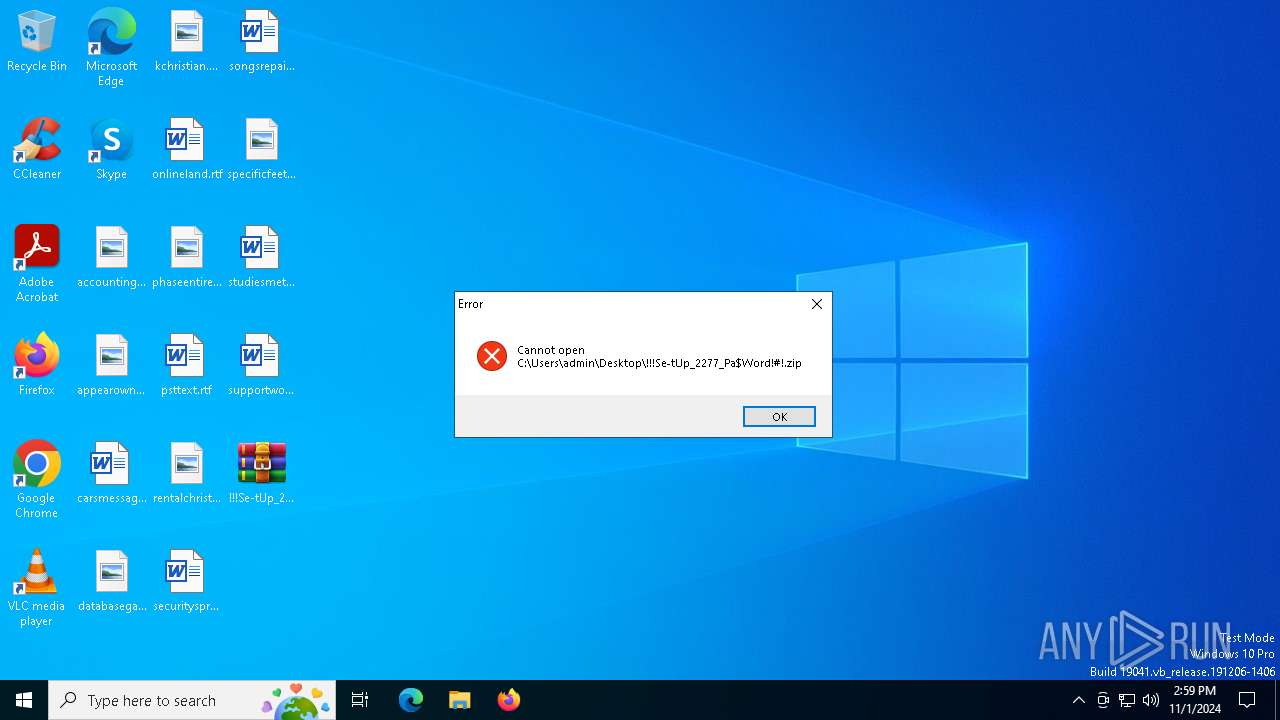
| File name: | !!!Se-tUp_2277_Pa$Word!#!.zip |
| Full analysis: | https://app.any.run/tasks/ec0006fa-738c-4794-8c15-083c00ca16b6 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | November 01, 2024, 14:59:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
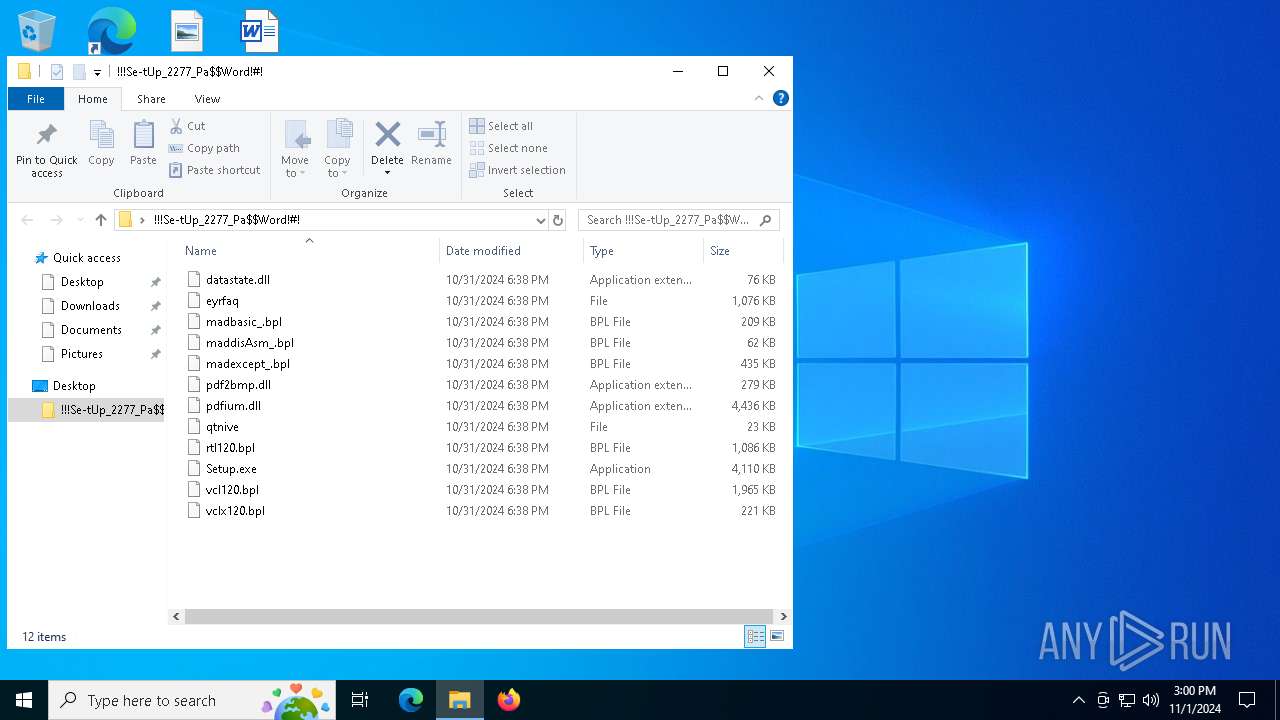
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | E7D61B47941EB1F258FCAC9B7BC34D5B |
| SHA1: | 6292DD0234B136531B186E1502F48010F930BCC8 |
| SHA256: | D8C7BA1DF28EA38DB7FB7DF99FB028D090DEE27C750F017CA75F8E5BF4D83D73 |
| SSDEEP: | 98304:Px8gAghX50j4hbhcPC7UxXBUrNQbmOODVqGhTaiq/oyXaT6f/1NQywlCosuIqaMh:RGaLeVSN6EOMx7rB |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6212)
Changes powershell execution policy (Bypass)
- OpenWith.exe (PID: 6860)
AMADEY has been detected (SURICATA)
- explorer.exe (PID: 6476)
Stealers network behavior
- svchost.exe (PID: 2172)
Connects to the CnC server
- explorer.exe (PID: 6476)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2172)
SUSPICIOUS
Executable content was dropped or overwritten
- AutoIt3.exe (PID: 6936)
- Setup.exe (PID: 5064)
- OpenWith.exe (PID: 6860)
Contacting a server suspected of hosting an CnC
- explorer.exe (PID: 6476)
- svchost.exe (PID: 2172)
Connects to unusual port
- MicrosoftEdgeUpdateCore.exe (PID: 7056)
Starts application with an unusual extension
- Setup.exe (PID: 5064)
Starts POWERSHELL.EXE for commands execution
- OpenWith.exe (PID: 6860)
Node.exe was dropped
- OpenWith.exe (PID: 6860)
The process executes Powershell scripts
- OpenWith.exe (PID: 6860)
INFO
Manual execution by a user
- WinRAR.exe (PID: 6100)
- Setup.exe (PID: 5064)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:10:31 19:38:24 |
| ZipCRC: | 0x663361a6 |
| ZipCompressedSize: | 81265 |
| ZipUncompressedSize: | 225792 |
| ZipFileName: | vclx120.bpl |
Total processes
151
Monitored processes
19
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 512 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\!!!Se-tUp_2277_Pa$Word!#!.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1 Version: 5.91.0 Modules
| |||||||||||||||
| 1084 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1500 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2380 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3580 | C:\WINDOWS\SysWOW64\comp.exe | C:\Windows\SysWOW64\comp.exe | — | 8Y82FKAG2RYGSX6OFYYIHG3XU6P3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: File Compare Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3944 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | nc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4144 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4316 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
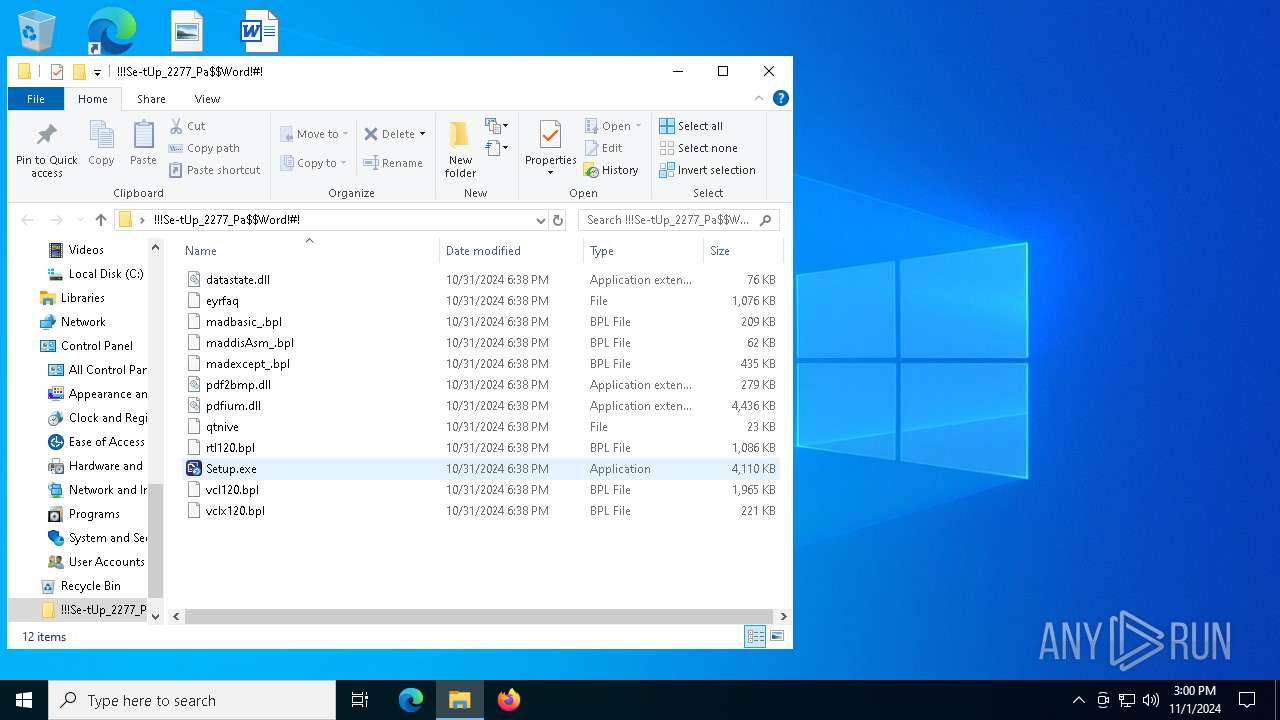
| 5064 | "C:\Users\admin\Desktop\!!!Se-tUp_2277_Pa$Word!#!\Setup.exe" | C:\Users\admin\Desktop\!!!Se-tUp_2277_Pa$Word!#!\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: iTop Inc. Integrity Level: MEDIUM Description: iTop Data Recovery Exit code: 1 Version: 4.4.0.687 Modules
| |||||||||||||||
Total events
11 436
Read events
11 405
Write events
18
Delete events
13
Modification events
| (PID) Process: | (512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_0 |
Value: 4C000000730100000402000000000000F0F0F00000000000000000000000000000000000000000002202070000000000000000003B000000B402000000000000000000000000000001000000 | |||
| (PID) Process: | (512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_1 |
Value: 4C000000730100000500000000000000F0F0F0000000000000000000000000000000000000000000DE0204000000000000000000180000002A00000000000000000000000000000002000000 | |||
| (PID) Process: | (512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_2 |
Value: 4C000000730100000400000000000000F0F0F00000000000000000000000000000000000000000001A0213000000000000000000180000006400000000000000000000000000000003000000 | |||
| (PID) Process: | (6100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (6100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
Executable files
21
Suspicious files
14
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6100 | WinRAR.exe | C:\Users\admin\Desktop\!!!Se-tUp_2277_Pa$Word!#!\datastate.dll | executable | |
MD5:28F0CCF746F952F94FF434CA989B7814 | SHA256:6010E2147A0F51A7BFA2F942A5A9EAAD9A294F463F717963B486ED3F53D305C2 | |||
| 6100 | WinRAR.exe | C:\Users\admin\Desktop\!!!Se-tUp_2277_Pa$Word!#!\Setup.exe | executable | |
MD5:95387CC85DACAD60B3E10665B43602E6 | SHA256:3C317DBAB70D3AB4FCE944C92532D111F69FD71DCA5C7F7C7B8D57E657F26A1A | |||
| 5064 | Setup.exe | C:\Users\admin\AppData\Roaming\XSGATY\madbasic_.bpl | executable | |
MD5:DC6655A38FFDC3C349F13828FC8EC36E | SHA256:16126FF5DAA3787A159CF4A39AA040B8050EBB66AB90DBB97C503110EF72824A | |||
| 5064 | Setup.exe | C:\Users\admin\AppData\Roaming\XSGATY\maddisAsm_.bpl | executable | |
MD5:84BC072F8EA30746F0982AFBDA3C638F | SHA256:52019F47F96CA868FA4E747C3B99CBA1B7AA57317BF8EBF9FCBF09AA576FE006 | |||
| 5064 | Setup.exe | C:\Users\admin\AppData\Roaming\XSGATY\pdfium.dll | executable | |
MD5:65A63BD3E6C4CE54299BF494582304F3 | SHA256:5B8D7269ED5CA414208FF017F52EE65F14D4D8A707A39A7DC3F9879C0C0CE335 | |||
| 6100 | WinRAR.exe | C:\Users\admin\Desktop\!!!Se-tUp_2277_Pa$Word!#!\pdfium.dll | executable | |
MD5:65A63BD3E6C4CE54299BF494582304F3 | SHA256:5B8D7269ED5CA414208FF017F52EE65F14D4D8A707A39A7DC3F9879C0C0CE335 | |||
| 6100 | WinRAR.exe | C:\Users\admin\Desktop\!!!Se-tUp_2277_Pa$Word!#!\madbasic_.bpl | executable | |
MD5:DC6655A38FFDC3C349F13828FC8EC36E | SHA256:16126FF5DAA3787A159CF4A39AA040B8050EBB66AB90DBB97C503110EF72824A | |||
| 4316 | more.com | C:\Users\admin\AppData\Local\Temp\ckk | — | |
MD5:— | SHA256:— | |||
| 5064 | Setup.exe | C:\Users\admin\AppData\Roaming\XSGATY\qtnive | binary | |
MD5:AAFA0C53281D6C12A6AC4662251E23BC | SHA256:551AE344D687E2DE3BF8F546B6EA2E959F54D26D52BABD472C3D174F01BAD629 | |||
| 5064 | Setup.exe | C:\Users\admin\AppData\Roaming\XSGATY\datastate.dll | executable | |
MD5:28F0CCF746F952F94FF434CA989B7814 | SHA256:6010E2147A0F51A7BFA2F942A5A9EAAD9A294F463F717963B486ED3F53D305C2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
63
DNS requests
36
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5824 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4516 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6476 | explorer.exe | POST | 200 | 172.67.213.173:80 | http://moviecentral-petparade.com/g9jvjfd73/index.php | unknown | — | — | malicious |
5012 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6860 | OpenWith.exe | GET | 200 | 142.250.185.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6476 | explorer.exe | POST | 200 | 172.67.213.173:80 | http://moviecentral-petparade.com/g9jvjfd73/index.php | unknown | — | — | malicious |
6860 | OpenWith.exe | GET | 200 | 142.250.185.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1252 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.209.189:443 | th.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6944 | svchost.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6944 | svchost.exe | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
4360 | SearchApp.exe | 2.23.209.135:443 | — | Akamai International B.V. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (creative-habitat .shop) |
2172 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
6860 | OpenWith.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (creative-habitat .shop) |
6476 | explorer.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
6476 | explorer.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
7 ETPRO signatures available at the full report