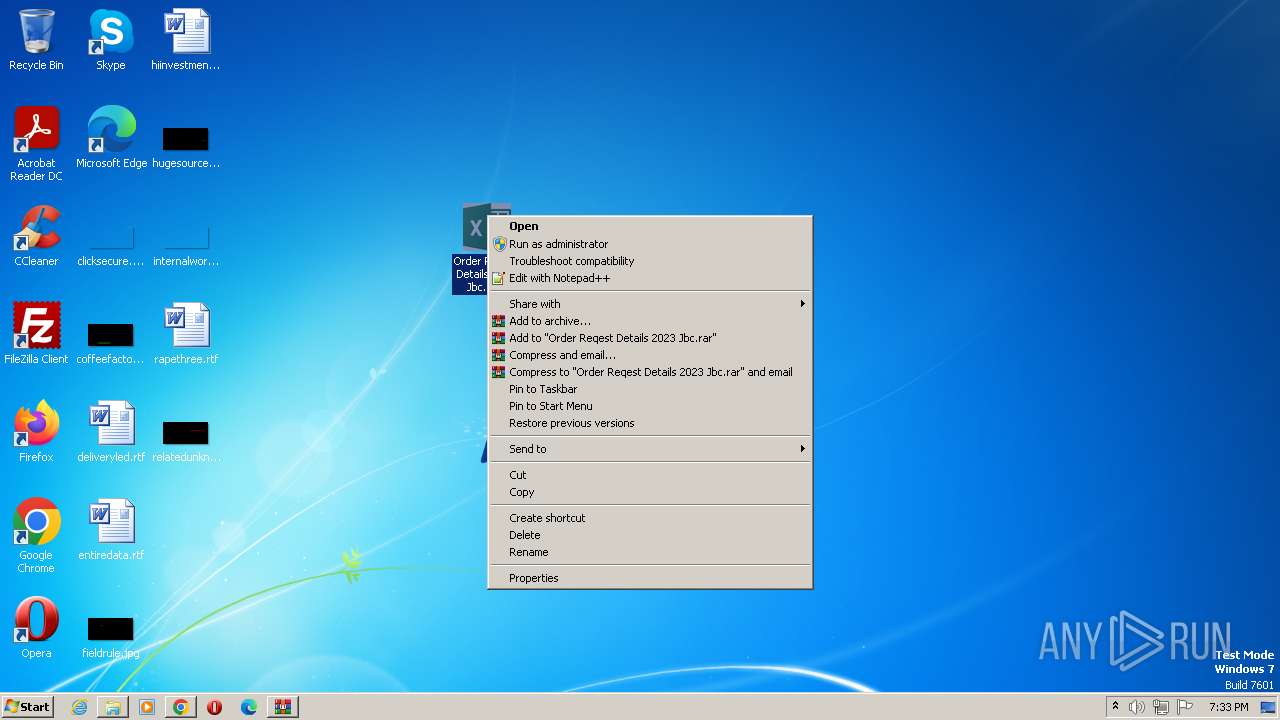
- Order Reqest Details 2023 Jbc.exe (PID: 600)
- Order Reqest Details 2023 Jbc.exe (PID: 3488)
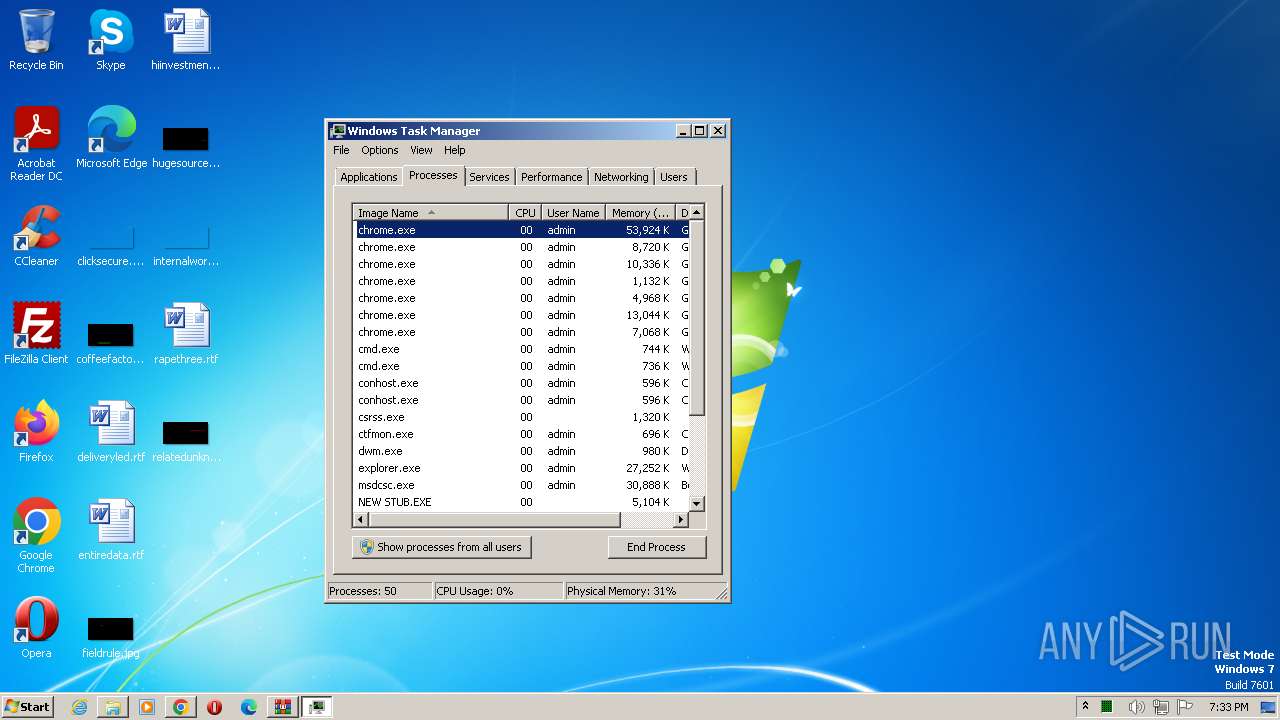
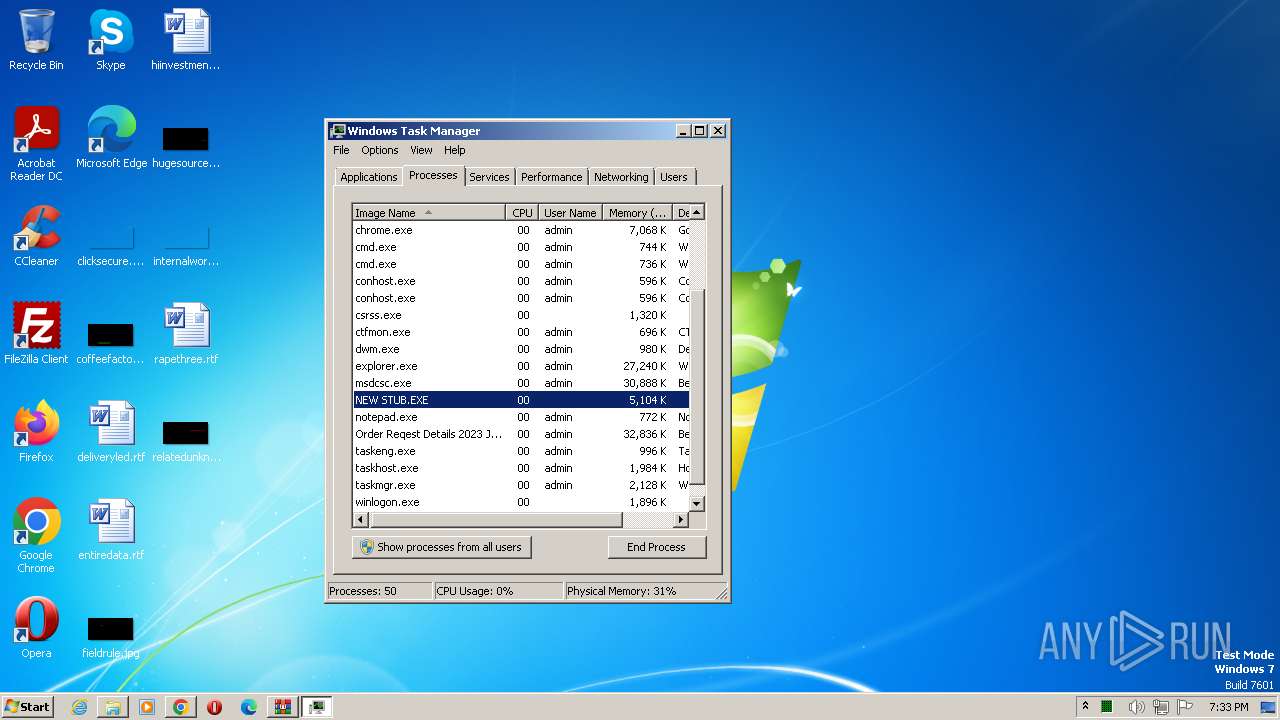
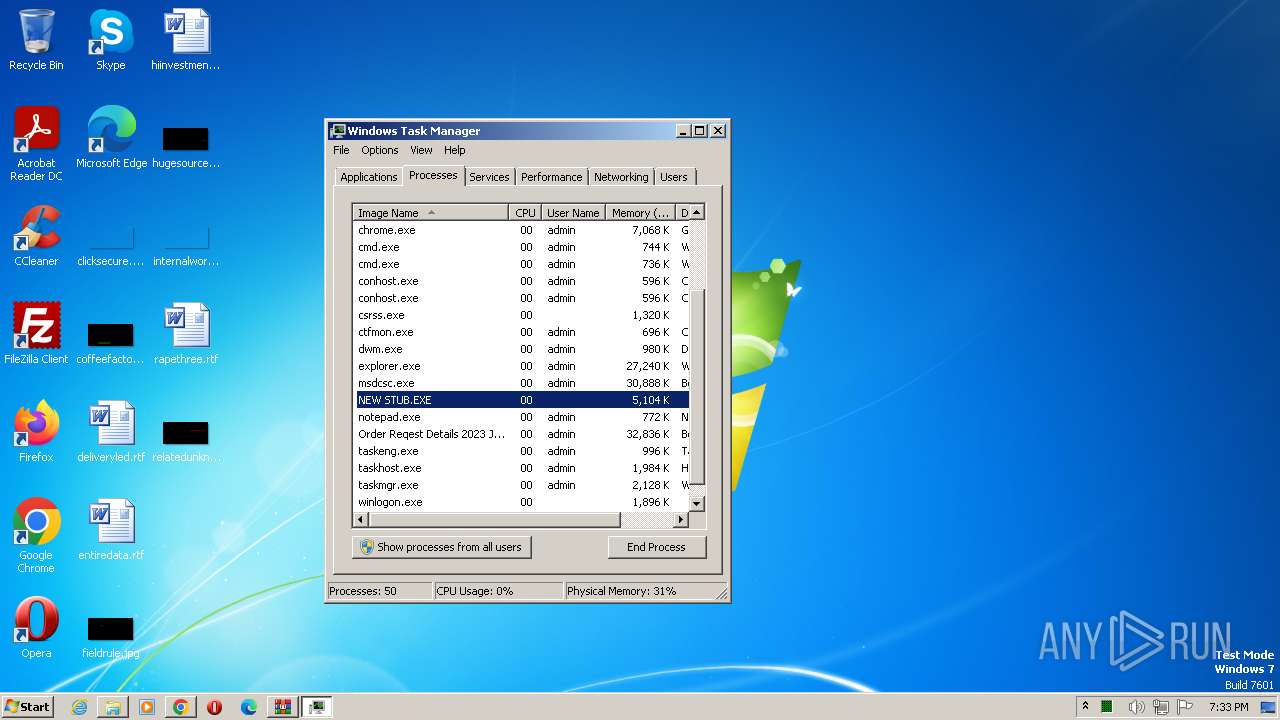
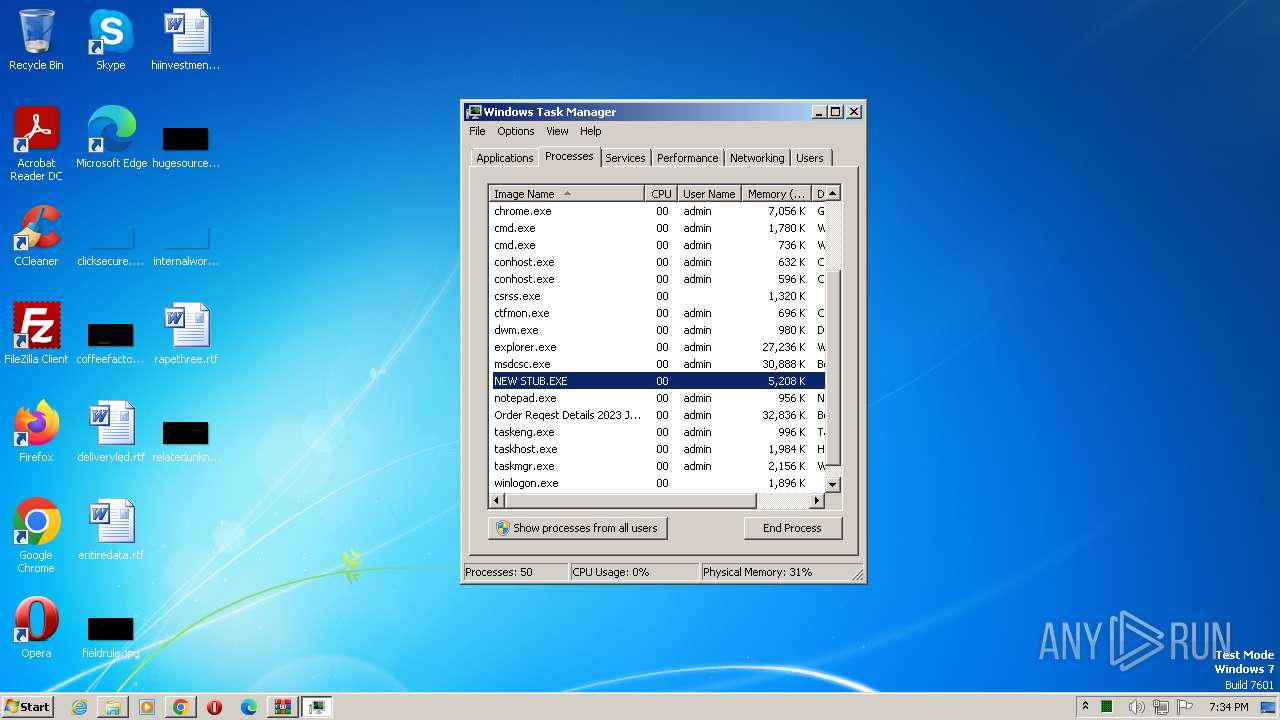
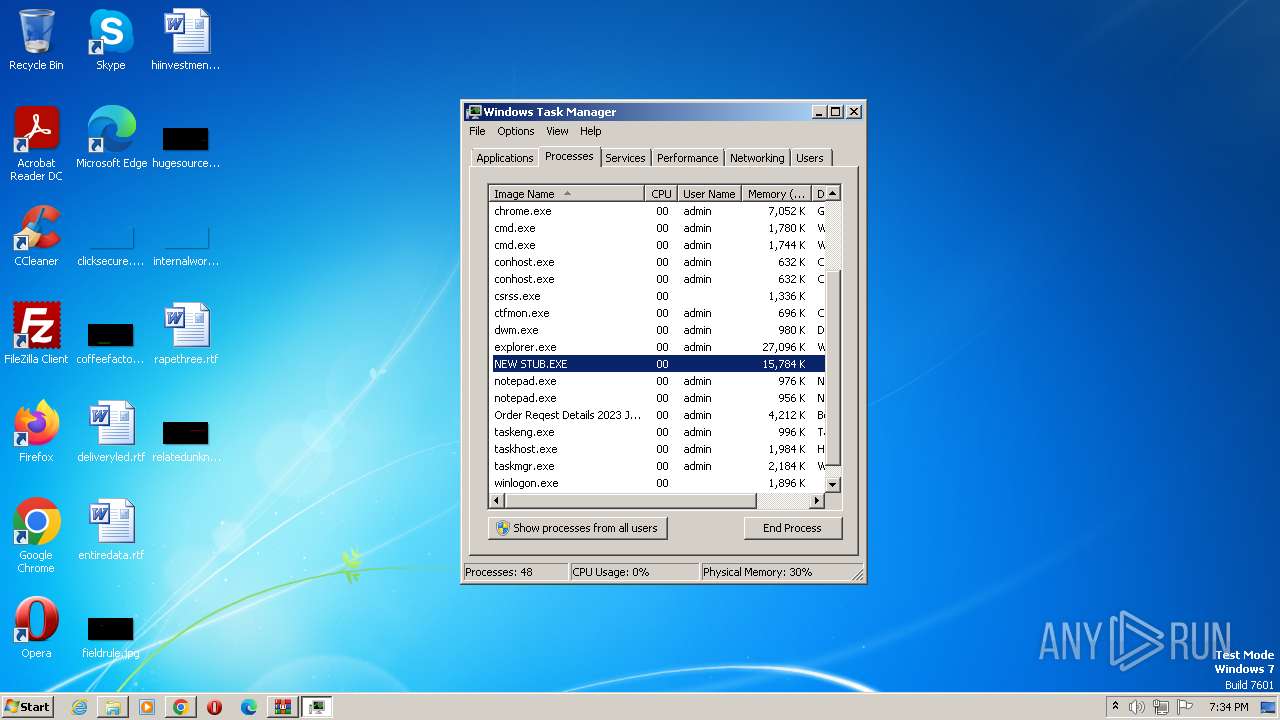
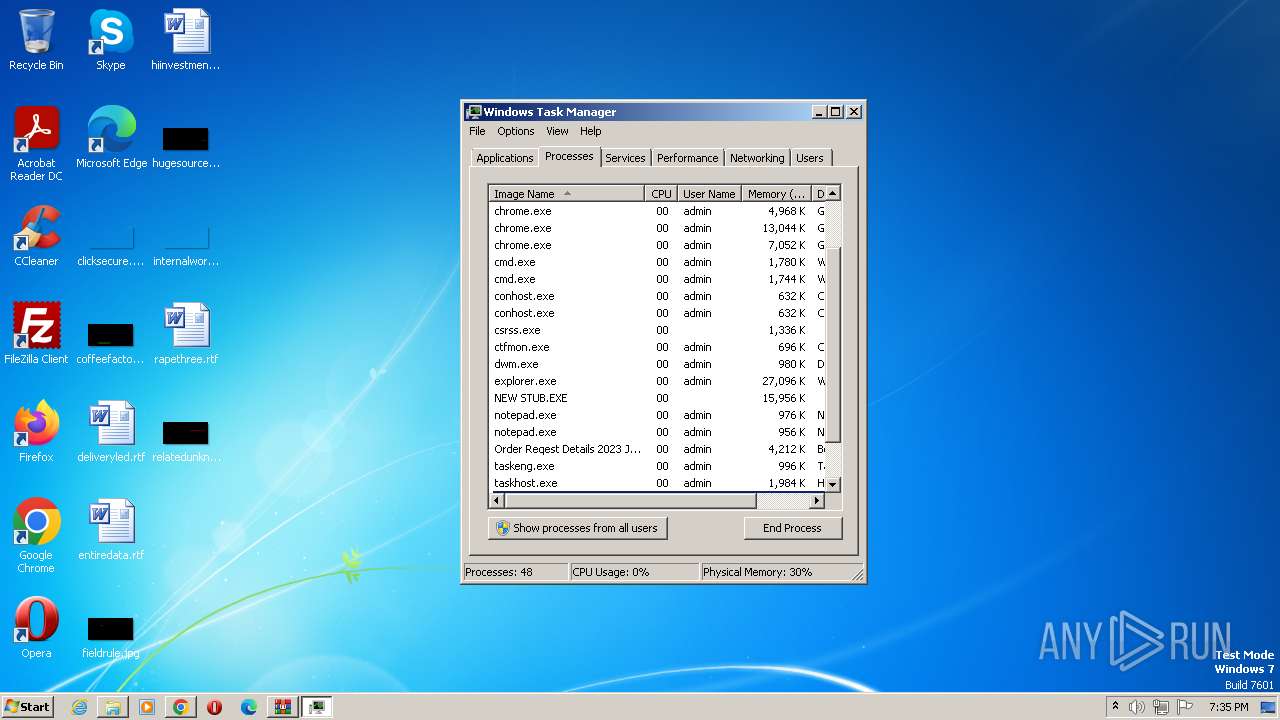
- NEW STUB.EXE (PID: 1480)
- msdcsc.exe (PID: 2424)
- Order Reqest Details 2023 Jbc.exe (PID: 2948)
- NEW STUB.EXE (PID: 3236)
- Order Reqest Details 2023 Jbc.exe (PID: 2716)
- msdcsc.exe (PID: 1836)
Uses Task Scheduler to run other applications
- Order Reqest Details 2023 Jbc.exe (PID: 2716)
- Order Reqest Details 2023 Jbc.exe (PID: 600)
- msdcsc.exe (PID: 2424)
Changes the login/logoff helper path in the registry
- Order Reqest Details 2023 Jbc.exe (PID: 3488)
NANOCORE detected by memory dumps
- NEW STUB.EXE (PID: 1480)
- Order Reqest Details 2023 Jbc.exe (PID: 2948)
Adds path to the Windows Defender exclusion list
- Order Reqest Details 2023 Jbc.exe (PID: 600)
Changes the autorun value in the registry
- Order Reqest Details 2023 Jbc.exe (PID: 2948)
DARKCOMET detected by memory dumps
- Order Reqest Details 2023 Jbc.exe (PID: 2948)
Creates or modifies Windows services
- Order Reqest Details 2023 Jbc.exe (PID: 2948)
Changes Security Center notification settings
- msdcsc.exe (PID: 1836)
SUSPICIOUS
Executable content was dropped or overwritten
- Order Reqest Details 2023 Jbc.exe (PID: 2716)
- Order Reqest Details 2023 Jbc.exe (PID: 3488)
- NEW STUB.EXE (PID: 1480)
Reads the Internet Settings
- Order Reqest Details 2023 Jbc.exe (PID: 3488)
- Order Reqest Details 2023 Jbc.exe (PID: 2716)
- Order Reqest Details 2023 Jbc.exe (PID: 600)
- Order Reqest Details 2023 Jbc.exe (PID: 2948)
- msdcsc.exe (PID: 2424)
Application launched itself
- Order Reqest Details 2023 Jbc.exe (PID: 2716)
- Order Reqest Details 2023 Jbc.exe (PID: 600)
- msdcsc.exe (PID: 2424)
Starts CMD.EXE for commands execution
- Order Reqest Details 2023 Jbc.exe (PID: 3488)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2920)
- cmd.exe (PID: 2872)
Start notepad (likely ransomware note)
- Order Reqest Details 2023 Jbc.exe (PID: 3488)
- Order Reqest Details 2023 Jbc.exe (PID: 2948)
Starts itself from another location
- Order Reqest Details 2023 Jbc.exe (PID: 3488)
Starts POWERSHELL.EXE for commands execution
- Order Reqest Details 2023 Jbc.exe (PID: 600)
Connects to unusual port
- NEW STUB.EXE (PID: 1480)
- Order Reqest Details 2023 Jbc.exe (PID: 2948)
Script adds exclusion path to Windows Defender
- Order Reqest Details 2023 Jbc.exe (PID: 600)
INFO
Application launched itself
- chrome.exe (PID: 1532)
The process uses the downloaded file
- chrome.exe (PID: 2068)
- WinRAR.exe (PID: 2528)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2528)
Manual execution by a user
- Order Reqest Details 2023 Jbc.exe (PID: 2716)
- Order Reqest Details 2023 Jbc.exe (PID: 600)
- notepad++.exe (PID: 1616)
- taskmgr.exe (PID: 3272)
- notepad++.exe (PID: 3972)
- WinRAR.exe (PID: 2528)
The process checks LSA protection
- notepad++.exe (PID: 1616)
- Order Reqest Details 2023 Jbc.exe (PID: 2716)
- Order Reqest Details 2023 Jbc.exe (PID: 3488)
- NEW STUB.EXE (PID: 1480)
- Order Reqest Details 2023 Jbc.exe (PID: 600)
- NEW STUB.EXE (PID: 3236)
- notepad++.exe (PID: 3972)
- Order Reqest Details 2023 Jbc.exe (PID: 2948)
- msdcsc.exe (PID: 2424)
- msdcsc.exe (PID: 1836)
Reads the computer name
- Order Reqest Details 2023 Jbc.exe (PID: 2716)
- Order Reqest Details 2023 Jbc.exe (PID: 600)
- Order Reqest Details 2023 Jbc.exe (PID: 3488)
- NEW STUB.EXE (PID: 1480)
- msdcsc.exe (PID: 2424)
- NEW STUB.EXE (PID: 3236)
- Order Reqest Details 2023 Jbc.exe (PID: 2948)
- msdcsc.exe (PID: 1836)
Checks supported languages
- Order Reqest Details 2023 Jbc.exe (PID: 600)
- Order Reqest Details 2023 Jbc.exe (PID: 3488)
- NEW STUB.EXE (PID: 1480)
- msdcsc.exe (PID: 2424)
- Order Reqest Details 2023 Jbc.exe (PID: 2948)
- NEW STUB.EXE (PID: 3236)
- Order Reqest Details 2023 Jbc.exe (PID: 2716)
- msdcsc.exe (PID: 1836)
Creates files or folders in the user directory
- Order Reqest Details 2023 Jbc.exe (PID: 2716)
- NEW STUB.EXE (PID: 1480)
Create files in a temporary directory
- Order Reqest Details 2023 Jbc.exe (PID: 2716)
- Order Reqest Details 2023 Jbc.exe (PID: 3488)
- Order Reqest Details 2023 Jbc.exe (PID: 600)
- msdcsc.exe (PID: 2424)
Reads the machine GUID from the registry
- Order Reqest Details 2023 Jbc.exe (PID: 2716)
- Order Reqest Details 2023 Jbc.exe (PID: 3488)
- NEW STUB.EXE (PID: 1480)
- Order Reqest Details 2023 Jbc.exe (PID: 600)
- NEW STUB.EXE (PID: 3236)
- msdcsc.exe (PID: 2424)
Process checks are UAC notifies on
- NEW STUB.EXE (PID: 1480)
Reads Environment values
- NEW STUB.EXE (PID: 1480)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Nanocore
(PID) Process(1480) NEW STUB.EXE
KeyboardLoggingTrue
BuildTime2021-04-18 18:21:52.193672
Version1.2.2.0
Mutex94803e62-45dd-47d9-9960-20dd767ecae3
DefaultGroupAPILA 2021
PrimaryConnectionHosttony3311.ddns.net
BackupConnectionHosttony3311.ddns.net
ConnectionPort10108
RunOnStartupTrue
RequestElevationFalse
BypassUserAccountControlFalse
ClearZoneIdentifierTrue
ClearAccessControlTrue
SetCriticalProcessFalse
PreventSystemSleepTrue
ActivateAwayModeFalse
EnableDebugModeFalse
RunDelay0
ConnectDelay4000
RestartDelay5000
TimeoutInterval5000
KeepAliveTimeout30000
MutexTimeout5000
LanTimeout2500
WanTimeout8000
BufferSize65535
MaxPacketSize10485760
GCThreshold10485760
UseCustomDnsServerTrue
PrimaryDnsServer8.8.8.8
BackupDnsServer8.8.4.4
Total processes
81
Monitored processes
34
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | attrib "C:\Users\admin\Desktop\Order Reqest Details 2023 Jbc.exe" +s +h | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 600 | "C:\Users\admin\Desktop\Order Reqest Details 2023 Jbc.exe" | C:\Users\admin\Desktop\Order Reqest Details 2023 Jbc.exe | explorer.exe | ||||||||||||
User: admin Company: Hewlett-Packard Integrity Level: HIGH Description: BeeTrial Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1480 | "C:\Users\admin\AppData\Local\Temp\NEW STUB.EXE" | C:\Users\admin\AppData\Local\Temp\NEW STUB.EXE | Order Reqest Details 2023 Jbc.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
Nanocore(PID) Process(1480) NEW STUB.EXE KeyboardLoggingTrue BuildTime2021-04-18 18:21:52.193672 Version1.2.2.0 Mutex94803e62-45dd-47d9-9960-20dd767ecae3 DefaultGroupAPILA 2021 PrimaryConnectionHosttony3311.ddns.net BackupConnectionHosttony3311.ddns.net ConnectionPort10108 RunOnStartupTrue RequestElevationFalse BypassUserAccountControlFalse ClearZoneIdentifierTrue ClearAccessControlTrue SetCriticalProcessFalse PreventSystemSleepTrue ActivateAwayModeFalse EnableDebugModeFalse RunDelay0 ConnectDelay4000 RestartDelay5000 TimeoutInterval5000 KeepAliveTimeout30000 MutexTimeout5000 LanTimeout2500 WanTimeout8000 BufferSize65535 MaxPacketSize10485760 GCThreshold10485760 UseCustomDnsServerTrue PrimaryDnsServer8.8.8.8 BackupDnsServer8.8.4.4 | |||||||||||||||
| 1496 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\DsgRewOasQTpD" /XML "C:\Users\admin\AppData\Local\Temp\tmpCC5.tmp" | C:\Windows\System32\schtasks.exe | — | Order Reqest Details 2023 Jbc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1532 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking "https://vtsamples.commondatastorage.googleapis.com/7a6ceb6ace388bfb6c1698a723df98ec107e7043e955d64b03fba81cb65627db?GoogleAccessId=758681729565-rc7fgq07icj8c9dm2gi34a4cckv235v1@developer.gserviceaccount.com&Expires=1690225636&Signature=dJywbNr3dJzVEzT6nIe91Lo7btBRsqqdaEqPOiala5wyCtFA%2F6OIfUJ202LRpaRfnsJvphpONFnw%0AExLTG2uB260PEpLWItZPFOSl5mO3KBzQqaNu%2BUVHQEOeQgFpqcVtlzfeR5mb5ZnMFVEJUJs3F%2Fba%0A%2FaJhjIU7bMAvNnsLwv19PBrboSWLr0dABoXQ%2BukTGqmj5NFcGWIMIQCPrJ%2BhtiEX26SRIUbgu%2BqA%0AXuvQ2Bk4Q1EJjmaOYosjopDeJXOzmYxS9ov0By1h3WgmZ72jCIai4VGRrlWxvUFS3YA%2FORfaz%2BGN%0AErra1z8e%2Brp%2BHoTSxzzoAdJ5pqSlONgHC%2Bc33Q%3D%3D&response-content-disposition=attachment%3B%20filename%3D%227a6ceb6ace388bfb6c1698a723df98ec107e7043e955d64b03fba81cb65627db%22&response-content-type=application%2Foctet-stream;" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
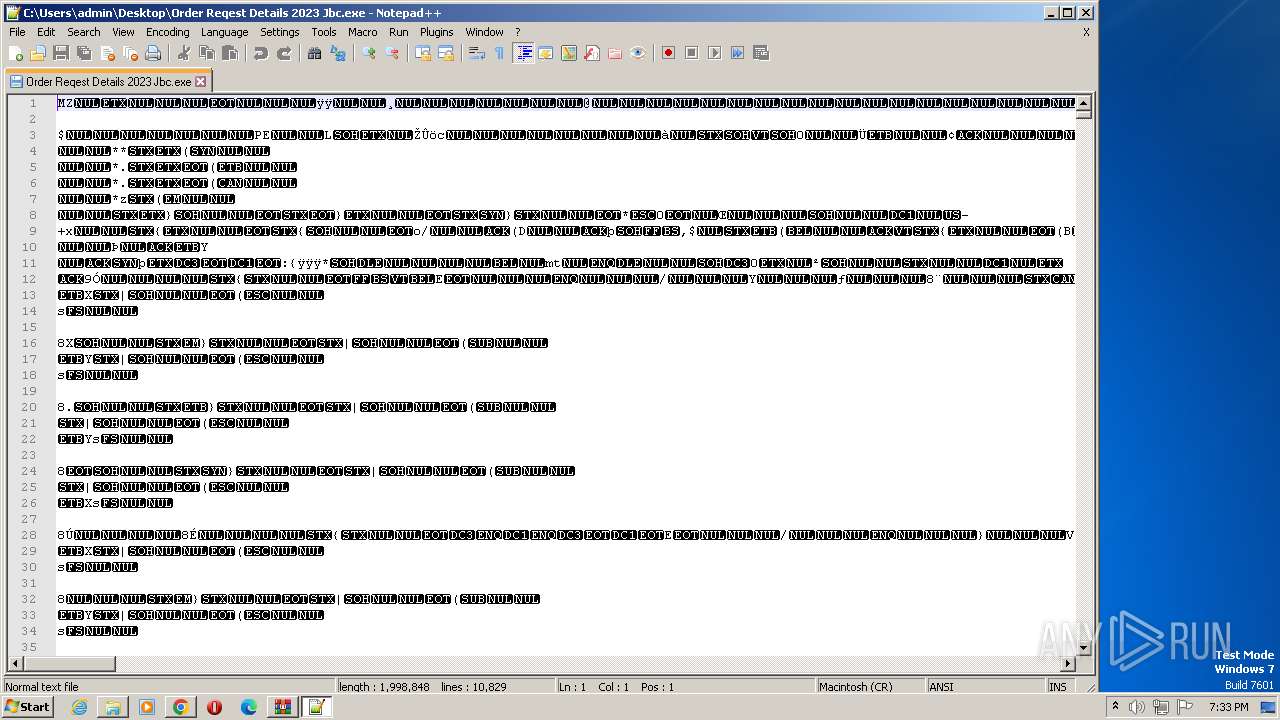
| 1616 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\Order Reqest Details 2023 Jbc.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 1836 | "C:\Users\admin\Documents\MSDCSC\msdcsc.exe" | C:\Users\admin\Documents\MSDCSC\msdcsc.exe | — | msdcsc.exe | |||||||||||
User: admin Company: Hewlett-Packard Integrity Level: MEDIUM Description: BeeTrial Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3448 --field-trial-handle=1176,i,17033238403367282551,17601205735516064256,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2180 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\DsgRewOasQTpD" /XML "C:\Users\admin\AppData\Local\Temp\tmp76DE.tmp" | C:\Windows\System32\schtasks.exe | — | Order Reqest Details 2023 Jbc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2260 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=1996 --field-trial-handle=1176,i,17033238403367282551,17601205735516064256,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
9 323
Read events
9 122
Write events
201
Delete events
0
Modification events
| (PID) Process: | (1532) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1532) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1532) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1532) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1532) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1532) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (1532) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1532) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1532) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (1532) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
5
Suspicious files
27
Text files
48
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1096c3.TMP | — | |
MD5:— | SHA256:— | |||
| 1532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 1532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old~RF10a77d.TMP | — | |
MD5:— | SHA256:— | |||
| 1532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\802d4c7b-5e1d-45f2-beb0-b03fde4d4c56.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 1532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF1096c3.TMP | text | |
MD5:C214500EDB0B5F56B9D3D27B32964AB2 | SHA256:6254FD03CFC08A142D6AEB8C037D25D42564C0CC6F294A3716DF19FDF254EBCE | |||
| 1532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF1097dd.TMP | text | |
MD5:74174B4F8AEB3CFDC18745625ED7865C | SHA256:419223BAED85740D27E427C390FDCA869AE1F4089A8415DE13CC4305F6907FDF | |||
| 1532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:D5C9ECBD2DCA29D89266782824D7AF99 | SHA256:D22D1243ACC064A30823180D0E583C853E9395367C78C2AD9DE59A463904F702 | |||
| 1532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:561161B0FF5BCA89BF47F8AC972A7499 | SHA256:ECCA5CCFA0BEED7581B39FCE03D0FD3B694DF0F92BFFF780F702118AD51FC17D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
167
DNS requests
32
Threats
11
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2720 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1532 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3340 | chrome.exe | 142.250.184.205:443 | accounts.google.com | GOOGLE | US | whitelisted |
3340 | chrome.exe | 216.58.206.48:443 | vtsamples.commondatastorage.googleapis.com | GOOGLE | US | whitelisted |
1532 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
3340 | chrome.exe | 142.250.186.106:443 | optimizationguide-pa.googleapis.com | — | — | whitelisted |
3340 | chrome.exe | 172.217.18.106:443 | optimizationguide-pa.googleapis.com | GOOGLE | US | whitelisted |
3340 | chrome.exe | 142.250.185.164:443 | www.google.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
vtsamples.commondatastorage.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| malicious |
optimizationguide-pa.googleapis.com |
| whitelisted |
dns.msftncsi.com |
| shared |
www.googleapis.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgedl.me.gvt1.com |
| whitelisted |
clients1.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1480 | NEW STUB.EXE | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
1480 | NEW STUB.EXE | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
1480 | NEW STUB.EXE | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
1480 | NEW STUB.EXE | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
1480 | NEW STUB.EXE | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
1084 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
1480 | NEW STUB.EXE | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
1480 | NEW STUB.EXE | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
1480 | NEW STUB.EXE | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
1084 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|