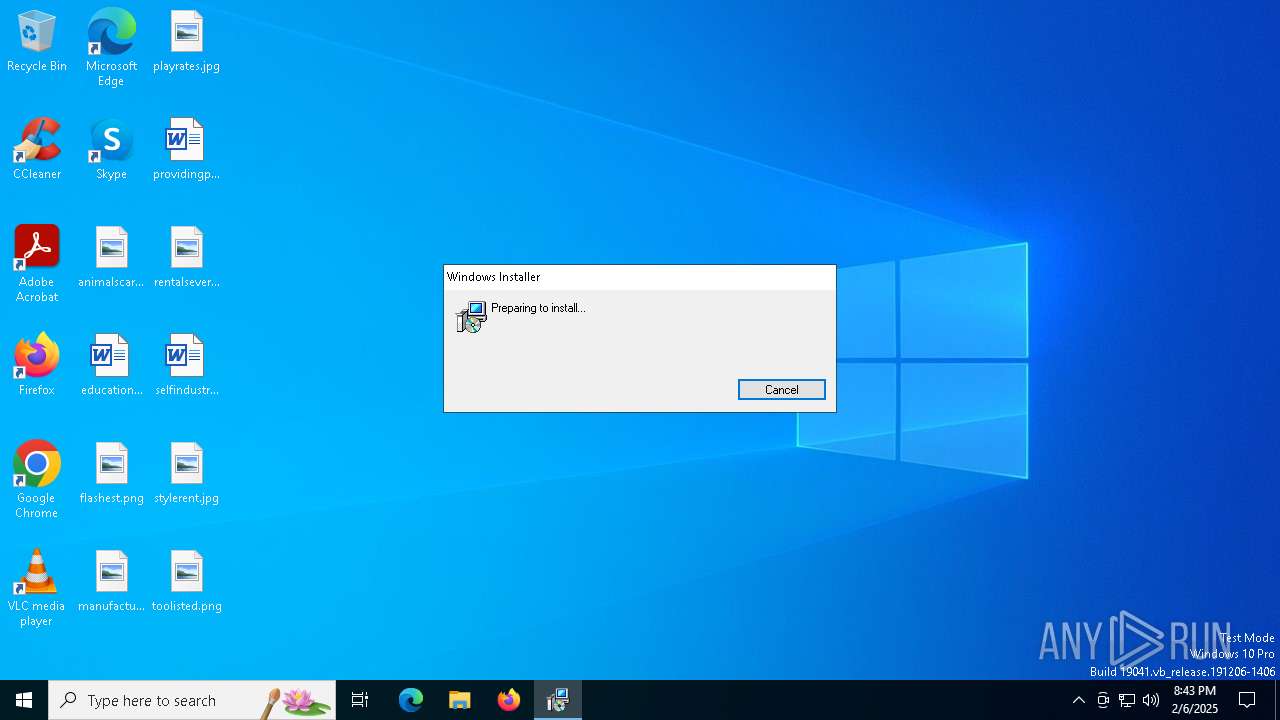
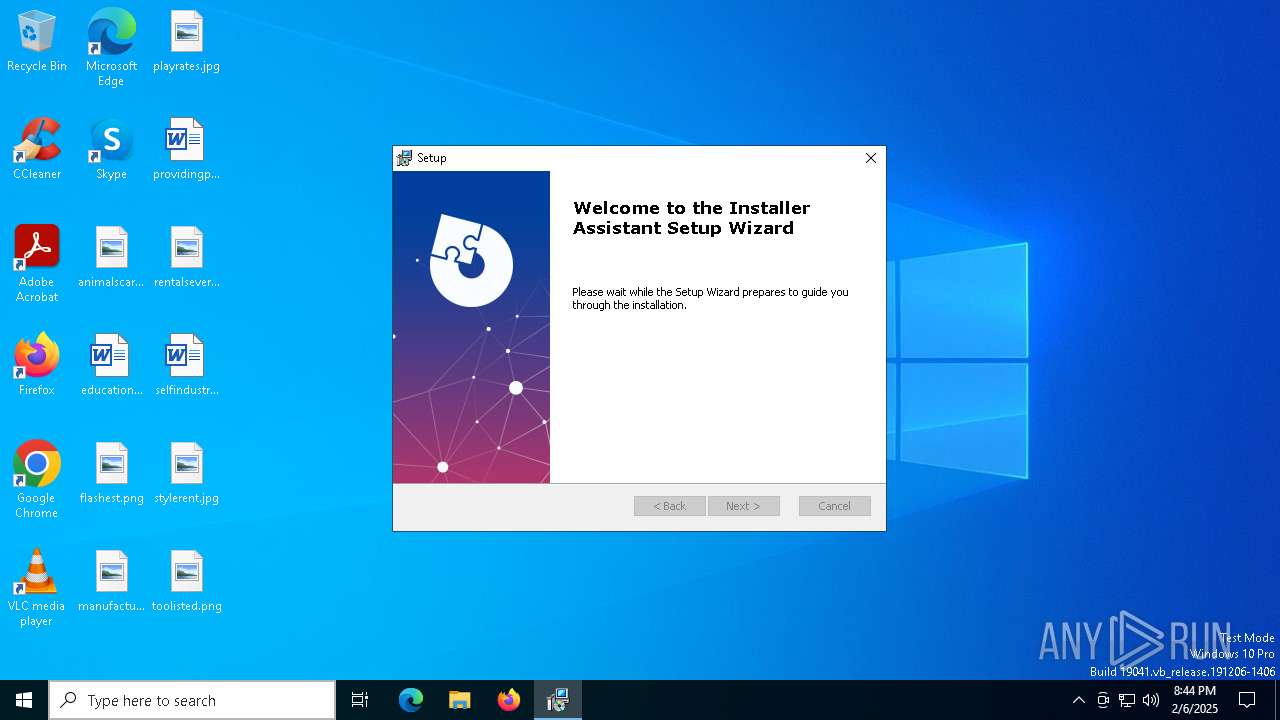
| File name: | TABSimulator_installer_39734987.msi |
| Full analysis: | https://app.any.run/tasks/aea7e5e7-adf5-4d1d-a07f-93eadd6018da |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | February 06, 2025, 20:43:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Dec 11 11:47:44 2009, Security: 0, Code page: 1252, Revision Number: {CDE0ABA5-0AE9-4CDC-BBA7-645FA44D11D5}, Number of Words: 10, Subject: Installer Assistant, Author: Eclipse Media Inc, Name of Creating Application: Advanced Installer 15.8 build b14c769f44, Template: ;1033, Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | 05353E5AC101EE2AF41C61F96F45CF09 |
| SHA1: | 771FB4A74E4021F7E3B35629E916C8E1DD5C37DD |
| SHA256: | D99B2EEDC405BD5A8447CB189DFF3B2E831174F94D2F98DD49A3716F347D11BA |
| SSDEEP: | 98304:LwAfqNgh2z/bqac+oUKi4sO8Lyt6S+w1BhpvsMl1QJ5Hs7jylBAQfCpwAfqNghXu:5LKFhS |
MALICIOUS
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 6692)
- msiexec.exe (PID: 6220)
- MSICB16.tmp (PID: 1292)
- msiexec.exe (PID: 6236)
- MSI3803.tmp (PID: 7156)
- msiexec.exe (PID: 6668)
Bypass execution policy to execute commands
- powershell.exe (PID: 6784)
- powershell.exe (PID: 2728)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 1540)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 1224)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 5712)
- powershell.exe (PID: 3736)
- powershell.exe (PID: 4716)
- powershell.exe (PID: 4536)
- powershell.exe (PID: 1064)
- powershell.exe (PID: 7124)
Changes the autorun value in the registry
- msiexec.exe (PID: 6692)
- msiexec.exe (PID: 6608)
BBWC has been detected (SURICATA)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 3172)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 1224)
- powershell.exe (PID: 4716)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 1064)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 6692)
- msiexec.exe (PID: 6220)
- MSICB16.tmp (PID: 1292)
- msiexec.exe (PID: 6236)
- MSI3803.tmp (PID: 7156)
- msiexec.exe (PID: 6668)
The process executes Powershell scripts
- msiexec.exe (PID: 6692)
- msiexec.exe (PID: 6220)
- msiexec.exe (PID: 6236)
- msiexec.exe (PID: 6668)
The process hide an interactive prompt from the user
- msiexec.exe (PID: 6692)
- msiexec.exe (PID: 6220)
- MSICB16.tmp (PID: 1292)
- msiexec.exe (PID: 6236)
- msiexec.exe (PID: 6668)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 6692)
- msiexec.exe (PID: 6220)
- msiexec.exe (PID: 6236)
- msiexec.exe (PID: 6668)
Retrieves command line args for running process (POWERSHELL)
- powershell.exe (PID: 6784)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6692)
- MSICB16.tmp (PID: 1292)
- MSI3803.tmp (PID: 7156)
- msiexec.exe (PID: 6668)
- MSI9149.tmp (PID: 5456)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 6524)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6608)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 1540)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 5712)
Access to an unwanted program domain was detected
- powershell.exe (PID: 1512)
- powershell.exe (PID: 3172)
Manipulates environment variables
- powershell.exe (PID: 1224)
- powershell.exe (PID: 4716)
Executes as Windows Service
- VSSVC.exe (PID: 4708)
- WmiApSrv.exe (PID: 7052)
Checks Windows Trust Settings
- msiexec.exe (PID: 6608)
- msiexec.exe (PID: 6668)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 6524)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 6692)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 1864)
Reverses array data (POWERSHELL)
- powershell.exe (PID: 1064)
- powershell.exe (PID: 7124)
Executable content was dropped or overwritten
- powershell.exe (PID: 1064)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 6524)
Starts application with an unusual extension
- msiexec.exe (PID: 6360)
Process drops legitimate windows executable
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 6524)
The executable file from the user directory is run by the CMD process
- sysinfo-app.exe (PID: 3620)
INFO
Reads the software policy settings
- msiexec.exe (PID: 6360)
- powershell.exe (PID: 6784)
- powershell.exe (PID: 2728)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 1540)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 5712)
- powershell.exe (PID: 3736)
- msiexec.exe (PID: 6608)
- powershell.exe (PID: 4536)
- msiexec.exe (PID: 6668)
- powershell.exe (PID: 1064)
- powershell.exe (PID: 7124)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 6524)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 1864)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6360)
- powershell.exe (PID: 6784)
- powershell.exe (PID: 2728)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 1540)
- powershell.exe (PID: 4020)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 5712)
- powershell.exe (PID: 3736)
- powershell.exe (PID: 4536)
- powershell.exe (PID: 1064)
- powershell.exe (PID: 7124)
Creates files or folders in the user directory
- msiexec.exe (PID: 6360)
- powershell.exe (PID: 6784)
- msiexec.exe (PID: 6692)
- msiexec.exe (PID: 6608)
- msiexec.exe (PID: 6668)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 6524)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 1864)
Checks supported languages
- msiexec.exe (PID: 6608)
- msiexec.exe (PID: 6692)
- msiexec.exe (PID: 6220)
- MSICB16.tmp (PID: 1292)
- msiexec.exe (PID: 6236)
- MSI3803.tmp (PID: 7156)
- msiexec.exe (PID: 6668)
- MSI9149.tmp (PID: 5456)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 6524)
- identity_helper.exe (PID: 1540)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 1864)
- sysinfo-app.exe (PID: 3620)
Checks proxy server information
- msiexec.exe (PID: 6360)
- powershell.exe (PID: 2728)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 1540)
- powershell.exe (PID: 1224)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 5712)
- powershell.exe (PID: 4716)
- powershell.exe (PID: 4536)
- msiexec.exe (PID: 6668)
- powershell.exe (PID: 1064)
- MSI9149.tmp (PID: 5456)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 6524)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 1864)
Reads the computer name
- msiexec.exe (PID: 6608)
- msiexec.exe (PID: 6692)
- msiexec.exe (PID: 6220)
- MSICB16.tmp (PID: 1292)
- msiexec.exe (PID: 6236)
- MSI3803.tmp (PID: 7156)
- msiexec.exe (PID: 6668)
- MSI9149.tmp (PID: 5456)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 6524)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 1864)
- identity_helper.exe (PID: 1540)
- sysinfo-app.exe (PID: 3620)
Reads Environment values
- msiexec.exe (PID: 6692)
- msiexec.exe (PID: 6220)
- MSICB16.tmp (PID: 1292)
- msiexec.exe (PID: 6236)
- MSI3803.tmp (PID: 7156)
- msiexec.exe (PID: 6668)
- identity_helper.exe (PID: 1540)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 1864)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6360)
- msiexec.exe (PID: 6692)
- msiexec.exe (PID: 6608)
- msiexec.exe (PID: 6668)
The sample compiled with english language support
- msiexec.exe (PID: 6360)
- msiexec.exe (PID: 6608)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 6524)
Create files in a temporary directory
- msiexec.exe (PID: 6692)
- powershell.exe (PID: 6784)
- msiexec.exe (PID: 6220)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 1540)
- powershell.exe (PID: 4020)
- msiexec.exe (PID: 6236)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 5712)
- powershell.exe (PID: 3736)
- powershell.exe (PID: 4536)
- powershell.exe (PID: 1064)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 6524)
- powershell.exe (PID: 2728)
Application launched itself
- msiexec.exe (PID: 6692)
- msedge.exe (PID: 2392)
Process checks computer location settings
- msiexec.exe (PID: 6692)
- MSICB16.tmp (PID: 1292)
- MSI3803.tmp (PID: 7156)
- MSI9149.tmp (PID: 5456)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 6524)
Disables trace logs
- powershell.exe (PID: 1512)
- powershell.exe (PID: 1540)
- powershell.exe (PID: 1224)
- powershell.exe (PID: 3172)
- powershell.exe (PID: 5712)
- powershell.exe (PID: 4716)
- powershell.exe (PID: 4536)
- powershell.exe (PID: 1064)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 1864)
- powershell.exe (PID: 2728)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1540)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 5712)
- powershell.exe (PID: 3172)
Starts application with an unusual extension
- msiexec.exe (PID: 6608)
Creates a software uninstall entry
- msiexec.exe (PID: 6608)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 4020)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6608)
- msiexec.exe (PID: 6668)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 6524)
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 1864)
Manages system restore points
- SrTasks.exe (PID: 3224)
Local mutex for internet shortcut management
- MSI9149.tmp (PID: 5456)
Reads product name
- setup_com.kiloo.subwaysurf_flow6mkt_39734987.exe (PID: 1864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2009:12:11 11:47:44 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {CDE0ABA5-0AE9-4CDC-BBA7-645FA44D11D5} |
| Words: | 10 |
| Subject: | Installer Assistant |
| Author: | Eclipse Media Inc |
| LastModifiedBy: | - |
| Software: | Advanced Installer 15.8 build b14c769f44 |
| Template: | ;1033 |
| Comments: | - |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
227
Monitored processes
86
Malicious processes
6
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6200 --field-trial-handle=2392,i,13856127076164865198,10565999326765818343,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1064 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss8627.tmp.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1192 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3128 --field-trial-handle=2392,i,13856127076164865198,10565999326765818343,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1200 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1224 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -noninteractive -ExecutionPolicy bypass -c "$w="$env:APPDATA"+'/BBWC/'; [Reflection.Assembly]::Load([System.IO.File]::ReadAllBytes($w+'WebCompanion.dll'));[WebCompanion.StartUp]::Start()" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | MSICB16.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1292 | "C:\WINDOWS\Installer\MSICB16.tmp" /DontWait /HideWindow /dir "C:\Users\admin\AppData\Roaming\BBWC\" C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe -noninteractive -ExecutionPolicy bypass -c "$w="$env:APPDATA"+'/BBWC/'; [Reflection.Assembly]::Load([System.IO.File]::ReadAllBytes($w+'WebCompanion.dll'));[WebCompanion.StartUp]::Start()" | C:\Windows\Installer\MSICB16.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Caphyon LTD Integrity Level: MEDIUM Description: File that launches another file Exit code: 0 Version: 15.8.0.0 Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss9DE6.tmp.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1540 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pssBFE9.tmp.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
90 178
Read events
89 694
Write events
445
Delete events
39
Modification events
| (PID) Process: | (2728) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2728) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2728) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2728) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2728) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2728) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2728) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2728) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2728) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2728) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
74
Suspicious files
331
Text files
111
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6692 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\msiBECF.tmp.txt | — | |
MD5:— | SHA256:— | |||
| 6692 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pssBED0.tmp.ps1 | — | |
MD5:— | SHA256:— | |||
| 6692 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pssC190.tmp.ps1 | — | |
MD5:— | SHA256:— | |||
| 6692 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\msi7B3D.tmp.txt | — | |
MD5:— | SHA256:— | |||
| 6692 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pss7B3E.tmp.ps1 | — | |
MD5:— | SHA256:— | |||
| 6692 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pss7C1A.tmp.ps1 | — | |
MD5:— | SHA256:— | |||
| 6360 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:61501F8C8528C4892B5F5056B2B614A3 | SHA256:70A20D3A5CC6133B32DC6E4DDF40261413CB0996CDF7051BB6348A48CCEDCB7F | |||
| 6360 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIBEB1.tmp | executable | |
MD5:07EBB743BBD7230E04C23BCBAA03FC44 | SHA256:194B29C26D925FDC1F1AA1802714118D0CA30E413C7FEA5C19A928EBA7CC43B0 | |||
| 6360 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_AC4F2376FB8C3DDE92B048621AC5B5AA | binary | |
MD5:6BFEE385E02806B7E39AD04F4796B517 | SHA256:F3E27FEDDB6A8167379310BF0B0E19DDDEF53616BA2474500EB29CF831820CE9 | |||
| 6360 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:C7187584BBCEA4F96751077447515E8B | SHA256:CC6704CC4CA24D778F91B9AD2FE903ADE51FE2AB07DBF07C3B3F8A17E9645ED6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
106
DNS requests
96
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3172 | powershell.exe | POST | 200 | 52.222.206.138:80 | http://d3cv8ymwoql87l.cloudfront.net/ | unknown | — | — | whitelisted |
4716 | powershell.exe | POST | 200 | 52.222.206.138:80 | http://d3cv8ymwoql87l.cloudfront.net/ | unknown | — | — | whitelisted |
4536 | powershell.exe | POST | 200 | 108.138.2.189:80 | http://d2vtta4ibs40qt.cloudfront.net/ | unknown | — | — | whitelisted |
4716 | powershell.exe | GET | 404 | 13.33.187.128:80 | http://sq4zqk.com/ext/fhgid?fid=39734987 | unknown | — | — | unknown |
5712 | powershell.exe | POST | 200 | 52.222.206.138:80 | http://d3cv8ymwoql87l.cloudfront.net/ | unknown | — | — | whitelisted |
4716 | powershell.exe | POST | 200 | 52.222.206.138:80 | http://d3cv8ymwoql87l.cloudfront.net/ | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6848 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6848 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6360 | msiexec.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.21.65.154:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
6848 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6848 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1512 | powershell.exe | Possibly Unwanted Program Detected | ADWARE [ANY.RUN] BBWC a browser hijacker app (PUP) |
1512 | powershell.exe | Possibly Unwanted Program Detected | ADWARE [ANY.RUN] BBWC a browser hijacker app (PUP) |
3172 | powershell.exe | Possibly Unwanted Program Detected | ADWARE [ANY.RUN] BBWC a browser hijacker app (PUP) |
2976 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2976 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2976 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2976 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2976 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2976 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2976 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |