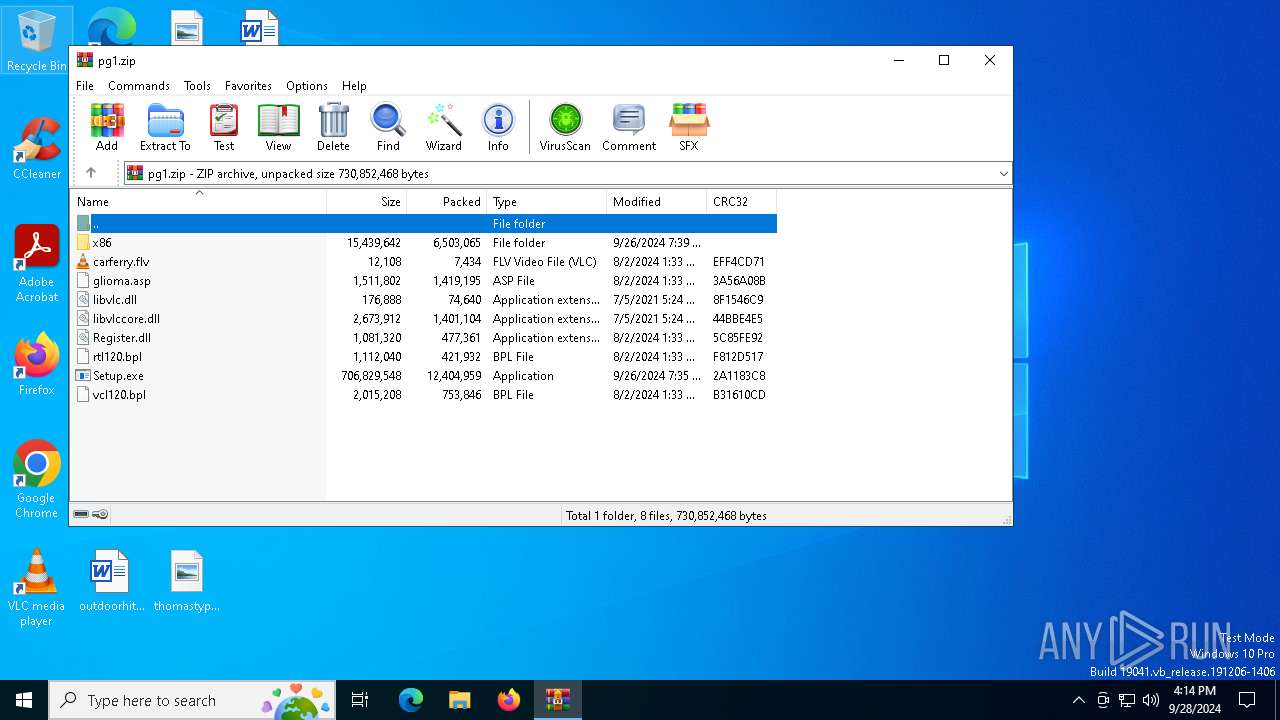
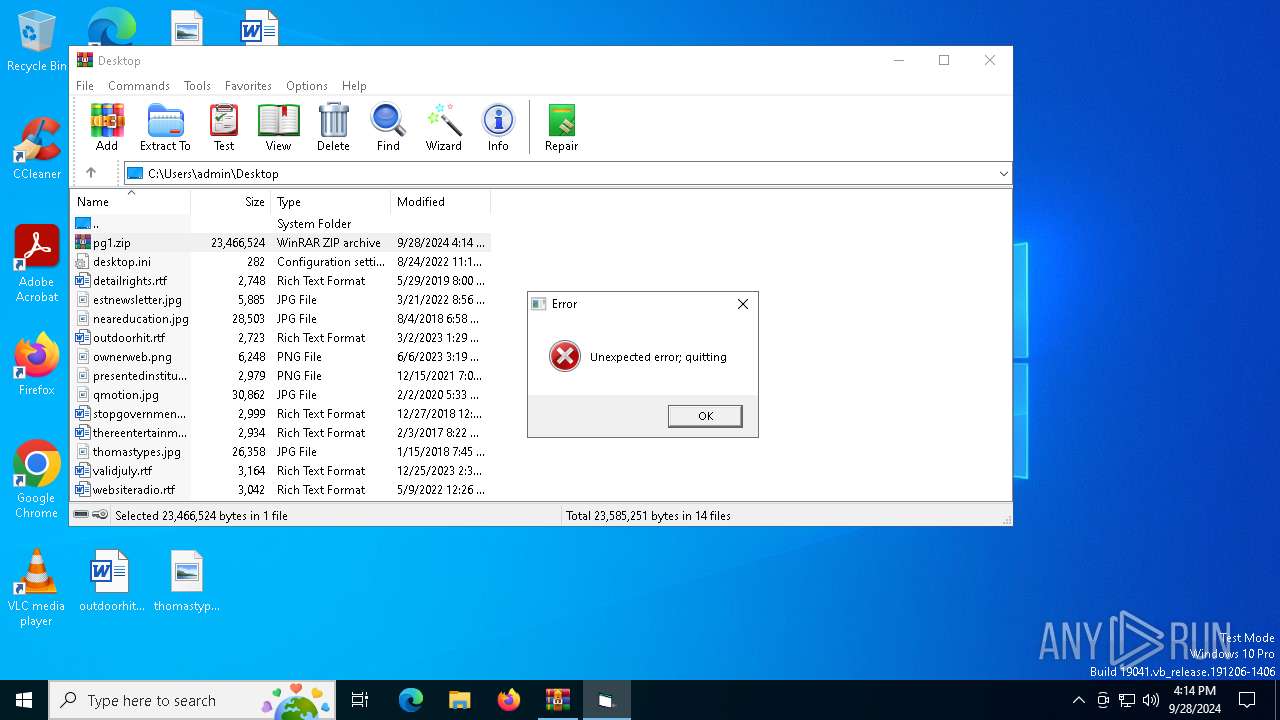
| File name: | pg1.zip |
| Full analysis: | https://app.any.run/tasks/c47c9006-c4c5-4420-a158-dac8c2e37b4f |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | September 28, 2024, 16:14:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 5703B0EAA4147BCA1CC42EB520CECD94 |
| SHA1: | 81A96BD47FCFCE4B5378221BDAA8308B6F3B9C40 |
| SHA256: | D823025626DF8A35A733A3FE144CBC3059E69C0CA09513490F7B894B72E0DF4B |
| SSDEEP: | 98304:ryTfawzTXANteAg36KDn897Gik6YkZAdiAMbb2KnyX1eUHauJStL/9QRK+45QUB8:uqc+3AWzixTmER6fqDXATiQgIN+a8rmU |
MALICIOUS
LUMMA has been detected (YARA)
- SearchIndexer.exe (PID: 2424)
- SearchIndexer.exe (PID: 4412)
Stealers network behavior
- SearchIndexer.exe (PID: 2424)
- SearchIndexer.exe (PID: 4412)
LUMMA has been detected (SURICATA)
- SearchIndexer.exe (PID: 2424)
- SearchIndexer.exe (PID: 4412)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6308)
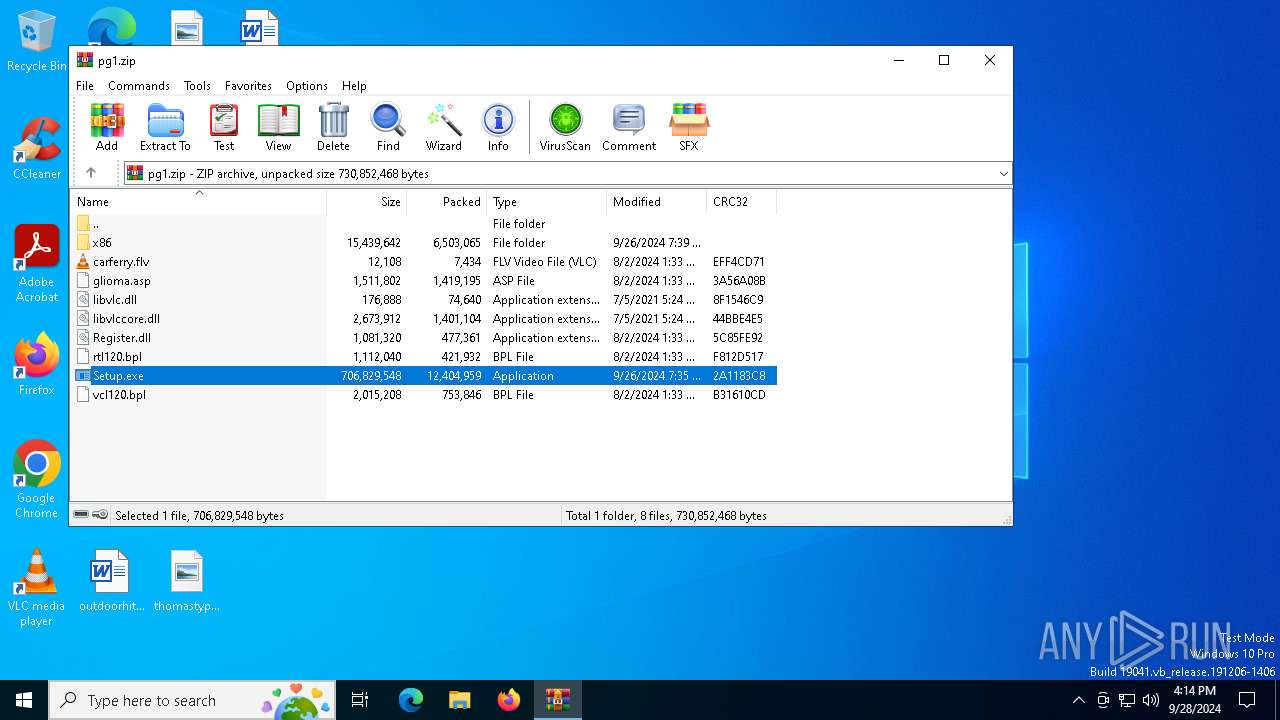
Executable content was dropped or overwritten
- Setup.exe (PID: 1636)
Starts application with an unusual extension
- Setup.exe (PID: 1636)
- Setup.exe (PID: 1928)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6308)
- WinRAR.exe (PID: 3584)
- WinRAR.exe (PID: 5664)
The process uses the downloaded file
- WinRAR.exe (PID: 6308)
- WinRAR.exe (PID: 3584)
- WinRAR.exe (PID: 5664)
Reads the computer name
- Setup.exe (PID: 1636)
- StrCmp.exe (PID: 4128)
- more.com (PID: 5908)
- Setup.exe (PID: 1928)
- more.com (PID: 6216)
- Setup.exe (PID: 5128)
Checks supported languages
- Setup.exe (PID: 1636)
- StrCmp.exe (PID: 4128)
- more.com (PID: 5908)
- Setup.exe (PID: 1928)
- more.com (PID: 6216)
- Setup.exe (PID: 5128)
Creates files or folders in the user directory
- Setup.exe (PID: 1636)
Create files in a temporary directory
- Setup.exe (PID: 1636)
- more.com (PID: 5908)
- more.com (PID: 6216)
- Setup.exe (PID: 5128)
- Setup.exe (PID: 1928)
Manual execution by a user
- WinRAR.exe (PID: 3584)
- Setup.exe (PID: 1928)
- WinRAR.exe (PID: 5664)
- Setup.exe (PID: 5128)
Reads the software policy settings
- SearchIndexer.exe (PID: 4412)
- SearchIndexer.exe (PID: 2424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:02 06:33:10 |
| ZipCRC: | 0xeff4cd71 |
| ZipCompressedSize: | 7434 |
| ZipUncompressedSize: | 12108 |
| ZipFileName: | carferry.flv |
Total processes
139
Monitored processes
13
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1636 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.39087\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.39087\Setup.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: pdUpdater Exit code: 1 Version: 17.0.0.0 Modules
| |||||||||||||||
| 1928 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: pdUpdater Exit code: 1 Version: 17.0.0.0 Modules
| |||||||||||||||
| 2424 | C:\WINDOWS\SysWOW64\SearchIndexer.exe | C:\Windows\SysWOW64\SearchIndexer.exe | more.com | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Indexer Exit code: 0 Version: 7.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3256 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3584 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\pg1.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4108 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4128 | C:\Users\admin\AppData\Roaming\mtls\CCRLJALMZLDQAJOZJVP\StrCmp.exe | C:\Users\admin\AppData\Roaming\mtls\CCRLJALMZLDQAJOZJVP\StrCmp.exe | — | Setup.exe | |||||||||||
User: admin Company: aaa Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 4412 | C:\WINDOWS\SysWOW64\SearchIndexer.exe | C:\Windows\SysWOW64\SearchIndexer.exe | more.com | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Indexer Exit code: 0 Version: 7.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5128 | "C:\Users\admin\Desktop\pg1\Setup.exe" | C:\Users\admin\Desktop\pg1\Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: pdUpdater Exit code: 0 Version: 17.0.0.0 Modules
| |||||||||||||||
| 5664 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\pg1.zip" C:\Users\admin\Desktop\pg1\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
10 497
Read events
10 477
Write events
20
Delete events
0
Modification events
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\pg1.zip | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
43
Suspicious files
11
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.39087\Setup.exe | — | |
MD5:— | SHA256:— | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.39087\libvlccore.dll | executable | |
MD5:E25413BB41C2F239FFDD3569F76E74B0 | SHA256:9126D9ABF91585456000FFFD9336478E91B9EA07ED2A25806A4E2E0437F96D29 | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.39087\x86\BIBUtils.dll | executable | |
MD5:79622B56347C1FD44B74BD4EA74CB813 | SHA256:0F2B3D012A9ABE420BC36C62847BBA6CA4478CEEBC018BAD2B19F22D481FCC10 | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.39087\carferry.flv | binary | |
MD5:16A30926E4EBC495D3659854C3731F63 | SHA256:DC260B93C358E10FC6F74C0B9F487DD0C2FD58E791EC5B0925B0546258923B36 | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.39087\Register.dll | executable | |
MD5:40B9628354EF4E6EF3C87934575545F4 | SHA256:372B14FCE2EB35B264F6D4AEEF7987DA56D951D3A09EF866CF55ED72763CAA12 | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.39087\libvlc.dll | executable | |
MD5:96214B94B796BFFC48D63289854AE5A2 | SHA256:528C416CFB4813EE5F1DA52743EF4ADB20043171230098B27E25D1DD90E3F288 | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.39087\x86\AIDE.dll | executable | |
MD5:AD388CE4C2CC3AAFF605994DA782D57E | SHA256:D3BA1ADBFEEF8F19E4AA570299C06D39A87DFC5FE3D85946270B722E44DACDA7 | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.39087\x86\Acrobat\Acrobat32OL.dll | executable | |
MD5:18E5A6296E02EFB842FB3D11CA0C7C63 | SHA256:629B4CEF2C394C6A1FAD37E5AC6F497B3BDAC489270D54F4E98C5DFC925EA883 | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.39087\x86\ACE.dll | executable | |
MD5:D0AE82CDF9911BEC3EDDDA128602AF04 | SHA256:F9675304D13EFAEE32E6B4A3317B64231A59B684532A898D12B4E7ED88518AFD | |||
| 5908 | more.com | C:\Users\admin\AppData\Local\Temp\uqvyfphgyfun | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
54
TCP/UDP connections
69
DNS requests
16
Threats
23
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 4.175.87.197:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 4.175.87.197:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
— | — | POST | 200 | 188.114.97.3:443 | https://swipedbakkwo.shop/api | unknown | — | — | malicious |
— | — | POST | 200 | 188.114.97.3:443 | https://swipedbakkwo.shop/api | unknown | text | 18 b | malicious |
— | — | POST | 200 | 188.114.97.3:443 | https://swipedbakkwo.shop/api | unknown | — | — | malicious |
— | — | POST | 200 | 188.114.97.3:443 | https://swipedbakkwo.shop/api | unknown | text | 18 b | malicious |
— | — | POST | 200 | 188.114.97.3:443 | https://swipedbakkwo.shop/api | unknown | text | 18 b | malicious |
— | — | POST | 200 | 188.114.97.3:443 | https://swipedbakkwo.shop/api | unknown | text | 48 b | malicious |
— | — | POST | 200 | 188.114.97.3:443 | https://swipedbakkwo.shop/api | unknown | html | 4.29 Kb | malicious |
— | — | POST | 200 | 188.114.97.3:443 | https://swipedbakkwo.shop/api | unknown | text | 18 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7108 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2424 | SearchIndexer.exe | 188.114.97.3:443 | swipedbakkwo.shop | CLOUDFLARENET | NL | unknown |
4412 | SearchIndexer.exe | 188.114.97.3:443 | swipedbakkwo.shop | CLOUDFLARENET | NL | unknown |
2384 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2384 | SIHClient.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2384 | SIHClient.exe | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
swipedbakkwo.shop |
| malicious |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2424 | SearchIndexer.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer Related Activity |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer CnC Host Checkin |
— | — | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Win32/Lumma Stealer Check-In |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer Related Activity M2 |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer CnC Host Checkin |
— | — | Malware Command and Control Activity Detected | ET MALWARE [ANY.RUN] Win32/Lumma Stealer Exfiltration |
— | — | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Win32/Lumma Stealer Exfiltration |
— | — | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Win32/Lumma Stealer Check-In |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer CnC Host Checkin |
3 ETPRO signatures available at the full report