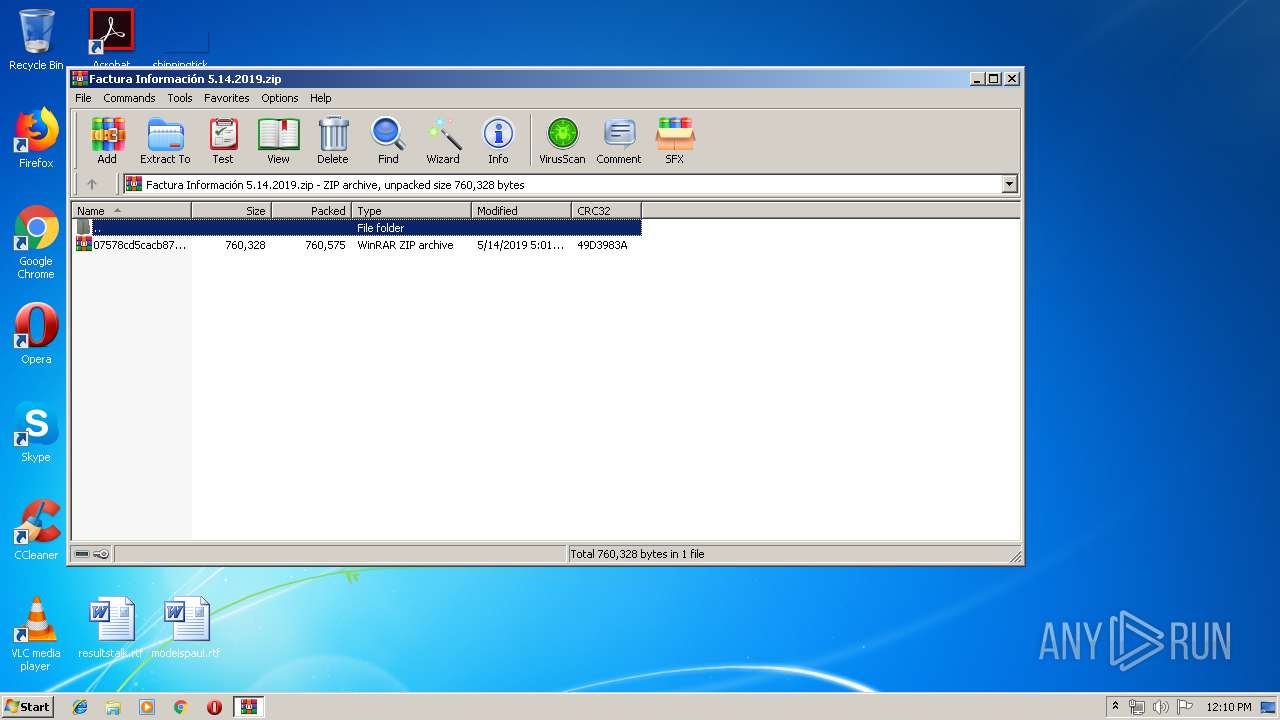
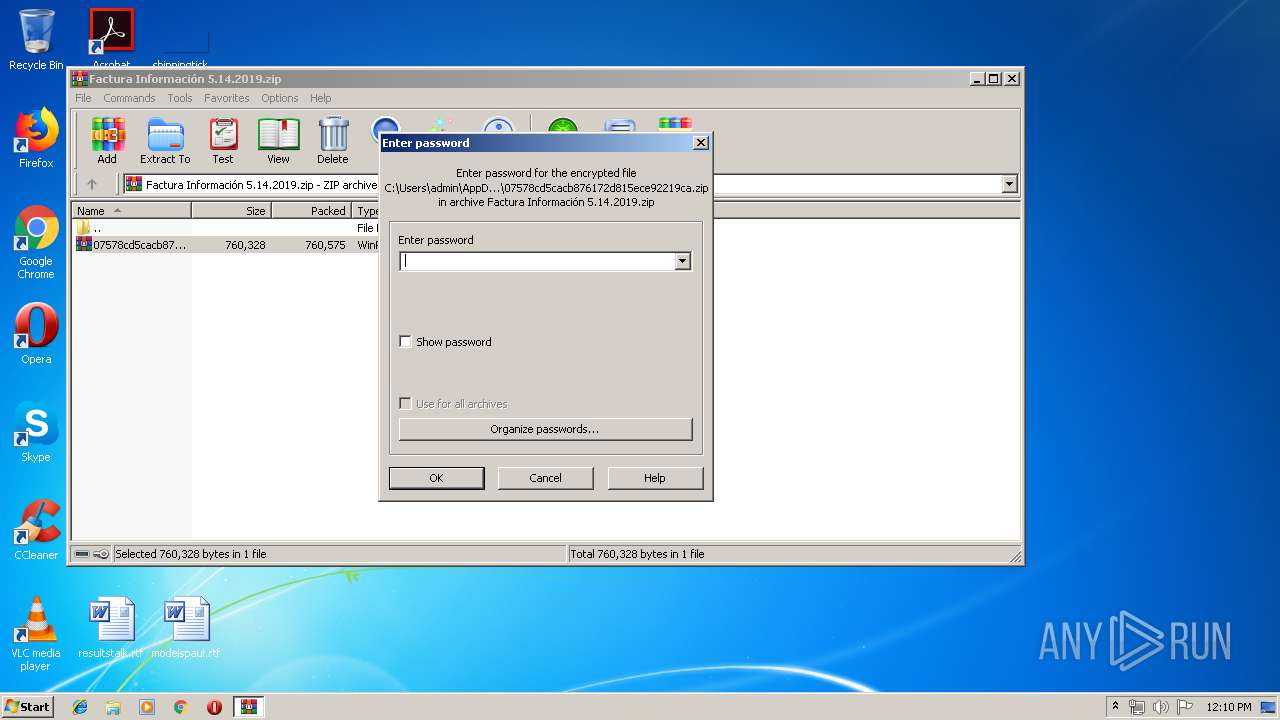
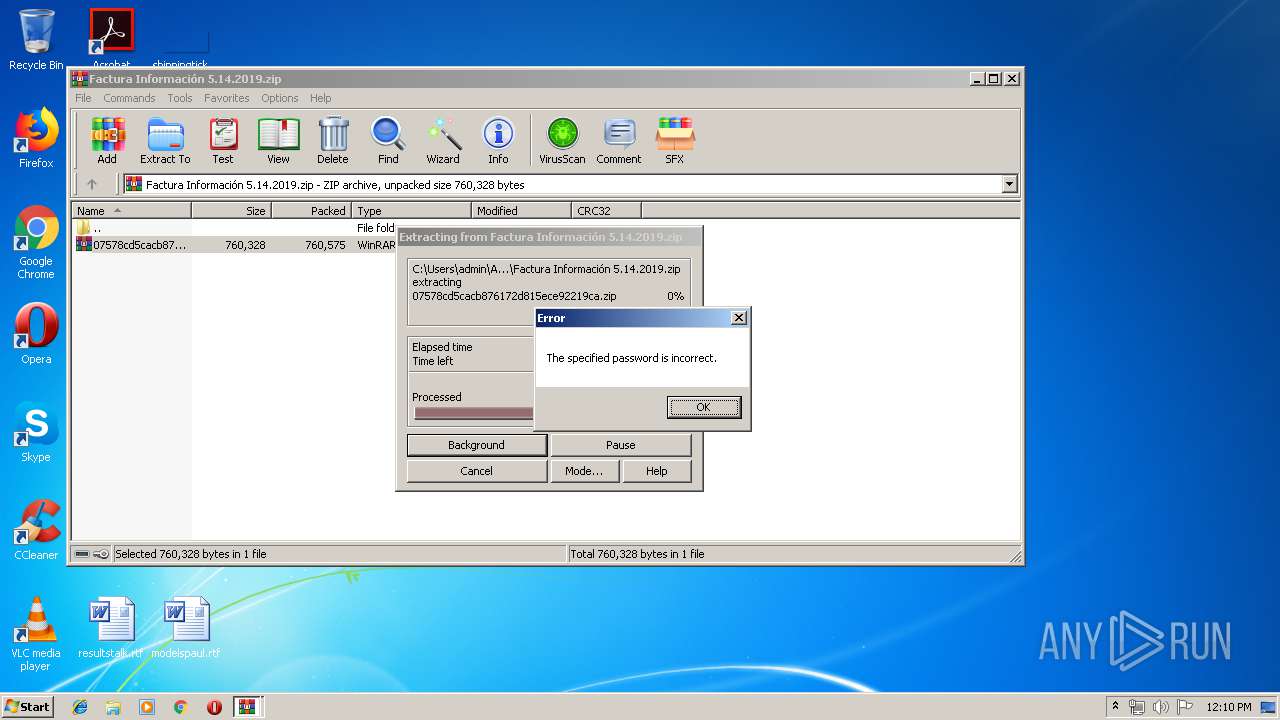
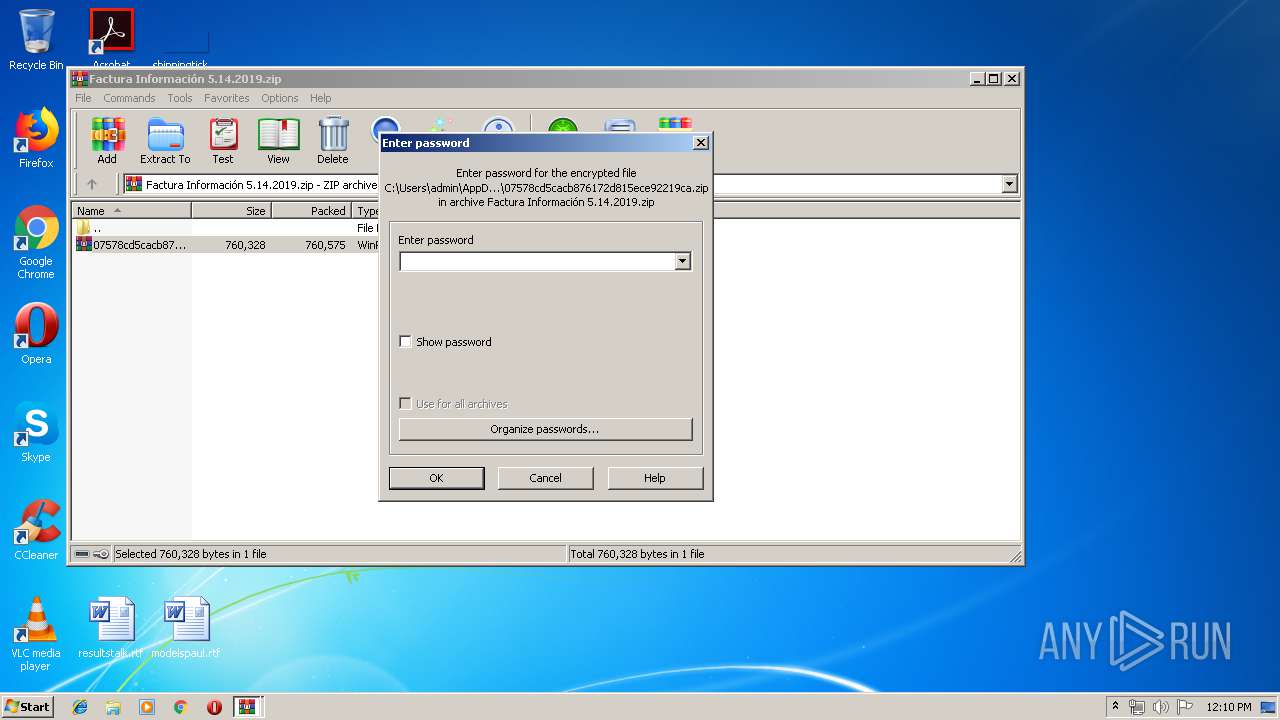
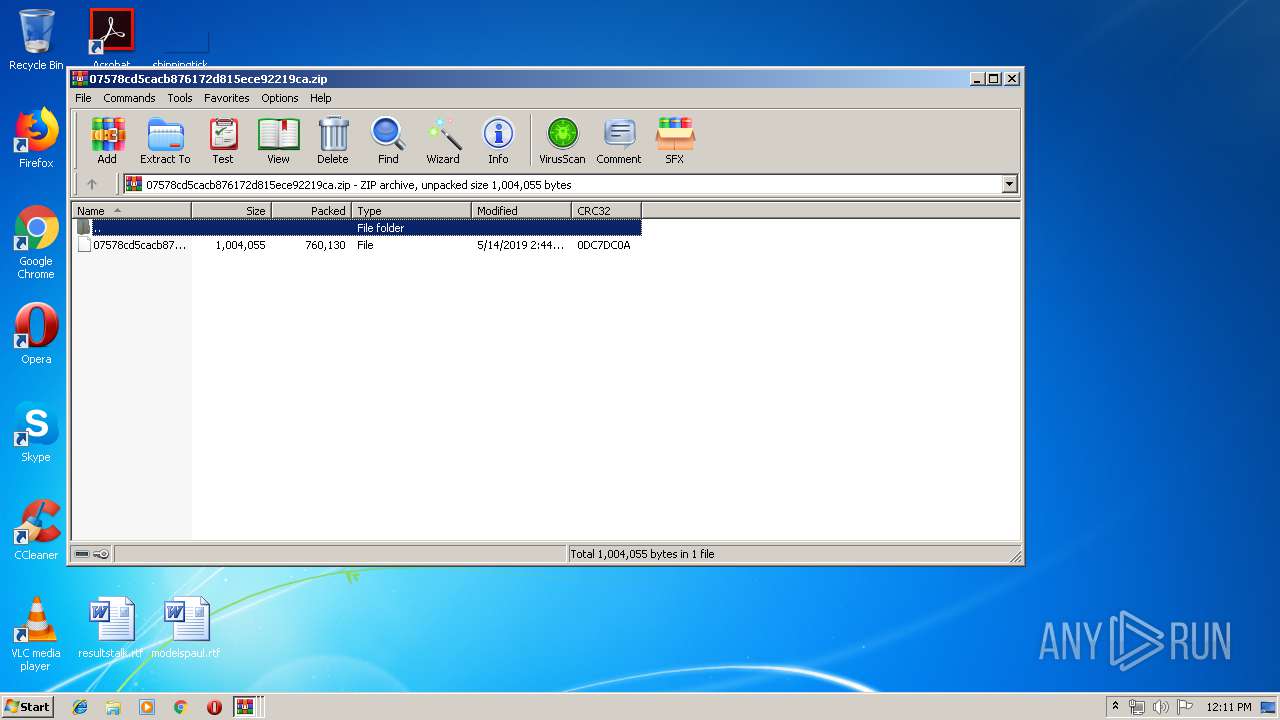
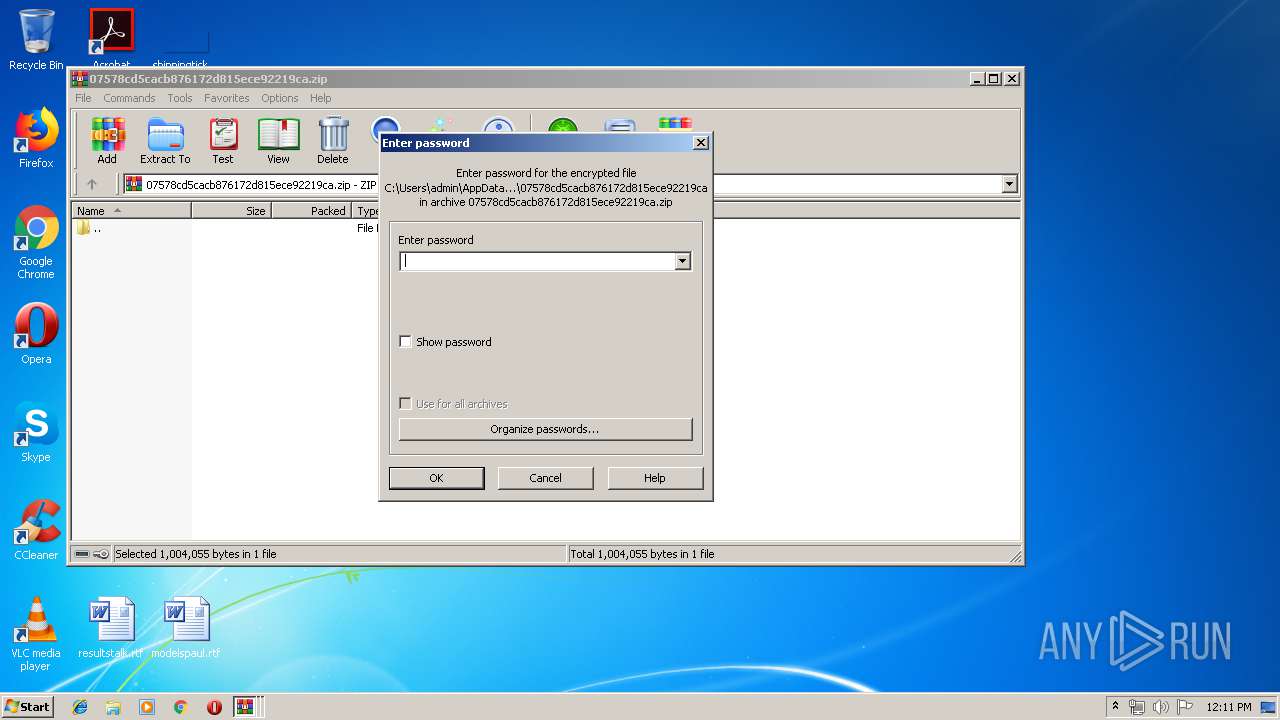
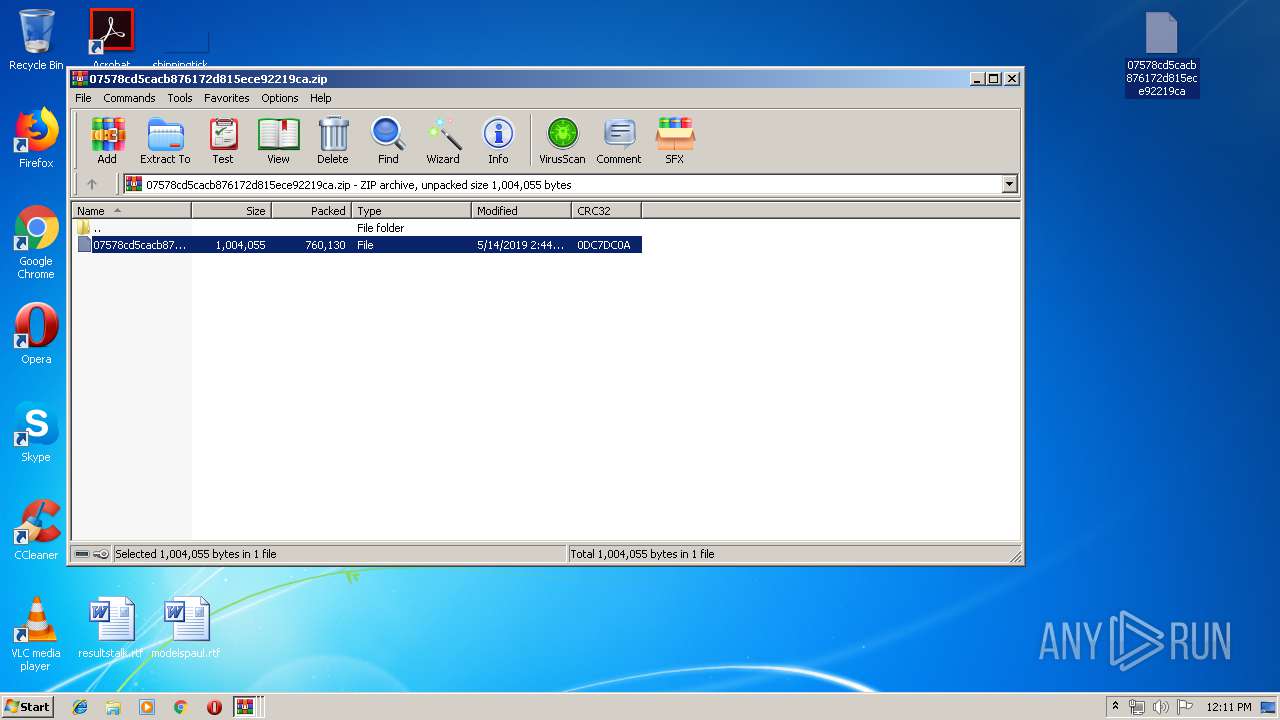
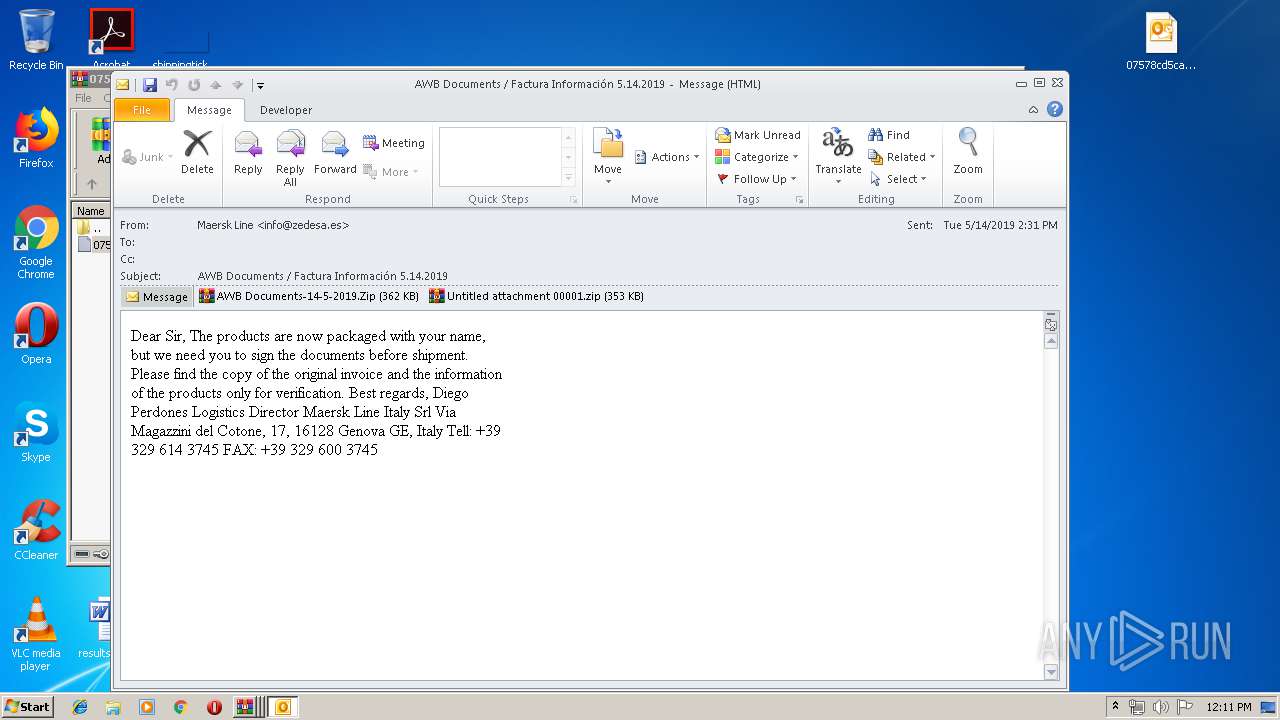
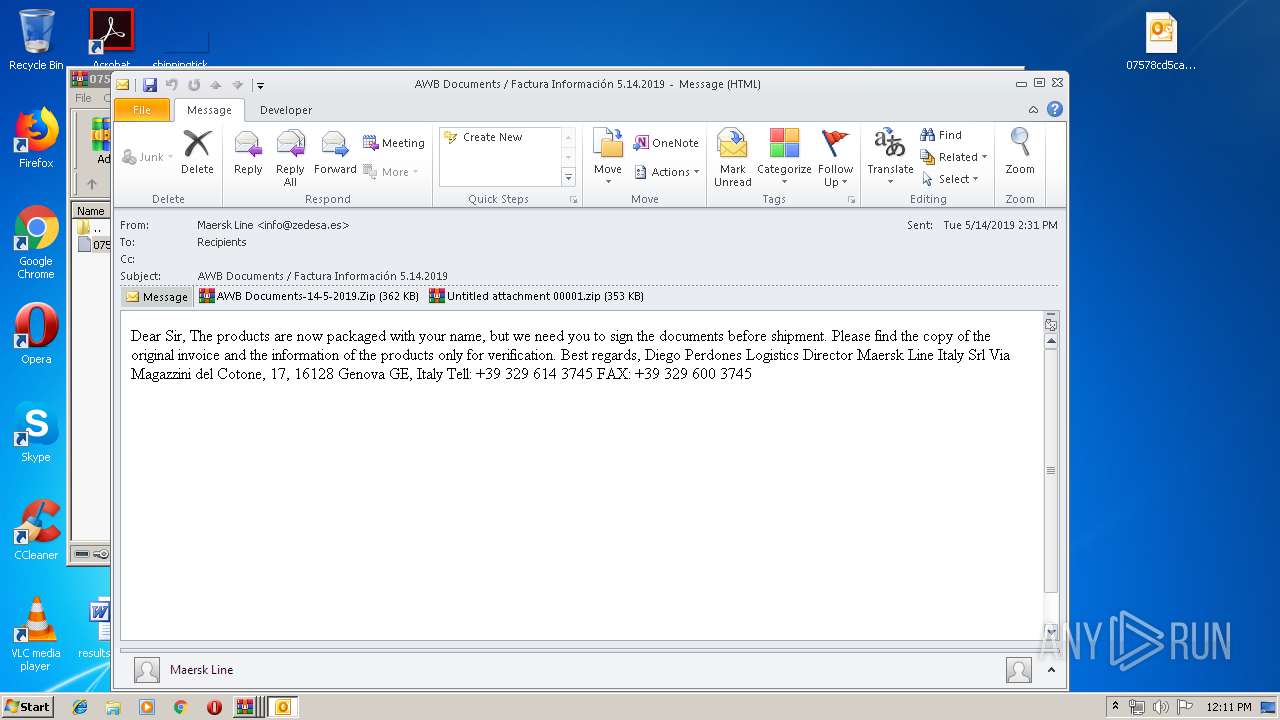
| File name: | Factura Información 5.14.2019.zip |
| Full analysis: | https://app.any.run/tasks/a44f88f4-dce3-4a76-87c9-dcc678c14503 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | May 15, 2019, 11:10:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | AA30B714387CC6C758D7B7E9377BB071 |
| SHA1: | 9008EA2ED02E1533F18F283E078C883E81D619B0 |
| SHA256: | DB4CE6E7B2C89B0E2C3DDA13C2C54147A0F25440DF4DB10FFAC18A1495144182 |
| SSDEEP: | 12288:D6kuVlciBy9K/offqyuG8m4nOjNp/9jPQRm9zwKpCL+p6NKS0PkiZSPYNRB7N:D6kuVl1k9K/2f4xm4Oj7lsRap6B0PKi9 |
MALICIOUS
Renames files like Ransomware
- explorer.exe (PID: 2044)
Application was dropped or rewritten from another process
- Factura Información.exe (PID: 1748)
Actions looks like stealing of personal data
- NETSTAT.EXE (PID: 2992)
Formbook was detected
- Firefox.exe (PID: 3216)
- NETSTAT.EXE (PID: 2992)
Connects to CnC server
- explorer.exe (PID: 2044)
FORMBOOK was detected
- explorer.exe (PID: 2044)
Changes the autorun value in the registry
- NETSTAT.EXE (PID: 2992)
Stealing of credential data
- NETSTAT.EXE (PID: 2992)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 2568)
Creates files in the user directory
- explorer.exe (PID: 2044)
- OUTLOOK.EXE (PID: 2416)
- NETSTAT.EXE (PID: 2992)
Reads Internet Cache Settings
- explorer.exe (PID: 2044)
- OUTLOOK.EXE (PID: 2416)
Uses NETSTAT.EXE to discover network connections
- explorer.exe (PID: 2044)
Starts CMD.EXE for commands execution
- NETSTAT.EXE (PID: 2992)
Loads DLL from Mozilla Firefox
- NETSTAT.EXE (PID: 2992)
INFO
Dropped object may contain Bitcoin addresses
- explorer.exe (PID: 2044)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2416)
Creates files in the user directory
- Firefox.exe (PID: 3216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:05:14 17:01:10 |
| ZipCRC: | 0x49d3983a |
| ZipCompressedSize: | 760575 |
| ZipUncompressedSize: | 760328 |
| ZipFileName: | 07578cd5cacb876172d815ece92219ca.zip |
Total processes
48
Monitored processes
10
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1748 | "C:\Users\admin\Desktop\Factura Información.exe" | C:\Users\admin\Desktop\Factura Información.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2044 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2128 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb2568.14230\07578cd5cacb876172d815ece92219ca.zip | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2320 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb2568.15007\07578cd5cacb876172d815ece92219ca.zip | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2416 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\07578cd5cacb876172d815ece92219ca.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2568 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Factura Información 5.14.2019.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2992 | "C:\Windows\System32\NETSTAT.EXE" | C:\Windows\System32\NETSTAT.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Netstat Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3216 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | NETSTAT.EXE | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 3904 | /c del "C:\Users\admin\Desktop\Factura Información.exe" | C:\Windows\System32\cmd.exe | — | NETSTAT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3932 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Untitled attachment 00001.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
7 085
Read events
6 570
Write events
495
Delete events
20
Modification events
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Factura Información 5.14.2019.zip | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2568) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2044) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (2044) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
1
Suspicious files
78
Text files
25
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2320.17371\07578cd5cacb876172d815ece92219ca | — | |
MD5:— | SHA256:— | |||
| 2416 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR16C2.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2416 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp18F6.tmp | — | |
MD5:— | SHA256:— | |||
| 2416 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp18F7.tmp | — | |
MD5:— | SHA256:— | |||
| 2416 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\0LEZLYK2\Untitled attachment 00001 (2).zip\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2568.15007\07578cd5cacb876172d815ece92219ca.zip | compressed | |
MD5:— | SHA256:— | |||
| 2568 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2568.14230\07578cd5cacb876172d815ece92219ca.zip | compressed | |
MD5:— | SHA256:— | |||
| 2416 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2044 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012019051520190516\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3932 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3932.21186\Factura Información.exe | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
6
DNS requests
7
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2416 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
2044 | explorer.exe | GET | — | 50.63.202.46:80 | http://www.99087755.com/at/?t6O47BM=K3wvK2ANea00g1KvhgQv4JzZUbVULwjT8UM/8xB2N/uXnfEEemOhw/f/Iwjh8Dlg4MQb+w==&9rA4D=J4Nh- | US | — | — | malicious |
2044 | explorer.exe | POST | — | 184.168.221.45:80 | http://www.theruthiejane.com/at/ | US | — | — | malicious |
2044 | explorer.exe | POST | — | 184.168.221.45:80 | http://www.theruthiejane.com/at/ | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2044 | explorer.exe | 50.63.202.46:80 | www.99087755.com | GoDaddy.com, LLC | US | malicious |
2044 | explorer.exe | 184.168.221.45:80 | www.theruthiejane.com | GoDaddy.com, LLC | US | malicious |
2416 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |
www.99087755.com |
| malicious |
www.theruthiejane.com |
| malicious |
www.talkavl.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2044 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
2044 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
2044 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
2044 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
2044 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
2044 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
3 ETPRO signatures available at the full report