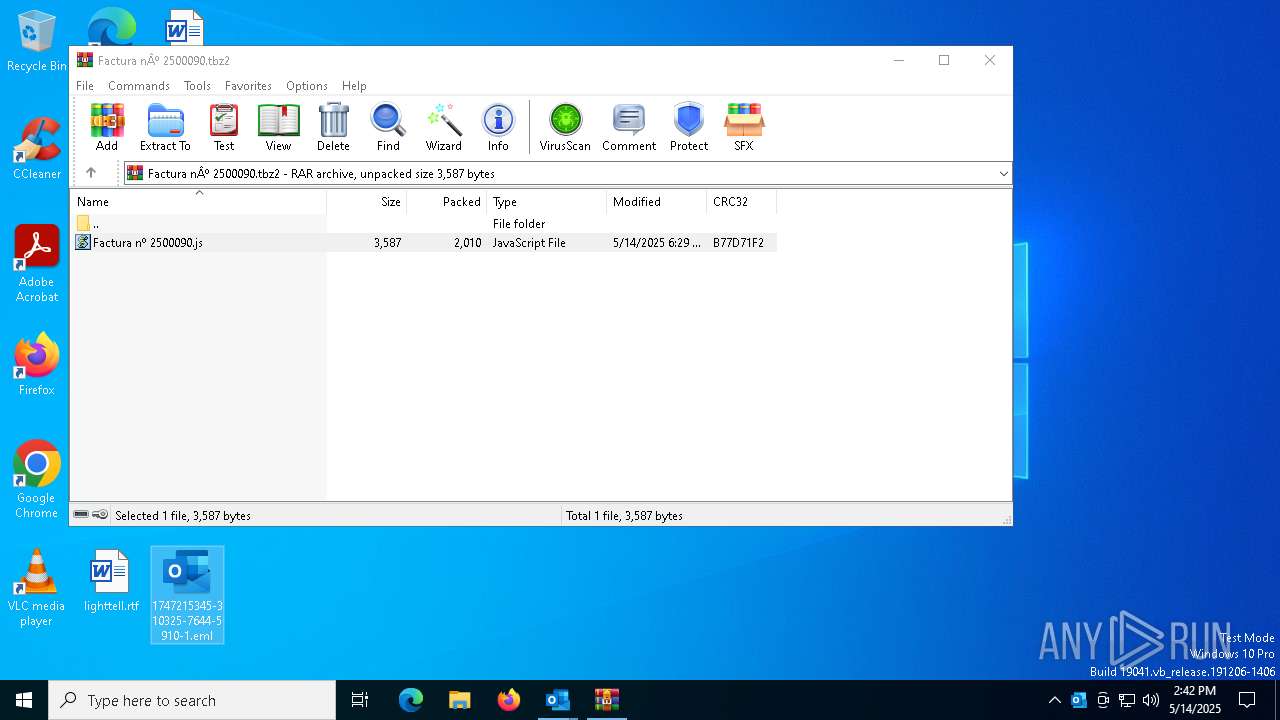
| File name: | 1747215345-310325-7644-5910-1.eml |
| Full analysis: | https://app.any.run/tasks/f9da11e3-994f-43c5-805b-86c0c87c9ad6 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 14, 2025, 14:41:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, Unicode text, UTF-8 text, with CRLF line terminators |
| MD5: | 0217330DDEB95C6E858F80362A09B82A |
| SHA1: | F94E4CAE16B2C17826D744E592E1AA60227E232A |
| SHA256: | D9408B786613A8698C902838472F91AD148C78E19F5B34EBD97D0992314ACB95 |
| SSDEEP: | 192:pvORl7g/hb0flrMyXpM8PZNITWX+SSbFhAlBS+jd5K:p2H+hwxM8PZN6hrAl/J5K |
MALICIOUS
Opens an HTTP connection (SCRIPT)
- cscript.exe (PID: 5164)
Gets path to any of the special folders (SCRIPT)
- cscript.exe (PID: 5164)
Creates internet connection object (SCRIPT)
- cscript.exe (PID: 5164)
Sends HTTP request (SCRIPT)
- cscript.exe (PID: 5164)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 7768)
Steals credentials from Web Browsers
- RegAsm.exe (PID: 7768)
AGENTTESLA has been detected (SURICATA)
- RegAsm.exe (PID: 7768)
SUSPICIOUS
Executable content was dropped or overwritten
- cscript.exe (PID: 5164)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 5164)
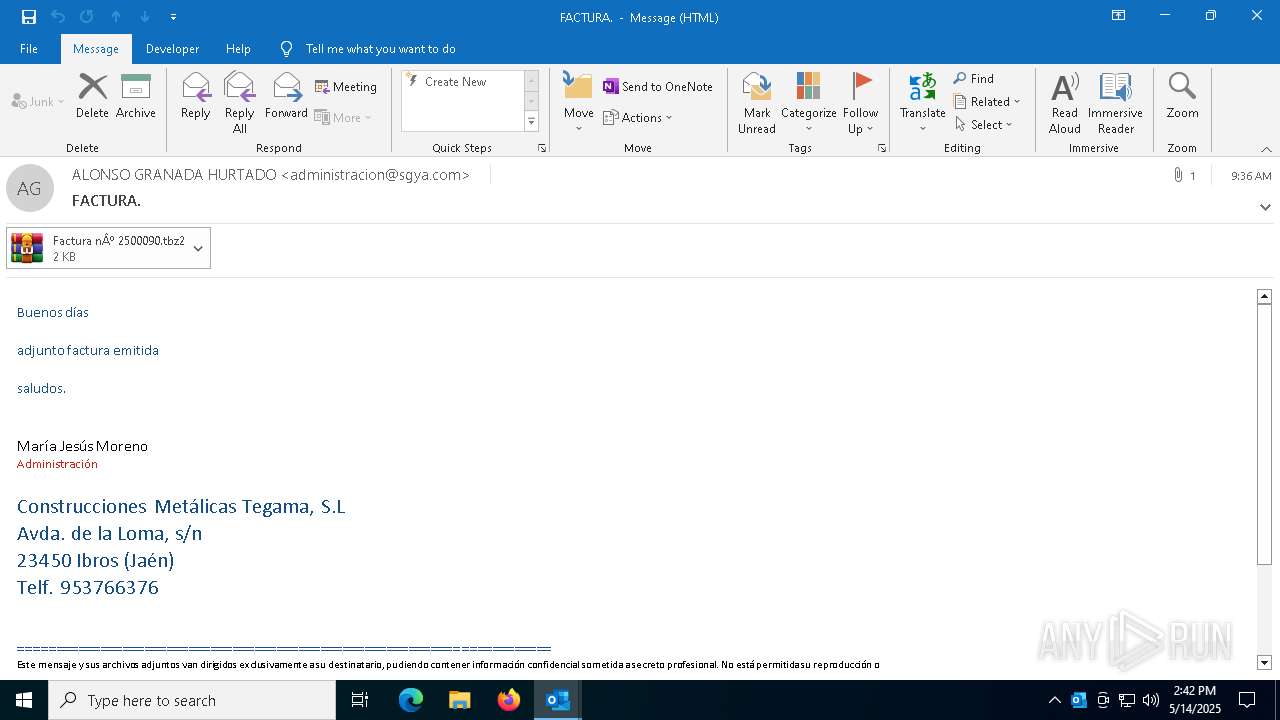
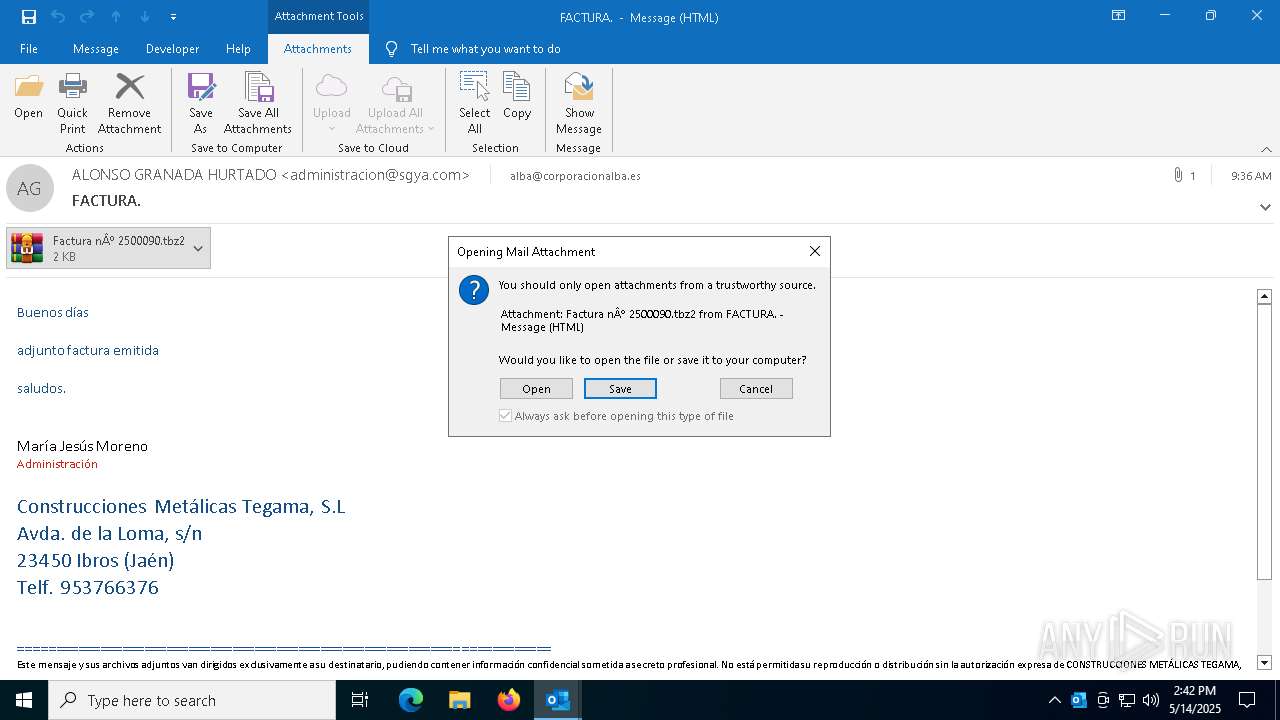
Email with suspicious attachment
- OUTLOOK.EXE (PID: 4880)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 5164)
Writes binary data to a Stream object (SCRIPT)
- cscript.exe (PID: 5164)
Saves data to a binary file (SCRIPT)
- cscript.exe (PID: 5164)
Potential Corporate Privacy Violation
- cscript.exe (PID: 5164)
Runs shell command (SCRIPT)
- cscript.exe (PID: 5164)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 5164)
Starts CMD.EXE for commands execution
- cscript.exe (PID: 5164)
Process requests binary or script from the Internet
- cscript.exe (PID: 5164)
Connects to the server without a host name
- KING1.exe (PID: 2320)
- cscript.exe (PID: 5164)
Connects to unusual port
- RegAsm.exe (PID: 7768)
Checks for external IP
- RegAsm.exe (PID: 7768)
- svchost.exe (PID: 2196)
Connects to FTP
- RegAsm.exe (PID: 7768)
INFO
Manual execution by a user
- OUTLOOK.EXE (PID: 7336)
- cscript.exe (PID: 5164)
Email with attachments
- OUTLOOK.EXE (PID: 4880)
Create files in a temporary directory
- cscript.exe (PID: 5164)
Checks supported languages
- KING1.exe (PID: 2320)
- RegAsm.exe (PID: 7768)
Reads security settings of Internet Explorer
- cscript.exe (PID: 5164)
Disables trace logs
- KING1.exe (PID: 2320)
- RegAsm.exe (PID: 7768)
Checks proxy server information
- KING1.exe (PID: 2320)
Reads the computer name
- RegAsm.exe (PID: 7768)
Reads the machine GUID from the registry
- RegAsm.exe (PID: 7768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
145
Monitored processes
13
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | "C:\Users\admin\AppData\Local\Temp\KING1.exe" | C:\Users\admin\AppData\Local\Temp\KING1.exe | cscript.exe | ||||||||||||
User: admin Company: AnyDesk Software GmbH Integrity Level: MEDIUM Description: Exit code: 0 Version: 9.0.2.0 Modules
| |||||||||||||||
| 4880 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml C:\Users\admin\Desktop\1747215345-310325-7644-5910-1.eml | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5164 | "C:\Windows\System32\CScript.exe" "C:\Users\admin\Desktop\Factura nº 2500090.js" | C:\Windows\System32\cscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5392 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6620 | "C:\Windows\System32\cmd.exe" /c del "C:\Users\admin\Desktop\Factura nº 2500090.js" | C:\Windows\System32\cmd.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7224 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7256 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7336 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\1747215345-310325-7644-5910-1.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
15 739
Read events
14 560
Write events
1 054
Delete events
125
Modification events
| (PID) Process: | (4880) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (4880) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\4880 |
| Operation: | write | Name: | 0 |
Value: 0B0E1083DAD4BDBA15F14EB1B42B48F3CDAC3F230046F89A9AF5E59BF1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5119026D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (4880) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (4880) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (4880) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4880) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (4880) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (4880) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (4880) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (4880) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
2
Suspicious files
9
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4880 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 4880 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:8268898AFA791EE6FEC1DC4958A91849 | SHA256:86EEE3372BA1DFA88DCC70ACD26971EFBC8AC7DE87499466E778843C90A43E21 | |||
| 4880 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:62CD96FC004BDA482BF3B5458C733930 | SHA256:51D8C3FEF82F48FE8BEE58CE27AB34BEF4F0AF6D5846D3AE41D3E3E871DA8D60 | |||
| 4880 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:E370A35052BB00E031680C04D45F2969 | SHA256:1DE157FCB99EA790E70A2C111A6916873B1E9FF6B0CB1C57C38A5A9CC563B883 | |||
| 4880 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 4880 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\1JL4ZFKP\Factura nº 2500090.tbz2:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 4880 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:1660516FCDC192DF050C7CB7BCB3A5A9 | SHA256:472D2EF694B4C1FE0402095141179FB85265BA8A085B2568914A24C1750D6248 | |||
| 4880 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_2EC7DA366A650545A8C8E377B760EE34.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 4880 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\1JL4ZFKP\Factura nº 2500090 (002).tbz2:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 4880 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:DFB7FF063551A8B810911C4E6FB8B897 | SHA256:3F8035573577B6E24903152B05DB946E85490D57305BFD22F4739A6629BFAECE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
34
DNS requests
21
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4880 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5164 | cscript.exe | GET | 200 | 176.65.144.23:80 | http://176.65.144.23/vik/KING1.exe | unknown | — | — | malicious |
2320 | KING1.exe | HEAD | 200 | 176.65.144.23:80 | http://176.65.144.23/vik/kinnggy2.aska | unknown | — | — | malicious |
920 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
920 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7768 | RegAsm.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
2320 | KING1.exe | GET | 200 | 176.65.144.23:80 | http://176.65.144.23/vik/kinnggy2.aska | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.139:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6148 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4880 | OUTLOOK.EXE | 52.123.131.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5164 | cscript.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5164 | cscript.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
5164 | cscript.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
5164 | cscript.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 31 |
5164 | cscript.exe | A Network Trojan was detected | ET MALWARE Possible Malicious Macro DL EXE Feb 2016 |
7768 | RegAsm.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
7768 | RegAsm.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7768 | RegAsm.exe | A Network Trojan was detected | ET MALWARE AgentTesla Exfil via FTP |