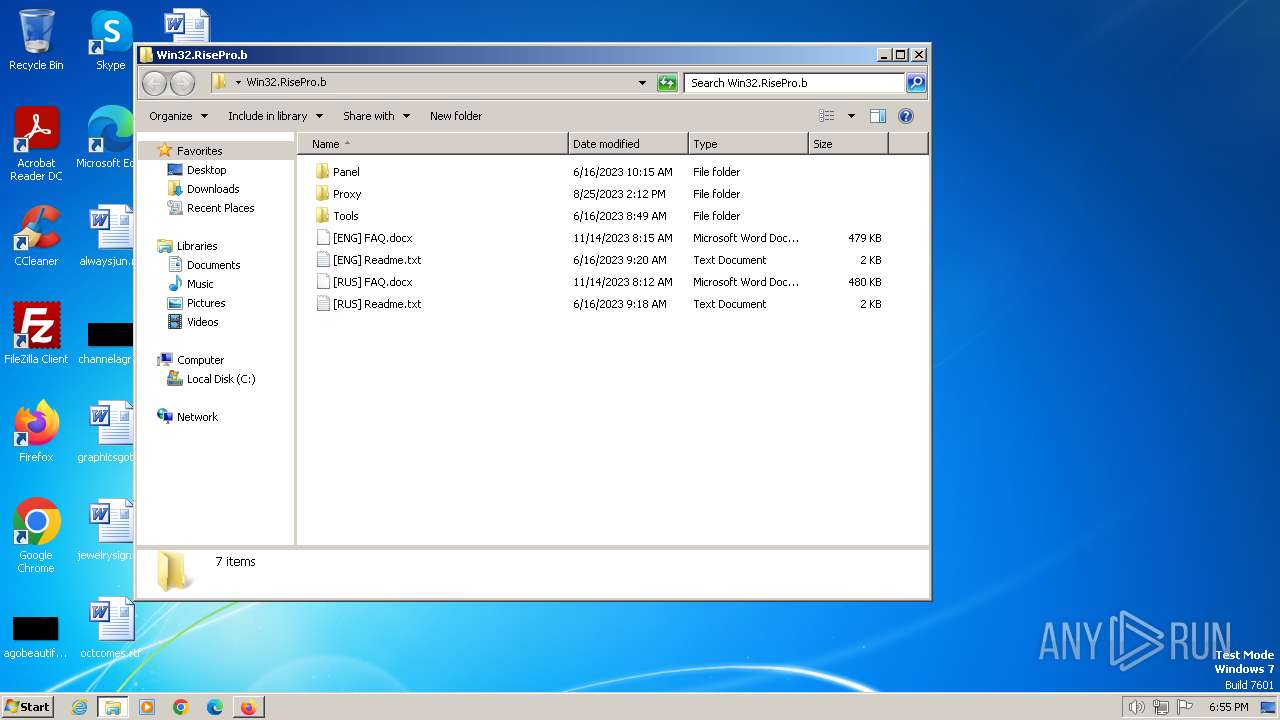
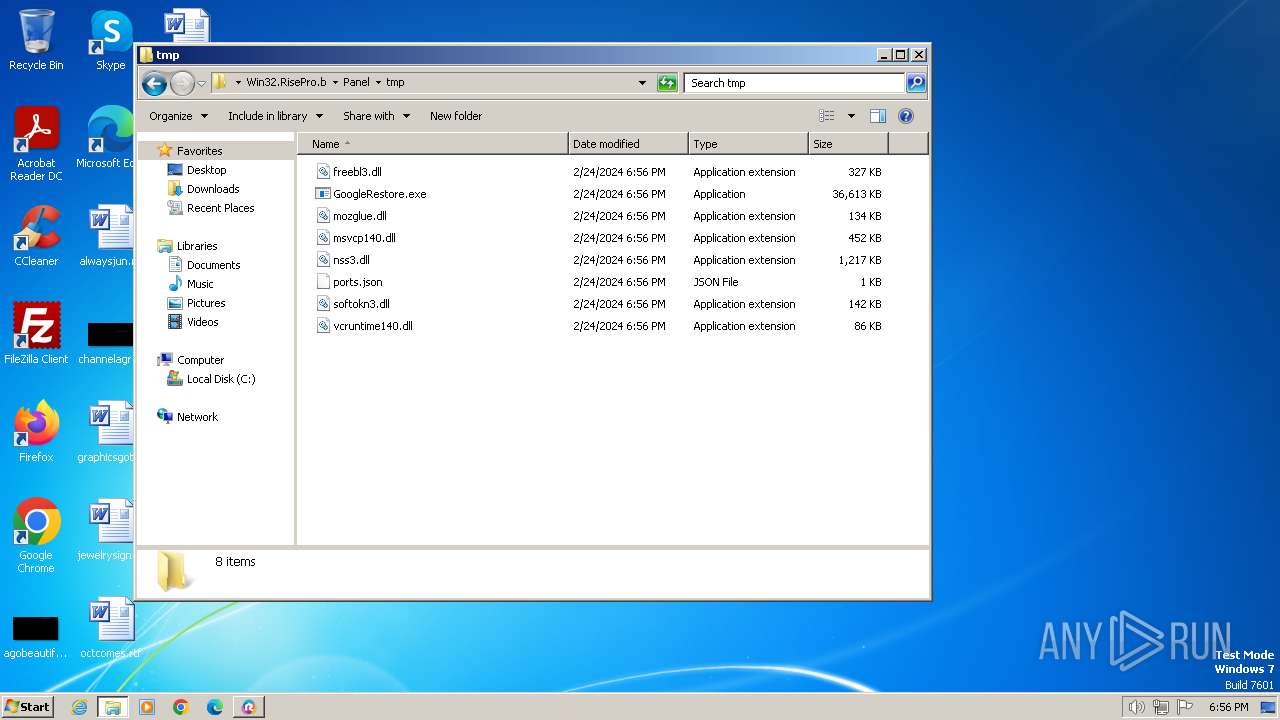
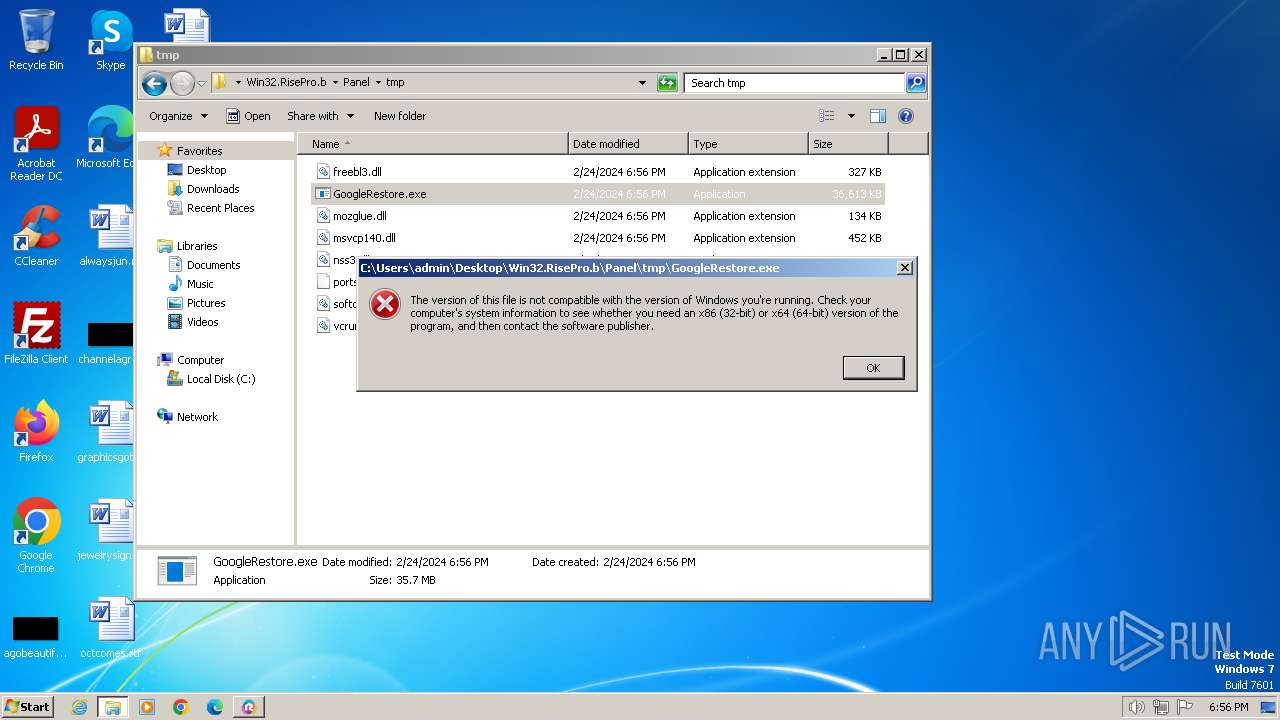
| URL: | https://samples.vx-underground.org/Archive/Builders/Win32.RisePro.b.7z |
| Full analysis: | https://app.any.run/tasks/eed19d81-5e9a-4bf5-9b36-9d81bfab5dfb |
| Verdict: | Malicious activity |
| Threats: | RisePro, an information-stealing malware, targets a wide range of sensitive data, including credit cards, passwords, and cryptocurrency wallets. By compromising infected devices, RisePro can steal valuable information and potentially cause significant financial and personal losses for victims. |
| Analysis date: | February 24, 2024, 18:54:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E2C1BE99C3E4EB2830E9BA0B7E622A74 |
| SHA1: | 9AE83056B8F5A3FF6C98DCB9835B0BBA0ABED3B6 |
| SHA256: | DAC5759B81EDF59A0EA61628C59A7356EA8BED937583167300AF184ABA5ACE62 |
| SSDEEP: | 3:N8JEIsGNMM8ZPM0DVI:2iDaz8Zt6 |
MALICIOUS
RISEPRO has been detected (YARA)
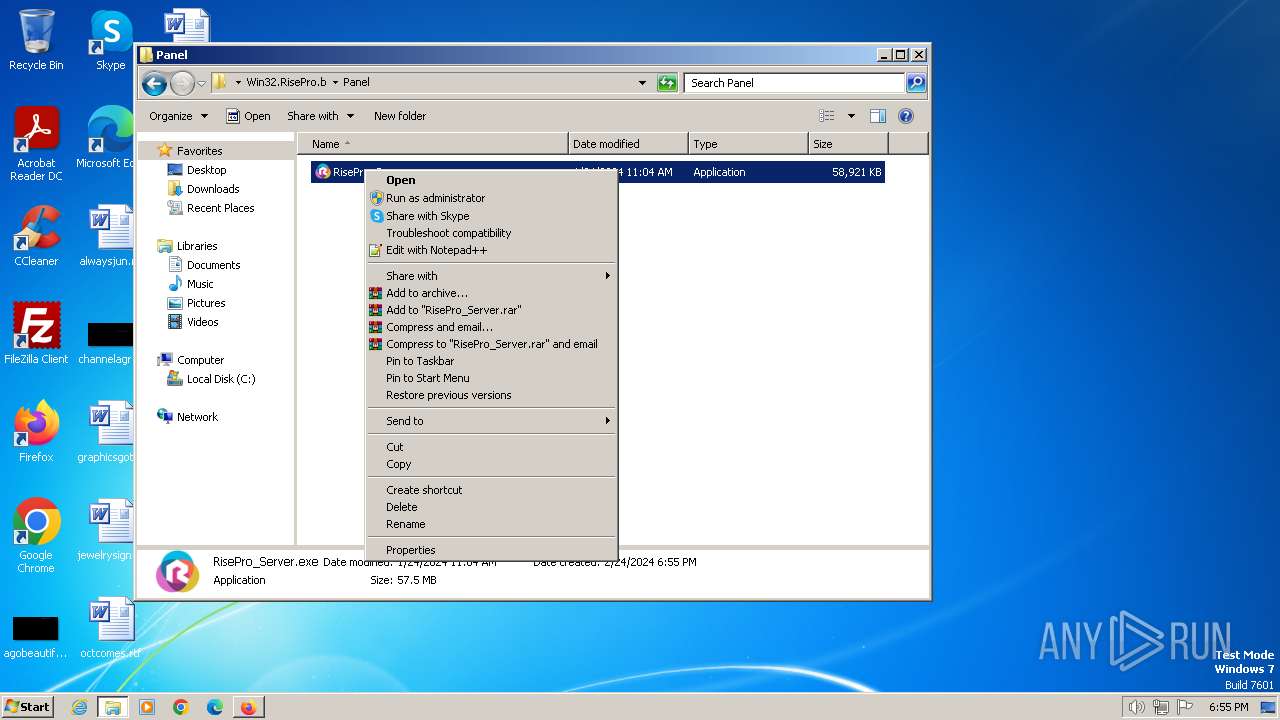
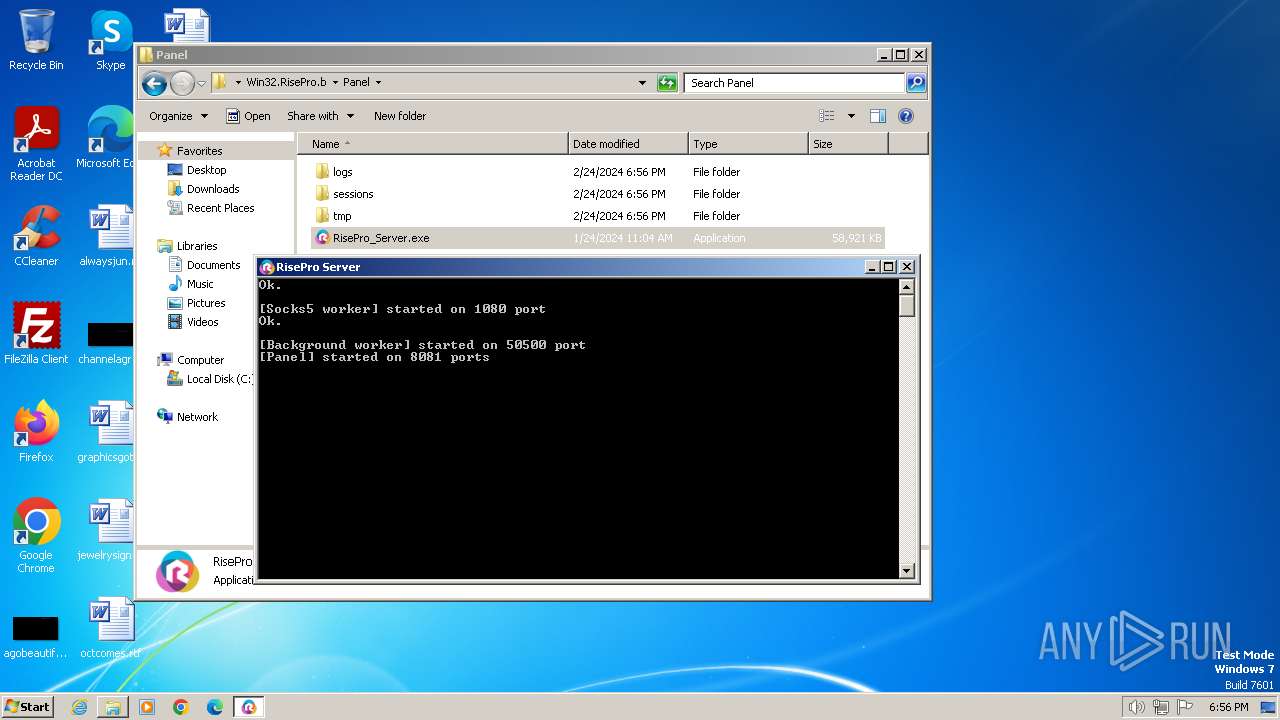
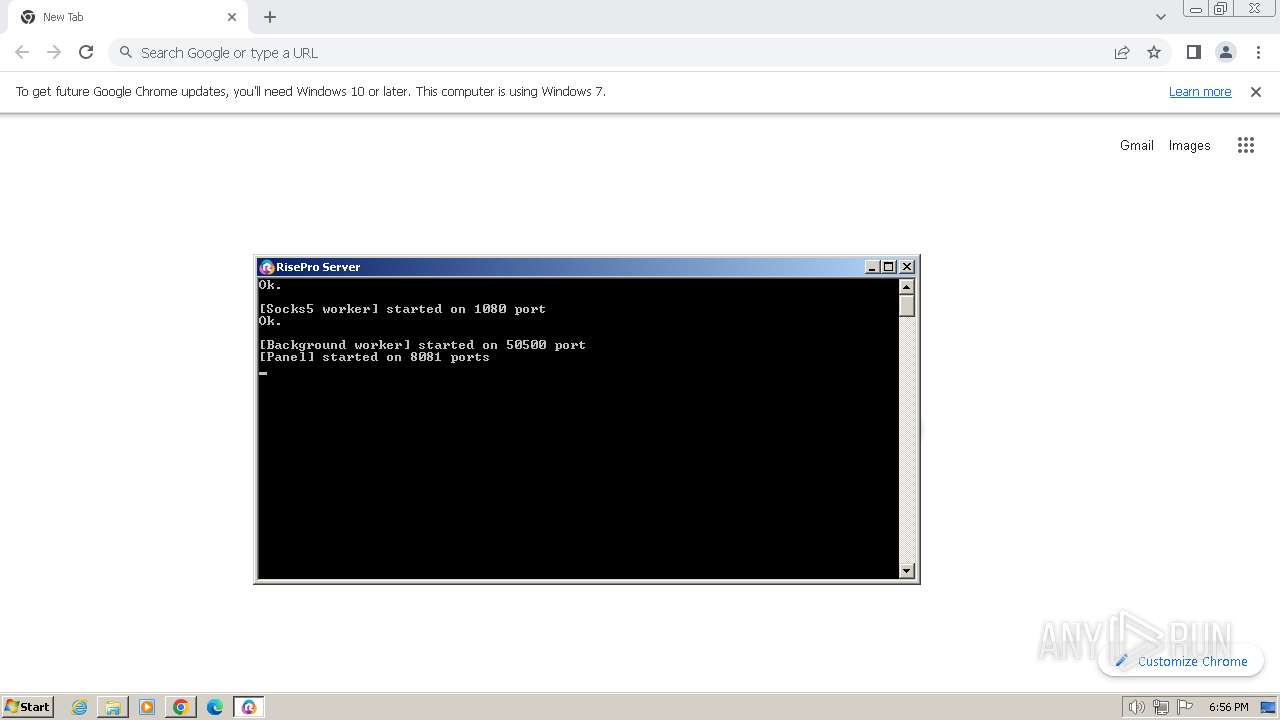
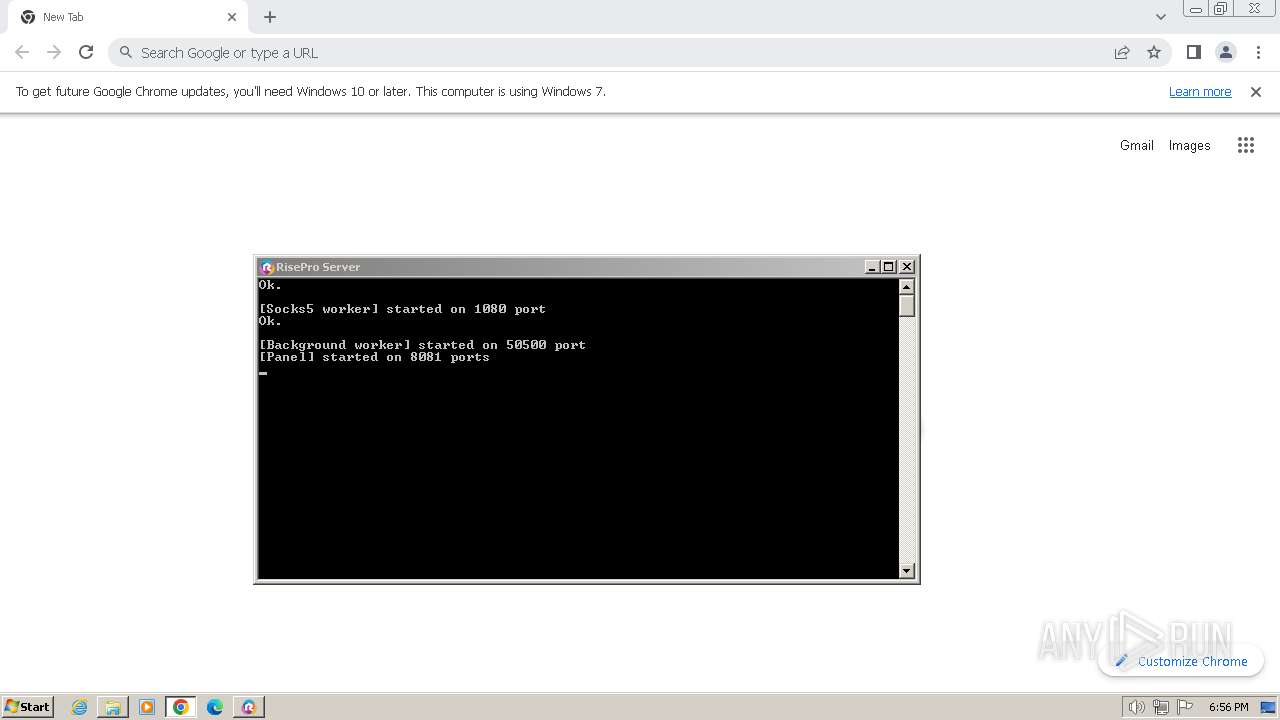
- RisePro_Server.exe (PID: 3356)
Drops the executable file immediately after the start
- RisePro_Server.exe (PID: 3356)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 752)
- RisePro_Server.exe (PID: 3356)
Starts CMD.EXE for commands execution
- RisePro_Server.exe (PID: 3356)
The process drops Mozilla's DLL files
- RisePro_Server.exe (PID: 3356)
Executable content was dropped or overwritten
- RisePro_Server.exe (PID: 3356)
The process drops C-runtime libraries
- RisePro_Server.exe (PID: 3356)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 3404)
- cmd.exe (PID: 2336)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 1000)
- cmd.exe (PID: 908)
Reads settings of System Certificates
- RisePro_Server.exe (PID: 3356)
INFO
Application launched itself
- firefox.exe (PID: 2160)
- firefox.exe (PID: 3652)
- chrome.exe (PID: 2436)
The process uses the downloaded file
- firefox.exe (PID: 3652)
- WinRAR.exe (PID: 752)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 752)
- firefox.exe (PID: 3652)
Manual execution by a user
- WinRAR.exe (PID: 752)
- RisePro_Server.exe (PID: 3356)
- chrome.exe (PID: 2436)
Executable content was dropped or overwritten
- firefox.exe (PID: 3652)
- WinRAR.exe (PID: 752)
Checks supported languages
- RisePro_Server.exe (PID: 3356)
Reads the machine GUID from the registry
- RisePro_Server.exe (PID: 3356)
Reads the software policy settings
- RisePro_Server.exe (PID: 3356)
Reads the computer name
- RisePro_Server.exe (PID: 3356)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
82
Monitored processes
39
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3732 --field-trial-handle=1188,i,14417006735389606344,3321627631789883509,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 752 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Win32.RisePro.b.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 796 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2136 --field-trial-handle=1188,i,14417006735389606344,3321627631789883509,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 848 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=1600 --field-trial-handle=1188,i,14417006735389606344,3321627631789883509,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 908 | C:\Windows\system32\cmd.exe /c netsh advfirewall firewall add rule name="RisePro External - 50500" dir=in action=allow protocol=TCP localport=50500 | C:\Windows\System32\cmd.exe | — | RisePro_Server.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 920 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=1328 --field-trial-handle=1188,i,14417006735389606344,3321627631789883509,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1000 | C:\Windows\system32\cmd.exe /c netsh advfirewall firewall add rule name="RisePro External - 1080" dir=in action=allow protocol=TCP localport=1080 | C:\Windows\System32\cmd.exe | — | RisePro_Server.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1000 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=972 --field-trial-handle=1188,i,14417006735389606344,3321627631789883509,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1572 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3652.3.191432188\1556394731" -childID 2 -isForBrowser -prefsHandle 2860 -prefMapHandle 2720 -prefsLen 34225 -prefMapSize 244195 -jsInitHandle 888 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {5765ea96-30ea-42c7-9779-a33fea630678} 3652 "\\.\pipe\gecko-crash-server-pipe.3652" 2872 169dde00 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1576 | C:\Windows\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | RisePro_Server.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
35 899
Read events
35 520
Write events
368
Delete events
11
Modification events
| (PID) Process: | (2160) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 6CE2115001000000 | |||
| (PID) Process: | (3652) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 2ECA135001000000 | |||
| (PID) Process: | (3652) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Installer\308046B0AF4A39CB |
| Operation: | delete value | Name: | installer.taskbarpin.win10.enabled |
Value: | |||
| (PID) Process: | (3652) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (3652) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (3652) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (3652) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (3652) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (3652) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (3652) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SetDefaultBrowserUserChoice |
Value: 1 | |||
Executable files
14
Suspicious files
183
Text files
98
Unknown types
148
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3652 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3652 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3652 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3652 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3652 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:B7A3C61D0C144CC5E166B1E769CA8F8C | SHA256:7FADCB77FFACA6B9E9F15C6F1CD3AAD4C20DCD90FA92429A627A3A7110CA2644 | |||
| 3652 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\activity-stream.discovery_stream.json.tmp | binary | |
MD5:7CAD2C83729A10427E4B09EF676FC1FD | SHA256:7BD059AE6272FE7789396B8EA6CBA36BB296F60FA2725F0EB86B75F1B0395964 | |||
| 3652 | firefox.exe | C:\Users\admin\Downloads\Win32.AZtKrQSC.RisePro.b.7z.part | compressed | |
MD5:9D4B0F076F1BD740FEDFE0D1350D9F40 | SHA256:C29317D30AEB22909FBFC5ADC6615E7F2E162A8DE7414EB1DB8C34FCBB3B5515 | |||
| 3652 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\protections.sqlite-journal | binary | |
MD5:6B47690EC04DDD5D34ACB70A7B6B547A | SHA256:6B2AB573BFBD2819E5FA101038269461A3DC0610BC021396C5E9FAFB80ADBDAB | |||
| 3652 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3652 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | text | |
MD5:60E0DE9E05EC76C749D80F0D15A81B21 | SHA256:08252FA62CCCCD316474E20CC7317A6B5C932B2C972234318E8CCDA39EC2EF48 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
81
DNS requests
162
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3652 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
3652 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
3652 | firefox.exe | GET | 200 | 2.22.61.59:80 | http://ciscobinary.openh264.org/openh264-win32-31c4d2e4a037526fd30d4e5c39f60885986cf865.zip | unknown | compressed | 461 Kb | unknown |
3652 | firefox.exe | POST | 200 | 95.101.54.217:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3652 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
3652 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
3652 | firefox.exe | POST | 200 | 95.101.54.217:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3652 | firefox.exe | POST | 200 | 95.101.54.145:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3652 | firefox.exe | POST | 200 | 95.101.54.145:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3652 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3652 | firefox.exe | 104.18.6.192:443 | samples.vx-underground.org | CLOUDFLARENET | — | shared |
3652 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
3652 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
3652 | firefox.exe | 95.101.54.145:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
3652 | firefox.exe | 34.117.188.166:443 | spocs.getpocket.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
3652 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | unknown |
3652 | firefox.exe | 142.250.185.202:443 | safebrowsing.googleapis.com | GOOGLE | US | whitelisted |
3652 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
samples.vx-underground.org |
| malicious |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
spocs.getpocket.com |
| shared |
ipv4only.arpa |
| whitelisted |
gkegw.prod.ads.prod.webservices.mozgcp.net |
| unknown |
r3.o.lencr.org |
| shared |
firefox.settings.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3060 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
3060 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |