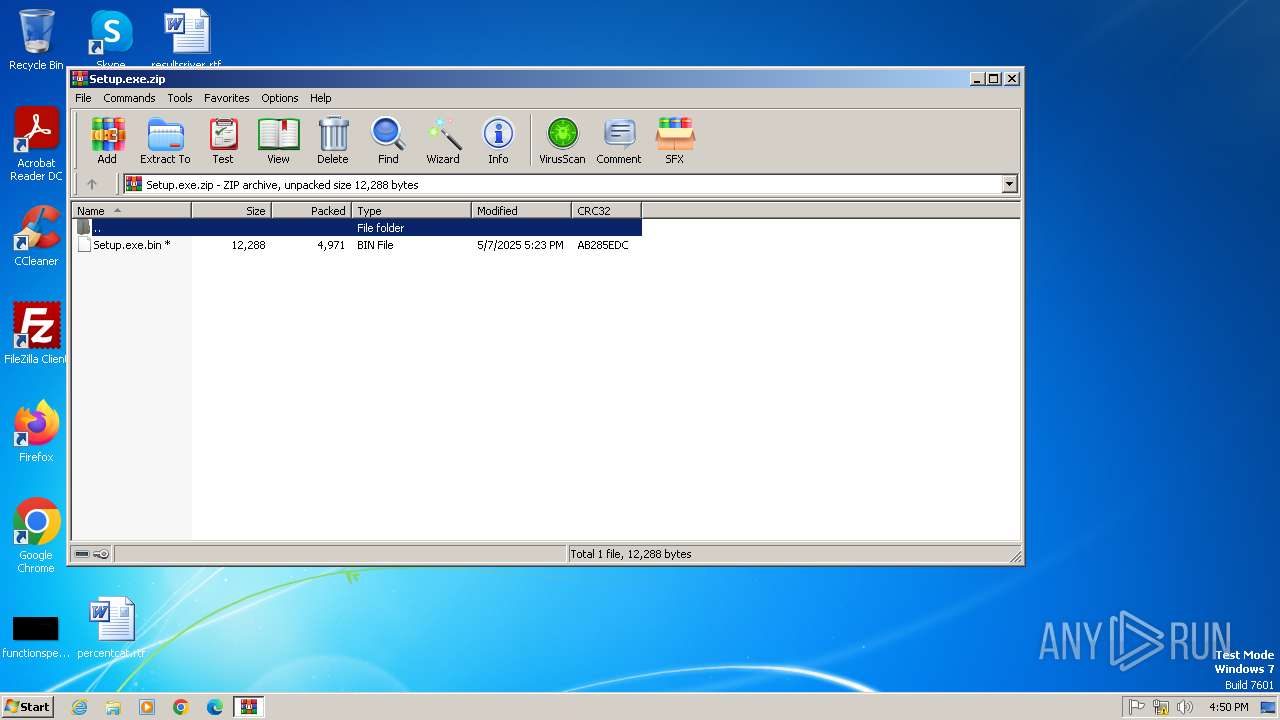
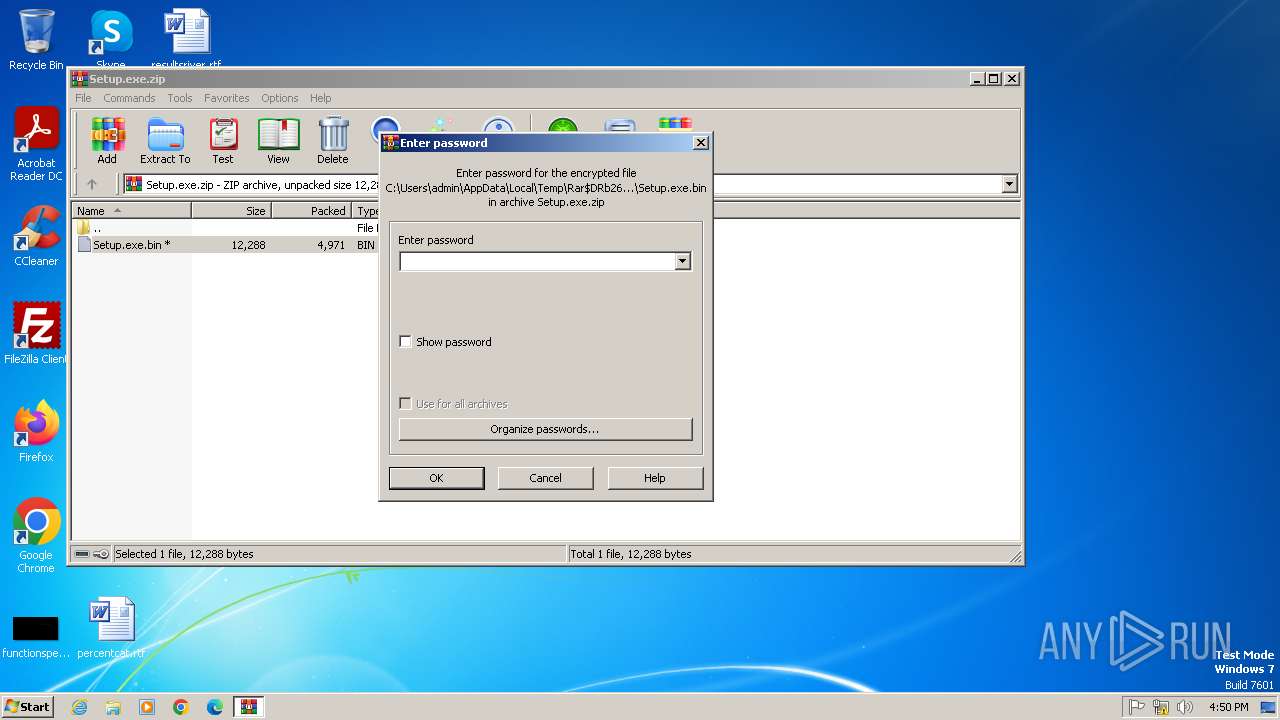
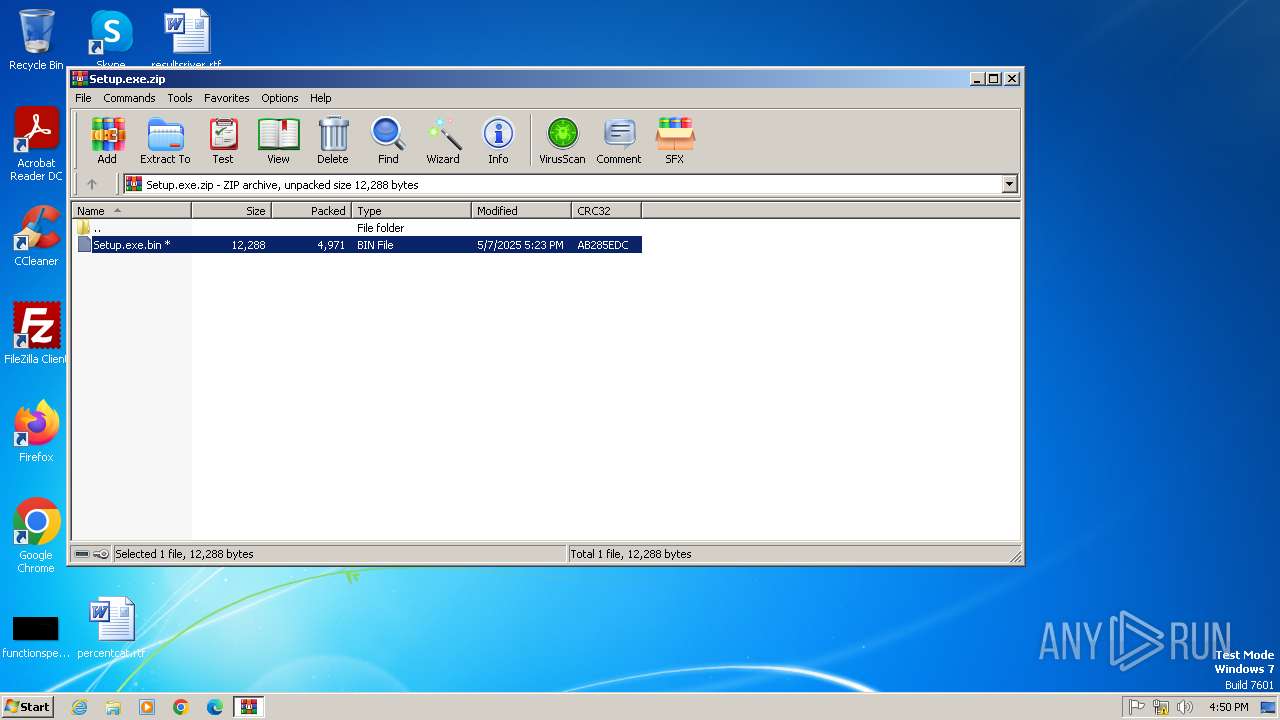
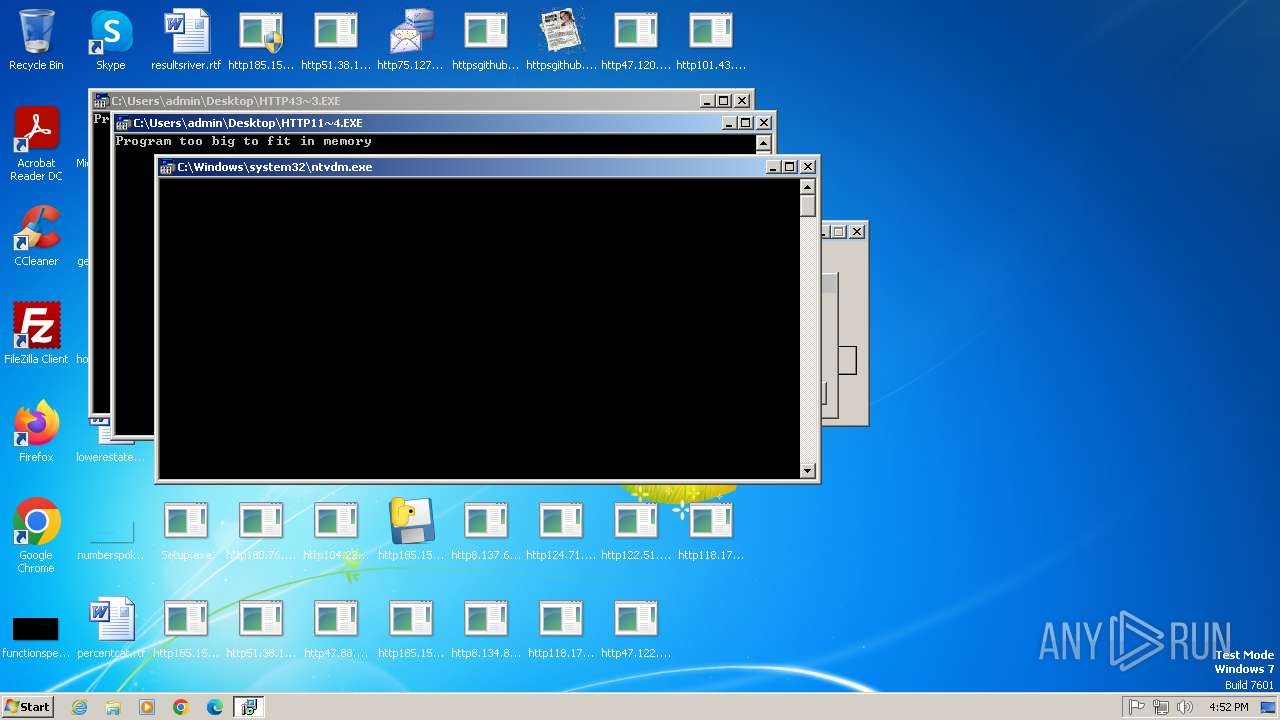
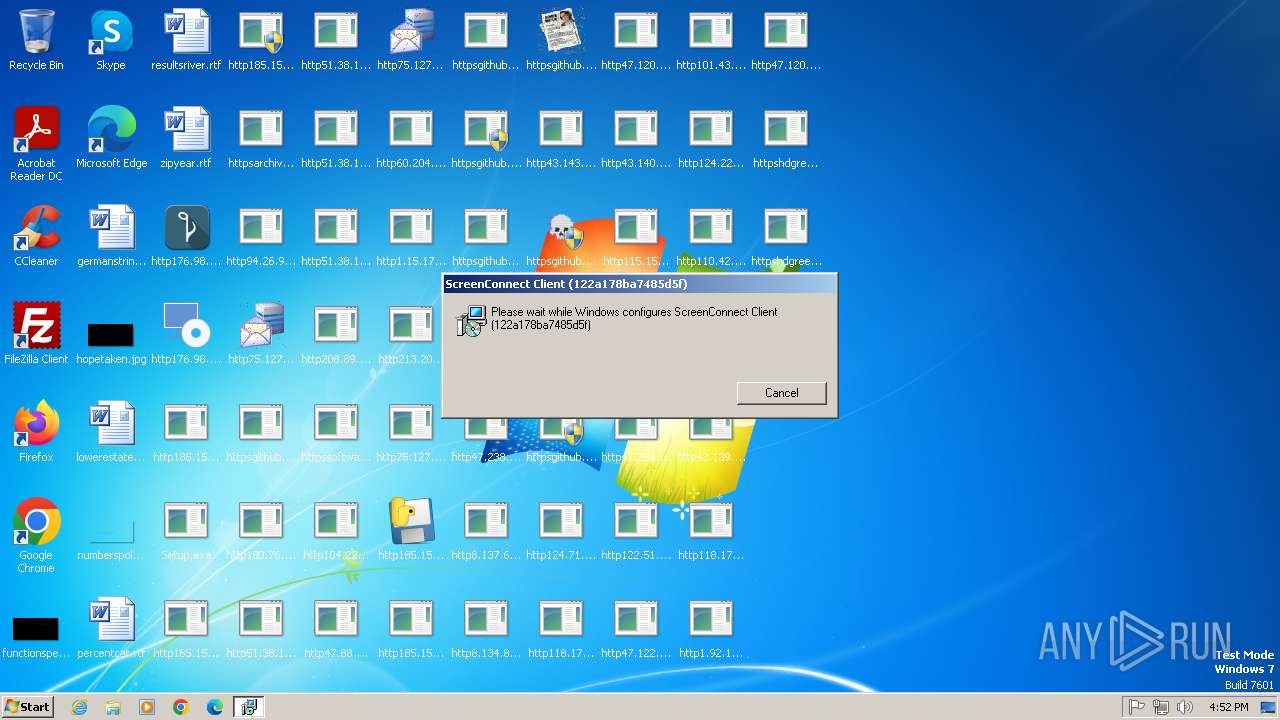
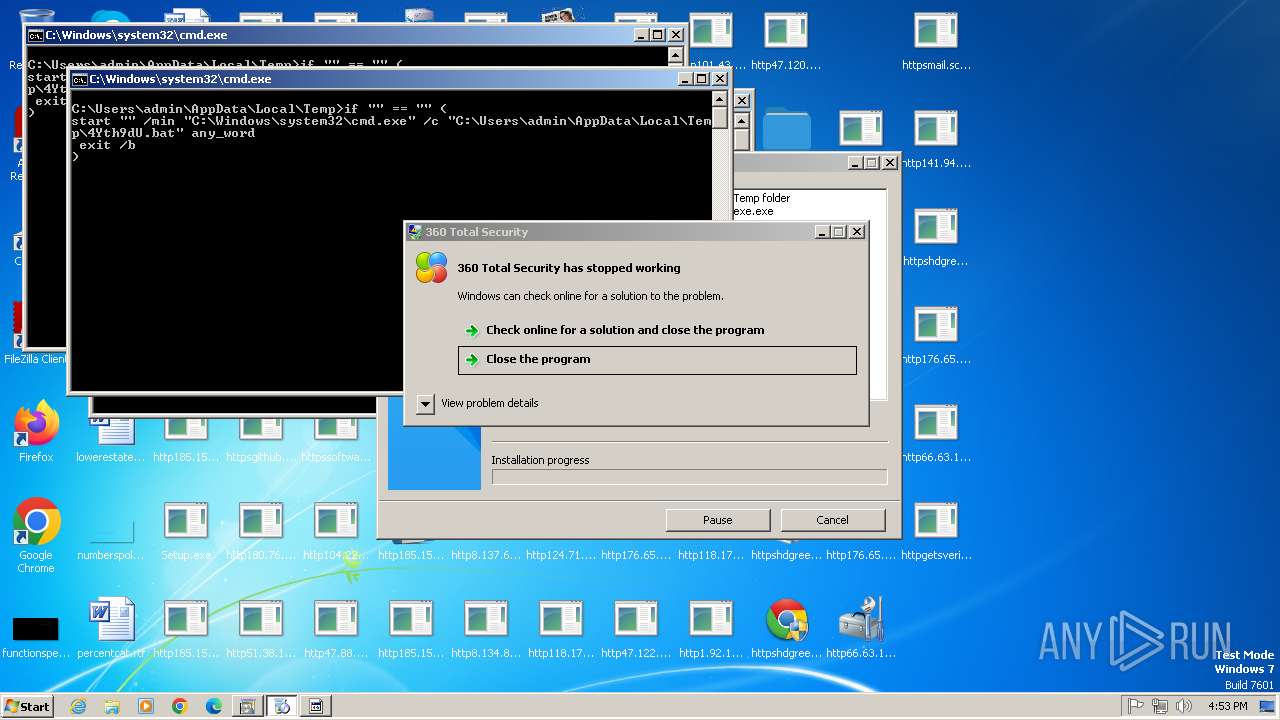
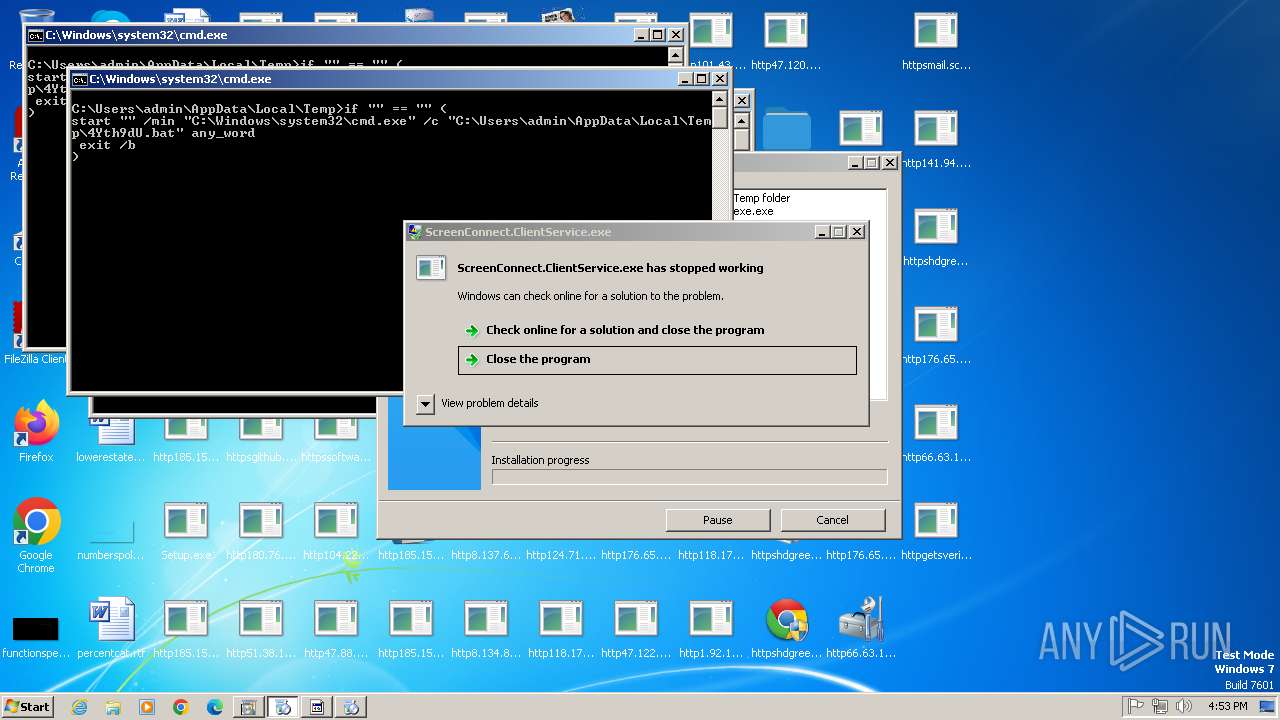
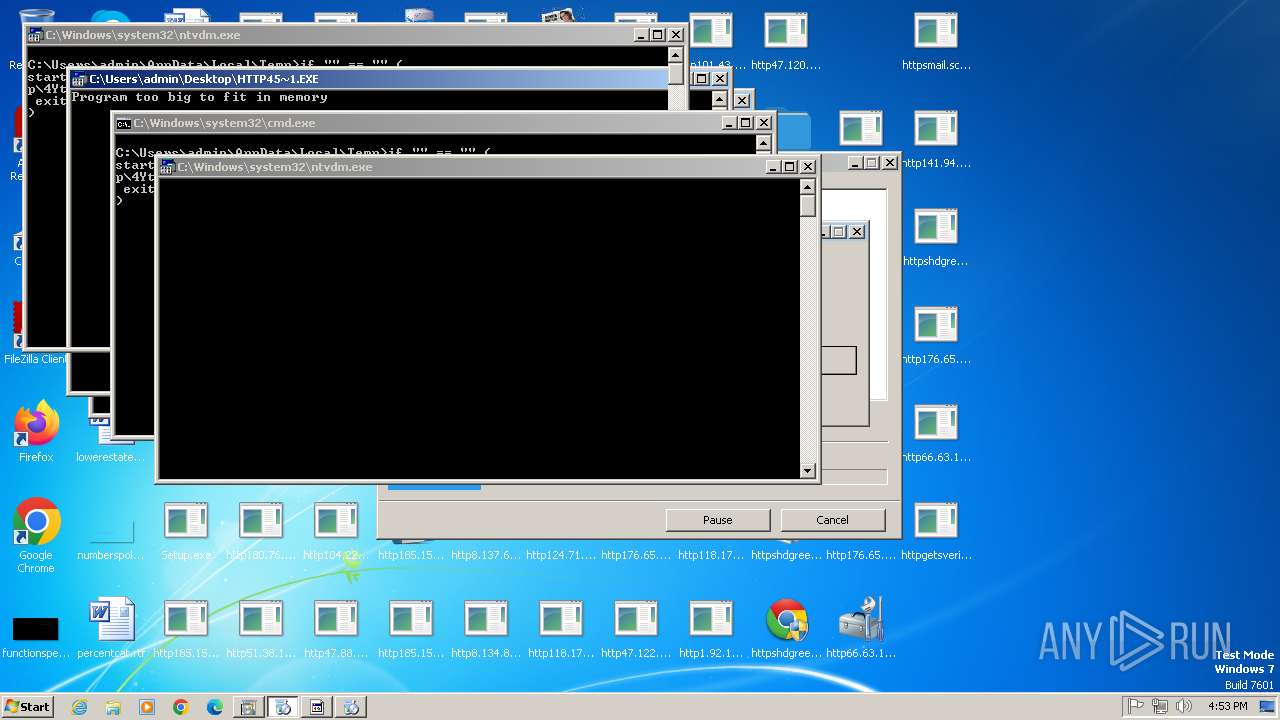
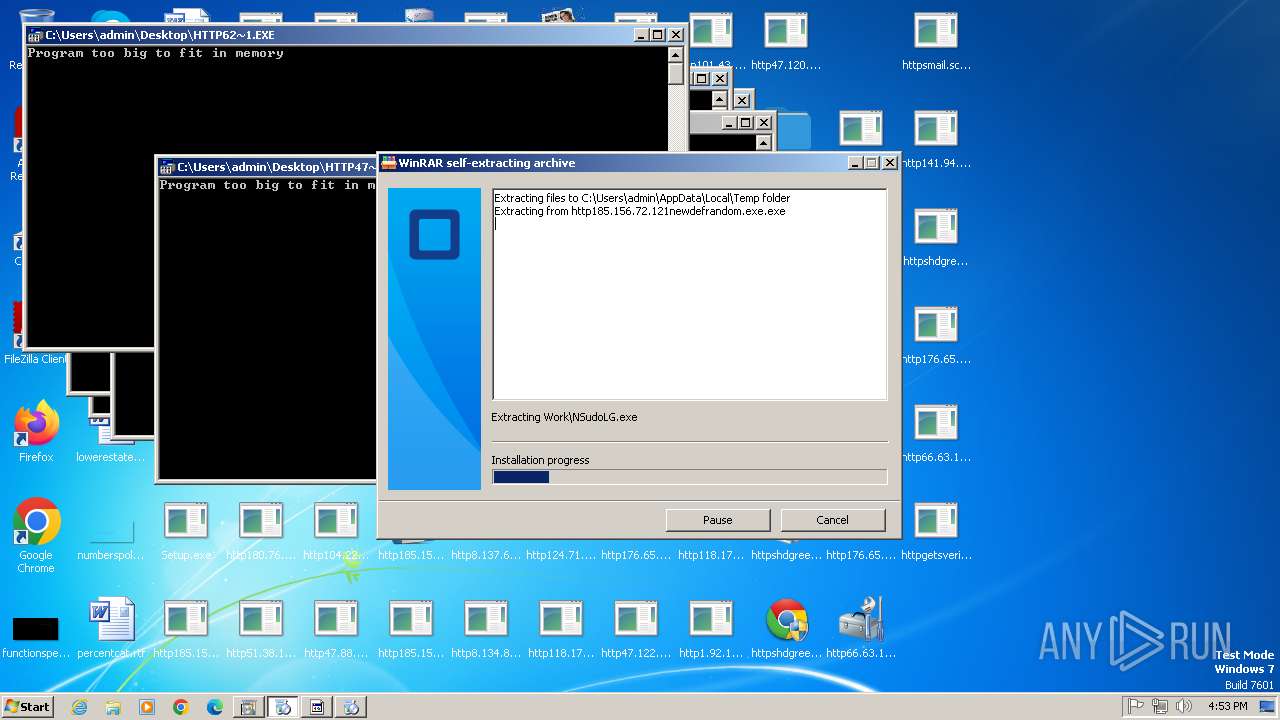
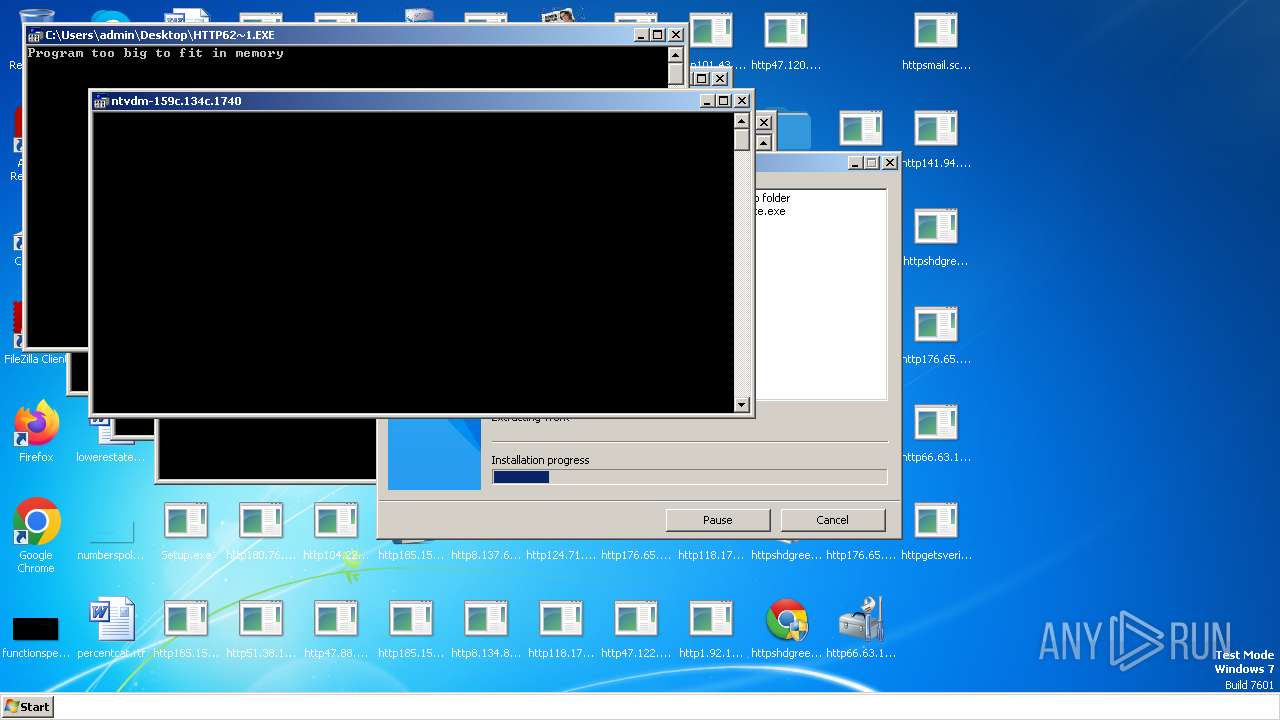
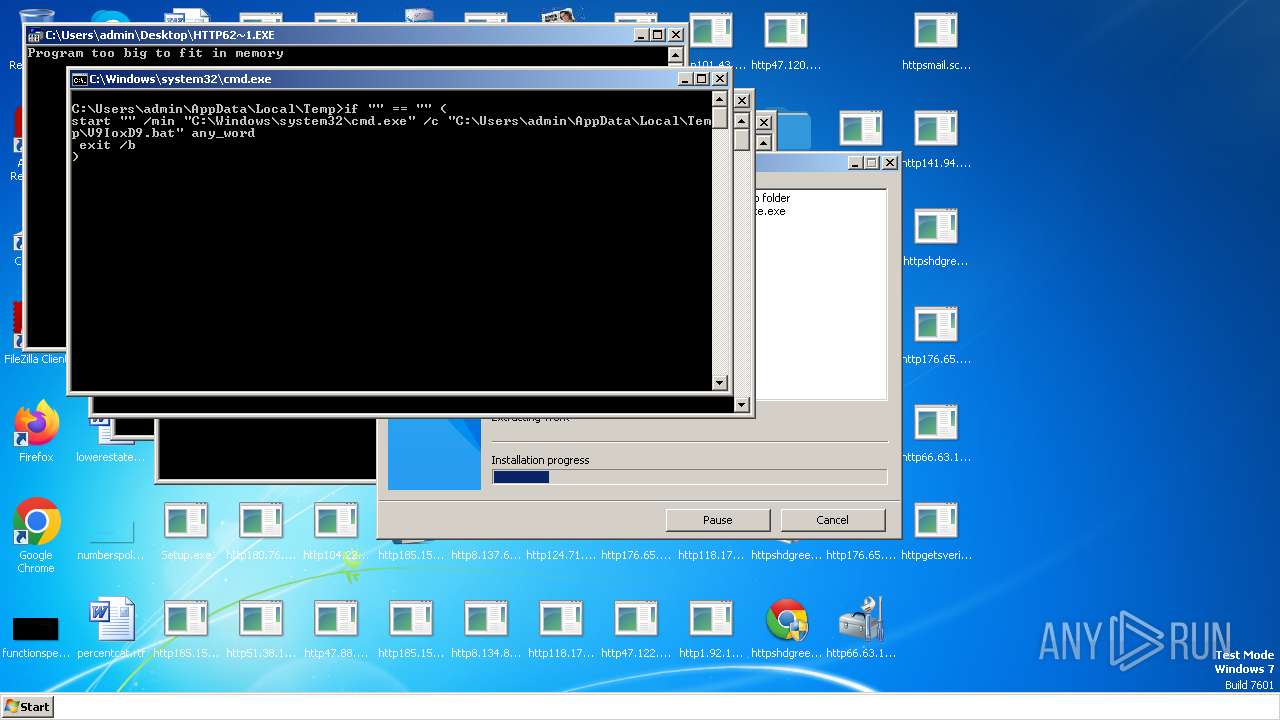
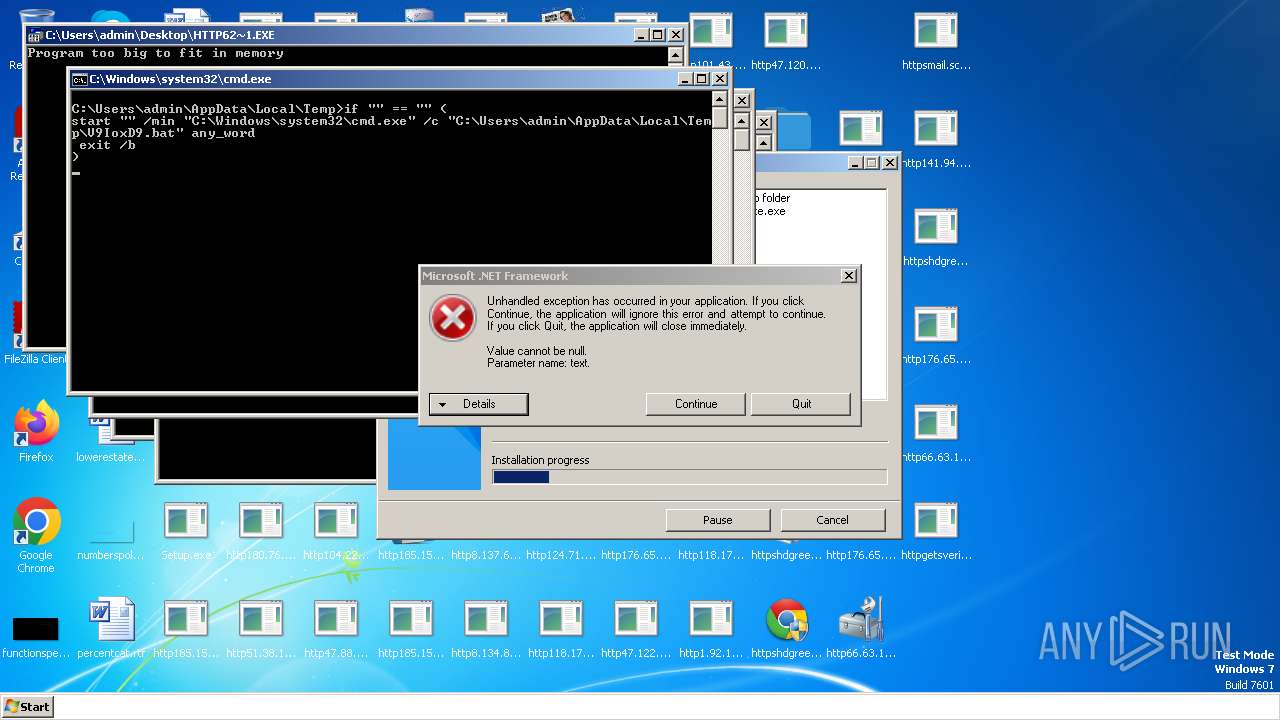
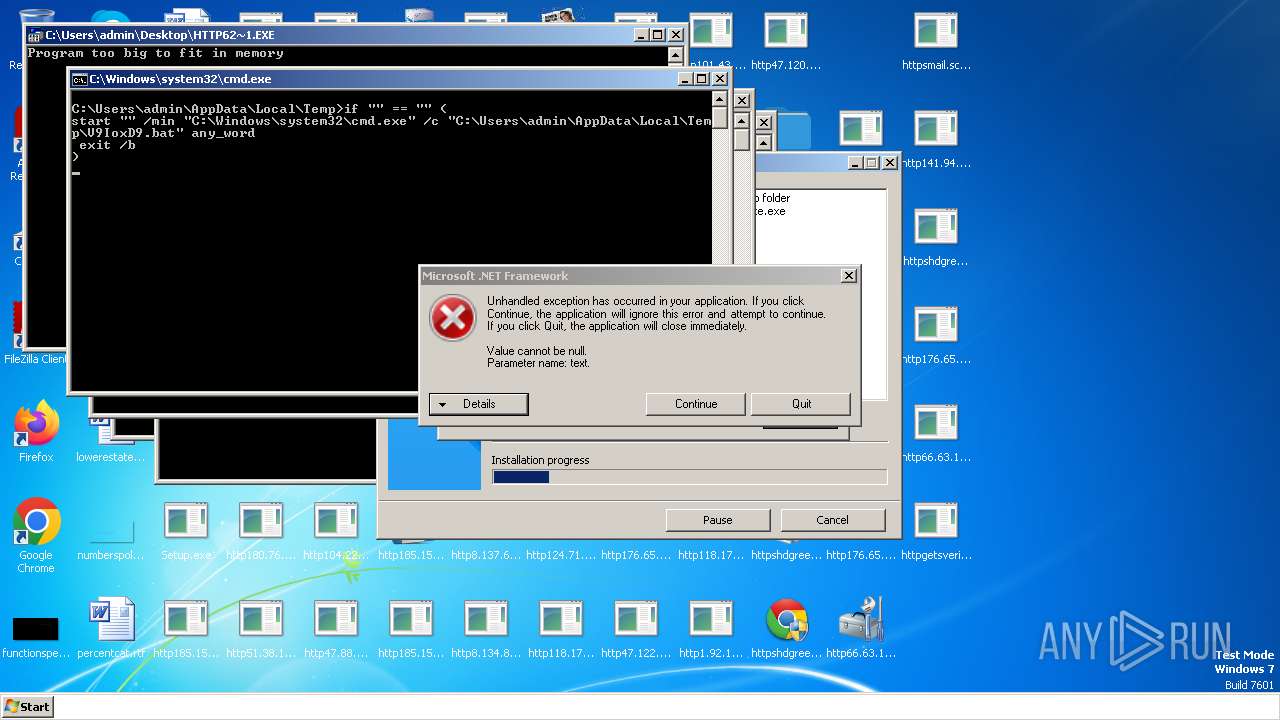
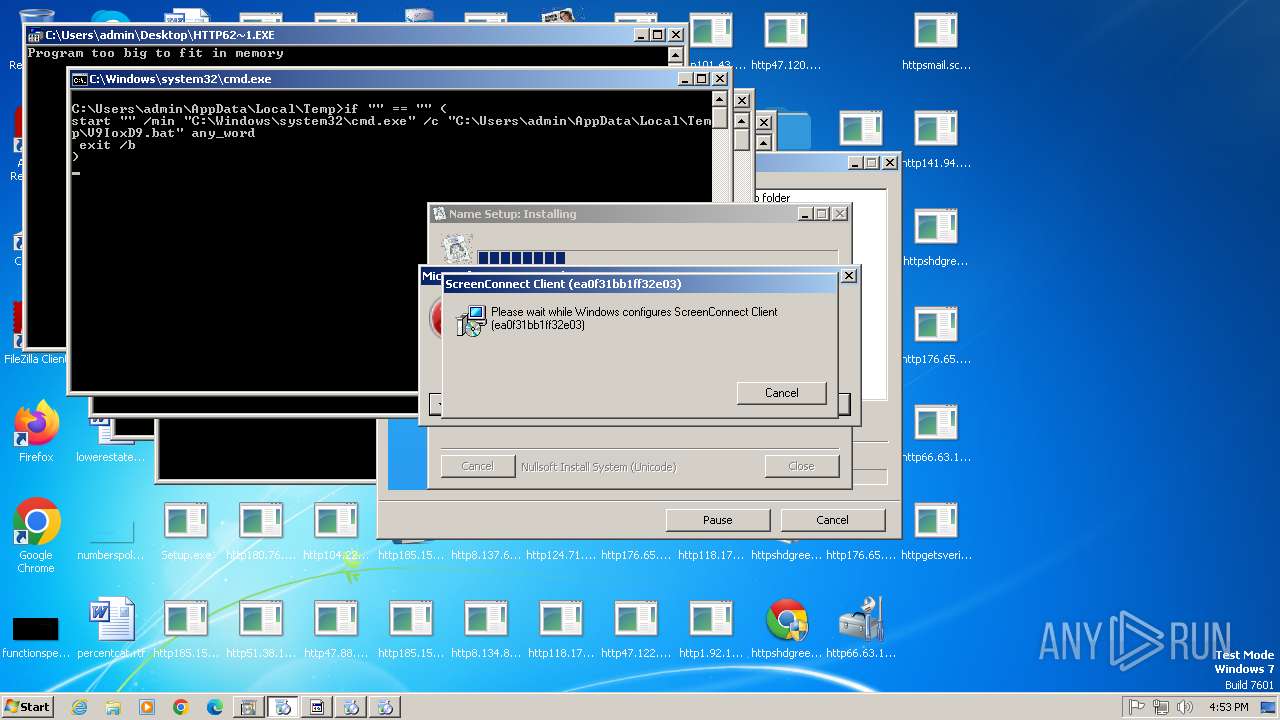
| File name: | Setup.exe.zip |
| Full analysis: | https://app.any.run/tasks/29e4b285-6a23-4b34-9666-b8631542a48d |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 16, 2025, 15:50:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 9E82E8D477C75272A0004A9E80C28243 |
| SHA1: | E30563D7FBC8CC9423596D5E8AEDF5F7FECCD630 |
| SHA256: | D99470578845274B50DB43CDF81E5271FEAD4A05ED52C26A549BF4A8F2CFE8F4 |
| SSDEEP: | 192:LhSPTnYN2wrfmBA/q+MG6Z+wbooklHRaIj2wwX7gK:LhSPTnYvmBEJMGS+IFX7T |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2624)
GHOSTSOCKS has been found (auto)
- Setup.exe (PID: 1032)
REDLINE has been detected (SURICATA)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- 3wQAlfL.exe (PID: 5960)
- 3wQAlfL.exe (PID: 4140)
Actions looks like stealing of personal data
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
REDLINE has been detected (YARA)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
Steals credentials from Web Browsers
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- svchost.exe (PID: 3352)
Changes the autorun value in the registry
- http176.98.185.87Quodlibet.exe.exe (PID: 892)
LEFTHOOK has been detected (SURICATA)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- 3wQAlfL.exe (PID: 5960)
- 3wQAlfL.exe (PID: 4140)
Stealers network behavior
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- InstallUtil.exe (PID: 3248)
- Setup.exe (PID: 1032)
METASTEALER has been detected (SURICATA)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- 3wQAlfL.exe (PID: 5960)
- 3wQAlfL.exe (PID: 4140)
Executing a file with an untrusted certificate
- http75.127.7.164Supawn.exe.exe (PID: 3284)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 2920)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 524)
- httpshdgreen.orgAlli_AI_stable_latest_release_ver_801_Setup_win.exe.exe (PID: 3472)
- httpshdgreen.orgPhilipPatrol.exe.exe (PID: 1108)
- httpshdgreen.orgGamma_app_stable_vers_107_2_setup_proVer%20(8).exe.exe (PID: 1740)
- httpshdgreen.orgAlli_Ai_app_stable_vers_107_2_setup_proVer.exe.exe (PID: 3164)
- httpshdgreen.orgSoft_Mine_app_stable_vers_113_2_setup_proVer.exe.exe (PID: 2332)
- http185.156.72.2filesmartin1random.exe.exe (PID: 3300)
- http185.156.72.2files740061926ra02W4S.exe.exe (PID: 2324)
- ra02W4S.exe (PID: 4064)
- httpsgithub.comlegendary99999dgadsgadsfgreleasesdownloaddfbvsdfbadbadbYearReload.exe.exe (PID: 1588)
- httpsgithub.comlegendary99999vdfsvgdfsavsdfvsreleasesdownloaddafbadfbwdfbaLatitudeVsnet.exe.exe (PID: 5624)
- SF32.exe (PID: 5936)
- http185.156.72.121filesunique2random.exe.exe (PID: 4248)
Connects to the CnC server
- svchost.exe (PID: 3352)
- Setup.exe (PID: 1032)
- svchost.exe (PID: 1080)
- ramez.exe (PID: 5200)
Lokibot is detected
- svchost.exe (PID: 3352)
- svchost.exe (PID: 3352)
LOKIBOT has been detected (SURICATA)
- svchost.exe (PID: 3352)
LOKIBOT has been detected (YARA)
- svchost.exe (PID: 3352)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 2092)
DCRAT mutex has been found
- bridgesurrogatefontsvc.exe (PID: 3680)
FORMBOOK has been detected (YARA)
- tzutil.exe (PID: 2904)
- wextract.exe (PID: 3288)
DCRAT has been detected (YARA)
- bridgesurrogatefontsvc.exe (PID: 3680)
AutoIt loader has been detected (YARA)
- Declaration.com (PID: 3196)
Signed with known abused certificate
- Setup.exe (PID: 1032)
FORMBOOK has been detected (SURICATA)
- Setup.exe (PID: 1032)
AGENTTESLA has been detected (YARA)
- RegAsm.exe (PID: 3236)
- aspnet_compiler.exe (PID: 2968)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 1080)
- Declaration.com (PID: 3196)
- http185.156.72.2lumarandom.exe.exe (PID: 2076)
- http185.156.72.2files6336929412Q1yLGzl.exe.exe (PID: 3088)
- b554c829b6.exe (PID: 6092)
- http185.156.72.121lumarandom.exe.exe (PID: 2112)
AGENTTESLA has been detected (SURICATA)
- InstallUtil.exe (PID: 3248)
- RegAsm.exe (PID: 1952)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2956)
- http213.209.150.210jsXClient.exe.exe (PID: 1240)
- cmd.exe (PID: 3124)
- cmd.exe (PID: 3556)
- cmd.exe (PID: 5064)
- cmd.exe (PID: 5936)
Starts CMD.EXE for self-deleting
- http66.63.187.190workaddon2.exe.exe (PID: 3040)
XWORM has been detected (SURICATA)
- http213.209.150.210jsXClient.exe.exe (PID: 1240)
Run PowerShell with an invisible window
- powershell.exe (PID: 4796)
- powershell.exe (PID: 4732)
SNAKEKEYLOGGER has been detected (SURICATA)
- RegSvcs.exe (PID: 4532)
Bypass execution policy to execute commands
- powershell.exe (PID: 5368)
Changes powershell execution policy (Bypass)
- Scvhost.exe (PID: 2684)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 5200)
Request from PowerShell that ran from MSHTA.EXE
- powershell.exe (PID: 4796)
Possible tool for stealing has been detected
- http185.156.72.2wellrandom.exe.exe (PID: 3192)
- firefox.exe (PID: 5904)
- firefox.exe (PID: 5000)
Suspicious browser debugging (Possible cookie theft)
- chrome.exe (PID: 4900)
- msedge.exe (PID: 4856)
- chrome.exe (PID: 3000)
- msedge.exe (PID: 4832)
Starts SC.EXE for service management
- cmd.exe (PID: 5724)
- cmd.exe (PID: 5856)
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.WindowsClient.exe (PID: 3356)
STEALER has been found (auto)
- Setup.exe (PID: 1032)
SUSPICIOUS
Reads the Internet Settings
- Setup.exe (PID: 1032)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- http75.127.7.164emmmmmmslay.exe.exe (PID: 2600)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 4028)
- wscript.exe (PID: 2092)
- WerFault.exe (PID: 4048)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 524)
Reads settings of System Certificates
- Setup.exe (PID: 1032)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- http75.127.7.164emmmmmmslay.exe.exe (PID: 2600)
Connects to unusual port
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- Setup.exe (PID: 1032)
- RegAsm.exe (PID: 1952)
- InstallUtil.exe (PID: 3248)
- http213.209.150.210jsXClient.exe.exe (PID: 1240)
- 3wQAlfL.exe (PID: 5960)
- 3wQAlfL.exe (PID: 4140)
- ScreenConnect.WindowsClient.exe (PID: 3356)
Contacting a server suspected of hosting an Exploit Kit
- svchost.exe (PID: 1080)
Reads security settings of Internet Explorer
- Setup.exe (PID: 1032)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 4028)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 524)
The process creates files with name similar to system file names
- Setup.exe (PID: 1032)
- http75.127.7.164Supawn.exe.exe (PID: 3284)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 2920)
Executable content was dropped or overwritten
- Setup.exe (PID: 1032)
- svchost.exe (PID: 3352)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 4028)
- http75.127.7.164Supawn.exe.exe (PID: 3284)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 2920)
- bridgesurrogatefontsvc.exe (PID: 3680)
- httpsgithub.compiunildunkos8nomrawrefsheadsmainsgsdg.exe.exe (PID: 3424)
- rundll32.exe (PID: 2476)
- wextract.exe (PID: 3288)
- httpshdgreen.orgAlli_AI_stable_latest_release_ver_801_Setup_win.exe.exe (PID: 3472)
- httpshdgreen.orgAlli_AI_stable_latest_release_ver_801_Setup_win.exe.tmp (PID: 3812)
- httpshdgreen.orgGamma_app_stable_vers_107_2_setup_proVer%20(8).exe.exe (PID: 1740)
- XBinderOutput.exe (PID: 4028)
- httpshdgreen.orgGamma_app_stable_vers_107_2_setup_proVer%20(8).exe.tmp (PID: 3144)
- dfsvc.exe (PID: 2064)
- httpshdgreen.orgSoft_Mine_app_stable_vers_113_2_setup_proVer.exe.exe (PID: 2332)
- http66.63.187.190workaddon2.exe.exe (PID: 3708)
- httpshdgreen.orgAlli_Ai_app_stable_vers_107_2_setup_proVer.exe.exe (PID: 3164)
- httpshdgreen.orgAlli_Ai_app_stable_vers_107_2_setup_proVer.exe.tmp (PID: 4040)
- httpshdgreen.orgSoft_Mine_app_stable_vers_113_2_setup_proVer.exe.tmp (PID: 3012)
- http213.209.150.210jsXClient.exe.exe (PID: 1240)
- http185.156.72.2filesunique1random.exe.exe (PID: 916)
- powershell.exe (PID: 4300)
- http185.156.72.2testminerandom.exe.exe (PID: 3392)
- powershell.exe (PID: 4796)
- http185.156.72.2offrandom.exe.exe (PID: 3700)
- ramez.exe (PID: 5200)
- httpsgithub.comlegendary99999bdfbsfdbdsbdabreleasesdownloadfabfsdbadbadb6.exe.exe (PID: 2532)
- 98a6feb6e4.exe (PID: 4344)
- Invision.com (PID: 5452)
- rundll32.exe (PID: 5416)
- http185.156.72.121filesunique1random.exe.exe (PID: 2548)
Process requests binary or script from the Internet
- Setup.exe (PID: 1032)
- http213.209.150.210jsXClient.exe.exe (PID: 1240)
- powershell.exe (PID: 4796)
- ramez.exe (PID: 5200)
Connects to the server without a host name
- Setup.exe (PID: 1032)
- svchost.exe (PID: 3352)
- http176.65.144.23brainWASXZC.exe.exe (PID: 2464)
- http176.65.144.23brainke.exe.exe (PID: 2860)
- http176.65.144.23brainZZXSWRGGSD.exe.exe (PID: 3212)
- http176.65.144.23marVZXYFASD.exe.exe (PID: 3744)
- http213.209.150.210jsXClient.exe.exe (PID: 1240)
- powershell.exe (PID: 4796)
- ramez.exe (PID: 5200)
- Alcrmv.exe (PID: 872)
Potential Corporate Privacy Violation
- Setup.exe (PID: 1032)
- http213.209.150.210jsXClient.exe.exe (PID: 1240)
- powershell.exe (PID: 4796)
- ramez.exe (PID: 5200)
- ScreenConnect.WindowsClient.exe (PID: 3356)
Contacting a server suspected of hosting an CnC
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- svchost.exe (PID: 3352)
- Setup.exe (PID: 1032)
- svchost.exe (PID: 1080)
- Declaration.com (PID: 3196)
- http185.156.72.2lumarandom.exe.exe (PID: 2076)
- http213.209.150.210jsXClient.exe.exe (PID: 1240)
- http185.156.72.2files6336929412Q1yLGzl.exe.exe (PID: 3088)
- ramez.exe (PID: 5200)
- 3wQAlfL.exe (PID: 5960)
- 3wQAlfL.exe (PID: 4140)
- b554c829b6.exe (PID: 6092)
- http185.156.72.121lumarandom.exe.exe (PID: 2112)
Adds/modifies Windows certificates
- Setup.exe (PID: 1032)
Reads browser cookies
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
Multiple wallet extension IDs have been found
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- bridgesurrogatefontsvc.exe (PID: 3680)
Creates file in the systems drive root
- ntvdm.exe (PID: 704)
Process drops legitimate windows executable
- Setup.exe (PID: 1032)
- httpshdgreen.orgGamma_app_stable_vers_107_2_setup_proVer%20(8).exe.tmp (PID: 3144)
- http66.63.187.190workaddon2.exe.exe (PID: 3708)
- httpshdgreen.orgSoft_Mine_app_stable_vers_113_2_setup_proVer.exe.tmp (PID: 3012)
- httpshdgreen.orgAlli_Ai_app_stable_vers_107_2_setup_proVer.exe.tmp (PID: 4040)
- http213.209.150.210jsXClient.exe.exe (PID: 1240)
- ramez.exe (PID: 5200)
There is functionality for communication over UDP network (YARA)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 3140)
Searches for installed software
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
Loads DLL from Mozilla Firefox
- svchost.exe (PID: 3352)
The process connected to a server suspected of theft
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- 3wQAlfL.exe (PID: 5960)
Possible Social Engineering Attempted
- svchost.exe (PID: 1080)
Accesses Microsoft Outlook profiles
- svchost.exe (PID: 3352)
There is functionality for taking screenshot (YARA)
- http75.127.7.164Supawn.exe.exe (PID: 3284)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 2920)
- bridgesurrogatefontsvc.exe (PID: 3680)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 524)
- Declaration.com (PID: 3196)
- httpshdgreen.orgayin.v0.1.0.exe.exe (PID: 2396)
- httpshdgreen.orgPhilipPatrol.exe.exe (PID: 1108)
- httpshdgreen.orgAlli_AI_stable_latest_release_ver_801_Setup_win.exe.tmp (PID: 3812)
Malware-specific behavior (creating "System.dll" in Temp)
- http75.127.7.164Supawn.exe.exe (PID: 3284)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 2920)
Executing commands from a ".bat" file
- wscript.exe (PID: 2092)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 524)
- http185.156.72.2filesmartin1random.exe.exe (PID: 3300)
- http185.156.72.2newdefrandom.exe.exe (PID: 2780)
- cmd.exe (PID: 5588)
- cmd.exe (PID: 5732)
- http185.156.72.2offrandom.exe.exe (PID: 3700)
- bb2b6c6edb.exe (PID: 2808)
- cmd.exe (PID: 4328)
- http185.156.72.121newdefrandom.exe.exe (PID: 4604)
- cmd.exe (PID: 2324)
- httpsgithub.comlegendary99999vdfsvgdfsavsdfvsreleasesdownloaddafbadfbwdfbaLatitudeVsnet.exe.exe (PID: 5624)
- httpsgithub.comlegendary99999dgadsgadsfgreleasesdownloaddfbvsdfbadbadbYearReload.exe.exe (PID: 1588)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 2092)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 524)
- cmd.exe (PID: 2692)
- httpshdgreen.orgPhilipPatrol.exe.exe (PID: 1108)
- http66.63.187.190workaddon2.exe.exe (PID: 3040)
- cmd.exe (PID: 2876)
- http185.156.72.2testexerandom.exe.exe (PID: 1224)
- http185.156.72.2filesmartin1random.exe.exe (PID: 3300)
- http185.156.72.2offrandom.exe.exe (PID: 3700)
- cmd.exe (PID: 5588)
- http185.156.72.2newdefrandom.exe.exe (PID: 2780)
- cmd.exe (PID: 5732)
- cmd.exe (PID: 5724)
- cmd.exe (PID: 5856)
- UserOOBEBroker.exe (PID: 4420)
- bb2b6c6edb.exe (PID: 2808)
- cmd.exe (PID: 5112)
- cmd.exe (PID: 4328)
- http185.156.72.121newdefrandom.exe.exe (PID: 4604)
- cmd.exe (PID: 3524)
- cmd.exe (PID: 2324)
- cmd.exe (PID: 2760)
- httpsgithub.comlegendary99999vdfsvgdfsavsdfvsreleasesdownloaddafbadfbwdfbaLatitudeVsnet.exe.exe (PID: 5624)
- http185.156.72.121testexerandom.exe.exe (PID: 3620)
- 09241e7fb8.exe (PID: 5612)
- httpsgithub.comlegendary99999dgadsgadsfgreleasesdownloaddfbvsdfbadbadbYearReload.exe.exe (PID: 1588)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2092)
Executes application which crashes
- svchost.exe (PID: 1196)
Get information on the list of running processes
- cmd.exe (PID: 2692)
- cmd.exe (PID: 2876)
- cmd.exe (PID: 5724)
- cmd.exe (PID: 6012)
- cmd.exe (PID: 3728)
- cmd.exe (PID: 5856)
- cmd.exe (PID: 5112)
- cmd.exe (PID: 2760)
- cmd.exe (PID: 4280)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2692)
- cmd.exe (PID: 2876)
- cmd.exe (PID: 5112)
- cmd.exe (PID: 5724)
- cmd.exe (PID: 5856)
Starts the AutoIt3 executable file
- cmd.exe (PID: 2692)
- cmd.exe (PID: 2876)
- cmd.exe (PID: 5112)
The executable file from the user directory is run by the CMD process
- Declaration.com (PID: 3196)
- Beverly.com (PID: 5296)
- Invision.com (PID: 5452)
Starts application with an unusual extension
- cmd.exe (PID: 2692)
- cmd.exe (PID: 2876)
- cmd.exe (PID: 5724)
- cmd.exe (PID: 5856)
- cmd.exe (PID: 3524)
- cmd.exe (PID: 2760)
- cmd.exe (PID: 5112)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 320)
- msiexec.exe (PID: 2364)
Application launched itself
- msiexec.exe (PID: 2712)
- cmd.exe (PID: 2692)
- Scvhost.exe (PID: 3136)
- http66.63.187.190workaddon2.exe.exe (PID: 3708)
- cmd.exe (PID: 2876)
- cmd.exe (PID: 5588)
- cmd.exe (PID: 5732)
- cmd.exe (PID: 5724)
- cmd.exe (PID: 5856)
- AddInProcess32.exe (PID: 1076)
- cmd.exe (PID: 4328)
- cmd.exe (PID: 5112)
- cmd.exe (PID: 3524)
- cmd.exe (PID: 2324)
- cmd.exe (PID: 2760)
Executes as Windows Service
- VSSVC.exe (PID: 3756)
Executing commands from ".cmd" file
- httpshdgreen.orgPhilipPatrol.exe.exe (PID: 1108)
Process drops SQLite DLL files
- wextract.exe (PID: 3288)
Checks for external IP
- svchost.exe (PID: 1080)
- aspnet_compiler.exe (PID: 2968)
- RegAsm.exe (PID: 3236)
- RegAsm.exe (PID: 1952)
- InstallUtil.exe (PID: 3248)
- RegSvcs.exe (PID: 4532)
Connects to SMTP port
- aspnet_compiler.exe (PID: 2968)
- RegSvcs.exe (PID: 4532)
Starts a Microsoft application from unusual location
- http66.63.187.190workaddon2.exe.exe (PID: 3040)
- http66.63.187.190workaddon2.exe.exe (PID: 3708)
- http213.209.150.210jsXClient.exe.exe (PID: 1240)
Connects to FTP
- RegAsm.exe (PID: 1952)
- InstallUtil.exe (PID: 3248)
Lists all scheduled tasks
- schtasks.exe (PID: 1928)
- schtasks.exe (PID: 5136)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3220)
Uses TASKKILL.EXE to kill Browsers
- http185.156.72.2wellrandom.exe.exe (PID: 3192)
- 44f50b133a.exe (PID: 5660)
- http185.156.72.121wellrandom.exe.exe (PID: 2088)
Hides command output
- cmd.exe (PID: 3220)
Starts POWERSHELL.EXE for commands execution
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 2776)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 872)
- mshta.exe (PID: 3072)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 848)
- Scvhost.exe (PID: 2684)
- mshta.exe (PID: 4232)
BASE64 encoded PowerShell command has been detected
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 2776)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 848)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 872)
Base64-obfuscated command line is found
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 2776)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 872)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 848)
Starts process via Powershell
- powershell.exe (PID: 4796)
- powershell.exe (PID: 4732)
Manipulates environment variables
- powershell.exe (PID: 4796)
- powershell.exe (PID: 4732)
Probably download files using WebClient
- mshta.exe (PID: 3072)
- mshta.exe (PID: 4232)
Found IP address in command line
- powershell.exe (PID: 4796)
- powershell.exe (PID: 4732)
Starts itself from another location
- http185.156.72.2testminerandom.exe.exe (PID: 3392)
The process executes Powershell scripts
- Scvhost.exe (PID: 2684)
Drops 7-zip archiver for unpacking
- http185.156.72.2offrandom.exe.exe (PID: 3700)
Uses TASKKILL.EXE to kill process
- http185.156.72.2wellrandom.exe.exe (PID: 3192)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5724)
- cmd.exe (PID: 5856)
- cmd.exe (PID: 3524)
- cmd.exe (PID: 2760)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- RegSvcs.exe (PID: 4532)
- Scvhost.exe (PID: 2684)
The process executes via Task Scheduler
- UserOOBEBroker.exe (PID: 4420)
MS Edge headless start
- msedge.exe (PID: 4856)
- msedge.exe (PID: 5508)
- msedge.exe (PID: 4832)
Stops a currently running service
- sc.exe (PID: 5752)
- sc.exe (PID: 6028)
- sc.exe (PID: 4196)
- sc.exe (PID: 2444)
- sc.exe (PID: 848)
- sc.exe (PID: 2088)
- sc.exe (PID: 3084)
- sc.exe (PID: 1020)
- sc.exe (PID: 4024)
- sc.exe (PID: 4984)
- sc.exe (PID: 5072)
- sc.exe (PID: 5276)
- sc.exe (PID: 1928)
- sc.exe (PID: 5356)
- sc.exe (PID: 3328)
- sc.exe (PID: 5736)
- sc.exe (PID: 920)
- sc.exe (PID: 284)
- sc.exe (PID: 3036)
- sc.exe (PID: 1768)
- sc.exe (PID: 5812)
- sc.exe (PID: 4464)
- sc.exe (PID: 4512)
- sc.exe (PID: 5424)
- sc.exe (PID: 5416)
- sc.exe (PID: 2868)
- sc.exe (PID: 4196)
- sc.exe (PID: 5360)
- sc.exe (PID: 6132)
- sc.exe (PID: 4444)
- sc.exe (PID: 5444)
- sc.exe (PID: 3312)
Windows service management via SC.EXE
- sc.exe (PID: 5840)
- sc.exe (PID: 2220)
- sc.exe (PID: 6120)
- sc.exe (PID: 3660)
- sc.exe (PID: 2564)
- sc.exe (PID: 5592)
- sc.exe (PID: 2408)
- sc.exe (PID: 3820)
- sc.exe (PID: 3744)
- sc.exe (PID: 1564)
- sc.exe (PID: 4936)
- sc.exe (PID: 3884)
- sc.exe (PID: 1664)
- sc.exe (PID: 5124)
- sc.exe (PID: 5040)
- sc.exe (PID: 4168)
- sc.exe (PID: 4736)
- sc.exe (PID: 3312)
- sc.exe (PID: 4732)
- sc.exe (PID: 812)
- sc.exe (PID: 5076)
- sc.exe (PID: 5268)
- sc.exe (PID: 5624)
- sc.exe (PID: 2196)
- sc.exe (PID: 5484)
- sc.exe (PID: 5060)
- sc.exe (PID: 5984)
- sc.exe (PID: 5820)
- sc.exe (PID: 2604)
- sc.exe (PID: 924)
- sc.exe (PID: 5852)
- sc.exe (PID: 5824)
- sc.exe (PID: 1564)
- sc.exe (PID: 3136)
- sc.exe (PID: 5536)
- sc.exe (PID: 848)
- sc.exe (PID: 3064)
- sc.exe (PID: 4856)
- sc.exe (PID: 812)
- sc.exe (PID: 5500)
- sc.exe (PID: 3948)
- sc.exe (PID: 3576)
- sc.exe (PID: 4260)
- sc.exe (PID: 3420)
- sc.exe (PID: 5072)
- sc.exe (PID: 5156)
- sc.exe (PID: 4144)
- sc.exe (PID: 5588)
- sc.exe (PID: 4168)
- sc.exe (PID: 5972)
- sc.exe (PID: 3304)
- sc.exe (PID: 4272)
- sc.exe (PID: 3428)
- sc.exe (PID: 2916)
- sc.exe (PID: 4332)
- sc.exe (PID: 3324)
- sc.exe (PID: 5676)
- sc.exe (PID: 5712)
- sc.exe (PID: 6128)
- sc.exe (PID: 3040)
- sc.exe (PID: 3100)
- sc.exe (PID: 5752)
- sc.exe (PID: 5812)
- sc.exe (PID: 4612)
- sc.exe (PID: 4688)
- sc.exe (PID: 5080)
Starts SC.EXE for service management
- cmd.exe (PID: 5724)
- cmd.exe (PID: 5856)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 2816)
- schtasks.exe (PID: 4116)
- schtasks.exe (PID: 5684)
- schtasks.exe (PID: 4580)
- schtasks.exe (PID: 2688)
- schtasks.exe (PID: 3220)
- schtasks.exe (PID: 3160)
- schtasks.exe (PID: 492)
- schtasks.exe (PID: 4732)
- schtasks.exe (PID: 6132)
INFO
Disables trace logs
- Setup.exe (PID: 1032)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- http75.127.7.164emmmmmmslay.exe.exe (PID: 2600)
Reads Environment values
- Setup.exe (PID: 1032)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- http75.127.7.164emmmmmmslay.exe.exe (PID: 2600)
- bridgesurrogatefontsvc.exe (PID: 3680)
Reads the software policy settings
- Setup.exe (PID: 1032)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- http75.127.7.164emmmmmmslay.exe.exe (PID: 2600)
- WerFault.exe (PID: 4048)
Reads the computer name
- Setup.exe (PID: 1032)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- http75.127.7.164Supawn.exe.exe (PID: 3284)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 2920)
- http75.127.7.164emmmmmmslay.exe.exe (PID: 2600)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 4028)
- httpsgithub.compiunildunkos8nomrawrefsheadsmainsgsdg.exe.exe (PID: 3424)
- bridgesurrogatefontsvc.exe (PID: 3680)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 524)
Reads the machine GUID from the registry
- Setup.exe (PID: 1032)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- http75.127.7.164emmmmmmslay.exe.exe (PID: 2600)
- bridgesurrogatefontsvc.exe (PID: 3680)
Checks supported languages
- Setup.exe (PID: 1032)
- http176.98.185.87Quodlibet.exe.exe (PID: 892)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 3140)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- http208.89.61.141560TiWorker.exe.exe (PID: 3004)
- http213.209.150.18alphamm.exe.exe (PID: 3236)
- http75.127.7.164Supawn.exe.exe (PID: 3284)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 2920)
- http94.26.90.204kjoxca.exe.exe (PID: 3100)
- http75.127.7.164emmmmmmslay.exe.exe (PID: 2600)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 4028)
- httpsgithub.compiunildunkos8nomrawrefsheadsmainsgsdg.exe.exe (PID: 3424)
- bridgesurrogatefontsvc.exe (PID: 3680)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 524)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2624)
- msiexec.exe (PID: 3628)
- msiexec.exe (PID: 2712)
- msiexec.exe (PID: 2244)
Manual execution by a user
- Setup.exe (PID: 1032)
- nslookup.exe (PID: 5716)
- cmd.exe (PID: 3556)
- cmd.exe (PID: 4596)
The sample compiled with english language support
- Setup.exe (PID: 1032)
- svchost.exe (PID: 3352)
- httpshdgreen.orgAlli_AI_stable_latest_release_ver_801_Setup_win.exe.tmp (PID: 3812)
- wextract.exe (PID: 3288)
- httpshdgreen.orgGamma_app_stable_vers_107_2_setup_proVer%20(8).exe.tmp (PID: 3144)
- http66.63.187.190workaddon2.exe.exe (PID: 3708)
- httpshdgreen.orgSoft_Mine_app_stable_vers_113_2_setup_proVer.exe.tmp (PID: 3012)
- httpshdgreen.orgAlli_Ai_app_stable_vers_107_2_setup_proVer.exe.tmp (PID: 4040)
- http185.156.72.2offrandom.exe.exe (PID: 3700)
- ramez.exe (PID: 5200)
- msiexec.exe (PID: 2712)
- Invision.com (PID: 5452)
Create files in a temporary directory
- http208.89.61.141560TiWorker.exe.exe (PID: 3004)
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- http213.209.150.18alphamm.exe.exe (PID: 3236)
- http94.26.90.204kjoxca.exe.exe (PID: 3100)
- http75.127.7.164Supawn.exe.exe (PID: 3284)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 2920)
- WerFault.exe (PID: 4048)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 524)
Creates files or folders in the user directory
- Setup.exe (PID: 1032)
- WerFault.exe (PID: 4048)
Reads product name
- http185.156.72.2files57658287103wQAlfL.exe.exe (PID: 3108)
- bridgesurrogatefontsvc.exe (PID: 3680)
Reads mouse settings
- http208.89.61.141560TiWorker.exe.exe (PID: 3004)
- http213.209.150.18alphamm.exe.exe (PID: 3236)
- http94.26.90.204kjoxca.exe.exe (PID: 3100)
Detects GO elliptic curve encryption (YARA)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 3140)
Application based on Golang
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 3140)
Drops encrypted VBS script (Microsoft Script Encoder)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 4028)
HTTPDEBUGGER has been detected
- http75.127.7.164emmmmmmslay.exe.exe (PID: 2600)
.NET Reactor protector has been detected
- bridgesurrogatefontsvc.exe (PID: 3680)
Creates a new folder
- cmd.exe (PID: 3816)
- cmd.exe (PID: 2600)
- cmd.exe (PID: 4616)
Detects InnoSetup installer (YARA)
- httpshdgreen.orgAlli_AI_stable_latest_release_ver_801_Setup_win.exe.exe (PID: 3472)
- httpshdgreen.orgAlli_AI_stable_latest_release_ver_801_Setup_win.exe.tmp (PID: 3812)
Compiled with Borland Delphi (YARA)
- httpshdgreen.orgAlli_AI_stable_latest_release_ver_801_Setup_win.exe.exe (PID: 3472)
- httpshdgreen.orgAlli_AI_stable_latest_release_ver_801_Setup_win.exe.tmp (PID: 3812)
The executable file from the user directory is run by the Powershell process
- TempSOSAORLUCPWU0ATVJA5IEWIEHDS703ZL.EXE (PID: 5276)
Changes the display of characters in the console
- cmd.exe (PID: 5724)
- cmd.exe (PID: 5856)
- cmd.exe (PID: 3524)
- cmd.exe (PID: 2760)
Application launched itself
- firefox.exe (PID: 5904)
- chrome.exe (PID: 3000)
- chrome.exe (PID: 4900)
- msedge.exe (PID: 4856)
- msedge.exe (PID: 4832)
- firefox.exe (PID: 5000)
- firefox.exe (PID: 3264)
Starts MODE.COM to configure console settings
- mode.com (PID: 5932)
- mode.com (PID: 4220)
- mode.com (PID: 5740)
- mode.com (PID: 5944)
Checks operating system version
- cmd.exe (PID: 5724)
- cmd.exe (PID: 5856)
- cmd.exe (PID: 3524)
- cmd.exe (PID: 2760)
Attempting to use instant messaging service
- Scvhost.exe (PID: 2684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(3108) http185.156.72.2files57658287103wQAlfL.exe.exe
C2 (1)154.91.34.165:64951
Botnetcheat
Keys
Xor
Options
ErrorMessage
LokiBot
(PID) Process(3352) svchost.exe
C294.156.177.41/alpha/five/fre.php
Decoys (4)kbfvzoboss.bid/alien/fre.php
alphastand.trade/alien/fre.php
alphastand.win/alien/fre.php
alphastand.top/alien/fre.php
AgentTesla
(PID) Process(2968) aspnet_compiler.exe
Protocolsmtp
Hostmail.phillipstradingcorpusa.com
Port587
Usernamemarcus@phillipstradingcorpusa.com
PasswordQg*r$Qz=oNd2
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:07 17:23:18 |
| ZipCRC: | 0xab285edc |
| ZipCompressedSize: | 4971 |
| ZipUncompressedSize: | 12288 |
| ZipFileName: | Setup.exe.bin |
Total processes
698
Monitored processes
559
Malicious processes
62
Suspicious processes
18
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | find /i "0x0" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 284 | sc stop "WdBoot" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 320 | C:\Windows\system32\MsiExec.exe -Embedding A76EB215BB03BADF76534D43F50E52FC C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 492 | schtasks /Delete /TN "Microsoft\Windows\Windows Defender\Windows Defender Verification" /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 524 | "C:\Users\admin\Desktop\httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe" | C:\Users\admin\Desktop\httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe | — | Setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 548 | "C:\Windows\SysWOW64\grpconv.exe" /shtml "C:\Users\admin\AppData\Roaming\watch-output_20250516165306.html" | C:\Windows\System32\grpconv.exe | — | Scvhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 604 | reg add "HKU\S-1-5-18\Software\Microsoft\Windows\CurrentVersion\Themes\Personalize" /v "AppsUseLightTheme" /t reg_dword /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 692 | reg delete "HKCR\Drive\shellex\ContextMenuHandlers\EPP" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 704 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\System32\ntvdm.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 704 | "C:\Users\admin\Desktop\http176.65.144.23vikWAXXEW.exe.exe" | C:\Users\admin\Desktop\http176.65.144.23vikWAXXEW.exe.exe | — | Setup.exe | |||||||||||
User: admin Company: Clouduser Integrity Level: MEDIUM Description: WAXXEW Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
141 079
Read events
138 842
Write events
2 143
Delete events
94
Modification events
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Setup.exe.zip | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
180
Suspicious files
371
Text files
165
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1032 | Setup.exe | C:\Users\admin\Desktop\httpsarchive.orgdownloadnew_image_20250515new_image.jpg.exe | — | |
MD5:— | SHA256:— | |||
| 1032 | Setup.exe | C:\Users\admin\Desktop\http185.156.72.2files6003232782oxDU0MW.exe.exe | executable | |
MD5:4EDFA1364A6E703A3DE2F73DA22841C3 | SHA256:27E23AB71F60E78FB0705F42134EDC4F0E6B99B9F0C82A8238D59DBCDE2C7D14 | |||
| 1032 | Setup.exe | C:\Users\admin\Desktop\http51.38.140.180cbotcbot_debug.exe.exe | executable | |
MD5:984F4BD2FB821583A9AF79A26D091D56 | SHA256:25171039CB6453F0BEC289800C09858BAF1D496BAD4647AD0DD1984B97E3792E | |||
| 704 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsDA4F.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 2624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2624.46529\Setup.exe.bin | executable | |
MD5:A14E63D27E1AC1DF185FA062103AA9AA | SHA256:DDA39F19837168845DE33959DE34BCFB7EE7F3A29AE55C9FA7F4CB12CB27F453 | |||
| 1032 | Setup.exe | C:\Users\admin\Desktop\http185.156.72.2files57658287103wQAlfL.exe.exe | executable | |
MD5:A85DED286361BD125CDFCEB0B6C93108 | SHA256:0F78A658B60F0879ACCCF0933D9AE8A5D2C188E9F16B8E6F7B01BD0CC9B5C4E1 | |||
| 704 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsDA3E.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 1032 | Setup.exe | C:\Users\admin\Desktop\http51.38.140.180cbotcbot.exe.exe | executable | |
MD5:6DCE41F8DAEB7F2638C7302BDC98B7E6 | SHA256:0ECABE011A9E44FFE4459C3C92230C4AB4A5B4B464D8748BDC065B911070758C | |||
| 1032 | Setup.exe | C:\Users\admin\Desktop\http51.38.140.180cbotraw_cbot.exe.exe | executable | |
MD5:DB1D95F512090B0F7AADF6C356330066 | SHA256:72129294F30C490CD4A8817262C82E007146DF5464C486CA9BF94A9CC2B4FC34 | |||
| 1032 | Setup.exe | C:\Users\admin\Desktop\http176.98.185.87Quodlibet.exe.exe | executable | |
MD5:61E040A6E8D6170E9843FE6B7B8C9FE7 | SHA256:D460044A5B2F4C50EF44ED82D6E52734E296CBC7BBBDFD7EAB10E785E49807CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
275
TCP/UDP connections
390
DNS requests
166
Threats
495
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1032 | Setup.exe | GET | 200 | 176.98.185.87:80 | http://176.98.185.87/Quodlibet.exe | unknown | — | — | unknown |
1032 | Setup.exe | GET | 200 | 176.98.185.87:80 | http://176.98.185.87/widsmob_denoise_win.exe | unknown | — | — | unknown |
1032 | Setup.exe | GET | 404 | 185.156.72.2:80 | http://185.156.72.2/files/5122596369/DMaTkR0.exe | unknown | — | — | unknown |
1032 | Setup.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/5765828710/3wQAlfL.exe | unknown | — | — | unknown |
1032 | Setup.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/6003232782/oxDU0MW.exe | unknown | — | — | unknown |
3108 | http185.156.72.2files57658287103wQAlfL.exe.exe | POST | 200 | 154.91.34.165:64951 | http://154.91.34.165:64951/ | unknown | — | — | unknown |
1032 | Setup.exe | GET | 200 | 51.38.140.180:80 | http://51.38.140.180/cbot/cbot.exe | unknown | — | — | unknown |
1032 | Setup.exe | GET | 200 | 51.38.140.180:80 | http://51.38.140.180/cbot/cbot_debug.exe | unknown | — | — | unknown |
1032 | Setup.exe | GET | 200 | 51.38.140.180:80 | http://51.38.140.180/cbot/raw_cbot_debug.exe | unknown | — | — | unknown |
1032 | Setup.exe | GET | 200 | 51.38.140.180:80 | http://51.38.140.180/cbot/raw_cbot.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1032 | Setup.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
1032 | Setup.exe | 185.215.113.66:80 | twizt.net | 1337team Limited | SC | malicious |
1032 | Setup.exe | 185.156.72.2:80 | — | Tov Vaiz Partner | RU | unknown |
1032 | Setup.exe | 176.98.185.87:80 | — | Art-telecom Ltd. | RU | unknown |
1032 | Setup.exe | 207.241.224.2:443 | archive.org | INTERNET-ARCHIVE | US | whitelisted |
1032 | Setup.exe | 207.241.227.233:443 | ia600303.us.archive.org | INTERNET-ARCHIVE | US | whitelisted |
1032 | Setup.exe | 91.193.19.130:443 | soap2dayfree.top | HZ Hosting Ltd | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
twizt.net |
| malicious |
archive.org |
| whitelisted |
mosssyoak.online |
| unknown |
ia600303.us.archive.org |
| whitelisted |
soap2dayfree.top |
| unknown |
pravaix.top |
| unknown |
regopramide.top |
| unknown |
fmovies123.top |
| unknown |
yxta.top |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1032 | Setup.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1032 | Setup.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1032 | Setup.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
1032 | Setup.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1032 | Setup.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
1032 | Setup.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
1032 | Setup.exe | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
1032 | Setup.exe | Misc activity | ET INFO Packed Executable Download |
1032 | Setup.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 34 |
1032 | Setup.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
Process | Message |
|---|---|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
http185.156.72.2lumarandom.exe.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status Originated: -1073741772
*** Source File: d:\iso_whid\x86fre\base\isolation\win32\isoreg_direct.cpp, line 1127
|
dfsvc.exe |
*** Status Originated: -1073741772
*** Source File: d:\iso_whid\x86fre\base\isolation\win32\isoreg_direct.cpp, line 1127
|
dfsvc.exe |
*** Status Originated: -1073741772
*** Source File: d:\iso_whid\x86fre\base\isolation\win32\isoreg_direct.cpp, line 1127
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|