| URL: | https://riapl.com/eleven/go.php?auth=d3af1d4a0b2977bd10ee467bf2bc5b46dde7805d82eb96ccaa |
| Full analysis: | https://app.any.run/tasks/cad9bee5-5b2f-44ed-8d76-8df863a9d2fb |
| Verdict: | Malicious activity |
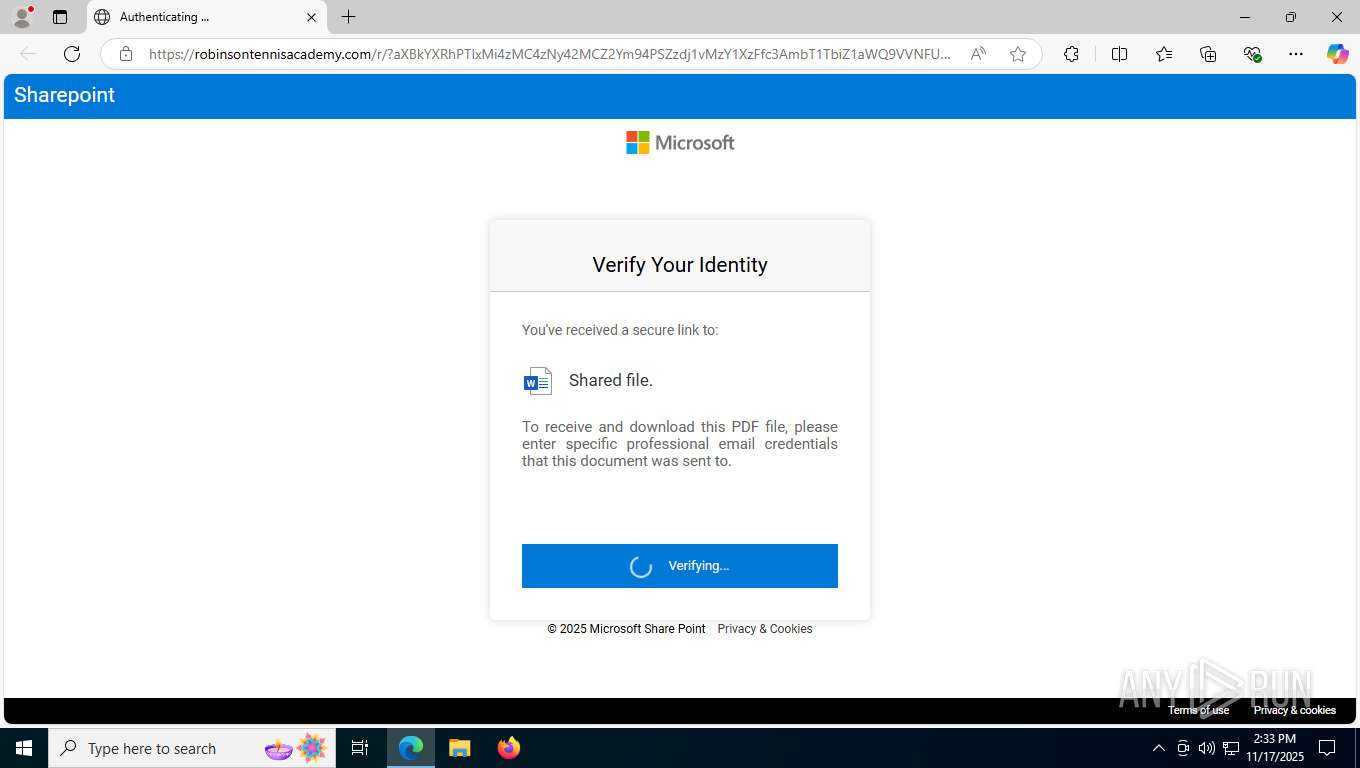
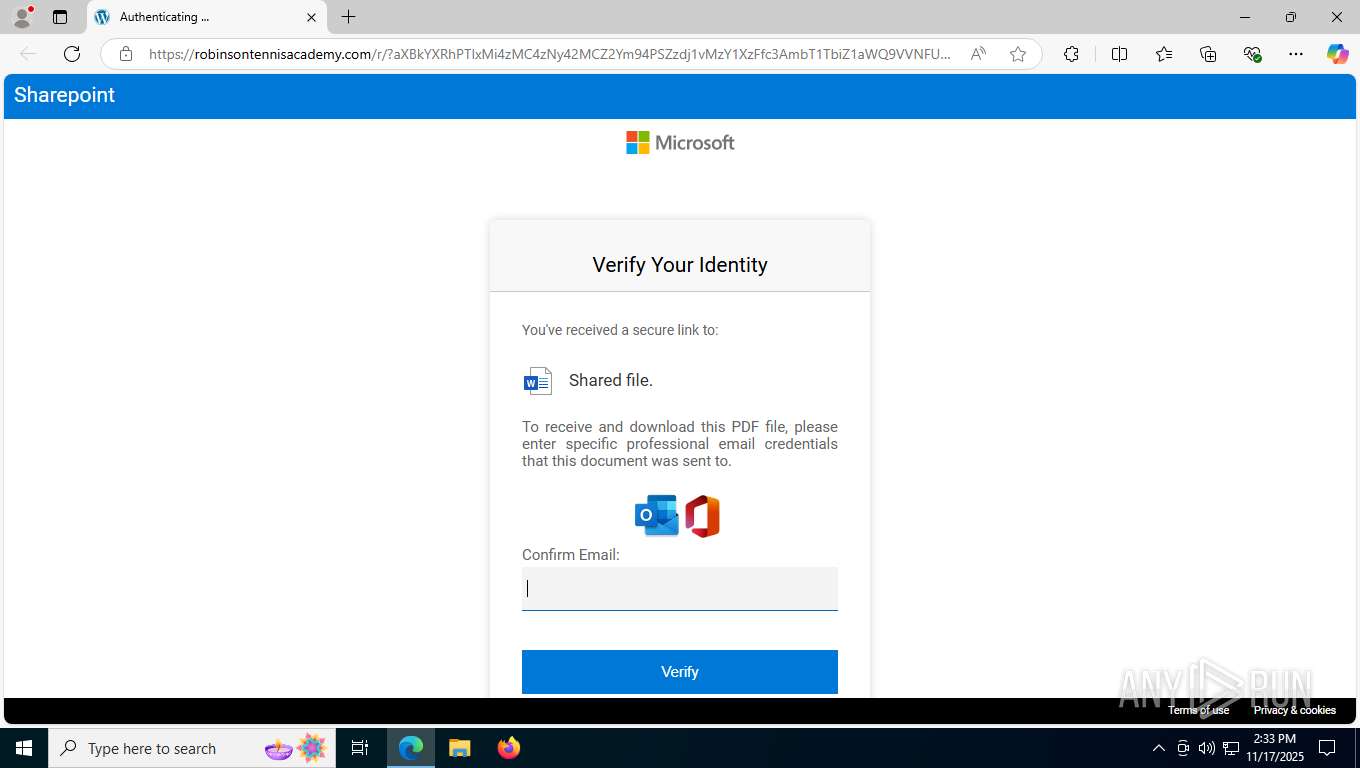
| Threats: | Mamba 2FA is an advanced phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) and target Microsoft 365 accounts. It focuses on intercepting authentication flows in real-time and enables threat actors to hijack user sessions and access sensitive systems even when additional security measures are in place. |
| Analysis date: | November 17, 2025, 14:33:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0F5FA8E758315B56A8D6AD22C5079E75 |
| SHA1: | AFB9C5239052A15382704182BF9B241468D54511 |
| SHA256: | D84CD968322ABFFD32DE978C44CB4E8AE58D219D14D0A88EAF7F39FE64CAB6EF |
| SSDEEP: | 3:N8mKIKAOTASNwyWEDYiVHXvAAYTn13ASdVQrLn:293AOTB7DVVHXty13AuVEL |
MALICIOUS
PHISHING has been detected (ML)
- msedge.exe (PID: 6980)
Mamba 2FA phishing kit has been detected
- msedge.exe (PID: 6980)
Fake Microsoft Authentication Page has been detected
- msedge.exe (PID: 6980)
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 2060)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- msedge.exe (PID: 6980)
Checks supported languages
- identity_helper.exe (PID: 8028)
Page contains obfuscated JavaScript
- msedge.exe (PID: 6980)
Reads Environment values
- identity_helper.exe (PID: 8028)
Reads the computer name
- identity_helper.exe (PID: 8028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
169
Monitored processes
21
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2060 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2220,i,10378928413719378828,15188821249279357176,262144 --variations-seed-version --mojo-platform-channel-handle=2480 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3120 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=6792,i,10378928413719378828,15188821249279357176,262144 --variations-seed-version --mojo-platform-channel-handle=6784 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3988 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=7040,i,10378928413719378828,15188821249279357176,262144 --variations-seed-version --mojo-platform-channel-handle=6236 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 4084 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2524,i,10378928413719378828,15188821249279357176,262144 --variations-seed-version --mojo-platform-channel-handle=2784 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 4868 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2232,i,10378928413719378828,15188821249279357176,262144 --variations-seed-version --mojo-platform-channel-handle=2228 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 5284 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=4400,i,10378928413719378828,15188821249279357176,262144 --variations-seed-version --mojo-platform-channel-handle=1520 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 5892 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x308,0x30c,0x310,0x304,0x318,0x7fff77ebf208,0x7fff77ebf214,0x7fff77ebf220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 6380 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=1312,i,10378928413719378828,15188821249279357176,262144 --variations-seed-version --mojo-platform-channel-handle=5532 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 6980 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" "https://riapl.com/eleven/go.php?auth=d3af1d4a0b2977bd10ee467bf2bc5b46dde7805d82eb96ccaa" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 7312 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=3 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=2016,i,10378928413719378828,15188821249279357176,262144 --variations-seed-version --mojo-platform-channel-handle=3668 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
587
Read events
587
Write events
0
Delete events
0
Modification events
Executable files
6
Suspicious files
75
Text files
40
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6980 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF161d41.TMP | — | |
MD5:— | SHA256:— | |||
| 6980 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6980 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF161d50.TMP | — | |
MD5:— | SHA256:— | |||
| 6980 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6980 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF161d50.TMP | — | |
MD5:— | SHA256:— | |||
| 6980 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF161d50.TMP | — | |
MD5:— | SHA256:— | |||
| 6980 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF161d50.TMP | — | |
MD5:— | SHA256:— | |||
| 6980 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6980 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6980 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
79
DNS requests
82
Threats
29
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2060 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:sqoRpmhMA4NiEAWwU5nHBX_Yvrx9n0cO7EIQzT7xlTg&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
3500 | svchost.exe | GET | 200 | 172.66.2.5:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2792 | svchost.exe | GET | 200 | 95.101.35.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5912 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5912 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.3.crl | unknown | — | — | whitelisted |
5912 | SIHClient.exe | GET | 200 | 2.19.126.146:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5912 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | — | — | whitelisted |
5912 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.3.crl | unknown | — | — | whitelisted |
5912 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
5912 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2792 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5596 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6312 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2060 | msedge.exe | 150.171.28.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2060 | msedge.exe | 150.171.22.17:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2060 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2060 | msedge.exe | 2.16.110.194:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
2060 | msedge.exe | 92.119.156.26:443 | riapl.com | APEIRON GLOBAL Pvt. Ltd. | NL | unknown |
2060 | msedge.exe | 2.16.241.227:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
riapl.com |
| unknown |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
xpaywalletcdn.azureedge.net |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgeassetservice.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2060 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain identified as Mamba2FA (robinsontennisacademy .com) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Mamba2FA HTTP URL Observed (sv= b64-encoded) |
— | — | Attempted Information Leak | PHISHING [ANY.RUN] Browser Fingerprinting related to Phishing Kits observed |
— | — | Possible Social Engineering Attempted | ET PHISHING Javascript Browser Fingerprinting POST Request |
— | — | Information Leak | SUSPICIOUS [ANY.RUN] FingerprintJS Collected Data observed in HTTP POST request |
— | — | Attempted Information Leak | PHISHING [ANY.RUN] Browser Fingerprinting related to Phishing Kits observed |
— | — | Information Leak | SUSPICIOUS [ANY.RUN] FingerprintJS Collected Data observed in HTTP POST request |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Mamba2FA HTTP URL Observed (ipdata= b64-encoded) |
— | — | Possible Social Engineering Attempted | ET PHISHING Javascript Browser Fingerprinting POST Request |
2060 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Bidirectional and low-latency communication CDN (cdn .socket .io) |