| File name: | 776ce2dc0c7d5950d6dc9a461838eeac.rtf |
| Full analysis: | https://app.any.run/tasks/7164f02d-648f-408d-bea8-3bba64a6ffff |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | March 22, 2019, 08:25:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, unknown version |
| MD5: | 776CE2DC0C7D5950D6DC9A461838EEAC |
| SHA1: | 5775E6FFD51AE87A009C1EFCF4A74F558DA47FC2 |
| SHA256: | DAEDA31C5360ADD69095BBA019D41588A73129E44158478D1E9C084507BB9AB2 |
| SSDEEP: | 3072:nhjjjjvvEmjlZiYC89dKtvTaCyo9ZDeFyz:nhjjjjvMmCmiFNyo9NEyz |
MALICIOUS
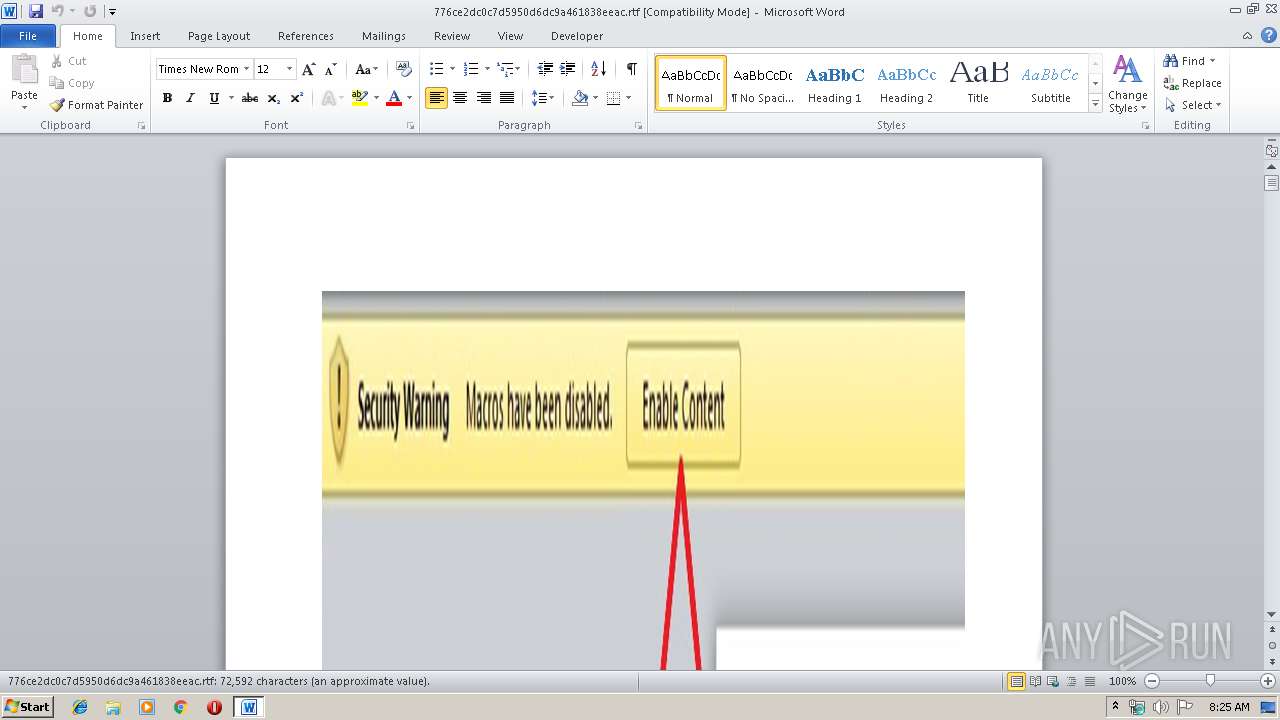
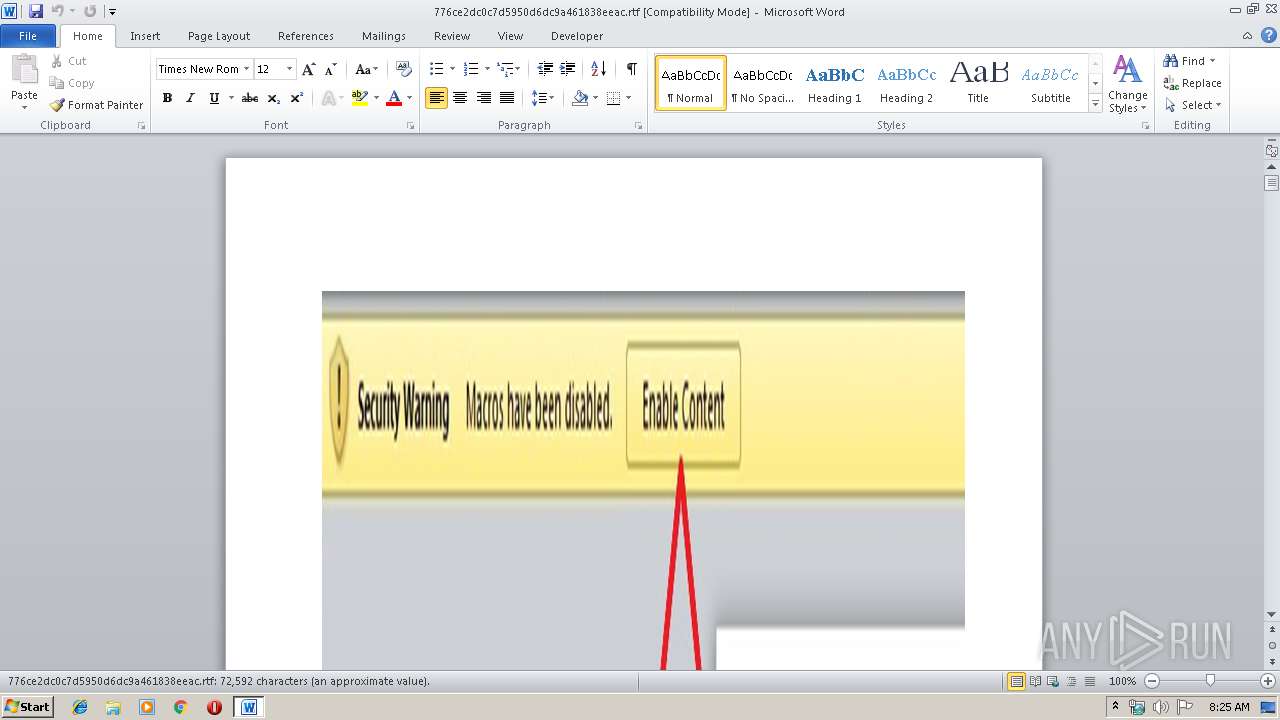
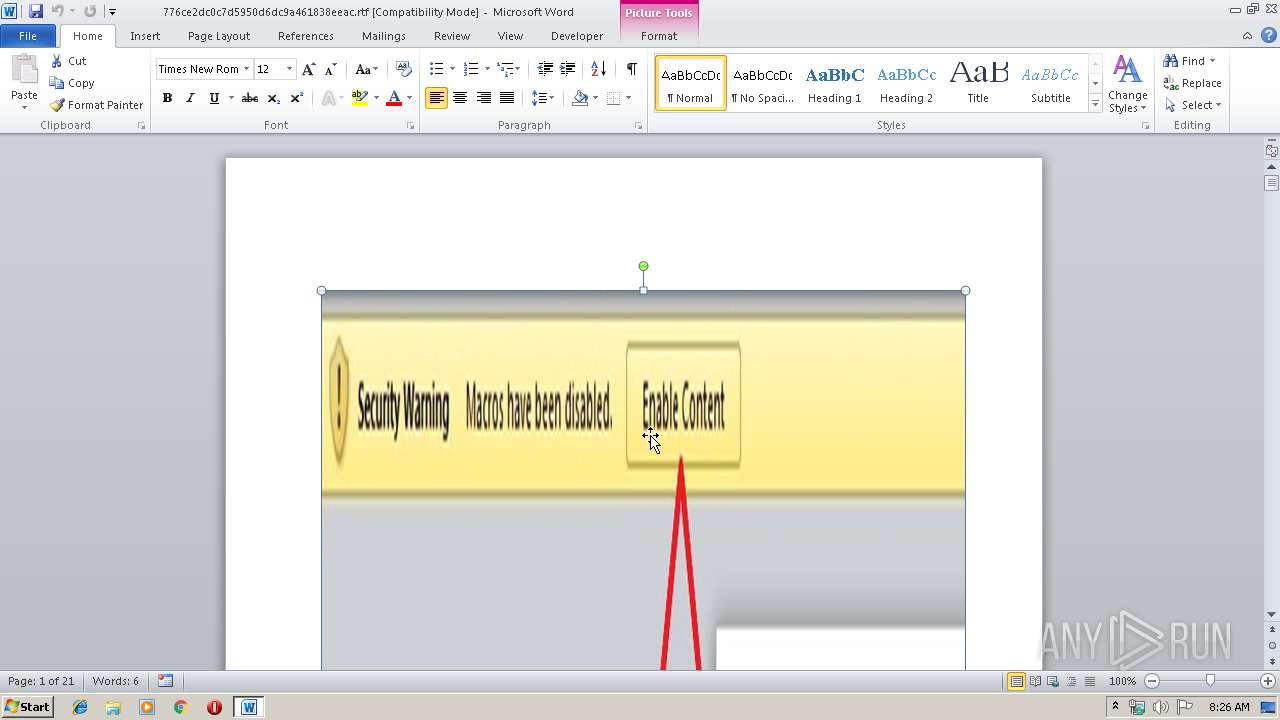
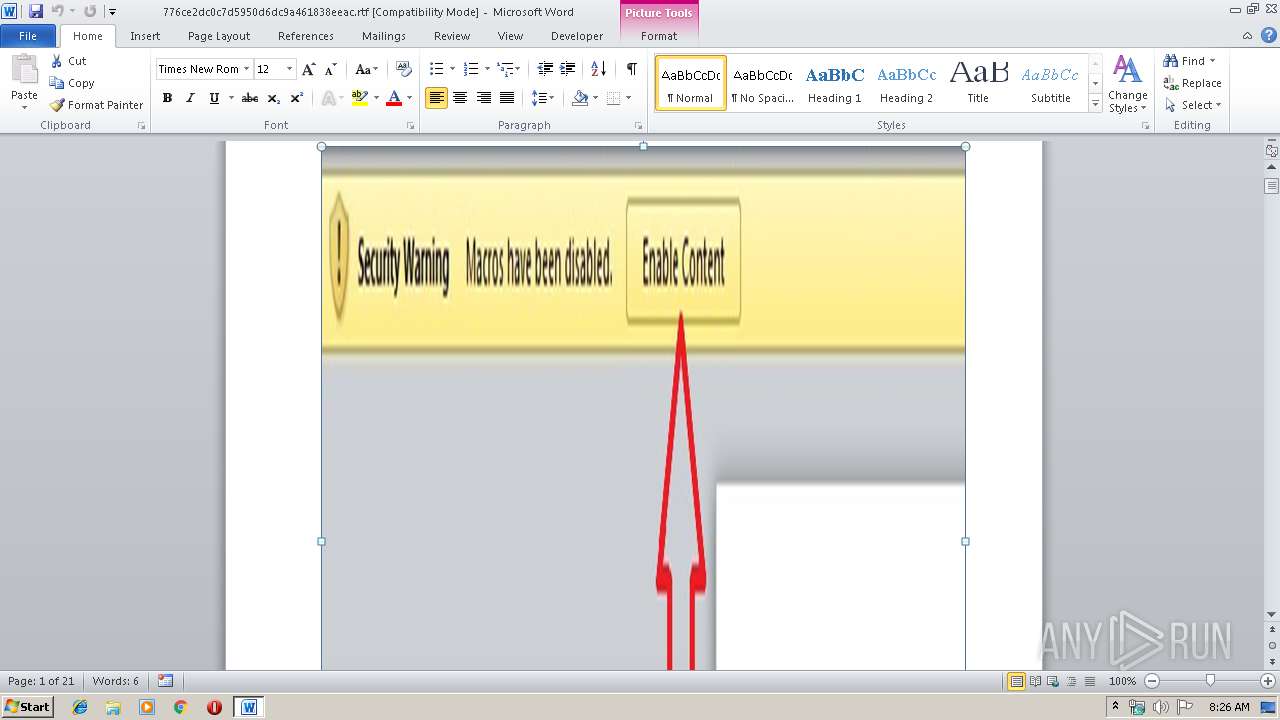
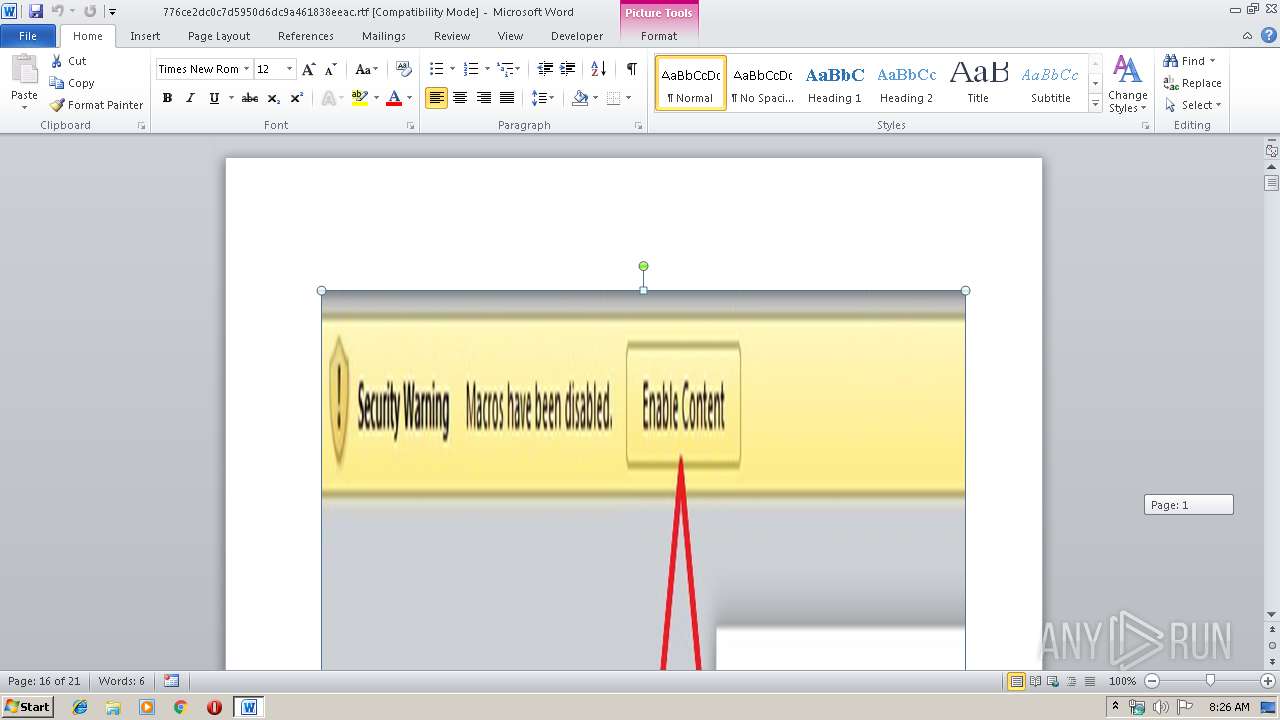
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 3500)
Suspicious connection from the Equation Editor
- EQNEDT32.EXE (PID: 3500)
Application was dropped or rewritten from another process
- 3.exe (PID: 3828)
- tgem.exe (PID: 3836)
- tgem.exe (PID: 936)
Downloads executable files from the Internet
- EQNEDT32.EXE (PID: 3500)
Downloads executable files with a strange extension
- EQNEDT32.EXE (PID: 3500)
Changes the autorun value in the registry
- raserver.exe (PID: 3304)
Formbook was detected
- raserver.exe (PID: 3304)
- Firefox.exe (PID: 2676)
Actions looks like stealing of personal data
- raserver.exe (PID: 3304)
FORMBOOK was detected
- explorer.exe (PID: 2036)
Connects to CnC server
- explorer.exe (PID: 2036)
Stealing of credential data
- raserver.exe (PID: 3304)
SUSPICIOUS
Creates files in the user directory
- EQNEDT32.EXE (PID: 3500)
- 3.exe (PID: 3828)
- raserver.exe (PID: 3304)
Executable content was dropped or overwritten
- EQNEDT32.EXE (PID: 3500)
- 3.exe (PID: 3828)
Starts itself from another location
- 3.exe (PID: 3828)
Application launched itself
- tgem.exe (PID: 3836)
Loads DLL from Mozilla Firefox
- raserver.exe (PID: 3304)
INFO
Starts Microsoft Office Application
- explorer.exe (PID: 2036)
Creates files in the user directory
- WINWORD.EXE (PID: 2684)
- Firefox.exe (PID: 2676)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
Total processes
37
Monitored processes
8
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 936 | "C:\Users\admin\AppData\Roaming\exp\tgem.exe" | C:\Users\admin\AppData\Roaming\exp\tgem.exe | — | tgem.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2036 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2676 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | raserver.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 65.0.2 Modules
| |||||||||||||||
| 2684 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\776ce2dc0c7d5950d6dc9a461838eeac.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3304 | "C:\Windows\System32\raserver.exe" | C:\Windows\System32\raserver.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Remote Assistance COM Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3500 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 3828 | C:\Users\Public\3.exe | C:\Users\Public\3.exe | EQNEDT32.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3836 | "C:\Users\admin\AppData\Roaming\exp\tgem.exe" | C:\Users\admin\AppData\Roaming\exp\tgem.exe | — | 3.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 388
Read events
754
Write events
629
Delete events
5
Modification events
| (PID) Process: | (2684) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | qz: |
Value: 717A3A007C0A0000010000000000000000000000 | |||
| (PID) Process: | (2684) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2684) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2684) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1316356126 | |||
| (PID) Process: | (2684) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1316356240 | |||
| (PID) Process: | (2684) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1316356241 | |||
| (PID) Process: | (2684) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 7C0A000020BEEBCD88E0D40100000000 | |||
| (PID) Process: | (2684) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | :|: |
Value: 3A7C3A007C0A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2684) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | :|: |
Value: 3A7C3A007C0A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2684) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
3
Suspicious files
73
Text files
2
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2684 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRFAF1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3828 | 3.exe | C:\Users\admin\AppData\Roaming\exp\tgem.exe:ZoneIdentifier | — | |
MD5:— | SHA256:— | |||
| 2684 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$6ce2dc0c7d5950d6dc9a461838eeac.rtf | pgc | |
MD5:— | SHA256:— | |||
| 3500 | EQNEDT32.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\974103[1].png | executable | |
MD5:— | SHA256:— | |||
| 2684 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3500 | EQNEDT32.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@bit[1].txt | text | |
MD5:— | SHA256:— | |||
| 3500 | EQNEDT32.EXE | C:\Users\Public\3.exe | executable | |
MD5:— | SHA256:— | |||
| 3304 | raserver.exe | C:\Users\admin\AppData\Roaming\992307UE\992logrc.ini | binary | |
MD5:— | SHA256:— | |||
| 2676 | Firefox.exe | C:\Users\admin\AppData\Roaming\992307UE\992logrf.ini | binary | |
MD5:— | SHA256:— | |||
| 3304 | raserver.exe | C:\Users\admin\AppData\Roaming\992307UE\992logim.jpeg | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
22
DNS requests
15
Threats
40
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2036 | explorer.exe | GET | — | 59.188.180.242:80 | http://www.biyoush.com/de/?BRQl=WfAzN30z9ZDmcmyMecoHEEMLRwJiUWYXMq46VJt3j1q251VXopOhU0G3WMJmCm8mwvUzng==&VP3DU=ljndSP_H1468qfM&sql=1 | HK | — | — | malicious |
2036 | explorer.exe | GET | 301 | 92.53.96.162:80 | http://www.selenga.info/de/?BRQl=lkKs2hRge4PG2gZ7pwtBEGur8OW6vrVfGY3Dio+a+j4uQPJThWZVXFm+XawyVZo+l3ep0A==&VP3DU=ljndSP_H1468qfM&sql=1 | RU | — | — | malicious |
2036 | explorer.exe | POST | — | 59.188.180.242:80 | http://www.biyoush.com/de/ | HK | — | — | malicious |
3500 | EQNEDT32.EXE | GET | 200 | 103.235.106.21:80 | http://joomliads.in/cgi/01/974103.png | IN | executable | 666 Kb | malicious |
3500 | EQNEDT32.EXE | GET | 301 | 67.199.248.11:80 | http://bit.ly/2TRwq4D | US | html | 124 b | shared |
2036 | explorer.exe | POST | — | 92.53.96.162:80 | http://www.selenga.info/de/ | RU | — | — | malicious |
2036 | explorer.exe | POST | — | 59.188.180.242:80 | http://www.biyoush.com/de/ | HK | — | — | malicious |
2036 | explorer.exe | POST | — | 92.53.96.162:80 | http://www.selenga.info/de/ | RU | — | — | malicious |
2036 | explorer.exe | POST | — | 92.53.96.162:80 | http://www.selenga.info/de/ | RU | — | — | malicious |
2036 | explorer.exe | GET | 302 | 23.20.239.12:80 | http://www.ladybea.com/de/?BRQl=aMCh7b/NLIe4+eCZKPZcml7ljA+xibyj0QaBm5X85VeaOJGjUdqu7RuhCMNN1vMsa5pjuw==&VP3DU=ljndSP_H1468qfM&sql=1 | US | html | 204 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3500 | EQNEDT32.EXE | 103.235.106.21:80 | joomliads.in | Netmagic Datacenter Mumbai | IN | suspicious |
2036 | explorer.exe | 92.53.96.162:80 | www.selenga.info | TimeWeb Ltd. | RU | malicious |
2036 | explorer.exe | 199.192.17.204:80 | www.verdictes.com | — | US | malicious |
2036 | explorer.exe | 88.150.145.167:80 | www.yogainstructorguide.com | iomart Cloud Services Limited. | GB | malicious |
3500 | EQNEDT32.EXE | 67.199.248.11:80 | bit.ly | Bitly Inc | US | shared |
2036 | explorer.exe | 59.188.180.242:80 | www.biyoush.com | AS number for New World Telephone Ltd. | HK | malicious |
2036 | explorer.exe | 23.20.239.12:80 | www.ladybea.com | Amazon.com, Inc. | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bit.ly |
| shared |
joomliads.in |
| malicious |
www.biyoush.com |
| malicious |
www.nemotoystore.com |
| unknown |
www.apptraffictoupgradingall.win |
| unknown |
www.us-limited-account.com |
| unknown |
www.speedy-music.com |
| unknown |
www.selenga.info |
| malicious |
www.ladybea.com |
| shared |
www.verdictes.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3500 | EQNEDT32.EXE | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |
3500 | EQNEDT32.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3500 | EQNEDT32.EXE | A Network Trojan was detected | ET TROJAN JS/WSF Downloader Dec 08 2016 M4 |
3500 | EQNEDT32.EXE | A Network Trojan was detected | ET TROJAN Windows Executable Downloaded With Image Content-Type Header |
3500 | EQNEDT32.EXE | Misc activity | SUSPICIOUS [PTsecurity] PE as Image Content type mismatch |
3500 | EQNEDT32.EXE | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
2036 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
2036 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
2036 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
2036 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
15 ETPRO signatures available at the full report