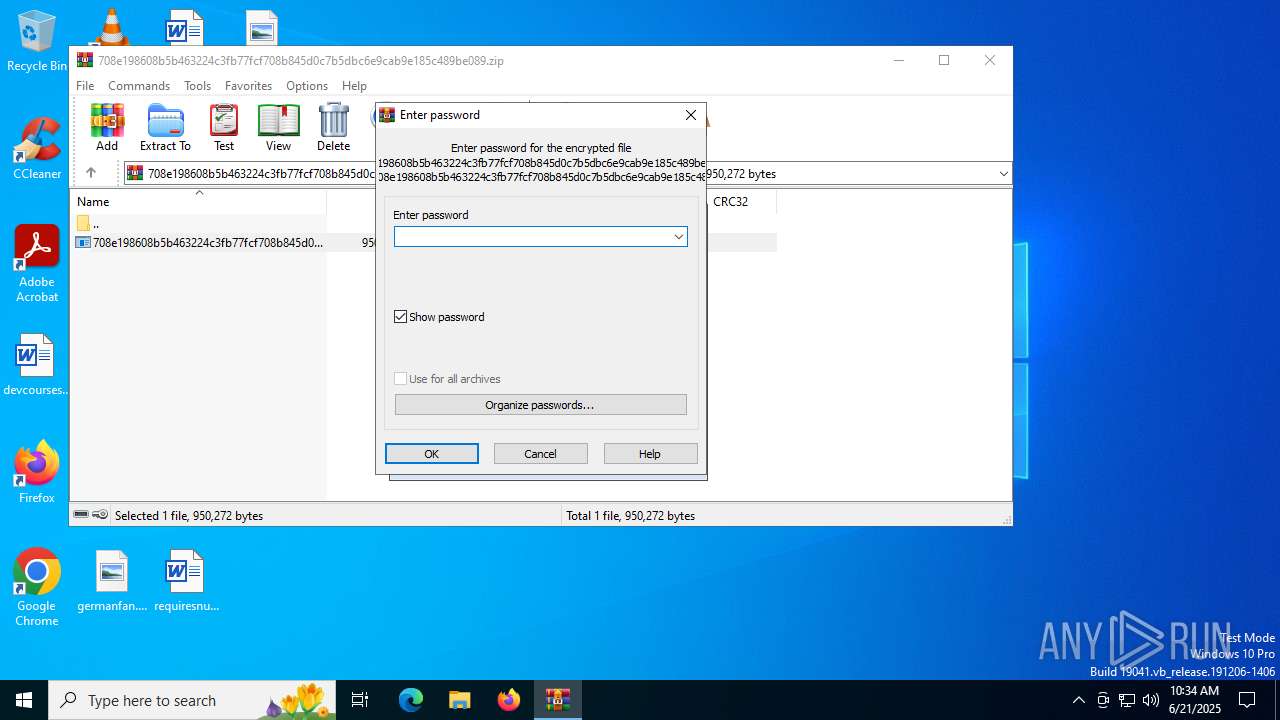
| URL: | https://bazaar.abuse.ch/download/708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089/ |
| Full analysis: | https://app.any.run/tasks/7382c78d-52a2-4171-8bb2-70fad62f6df1 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | June 21, 2025, 10:33:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 26AB4180E4068FA2733BE1E50BF22DD1 |
| SHA1: | BE86398EE4847BE302808CDC40331FBE5FBADA11 |
| SHA256: | D9F5981A4D96420337618038E3E5DEC032ED8296C4D0D79CFADCAB48955587C7 |
| SSDEEP: | 3:N8N0uDWB4SwZqxTyyvq926SHQBSGEHu7r:23GfHVyqp4 |
MALICIOUS
AGENTTESLA mutex has been found
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 8092)
Uses Task Scheduler to run other applications
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 8092)
AGENTTESLA has been detected (YARA)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 416)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5008)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 8092)
Executable content was dropped or overwritten
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 8092)
Application launched itself
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 8092)
INFO
Reads the computer name
- identity_helper.exe (PID: 7672)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 8092)
- identity_helper.exe (PID: 5952)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3160)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 416)
Reads Environment values
- identity_helper.exe (PID: 7672)
- identity_helper.exe (PID: 5952)
Checks supported languages
- identity_helper.exe (PID: 7672)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 8092)
- identity_helper.exe (PID: 5952)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3160)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 416)
Application launched itself
- msedge.exe (PID: 4500)
- msedge.exe (PID: 7984)
Launching a file from the Downloads directory
- msedge.exe (PID: 4500)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5008)
Reads the machine GUID from the registry
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 8092)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3160)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 416)
Reads Microsoft Office registry keys
- msedge.exe (PID: 4500)
Manual execution by a user
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3160)
Creates files or folders in the user directory
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 8092)
Process checks computer location settings
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 8092)
Create files in a temporary directory
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 8092)
Checks proxy server information
- slui.exe (PID: 7764)
Reads the software policy settings
- slui.exe (PID: 7764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(416) 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe
Protocolsmtp
Hostsmtp.godforeu.com
Port587
Usernamelogs@godforeu.com
PasswordO8k#Pz4sk:w_
Total processes
184
Monitored processes
42
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 416 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb5008.34948\708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb5008.34948\708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe | 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: App Version: 1.0.0.0 Modules
AgentTesla(PID) Process(416) 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe Protocolsmtp Hostsmtp.godforeu.com Port587 Usernamelogs@godforeu.com PasswordO8k#Pz4sk:w_ | |||||||||||||||
| 1760 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --always-read-main-dll --field-trial-handle=4472,i,2090558644395453462,15915679195657386307,262144 --variations-seed-version --mojo-platform-channel-handle=3584 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2780 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5248,i,17236579499339352241,9078439067122275940,262144 --variations-seed-version --mojo-platform-channel-handle=5152 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3160 | "C:\Users\admin\Desktop\708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe" | C:\Users\admin\Desktop\708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: App Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3580 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2212,i,2090558644395453462,15915679195657386307,262144 --variations-seed-version --mojo-platform-channel-handle=2516 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3608 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=4264,i,17236579499339352241,9078439067122275940,262144 --variations-seed-version --mojo-platform-channel-handle=5080 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3636 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4244,i,2090558644395453462,15915679195657386307,262144 --variations-seed-version --mojo-platform-channel-handle=4264 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3948 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2332,i,2090558644395453462,15915679195657386307,262144 --variations-seed-version --mojo-platform-channel-handle=2320 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 4084 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6512,i,2090558644395453462,15915679195657386307,262144 --variations-seed-version --mojo-platform-channel-handle=6936 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 4372 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6652,i,2090558644395453462,15915679195657386307,262144 --variations-seed-version --mojo-platform-channel-handle=6836 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
10 788
Read events
10 740
Write events
48
Delete events
0
Modification events
| (PID) Process: | (4500) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4500) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4500) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4500) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4500) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: FC5B68CBA8962F00 | |||
| (PID) Process: | (4500) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {B73300CD-4909-4D2A-858B-276CB17C70DF} | |||
| (PID) Process: | (4500) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {6EDA602C-E13F-4078-B6DE-E3C50741A62B} | |||
| (PID) Process: | (4500) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {9A0FAE45-3C35-4033-8968-83F50C5F9FC9} | |||
| (PID) Process: | (4500) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {A174D751-C54A-4166-A307-ED3C1B363D9B} | |||
| (PID) Process: | (4500) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {68B2170C-40F9-4BA0-A6BE-24B26037BF7F} | |||
Executable files
13
Suspicious files
172
Text files
66
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4500 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1765bf.TMP | — | |
MD5:— | SHA256:— | |||
| 4500 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF1765af.TMP | — | |
MD5:— | SHA256:— | |||
| 4500 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4500 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1765bf.TMP | — | |
MD5:— | SHA256:— | |||
| 4500 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4500 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1765ed.TMP | — | |
MD5:— | SHA256:— | |||
| 4500 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4500 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF1765fd.TMP | — | |
MD5:— | SHA256:— | |||
| 4500 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4500 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1765fd.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
85
DNS requests
80
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3580 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:ElN-eKwyuZUMzSMmKUDgXqev1XwFqCXM1PBrHwixDyI&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
4168 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4864 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4864 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5060 | svchost.exe | HEAD | 200 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751046505&P2=404&P3=2&P4=XxE6l6E9aUBdvKv8bKmjLp2G9p8UoIfnqrKETiS5C7hqR4zioQDqPOF%2fUR6%2fjUtM%2bELIIw2Ge1T6qK3hNYZOSw%3d%3d | unknown | — | — | whitelisted |
5060 | svchost.exe | GET | 206 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751046505&P2=404&P3=2&P4=XxE6l6E9aUBdvKv8bKmjLp2G9p8UoIfnqrKETiS5C7hqR4zioQDqPOF%2fUR6%2fjUtM%2bELIIw2Ge1T6qK3hNYZOSw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6700 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3580 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3580 | msedge.exe | 104.19.229.21:443 | js.hcaptcha.com | CLOUDFLARENET | — | whitelisted |
3580 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3580 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3580 | msedge.exe | 151.101.130.49:443 | bazaar.abuse.ch | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
bazaar.abuse.ch |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
js.hcaptcha.com |
| whitelisted |
newassets.hcaptcha.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
3580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
3580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
3580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
3580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
3580 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |