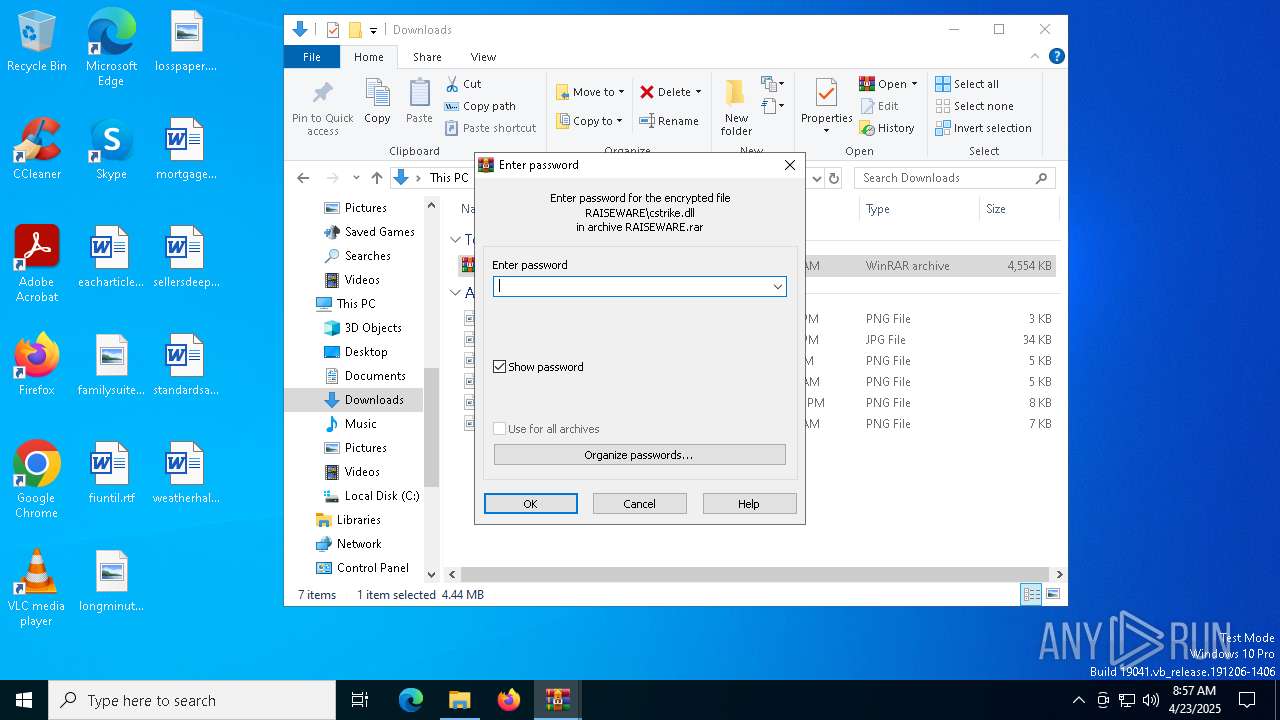
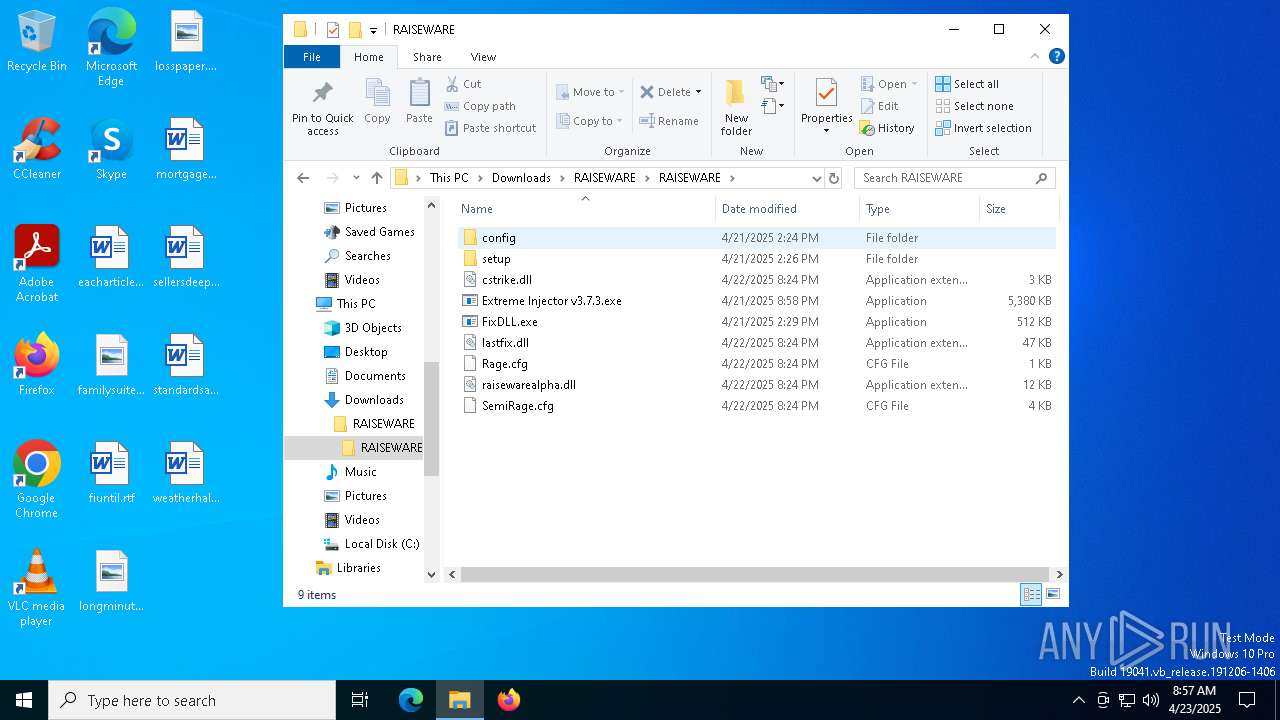
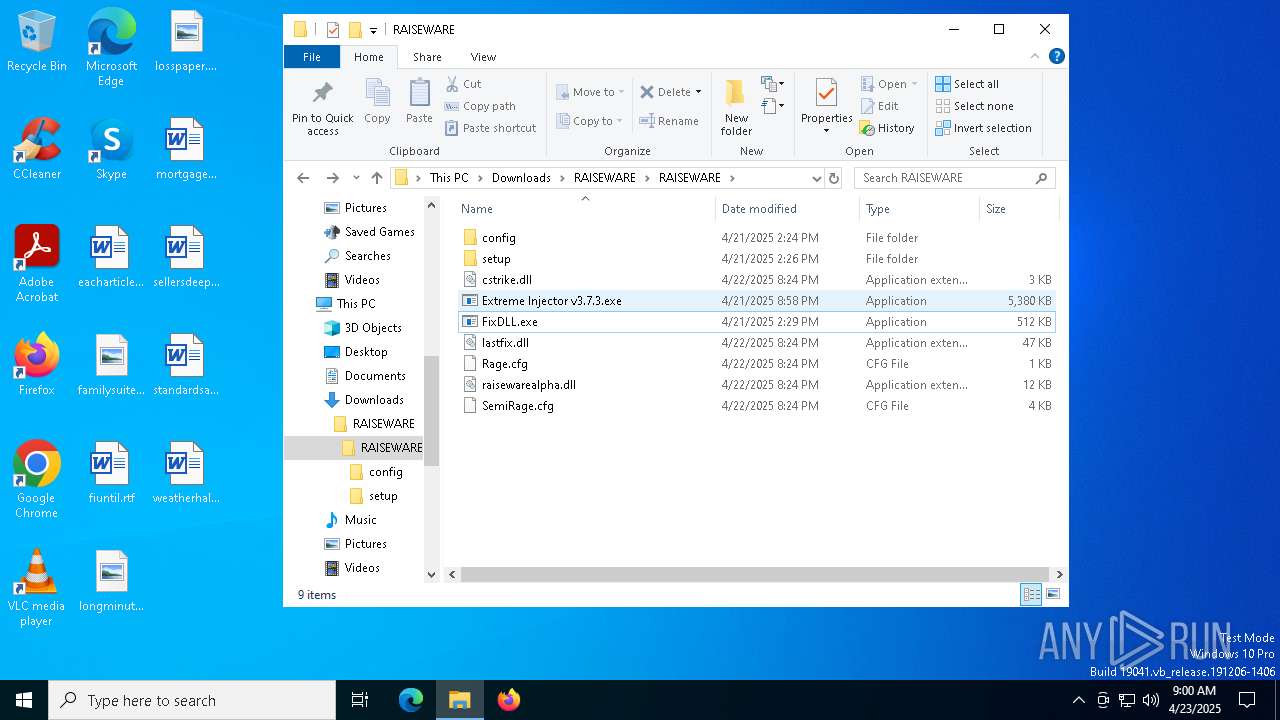
| URL: | https://www.mediafire.com/file/ftux0jgxfg9qhbx/RAISEWARE.rar/file |
| Full analysis: | https://app.any.run/tasks/b8b08e77-0cc5-4c9c-85d0-f0efba4fa69c |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | April 23, 2025, 08:56:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 219204F5F3FC8FA6BAFA0C713EB29BBF |
| SHA1: | B94DB4FCD6164EC27A448271A2585BFD5DD7B1D0 |
| SHA256: | D8B188F10FACD0488A2CD2DE714F55AE32A2F912238ECE96062F9488C7CB0BDB |
| SSDEEP: | 3:N8DSLw3eGUoCfcBA:2OLw3eGwiA |
MALICIOUS
Executing a file with an untrusted certificate
- Extreme Injector v3.7.3.exe (PID: 7684)
- Extreme Injector v3.7.3.exe (PID: 1180)
- Extreme Injector v3.7.3.exe (PID: 8116)
- Extreme Injector v3.7.3.exe (PID: 896)
- qbutngoajxis.exe (PID: 5136)
Changes Windows Defender settings
- Extreme Injector v3.7.3.exe (PID: 896)
- qbutngoajxis.exe (PID: 5136)
Uninstalls Malicious Software Removal Tool (MRT)
- cmd.exe (PID: 6108)
- cmd.exe (PID: 2408)
Adds extension to the Windows Defender exclusion list
- Extreme Injector v3.7.3.exe (PID: 896)
- qbutngoajxis.exe (PID: 5136)
Application was injected by another process
- lsass.exe (PID: 756)
- svchost.exe (PID: 1260)
- svchost.exe (PID: 1288)
- svchost.exe (PID: 468)
- svchost.exe (PID: 1252)
- svchost.exe (PID: 1352)
- svchost.exe (PID: 1044)
- svchost.exe (PID: 1232)
- svchost.exe (PID: 1416)
- svchost.exe (PID: 1524)
- svchost.exe (PID: 1444)
- svchost.exe (PID: 1784)
- svchost.exe (PID: 1892)
- svchost.exe (PID: 1792)
- svchost.exe (PID: 1772)
- svchost.exe (PID: 1980)
- svchost.exe (PID: 2396)
- svchost.exe (PID: 1988)
- svchost.exe (PID: 2196)
- svchost.exe (PID: 2292)
- svchost.exe (PID: 2068)
- svchost.exe (PID: 2172)
- svchost.exe (PID: 2448)
- svchost.exe (PID: 2544)
- svchost.exe (PID: 1652)
- svchost.exe (PID: 1552)
- svchost.exe (PID: 1904)
- svchost.exe (PID: 2536)
- svchost.exe (PID: 3084)
- svchost.exe (PID: 2932)
- spoolsv.exe (PID: 2732)
- svchost.exe (PID: 2624)
- svchost.exe (PID: 2584)
- svchost.exe (PID: 3104)
- svchost.exe (PID: 3232)
- OfficeClickToRun.exe (PID: 3112)
- svchost.exe (PID: 2880)
- svchost.exe (PID: 3184)
- svchost.exe (PID: 3196)
- svchost.exe (PID: 3284)
- svchost.exe (PID: 3564)
- svchost.exe (PID: 2920)
- svchost.exe (PID: 3216)
- svchost.exe (PID: 3860)
- svchost.exe (PID: 3812)
- svchost.exe (PID: 860)
- svchost.exe (PID: 4508)
- svchost.exe (PID: 4952)
- svchost.exe (PID: 2996)
- winlogon.exe (PID: 6648)
- sihost.exe (PID: 4984)
- uhssvc.exe (PID: 648)
- svchost.exe (PID: 6024)
- explorer.exe (PID: 5492)
- dwm.exe (PID: 6568)
- svchost.exe (PID: 4544)
- svchost.exe (PID: 4312)
- svchost.exe (PID: 4292)
- MoUsoCoreWorker.exe (PID: 5496)
- svchost.exe (PID: 2112)
- dllhost.exe (PID: 5880)
- svchost.exe (PID: 1572)
- svchost.exe (PID: 1684)
- dllhost.exe (PID: 6896)
- svchost.exe (PID: 6608)
- dllhost.exe (PID: 6176)
- svchost.exe (PID: 5212)
- ApplicationFrameHost.exe (PID: 6952)
- UserOOBEBroker.exe (PID: 1248)
- svchost.exe (PID: 4916)
- svchost.exe (PID: 4684)
- svchost.exe (PID: 6544)
- svchost.exe (PID: 5132)
- svchost.exe (PID: 6180)
- audiodg.exe (PID: 6168)
- svchost.exe (PID: 7156)
- svchost.exe (PID: 8184)
- ctfmon.exe (PID: 956)
- RuntimeBroker.exe (PID: 1036)
- RuntimeBroker.exe (PID: 5368)
- RuntimeBroker.exe (PID: 6160)
- WmiPrvSE.exe (PID: 6480)
- svchost.exe (PID: 7884)
- WmiPrvSE.exe (PID: 7960)
- svchost.exe (PID: 5408)
- taskhostw.exe (PID: 8012)
Runs injected code in another process
- dialer.exe (PID: 7396)
- dialer.exe (PID: 3968)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2196)
Vulnerable driver has been detected
- qbutngoajxis.exe (PID: 5136)
XMRIG has been detected (YARA)
- dialer.exe (PID: 7716)
SUSPICIOUS
Starts process via Powershell
- powershell.exe (PID: 7664)
- powershell.exe (PID: 5344)
- powershell.exe (PID: 8120)
Starts POWERSHELL.EXE for commands execution
- Extreme Injector v3.7.3.exe (PID: 7684)
- Extreme Injector v3.7.3.exe (PID: 1180)
- Extreme Injector v3.7.3.exe (PID: 8116)
- Extreme Injector v3.7.3.exe (PID: 896)
- qbutngoajxis.exe (PID: 5136)
Script adds exclusion path to Windows Defender
- Extreme Injector v3.7.3.exe (PID: 896)
- qbutngoajxis.exe (PID: 5136)
Script adds exclusion extension to Windows Defender
- Extreme Injector v3.7.3.exe (PID: 896)
- qbutngoajxis.exe (PID: 5136)
Manipulates environment variables
- powershell.exe (PID: 2392)
- powershell.exe (PID: 6156)
Starts CMD.EXE for commands execution
- Extreme Injector v3.7.3.exe (PID: 896)
- qbutngoajxis.exe (PID: 5136)
Stops a currently running service
- sc.exe (PID: 2852)
- sc.exe (PID: 2236)
- sc.exe (PID: 7332)
- sc.exe (PID: 7708)
- sc.exe (PID: 5384)
- sc.exe (PID: 6572)
- sc.exe (PID: 6904)
- sc.exe (PID: 776)
- sc.exe (PID: 5968)
- sc.exe (PID: 5084)
- sc.exe (PID: 1672)
Process uninstalls Windows update
- wusa.exe (PID: 7788)
- wusa.exe (PID: 3796)
Starts SC.EXE for service management
- Extreme Injector v3.7.3.exe (PID: 896)
- qbutngoajxis.exe (PID: 5136)
Windows service management via SC.EXE
- sc.exe (PID: 7520)
- sc.exe (PID: 5400)
Uses powercfg.exe to modify the power settings
- Extreme Injector v3.7.3.exe (PID: 896)
- qbutngoajxis.exe (PID: 5136)
Creates a new Windows service
- sc.exe (PID: 4692)
Executable content was dropped or overwritten
- Extreme Injector v3.7.3.exe (PID: 896)
- qbutngoajxis.exe (PID: 5136)
Executes as Windows Service
- qbutngoajxis.exe (PID: 5136)
Drops a system driver (possible attempt to evade defenses)
- qbutngoajxis.exe (PID: 5136)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2196)
INFO
Application launched itself
- chrome.exe (PID: 4880)
Reads the time zone
- MoUsoCoreWorker.exe (PID: 5496)
- WmiPrvSE.exe (PID: 7960)
- svchost.exe (PID: 2396)
Creates files in the program directory
- MoUsoCoreWorker.exe (PID: 5496)
- Extreme Injector v3.7.3.exe (PID: 896)
Manual execution by a user
- WinRAR.exe (PID: 2040)
- Extreme Injector v3.7.3.exe (PID: 7684)
- FixDLL.exe (PID: 5172)
- Extreme Injector v3.7.3.exe (PID: 1180)
- Extreme Injector v3.7.3.exe (PID: 8116)
- FixDLL.exe (PID: 8156)
- FixDLL.exe (PID: 3900)
- Extreme Injector v3.7.3.exe (PID: 896)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
Reads the software policy settings
- slui.exe (PID: 7804)
- lsass.exe (PID: 756)
- slui.exe (PID: 5136)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5492)
- OfficeClickToRun.exe (PID: 3112)
The sample compiled with english language support
- WinRAR.exe (PID: 2040)
- Extreme Injector v3.7.3.exe (PID: 896)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2040)
Checks supported languages
- Extreme Injector v3.7.3.exe (PID: 7684)
- FixDLL.exe (PID: 5172)
- Extreme Injector v3.7.3.exe (PID: 1180)
- Extreme Injector v3.7.3.exe (PID: 8116)
- FixDLL.exe (PID: 8156)
- Extreme Injector v3.7.3.exe (PID: 896)
- FixDLL.exe (PID: 3900)
- uhssvc.exe (PID: 648)
- qbutngoajxis.exe (PID: 5136)
Reads the computer name
- FixDLL.exe (PID: 5172)
- FixDLL.exe (PID: 8156)
- FixDLL.exe (PID: 3900)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7664)
- powershell.exe (PID: 5344)
- powershell.exe (PID: 8120)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 6156)
Checks proxy server information
- slui.exe (PID: 5136)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 6156)
The sample compiled with japanese language support
- qbutngoajxis.exe (PID: 5136)
UPX packer has been detected
- dialer.exe (PID: 7716)
Creates files or folders in the user directory
- lsass.exe (PID: 756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
252
Monitored processes
198
Malicious processes
95
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 468 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 648 | "C:\Program Files\Microsoft Update Health Tools\uhssvc.exe" | C:\Program Files\Microsoft Update Health Tools\uhssvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Update Health Service Version: 10.0.19041.3626 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=32 --mojo-platform-channel-handle=6636 --field-trial-handle=1888,i,4678125886711011568,7821011088126528122,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 756 | C:\WINDOWS\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | C:\WINDOWS\system32\sc.exe stop WaaSMedicSvc | C:\Windows\System32\sc.exe | — | qbutngoajxis.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=19 --mojo-platform-channel-handle=6600 --field-trial-handle=1888,i,4678125886711011568,7821011088126528122,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 860 | C:\WINDOWS\System32\svchost.exe -k LocalServiceNetworkRestricted -s RmSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=6040 --field-trial-handle=1888,i,4678125886711011568,7821011088126528122,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 896 | "C:\Users\admin\Downloads\RAISEWARE\RAISEWARE\Extreme Injector v3.7.3.exe" | C:\Users\admin\Downloads\RAISEWARE\RAISEWARE\Extreme Injector v3.7.3.exe | explorer.exe | ||||||||||||
User: admin Company: Update Integrity Level: HIGH Description: Update Exit code: 0 Version: 1,1,1,0 Modules
| |||||||||||||||
| 956 | "ctfmon.exe" | C:\Windows\System32\ctfmon.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CTF Loader Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
131 836
Read events
130 647
Write events
886
Delete events
303
Modification events
| (PID) Process: | (5496) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Wosc\Client\Persistent\ClientState\WOSC |
| Operation: | write | Name: | ETag |
Value: "14B6668685A86B8B3340E54F72D5299AE61E827C825447B3AD621BDEC5D8860D3D8C46FDEB5D66C7AC15AF89::2F263157C8" | |||
| (PID) Process: | (5496) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Wosc\Client\Persistent\ClientState\WOSC |
| Operation: | delete value | Name: | ETagBackup |
Value: | |||
| (PID) Process: | (5496) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Wosc\Client\Persistent\ClientState\WOSC |
| Operation: | write | Name: | LastUpdated |
Value: 8E3936922DB4DB01 | |||
| (PID) Process: | (5496) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Wosc\Client\Persistent\ClientState\WOSC |
| Operation: | write | Name: | LastRefreshAttempted |
Value: BFD990922DB4DB01 | |||
| (PID) Process: | (5496) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Wosc\Client\Persistent\ClientState\WOSC |
| Operation: | write | Name: | RefreshInterval |
Value: 1701 | |||
| (PID) Process: | (5496) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Wosc\Client\Persistent\ClientState\WOSC |
| Operation: | write | Name: | LastHTTPCode |
Value: 200 | |||
| (PID) Process: | (5496) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Wosc\Client\Persistent\ClientState\WOSC |
| Operation: | write | Name: | LastDeviceTokenResult |
Value: 1 | |||
| (PID) Process: | (5496) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Wosc\Client\Persistent\ClientState\WOSC |
| Operation: | write | Name: | LastUserTokenResult |
Value: 1 | |||
| (PID) Process: | (5496) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Wosc\Client\Persistent\ClientState\WOSC |
| Operation: | write | Name: | QueryStringHash |
Value: 74C8F926B48B2C7F3F0B19028BD837D06E41450B9845AF41EE57A682BEFD25BE | |||
| (PID) Process: | (5496) MoUsoCoreWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Wosc\Client\Persistent\ClientState\WOSC |
| Operation: | delete value | Name: | Version |
Value: | |||
Executable files
4
Suspicious files
174
Text files
47
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c8a1.TMP | — | |
MD5:— | SHA256:— | |||
| 4880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10c8a1.TMP | — | |
MD5:— | SHA256:— | |||
| 4880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10c8a1.TMP | — | |
MD5:— | SHA256:— | |||
| 4880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10c8a1.TMP | — | |
MD5:— | SHA256:— | |||
| 4880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10c8c0.TMP | — | |
MD5:— | SHA256:— | |||
| 4880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
323
DNS requests
380
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1132 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1132 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7956 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adp7lmscefogeldj4te6xerqth3a_9.55.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.55.0_all_ocm7dvbavb37zglvqhfr5kszse.crx3 | unknown | — | — | whitelisted |
7956 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adp7lmscefogeldj4te6xerqth3a_9.55.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.55.0_all_ocm7dvbavb37zglvqhfr5kszse.crx3 | unknown | — | — | whitelisted |
7956 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adp7lmscefogeldj4te6xerqth3a_9.55.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.55.0_all_ocm7dvbavb37zglvqhfr5kszse.crx3 | unknown | — | — | whitelisted |
7956 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adp7lmscefogeldj4te6xerqth3a_9.55.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.55.0_all_ocm7dvbavb37zglvqhfr5kszse.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4880 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7328 | chrome.exe | 104.17.151.117:443 | www.mediafire.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.mediafire.com |
| whitelisted |
accounts.google.com |
| whitelisted |
the.gatekeeperconsent.com |
| unknown |
www.googletagmanager.com |
| whitelisted |
static.mediafire.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7328 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
7328 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
7328 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7328 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7328 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
7328 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
7328 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7328 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7328 | chrome.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
7328 | chrome.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |