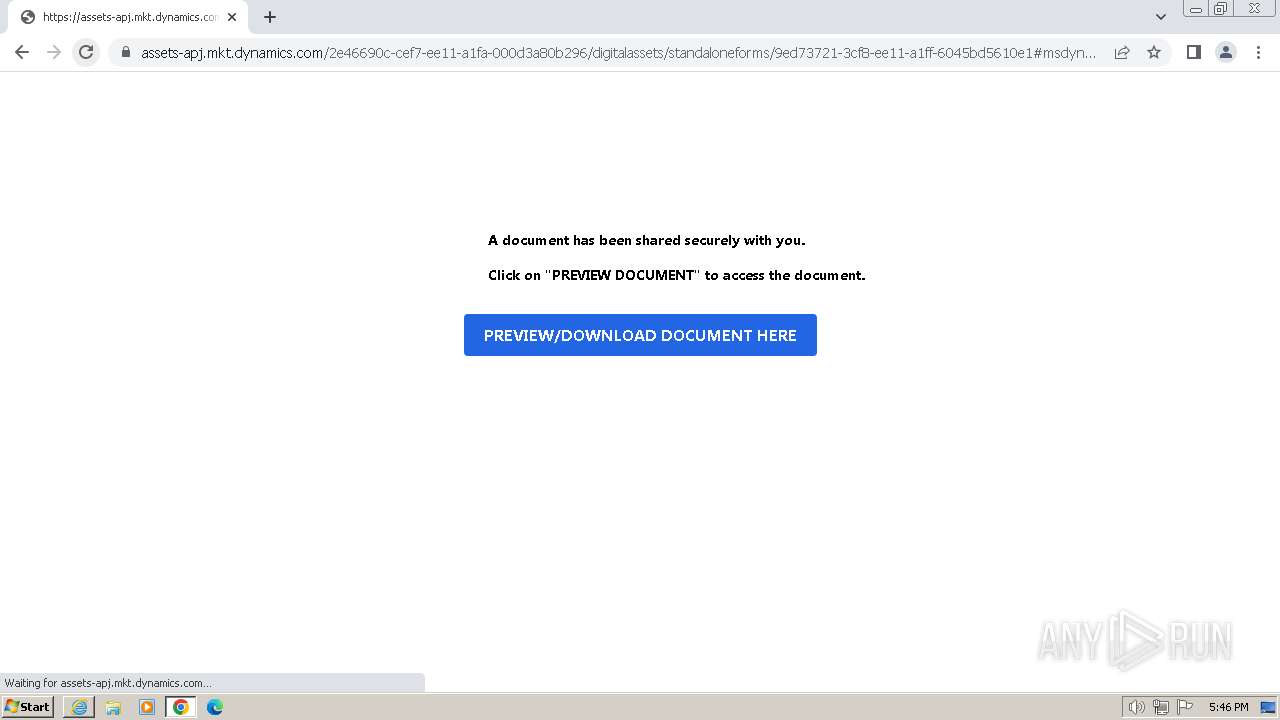
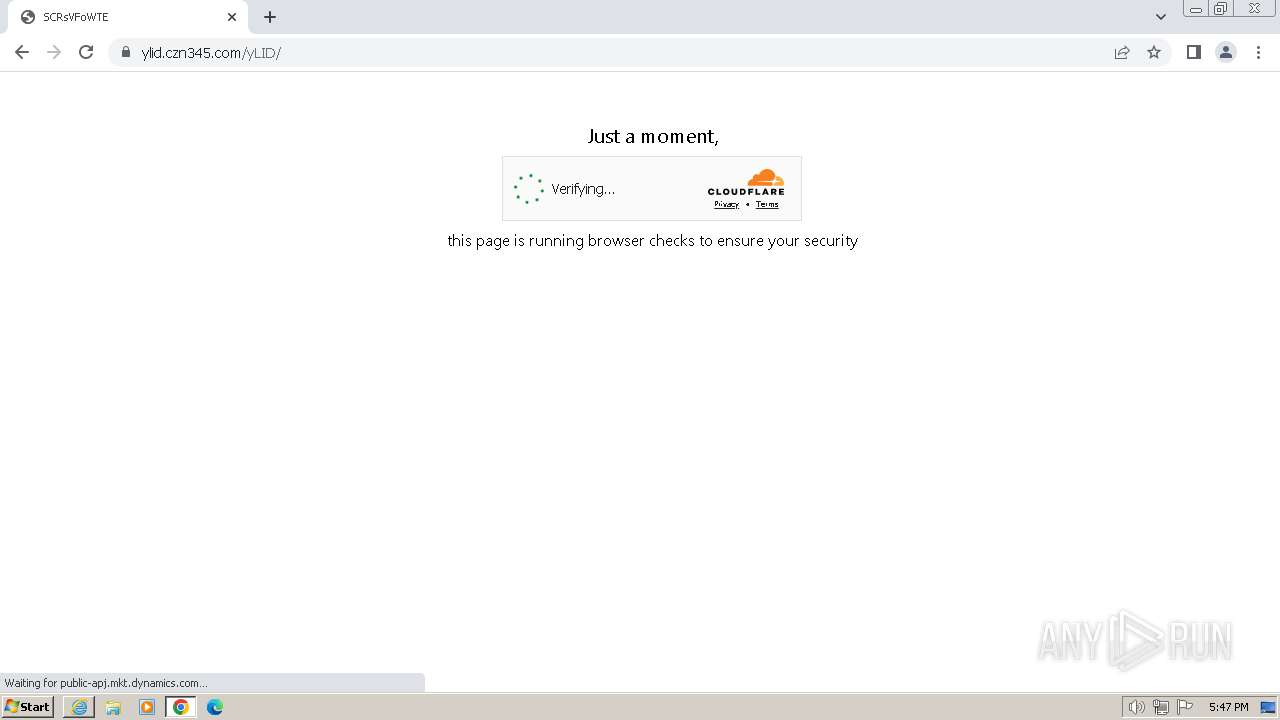
| URL: | https://public-apj.mkt.dynamics.com/api/orgs/2e46690c-cef7-ee11-a1fa-000d3a80b296/r/n2LyedAw906ftVp2sXt9gQEAAAA?target=%7B%22TargetUrl%22%3A%22https%253A%252F%252Fassets-apj.mkt.dynamics.com%252F2e46690c-cef7-ee11-a1fa-000d3a80b296%252Fdigitalassets%252Fstandaloneforms%252F9ed73721-3cf8-ee11-a1ff-6045bd5610e1%22%2C%22RedirectOptions%22%3A%7B%221%22%3Anull%7D%7D&digest=J3pkRAkMhMO1a1wx1xs2WnFwPh3LgDHhHiqnnzGZV2Q%3D&secretVersion=428ce0e26eb34577a188eae4c4f47844 |
| Full analysis: | https://app.any.run/tasks/0146c9a4-060a-4d6c-9c17-49930d54fba5 |
| Verdict: | Malicious activity |
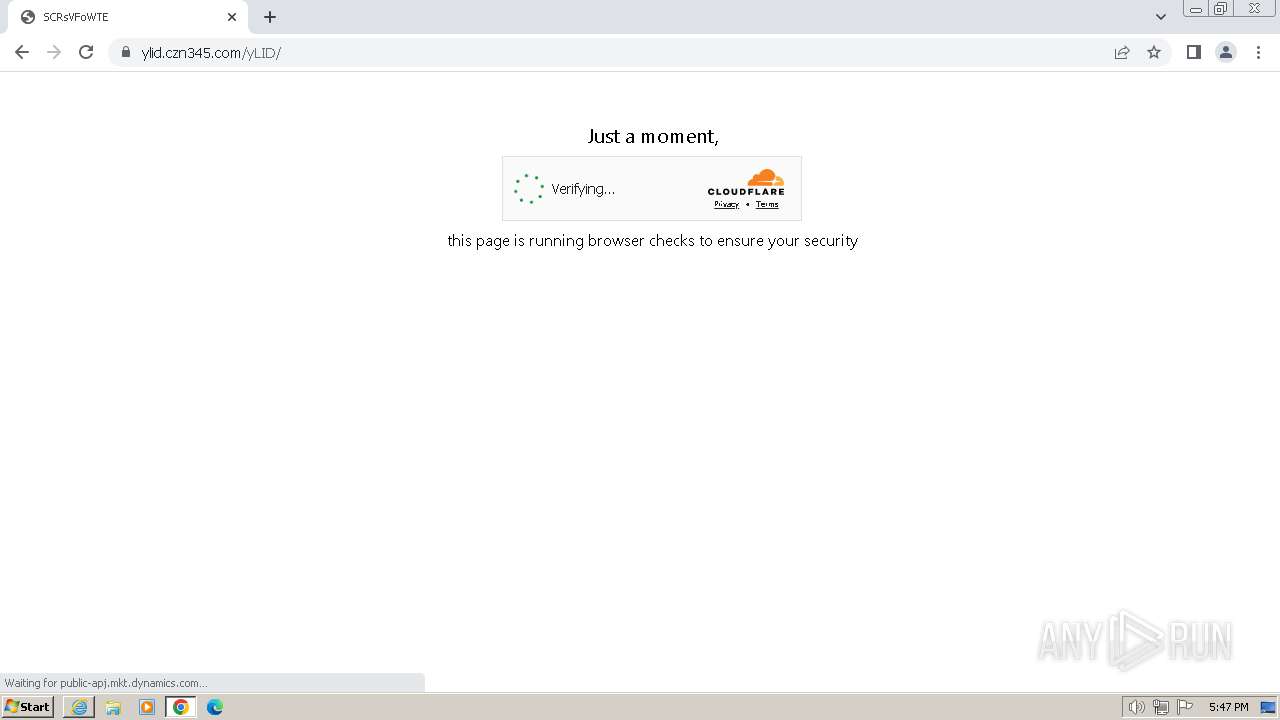
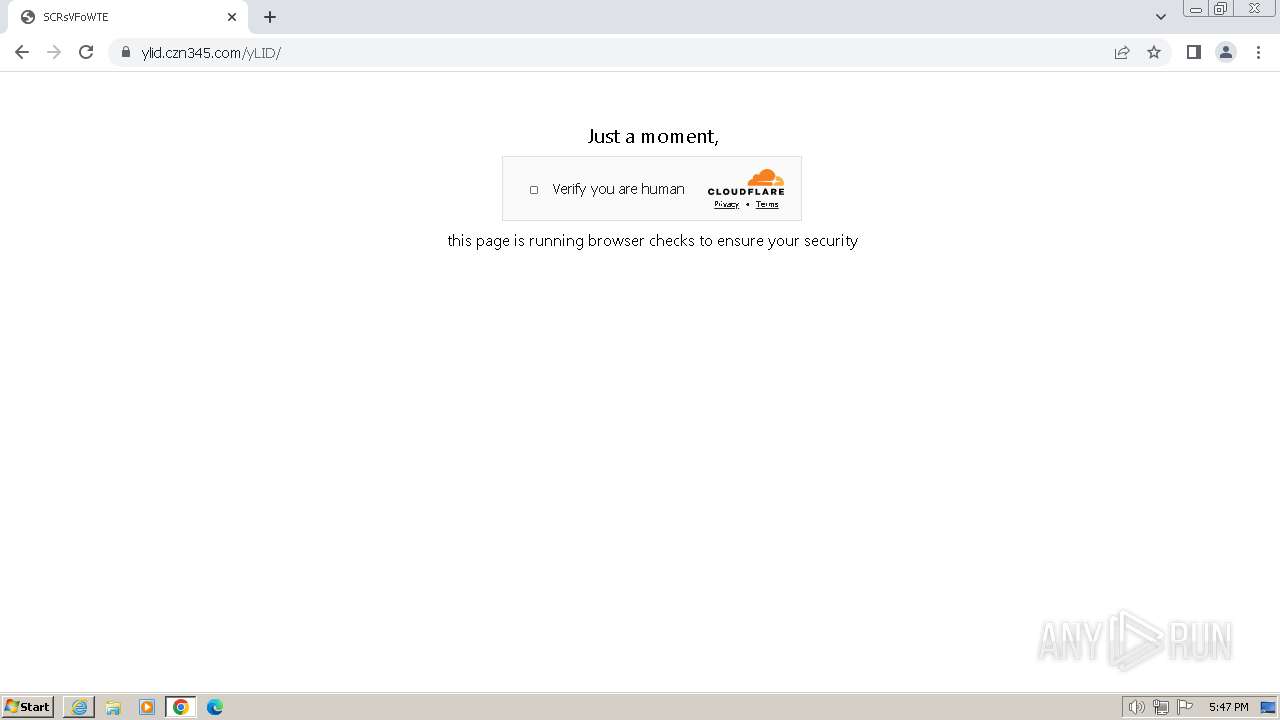
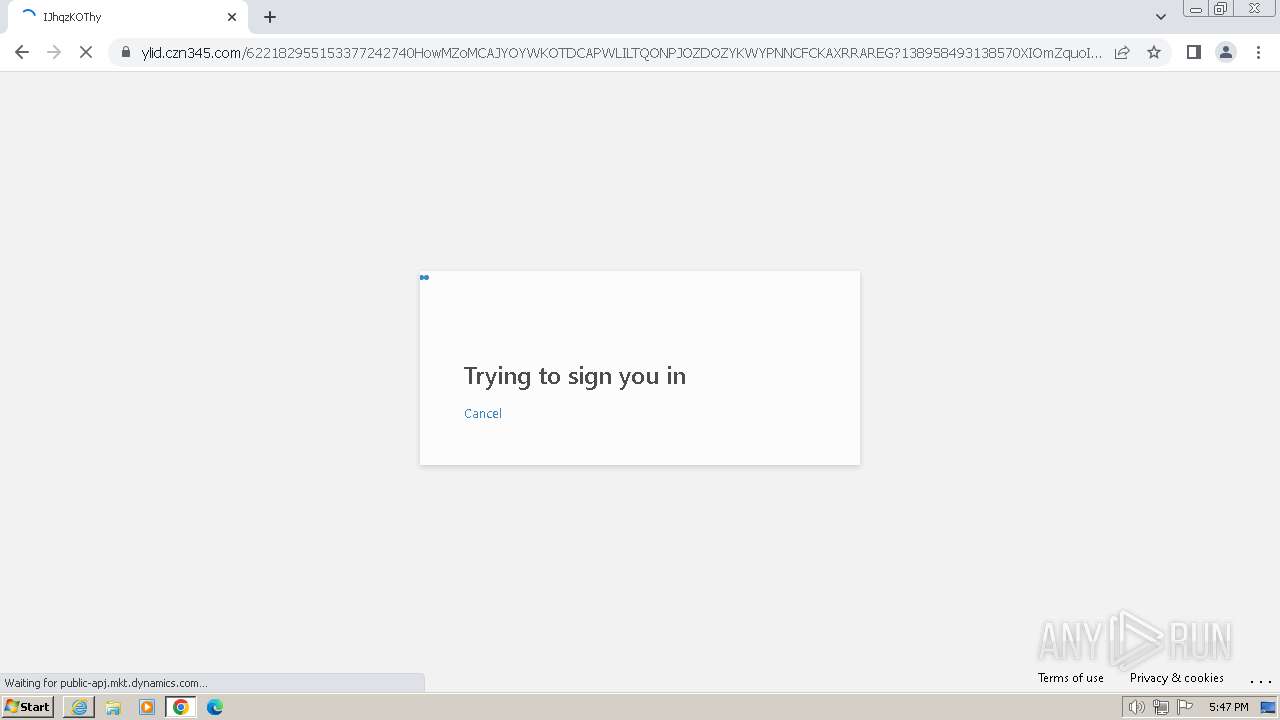
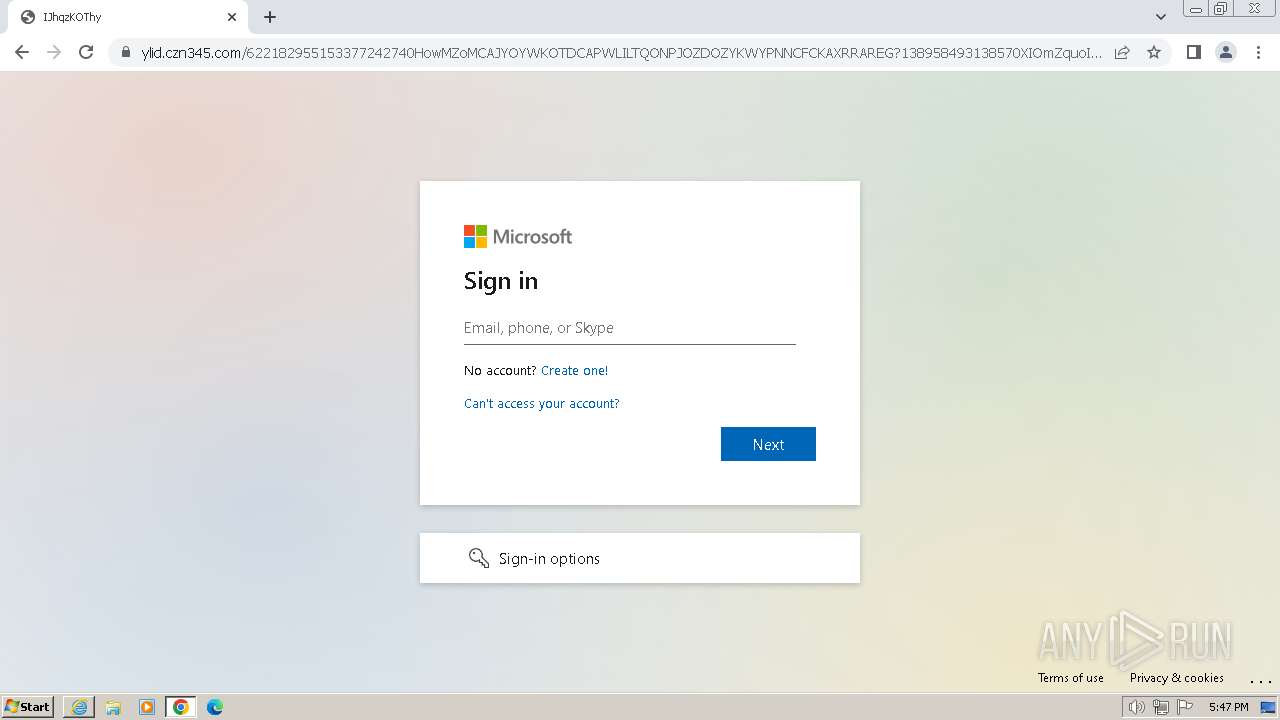
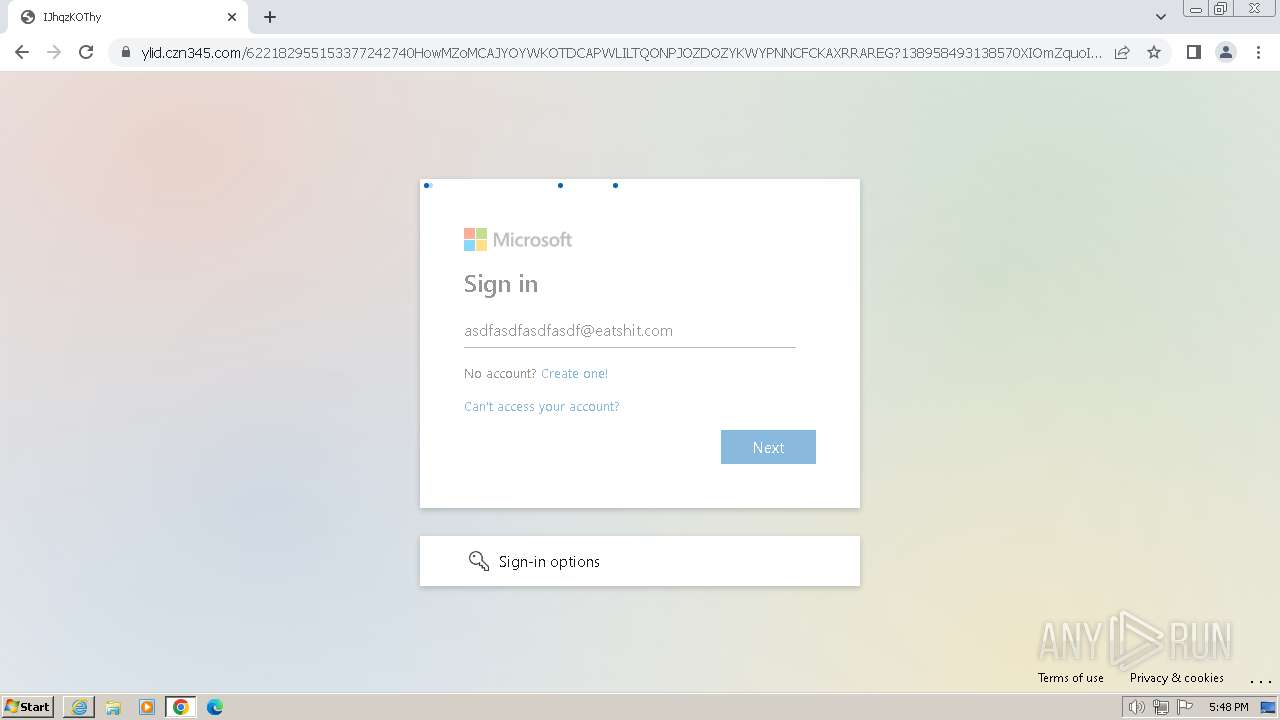
| Threats: | Tycoon 2FA is a phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) protections, particularly targeting Microsoft 365 and Gmail accounts. Its advanced evasion techniques and modular architecture make it a significant threat to organizations relying on MFA for security. |
| Analysis date: | April 15, 2024, 16:43:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | DF98C781D34F43F06555DDB6B7E77CA7 |
| SHA1: | 9D9A70DAAD623762963D4B055F88B3BBD31842E6 |
| SHA256: | DDAC6D5150D4DB432ECB5CED7713C00799B702D9F5ECBA27BC29685368C7C388 |
| SSDEEP: | 12:2UQKS0BgcEwJDDQIbINAbYC1QXcIsJ6slJA0WAmX7No:25UBqWVbINAGxo8vAmXu |
MALICIOUS
PHISHING has been detected (SURICATA)
- chrome.exe (PID: 392)
SUSPICIOUS
No suspicious indicators.INFO
Drops the executable file immediately after the start
- chrome.exe (PID: 3168)
Application launched itself
- iexplore.exe (PID: 2424)
- chrome.exe (PID: 668)
Manual execution by a user
- chrome.exe (PID: 668)
Executable content was dropped or overwritten
- chrome.exe (PID: 3168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
61
Monitored processes
23
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1324 --field-trial-handle=1156,i,13497143000892721957,7874057946996770877,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 532 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=2336 --field-trial-handle=1156,i,13497143000892721957,7874057946996770877,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1536 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6ba38b38,0x6ba38b48,0x6ba38b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=3704 --field-trial-handle=1156,i,13497143000892721957,7874057946996770877,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3680 --field-trial-handle=1156,i,13497143000892721957,7874057946996770877,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=2400 --field-trial-handle=1156,i,13497143000892721957,7874057946996770877,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1604 --field-trial-handle=1156,i,13497143000892721957,7874057946996770877,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2424 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://public-apj.mkt.dynamics.com/api/orgs/2e46690c-cef7-ee11-a1fa-000d3a80b296/r/n2LyedAw906ftVp2sXt9gQEAAAA?target=%7B%22TargetUrl%22%3A%22https%253A%252F%252Fassets-apj.mkt.dynamics.com%252F2e46690c-cef7-ee11-a1fa-000d3a80b296%252Fdigitalassets%252Fstandaloneforms%252F9ed73721-3cf8-ee11-a1ff-6045bd5610e1%22%2C%22RedirectOptions%22%3A%7B%221%22%3Anull%7D%7D&digest=J3pkRAkMhMO1a1wx1xs2WnFwPh3LgDHhHiqnnzGZV2Q%3D&secretVersion=428ce0e26eb34577a188eae4c4f47844" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=1356 --field-trial-handle=1156,i,13497143000892721957,7874057946996770877,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
27 451
Read events
27 270
Write events
152
Delete events
29
Modification events
| (PID) Process: | (2424) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2424) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 107384224 | |||
| (PID) Process: | (2424) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31100756 | |||
| (PID) Process: | (2424) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 407547974 | |||
| (PID) Process: | (2424) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31100756 | |||
| (PID) Process: | (2424) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2424) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2424) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2424) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2424) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
2
Suspicious files
69
Text files
70
Unknown types
45
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | der | |
MD5:— | SHA256:— | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:— | SHA256:— | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C389FD106AACA95B265CC81A85B3522B_4C7284B2478F06E434116143959923F9 | der | |
MD5:— | SHA256:— | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C389FD106AACA95B265CC81A85B3522B_4C7284B2478F06E434116143959923F9 | binary | |
MD5:— | SHA256:— | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:— | SHA256:— | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:— | SHA256:— | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\093CB42092635CBCBD1EEE777DF944DC_2EAA5A7F9C8F8D630B44F18B72794658 | der | |
MD5:— | SHA256:— | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\093CB42092635CBCBD1EEE777DF944DC_2EAA5A7F9C8F8D630B44F18B72794658 | binary | |
MD5:— | SHA256:— | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\9ed73721-3cf8-ee11-a1ff-6045bd5610e1[1].htm | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
66
DNS requests
73
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3232 | iexplore.exe | GET | 304 | 41.63.96.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7b7527f693947e4b | unknown | — | — | unknown |
3232 | iexplore.exe | GET | 304 | 41.63.96.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ca377ab81dff1b41 | unknown | — | — | unknown |
3232 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
3232 | iexplore.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSzT%2FzqwcqNvhP9i4c4sCPz2JbzrAQU%2FglxQFUFEETYpIF1uJ4a6UoGiMgCEzMAJ7rynDxpUj4N5NgAAAAnuvI%3D | unknown | — | — | unknown |
3232 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | unknown |
3232 | iexplore.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBQbxmMY0ZtiFXXusCt0ac1S1Zoq4gQU9n4vvYCjSrJwW%2Bvfmh%2FY7cphgAcCEzMAJYcelTQYvrg%2B1LwAAAAlhx4%3D | unknown | — | — | unknown |
2424 | iexplore.exe | GET | 304 | 41.63.96.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7750f9b3ceea0670 | unknown | — | — | unknown |
3232 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
2424 | iexplore.exe | GET | 304 | 41.63.96.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?21c931e033ae0961 | unknown | — | — | unknown |
2424 | iexplore.exe | GET | 304 | 41.63.96.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?2e8cddc0ef9c43e8 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
3232 | iexplore.exe | 20.195.84.128:443 | public-apj.mkt.dynamics.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3232 | iexplore.exe | 41.63.96.128:80 | ctldl.windowsupdate.com | LLNW | ZA | unknown |
3232 | iexplore.exe | 41.63.96.0:80 | ctldl.windowsupdate.com | LLNW | ZA | unknown |
3232 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3232 | iexplore.exe | 204.79.197.203:80 | oneocsp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3232 | iexplore.exe | 13.107.213.45:443 | assets-apj.mkt.dynamics.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
public-apj.mkt.dynamics.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
oneocsp.microsoft.com |
| whitelisted |
assets-apj.mkt.dynamics.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
cxppusa1formui01cdnsa01-endpoint.azureedge.net |
| malicious |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
392 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
392 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
392 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
392 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
392 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Client-Server Socket.IO CDN communication (cdn.socket .io) |
392 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Phishing domain chain detected (Tycoon 2FA) |
392 | chrome.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup Domain (ipapi .co in DNS lookup) |
392 | chrome.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup Domain (ipapi .co in DNS lookup) |