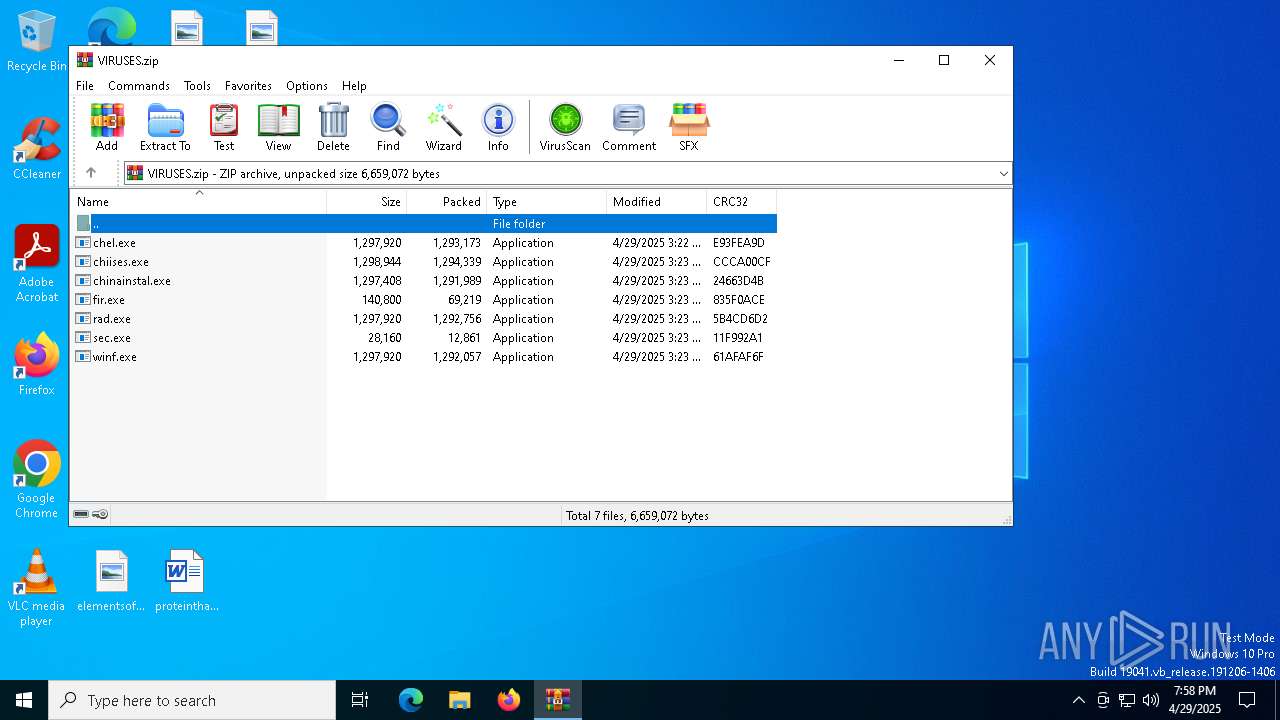
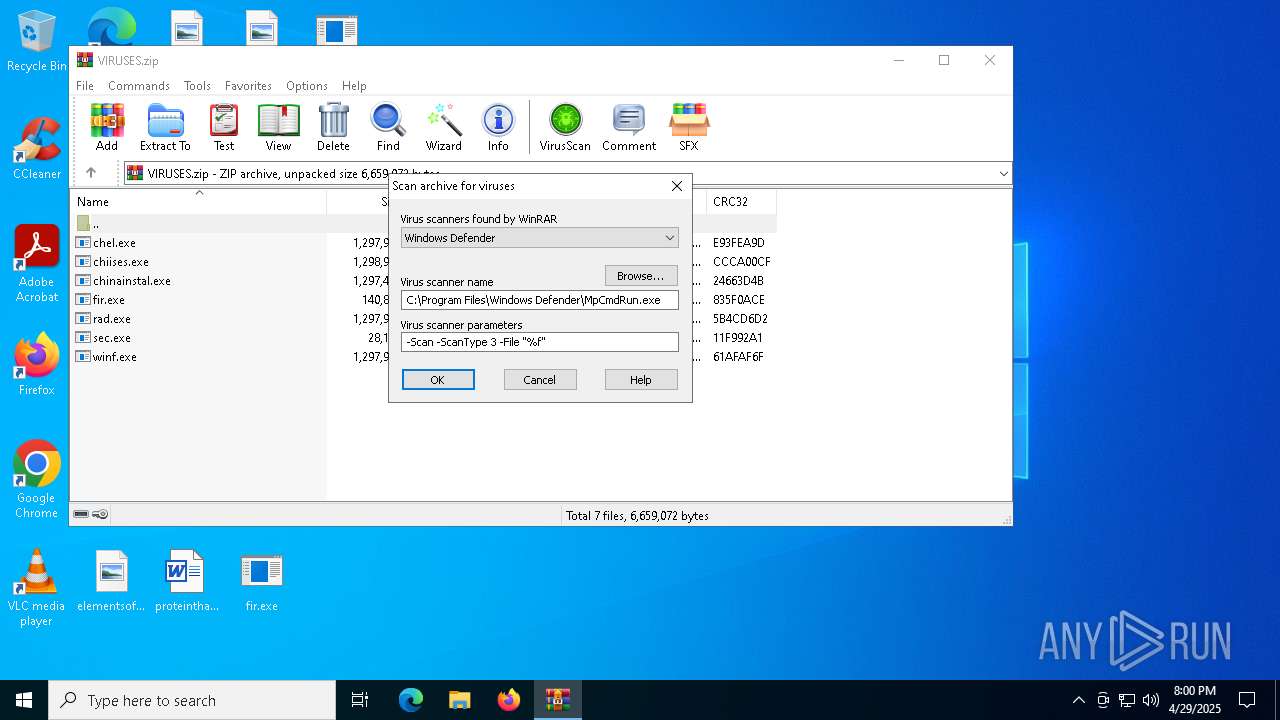
| File name: | VIRUSES.zip |
| Full analysis: | https://app.any.run/tasks/78d0fce4-7cc4-499a-9e2c-284a239ba2d6 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 29, 2025, 19:58:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 45A71F5F24F1E1B3B0B717C1DE6D0167 |
| SHA1: | 4D9807BE2DD263C075D409C8E6246CCE23558D14 |
| SHA256: | DA3E4EA2FF5C13C721B5B4A0FC20D52E528699146E1548E8765EE785FD22588A |
| SSDEEP: | 98304:nrDNAD1S/zj72Ywgw/I1K2J9B+bQNHbMyCpodCQu2jdjZ2mhRgolBhKxsgA6nTmo:aVYMWIFWX+ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2108)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 516)
- cmd.exe (PID: 4152)
- cmd.exe (PID: 7388)
VIDAR mutex has been found
- fir.exe (PID: 6816)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
Connects to the CnC server
- svchost.exe (PID: 2196)
LUMMA mutex has been found
- rad.exe (PID: 6068)
- winf.exe (PID: 6436)
Actions looks like stealing of personal data
- rad.exe (PID: 6068)
- fir.exe (PID: 6816)
- winf.exe (PID: 6436)
Steals credentials from Web Browsers
- rad.exe (PID: 6068)
- fir.exe (PID: 6816)
- winf.exe (PID: 6436)
SUSPICIOUS
Starts CMD.EXE for commands execution
- sec.exe (PID: 4452)
- service.exe (PID: 2908)
- service.exe (PID: 7344)
- WinRAR.exe (PID: 2108)
Executable content was dropped or overwritten
- sec.exe (PID: 4452)
Reads security settings of Internet Explorer
- sec.exe (PID: 4452)
- fir.exe (PID: 6816)
- service.exe (PID: 2908)
- service.exe (PID: 7344)
- WinRAR.exe (PID: 2108)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- fir.exe (PID: 6816)
- winf.exe (PID: 6436)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
Searches for installed software
- fir.exe (PID: 6816)
- winf.exe (PID: 6436)
- rad.exe (PID: 6068)
The process executes via Task Scheduler
- service.exe (PID: 7344)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 2108)
INFO
Manual execution by a user
- sec.exe (PID: 4452)
- fir.exe (PID: 6816)
- winf.exe (PID: 6436)
- service.exe (PID: 2908)
- rad.exe (PID: 6068)
Checks supported languages
- sec.exe (PID: 4452)
- fir.exe (PID: 6816)
- winf.exe (PID: 6436)
- service.exe (PID: 2908)
- rad.exe (PID: 6068)
- service.exe (PID: 7344)
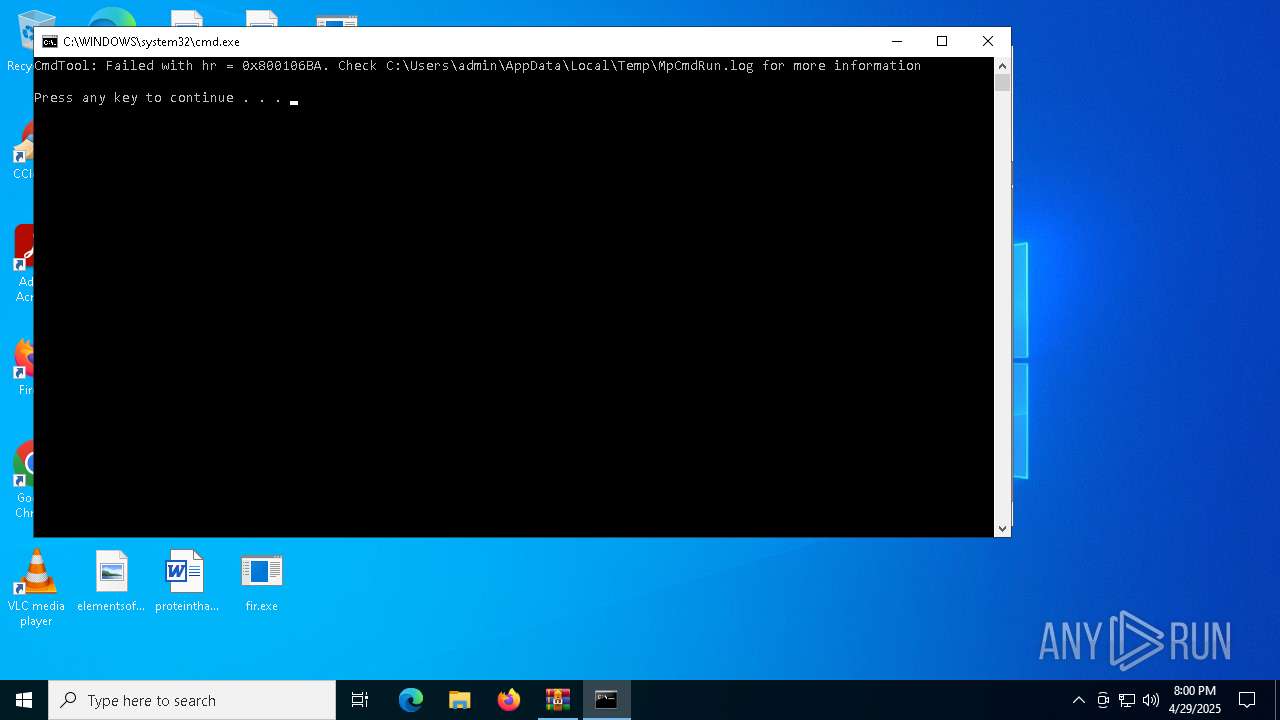
- MpCmdRun.exe (PID: 7672)
Creates files or folders in the user directory
- sec.exe (PID: 4452)
- fir.exe (PID: 6816)
Process checks computer location settings
- sec.exe (PID: 4452)
- service.exe (PID: 2908)
- service.exe (PID: 7344)
Reads the computer name
- sec.exe (PID: 4452)
- fir.exe (PID: 6816)
- service.exe (PID: 2908)
- winf.exe (PID: 6436)
- rad.exe (PID: 6068)
- service.exe (PID: 7344)
- MpCmdRun.exe (PID: 7672)
Auto-launch of the file from Task Scheduler
- cmd.exe (PID: 516)
- cmd.exe (PID: 4152)
- cmd.exe (PID: 7388)
Creates files in the program directory
- fir.exe (PID: 6816)
Checks proxy server information
- fir.exe (PID: 6816)
- slui.exe (PID: 7576)
Reads the software policy settings
- fir.exe (PID: 6816)
- winf.exe (PID: 6436)
- rad.exe (PID: 6068)
- slui.exe (PID: 7576)
Reads the machine GUID from the registry
- fir.exe (PID: 6816)
- winf.exe (PID: 6436)
- rad.exe (PID: 6068)
Attempting to use instant messaging service
- winf.exe (PID: 6436)
- fir.exe (PID: 6816)
Reads product name
- fir.exe (PID: 6816)
Reads Environment values
- fir.exe (PID: 6816)
Reads CPU info
- fir.exe (PID: 6816)
Application launched itself
- chrome.exe (PID: 5800)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2108)
Create files in a temporary directory
- MpCmdRun.exe (PID: 7672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:29 18:22:56 |
| ZipCRC: | 0xe93fea9d |
| ZipCompressedSize: | 1293173 |
| ZipUncompressedSize: | 1297920 |
| ZipFileName: | chel.exe |
Total processes
178
Monitored processes
53
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Windows\System32\cmd.exe" /C schtasks /create /tn GoogleUpdaterex /tr %APPDATA%\service.exe /st 00:00 /du 9999:59 /sc daily /ri 1 /f | C:\Windows\SysWOW64\cmd.exe | — | sec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --remote-debugging-port=9223 --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3276 --field-trial-handle=1972,i,9788737166110424175,9924031214480354501,262144 --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2220 --field-trial-handle=1972,i,9788737166110424175,9924031214480354501,262144 --variations-seed-version /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=6044 --field-trial-handle=1972,i,9788737166110424175,9924031214480354501,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1812 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2108 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\VIRUSES.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2616 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR2108.15772\Rar$Scan125538.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2908 | C:\Users\admin\AppData\Roaming\service.exe | C:\Users\admin\AppData\Roaming\service.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3676 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5908 --field-trial-handle=1972,i,9788737166110424175,9924031214480354501,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
35 022
Read events
34 960
Write events
55
Delete events
7
Modification events
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\VIRUSES.zip | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
13
Suspicious files
360
Text files
36
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF1111a1.TMP | — | |
MD5:— | SHA256:— | |||
| 5800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF1111a1.TMP | — | |
MD5:— | SHA256:— | |||
| 5800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1111b0.TMP | — | |
MD5:— | SHA256:— | |||
| 5800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF1111b0.TMP | — | |
MD5:— | SHA256:— | |||
| 5800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1111cf.TMP | — | |
MD5:— | SHA256:— | |||
| 5800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5800 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
77
TCP/UDP connections
71
DNS requests
35
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 149.154.167.99:443 | https://t.me/m00f3r | unknown | — | — | unknown |
2104 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 5.75.209.111:443 | https://66.44.4t.com/ | unknown | — | — | unknown |
— | — | GET | 200 | 149.154.167.99:443 | https://t.me/wermnjgk34 | unknown | html | 11.9 Kb | whitelisted |
— | — | POST | 200 | 5.75.209.111:443 | https://66.44.4t.com/ | unknown | text | 2.13 Kb | malicious |
— | — | POST | 200 | 5.75.209.111:443 | https://66.44.4t.com/ | unknown | text | 58 b | unknown |
— | — | POST | 200 | 188.114.97.3:443 | https://lucticiq.run/tqwu | unknown | binary | 32.7 Kb | unknown |
— | — | POST | 200 | 5.75.209.111:443 | https://66.44.4t.com/ | unknown | text | 5.69 Kb | malicious |
— | — | POST | 200 | 104.21.51.232:443 | https://zenithcorde.top/auid | unknown | binary | 69 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6816 | fir.exe | 149.154.167.99:443 | t.me | Telegram Messenger Inc | GB | whitelisted |
6816 | fir.exe | 5.75.209.111:443 | 66.44.4t.com | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
t.me |
| whitelisted |
66.44.4t.com |
| malicious |
lucticiq.run |
| unknown |
bearjk.live |
| malicious |
zenithcorde.top |
| malicious |
clientservices.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6816 | fir.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
6436 | winf.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
2196 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected Domain Associated with Malware Distribution (zenithcorde .top) |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (bearjk .live) |
— | — | A Network Trojan was detected | ET MALWARE Win32/Stealc/Vidar Stealer Style Headers In HTTP POST M1 |
— | — | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
— | — | Malware Command and Control Activity Detected | ET MALWARE Win32/Stealc/Vidar Stealer Style Headers In HTTP POST M2 |
— | — | Malware Command and Control Activity Detected | ET MALWARE Win32/Stealc/Vidar Stealer Active C2 Responding with plugins Config M1 |
— | — | Malware Command and Control Activity Detected | ET MALWARE Win32/Stealc/Vidar Stealer Style Headers In HTTP POST M2 |