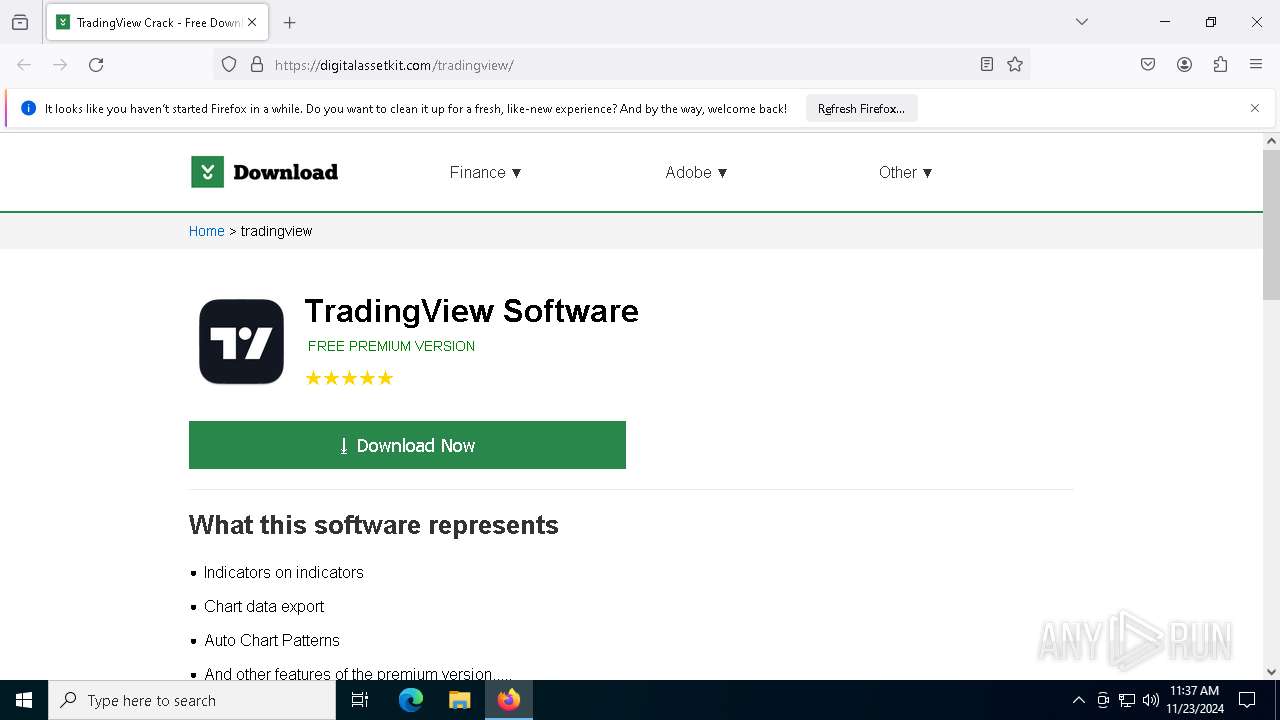
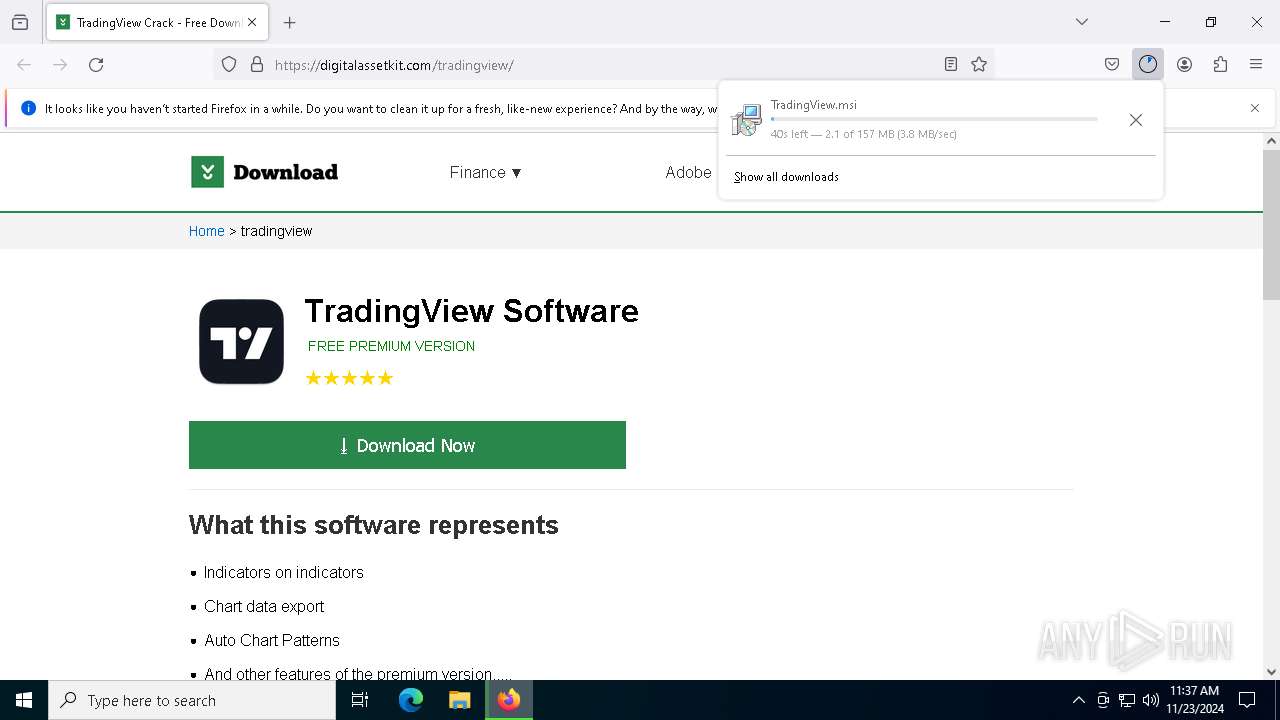
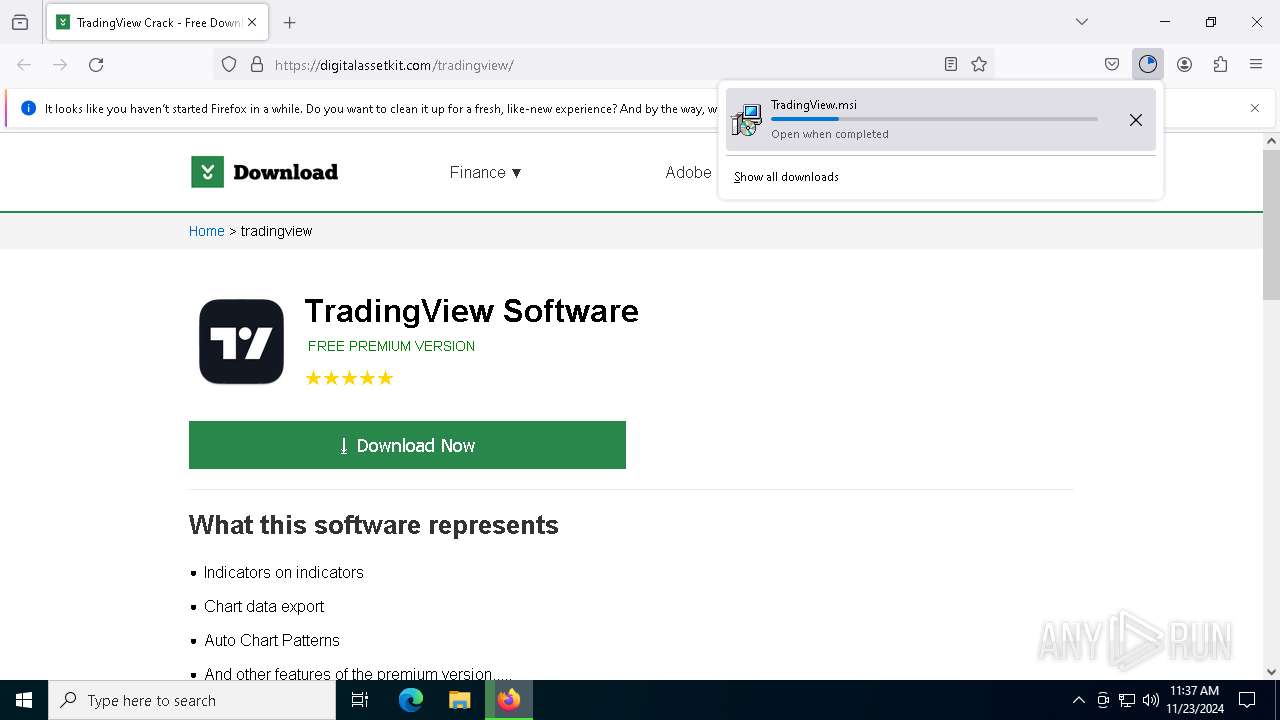
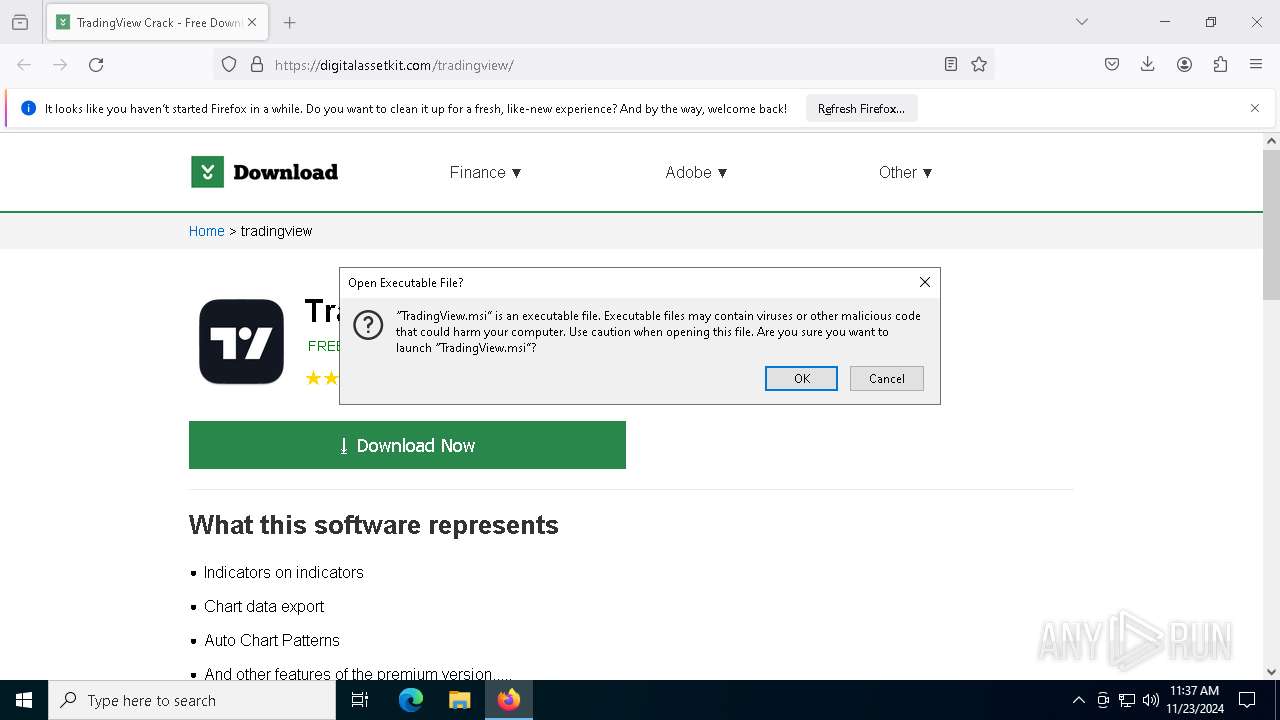
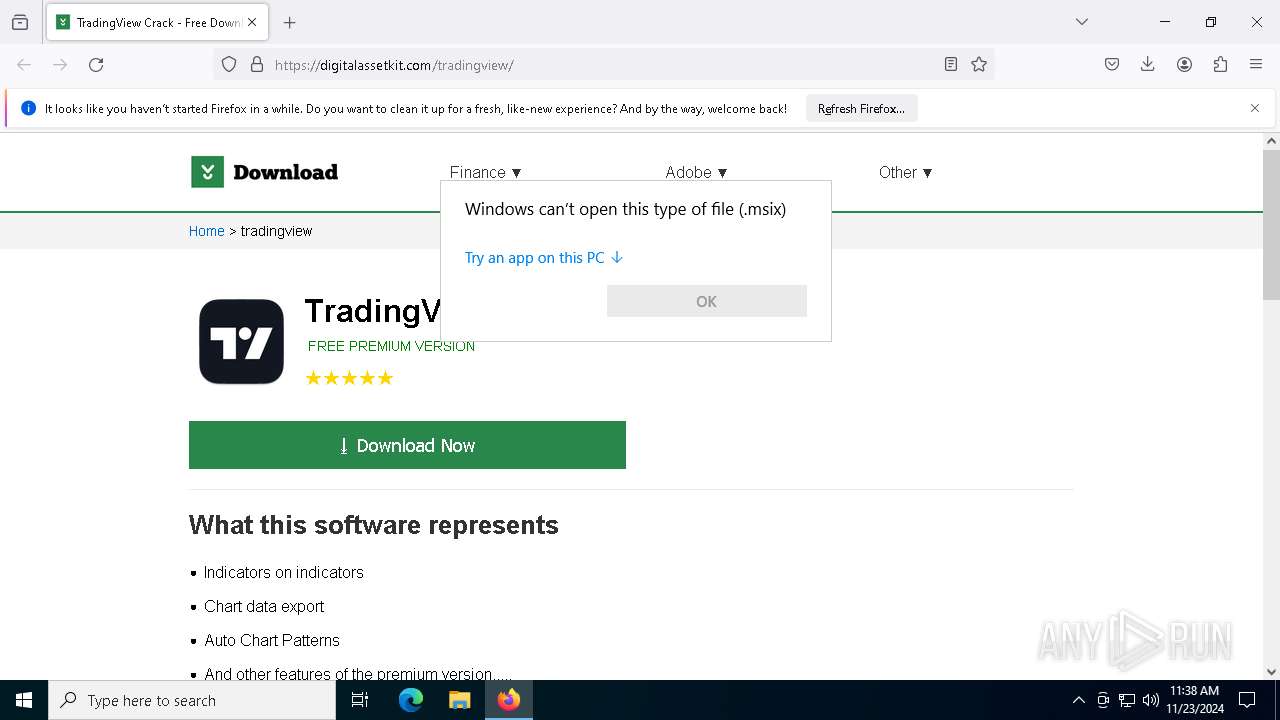
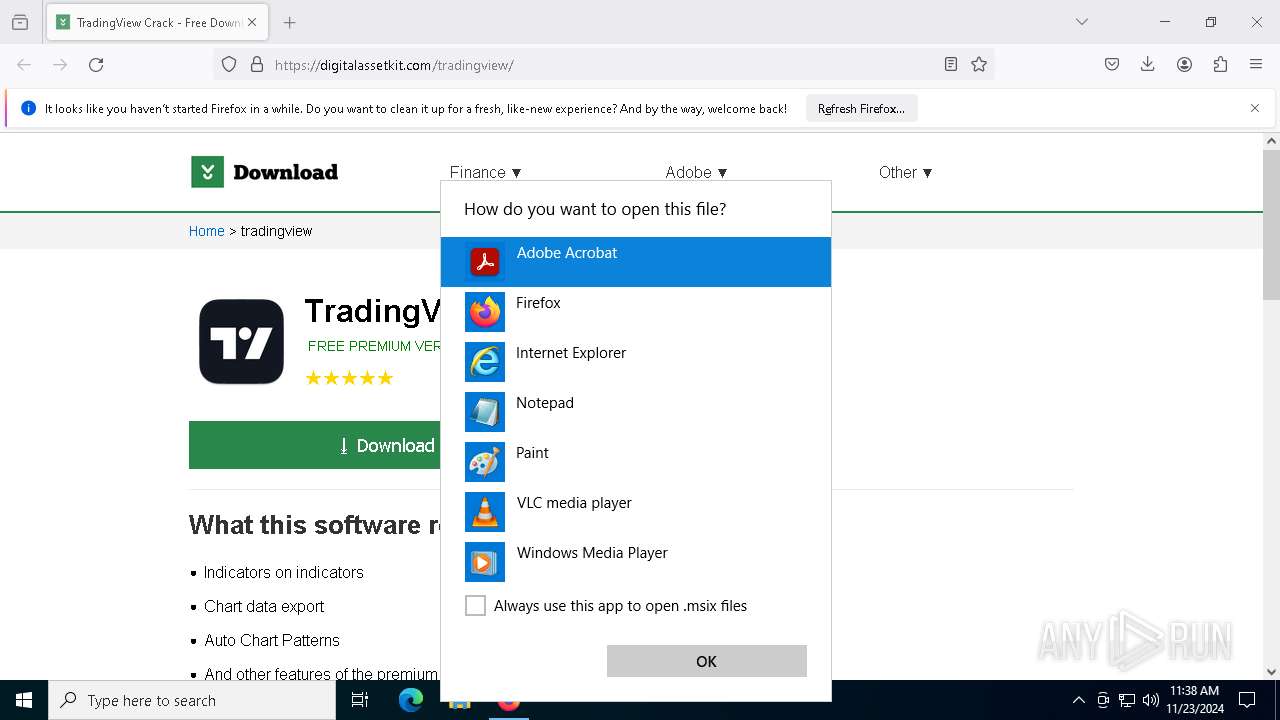
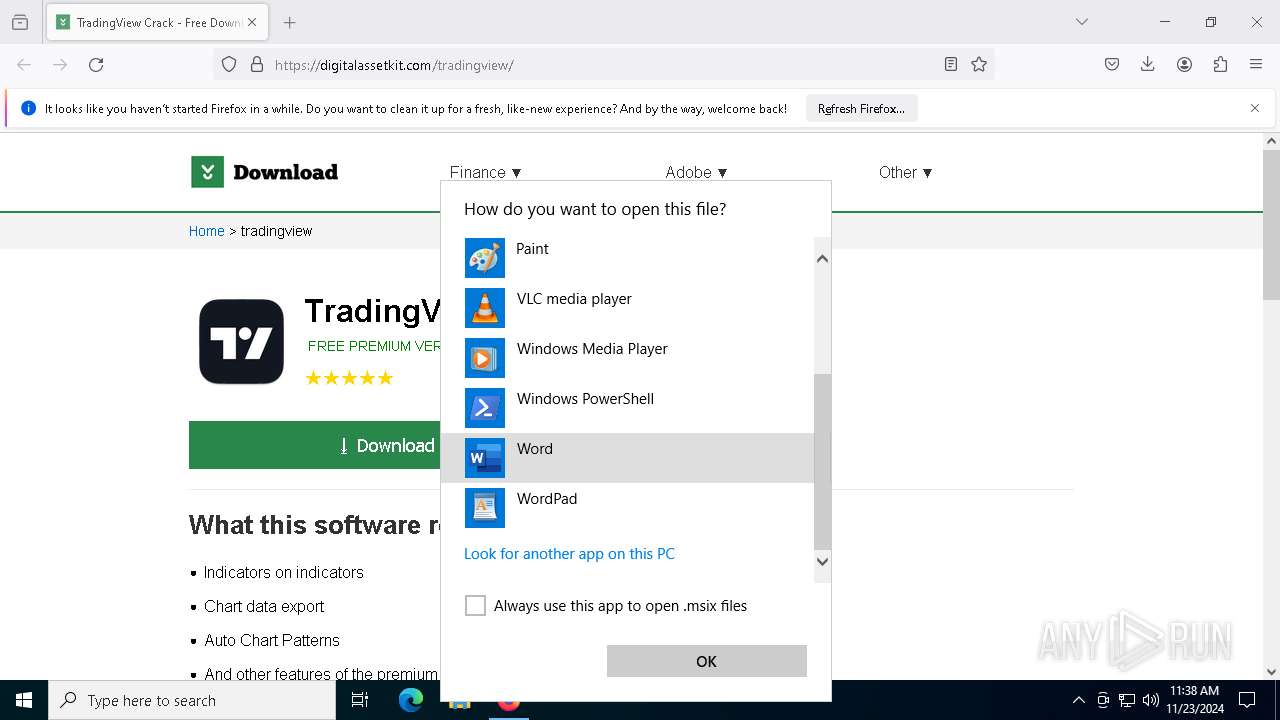
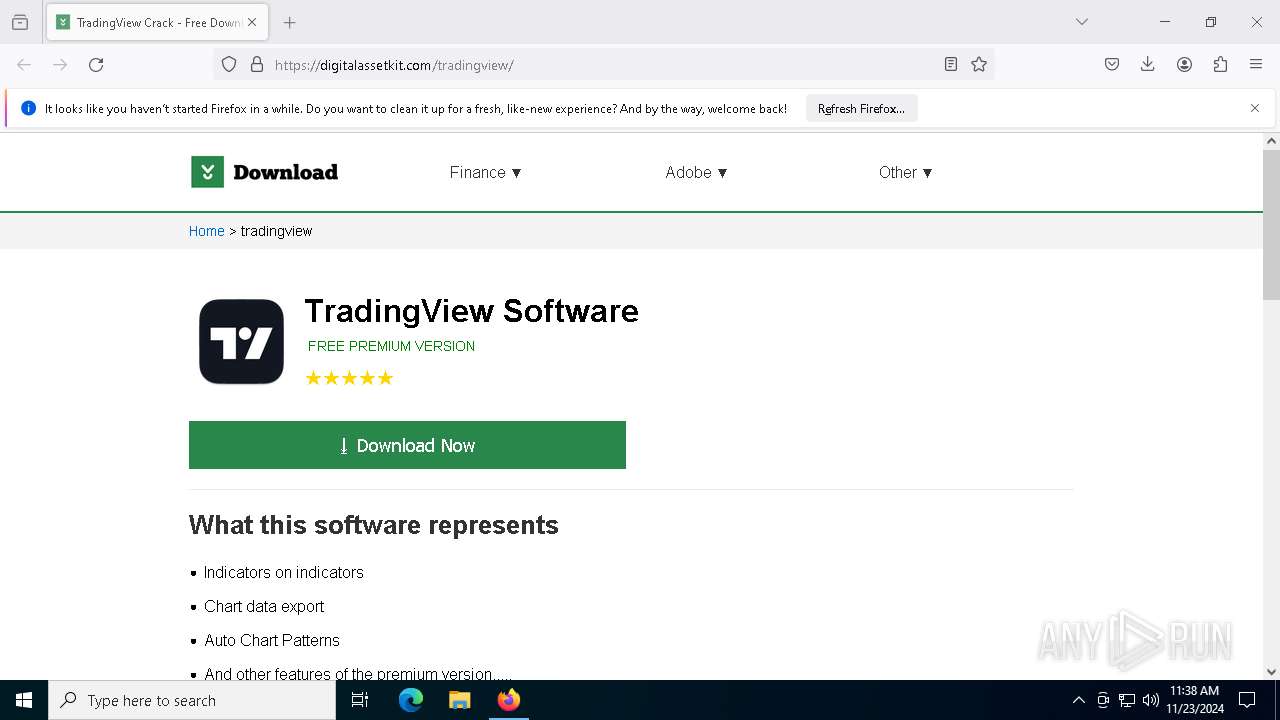
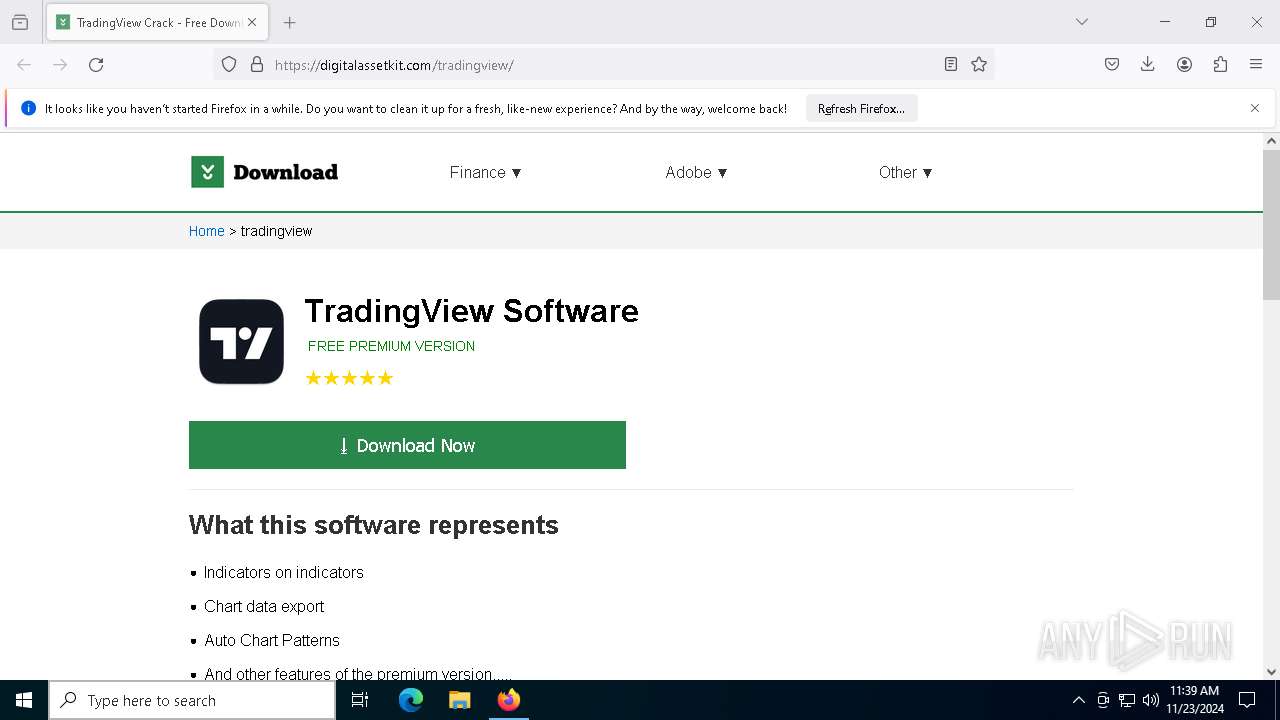
| URL: | https://digitalassetkit.com/tradingview/ |
| Full analysis: | https://app.any.run/tasks/9a4d5dbf-9d3e-4b8d-8e62-4cfccc3bb55b |
| Verdict: | Malicious activity |
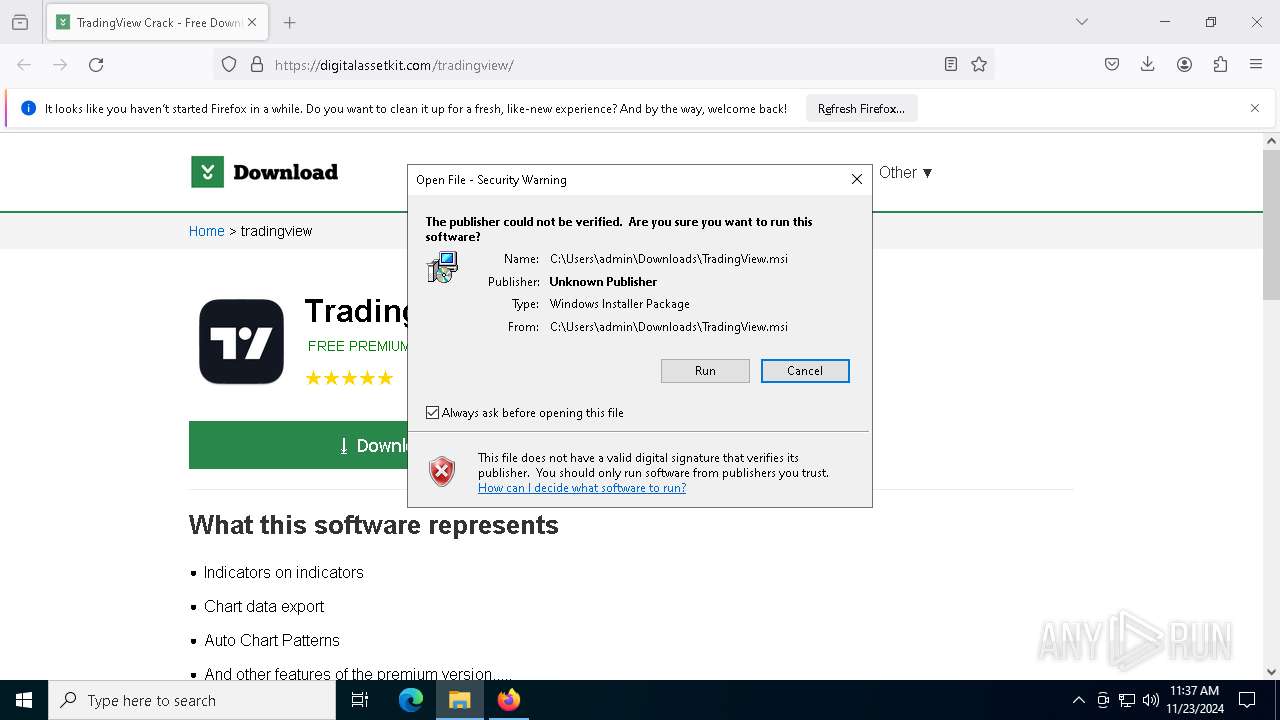
| Threats: | Danabot is an advanced banking Trojan malware that was designed to steal financial information from victims. Out of the Trojans in the wild, this is one of the most advanced thanks to the modular design and a complex delivery method. |
| Analysis date: | November 23, 2024, 11:36:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 476F81D77DEBB084D11FFB27AE5FEF23 |
| SHA1: | 728D2293FE661247F4B1C5B140DD16E881F3DCF0 |
| SHA256: | DB5581568CA580F4CEB9C9F6339CEFD32D53EA044AAD373EE3140D3F25C953B9 |
| SSDEEP: | 3:N8UB0jzBEBZIK:2UeyH3 |
MALICIOUS
DANABOT has been detected (YARA)
- AudioReaderXL.exe (PID: 2632)
- AudioReaderXL.exe (PID: 3888)
DANABOT has been detected (SURICATA)
- AudioReaderXL.exe (PID: 2632)
- AudioReaderXL.exe (PID: 8180)
Change Internet Settings
- AudioReaderXL.exe (PID: 2632)
Changes the autorun value in the registry
- AudioReaderXL.exe (PID: 2632)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 8012)
Checks Windows Trust Settings
- msiexec.exe (PID: 7964)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7964)
- AudioReaderXL.exe (PID: 2632)
Process drops legitimate windows executable
- msiexec.exe (PID: 7964)
There is functionality for taking screenshot (YARA)
- AudioReaderXL.exe (PID: 2632)
- AudioReaderXL.exe (PID: 3888)
- AudioReaderXL.exe (PID: 8180)
Reads the date of Windows installation
- AudioReaderXL.exe (PID: 2632)
Reads security settings of Internet Explorer
- AudioReaderXL.exe (PID: 2632)
- AudioReaderXL.exe (PID: 8180)
Contacting a server suspected of hosting an CnC
- AudioReaderXL.exe (PID: 2632)
- AudioReaderXL.exe (PID: 8180)
Searches for installed software
- AudioReaderXL.exe (PID: 2632)
- AudioReaderXL.exe (PID: 8180)
Application launched itself
- AudioReaderXL.exe (PID: 2632)
Adds/modifies Windows certificates
- AudioReaderXL.exe (PID: 8180)
INFO
Application launched itself
- firefox.exe (PID: 3820)
- firefox.exe (PID: 6012)
- AcroCEF.exe (PID: 7484)
- Acrobat.exe (PID: 2072)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7904)
- OpenWith.exe (PID: 6752)
The process uses the downloaded file
- firefox.exe (PID: 3820)
Reads the software policy settings
- msiexec.exe (PID: 7904)
- msiexec.exe (PID: 7964)
Checks supported languages
- msiexec.exe (PID: 7964)
- AudioReaderXL.exe (PID: 2632)
- AudioReaderXL.exe (PID: 3888)
- AudioReaderXL.exe (PID: 8180)
Manual execution by a user
- msiexec.exe (PID: 7904)
Reads the computer name
- msiexec.exe (PID: 7964)
- AudioReaderXL.exe (PID: 2632)
- AudioReaderXL.exe (PID: 3888)
- AudioReaderXL.exe (PID: 8180)
Executable content was dropped or overwritten
- firefox.exe (PID: 3820)
- msiexec.exe (PID: 7964)
Manages system restore points
- SrTasks.exe (PID: 7420)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7964)
- AudioReaderXL.exe (PID: 2632)
- AudioReaderXL.exe (PID: 8180)
- AudioReaderXL.exe (PID: 3888)
Creates a software uninstall entry
- msiexec.exe (PID: 7964)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6752)
Reads Environment values
- AudioReaderXL.exe (PID: 2632)
Sends debugging messages
- Acrobat.exe (PID: 936)
Reads CPU info
- AudioReaderXL.exe (PID: 2632)
- AudioReaderXL.exe (PID: 8180)
Reads product name
- AudioReaderXL.exe (PID: 2632)
Reads Windows Product ID
- AudioReaderXL.exe (PID: 2632)
Process checks computer location settings
- AudioReaderXL.exe (PID: 2632)
Disables trace logs
- AudioReaderXL.exe (PID: 2632)
- AudioReaderXL.exe (PID: 8180)
Checks proxy server information
- AudioReaderXL.exe (PID: 2632)
- AudioReaderXL.exe (PID: 8180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
163
Monitored processes
32
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 624 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2092 -parentBuildID 20240213221259 -prefsHandle 2084 -prefMapHandle 2072 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {4c992c31-4820-480e-90f4-68c4fa0e8d18} 3820 "\\.\pipe\gecko-crash-server-pipe.3820" 1ad5907ff10 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
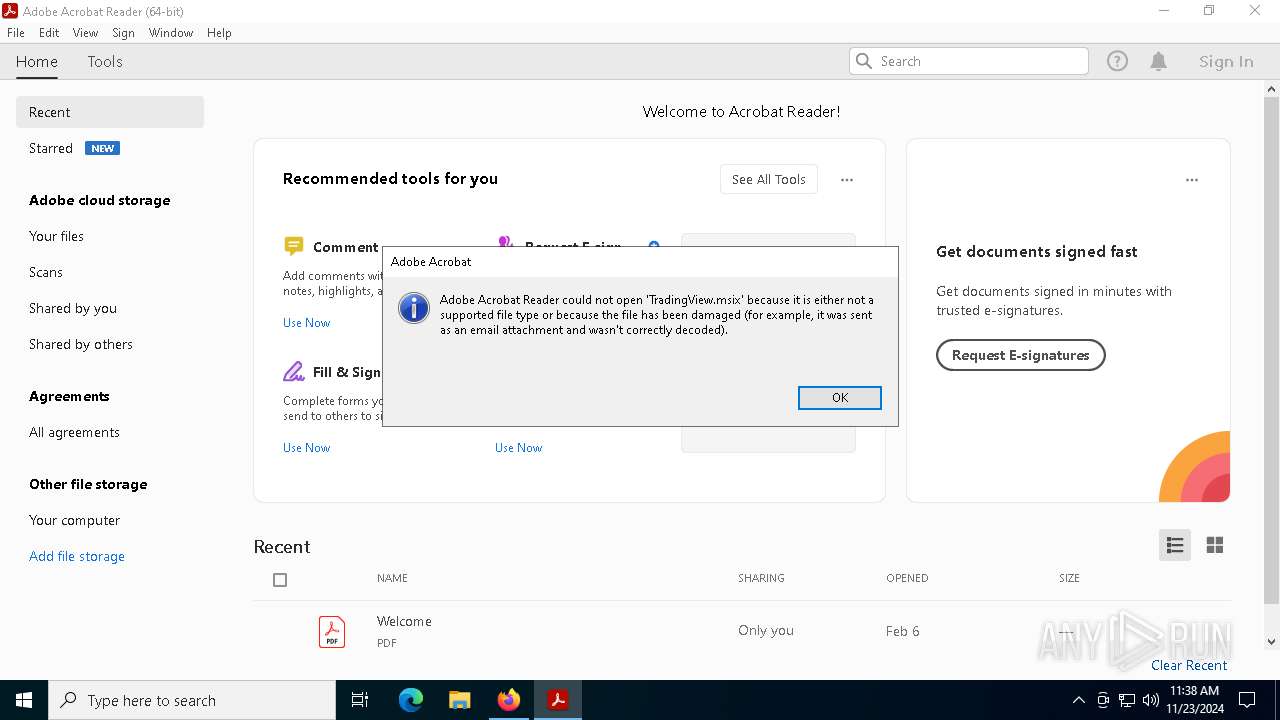
| 936 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\AppData\Local\Programs\Advanced ChrisPC Win Experience Index Ultimate\TradingView.msix" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2072 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" "C:\Users\admin\AppData\Local\Programs\Advanced ChrisPC Win Experience Index Ultimate\TradingView.msix" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2600 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1540 --field-trial-handle=1616,i,6218268530321665897,6471563458027280093,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2632 | "C:\Users\admin\AppData\Local\Programs\Advanced ChrisPC Win Experience Index Ultimate\AudioReaderXL.exe" | C:\Users\admin\AppData\Local\Programs\Advanced ChrisPC Win Experience Index Ultimate\AudioReaderXL.exe | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 9.4.0.54 Modules
| |||||||||||||||
| 3544 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5140 -childID 6 -isForBrowser -prefsHandle 5352 -prefMapHandle 5328 -prefsLen 31197 -prefMapSize 244583 -jsInitHandle 1288 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {c30f7791-6750-4d4a-96b7-61822d09db6f} 3820 "\\.\pipe\gecko-crash-server-pipe.3820" 1ad708c1d90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
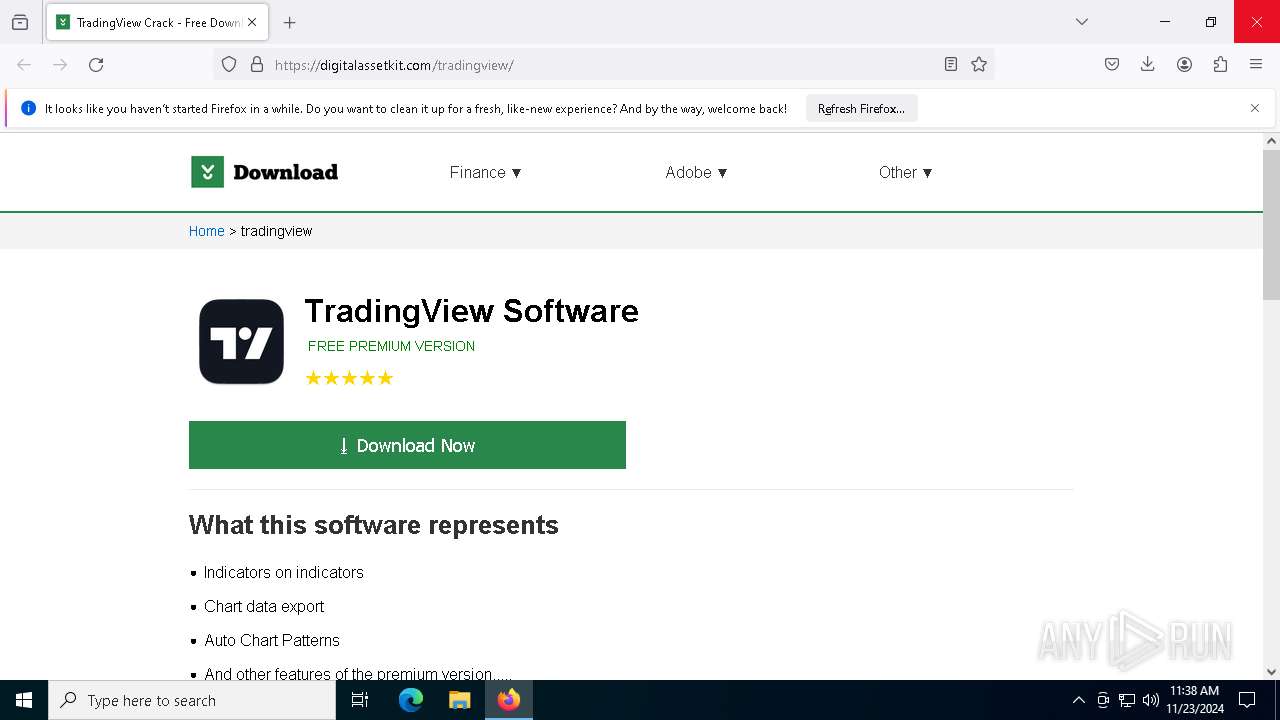
| 3820 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://digitalassetkit.com/tradingview/ | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3888 | "C:\Users\admin\AppData\Local\Programs\Advanced ChrisPC Win Experience Index Ultimate\AudioReaderXL.exe" | C:\Users\admin\AppData\Local\Programs\Advanced ChrisPC Win Experience Index Ultimate\AudioReaderXL.exe | AudioReaderXL.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 9.4.0.54 Modules
| |||||||||||||||
| 3920 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1624 --field-trial-handle=1616,i,6218268530321665897,6471563458027280093,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
Total events
53 667
Read events
53 053
Write events
585
Delete events
29
Modification events
| (PID) Process: | (3820) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (7964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000007F1E1C229C3DDB011C1F00003C1F0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000078F31C229C3DDB011C1F00003C1F0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000077DA58229C3DDB011C1F00003C1F0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000294E59229C3DDB011C1F00003C1F0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000271D5B229C3DDB011C1F00003C1F0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000077345E229C3DDB011C1F00003C1F0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7964) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000005DB8D8229C3DDB011C1F0000B81F0000E803000001000000000000000000000042CFA51B35EF1C498D05760F89917FD800000000000000000000000000000000 | |||
| (PID) Process: | (8012) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000009E8FE6229C3DDB014C1F00006C1F0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (8012) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000009E8FE6229C3DDB014C1F0000D81F0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
9
Suspicious files
301
Text files
68
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3820 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3820 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 3820 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 3820 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3820 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3820 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3820 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:D79C0DA3EC489BB13B9BE62F4A4B7124 | SHA256:7E6090C9C1812F1827AC5C280C8D7C0A1B9B054386D5F73C2D8E02AE2E2E4352 | |||
| 3820 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:E3B3B569B64BE4DBB8C46132B103CD7B | SHA256:ECA2D8E37887C67A0920E19B7BDA1648751CCEE9DA31DDBD18BA1D7ED05E7599 | |||
| 3820 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3820 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:E3B3B569B64BE4DBB8C46132B103CD7B | SHA256:ECA2D8E37887C67A0920E19B7BDA1648751CCEE9DA31DDBD18BA1D7ED05E7599 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
108
DNS requests
122
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3820 | firefox.exe | POST | 200 | 184.24.77.53:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
3820 | firefox.exe | POST | 200 | 184.24.77.53:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
3820 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
188 | svchost.exe | GET | 304 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
188 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
188 | svchost.exe | 23.48.23.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
188 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
digitalassetkit.com |
| unknown |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
3820 | firefox.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
3820 | firefox.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
3820 | firefox.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
2632 | AudioReaderXL.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Danabot TCP Packet |