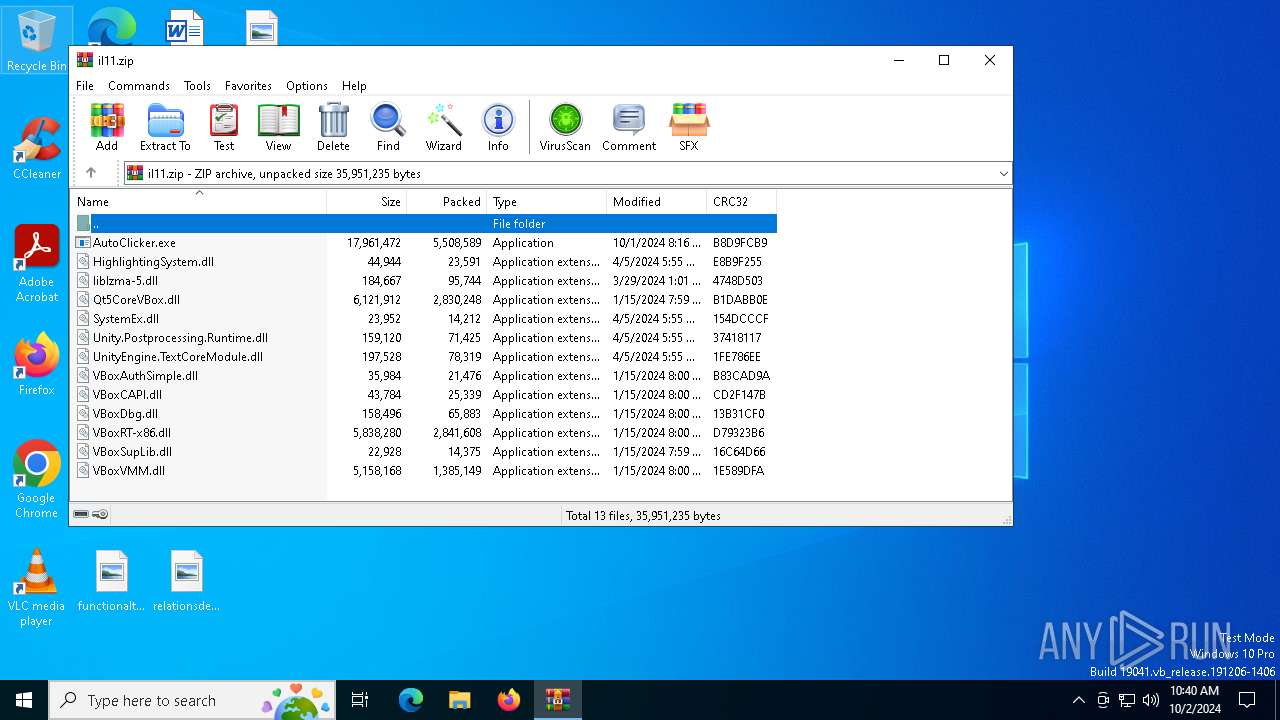
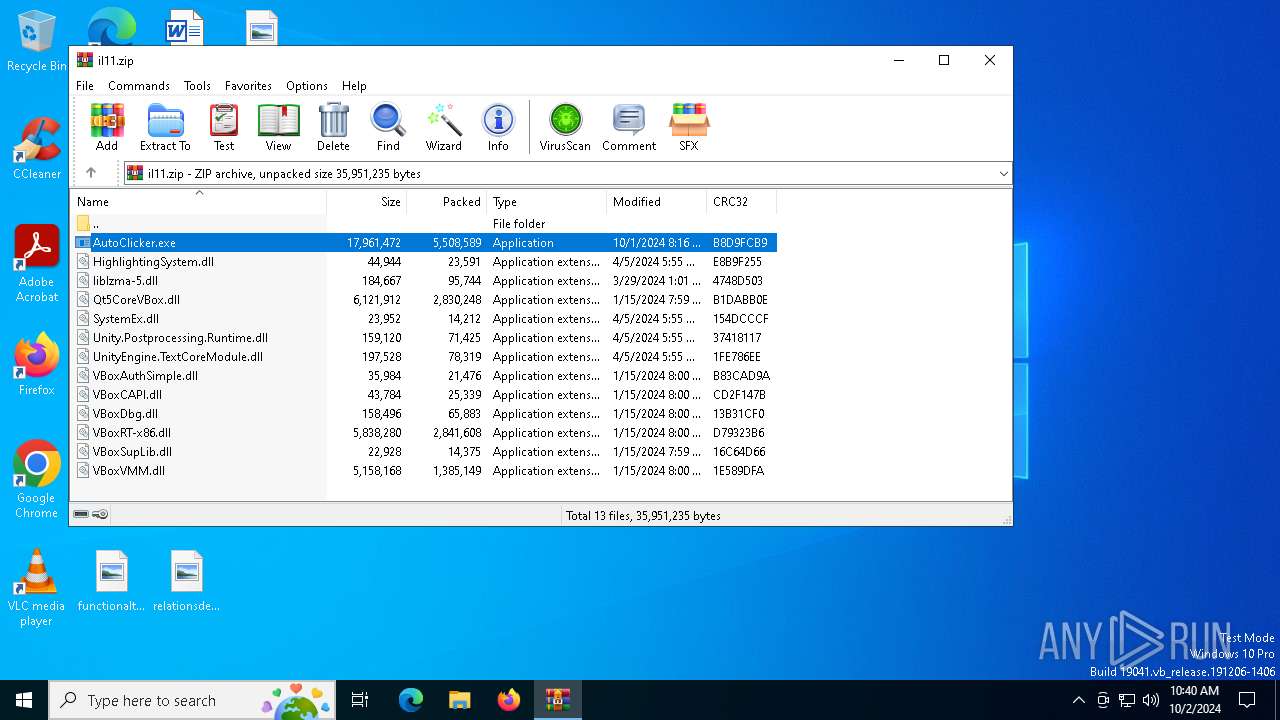
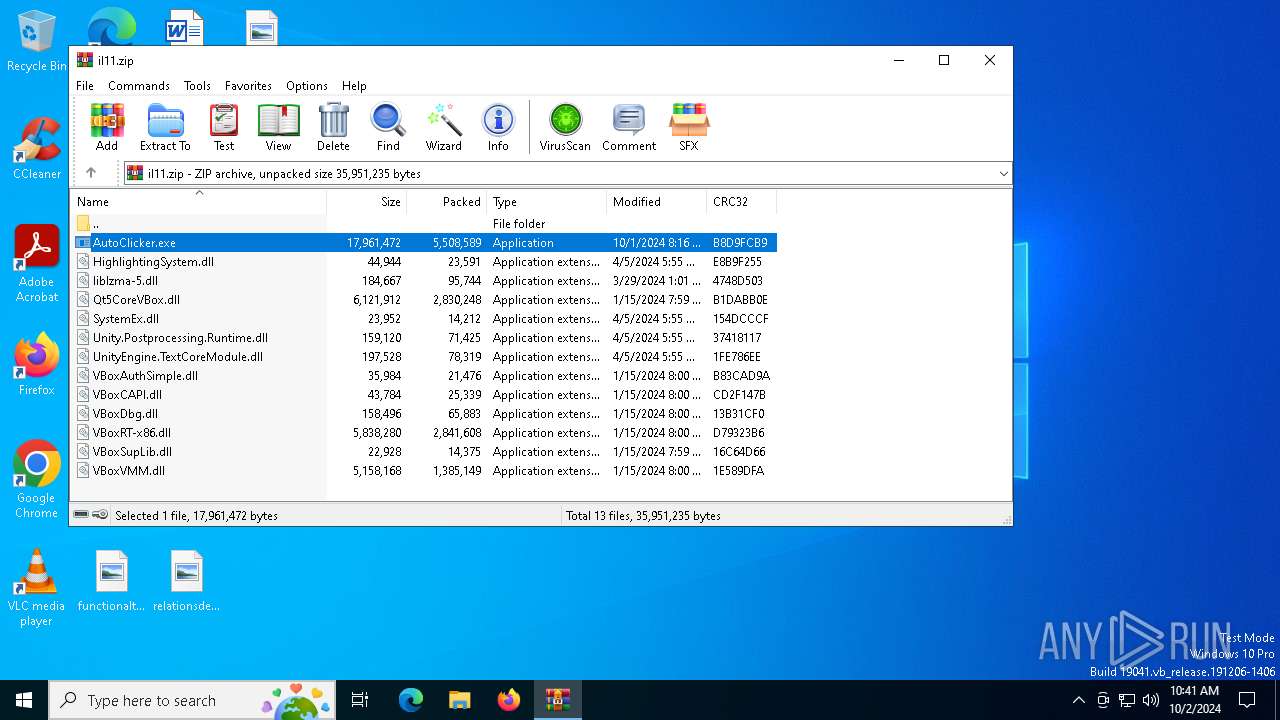
| File name: | il11.zip |
| Full analysis: | https://app.any.run/tasks/720d0627-744d-4019-a66a-f5c42f180631 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | October 02, 2024, 10:40:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | FC76127E2E452F6AB4EF59F87D983E60 |
| SHA1: | 6DAE84107BB8156EC206846262815269714BABF9 |
| SHA256: | DCC77D65AEB1FA9C17B0989F2205FBC10CE9D34D46C43DA0B83B7E2A2DA895AA |
| SSDEEP: | 98304:2QhdsFAj9eGdzMCZ2DesuzZ9UH8V0zVjCHR83QZZRBQlsApD+K4MtMKdch+OaKMG:Zo9nEA3zhIzQsyLRmDoyGEBqjFWWW |
MALICIOUS
Stealers network behavior
- BitLockerToGo.exe (PID: 5164)
LUMMA has been detected (SURICATA)
- BitLockerToGo.exe (PID: 5164)
Actions looks like stealing of personal data
- BitLockerToGo.exe (PID: 5164)
LUMMA has been detected (YARA)
- BitLockerToGo.exe (PID: 5164)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3316)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 3316)
INFO
Checks supported languages
- BitLockerToGo.exe (PID: 5164)
- AutoClicker.exe (PID: 3920)
Reads the software policy settings
- BitLockerToGo.exe (PID: 5164)
Reads the computer name
- BitLockerToGo.exe (PID: 5164)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3316)
The process uses the downloaded file
- WinRAR.exe (PID: 3316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(5164) BitLockerToGo.exe
C2 (9)agentyanlark.site
delaylacedmn.site
famikyjdiag.site
writekdmsnu.site
bellykmrebk.site
fallydisablek.site
underlinemdsj.site
possiwreeste.site
commandejorsk.site
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:04:05 22:55:22 |
| ZipCRC: | 0x1fe786ee |
| ZipCompressedSize: | 78319 |
| ZipUncompressedSize: | 197528 |
| ZipFileName: | UnityEngine.TextCoreModule.dll |
Total processes
129
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3316 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\il11.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3920 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3316.47005\AutoClicker.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3316.47005\AutoClicker.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: OP Auto Clicker Exit code: 666 Version: 4.0 Modules
| |||||||||||||||
| 5164 | "C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe" | C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe | AutoClicker.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BitLocker To Go Reader Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
Lumma(PID) Process(5164) BitLockerToGo.exe C2 (9)agentyanlark.site delaylacedmn.site famikyjdiag.site writekdmsnu.site bellykmrebk.site fallydisablek.site underlinemdsj.site possiwreeste.site commandejorsk.site | |||||||||||||||
Total events
3 389
Read events
3 383
Write events
6
Delete events
0
Modification events
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\il11.zip | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
13
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3316.47005\UnityEngine.TextCoreModule.dll | executable | |
MD5:2D22F420CBB3D8488C1D1FBC5E44AF2C | SHA256:AF5DDC2EA31739CD991B604D397CA35A9B6875782F5073CD01323B99091D9A06 | |||
| 3316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3316.47005\AutoClicker.exe | executable | |
MD5:0411FB81A250A998EEA8B44E76B04FA9 | SHA256:107FAB209E5C7DF24F25F1FE143CDAF294BF1F3EE40CAF8E5F8D5911FAD36332 | |||
| 3316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3316.47005\VBoxAuthSimple.dll | executable | |
MD5:C9E36A1B0F08CFFCAC148E5ED38644F5 | SHA256:77705AD4125E40691E6182FE22A67241FD5AAD3254FA8D39ED42ADC8B4D704C0 | |||
| 3316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3316.47005\SystemEx.dll | executable | |
MD5:FBA0FC7EC66D149D2096AB7032F751C5 | SHA256:A78C4D08C6726E1E560C3A47436C631847423CAB95032D02CCD4E10F92E6D937 | |||
| 3316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3316.47005\VBoxRT-x86.dll | executable | |
MD5:88C1CB4E7078FE246F08C0D00C265346 | SHA256:A3A43521433AD0FE1DCEC57C7E72C449626DEF4F71AD949F83B91E051456F83C | |||
| 3316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3316.47005\HighlightingSystem.dll | executable | |
MD5:88515E9DDFD6A8973BC511856DBFDDE3 | SHA256:E4EA835DE0509C0F0EC1E2D2F5FFF41AA9F85C393010918878D9F4D6C4732D6B | |||
| 3316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3316.47005\Unity.Postprocessing.Runtime.dll | executable | |
MD5:7B8E880171D8DA576DE2ACA1876F9F19 | SHA256:2F008162BC30642099F6083C60AA1A6BB39B6AB60A64D15BDA9A0F30216DFA47 | |||
| 3316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3316.47005\Qt5CoreVBox.dll | executable | |
MD5:289FFDA30516019935321C48BD4F879C | SHA256:28D7665BE8FF659B533FCEB5F337C633745C137626495E6F3F96A63E944D4D41 | |||
| 3316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3316.47005\VBoxVMM.dll | executable | |
MD5:DBFCDD86BDA68AB53D8B50329EF713F5 | SHA256:DDEBDB740915CDB367C3ADF61D62F7B9CF1C7535CC8EDBB7D80C9B8ADD055AFA | |||
| 3316 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3316.47005\liblzma-5.dll | executable | |
MD5:7208D242E5BCE19E669BE0744D03A2F0 | SHA256:E5B17C53A932497F0994881B87A55381A282D0BAB2E3BD41933B308FC7127F78 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
52
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1404 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2060 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2060 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1940 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5388 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5388 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1404 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1404 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
fallydisablek.site |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5164 | BitLockerToGo.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |