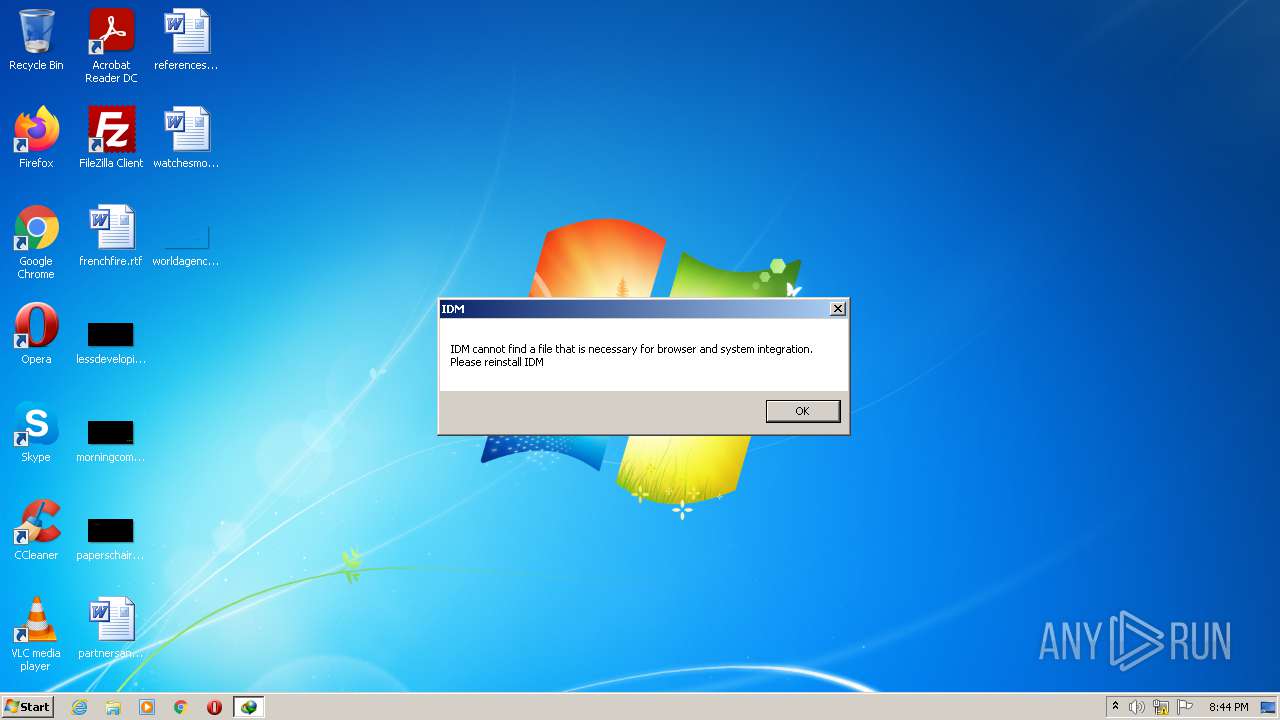
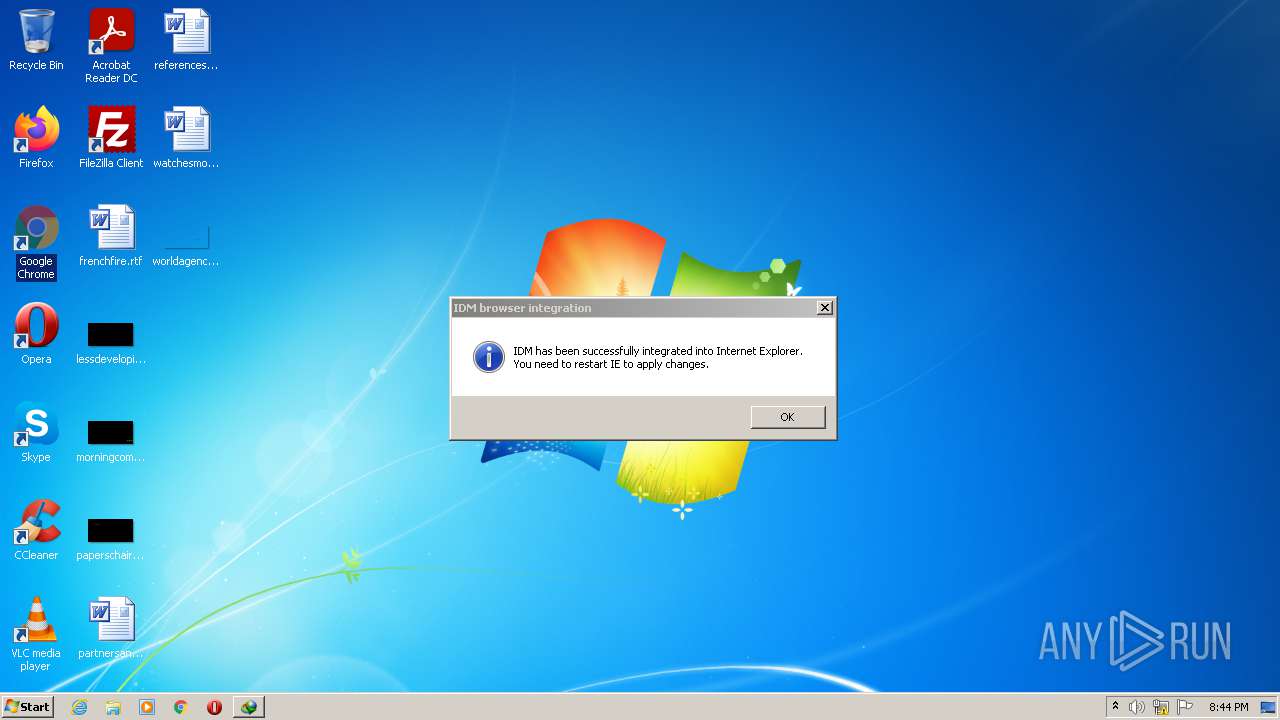
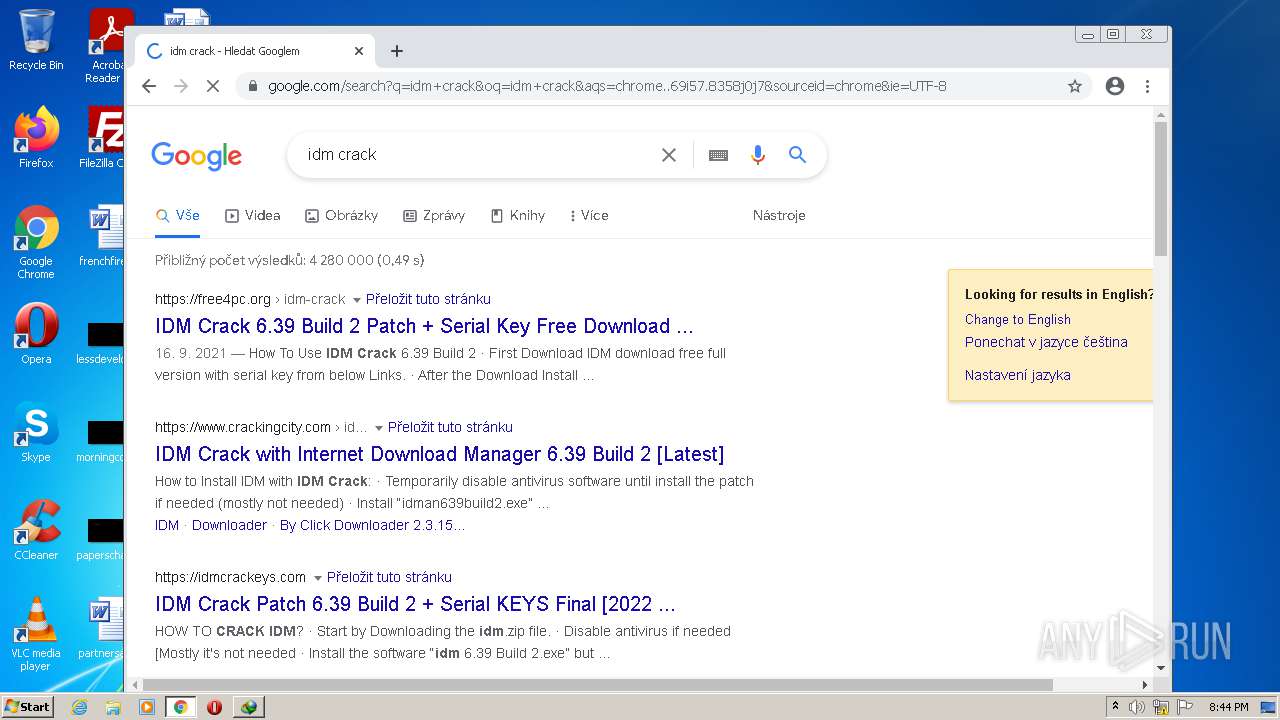
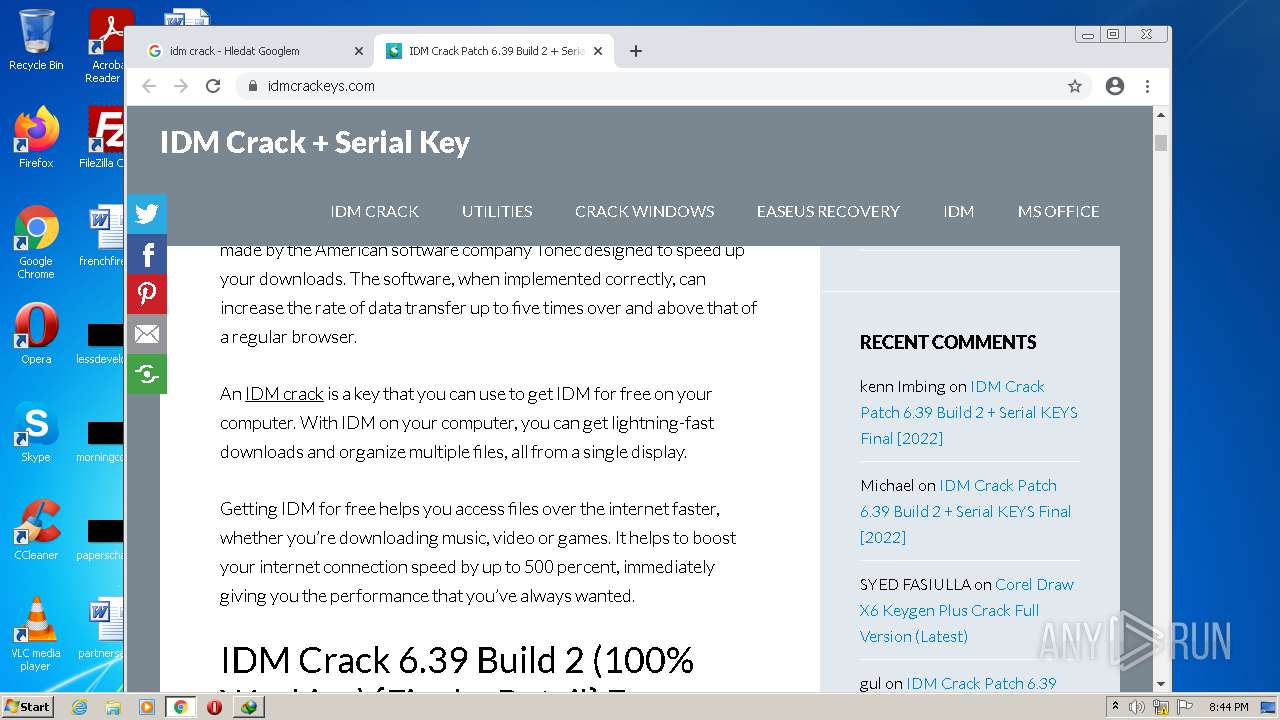
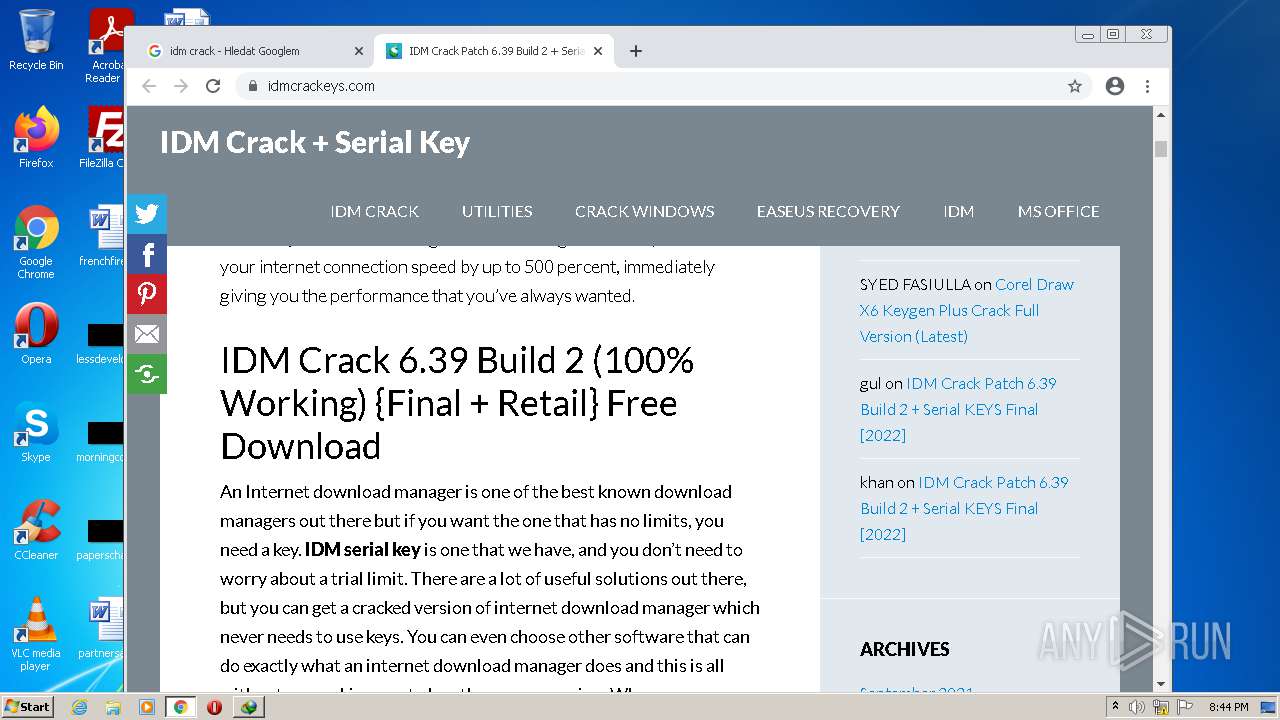
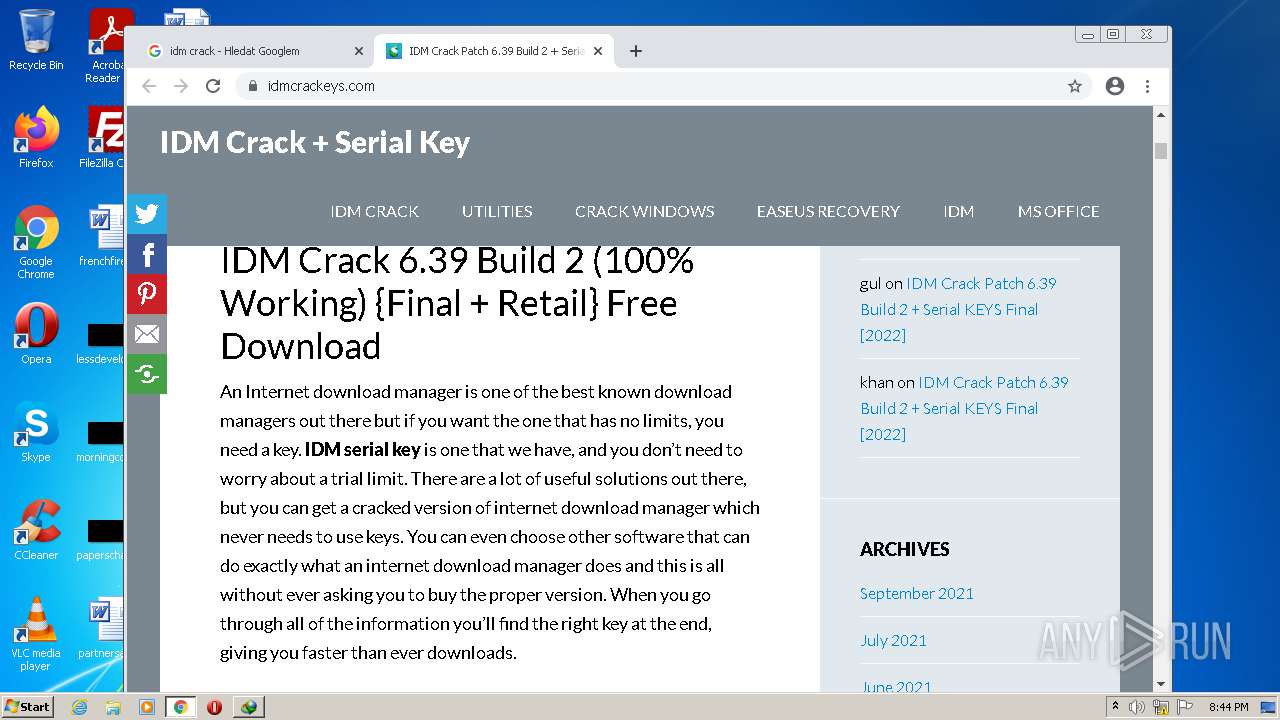
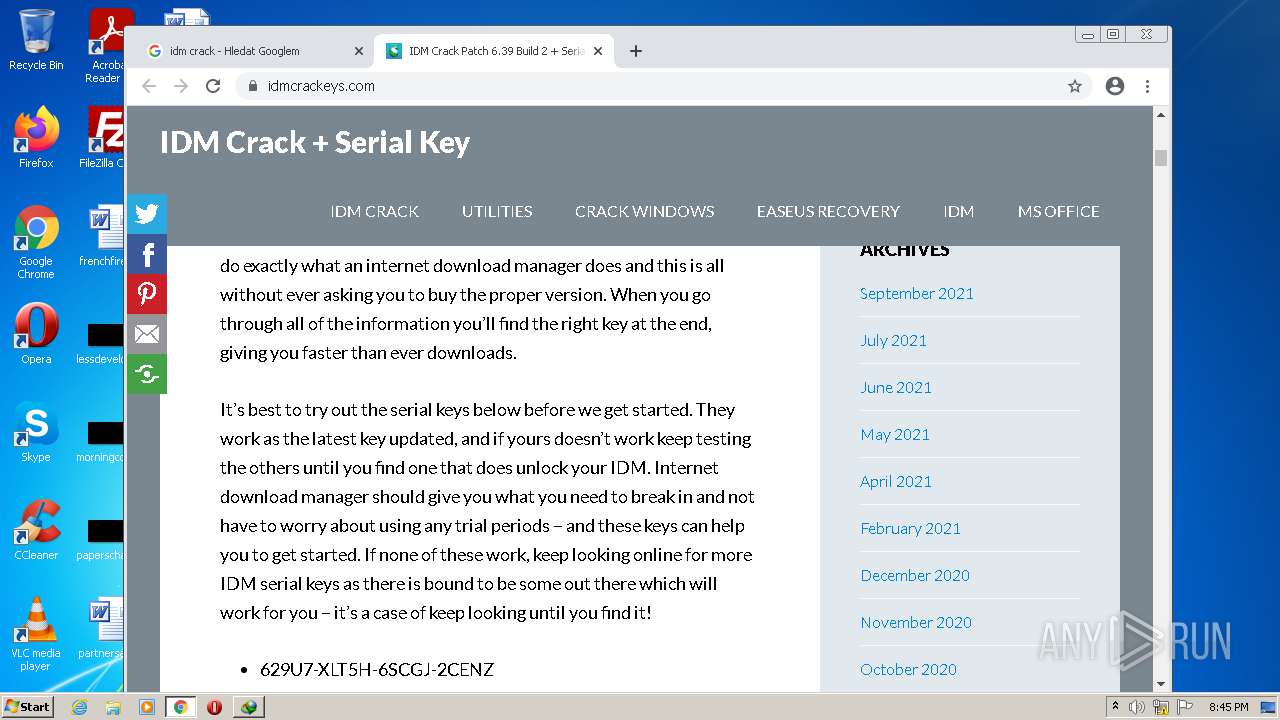
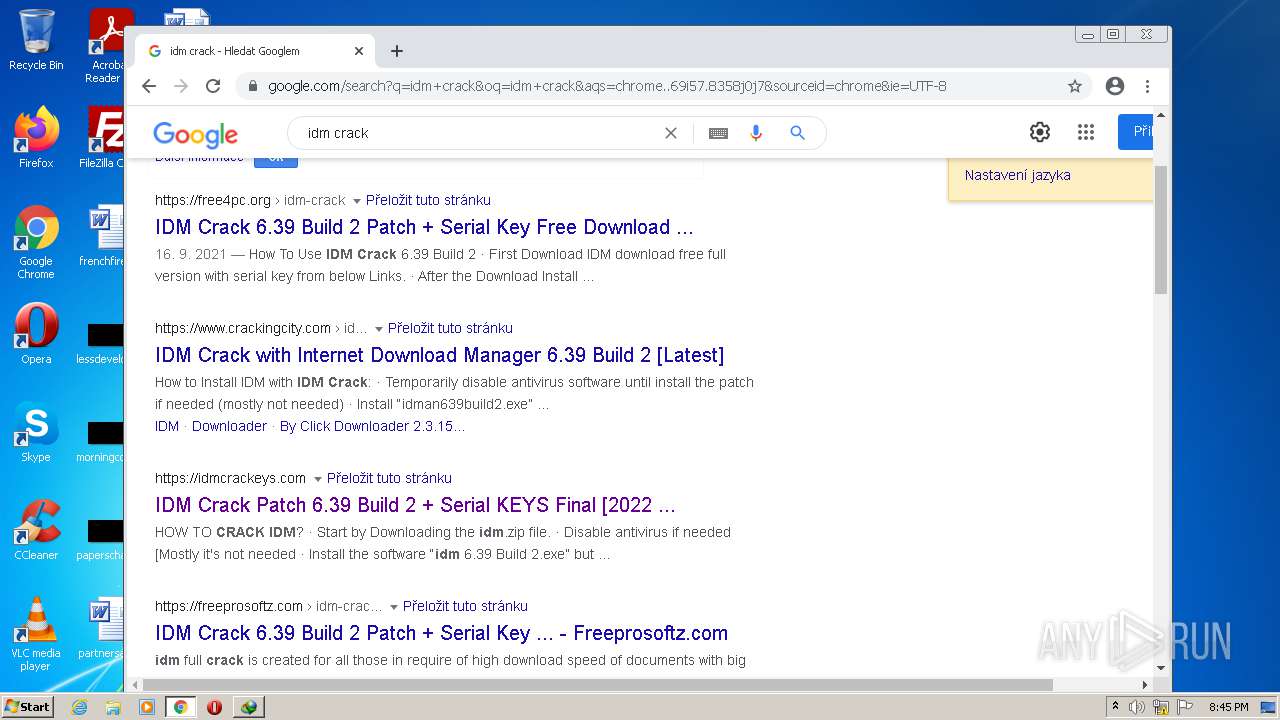
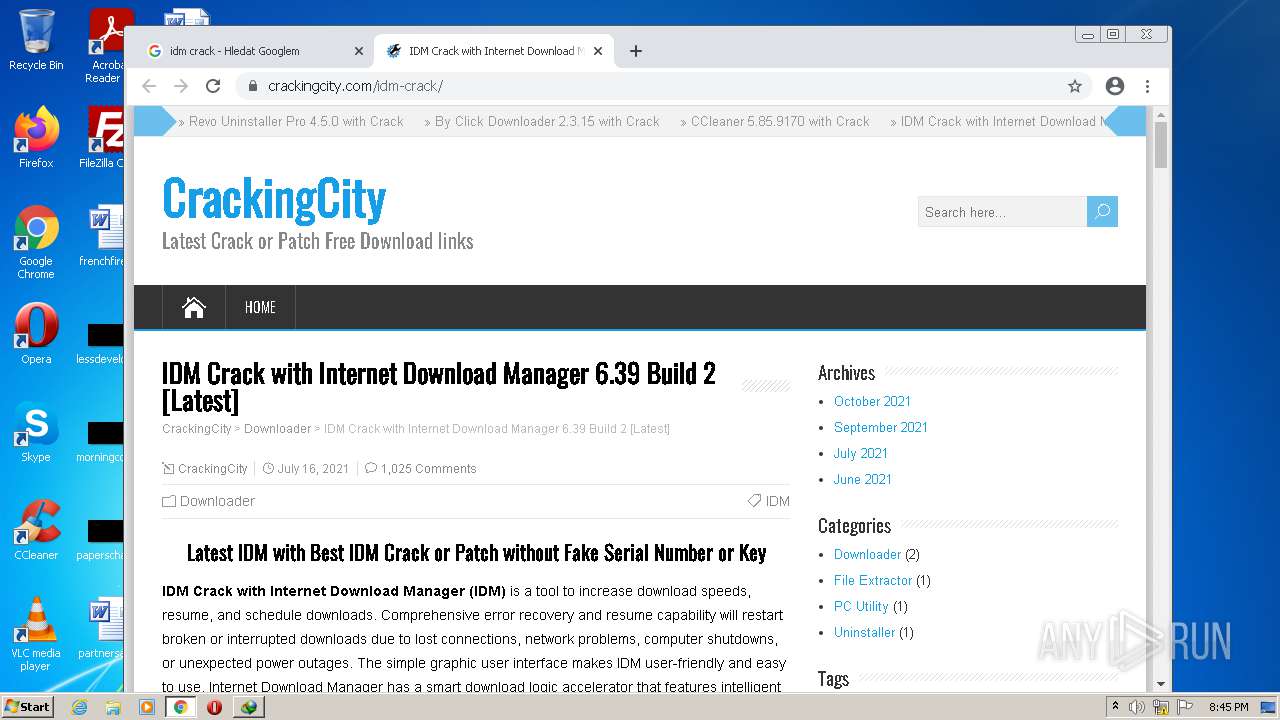
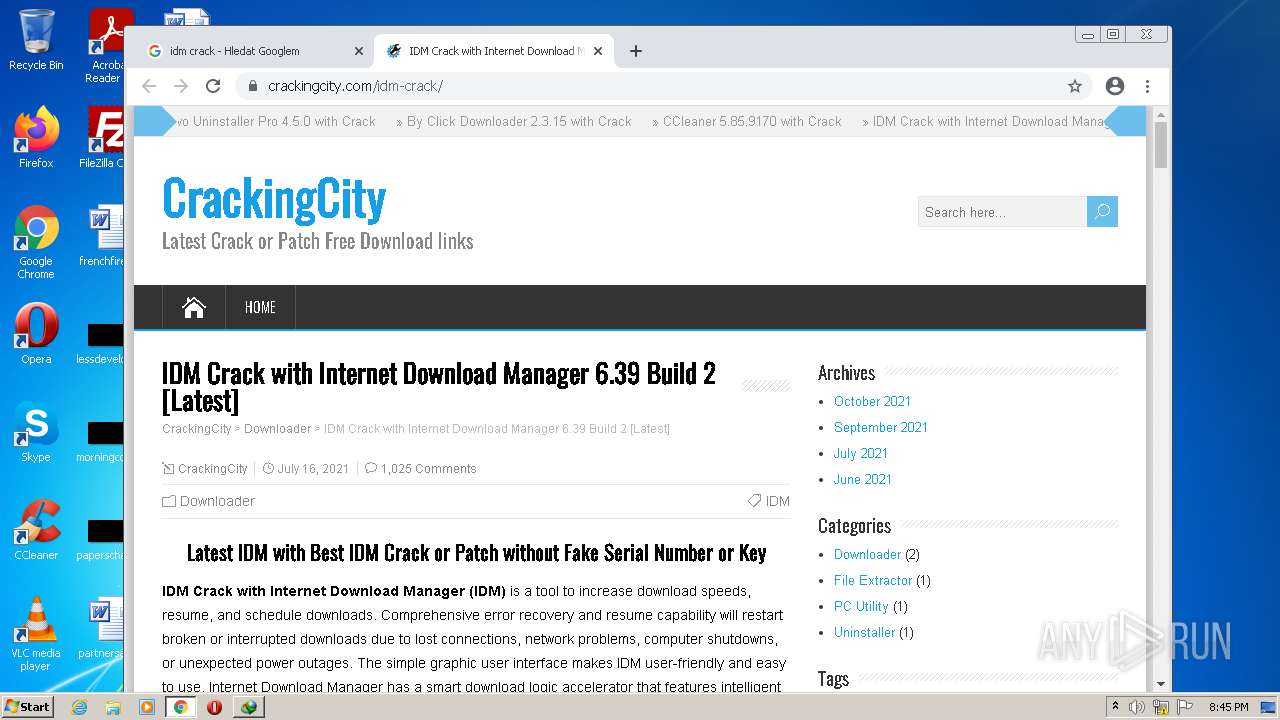
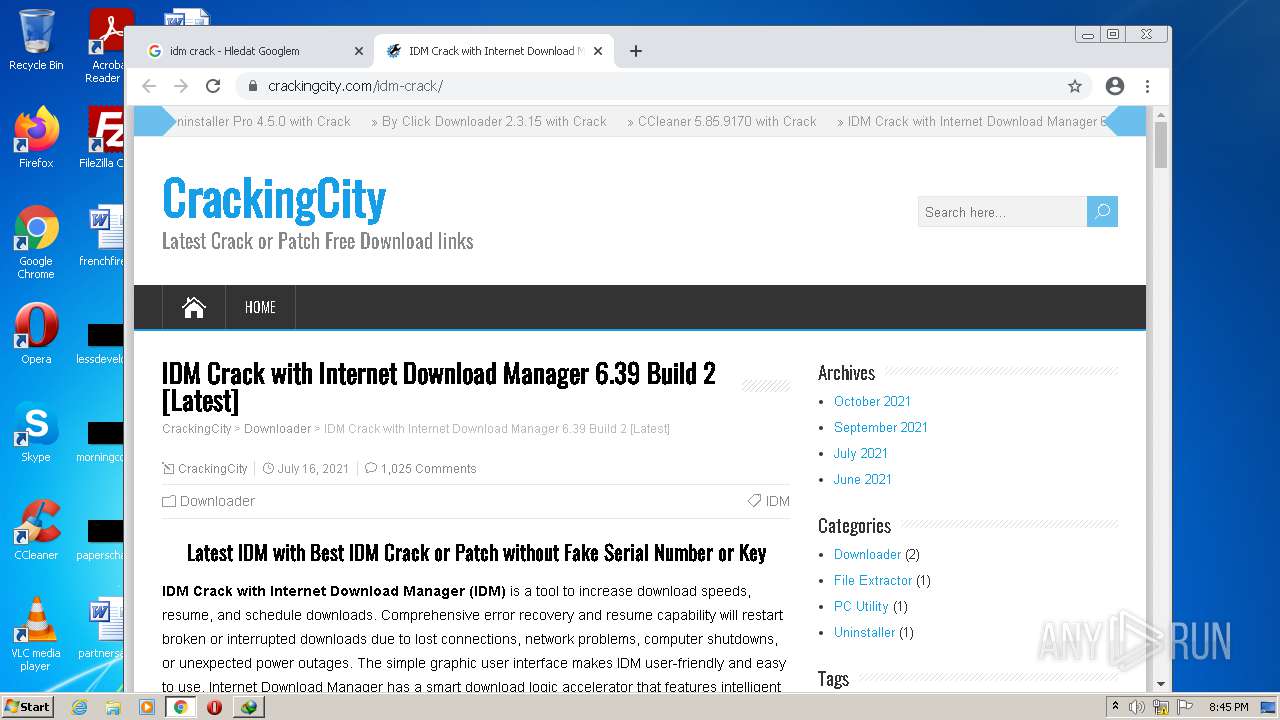
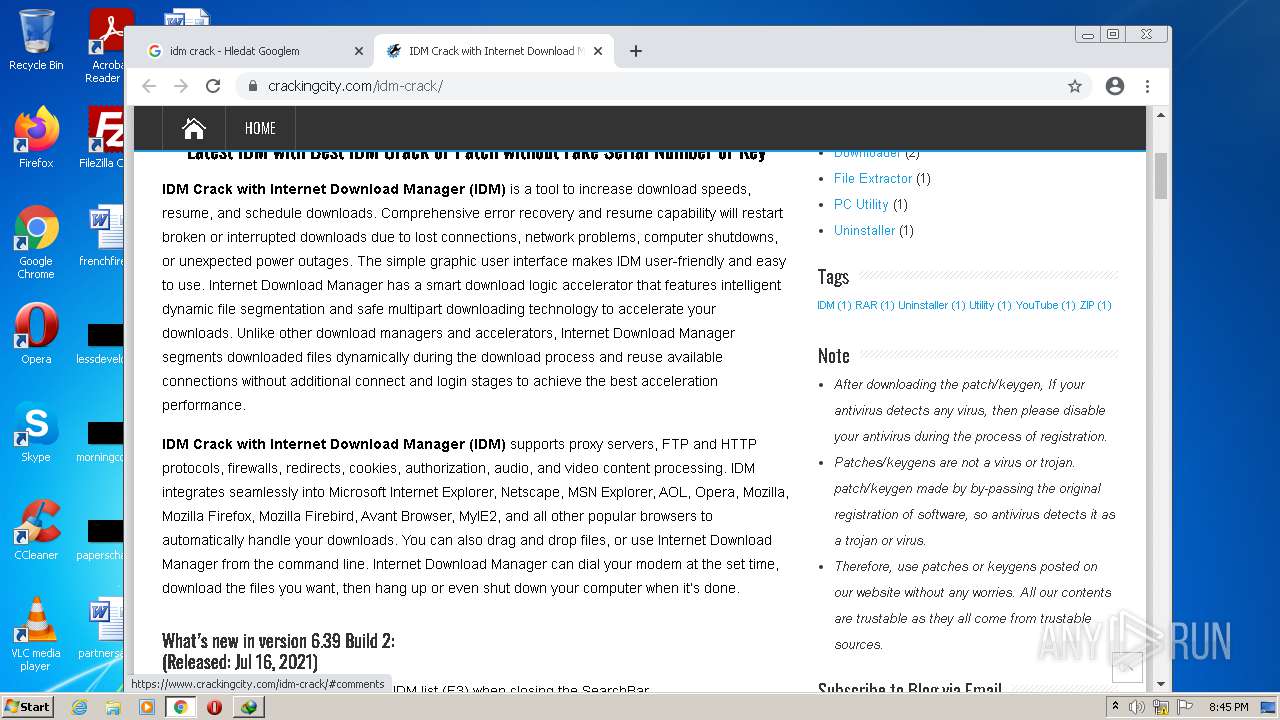
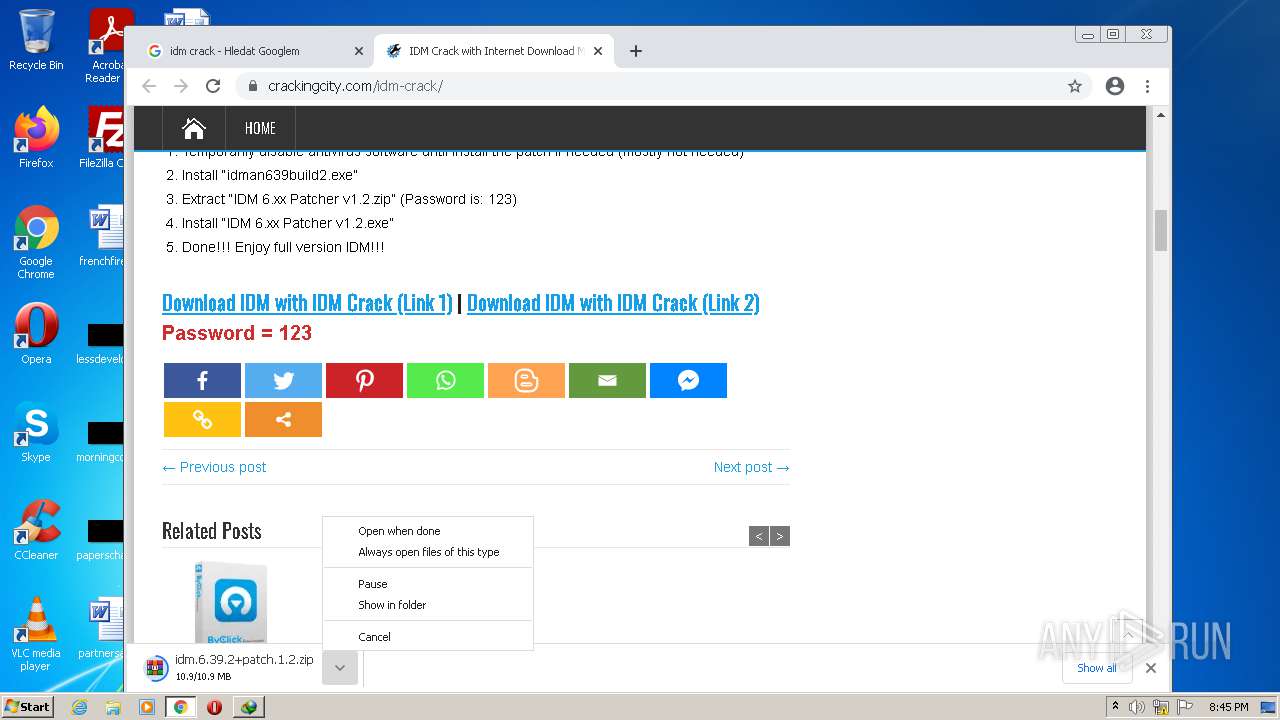
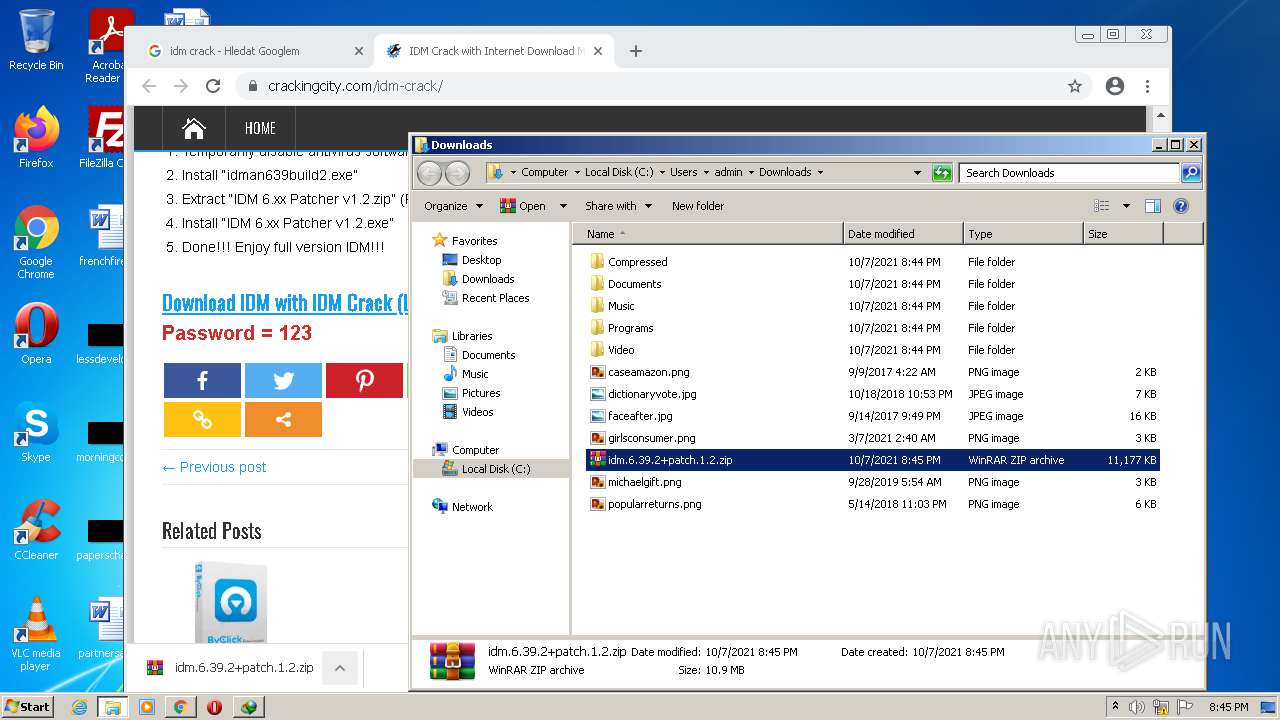
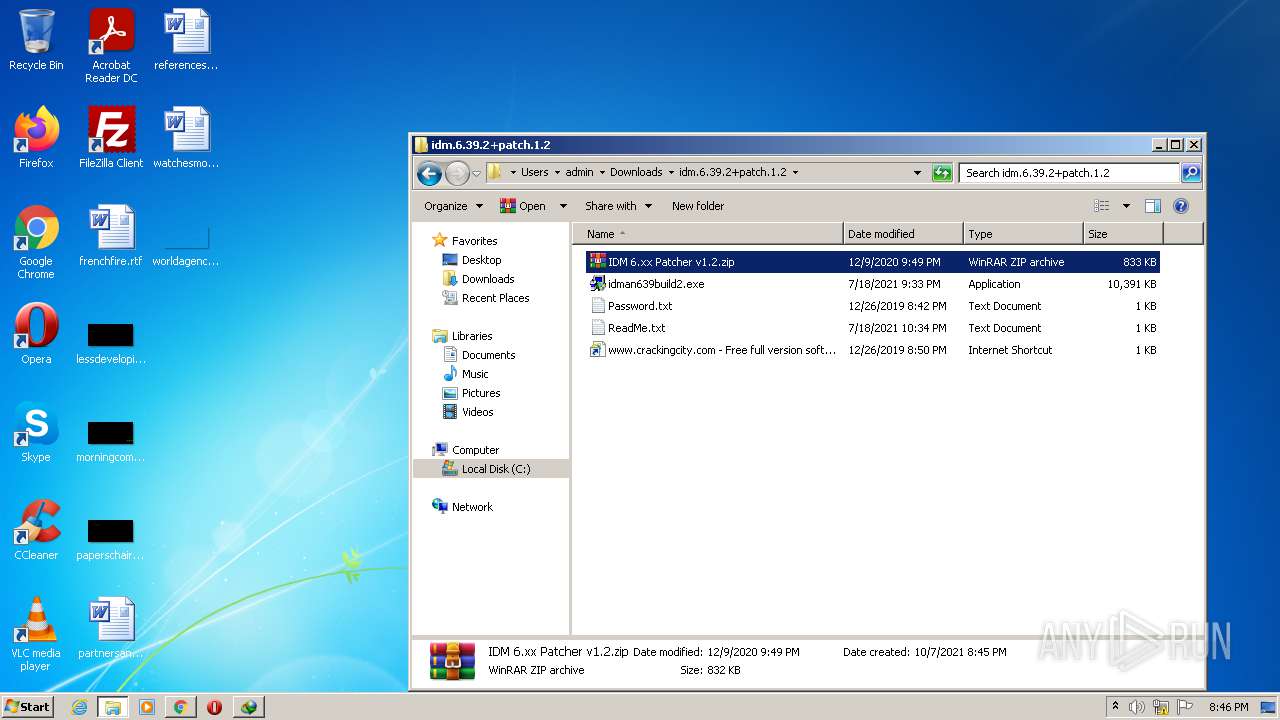
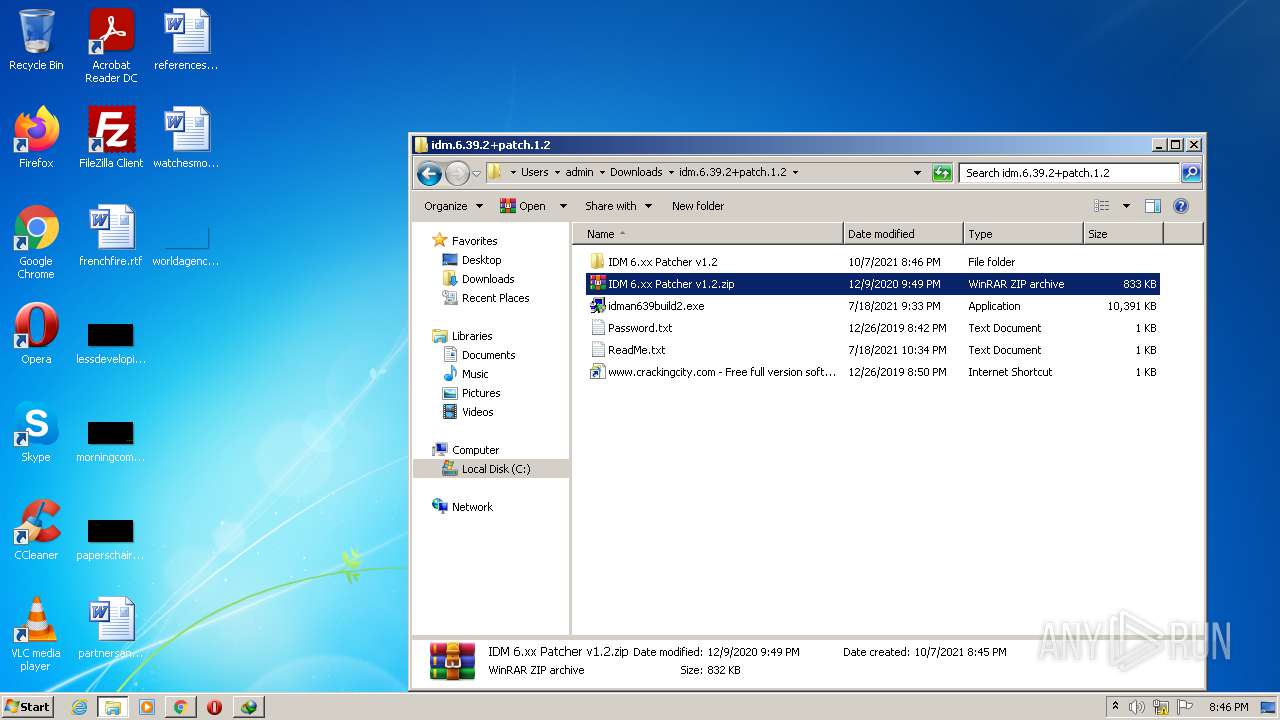
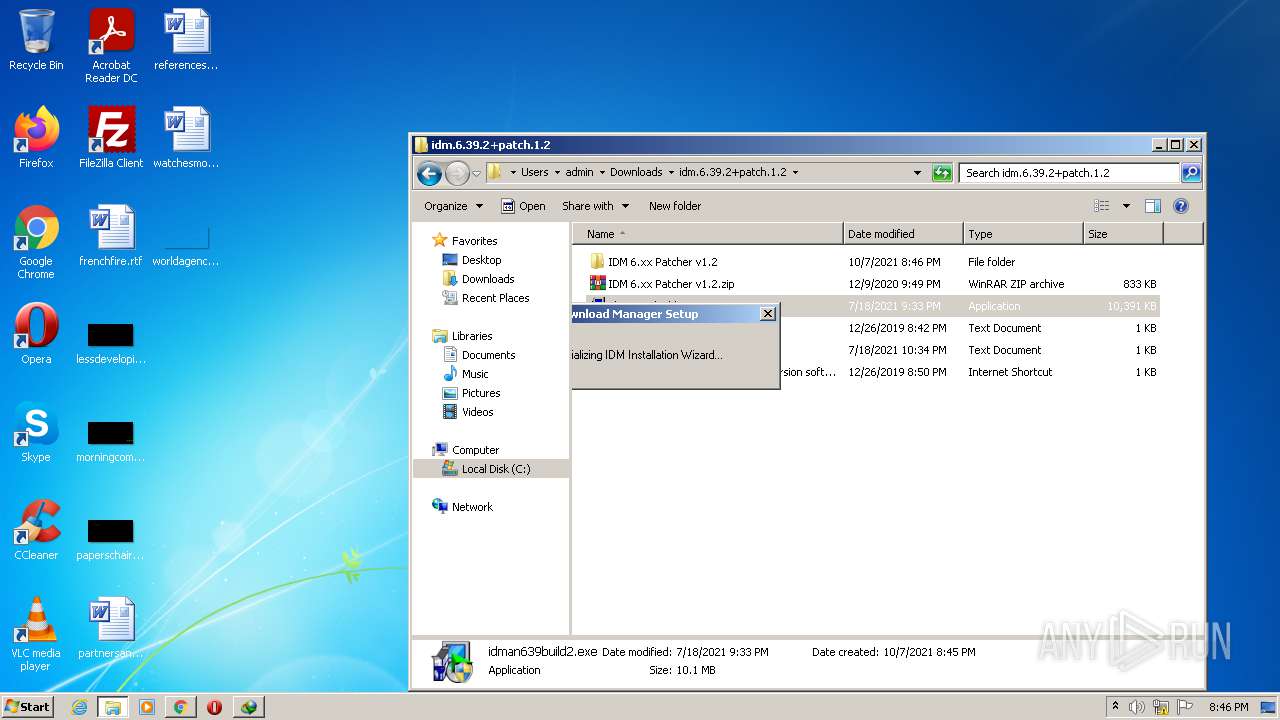
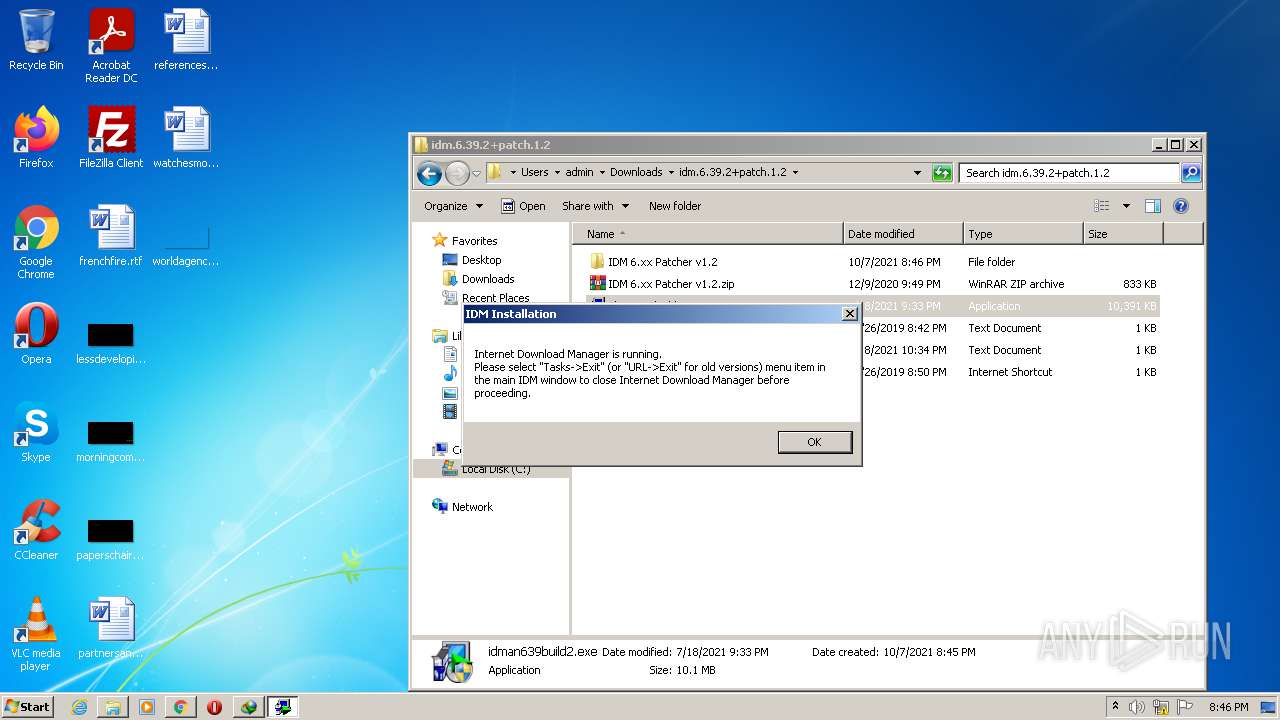
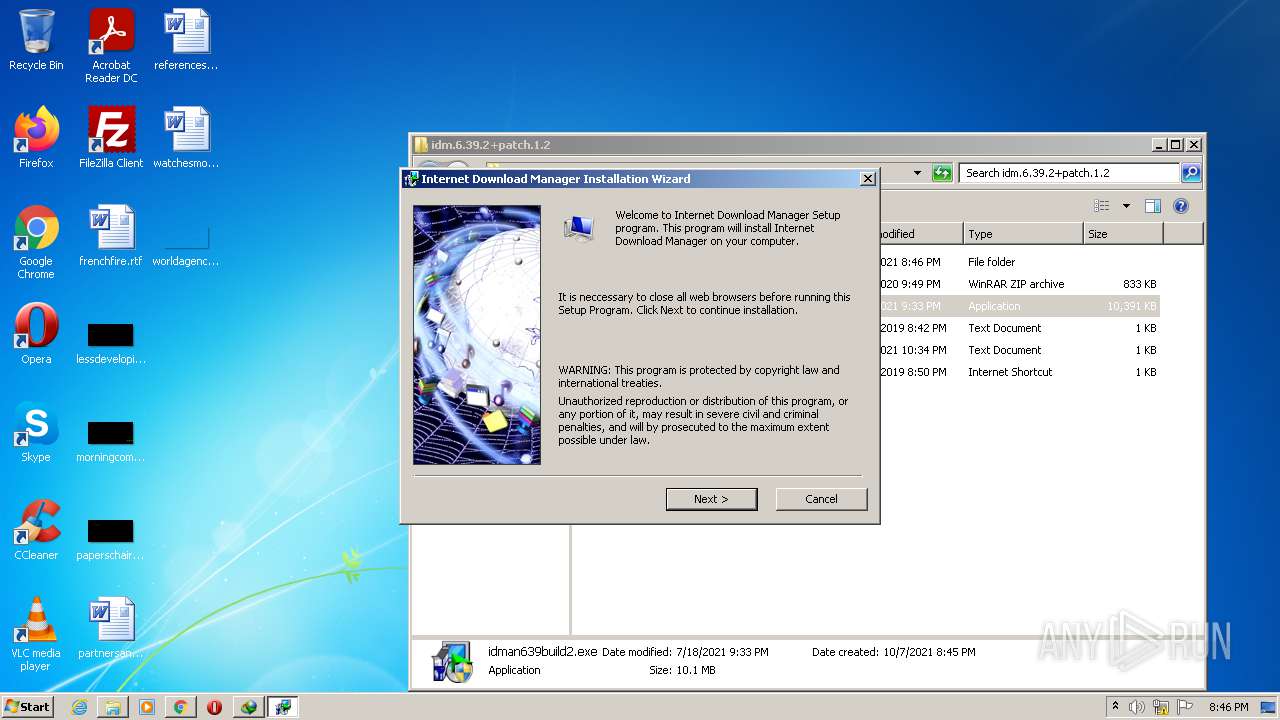
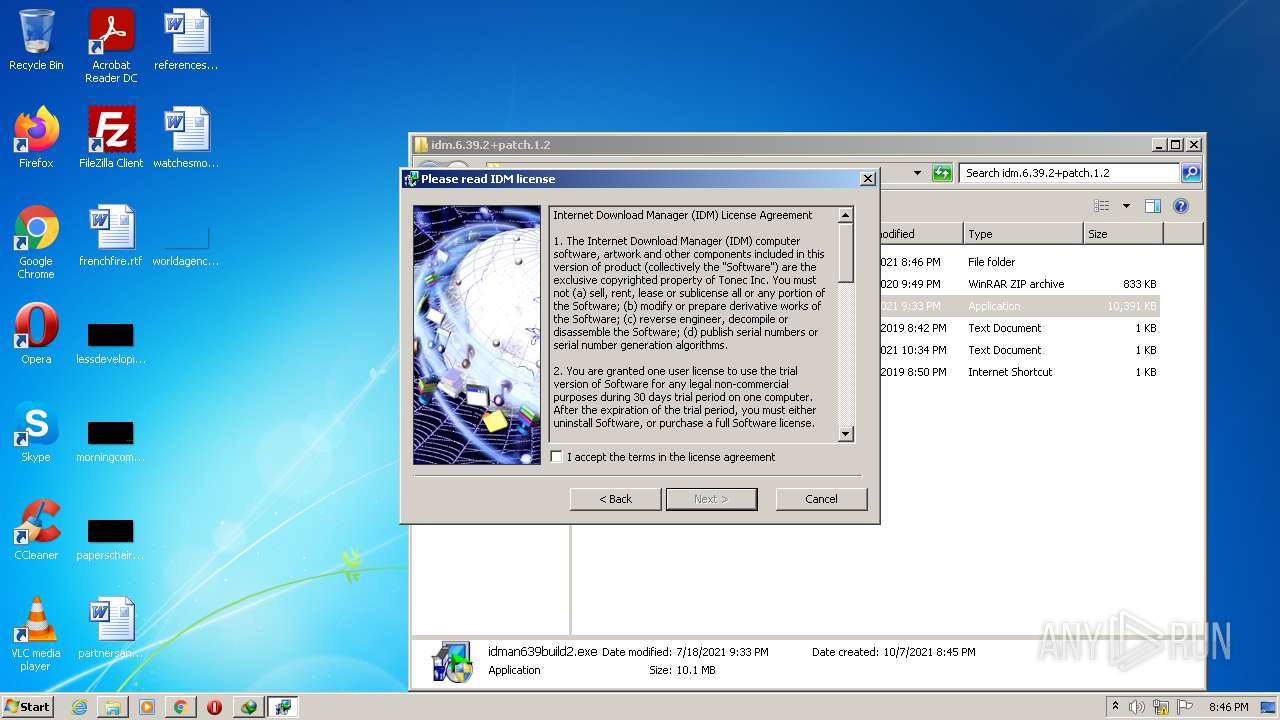
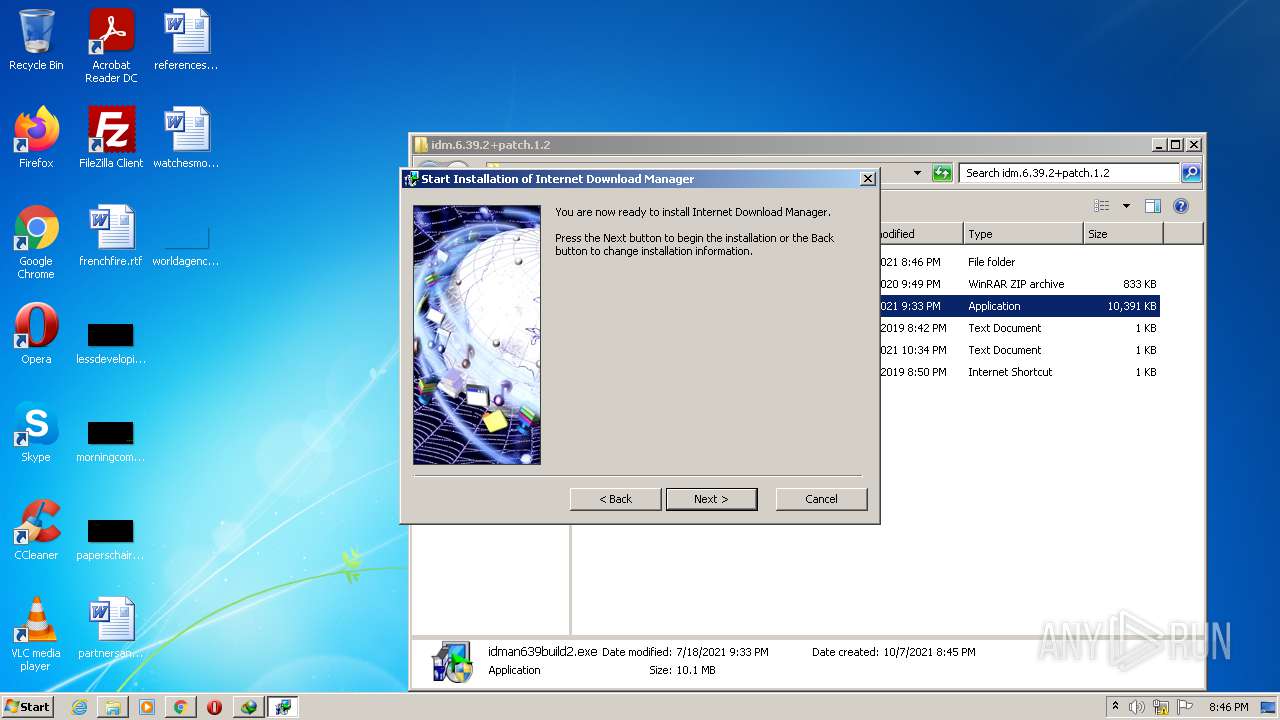
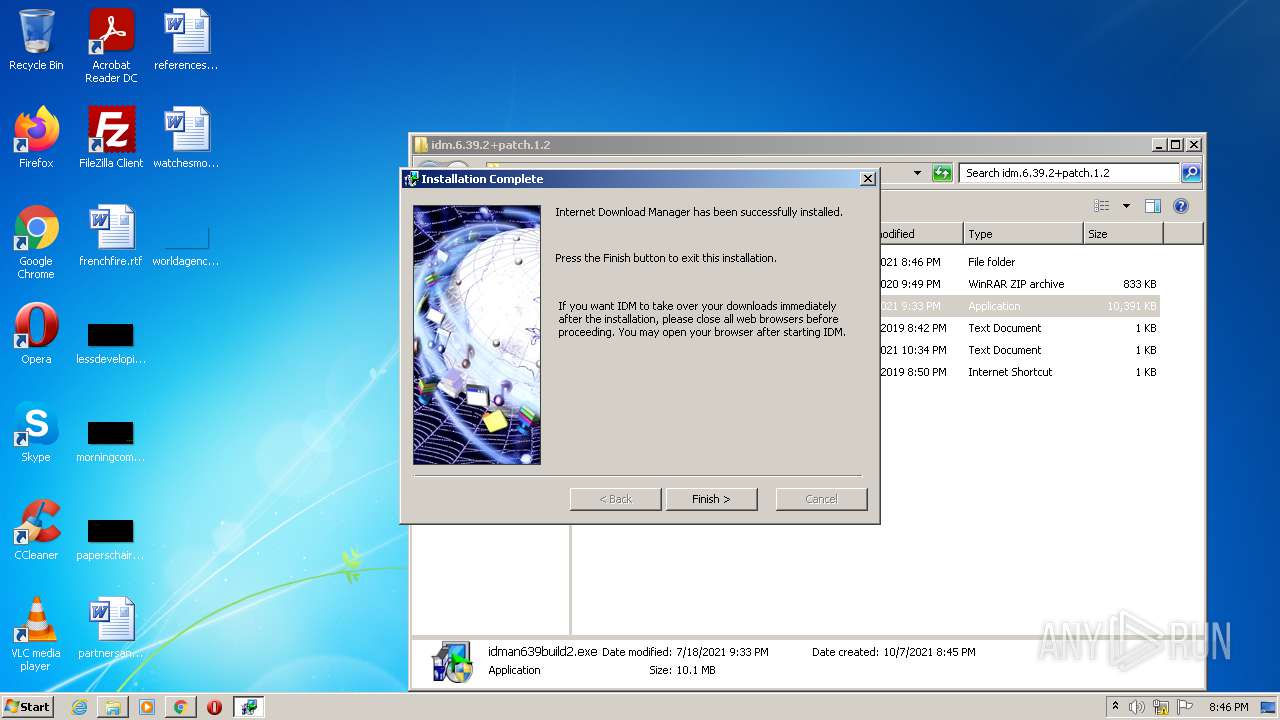
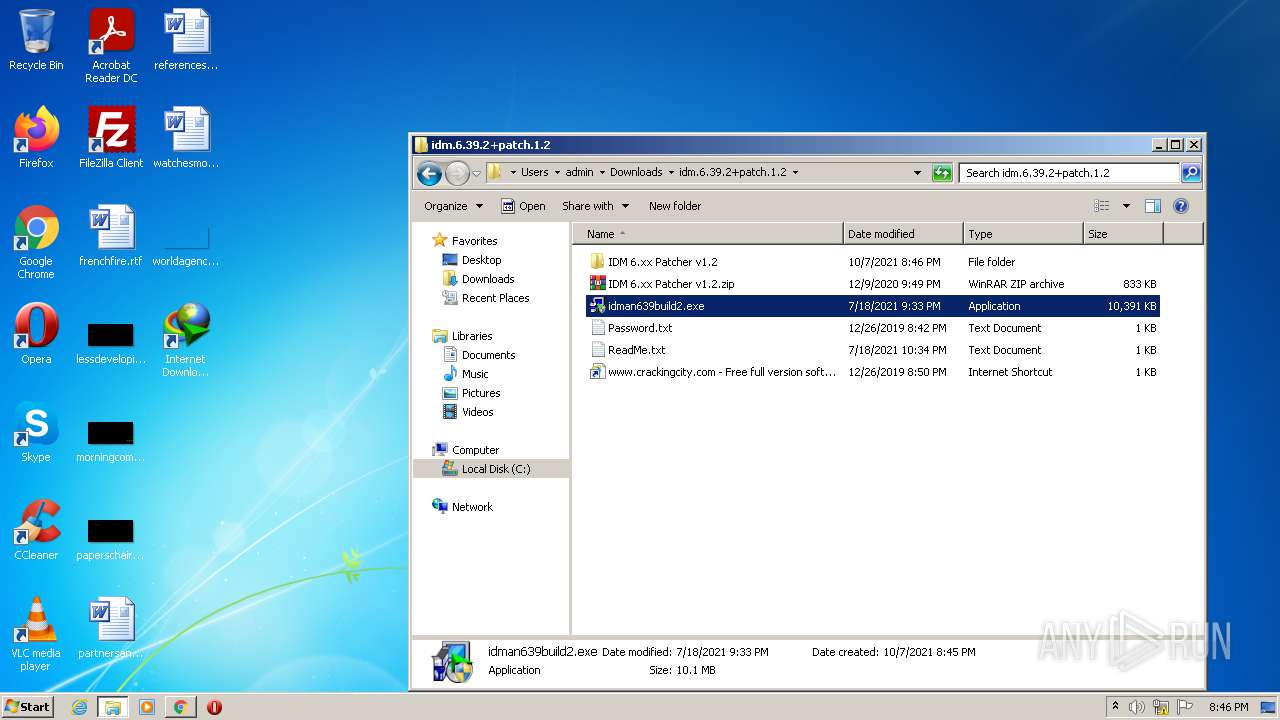
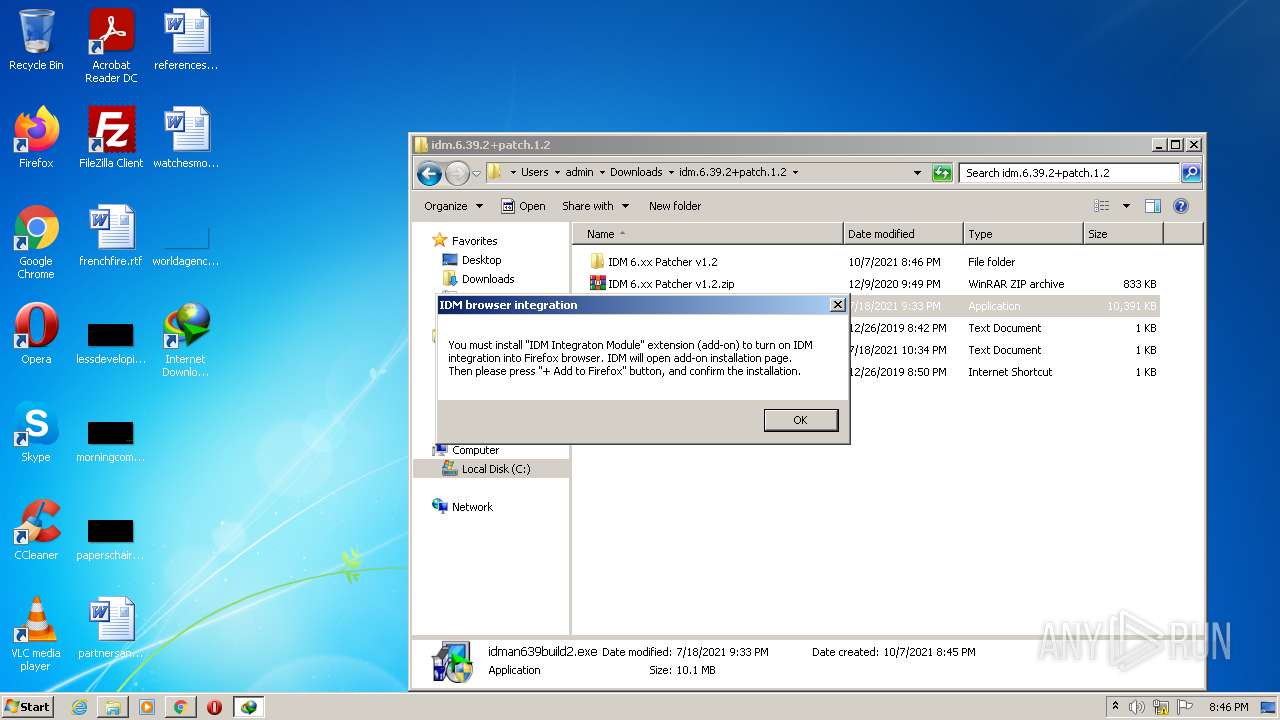
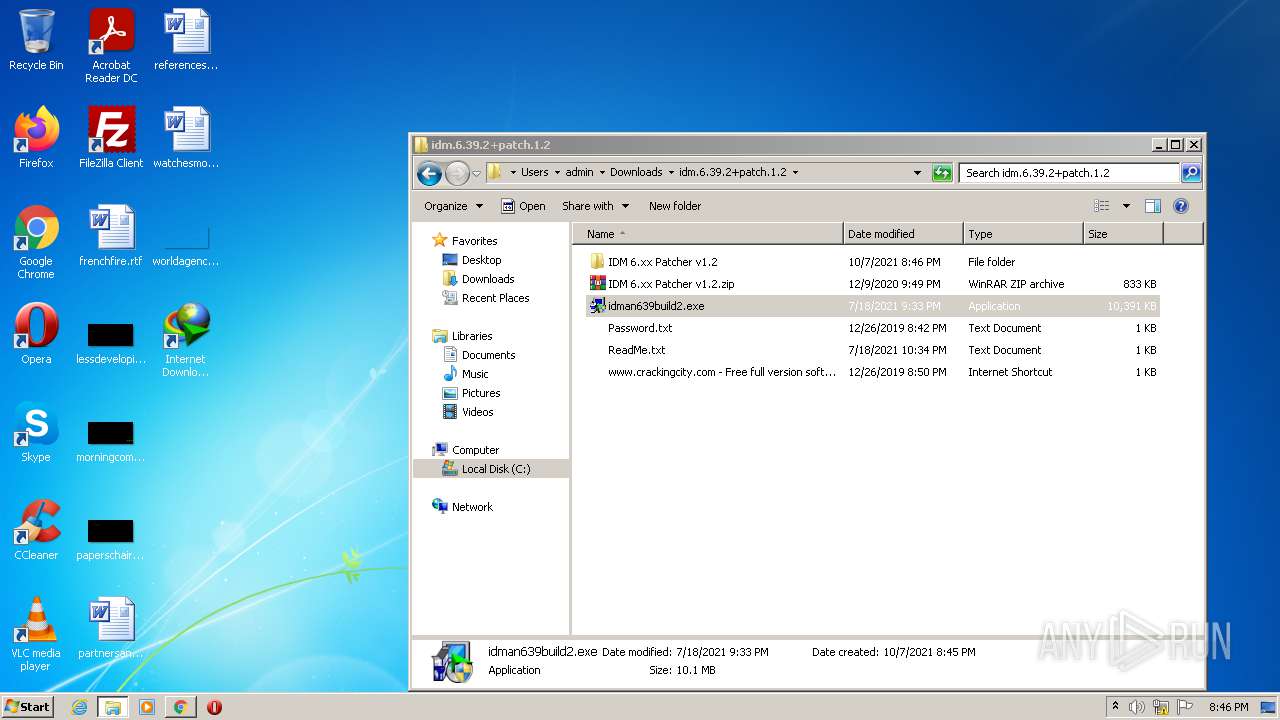
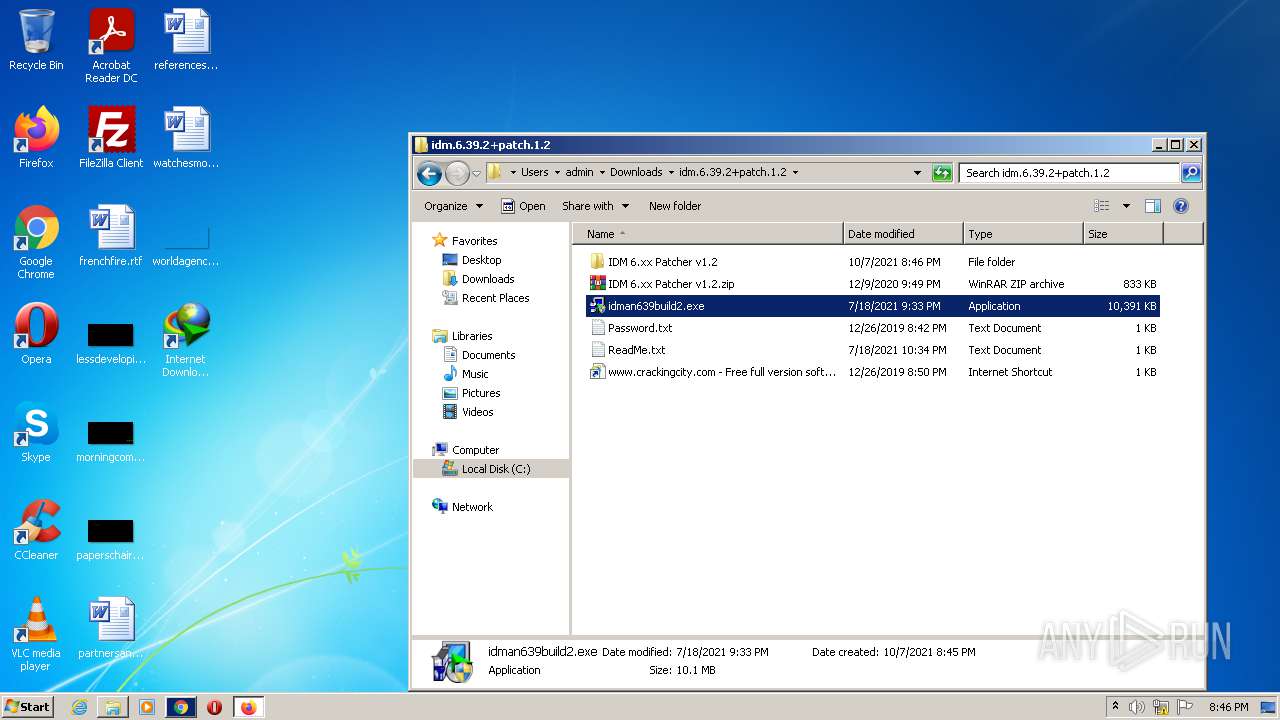
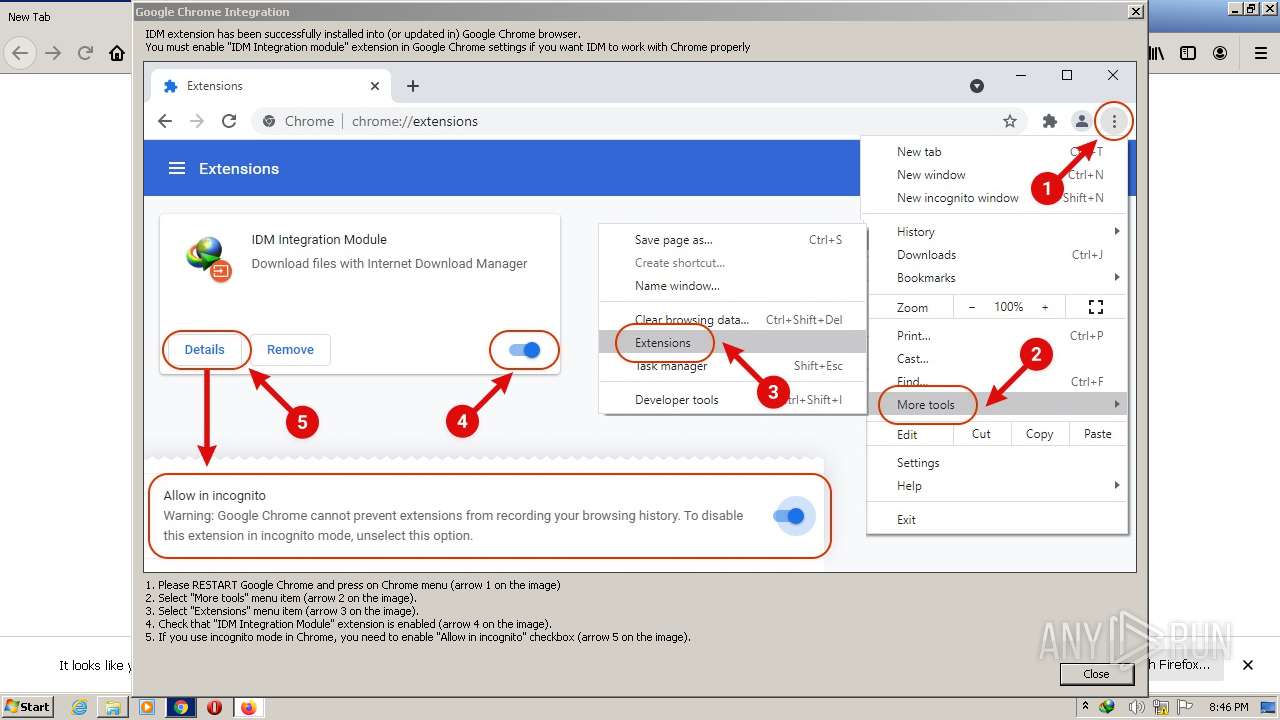
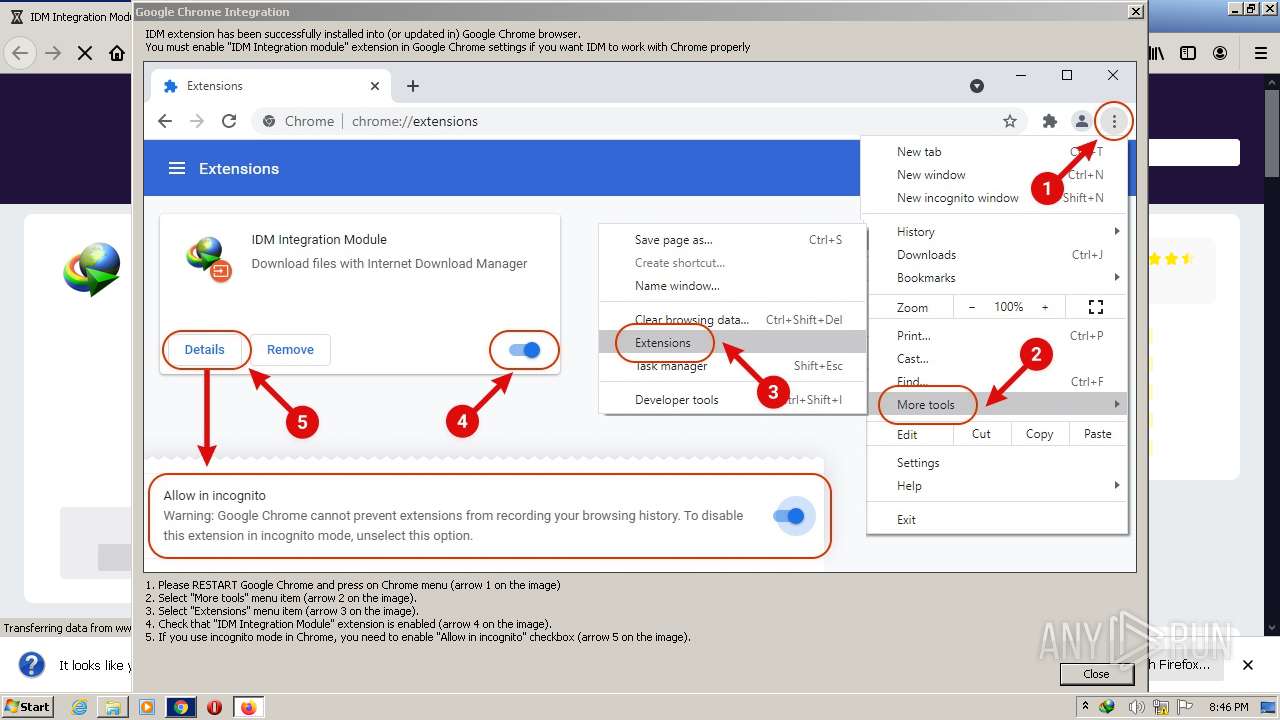
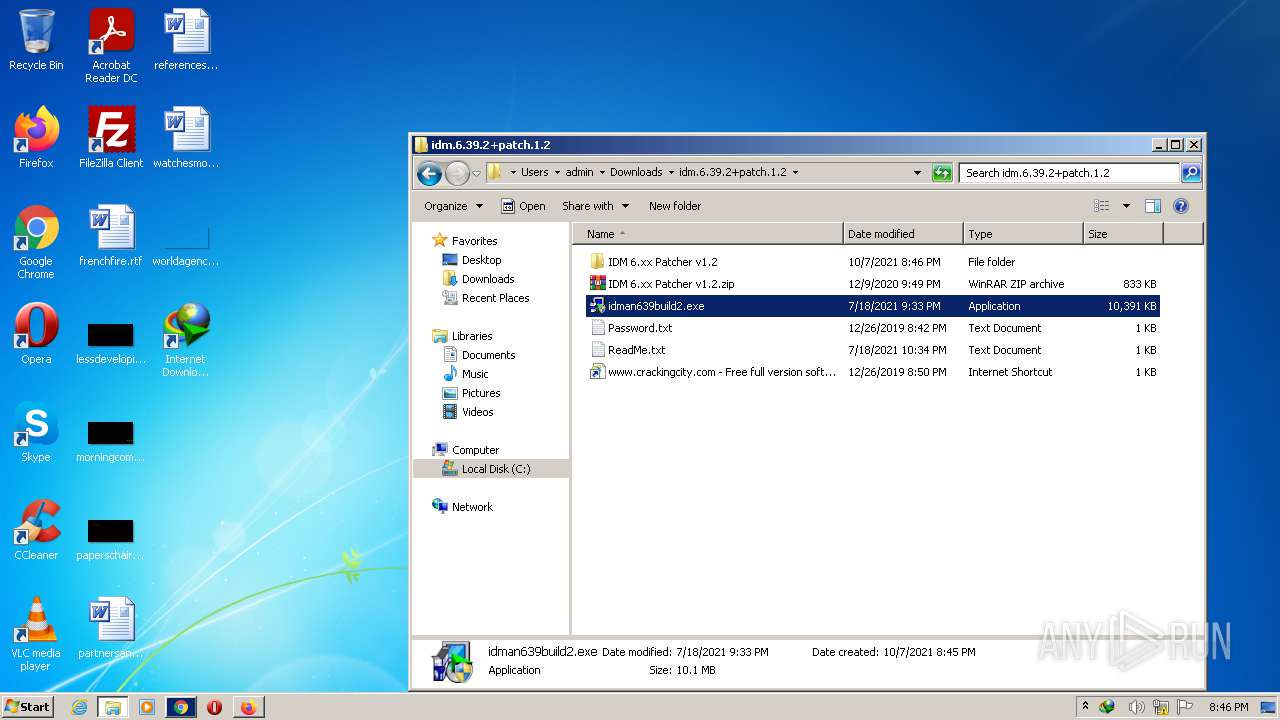
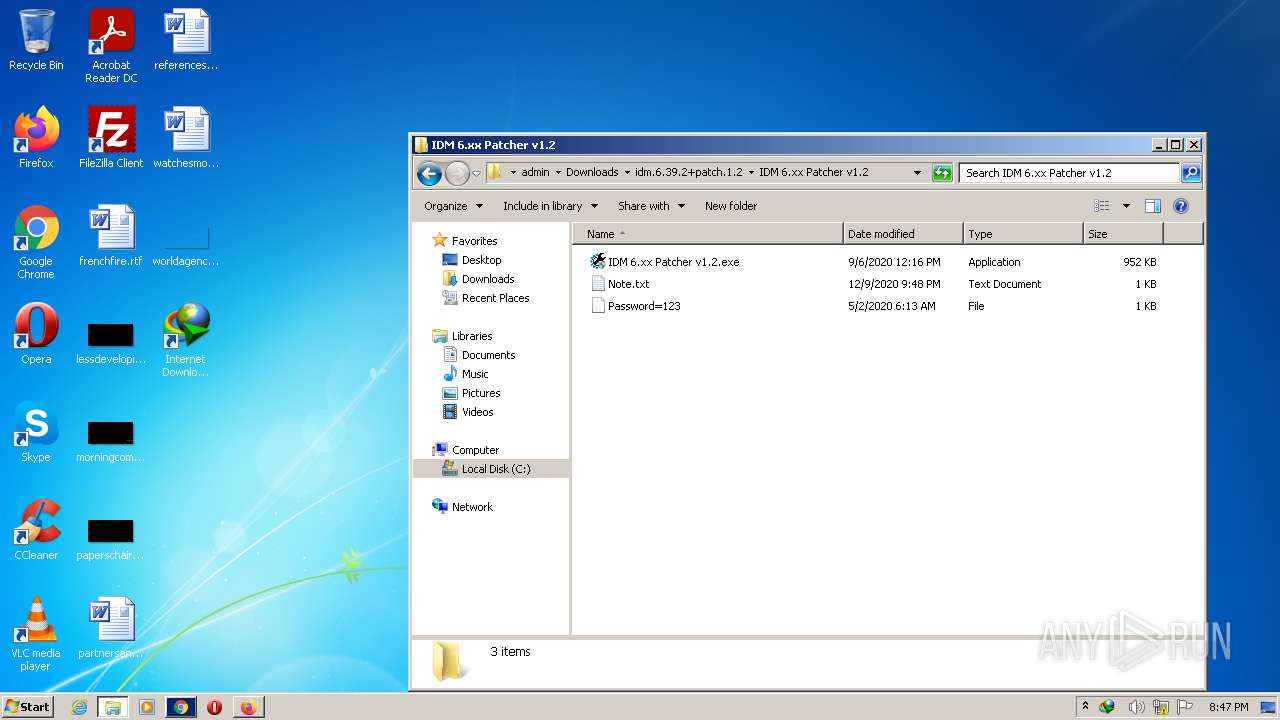
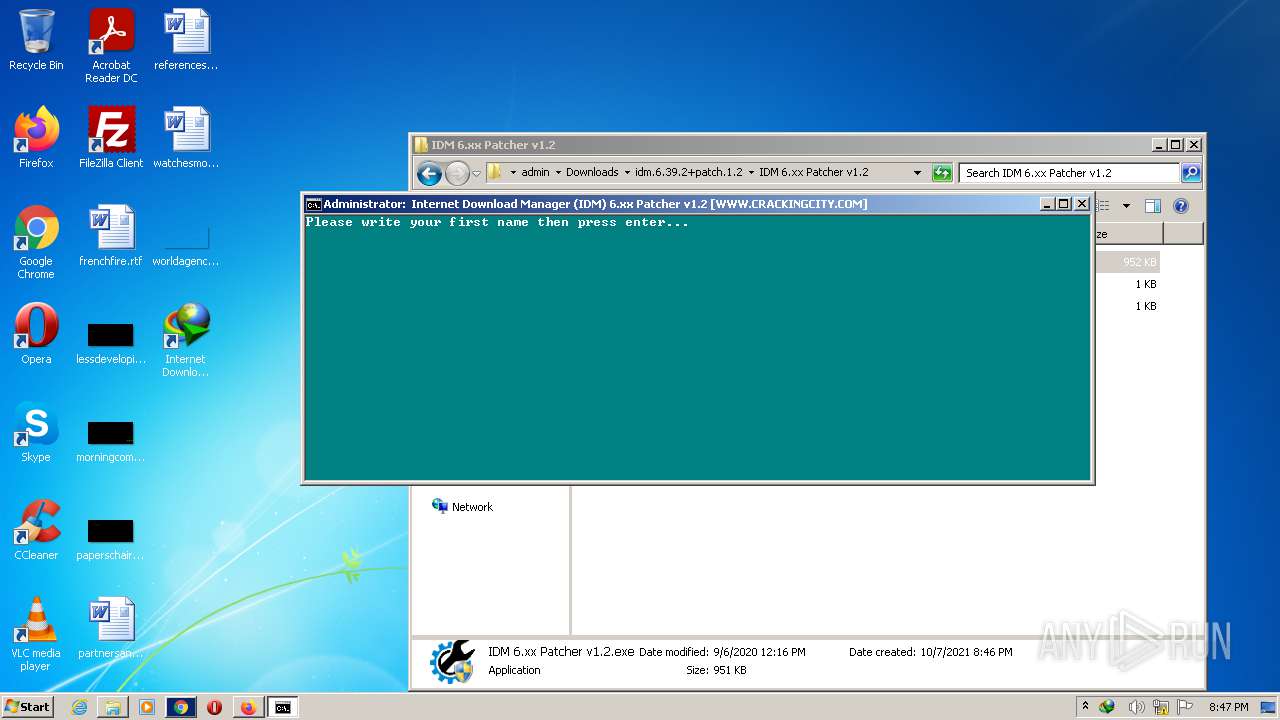
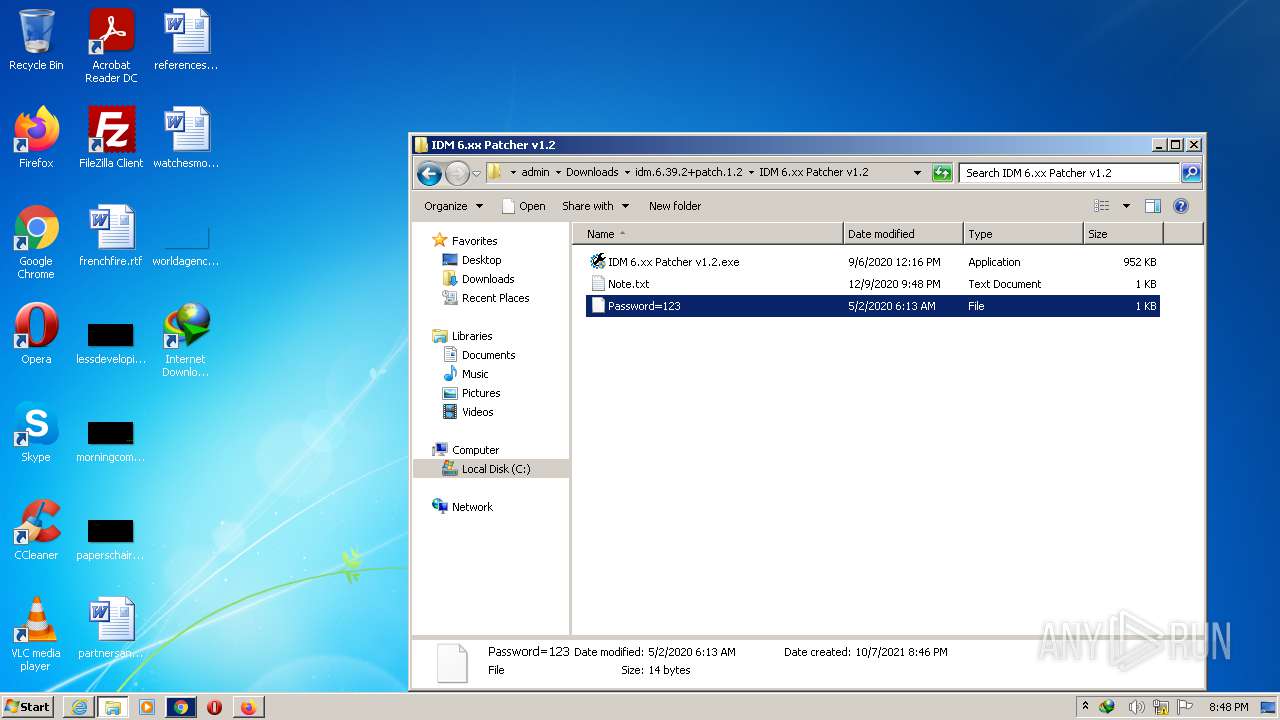
| File name: | IDMan.exe |
| Full analysis: | https://app.any.run/tasks/108e5aac-09c7-46c8-92de-0561363317fa |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | October 07, 2021, 19:44:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7E0607830FCFA47D4F96A893334C6405 |
| SHA1: | B61E7B96340C8044C1458AFD0C0381A8307FB6E6 |
| SHA256: | DAA93B4D1A9281D05FFC991BB86433D5AFD17857D2EE8CD4E67775CD636012DA |
| SSDEEP: | 98304:/ph5LoBUHDHuIN0P4lr18frP3wbzWFimaI7dlZAq:/R8UHDDNWgbzWFimaI7dl |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 3392)
- chrome.exe (PID: 2824)
- rundll32.exe (PID: 3960)
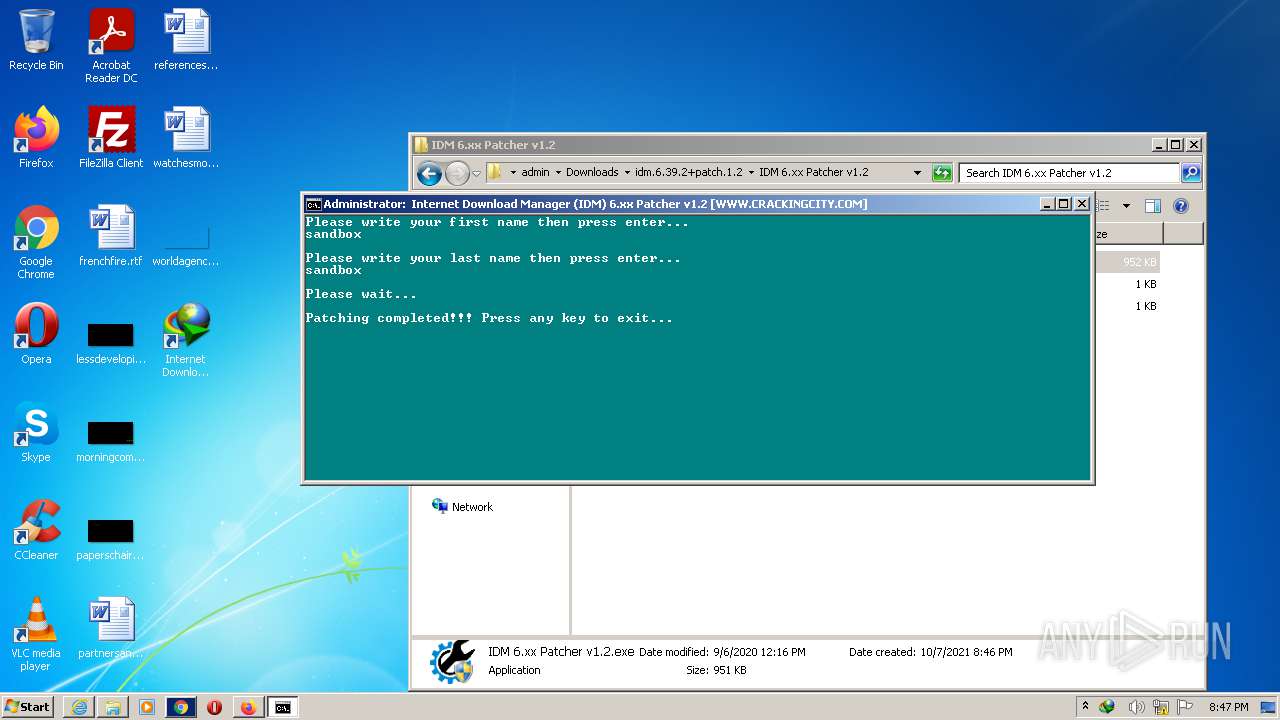
- IDM 6.xx Patcher v1.2.exe (PID: 2392)
- 7za.exe (PID: 3420)
- 7za.exe (PID: 2488)
- 7za.exe (PID: 368)
- 7za.exe (PID: 1996)
Application was dropped or rewritten from another process
- idman639build2.exe (PID: 612)
- idman639build2.exe (PID: 3916)
- IDM 6.xx Patcher v1.2.exe (PID: 2596)
- IDM 6.xx Patcher v1.2.exe (PID: 2392)
- AB2EF.exe (PID: 3024)
- 7za.exe (PID: 2396)
- 7za.exe (PID: 3432)
- 7za.exe (PID: 3420)
- AB2EF.exe (PID: 2576)
- AB2EF.exe (PID: 3920)
- AB2EF.exe (PID: 3648)
- AB2EF.exe (PID: 4088)
- AB2EF.exe (PID: 2396)
- AB2EF.exe (PID: 188)
- 7za.exe (PID: 2488)
- fart.exe (PID: 580)
- fart.exe (PID: 2160)
- fart.exe (PID: 3396)
- fart.exe (PID: 3236)
- fart.exe (PID: 368)
- fart.exe (PID: 3504)
- fart.exe (PID: 840)
- fart.exe (PID: 3260)
- fart.exe (PID: 2420)
- fart.exe (PID: 3224)
- fart.exe (PID: 2060)
- fart.exe (PID: 4060)
- fart.exe (PID: 3420)
- fart.exe (PID: 1528)
- fart.exe (PID: 3720)
- fart.exe (PID: 3336)
- fart.exe (PID: 3748)
- fart.exe (PID: 2412)
- fart.exe (PID: 2372)
- fart.exe (PID: 3864)
- fart.exe (PID: 2468)
- fart.exe (PID: 4088)
- fart.exe (PID: 2412)
- fart.exe (PID: 3864)
- fart.exe (PID: 2996)
- fart.exe (PID: 2556)
- fart.exe (PID: 2000)
- fart.exe (PID: 1528)
- fart.exe (PID: 1000)
- fart.exe (PID: 4088)
- fart.exe (PID: 2412)
- fart.exe (PID: 2820)
- fart.exe (PID: 3068)
- 7za.exe (PID: 368)
- 7za.exe (PID: 1996)
- NSudo86x.exe (PID: 3096)
- NSudo86x.exe (PID: 2720)
- NSudo86x.exe (PID: 3020)
- delcert.exe (PID: 3420)
- NSudo86x.exe (PID: 2940)
- NSudo86x.exe (PID: 3408)
- NSudo86x.exe (PID: 3408)
- NSudo86x.exe (PID: 4088)
- NSudo86x.exe (PID: 840)
- NSudo86x.exe (PID: 3812)
- NSudo86x.exe (PID: 3496)
- NSudo86x.exe (PID: 2076)
- NSudo86x.exe (PID: 3604)
- NSudo86x.exe (PID: 1056)
- NSudo86x.exe (PID: 3604)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 768)
- NSudo86x.exe (PID: 2752)
- NSudo86x.exe (PID: 2576)
- NSudo86x.exe (PID: 1056)
- NSudo86x.exe (PID: 576)
- NSudo86x.exe (PID: 2996)
- NSudo86x.exe (PID: 2396)
- NSudo86x.exe (PID: 3324)
- NSudo86x.exe (PID: 984)
- NSudo86x.exe (PID: 2072)
- NSudo86x.exe (PID: 2396)
- NSudo86x.exe (PID: 2540)
- NSudo86x.exe (PID: 3504)
- NSudo86x.exe (PID: 2244)
- NSudo86x.exe (PID: 3644)
- NSudo86x.exe (PID: 2820)
- NSudo86x.exe (PID: 3824)
- NSudo86x.exe (PID: 2576)
- NSudo86x.exe (PID: 2464)
- NSudo86x.exe (PID: 3352)
- NSudo86x.exe (PID: 3420)
- NSudo86x.exe (PID: 3864)
- NSudo86x.exe (PID: 3140)
- NSudo86x.exe (PID: 3644)
- NSudo86x.exe (PID: 1336)
- NSudo86x.exe (PID: 2068)
- NSudo86x.exe (PID: 2644)
- NSudo86x.exe (PID: 3864)
- NSudo86x.exe (PID: 1336)
- NSudo86x.exe (PID: 3764)
- NSudo86x.exe (PID: 2720)
- NSudo86x.exe (PID: 3868)
- NSudo86x.exe (PID: 3656)
- NSudo86x.exe (PID: 3868)
- NSudo86x.exe (PID: 2576)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 188)
- NSudo86x.exe (PID: 368)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 2540)
- NSudo86x.exe (PID: 2420)
- NSudo86x.exe (PID: 2500)
- NSudo86x.exe (PID: 3864)
- NSudo86x.exe (PID: 2384)
- NSudo86x.exe (PID: 3656)
- NSudo86x.exe (PID: 3020)
- NSudo86x.exe (PID: 2592)
- NSudo86x.exe (PID: 3764)
- NSudo86x.exe (PID: 2500)
- NSudo86x.exe (PID: 3412)
- NSudo86x.exe (PID: 2880)
- NSudo86x.exe (PID: 2096)
- NSudo86x.exe (PID: 3432)
- NSudo86x.exe (PID: 2972)
- NSudo86x.exe (PID: 3776)
- NSudo86x.exe (PID: 2144)
- NSudo86x.exe (PID: 2420)
- NSudo86x.exe (PID: 3416)
- NSudo86x.exe (PID: 3720)
- NSudo86x.exe (PID: 3720)
- NSudo86x.exe (PID: 2700)
- NSudo86x.exe (PID: 2972)
- NSudo86x.exe (PID: 372)
- NSudo86x.exe (PID: 2144)
- NSudo86x.exe (PID: 2244)
- NSudo86x.exe (PID: 3412)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 3324)
- NSudo86x.exe (PID: 3416)
- NSudo86x.exe (PID: 2160)
- NSudo86x.exe (PID: 3988)
- NSudo86x.exe (PID: 2876)
Changes the autorun value in the registry
- rundll32.exe (PID: 3960)
- IDMan.exe (PID: 556)
Starts NET.EXE for service management
- Uninstall.exe (PID: 3428)
REMCOS was detected
- IDMan.exe (PID: 556)
SUSPICIOUS
Checks supported languages
- IDMan.exe (PID: 3836)
- WinRAR.exe (PID: 2108)
- WinRAR.exe (PID: 3392)
- idman639build2.exe (PID: 3916)
- IDM1.tmp (PID: 2132)
- IDMan.exe (PID: 556)
- idmBroker.exe (PID: 3252)
- Uninstall.exe (PID: 3428)
- IDMan.exe (PID: 2292)
- MediumILStart.exe (PID: 2880)
- IEMonitor.exe (PID: 368)
- IDM 6.xx Patcher v1.2.exe (PID: 2392)
- cmd.exe (PID: 1284)
- 7za.exe (PID: 2396)
- 7za.exe (PID: 3432)
- cmd.exe (PID: 3812)
- cmd.exe (PID: 3000)
- 7za.exe (PID: 3420)
- AB2EF.exe (PID: 2576)
- AB2EF.exe (PID: 3024)
- AB2EF.exe (PID: 3920)
- AB2EF.exe (PID: 188)
- mode.com (PID: 3872)
- AB2EF.exe (PID: 3648)
- AB2EF.exe (PID: 4088)
- AB2EF.exe (PID: 2396)
- cmd.exe (PID: 2592)
- 7za.exe (PID: 2488)
- fart.exe (PID: 580)
- fart.exe (PID: 2160)
- fart.exe (PID: 368)
- fart.exe (PID: 3504)
- fart.exe (PID: 840)
- fart.exe (PID: 3396)
- fart.exe (PID: 3236)
- fart.exe (PID: 2420)
- fart.exe (PID: 3224)
- fart.exe (PID: 3720)
- fart.exe (PID: 4060)
- fart.exe (PID: 3420)
- fart.exe (PID: 1528)
- fart.exe (PID: 3336)
- fart.exe (PID: 3748)
- fart.exe (PID: 3260)
- fart.exe (PID: 2060)
- fart.exe (PID: 2996)
- fart.exe (PID: 4088)
- fart.exe (PID: 2468)
- fart.exe (PID: 2372)
- fart.exe (PID: 2412)
- fart.exe (PID: 2556)
- fart.exe (PID: 2820)
- fart.exe (PID: 3864)
- fart.exe (PID: 2412)
- fart.exe (PID: 3864)
- fart.exe (PID: 2000)
- fart.exe (PID: 4088)
- fart.exe (PID: 1528)
- fart.exe (PID: 1000)
- fart.exe (PID: 2412)
- fart.exe (PID: 3068)
- 7za.exe (PID: 1996)
- 7za.exe (PID: 368)
- delcert.exe (PID: 3420)
- NSudo86x.exe (PID: 2720)
- NSudo86x.exe (PID: 3096)
- NSudo86x.exe (PID: 3408)
- NSudo86x.exe (PID: 2940)
- NSudo86x.exe (PID: 3020)
- NSudo86x.exe (PID: 4088)
- NSudo86x.exe (PID: 3812)
- NSudo86x.exe (PID: 3408)
- NSudo86x.exe (PID: 3496)
- NSudo86x.exe (PID: 2076)
- NSudo86x.exe (PID: 840)
- NSudo86x.exe (PID: 3604)
- NSudo86x.exe (PID: 1056)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 3604)
- NSudo86x.exe (PID: 2576)
- NSudo86x.exe (PID: 2752)
- NSudo86x.exe (PID: 1056)
- NSudo86x.exe (PID: 576)
- NSudo86x.exe (PID: 768)
- NSudo86x.exe (PID: 3324)
- NSudo86x.exe (PID: 2396)
- NSudo86x.exe (PID: 2996)
- NSudo86x.exe (PID: 2396)
- NSudo86x.exe (PID: 2072)
- NSudo86x.exe (PID: 2540)
- NSudo86x.exe (PID: 984)
- NSudo86x.exe (PID: 3644)
- NSudo86x.exe (PID: 3504)
- NSudo86x.exe (PID: 2244)
- NSudo86x.exe (PID: 2820)
- NSudo86x.exe (PID: 3824)
- NSudo86x.exe (PID: 2576)
- NSudo86x.exe (PID: 2464)
- NSudo86x.exe (PID: 3420)
- NSudo86x.exe (PID: 3352)
- NSudo86x.exe (PID: 3644)
- NSudo86x.exe (PID: 3864)
- NSudo86x.exe (PID: 1336)
- NSudo86x.exe (PID: 2644)
- NSudo86x.exe (PID: 3140)
- NSudo86x.exe (PID: 1336)
- NSudo86x.exe (PID: 3764)
- NSudo86x.exe (PID: 2068)
- NSudo86x.exe (PID: 3864)
- NSudo86x.exe (PID: 2720)
- NSudo86x.exe (PID: 3868)
- NSudo86x.exe (PID: 3656)
- NSudo86x.exe (PID: 3868)
- NSudo86x.exe (PID: 2576)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 368)
- NSudo86x.exe (PID: 188)
- NSudo86x.exe (PID: 2540)
- NSudo86x.exe (PID: 2500)
- NSudo86x.exe (PID: 3864)
- NSudo86x.exe (PID: 2420)
- NSudo86x.exe (PID: 2384)
- NSudo86x.exe (PID: 3020)
- NSudo86x.exe (PID: 2592)
- NSudo86x.exe (PID: 3656)
- NSudo86x.exe (PID: 3764)
- NSudo86x.exe (PID: 2500)
- NSudo86x.exe (PID: 3412)
- NSudo86x.exe (PID: 2096)
- NSudo86x.exe (PID: 2880)
- NSudo86x.exe (PID: 3432)
- NSudo86x.exe (PID: 2144)
- NSudo86x.exe (PID: 2972)
- NSudo86x.exe (PID: 3776)
- NSudo86x.exe (PID: 2420)
- NSudo86x.exe (PID: 3416)
- NSudo86x.exe (PID: 3720)
- NSudo86x.exe (PID: 2972)
- NSudo86x.exe (PID: 3720)
- NSudo86x.exe (PID: 2700)
- NSudo86x.exe (PID: 2144)
- NSudo86x.exe (PID: 372)
- NSudo86x.exe (PID: 2244)
- NSudo86x.exe (PID: 3412)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 3324)
- NSudo86x.exe (PID: 3416)
- NSudo86x.exe (PID: 2160)
- NSudo86x.exe (PID: 3988)
- IDMan.exe (PID: 2996)
- NSudo86x.exe (PID: 2876)
- IEMonitor.exe (PID: 2500)
- IDMan.exe (PID: 4976)
Reads the computer name
- IDMan.exe (PID: 3836)
- WinRAR.exe (PID: 3392)
- WinRAR.exe (PID: 2108)
- IDM1.tmp (PID: 2132)
- IDMan.exe (PID: 556)
- Uninstall.exe (PID: 3428)
- MediumILStart.exe (PID: 2880)
- IDMan.exe (PID: 2292)
- IEMonitor.exe (PID: 368)
- 7za.exe (PID: 3432)
- IDM 6.xx Patcher v1.2.exe (PID: 2392)
- 7za.exe (PID: 2396)
- 7za.exe (PID: 3420)
- 7za.exe (PID: 2488)
- 7za.exe (PID: 1996)
- 7za.exe (PID: 368)
- NSudo86x.exe (PID: 2720)
- NSudo86x.exe (PID: 3096)
- NSudo86x.exe (PID: 2940)
- NSudo86x.exe (PID: 3020)
- NSudo86x.exe (PID: 3408)
- NSudo86x.exe (PID: 4088)
- NSudo86x.exe (PID: 3812)
- NSudo86x.exe (PID: 3408)
- NSudo86x.exe (PID: 840)
- NSudo86x.exe (PID: 3496)
- NSudo86x.exe (PID: 2076)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 3604)
- NSudo86x.exe (PID: 1056)
- NSudo86x.exe (PID: 3604)
- NSudo86x.exe (PID: 2576)
- NSudo86x.exe (PID: 2752)
- NSudo86x.exe (PID: 1056)
- NSudo86x.exe (PID: 576)
- NSudo86x.exe (PID: 768)
- NSudo86x.exe (PID: 3324)
- NSudo86x.exe (PID: 2396)
- NSudo86x.exe (PID: 2996)
- NSudo86x.exe (PID: 2396)
- NSudo86x.exe (PID: 2072)
- NSudo86x.exe (PID: 984)
- NSudo86x.exe (PID: 3644)
- NSudo86x.exe (PID: 3504)
- NSudo86x.exe (PID: 2540)
- NSudo86x.exe (PID: 2244)
- NSudo86x.exe (PID: 2576)
- NSudo86x.exe (PID: 2820)
- NSudo86x.exe (PID: 3420)
- NSudo86x.exe (PID: 2464)
- NSudo86x.exe (PID: 3824)
- NSudo86x.exe (PID: 3644)
- NSudo86x.exe (PID: 3864)
- NSudo86x.exe (PID: 3352)
- NSudo86x.exe (PID: 1336)
- NSudo86x.exe (PID: 2644)
- NSudo86x.exe (PID: 3140)
- NSudo86x.exe (PID: 3864)
- NSudo86x.exe (PID: 1336)
- NSudo86x.exe (PID: 2068)
- NSudo86x.exe (PID: 2720)
- NSudo86x.exe (PID: 3868)
- NSudo86x.exe (PID: 3656)
- NSudo86x.exe (PID: 3764)
- NSudo86x.exe (PID: 3868)
- NSudo86x.exe (PID: 2576)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 368)
- NSudo86x.exe (PID: 188)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 2500)
- NSudo86x.exe (PID: 2540)
- NSudo86x.exe (PID: 2384)
- NSudo86x.exe (PID: 3864)
- NSudo86x.exe (PID: 2420)
- NSudo86x.exe (PID: 3656)
- NSudo86x.exe (PID: 3020)
- NSudo86x.exe (PID: 2592)
- NSudo86x.exe (PID: 3412)
- NSudo86x.exe (PID: 3764)
- NSudo86x.exe (PID: 2500)
- NSudo86x.exe (PID: 2096)
- NSudo86x.exe (PID: 3432)
- NSudo86x.exe (PID: 2880)
- NSudo86x.exe (PID: 2144)
- NSudo86x.exe (PID: 2972)
- NSudo86x.exe (PID: 2420)
- NSudo86x.exe (PID: 3416)
- NSudo86x.exe (PID: 3776)
- NSudo86x.exe (PID: 3720)
- NSudo86x.exe (PID: 2972)
- NSudo86x.exe (PID: 2700)
- NSudo86x.exe (PID: 3720)
- NSudo86x.exe (PID: 2144)
- NSudo86x.exe (PID: 372)
- NSudo86x.exe (PID: 2244)
- NSudo86x.exe (PID: 3412)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 3324)
- NSudo86x.exe (PID: 3416)
- NSudo86x.exe (PID: 2160)
- cmd.exe (PID: 3000)
- NSudo86x.exe (PID: 3988)
- NSudo86x.exe (PID: 2876)
- IDMan.exe (PID: 2996)
- IEMonitor.exe (PID: 2500)
- IDMan.exe (PID: 4976)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3284)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3392)
- WinRAR.exe (PID: 2108)
- chrome.exe (PID: 2824)
- IDMan.exe (PID: 556)
- IDM 6.xx Patcher v1.2.exe (PID: 2392)
- 7za.exe (PID: 3420)
- rundll32.exe (PID: 3960)
- cmd.exe (PID: 3000)
- 7za.exe (PID: 2488)
- certutil.exe (PID: 2468)
- 7za.exe (PID: 1996)
- 7za.exe (PID: 368)
- firefox.exe (PID: 4000)
Drops a file that was compiled in debug mode
- chrome.exe (PID: 2824)
- IDMan.exe (PID: 556)
- rundll32.exe (PID: 3960)
- cmd.exe (PID: 3000)
- 7za.exe (PID: 1996)
- 7za.exe (PID: 368)
- certutil.exe (PID: 2468)
- firefox.exe (PID: 4000)
Creates a directory in Program Files
- IDM1.tmp (PID: 2132)
Creates files in the program directory
- IDM1.tmp (PID: 2132)
- IDMan.exe (PID: 556)
- cmd.exe (PID: 3000)
Creates files in the user directory
- IDM1.tmp (PID: 2132)
- IDMan.exe (PID: 556)
- IDMan.exe (PID: 2996)
Starts application with an unusual extension
- idman639build2.exe (PID: 3916)
Creates a software uninstall entry
- IDM1.tmp (PID: 2132)
Creates/Modifies COM task schedule object
- IDM1.tmp (PID: 2132)
- IDMan.exe (PID: 556)
- Uninstall.exe (PID: 3428)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 3428)
Removes files from Windows directory
- rundll32.exe (PID: 3960)
- certutil.exe (PID: 3812)
- certutil.exe (PID: 2468)
Creates files in the driver directory
- rundll32.exe (PID: 3960)
Creates files in the Windows directory
- rundll32.exe (PID: 3960)
- certutil.exe (PID: 3812)
- certutil.exe (PID: 2468)
Reads the time zone
- runonce.exe (PID: 2116)
Creates or modifies windows services
- Uninstall.exe (PID: 3428)
Executed via COM
- IDMan.exe (PID: 2292)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 1284)
- cmd.exe (PID: 3000)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3812)
- cmd.exe (PID: 3000)
- cmd.exe (PID: 2592)
- NSudo86x.exe (PID: 3096)
- NSudo86x.exe (PID: 2720)
- NSudo86x.exe (PID: 3020)
- NSudo86x.exe (PID: 3408)
- NSudo86x.exe (PID: 2940)
- NSudo86x.exe (PID: 3812)
- NSudo86x.exe (PID: 3408)
- NSudo86x.exe (PID: 4088)
- NSudo86x.exe (PID: 3496)
- NSudo86x.exe (PID: 2076)
- NSudo86x.exe (PID: 840)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 3604)
- NSudo86x.exe (PID: 1056)
- NSudo86x.exe (PID: 2576)
- NSudo86x.exe (PID: 2752)
- NSudo86x.exe (PID: 3604)
- NSudo86x.exe (PID: 1056)
- NSudo86x.exe (PID: 576)
- NSudo86x.exe (PID: 768)
- NSudo86x.exe (PID: 3324)
- NSudo86x.exe (PID: 2396)
- NSudo86x.exe (PID: 2996)
- NSudo86x.exe (PID: 2396)
- NSudo86x.exe (PID: 2072)
- NSudo86x.exe (PID: 984)
- NSudo86x.exe (PID: 3644)
- NSudo86x.exe (PID: 3504)
- NSudo86x.exe (PID: 2244)
- NSudo86x.exe (PID: 2540)
- NSudo86x.exe (PID: 2576)
- NSudo86x.exe (PID: 2820)
- NSudo86x.exe (PID: 3824)
- NSudo86x.exe (PID: 3420)
- NSudo86x.exe (PID: 2464)
- NSudo86x.exe (PID: 3140)
- NSudo86x.exe (PID: 3644)
- NSudo86x.exe (PID: 3864)
- NSudo86x.exe (PID: 3352)
- NSudo86x.exe (PID: 1336)
- NSudo86x.exe (PID: 2644)
- NSudo86x.exe (PID: 2068)
- NSudo86x.exe (PID: 3864)
- NSudo86x.exe (PID: 1336)
- NSudo86x.exe (PID: 2720)
- NSudo86x.exe (PID: 3868)
- NSudo86x.exe (PID: 3656)
- NSudo86x.exe (PID: 3764)
- NSudo86x.exe (PID: 3868)
- NSudo86x.exe (PID: 2576)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 188)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 368)
- NSudo86x.exe (PID: 2500)
- NSudo86x.exe (PID: 2540)
- NSudo86x.exe (PID: 2420)
- NSudo86x.exe (PID: 2384)
- NSudo86x.exe (PID: 3864)
- NSudo86x.exe (PID: 3656)
- NSudo86x.exe (PID: 3020)
- NSudo86x.exe (PID: 2592)
- NSudo86x.exe (PID: 3412)
- NSudo86x.exe (PID: 3764)
- NSudo86x.exe (PID: 2500)
- NSudo86x.exe (PID: 2096)
- NSudo86x.exe (PID: 2880)
- NSudo86x.exe (PID: 3432)
- NSudo86x.exe (PID: 2144)
- NSudo86x.exe (PID: 2972)
- NSudo86x.exe (PID: 3776)
- NSudo86x.exe (PID: 2420)
- NSudo86x.exe (PID: 3416)
- NSudo86x.exe (PID: 3720)
- NSudo86x.exe (PID: 2972)
- NSudo86x.exe (PID: 3720)
- NSudo86x.exe (PID: 2144)
- NSudo86x.exe (PID: 372)
- NSudo86x.exe (PID: 2700)
- NSudo86x.exe (PID: 3412)
- NSudo86x.exe (PID: 2484)
- NSudo86x.exe (PID: 2244)
- NSudo86x.exe (PID: 3324)
- NSudo86x.exe (PID: 3416)
- NSudo86x.exe (PID: 2160)
- NSudo86x.exe (PID: 2876)
Starts CMD.EXE for commands execution
- IDM 6.xx Patcher v1.2.exe (PID: 2392)
- cmd.exe (PID: 3000)
Application launched itself
- cmd.exe (PID: 3000)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3000)
Drops a file with too old compile date
- 7za.exe (PID: 2488)
- 7za.exe (PID: 1996)
Starts CertUtil for decode files
- cmd.exe (PID: 3000)
Starts Internet Explorer
- cmd.exe (PID: 3000)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3648)
INFO
Checks supported languages
- chrome.exe (PID: 3284)
- chrome.exe (PID: 2980)
- chrome.exe (PID: 1708)
- chrome.exe (PID: 116)
- chrome.exe (PID: 2368)
- chrome.exe (PID: 1320)
- chrome.exe (PID: 1440)
- chrome.exe (PID: 2336)
- chrome.exe (PID: 2268)
- chrome.exe (PID: 3544)
- chrome.exe (PID: 3756)
- chrome.exe (PID: 3816)
- chrome.exe (PID: 2752)
- chrome.exe (PID: 2352)
- chrome.exe (PID: 2992)
- chrome.exe (PID: 3036)
- chrome.exe (PID: 3212)
- chrome.exe (PID: 2956)
- chrome.exe (PID: 3956)
- chrome.exe (PID: 2584)
- chrome.exe (PID: 2476)
- chrome.exe (PID: 1272)
- chrome.exe (PID: 4068)
- chrome.exe (PID: 2952)
- chrome.exe (PID: 3224)
- chrome.exe (PID: 708)
- chrome.exe (PID: 3776)
- chrome.exe (PID: 3112)
- chrome.exe (PID: 3868)
- chrome.exe (PID: 3384)
- chrome.exe (PID: 556)
- chrome.exe (PID: 3028)
- chrome.exe (PID: 2824)
- chrome.exe (PID: 3124)
- chrome.exe (PID: 3140)
- chrome.exe (PID: 2932)
- chrome.exe (PID: 3392)
- firefox.exe (PID: 3160)
- chrome.exe (PID: 1276)
- firefox.exe (PID: 2212)
- firefox.exe (PID: 4000)
- rundll32.exe (PID: 3960)
- runonce.exe (PID: 2116)
- grpconv.exe (PID: 3772)
- net.exe (PID: 2616)
- net1.exe (PID: 2316)
- firefox.exe (PID: 1896)
- chrome.exe (PID: 1184)
- firefox.exe (PID: 2568)
- firefox.exe (PID: 3008)
- firefox.exe (PID: 2728)
- firefox.exe (PID: 1952)
- chrome.exe (PID: 2312)
- firefox.exe (PID: 2476)
- attrib.exe (PID: 2596)
- reg.exe (PID: 3920)
- find.exe (PID: 3068)
- reg.exe (PID: 2468)
- find.exe (PID: 3648)
- find.exe (PID: 1900)
- reg.exe (PID: 2144)
- reg.exe (PID: 3144)
- find.exe (PID: 3224)
- chrome.exe (PID: 3096)
- chrome.exe (PID: 2244)
- reg.exe (PID: 3432)
- taskkill.exe (PID: 4068)
- taskkill.exe (PID: 3336)
- taskkill.exe (PID: 3236)
- taskkill.exe (PID: 3988)
- taskkill.exe (PID: 3352)
- taskkill.exe (PID: 2268)
- taskkill.exe (PID: 3352)
- taskkill.exe (PID: 1000)
- chrome.exe (PID: 2268)
- certutil.exe (PID: 3812)
- attrib.exe (PID: 1336)
- attrib.exe (PID: 2372)
- chrome.exe (PID: 2588)
- certutil.exe (PID: 2468)
- REG.exe (PID: 3496)
- reg.exe (PID: 3144)
- REG.exe (PID: 2068)
- reg.exe (PID: 2420)
- reg.exe (PID: 2876)
- REG.exe (PID: 2876)
- REG.exe (PID: 368)
- REG.exe (PID: 3868)
- reg.exe (PID: 2824)
- reg.exe (PID: 3920)
- reg.exe (PID: 2468)
- REG.exe (PID: 2060)
- reg.exe (PID: 2636)
- REG.exe (PID: 368)
- REG.exe (PID: 2076)
- reg.exe (PID: 3264)
- REG.exe (PID: 1532)
- reg.exe (PID: 1284)
- REG.exe (PID: 2312)
- reg.exe (PID: 2124)
- REG.exe (PID: 984)
- reg.exe (PID: 2468)
- reg.exe (PID: 2420)
- REG.exe (PID: 2720)
- REG.exe (PID: 2604)
- reg.exe (PID: 4032)
- reg.exe (PID: 2396)
- reg.exe (PID: 3656)
- REG.exe (PID: 2192)
- REG.exe (PID: 2720)
- reg.exe (PID: 2464)
- REG.exe (PID: 2260)
- reg.exe (PID: 1200)
- REG.exe (PID: 4060)
- reg.exe (PID: 580)
- reg.exe (PID: 1192)
- REG.exe (PID: 3096)
- REG.exe (PID: 3432)
- reg.exe (PID: 2484)
- reg.exe (PID: 580)
- REG.exe (PID: 2268)
- REG.exe (PID: 572)
- REG.exe (PID: 2144)
- reg.exe (PID: 2192)
- reg.exe (PID: 1060)
- reg.exe (PID: 768)
- reg.exe (PID: 2996)
- REG.exe (PID: 2920)
- REG.exe (PID: 2156)
- REG.exe (PID: 2824)
- reg.exe (PID: 3140)
- REG.exe (PID: 2312)
- reg.exe (PID: 2752)
- reg.exe (PID: 2468)
- REG.exe (PID: 2644)
- reg.exe (PID: 3264)
- reg.exe (PID: 2836)
- REG.exe (PID: 3052)
- REG.exe (PID: 3864)
- reg.exe (PID: 3868)
- REG.exe (PID: 2972)
- REG.exe (PID: 2604)
- reg.exe (PID: 1284)
- reg.exe (PID: 2124)
- REG.exe (PID: 3648)
- reg.exe (PID: 2232)
- reg.exe (PID: 2232)
- REG.exe (PID: 2260)
- reg.exe (PID: 1532)
- REG.exe (PID: 2372)
- reg.exe (PID: 2996)
- REG.exe (PID: 3336)
- reg.exe (PID: 3336)
- REG.exe (PID: 3140)
- REG.exe (PID: 2312)
- reg.exe (PID: 2000)
- REG.exe (PID: 1872)
- reg.exe (PID: 3412)
- reg.exe (PID: 3160)
- reg.exe (PID: 2484)
- REG.exe (PID: 3920)
- reg.exe (PID: 2972)
- REG.exe (PID: 3604)
- REG.exe (PID: 2880)
- REG.exe (PID: 1056)
- reg.exe (PID: 2124)
- REG.exe (PID: 3020)
- reg.exe (PID: 3052)
- REG.exe (PID: 3420)
- reg.exe (PID: 3416)
- REG.exe (PID: 572)
- reg.exe (PID: 2160)
- REG.exe (PID: 4068)
- reg.exe (PID: 372)
- reg.exe (PID: 3496)
- REG.exe (PID: 3412)
- REG.exe (PID: 2124)
- reg.exe (PID: 1200)
- REG.exe (PID: 1000)
- REG.exe (PID: 3260)
- reg.exe (PID: 2232)
- REG.exe (PID: 1284)
- reg.exe (PID: 576)
- REG.exe (PID: 3144)
- reg.exe (PID: 3988)
- reg.exe (PID: 1528)
- REG.exe (PID: 2144)
- reg.exe (PID: 1000)
- reg.exe (PID: 2260)
- reg.exe (PID: 2644)
- REG.exe (PID: 2420)
- REG.exe (PID: 2384)
- REG.exe (PID: 4088)
- reg.exe (PID: 2720)
- reg.exe (PID: 3352)
- REG.exe (PID: 3420)
- REG.exe (PID: 3764)
- reg.exe (PID: 2268)
- REG.exe (PID: 368)
- reg.exe (PID: 2940)
- REG.exe (PID: 2144)
- reg.exe (PID: 188)
- REG.exe (PID: 3920)
- reg.exe (PID: 2464)
- reg.exe (PID: 1200)
- REG.exe (PID: 4032)
- reg.exe (PID: 572)
- REG.exe (PID: 1200)
- reg.exe (PID: 3144)
- REG.exe (PID: 3336)
- REG.exe (PID: 1284)
- reg.exe (PID: 2820)
- reg.exe (PID: 3988)
- REG.exe (PID: 2836)
- REG.exe (PID: 2420)
- reg.exe (PID: 2588)
- reg.exe (PID: 2244)
- reg.exe (PID: 3672)
- REG.exe (PID: 3352)
- reg.exe (PID: 3236)
- REG.exe (PID: 3420)
- reg.exe (PID: 3052)
- REG.exe (PID: 1528)
- REG.exe (PID: 840)
- REG.exe (PID: 4060)
- reg.exe (PID: 588)
- REG.exe (PID: 3656)
- reg.exe (PID: 2720)
- reg.exe (PID: 3140)
- reg.exe (PID: 2144)
- REG.exe (PID: 3412)
- reg.exe (PID: 2268)
- REG.exe (PID: 2588)
- REG.exe (PID: 3324)
- reg.exe (PID: 576)
- reg.exe (PID: 628)
- REG.exe (PID: 3764)
- reg.exe (PID: 2700)
- REG.exe (PID: 3408)
- reg.exe (PID: 2396)
- REG.exe (PID: 2920)
- reg.exe (PID: 2124)
- reg.exe (PID: 2124)
- reg.exe (PID: 2824)
- REG.exe (PID: 3496)
- reg.exe (PID: 3864)
- REG.exe (PID: 2824)
- reg.exe (PID: 576)
- reg.exe (PID: 3416)
- reg.exe (PID: 2232)
- REG.exe (PID: 1000)
- reg.exe (PID: 2192)
- reg.exe (PID: 2228)
- reg.exe (PID: 2072)
- REG.exe (PID: 2396)
- REG.exe (PID: 3656)
- reg.exe (PID: 2720)
- reg.exe (PID: 2940)
- reg.exe (PID: 3260)
- reg.exe (PID: 1532)
- REG.exe (PID: 3644)
- reg.exe (PID: 2972)
- REG.exe (PID: 3324)
- iexplore.exe (PID: 3236)
- iexplore.exe (PID: 3648)
- rundll32.exe (PID: 5712)
Manual execution by user
- chrome.exe (PID: 3284)
- WinRAR.exe (PID: 3392)
- WinRAR.exe (PID: 2108)
- idman639build2.exe (PID: 612)
- idman639build2.exe (PID: 3916)
- firefox.exe (PID: 2212)
- IDM 6.xx Patcher v1.2.exe (PID: 2596)
- IDM 6.xx Patcher v1.2.exe (PID: 2392)
- rundll32.exe (PID: 5712)
- IDMan.exe (PID: 4976)
Reads the computer name
- chrome.exe (PID: 3284)
- chrome.exe (PID: 1708)
- chrome.exe (PID: 116)
- chrome.exe (PID: 2336)
- chrome.exe (PID: 2992)
- chrome.exe (PID: 2584)
- chrome.exe (PID: 2956)
- chrome.exe (PID: 2952)
- chrome.exe (PID: 3112)
- chrome.exe (PID: 3776)
- firefox.exe (PID: 3160)
- rundll32.exe (PID: 3960)
- runonce.exe (PID: 2116)
- net1.exe (PID: 2316)
- firefox.exe (PID: 1896)
- firefox.exe (PID: 2568)
- firefox.exe (PID: 3008)
- firefox.exe (PID: 4000)
- firefox.exe (PID: 2476)
- firefox.exe (PID: 2728)
- firefox.exe (PID: 1952)
- taskkill.exe (PID: 3236)
- taskkill.exe (PID: 1000)
- taskkill.exe (PID: 3336)
- taskkill.exe (PID: 3988)
- taskkill.exe (PID: 4068)
- taskkill.exe (PID: 3352)
- taskkill.exe (PID: 2268)
- taskkill.exe (PID: 3352)
- certutil.exe (PID: 3812)
- certutil.exe (PID: 2468)
- iexplore.exe (PID: 3648)
- iexplore.exe (PID: 3236)
- rundll32.exe (PID: 5712)
Reads the hosts file
- chrome.exe (PID: 3284)
- chrome.exe (PID: 1708)
Reads settings of System Certificates
- chrome.exe (PID: 1708)
- IDMan.exe (PID: 556)
- IDMan.exe (PID: 2292)
- IDMan.exe (PID: 2996)
- iexplore.exe (PID: 3648)
- iexplore.exe (PID: 3236)
- IDMan.exe (PID: 4976)
Application launched itself
- chrome.exe (PID: 3284)
- firefox.exe (PID: 2212)
- firefox.exe (PID: 4000)
- iexplore.exe (PID: 3236)
Reads the date of Windows installation
- chrome.exe (PID: 2584)
- firefox.exe (PID: 4000)
Checks Windows Trust Settings
- IDMan.exe (PID: 556)
- IDMan.exe (PID: 2292)
- iexplore.exe (PID: 3648)
- IDMan.exe (PID: 2996)
- IDMan.exe (PID: 4976)
- iexplore.exe (PID: 3236)
Dropped object may contain Bitcoin addresses
- IDMan.exe (PID: 556)
- firefox.exe (PID: 4000)
Reads CPU info
- runonce.exe (PID: 2116)
- firefox.exe (PID: 4000)
- reg.exe (PID: 2468)
- reg.exe (PID: 2144)
Creates files in the program directory
- firefox.exe (PID: 4000)
Creates files in the user directory
- firefox.exe (PID: 4000)
- iexplore.exe (PID: 3236)
- iexplore.exe (PID: 3648)
Changes internet zones settings
- iexplore.exe (PID: 3236)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3648)
- iexplore.exe (PID: 3236)
Reads internet explorer settings
- iexplore.exe (PID: 3648)
Changes settings of System certificates
- iexplore.exe (PID: 3648)
- iexplore.exe (PID: 3236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (18.4) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (13.3) |
| .exe | | | Win64 Executable (generic) (11.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (2.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:07:17 07:17:28+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 2443264 |
| InitializedDataSize: | 3287040 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x208dfc |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.39.2.2 |
| ProductVersionNumber: | 6.39.2.2 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | http://www.internetdownloadmanager.com |
| CompanyName: | Tonec Inc. |
| FileDescription: | Internet Download Manager (IDM) |
| FileVersion: | 6, 39, 2, 2 |
| InternalName: | Internet Download Manager |
| LegalCopyright: | Tonec FZE, Copyright © 1999 - 2021 |
| LegalTrademarks: | Internet Download Manager |
| OriginalFileName: | IDMan.exe |
| ProductName: | Internet Download Manager (IDM) |
| ProductVersion: | 6, 39, 2, 2 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 17-Jul-2021 05:17:28 |
| Detected languages: |
|
| Debug artifacts: |
|
| Comments: | http://www.internetdownloadmanager.com |
| CompanyName: | Tonec Inc. |
| FileDescription: | Internet Download Manager (IDM) |
| FileVersion: | 6, 39, 2, 2 |
| InternalName: | Internet Download Manager |
| LegalCopyright: | Tonec FZE, Copyright © 1999 - 2021 |
| LegalTrademarks: | Internet Download Manager |
| OriginalFilename: | IDMan.exe |
| ProductName: | Internet Download Manager (IDM) |
| ProductVersion: | 6, 39, 2, 2 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 17-Jul-2021 05:17:28 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0025477C | 0x00254800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.59412 |
.rdata | 0x00256000 | 0x000B8906 | 0x000B8A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.8694 |
.data | 0x0030F000 | 0x00010FBC | 0x00008000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.60185 |
.rsrc | 0x00320000 | 0x00224BC0 | 0x00224C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.45492 |
.reloc | 0x00545000 | 0x00034084 | 0x00034200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.18266 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.30925 | 1633 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 5.47275 | 4264 | UNKNOWN | English - United States | RT_ICON |
3 | 5.90283 | 1128 | UNKNOWN | English - United States | RT_ICON |
4 | 6.73358 | 2216 | UNKNOWN | English - United States | RT_ICON |
5 | 6.23219 | 4264 | UNKNOWN | English - United States | RT_ICON |
6 | 6.15891 | 2216 | UNKNOWN | English - United States | RT_ICON |
7 | 3.13238 | 338 | UNKNOWN | English - United States | RT_STRING |
8 | 1.0333 | 44 | UNKNOWN | English - United States | RT_STRING |
9 | 4.68664 | 4264 | UNKNOWN | English - United States | RT_ICON |
10 | 6.28402 | 2216 | UNKNOWN | English - United States | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
KERNEL32.dll |
SHLWAPI.dll |
USER32.dll |
WS2_32.dll (delay-loaded) |
Total processes
481
Monitored processes
422
Malicious processes
90
Suspicious processes
30
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1048,14774496759062719614,14214145412005656972,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1056 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 188 | AB2EF g93Xcv53d5 | C:\Users\admin\AppData\Local\Temp\ytmp\AB2EF.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 188 | "NSudo86x.exe" -Wait -U:T -P:E -UseCurrentConsole REG DELETE "HKU\.DEFAULT\Software\Classes\Wow6432Node\CLSID\{79873CC5-3951-43ED-BDF9-D8759474B6FD}" /f | C:\Users\admin\AppData\Local\Temp\ytmp\NSudo86x.exe | — | cmd.exe | |||||||||||
User: admin Company: M2-Team Integrity Level: HIGH Description: NSudo for Windows Exit code: 0 Version: 6.2.1812.31 Modules
| |||||||||||||||
| 188 | REG DELETE "HKCU\Software\Wow6432Node\DownloadManager" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 368 | "C:\Program Files\Internet Download Manager\IEMonitor.exe" | C:\Program Files\Internet Download Manager\IEMonitor.exe | — | IDMan.exe | |||||||||||
User: admin Company: Tonec Inc. Integrity Level: MEDIUM Description: Internet Download Manager agent for click monitoring in IE-based browsers Exit code: 1 Version: 6, 37, 8, 1 Modules
| |||||||||||||||
| 368 | FART -c -i "idm.tmp" "68dd140000" "6a00909090" | C:\Users\admin\AppData\Local\Temp\ytmp\fart.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 368 | 7za e files.tmp -pidm@idm420 -aoa "NSudo86x.exe" | C:\Users\admin\AppData\Local\Temp\ytmp\7za.exe | cmd.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 368 | REG DELETE "HKLM\Software\Classes\CLSID\{07999AC3-058B-40BF-984F-69EB1E554CA7}" /f | C:\Windows\system32\REG.exe | NSudo86x.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 368 | REG DELETE "HKLM\Software\Classes\CLSID\{79873CC5-3951-43ED-BDF9-D8759474B6FD}" /f | C:\Windows\system32\REG.exe | NSudo86x.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 368 | "NSudo86x.exe" -Wait -U:T -P:E -UseCurrentConsole REG DELETE "HKLM\Software\Wow6432Node\Internet Download Manager" /f | C:\Users\admin\AppData\Local\Temp\ytmp\NSudo86x.exe | — | cmd.exe | |||||||||||
User: admin Company: M2-Team Integrity Level: HIGH Description: NSudo for Windows Exit code: 0 Version: 6.2.1812.31 Modules
| |||||||||||||||
Total events
80 867
Read events
79 357
Write events
1 405
Delete events
105
Modification events
| (PID) Process: | (3836) IDMan.exe | Key: | HKEY_CURRENT_USER\Software\DownloadManager\IDMBI\IEXPLORE |
| Operation: | write | Name: | name |
Value: Internet Explorer | |||
| (PID) Process: | (3836) IDMan.exe | Key: | HKEY_CURRENT_USER\Software\DownloadManager\IDMBI\IEXPLORE |
| Operation: | write | Name: | int |
Value: 1 | |||
| (PID) Process: | (3836) IDMan.exe | Key: | HKEY_CURRENT_USER\Software\DownloadManager\IDMBI\msedge |
| Operation: | write | Name: | name |
Value: Microsoft Edge | |||
| (PID) Process: | (3836) IDMan.exe | Key: | HKEY_CURRENT_USER\Software\DownloadManager\IDMBI\msedge |
| Operation: | write | Name: | int |
Value: 1 | |||
| (PID) Process: | (3836) IDMan.exe | Key: | HKEY_CURRENT_USER\Software\DownloadManager\IDMBI\Firefox |
| Operation: | write | Name: | name |
Value: Mozilla Firefox | |||
| (PID) Process: | (3836) IDMan.exe | Key: | HKEY_CURRENT_USER\Software\DownloadManager\IDMBI\Firefox |
| Operation: | write | Name: | int |
Value: 1 | |||
| (PID) Process: | (3836) IDMan.exe | Key: | HKEY_CURRENT_USER\Software\DownloadManager\IDMBI\chrome |
| Operation: | write | Name: | name |
Value: Google Chrome | |||
| (PID) Process: | (3836) IDMan.exe | Key: | HKEY_CURRENT_USER\Software\DownloadManager\IDMBI\chrome |
| Operation: | write | Name: | int |
Value: 1 | |||
| (PID) Process: | (3836) IDMan.exe | Key: | HKEY_CURRENT_USER\Software\DownloadManager\IDMBI\OPERA |
| Operation: | write | Name: | name |
Value: Opera | |||
| (PID) Process: | (3836) IDMan.exe | Key: | HKEY_CURRENT_USER\Software\DownloadManager\IDMBI\OPERA |
| Operation: | write | Name: | int |
Value: 1 | |||
Executable files
25
Suspicious files
278
Text files
464
Unknown types
74
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-615F4E19-CD4.pma | — | |
MD5:— | SHA256:— | |||
| 1708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\index | binary | |
MD5:— | SHA256:— | |||
| 3284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\bcb9dd7d-e6db-4374-b3e5-eea8b1e20a9f.tmp | text | |
MD5:— | SHA256:— | |||
| 3284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 3284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF9791c.TMP | text | |
MD5:64AD8ED3E666540337BA541C549F72F7 | SHA256:BECBDB08B5B37D203A85F2E974407334053BB1D2270F0B3C9A4DB963896F2206 | |||
| 3284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF9792b.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
| 3284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:00046F773EFDD3C8F8F6D0F87A2B93DC | SHA256:593EDE11D17AF7F016828068BCA2E93CF240417563FB06DC8A579110AEF81731 | |||
| 1708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\data_1 | vxd | |
MD5:259E7ED5FB3C6C90533B963DA5B2FC1B | SHA256:35BB2F189C643DCF52ECF037603D104035ECDC490BF059B7736E58EF7D821A09 | |||
| 3284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF979b8.TMP | text | |
MD5:81F483F77EE490F35306A4F94DB2286B | SHA256:82434CE3C9D13F509EBEEBE3A7A1A1DE9AB4557629D9FC855761E0CFA45E8BCE | |||
| 3284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:7721CDA9F5B73CE8A135471EB53B4E0E | SHA256:DD730C576766A46FFC84E682123248ECE1FF1887EC0ACAB22A5CE93A450F4500 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
64
TCP/UDP connections
155
DNS requests
179
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/YGkwa4MXjfWSuERyWQYP_A_4/aapLKTSZ439A-0g3nqJr3Q | US | — | — | whitelisted |
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | crx | 2.81 Kb | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 5.63 Kb | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | ini | 20.9 Kb | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 10.1 Kb | whitelisted |
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/mdmguwvzgrqfqo2pe6jth7ue6y_45/khaoiebndkojlmppeemjhbpbandiljpe_45_win_adcs3xk2sovipzzwrg2uk2acjzwq.crx3 | US | binary | 419 Kb | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 358 Kb | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 718 Kb | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 178 Kb | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 43.4 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1708 | chrome.exe | 216.58.212.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1708 | chrome.exe | 216.58.212.174:443 | apis.google.com | Google Inc. | US | whitelisted |
1936 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | Microsoft Corporation | GB | whitelisted |
1708 | chrome.exe | 172.217.23.99:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
1708 | chrome.exe | 34.104.35.123:80 | edgedl.me.gvt1.com | — | US | whitelisted |
1708 | chrome.exe | 216.58.212.150:443 | i.ytimg.com | Google Inc. | US | whitelisted |
1708 | chrome.exe | 216.58.212.142:443 | play.google.com | Google Inc. | US | whitelisted |
1708 | chrome.exe | 216.58.212.130:443 | adservice.google.com | Google Inc. | US | whitelisted |
1708 | chrome.exe | 172.67.164.43:443 | idmcrackeys.com | — | US | unknown |
1708 | chrome.exe | 142.250.184.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clients2.google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2996 | IDMan.exe | Potential Corporate Privacy Violation | ET POLICY Outgoing Basic Auth Base64 HTTP Password detected unencrypted |