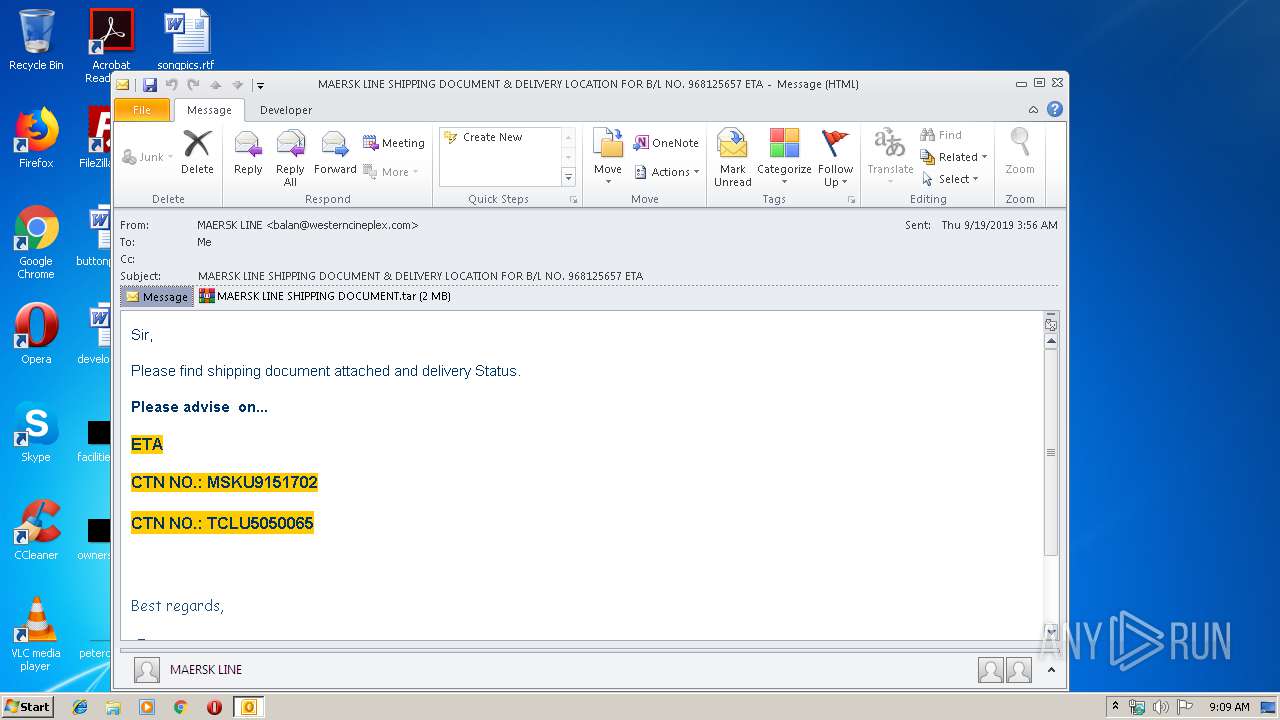
| File name: | 46YhX91Wb2zKPyyKUGF.eml |
| Full analysis: | https://app.any.run/tasks/dad059aa-9823-4b48-bbae-7b53814f35d1 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | September 19, 2019, 08:08:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | CEAB3CEA6F4ADF99C9FA5010EF17B747 |
| SHA1: | 427AAA65DB68573FDC6A28C50A19FBCE008FF1F4 |
| SHA256: | DAA748F2CA161BF6A8960B3C04CABD09CBAD4D494C4B009F5813C3E54A79FA72 |
| SSDEEP: | 24576:vLp5WVJMiLzsyOE3hvCEav6qcGkptrLegC/nw3l2VMWeIrYR30dK0qDKDgeLOR7z:vLda3JPaIRtHegCfwMfcRdDKZGHvSl6 |
MALICIOUS
Application was dropped or rewritten from another process
- MAERSK LINE SHIPPING DOCUMENT.exe (PID: 2664)
- hao.exe (PID: 3560)
AGENTTESLA was detected
- RegSvcs.exe (PID: 4028)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 4028)
SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3504)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3504)
Executable content was dropped or overwritten
- MAERSK LINE SHIPPING DOCUMENT.exe (PID: 2664)
- WinRAR.exe (PID: 3024)
Drop AutoIt3 executable file
- MAERSK LINE SHIPPING DOCUMENT.exe (PID: 2664)
Reads Windows Product ID
- RegSvcs.exe (PID: 4028)
Reads Environment values
- RegSvcs.exe (PID: 4028)
Checks for external IP
- RegSvcs.exe (PID: 4028)
INFO
Dropped object may contain Bitcoin addresses
- MAERSK LINE SHIPPING DOCUMENT.exe (PID: 2664)
Reads settings of System Certificates
- RegSvcs.exe (PID: 4028)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
39
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2664 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.7630\MAERSK LINE SHIPPING DOCUMENT.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.7630\MAERSK LINE SHIPPING DOCUMENT.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3024 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\N10KKQKJ\MAERSK LINE SHIPPING DOCUMENT.tar" | C:\Program Files\WinRAR\WinRAR.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3504 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\46YhX91Wb2zKPyyKUGF.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3560 | "C:\Users\admin\AppData\Local\Temp\28535807\hao.exe" uvqolw | C:\Users\admin\AppData\Local\Temp\28535807\hao.exe | — | MAERSK LINE SHIPPING DOCUMENT.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 8, 1 Modules
| |||||||||||||||
| 4028 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | hao.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
Total events
2 428
Read events
1 977
Write events
432
Delete events
19
Modification events
| (PID) Process: | (3504) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3504) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3504) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | n$ |
Value: 7F6E2400B00D0000010000000000000000000000 | |||
| (PID) Process: | (3504) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: B00D0000B21B5788C16ED50100000000 | |||
| (PID) Process: | (3504) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3504) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220222080 | |||
| (PID) Process: | (3504) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3504) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3504) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3504) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1328742421 | |||
Executable files
2
Suspicious files
2
Text files
94
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3504 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR9A70.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3504 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp9CA3.tmp | — | |
MD5:— | SHA256:— | |||
| 3504 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\N10KKQKJ\MAERSK LINE SHIPPING DOCUMENT (2).tar\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2664 | MAERSK LINE SHIPPING DOCUMENT.exe | C:\Users\admin\AppData\Local\Temp\28535807\uvqolw | — | |
MD5:— | SHA256:— | |||
| 3504 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\829110EA.dat | image | |
MD5:— | SHA256:— | |||
| 3504 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3504 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\N10KKQKJ\MAERSK LINE SHIPPING DOCUMENT.tar | compressed | |
MD5:— | SHA256:— | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.7630\MAERSK LINE SHIPPING DOCUMENT.exe | executable | |
MD5:— | SHA256:— | |||
| 2664 | MAERSK LINE SHIPPING DOCUMENT.exe | C:\Users\admin\AppData\Local\Temp\28535807\sof.ico | text | |
MD5:— | SHA256:— | |||
| 2664 | MAERSK LINE SHIPPING DOCUMENT.exe | C:\Users\admin\AppData\Local\Temp\28535807\jkf.dat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
3
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4028 | RegSvcs.exe | GET | 200 | 3.224.145.145:80 | http://checkip.amazonaws.com/ | US | text | 14 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3504 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
4028 | RegSvcs.exe | 3.224.145.145:80 | checkip.amazonaws.com | — | US | shared |
4028 | RegSvcs.exe | 199.193.7.228:587 | smtp.privateemail.com | Namecheap, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
checkip.amazonaws.com |
| malicious |
smtp.privateemail.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4028 | RegSvcs.exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla IP Check |
4028 | RegSvcs.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
2 ETPRO signatures available at the full report