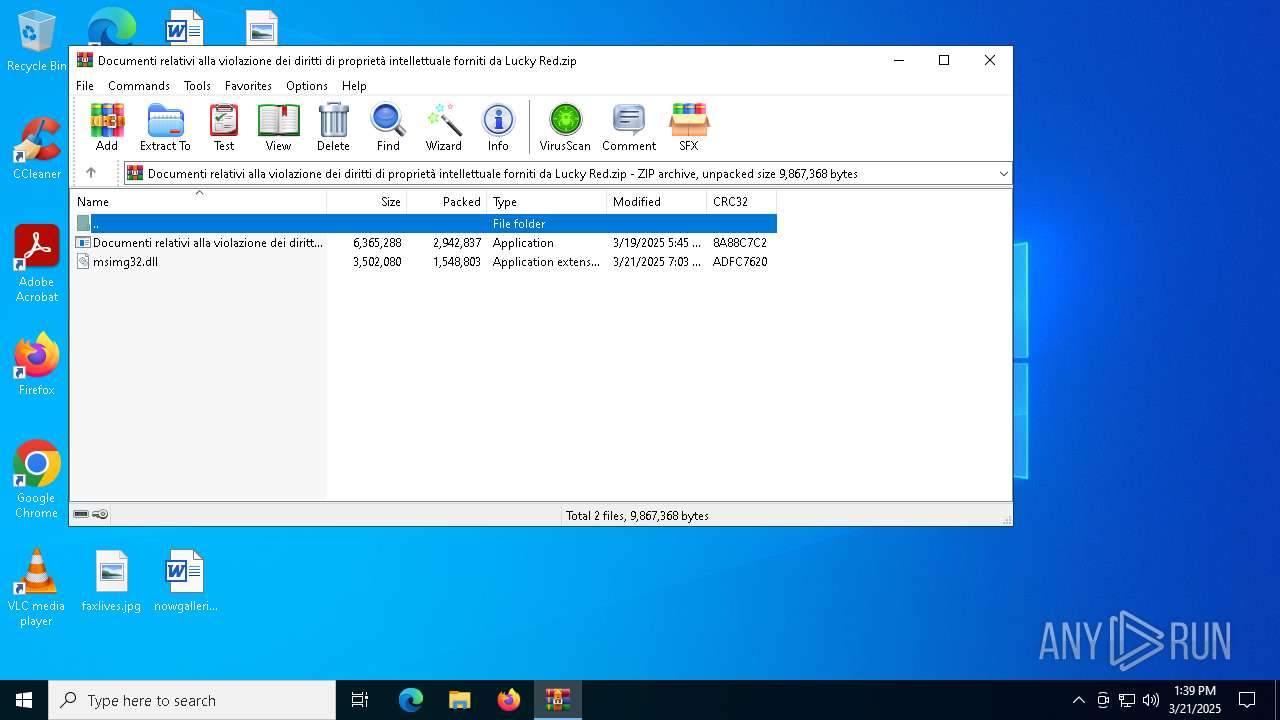
| File name: | Documenti relativi alla violazione dei diritti di proprietà intellettuale forniti da Lucky Red.zip |
| Full analysis: | https://app.any.run/tasks/e3899528-c676-4b4b-b12f-677e1c672fa0 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | March 21, 2025, 13:38:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 77C458B8883EF894ECE7510CB76A700C |
| SHA1: | 7AC59B9A483C7BA6B65FA823360E0375B87DFB5B |
| SHA256: | DC44419581FA7664610356D21877865C6D9C9992F779077DC15E3491966F0E91 |
| SSDEEP: | 98304:BtI5r6chRncVx3xhD5sBfPk5LOUHJMILOE5uIha1vCAySi/5iXlhb6Xj3ZOjs0l6:8cJTNpNufQ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7400)
RHADAMANTHYS mutex has been found
- Documenti relativi alla violazione dei diritti di proprietà intellettuale forniti da Lucky Red.exe (PID: 2320)
- svchost.exe (PID: 7208)
Actions looks like stealing of personal data
- chrome.exe (PID: 7900)
- msedge.exe (PID: 8028)
- csc.exe (PID: 1180)
RHADAMANTHYS has been detected (YARA)
- svchost.exe (PID: 5112)
Steals credentials from Web Browsers
- msedge.exe (PID: 8028)
Scans artifacts that could help determine the target
- msedge.exe (PID: 8028)
RHADAMANTHYS has been detected (SURICATA)
- svchost.exe (PID: 5112)
Starts Visual C# compiler
- @0z8p1kE.exe (PID: 3620)
PUREHVNC has been detected (YARA)
- csc.exe (PID: 1180)
ASYNCRAT has been detected (SURICATA)
- csc.exe (PID: 1180)
SUSPICIOUS
Application launched itself
- Documenti relativi alla violazione dei diritti di proprietà intellettuale forniti da Lucky Red.exe (PID: 6744)
- chrome.exe (PID: 7900)
- msedge.exe (PID: 8028)
There is functionality for taking screenshot (YARA)
- Documenti relativi alla violazione dei diritti di proprietà intellettuale forniti da Lucky Red.exe (PID: 6744)
The process checks if it is being run in the virtual environment
- svchost.exe (PID: 7208)
Connects to unusual port
- svchost.exe (PID: 7208)
- svchost.exe (PID: 5112)
- csc.exe (PID: 1180)
Executes application which crashes
- Documenti relativi alla violazione dei diritti di proprietà intellettuale forniti da Lucky Red.exe (PID: 2320)
- @0z8p1kE.exe (PID: 3620)
Multiple wallet extension IDs have been found
- svchost.exe (PID: 5112)
- csc.exe (PID: 1180)
Reads Mozilla Firefox installation path
- msedge.exe (PID: 8028)
Reads security settings of Internet Explorer
- msedge.exe (PID: 8028)
Loads DLL from Mozilla Firefox
- svchost.exe (PID: 5112)
Executable content was dropped or overwritten
- svchost.exe (PID: 5112)
- wmlaunch.exe (PID: 864)
Searches for installed software
- svchost.exe (PID: 5112)
Contacting a server suspected of hosting an CnC
- csc.exe (PID: 1180)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7400)
The sample compiled with english language support
- WinRAR.exe (PID: 7400)
- wmlaunch.exe (PID: 864)
- svchost.exe (PID: 5112)
Manual execution by a user
- Documenti relativi alla violazione dei diritti di proprietà intellettuale forniti da Lucky Red.exe (PID: 6744)
- svchost.exe (PID: 7208)
- svchost.exe (PID: 5112)
- notepad.exe (PID: 5324)
Checks supported languages
- Documenti relativi alla violazione dei diritti di proprietà intellettuale forniti da Lucky Red.exe (PID: 6744)
- Documenti relativi alla violazione dei diritti di proprietà intellettuale forniti da Lucky Red.exe (PID: 2320)
- msedge.exe (PID: 8028)
- chrome.exe (PID: 7900)
- wmlaunch.exe (PID: 864)
- @0z8p1kE.exe (PID: 3620)
- csc.exe (PID: 1180)
Reads the computer name
- chrome.exe (PID: 7900)
- msedge.exe (PID: 8028)
- wmlaunch.exe (PID: 864)
- csc.exe (PID: 1180)
Create files in a temporary directory
- svchost.exe (PID: 5112)
- chrome.exe (PID: 7900)
- msedge.exe (PID: 8028)
Reads Environment values
- chrome.exe (PID: 7900)
- msedge.exe (PID: 8028)
Process checks computer location settings
- chrome.exe (PID: 7900)
- msedge.exe (PID: 8028)
Process checks whether UAC notifications are on
- msedge.exe (PID: 8028)
Reads the machine GUID from the registry
- msedge.exe (PID: 8028)
- chrome.exe (PID: 7900)
- wmlaunch.exe (PID: 864)
- csc.exe (PID: 1180)
Checks proxy server information
- msedge.exe (PID: 8028)
- chrome.exe (PID: 7900)
- slui.exe (PID: 720)
Creates files or folders in the user directory
- msedge.exe (PID: 8028)
- wmlaunch.exe (PID: 864)
Reads the software policy settings
- slui.exe (PID: 720)
- csc.exe (PID: 1180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:03:19 06:45:22 |
| ZipCRC: | 0x8a88c7c2 |
| ZipCompressedSize: | 2942837 |
| ZipUncompressedSize: | 6365288 |
| ZipFileName: | Documenti relativi alla violazione dei diritti di propriet? intellettuale forniti da Lucky Red.exe |
Total processes
185
Monitored processes
39
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3252 --field-trial-handle=2364,i,10480520392738605069,11833915986432136078,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 864 | "C:\Program Files\Windows Media Player\wmlaunch.exe" | C:\Program Files\Windows Media Player\wmlaunch.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Launcher Version: 12.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=4680 --field-trial-handle=2364,i,10480520392738605069,11833915986432136078,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1180 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | @0z8p1kE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2412 --field-trial-handle=2364,i,10480520392738605069,11833915986432136078,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2320 | "C:\Users\admin\Desktop\Documenti relativi alla violazione dei diritti di proprietà intellettuale forniti da Lucky Red.exe" | C:\Users\admin\Desktop\Documenti relativi alla violazione dei diritti di proprietà intellettuale forniti da Lucky Red.exe | Documenti relativi alla violazione dei diritti di proprietà intellettuale forniti da Lucky Red.exe | ||||||||||||
User: admin Company: Haihaisoft Limited Integrity Level: MEDIUM Description: Haihaisoft PDF Reader Exit code: 3221225477 Version: 1.5.7.0 Modules
| |||||||||||||||
| 2332 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3284 --field-trial-handle=2364,i,10480520392738605069,11833915986432136078,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2780 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=4868 --field-trial-handle=2364,i,10480520392738605069,11833915986432136078,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2908 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3208 --field-trial-handle=1944,i,1328311016504328466,12220526003333048073,262144 --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
10 817
Read events
10 774
Write events
29
Delete events
14
Modification events
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 8 |
Value: | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 7 |
Value: | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 6 |
Value: | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 5 |
Value: | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 4 |
Value: | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 3 |
Value: | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Preferences | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\ext | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (7400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
Executable files
11
Suspicious files
173
Text files
65
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7900 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr4752.tmp\Crashpad\settings.dat | binary | |
MD5:B5AF54AFBC81D4357409064E470FF55C | SHA256:07492FDD1C19888545C8943EBF77441DFC912049B94AA2F6F4D5B925E8EE8A04 | |||
| 7900 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr4752.tmp\Default\1d27b9ba-a855-4a84-a2f9-1336a6c72820.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 7900 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr4752.tmp\Default\Code Cache\wasm\index | binary | |
MD5:54CB446F628B2EA4A5BCE5769910512E | SHA256:FBCFE23A2ECB82B7100C50811691DDE0A33AA3DA8D176BE9882A9DB485DC0F2D | |||
| 7900 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr4752.tmp\b62cfc1d-1493-4a3d-a014-ad3cedc31ea0.tmp | binary | |
MD5:E98AB04E86FE8C4B852A263BBDBE2059 | SHA256:EA7BC2A8179A1F9217AC24C001C4F44CE54A3D1882BDBB0F1B2B72392B57A162 | |||
| 7900 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr4752.tmp\Default\History-journal | — | |
MD5:— | SHA256:— | |||
| 7900 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr4752.tmp\Default\README | text | |
MD5:883D62ACD72005F3AD7A14500D482033 | SHA256:C43668EEC4A8D88A5B3A06A84F8846853FE33E54293C2DB56899A5A5DFB4D944 | |||
| 7900 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr4752.tmp\Default\Site Characteristics Database\MANIFEST-000001 | binary | |
MD5:5AF87DFD673BA2115E2FCF5CFDB727AB | SHA256:F9D31B278E215EB0D0E9CD709EDFA037E828F36214AB7906F612160FEAD4B2B4 | |||
| 7400 | WinRAR.exe | C:\Users\admin\Desktop\Documenti relativi alla violazione dei diritti di proprietà intellettuale forniti da Lucky Red.exe | executable | |
MD5:192652C572606A94BFA09DB80F273005 | SHA256:687B849615DE7D8EF4ECC89EEEEA3C189E6316D980CFB8CA6B1BED2D4B070CD3 | |||
| 7900 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr4752.tmp\Default\Sync Data\LevelDB\MANIFEST-000001 | binary | |
MD5:5AF87DFD673BA2115E2FCF5CFDB727AB | SHA256:F9D31B278E215EB0D0E9CD709EDFA037E828F36214AB7906F612160FEAD4B2B4 | |||
| 7900 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr4752.tmp\Default\Code Cache\wasm\index-dir\temp-index | binary | |
MD5:2F397BDFCECEEC90E810F5071357F690 | SHA256:1A74AD9988A2FAC1DE66586E50A2970C8542AF9FEE82E858C10041C195AB1F6F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
61
DNS requests
51
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7524 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3140 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3140 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
— | — | 20.197.71.89:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
1196 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5112 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Rhadamanthys SSL Certificate and JA3s |
5112 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Rhadamanthys SSL Certificate and JA3s |
1180 | csc.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
1180 | csc.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |