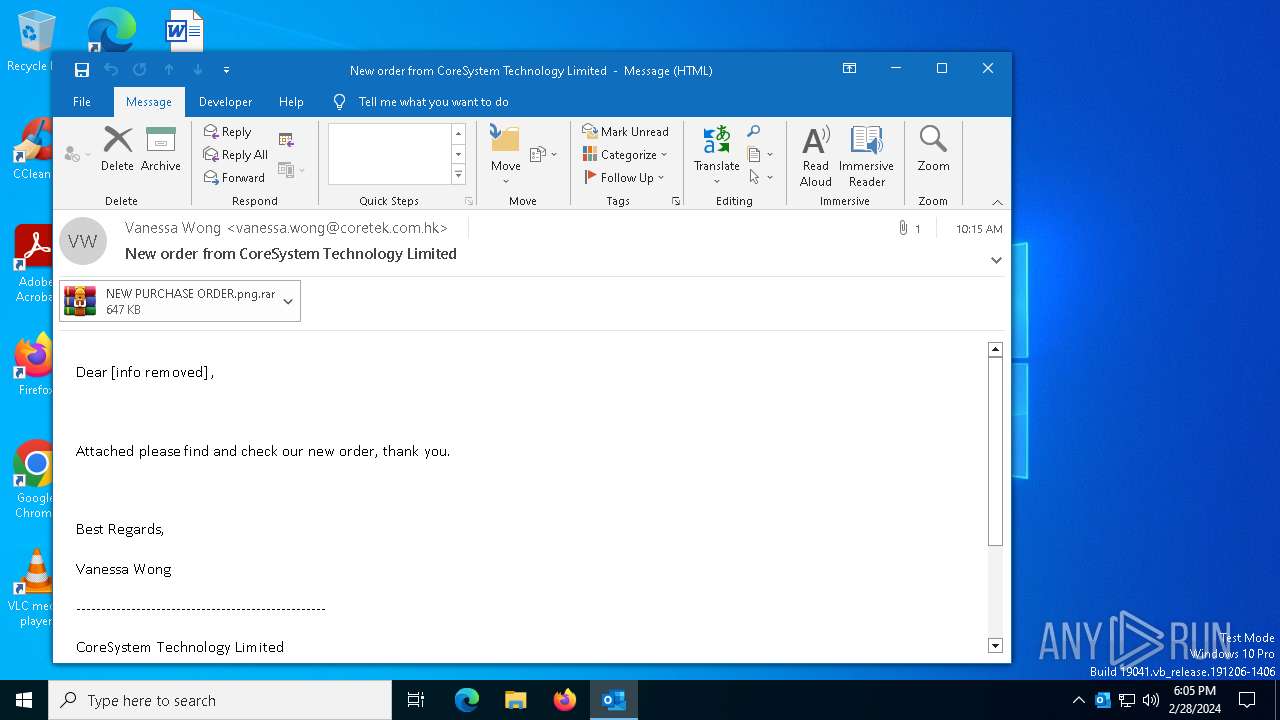
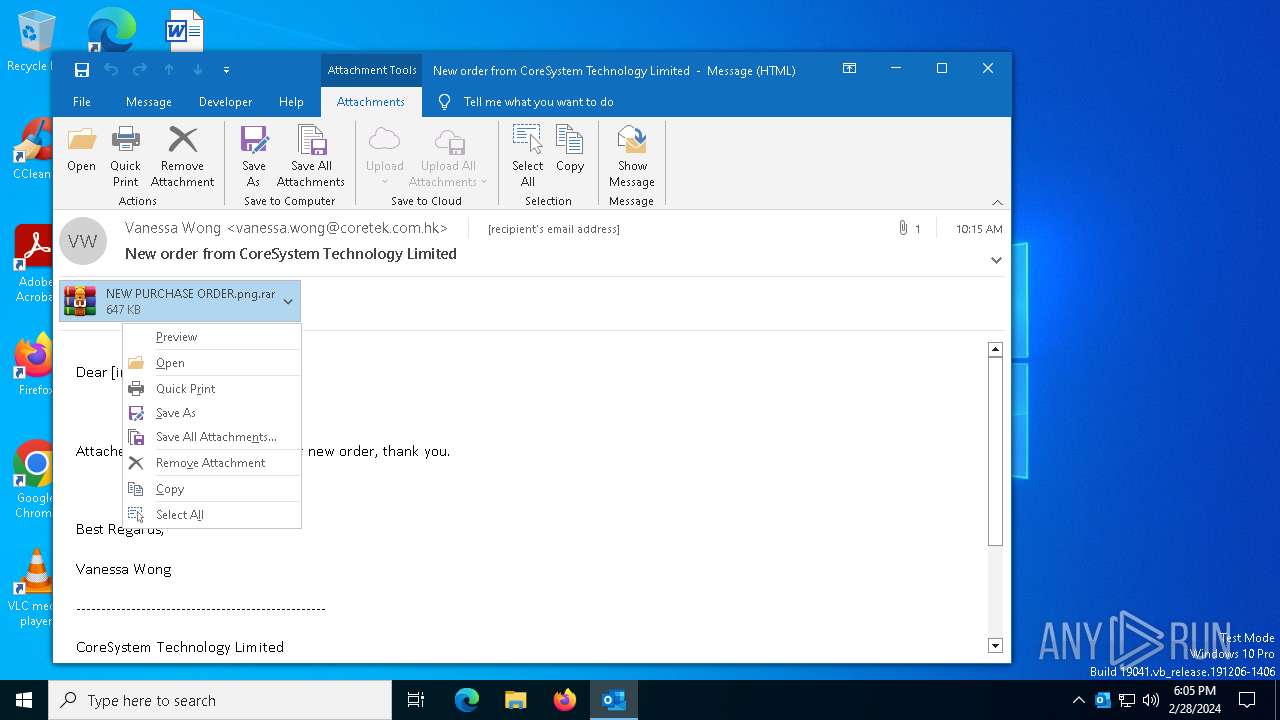
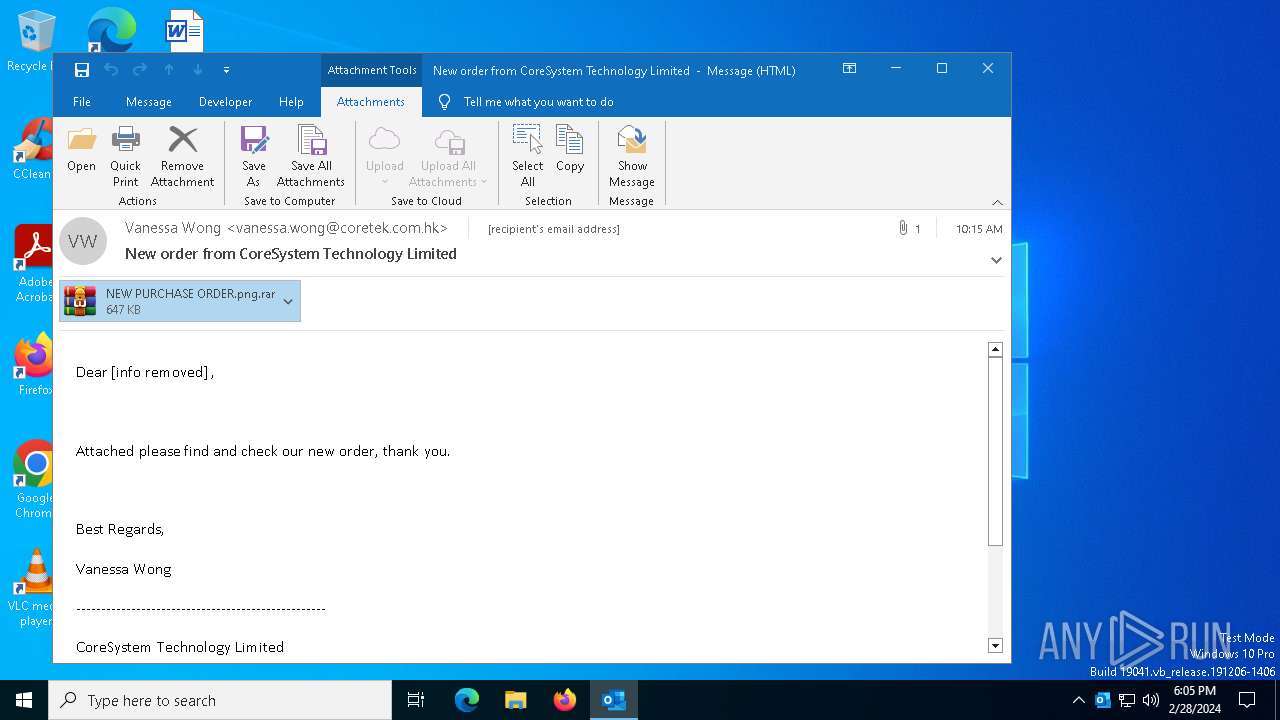
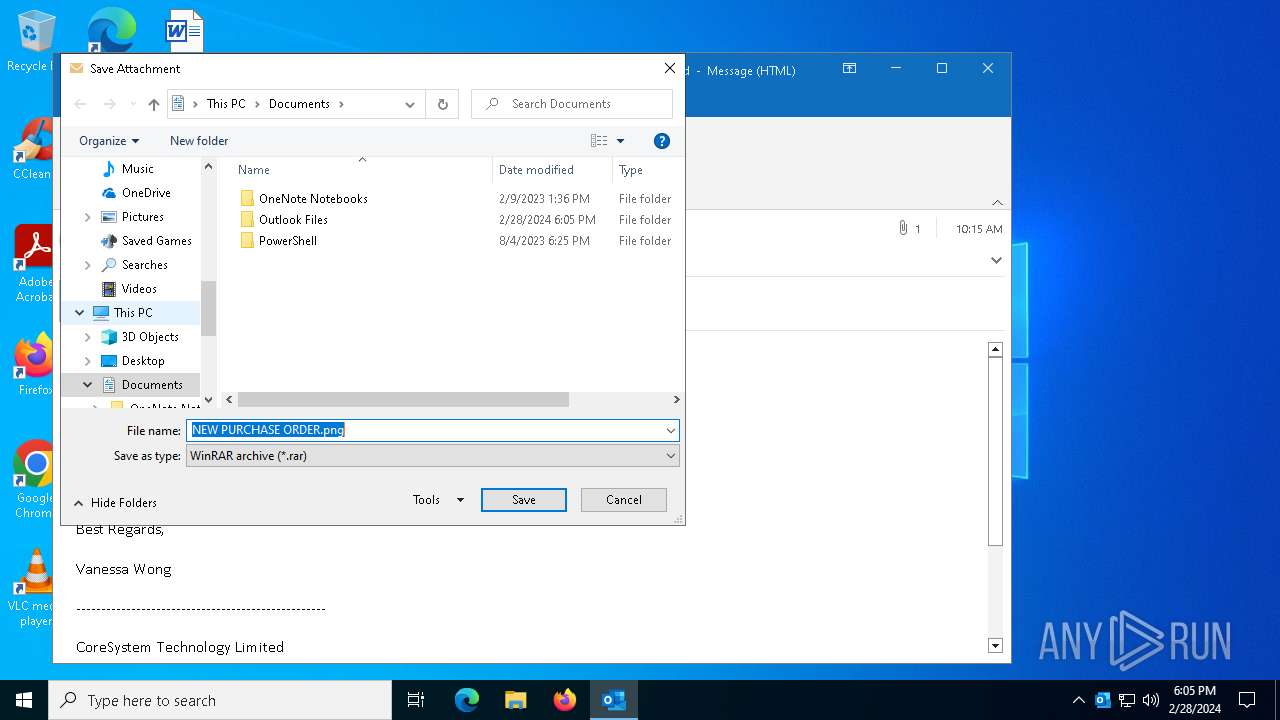
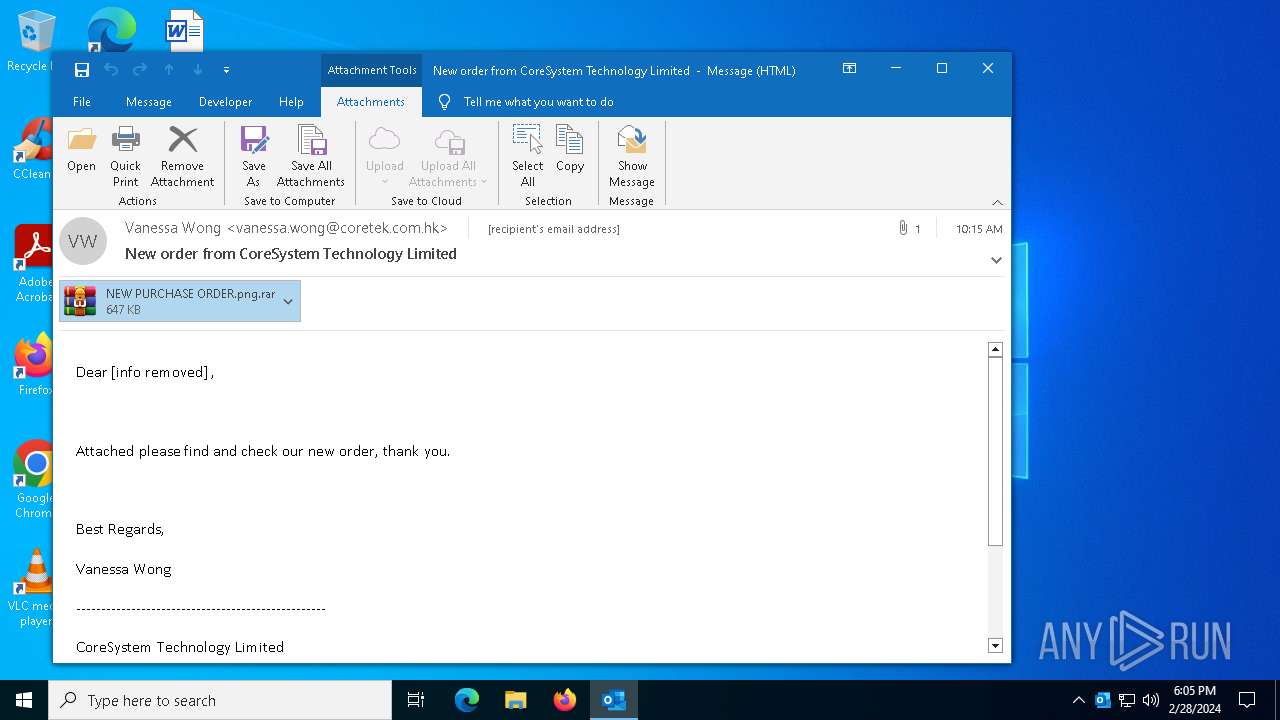
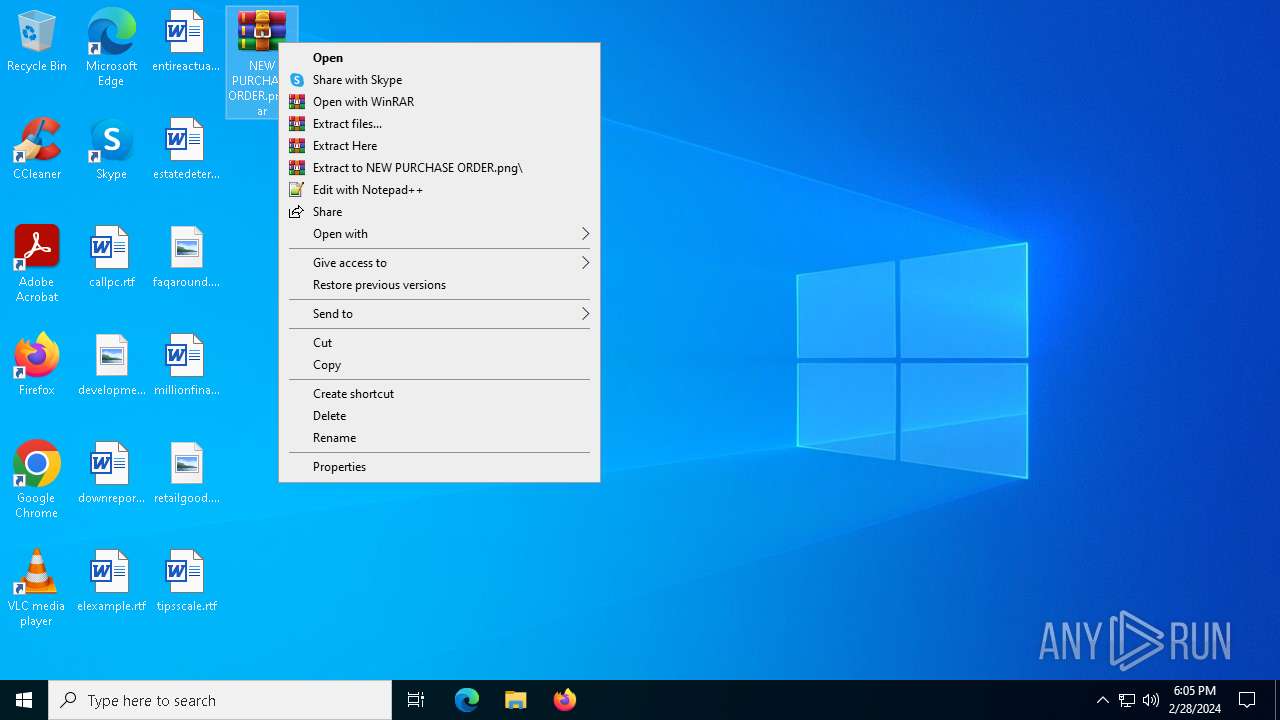
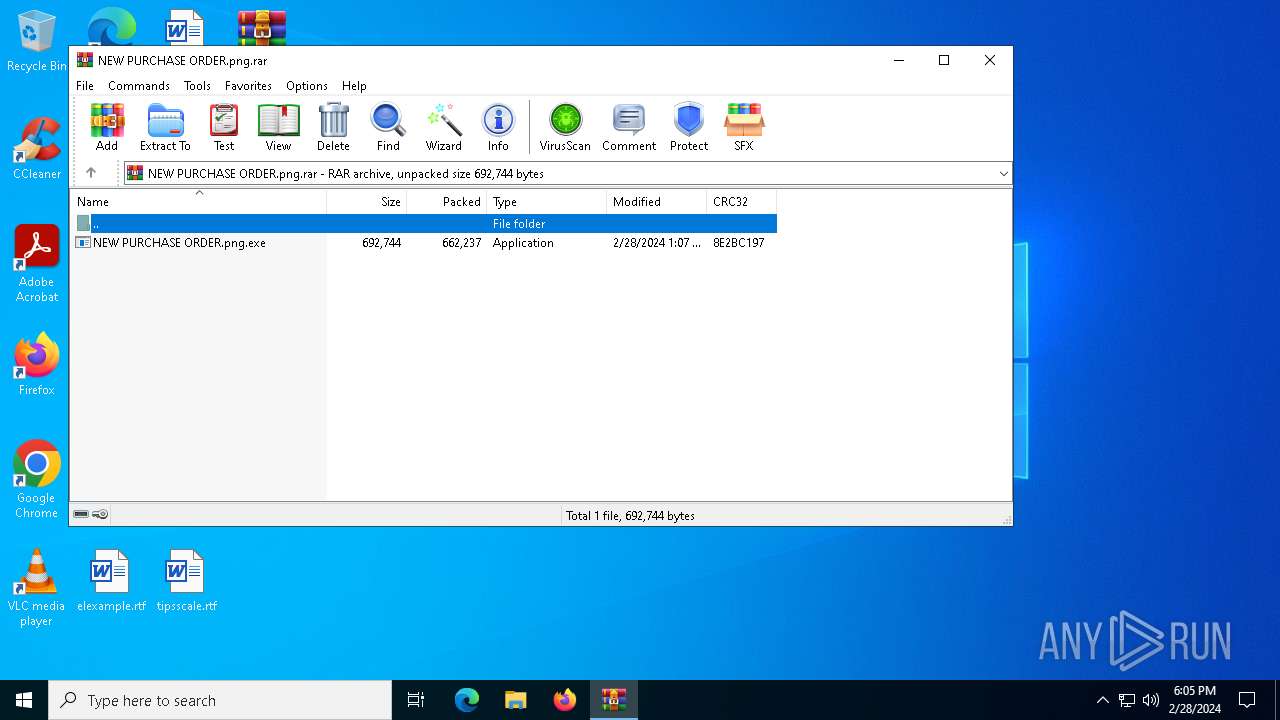
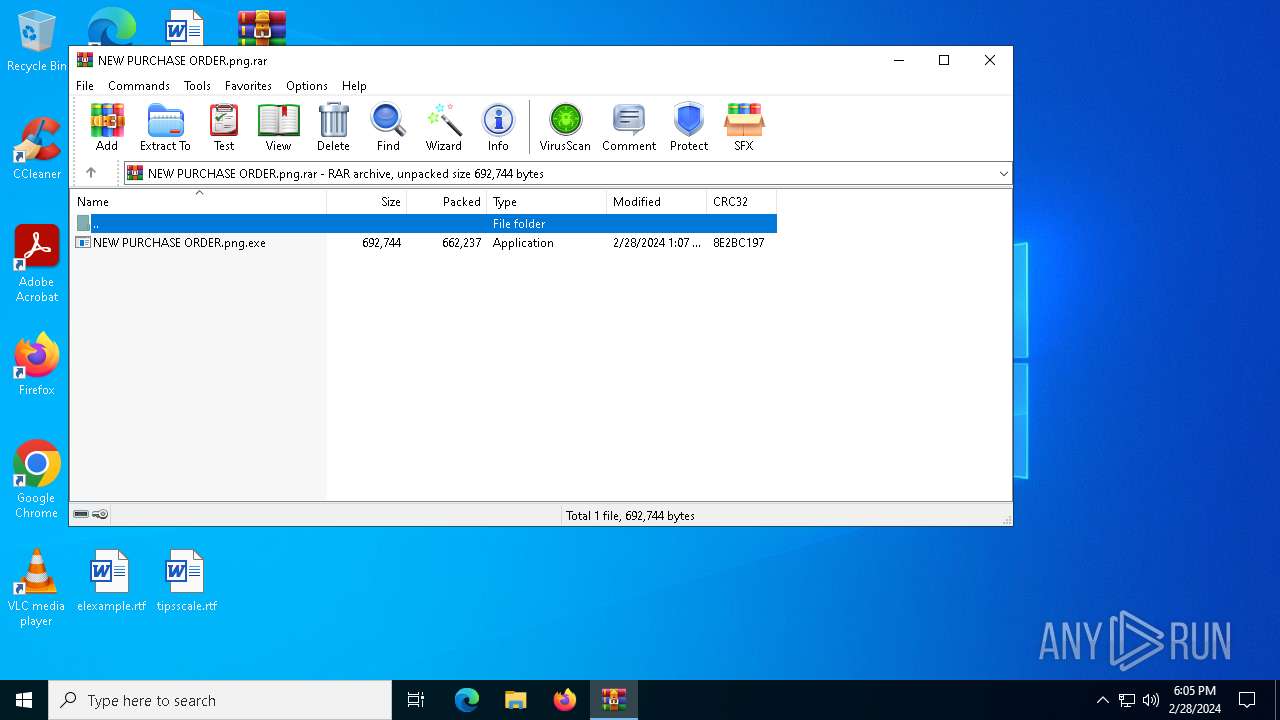
| File name: | New order from CoreSystem Technology Limited - "Vanessa Wong"<vanessa.wong@coretek.com.hk> - 2024-02-28 1015.eml |
| Full analysis: | https://app.any.run/tasks/66c5fc05-b7cf-4645-b52b-85646f51a766 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | February 28, 2024, 18:05:13 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | 06CD3C1E555C1F15F0A879946EE33E6E |
| SHA1: | 8A40924DDD4F1EE9AD82246D444331E2F7019FF9 |
| SHA256: | D9230E40C8322B1150C1240F5971922D3A2B6E29205F1DBFF0A2E8716B0BFC96 |
| SSDEEP: | 24576:qnuFeQs1Evs25vE732VDGOA20LhWVVtbgW:neQcEDvm2R2+PbZ |
MALICIOUS
Drops the executable file immediately after the start
- OUTLOOK.EXE (PID: 5524)
- RegSvcs.exe (PID: 5492)
- NEW PURCHASE ORDER.png.exe (PID: 7032)
Scans artifacts that could help determine the target
- RegSvcs.exe (PID: 5492)
Connects to the CnC server
- RegSvcs.exe (PID: 5492)
Changes the autorun value in the registry
- RegSvcs.exe (PID: 5492)
AGENTTESLA has been detected (SURICATA)
- RegSvcs.exe (PID: 5492)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 5492)
Steals credentials from Web Browsers
- RegSvcs.exe (PID: 5492)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4472)
- NEW PURCHASE ORDER.png.exe (PID: 7032)
Reads the date of Windows installation
- NEW PURCHASE ORDER.png.exe (PID: 7032)
Process drops legitimate windows executable
- RegSvcs.exe (PID: 5492)
Executable content was dropped or overwritten
- RegSvcs.exe (PID: 5492)
- NEW PURCHASE ORDER.png.exe (PID: 7032)
Connects to SMTP port
- RegSvcs.exe (PID: 5492)
INFO
Manual execution by a user
- WinRAR.exe (PID: 4472)
Checks supported languages
- RegSvcs.exe (PID: 5492)
- NEW PURCHASE ORDER.png.exe (PID: 7032)
Reads the computer name
- RegSvcs.exe (PID: 5492)
- NEW PURCHASE ORDER.png.exe (PID: 7032)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4472)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4472)
Reads the machine GUID from the registry
- NEW PURCHASE ORDER.png.exe (PID: 7032)
- RegSvcs.exe (PID: 5492)
Create files in a temporary directory
- NEW PURCHASE ORDER.png.exe (PID: 7032)
Creates files or folders in the user directory
- NEW PURCHASE ORDER.png.exe (PID: 7032)
- RegSvcs.exe (PID: 5492)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 5524)
Reads Microsoft Office registry keys
- RegSvcs.exe (PID: 5492)
Reads Environment values
- RegSvcs.exe (PID: 5492)
Process checks computer location settings
- NEW PURCHASE ORDER.png.exe (PID: 7032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
141
Monitored processes
9
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2440 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\xoOiedqKhWYXR" /XML "C:\Users\admin\AppData\Local\Temp\tmp3DD2.tmp" | C:\Windows\SysWOW64\schtasks.exe | — | NEW PURCHASE ORDER.png.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2492 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | — | NEW PURCHASE ORDER.png.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4192 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "D848A4C2-C337-463E-96C5-5589DD2857F6" "456631DA-6EBE-4969-9056-044A250A13C9" "5524" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 4472 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\NEW PURCHASE ORDER.png.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5492 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | NEW PURCHASE ORDER.png.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 5524 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\Downloads\66c5fc05-b7cf-4645-b52b-85646f51a766.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6748 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7032 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4472.4620\NEW PURCHASE ORDER.png.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4472.4620\NEW PURCHASE ORDER.png.exe | WinRAR.exe | ||||||||||||
User: admin Company: yet Integrity Level: MEDIUM Description: ww Exit code: 0 Version: 3.6.8.2 Modules
| |||||||||||||||
Total events
28 936
Read events
27 793
Write events
1 004
Delete events
139
Modification events
| (PID) Process: | (5524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E05000000000000000500000000000000 | |||
| (PID) Process: | (5524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\5524 |
| Operation: | write | Name: | 0 |
Value: 0B0E10CC56902B5FC0D84EA89411DCA73F217F230046A98DE4A78BCE9AED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511942BD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (5524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (5524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (5524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (5524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (5524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: 90DAD708-B605-4845-A6C4-89376D82CD0B | |||
| (PID) Process: | (5524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20230209T1802460432-6544.etl | |||
| (PID) Process: | (5524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
3
Suspicious files
14
Text files
7
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5524 | OUTLOOK.EXE | C:\USERS\ADMIN\DOCUMENTS\OUTLOOK FILES\OUTLOOK1.PST | — | |
MD5:— | SHA256:— | |||
| 5524 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:D23DD5B1E68D86ADE4697674AAE2BFCA | SHA256:62652FC1BB5D9C512EA20C6F615FE514E6E6B6A26148545E68F7F163A71CBCCE | |||
| 5524 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:699FD322B3F9E9D62AE2837FBA616885 | SHA256:8B68EAFDFE7F82C63F086B3AF0A5B18DE36E4ADF5D82823BB0642E48AFBB21FE | |||
| 5524 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FORMS\FRMDATA64.DAT | binary | |
MD5:6D4DE3C5917BAA7B9B0C272974B2FD4E | SHA256:EA295E017CCCD7A740EE9B7BFED3CC7C0FBBE82C991C26C051F8B3F549AB2F14 | |||
| 5524 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olk5A39.tmp | binary | |
MD5:E0BF419925C505BE3B36B4881BE36F84 | SHA256:15BB0EC44A5443437C0BCAD0577DE1A23788A9B824FFB02F87AC5A019CF161E7 | |||
| 5524 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:16886126303E5A039BEF3667E984638A | SHA256:3E9AF475BFCABA7EB255562CEA29E782B8EFA84FF5BD6ECD92554FB7F818A4CC | |||
| 5524 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | der | |
MD5:43E157F235A1E7A3ED39EA2A7EDB6AC8 | SHA256:4D48BD47C9071CEAFFD8B0674AE4B1BAA29955B21505D2FE63DE08A9A4713DC7 | |||
| 5524 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:5EC5D9CF867D526B9B054BADDCB0B4BB | SHA256:61738DD4F3611067B45BB96BA5D1A3253C4CEE0CA9DF25863ECA2CDA3313AF26 | |||
| 5524 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\460E7456-B001-4D5E-8AC6-13C6E78BBF64 | xml | |
MD5:1454AE7BFF2EEB7F48DE50B7D38E3A89 | SHA256:9924303100A8185B6E9A97066722FAE6356C10922570EEB27F81A64B209571DE | |||
| 5524 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\5475cb191e478c39370a215b2da98a37e9dc813d.tbres | binary | |
MD5:B9C471B45FB3BE86FEC7D07876B03C78 | SHA256:0E00D6A0B3ED8B7974688EE860C92234E166F0E6968D55BAD88C4F48AC91CFE3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
42
DNS requests
24
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5364 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
5524 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | binary | 471 b | unknown |
5524 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
1560 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.01 Kb | unknown |
1452 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
2464 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
5928 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3848 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1560 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5928 | svchost.exe | 40.126.31.69:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6896 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5524 | OUTLOOK.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5928 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1560 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
5524 | OUTLOOK.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
nleditor.osi.office.net |
| whitelisted |
odc.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5492 | RegSvcs.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
2 ETPRO signatures available at the full report