| File name: | Setup.exe |
| Full analysis: | https://app.any.run/tasks/9fb4563b-da31-4c39-8b6c-b2a0e0beb9ba |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 29, 2025, 11:36:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 18343F5CBF09AF16B70E4BDB87C5FC91 |
| SHA1: | 658DAA31317EE322B731BBEB60513CF7B4BDEB0B |
| SHA256: | DB3FC10F5DD5F1D577A19988E1C4E127935224CFAE35C02823F312C88CA953D8 |
| SSDEEP: | 98304:cPFKLwTEGKLaCJl7UotN5srrUK7vgyONaCr:N |
MALICIOUS
Executing a file with an untrusted certificate
- Setup.exe (PID: 4776)
- Setup.exe (PID: 6744)
- WB3CLQX67JBJ0EUM1.exe (PID: 5720)
- JB0EEJU1TROISKQGDPSCHWFG83R3.exe (PID: 5228)
- A0I9AJ2OCUELTUP4XXW327.exe (PID: 6156)
- 1T9VRPYAY297LOAAL3I8F3H9KUEN1HT.exe (PID: 4488)
LUMMA mutex has been found
- Setup.exe (PID: 4776)
- Setup.exe (PID: 6744)
Steals credentials from Web Browsers
- Setup.exe (PID: 4776)
- Setup.exe (PID: 6744)
Actions looks like stealing of personal data
- Setup.exe (PID: 4776)
- Setup.exe (PID: 6744)
Known privilege escalation attack
- dllhost.exe (PID: 4996)
Changes the autorun value in the registry
- JB0EEJU1TROISKQGDPSCHWFG83R3.exe (PID: 5228)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- Setup.exe (PID: 4776)
- Setup.exe (PID: 6744)
Searches for installed software
- Setup.exe (PID: 4776)
- Setup.exe (PID: 6744)
Executable content was dropped or overwritten
- Setup.exe (PID: 4776)
- Clus-Blue.exe (PID: 1040)
- Clus-Blue.exe (PID: 3008)
- Setup.exe (PID: 6744)
- JB0EEJU1TROISKQGDPSCHWFG83R3.exe (PID: 5228)
The process drops C-runtime libraries
- Setup.exe (PID: 4776)
- Clus-Blue.exe (PID: 1040)
- Setup.exe (PID: 6744)
Process drops legitimate windows executable
- Clus-Blue.exe (PID: 1040)
- Setup.exe (PID: 4776)
- Setup.exe (PID: 6744)
Starts itself from another location
- Clus-Blue.exe (PID: 1040)
- Clus-Blue.exe (PID: 2244)
Executes application which crashes
- WB3CLQX67JBJ0EUM1.exe (PID: 5720)
INFO
Checks supported languages
- Setup.exe (PID: 4776)
- Setup.exe (PID: 6744)
- WB3CLQX67JBJ0EUM1.exe (PID: 5720)
- Clus-Blue.exe (PID: 1040)
- Clus-Blue.exe (PID: 3008)
- JB0EEJU1TROISKQGDPSCHWFG83R3.exe (PID: 5228)
- 360Tray.exe (PID: 6712)
- Clus-Blue.exe (PID: 2244)
- Clus-Blue.exe (PID: 6392)
- A0I9AJ2OCUELTUP4XXW327.exe (PID: 6156)
- 1T9VRPYAY297LOAAL3I8F3H9KUEN1HT.exe (PID: 4488)
- Clus-Blue.exe (PID: 6512)
- 360Tray.exe (PID: 4040)
- Clus-Blue.exe (PID: 6148)
The sample compiled with russian language support
- Setup.exe (PID: 4776)
Manual execution by a user
- Setup.exe (PID: 6744)
Reads the software policy settings
- Setup.exe (PID: 4776)
- Setup.exe (PID: 6744)
Reads the computer name
- Setup.exe (PID: 4776)
- Setup.exe (PID: 6744)
- Clus-Blue.exe (PID: 1040)
- Clus-Blue.exe (PID: 3008)
- JB0EEJU1TROISKQGDPSCHWFG83R3.exe (PID: 5228)
- 360Tray.exe (PID: 6712)
- Clus-Blue.exe (PID: 6392)
- Clus-Blue.exe (PID: 2244)
- Clus-Blue.exe (PID: 6512)
- 360Tray.exe (PID: 4040)
- Clus-Blue.exe (PID: 6148)
Create files in a temporary directory
- Setup.exe (PID: 4776)
- Clus-Blue.exe (PID: 3008)
- Setup.exe (PID: 6744)
- Clus-Blue.exe (PID: 6392)
- Clus-Blue.exe (PID: 6512)
- Clus-Blue.exe (PID: 6148)
The sample compiled with english language support
- Setup.exe (PID: 4776)
- Clus-Blue.exe (PID: 1040)
- Setup.exe (PID: 6744)
- JB0EEJU1TROISKQGDPSCHWFG83R3.exe (PID: 5228)
Creates files in the program directory
- Clus-Blue.exe (PID: 1040)
- Clus-Blue.exe (PID: 3008)
- JB0EEJU1TROISKQGDPSCHWFG83R3.exe (PID: 5228)
The sample compiled with chinese language support
- Clus-Blue.exe (PID: 3008)
Reads the machine GUID from the registry
- 360Tray.exe (PID: 6712)
- 360Tray.exe (PID: 4040)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 4996)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:06:27 10:41:20+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 910848 |
| InitializedDataSize: | 919552 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8415f |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.2.30.4914 |
| ProductVersionNumber: | 3.2.30.4914 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Russian |
| CharacterSet: | Unicode |
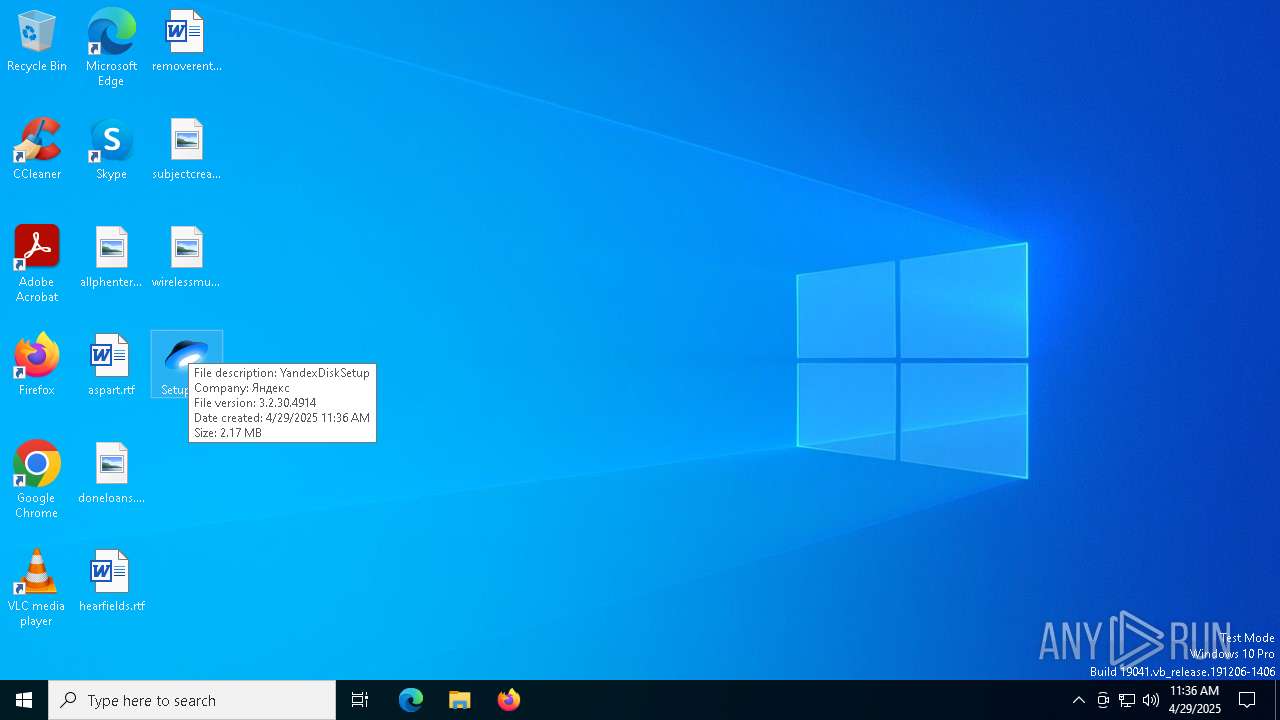
| CompanyName: | Яндекс |
| FileDescription: | YandexDiskSetup |
| FileVersion: | 3.2.30.4914 |
| InternalName: | YandexDiskSetup |
| LegalCopyright: | © 2016-2023 ООО "ЯНДЕКС" |
| OriginalFileName: | YandexDiskSetup.exe |
| ProductName: | Яндекс.Диск |
| ProductVersion: | 3.2.30.4914 |
| Tag040904B0: | - |
| Tag041F04B0: | - |
Total processes
153
Monitored processes
20
Malicious processes
4
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1040 | "C:\Users\admin\AppData\Local\Temp\O3QTKMZE4EOVT9RNVCBDUHDJXA\Clus-Blue.exe" | C:\Users\admin\AppData\Local\Temp\O3QTKMZE4EOVT9RNVCBDUHDJXA\Clus-Blue.exe | Setup.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1040 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5720 -s 640 | C:\Windows\SysWOW64\WerFault.exe | — | WB3CLQX67JBJ0EUM1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2244 | "C:\Users\admin\AppData\Local\Temp\84P40ADNQX6MLJBVE0\Clus-Blue.exe" | C:\Users\admin\AppData\Local\Temp\84P40ADNQX6MLJBVE0\Clus-Blue.exe | — | Setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2392 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5720 -s 596 | C:\Windows\SysWOW64\WerFault.exe | — | WB3CLQX67JBJ0EUM1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3008 | C:\ProgramData\Fidl\Clus-Blue.exe | C:\ProgramData\Fidl\Clus-Blue.exe | Clus-Blue.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4040 | "C:\ProgramData\Fidl\360Tray.exe" "C:\ProgramData\Fidl\360Tray.exe" /onui | C:\ProgramData\Fidl\360Tray.exe | — | Clus-Blue.exe | |||||||||||
User: admin Company: 360.cn Integrity Level: MEDIUM Description: 360安全卫士 安全防护中心模块 Exit code: 0 Version: 12, 0, 0, 1761 Modules
| |||||||||||||||
| 4488 | "C:\Users\admin\AppData\Local\Temp\1T9VRPYAY297LOAAL3I8F3H9KUEN1HT.exe" | C:\Users\admin\AppData\Local\Temp\1T9VRPYAY297LOAAL3I8F3H9KUEN1HT.exe | — | Setup.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Autostart program viewer Exit code: 0 Version: 14.09 Modules
| |||||||||||||||
| 4776 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Яндекс Integrity Level: MEDIUM Description: YandexDiskSetup Exit code: 0 Version: 3.2.30.4914 Modules
| |||||||||||||||
| 4996 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\SysWOW64\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5228 | "C:\Users\admin\AppData\Local\Temp\JB0EEJU1TROISKQGDPSCHWFG83R3.exe" | C:\Users\admin\AppData\Local\Temp\JB0EEJU1TROISKQGDPSCHWFG83R3.exe | Setup.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Autostart program viewer Version: 14.09 Modules
| |||||||||||||||
Total events
2 779
Read events
2 774
Write events
5
Delete events
0
Modification events
| (PID) Process: | (5228) JB0EEJU1TROISKQGDPSCHWFG83R3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Autoruns |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (4488) 1T9VRPYAY297LOAAL3I8F3H9KUEN1HT.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Autoruns |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (5228) JB0EEJU1TROISKQGDPSCHWFG83R3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Safari |
Value: C:\ProgramData\Safari\Safari.exe | |||
| (PID) Process: | (4996) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
Executable files
45
Suspicious files
12
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4776 | Setup.exe | C:\Users\admin\AppData\Local\Temp\O3QTKMZE4EOVT9RNVCBDUHDJXA\Qt5Network.dll | executable | |
MD5:D73AA4F8749269D1590541E567387489 | SHA256:7BFDFED166846921DAB87D51CA9B338C1FDD7F96C117E3BA0EDC07ED06DD9CB1 | |||
| 4776 | Setup.exe | C:\Users\admin\AppData\Local\Temp\O3QTKMZE4EOVT9RNVCBDUHDJXA\msvcr120.dll | executable | |
MD5:AEB29CCC27E16C4FD223A00189B44524 | SHA256:D28C7AB34842B6149609BD4E6B566DDAB8B891F0D5062480A253EF20A6A2CAAA | |||
| 4776 | Setup.exe | C:\Users\admin\AppData\Local\Temp\O3QTKMZE4EOVT9RNVCBDUHDJXA\Qt5Gui.dll | executable | |
MD5:72AC63E9E9F015D6471DDE58297A4FC6 | SHA256:6B8A49B6B37D69213762C8F2C8A9970014364F4055F08A850D27C0343FBE00DE | |||
| 4776 | Setup.exe | C:\Users\admin\AppData\Local\Temp\O3QTKMZE4EOVT9RNVCBDUHDJXA\Qt5Core.dll | executable | |
MD5:5AF1A8D3E720C2ECD7C835510429DA9F | SHA256:45A830C44F93ABA5658E5E9697DE42B3F3EB383BBBF174ADE65A78F9A6C7D8B2 | |||
| 4776 | Setup.exe | C:\Users\admin\AppData\Local\Temp\O3QTKMZE4EOVT9RNVCBDUHDJXA\Lab.cum | binary | |
MD5:7CB269327E0287F8258AB2A1B4735207 | SHA256:2ABC5BD527D19B41EE95A26DAD8D77E292FC5152A141BCDBF588C5D3433C02D8 | |||
| 4776 | Setup.exe | C:\Users\admin\AppData\Local\Temp\O3QTKMZE4EOVT9RNVCBDUHDJXA\Kingfrae.srze | binary | |
MD5:FA90A001C2F9BDC09DF22B6A8106FEA3 | SHA256:F957352080219828DCBC012B60736C624D7340D6CEEE97AABB5C505B68F3694B | |||
| 4776 | Setup.exe | C:\Users\admin\AppData\Local\Temp\O3QTKMZE4EOVT9RNVCBDUHDJXA\libssl-1_1-x64.dll | executable | |
MD5:2574E9E3159CD45194EAC2591EADC73A | SHA256:2D7208FAE6767F5F01664448F4EA89C8009F75DB4C20FECDEA508A498A6A1223 | |||
| 4776 | Setup.exe | C:\Users\admin\AppData\Local\Temp\O3QTKMZE4EOVT9RNVCBDUHDJXA\libcurl.dll | executable | |
MD5:1824EC8765523B8BBC77B14F665F842A | SHA256:FBADEDE08DFCBC8871C1BD2027A73F3AAC74B3A8247240ED315CCCABC3363F20 | |||
| 4776 | Setup.exe | C:\Users\admin\AppData\Local\Temp\O3QTKMZE4EOVT9RNVCBDUHDJXA\Clus-Blue.exe | executable | |
MD5:20BC61AA222AA74059F4D42872A76EB5 | SHA256:B1465F5CE1D0F83EF9B6086C81D8788B50C09BD329374BD3D04DC61807551435 | |||
| 1040 | Clus-Blue.exe | C:\ProgramData\Fidl\Lab.cum | binary | |
MD5:7CB269327E0287F8258AB2A1B4735207 | SHA256:2ABC5BD527D19B41EE95A26DAD8D77E292FC5152A141BCDBF588C5D3433C02D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
35
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.185:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.185:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
780 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
780 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.185:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.185:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4776 | Setup.exe | 172.67.204.131:443 | nodepathr.run | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nodepathr.run |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |