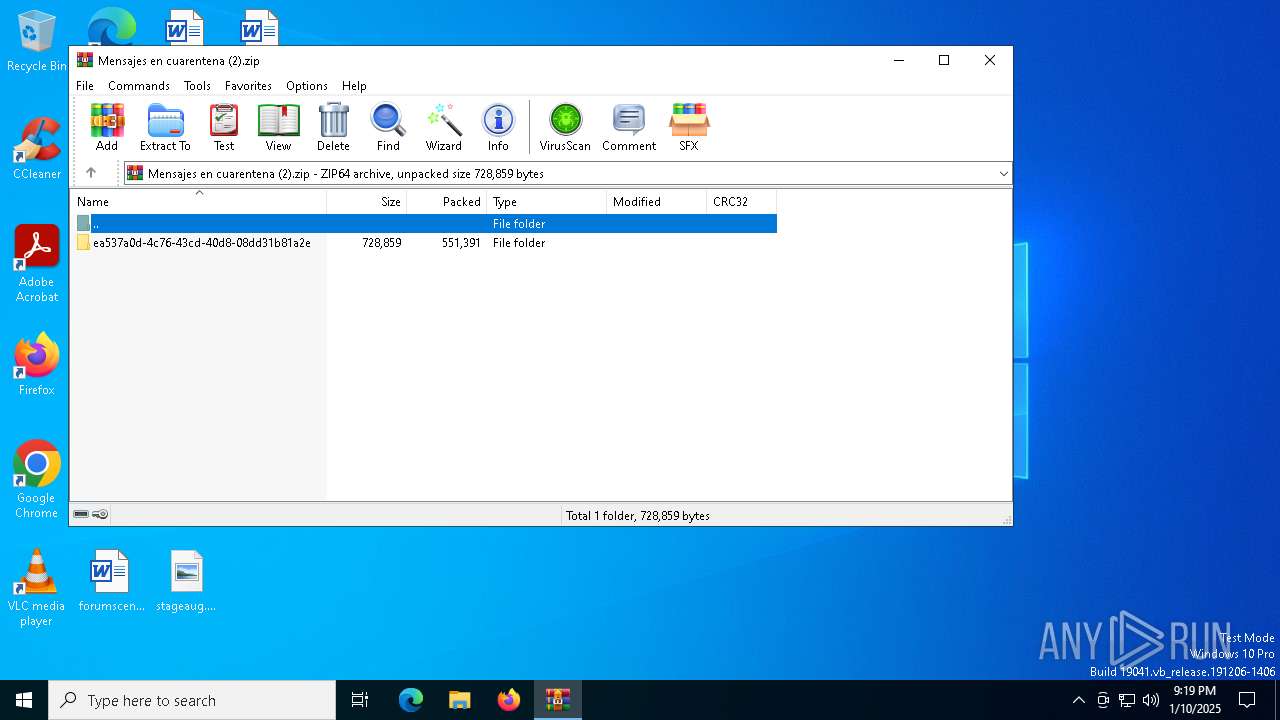
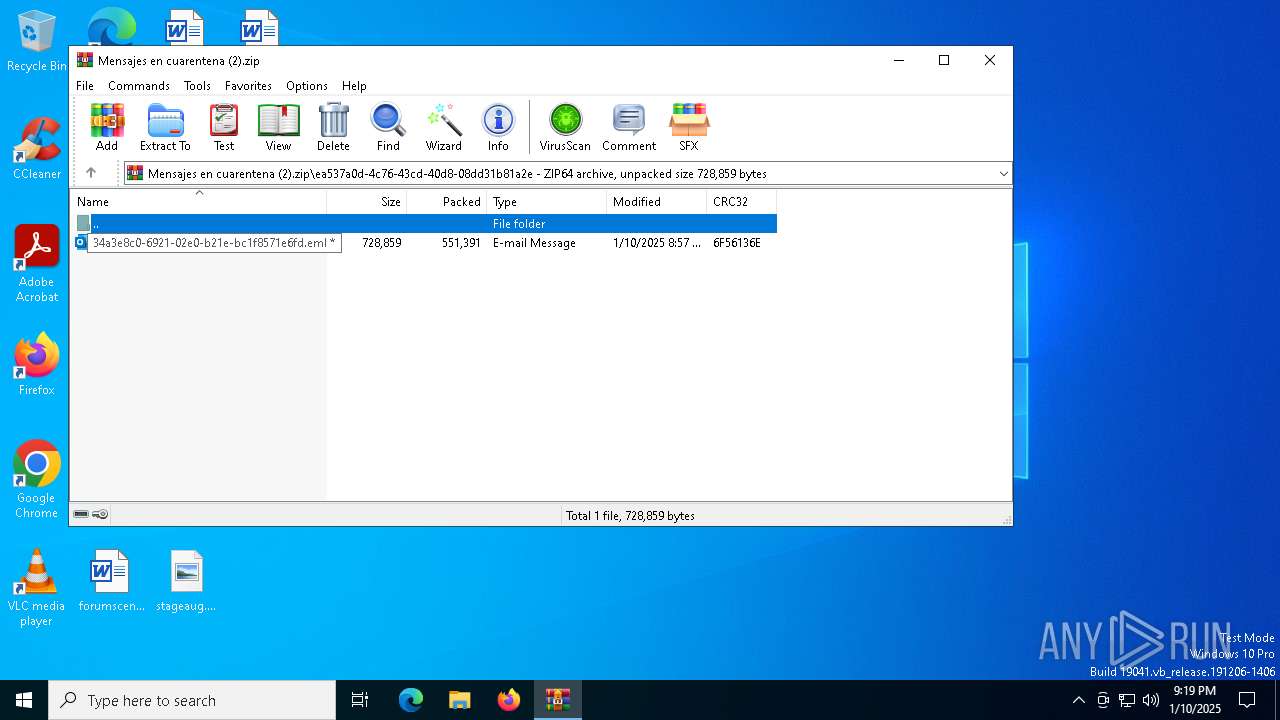
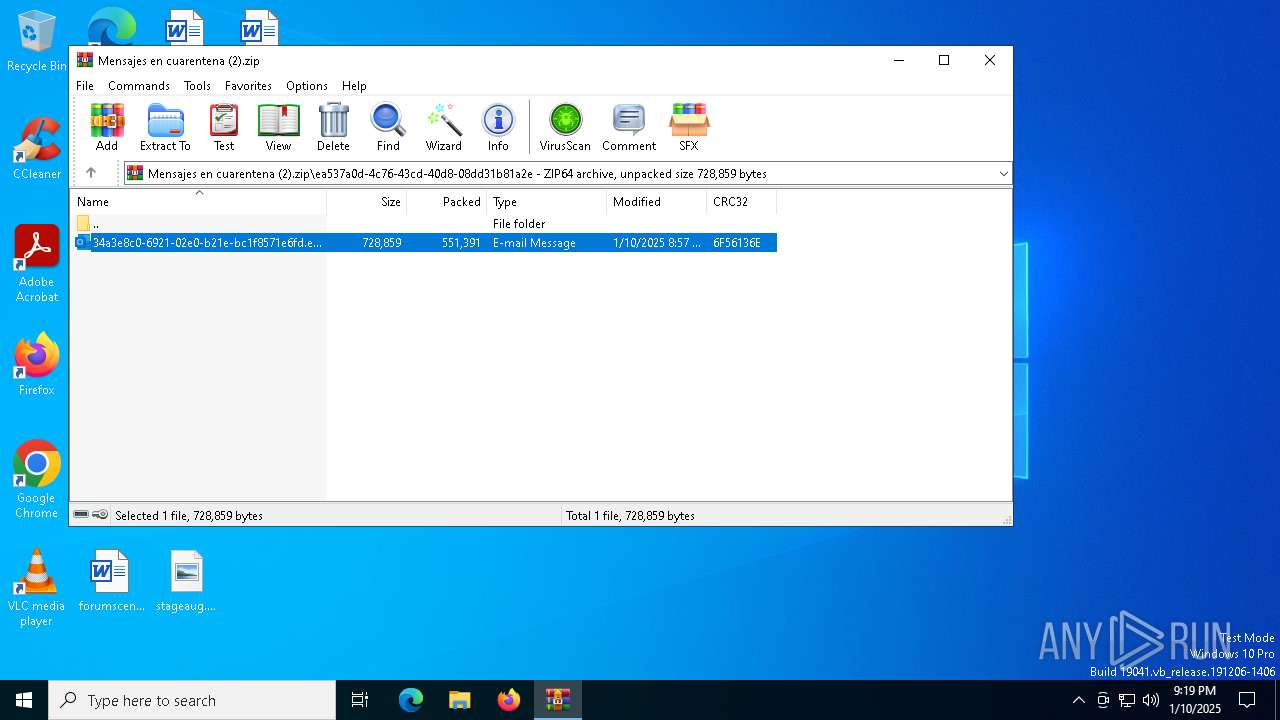
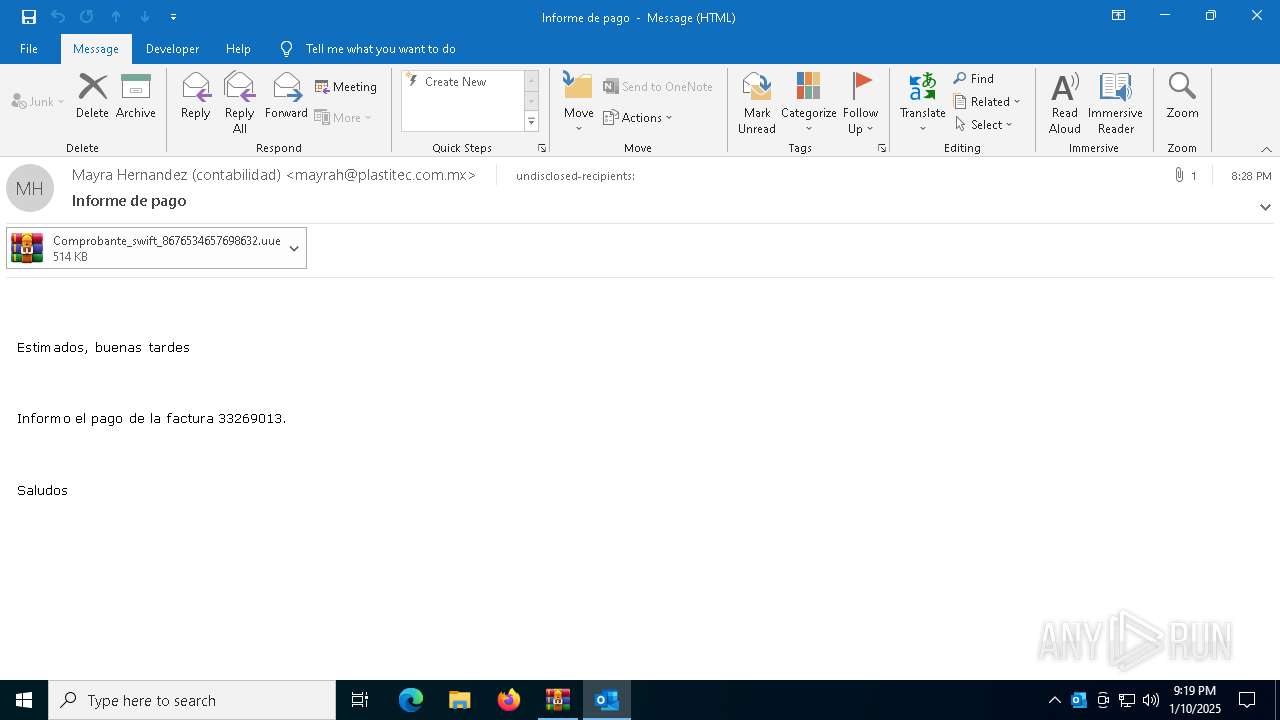
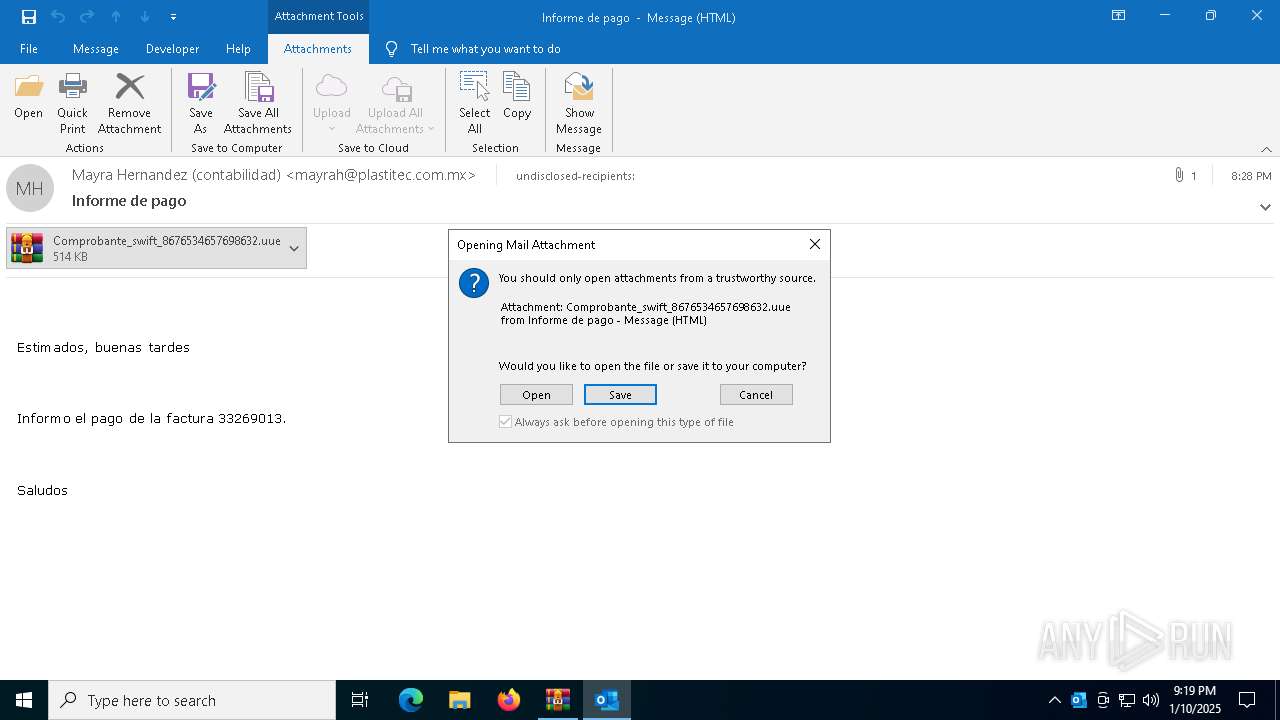
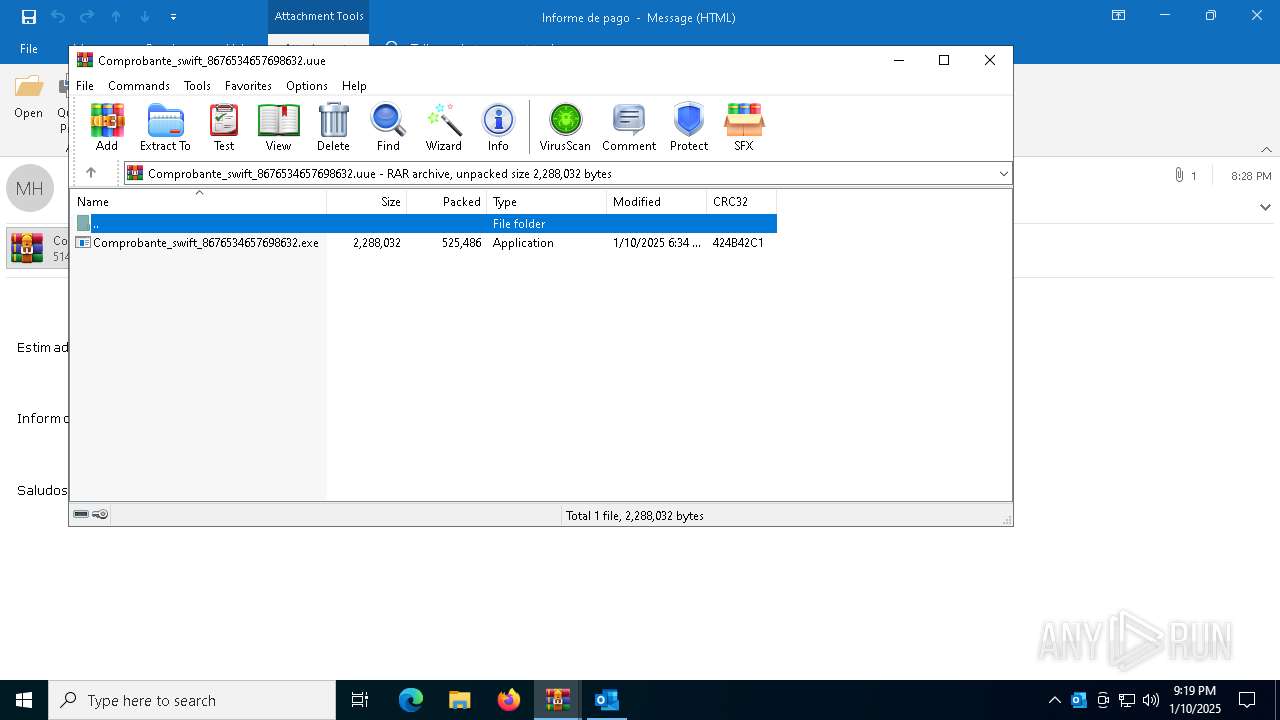
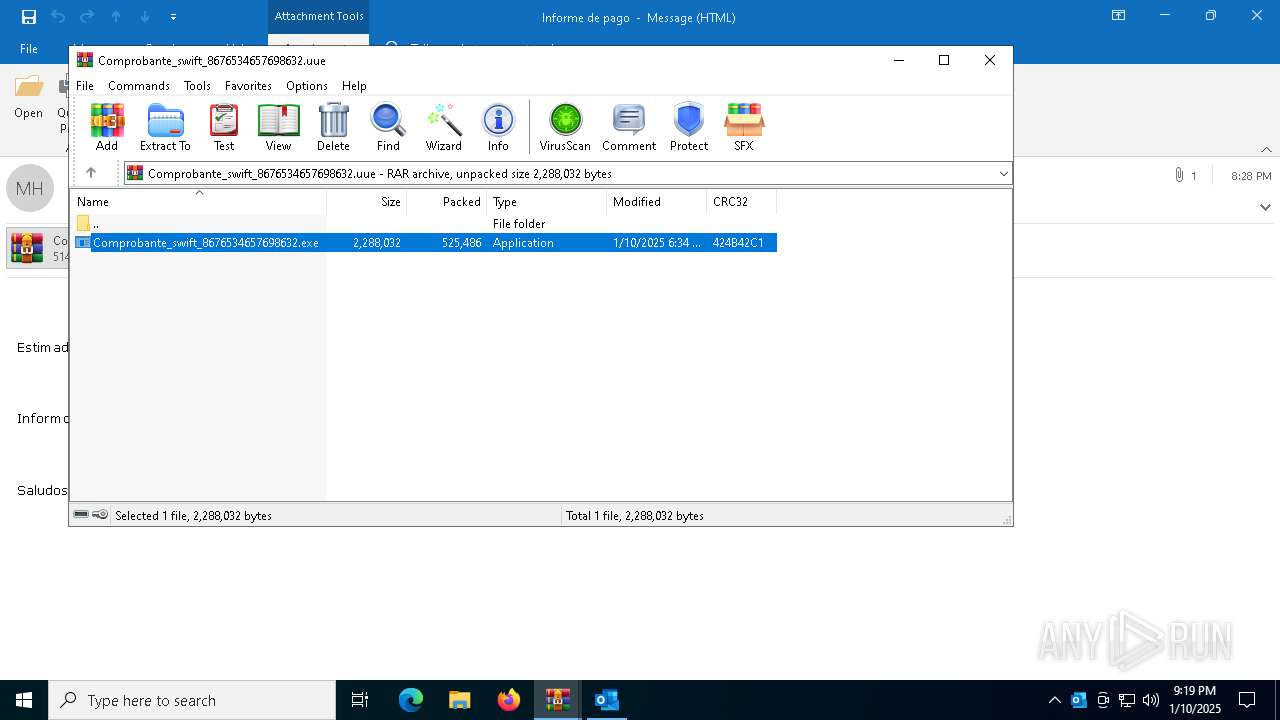
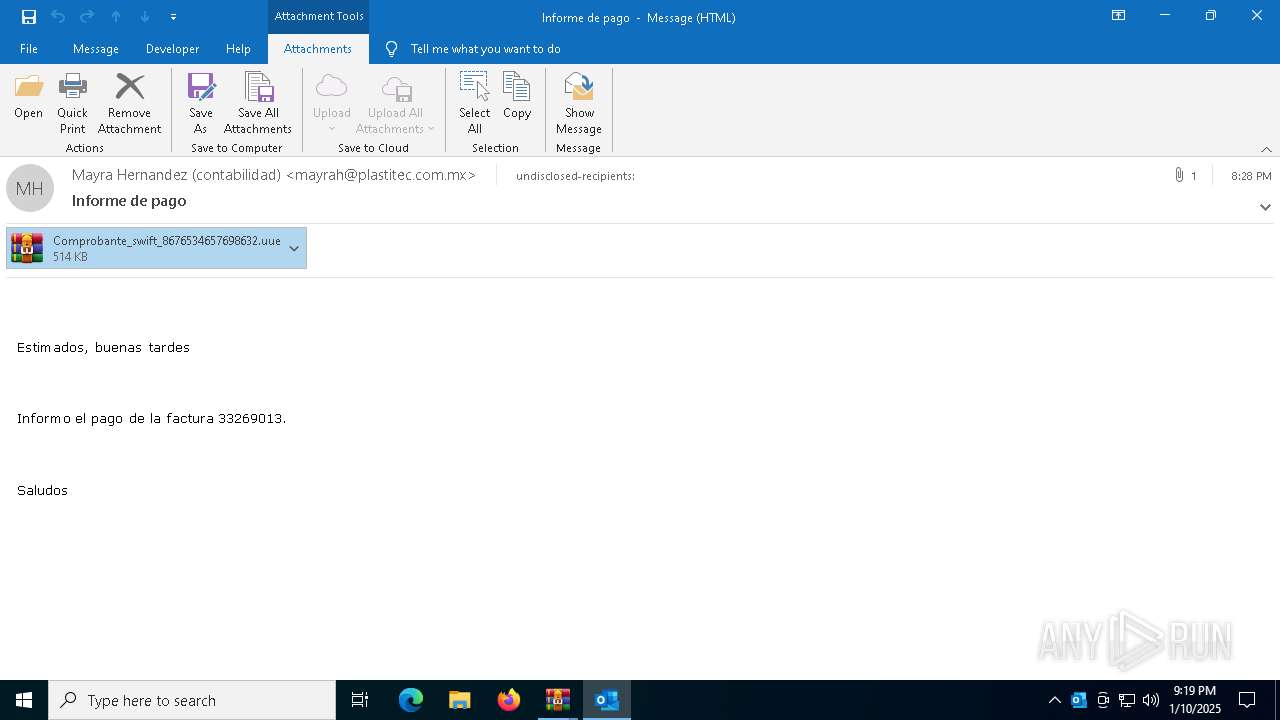
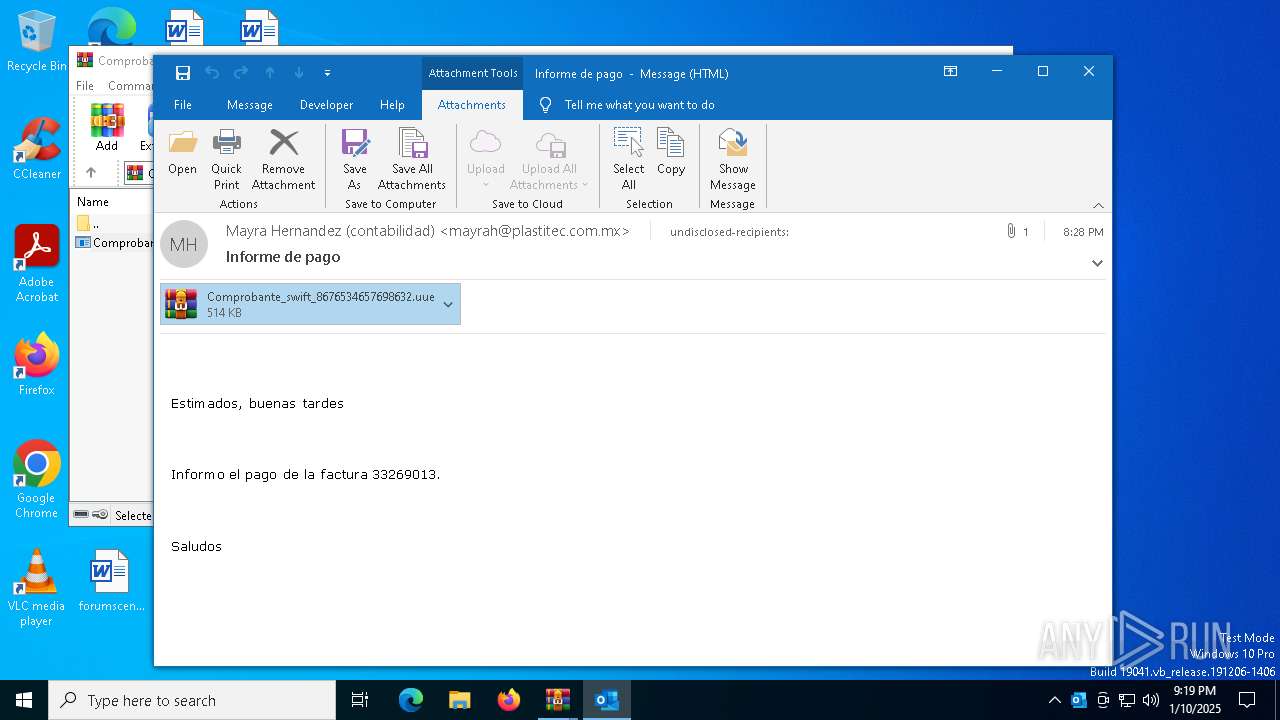
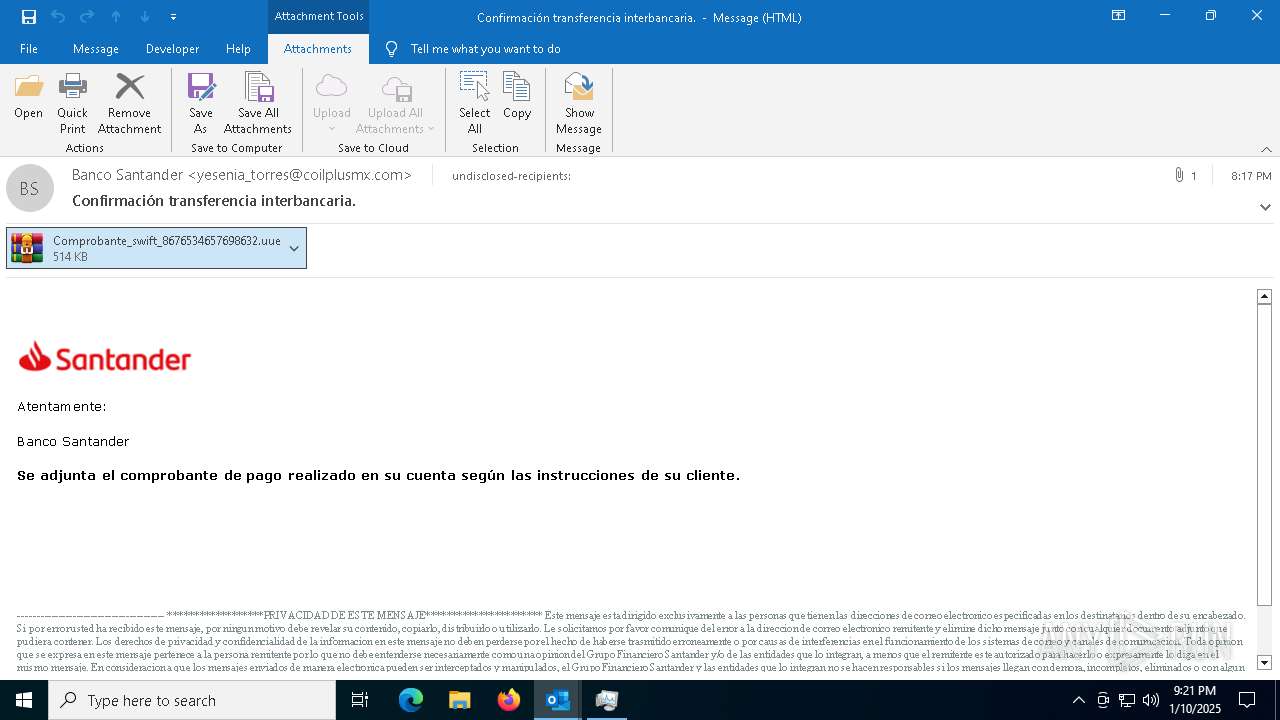
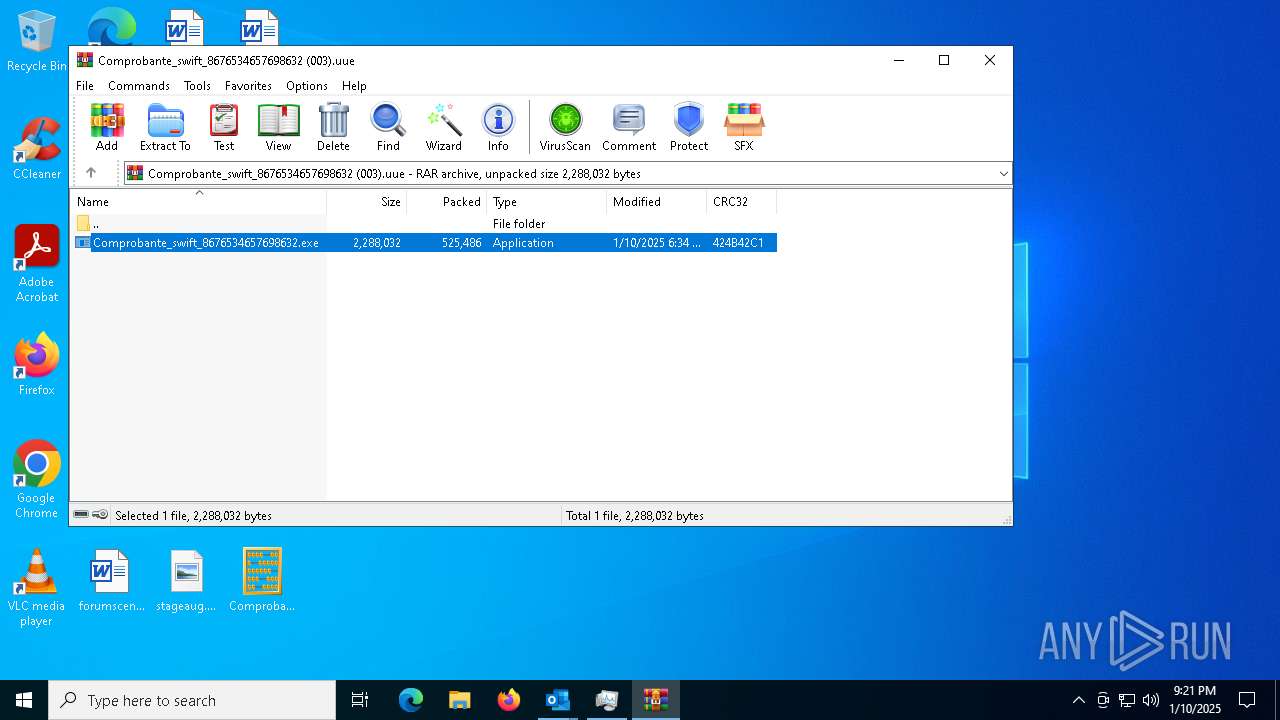
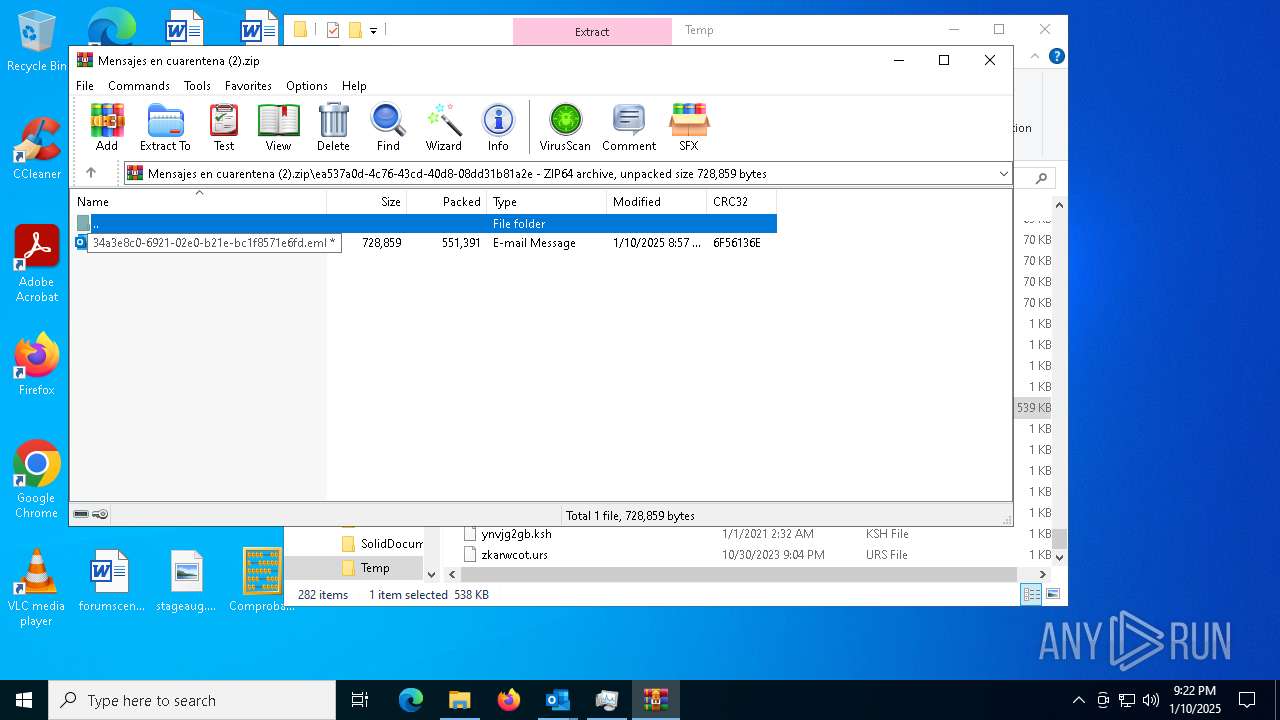
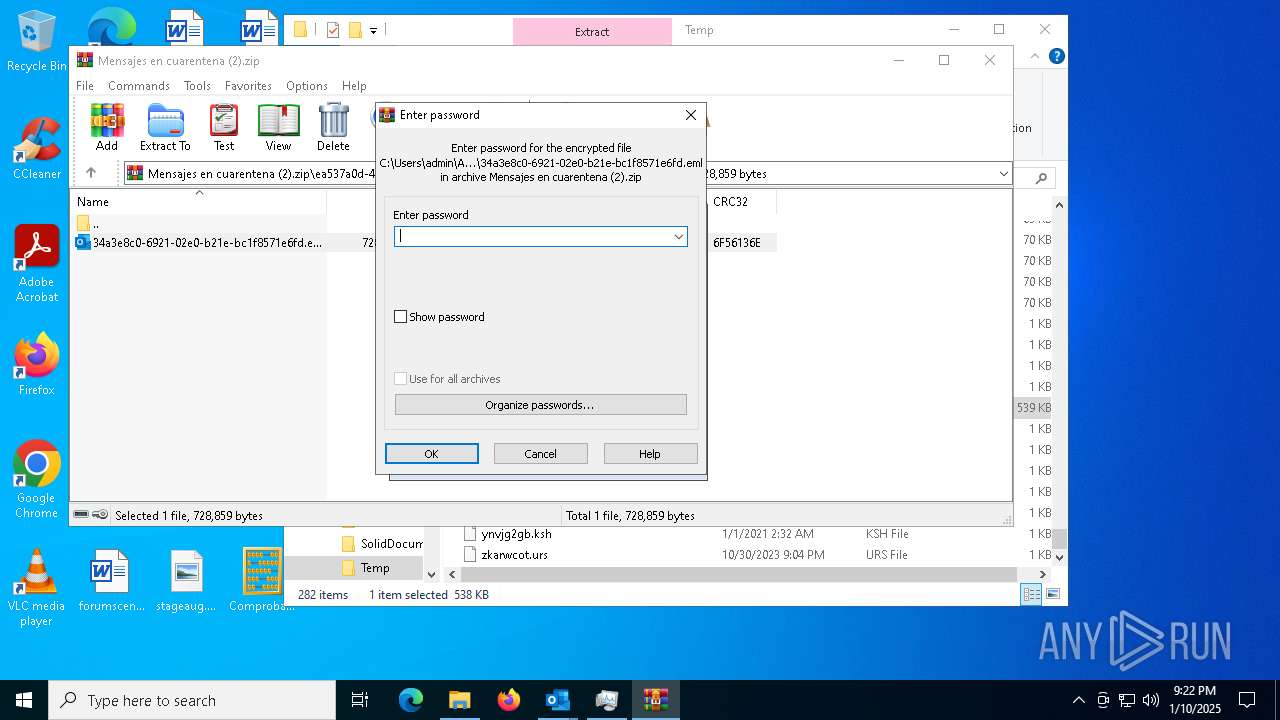
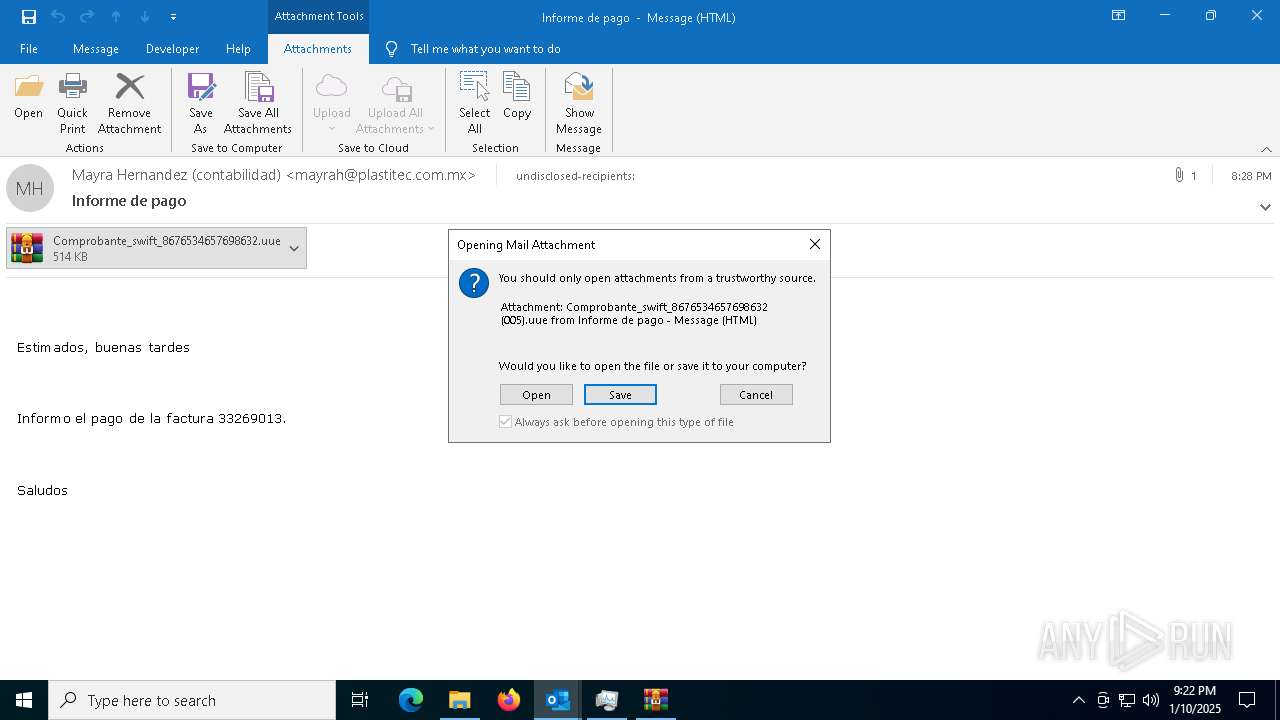
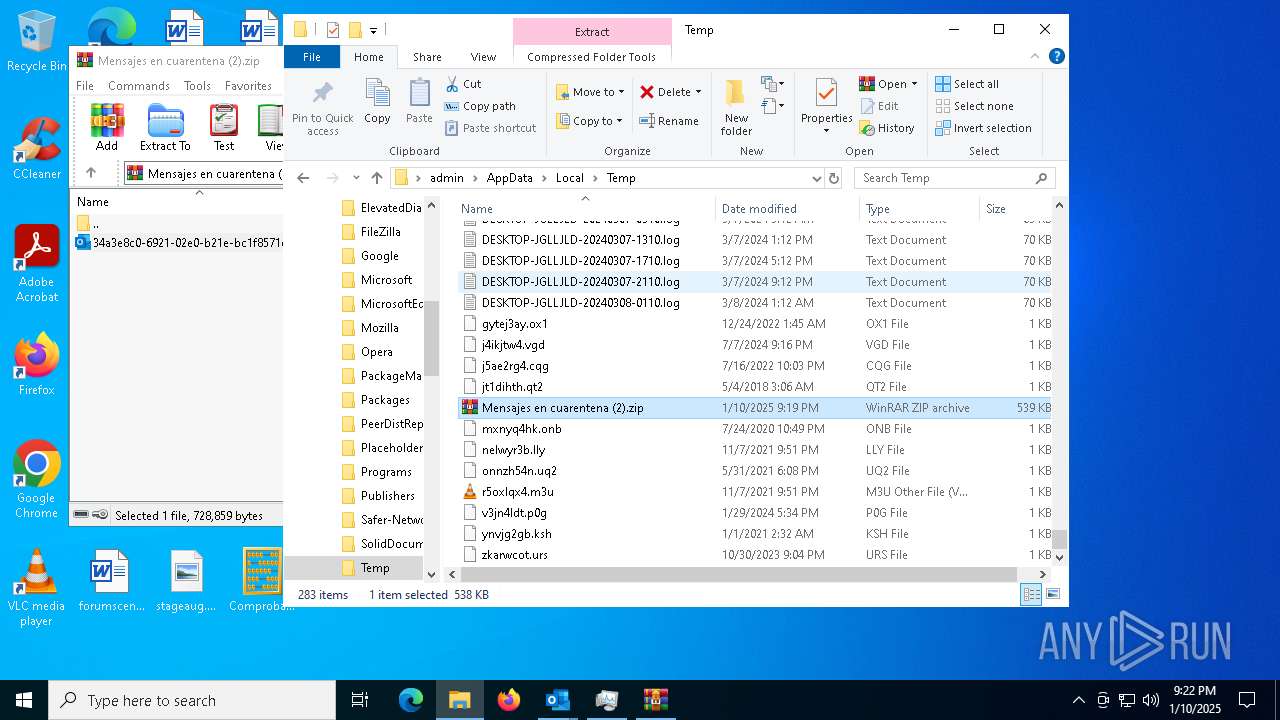
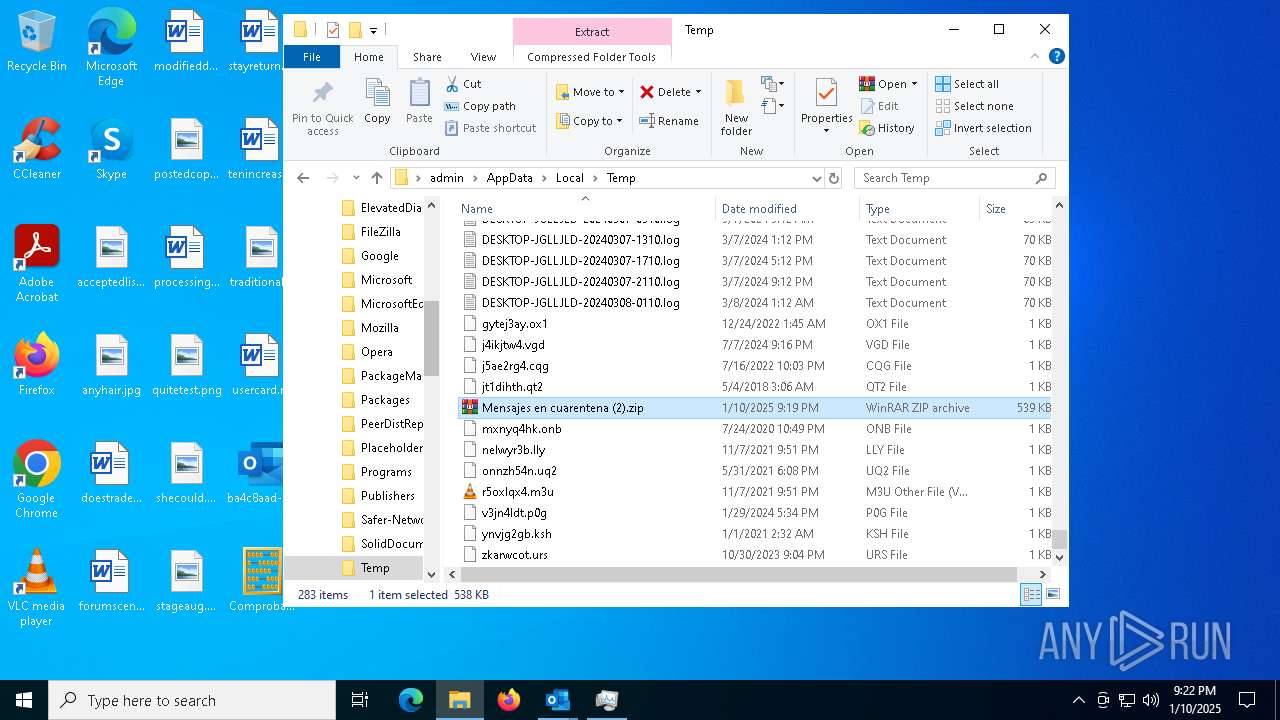
| File name: | Mensajes en cuarentena (2).zip |
| Full analysis: | https://app.any.run/tasks/dfbaac18-6ccc-440f-a57e-f247d884f5e5 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | January 10, 2025, 21:18:56 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | E59D7DA9EA3112DF8D097A3DC75CBBA5 |
| SHA1: | ADB0F354A75BE0ABAC24A2E5E7EEF399EA1DB71B |
| SHA256: | D7F7DF47472593076077B7052725B8440A32637BC54FB8AFAB9FE3868C50A443 |
| SSDEEP: | 24576:WXoPVvDWrFUL15HhiNkBZhy2w+eL6THb4FgCM4FHs8URzVgz2:WXoPVvDWrFUL15HhiNaZhy2w+eL6THbB |
MALICIOUS
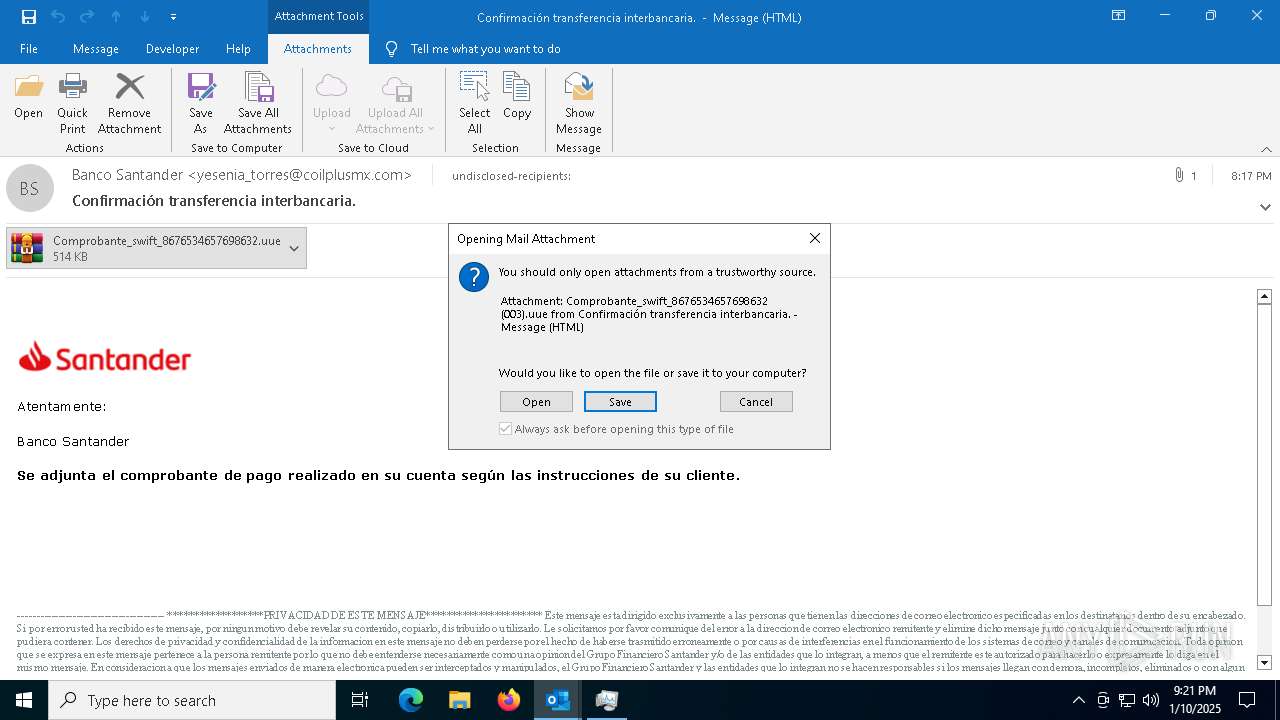
Executing a file with an untrusted certificate
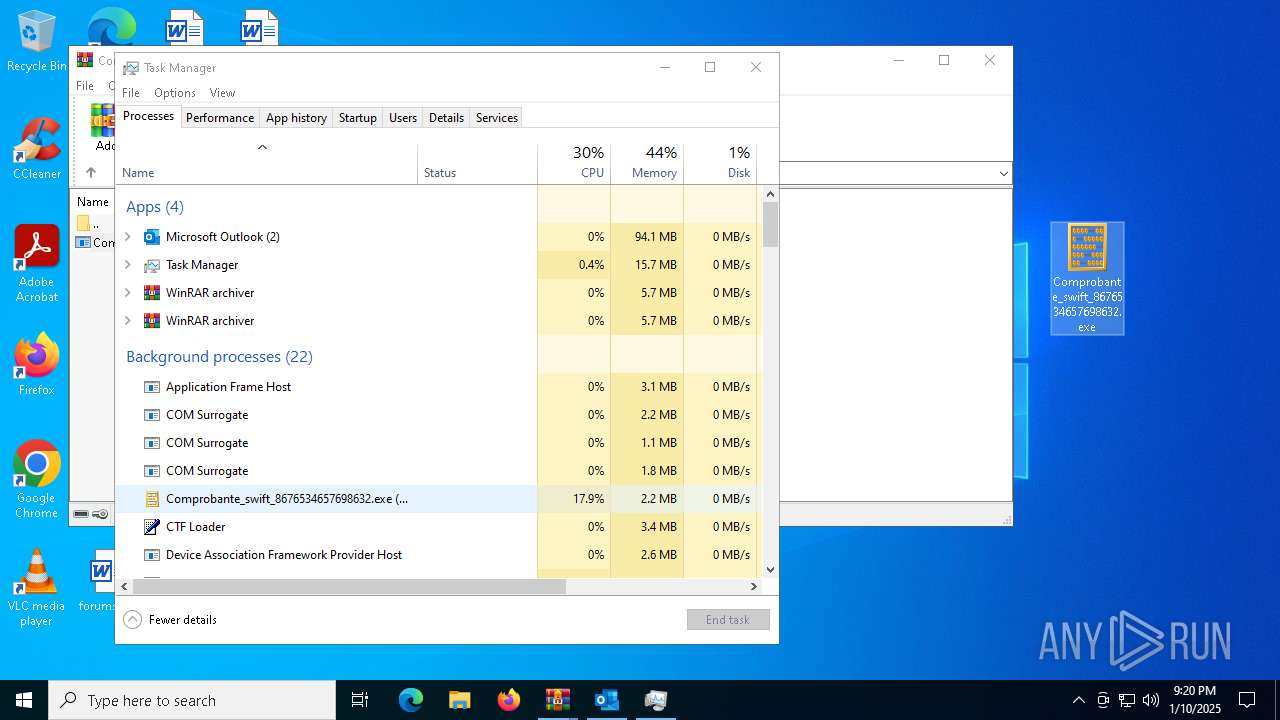
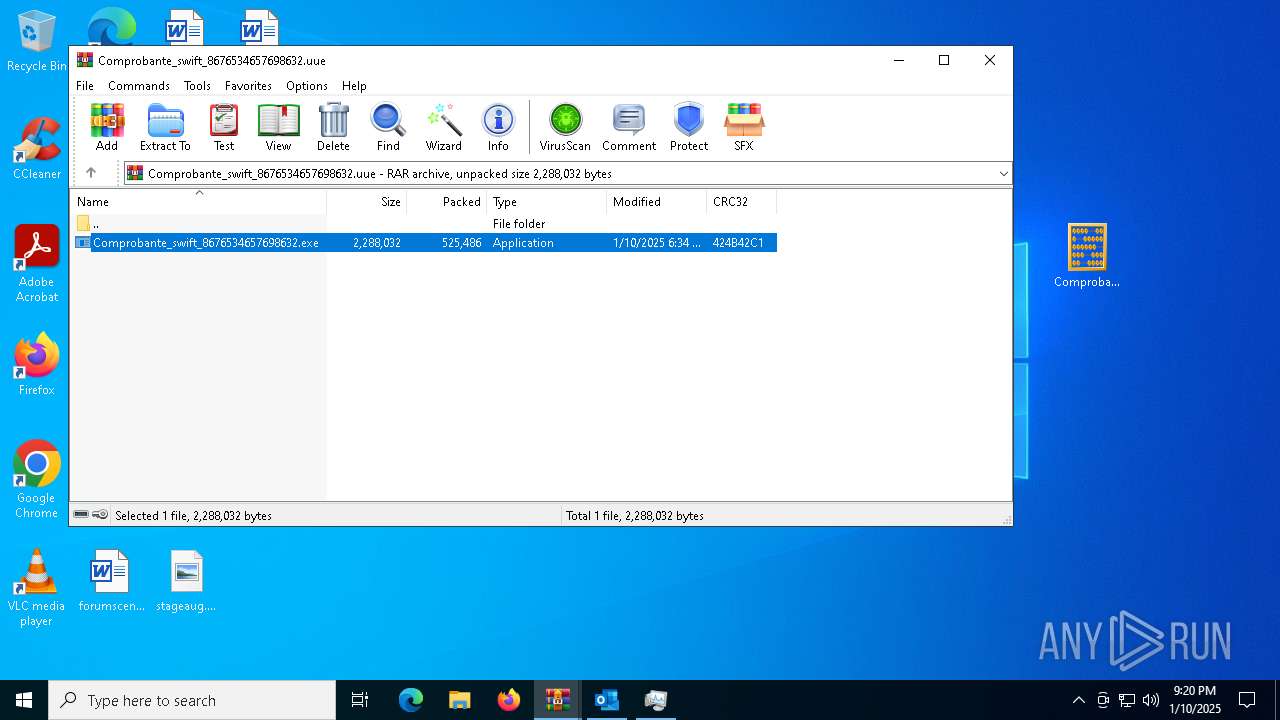
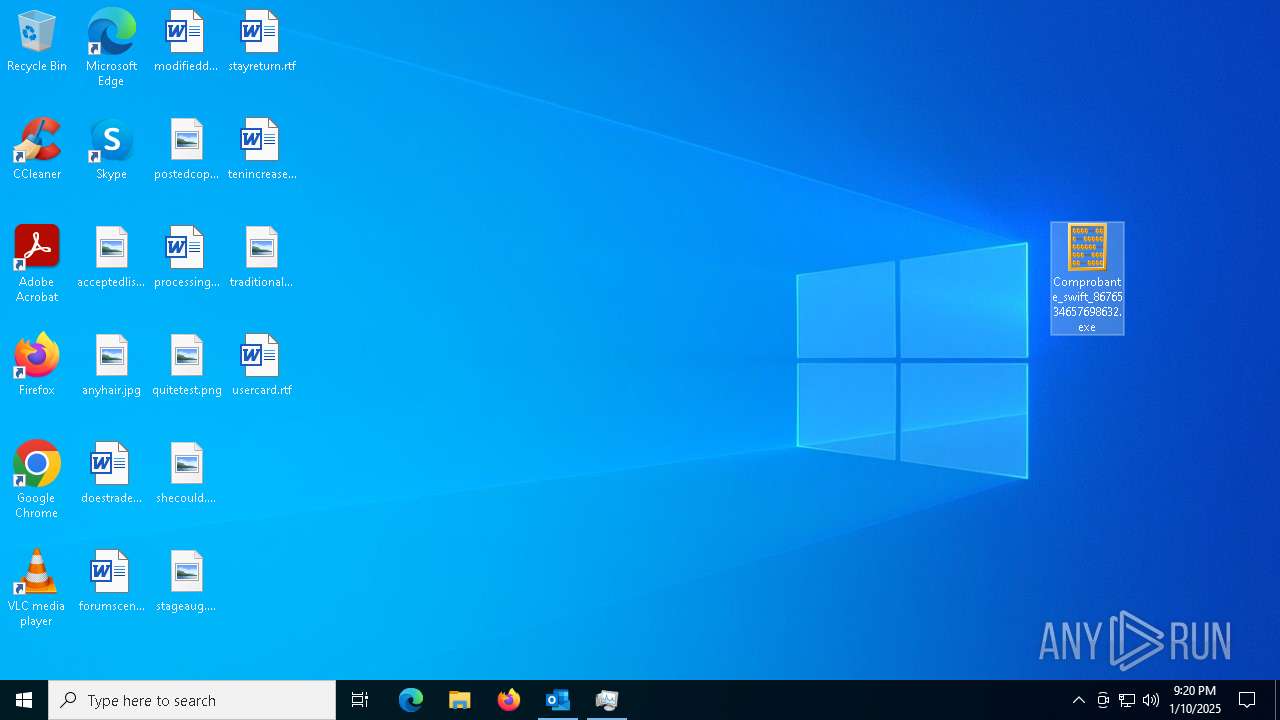
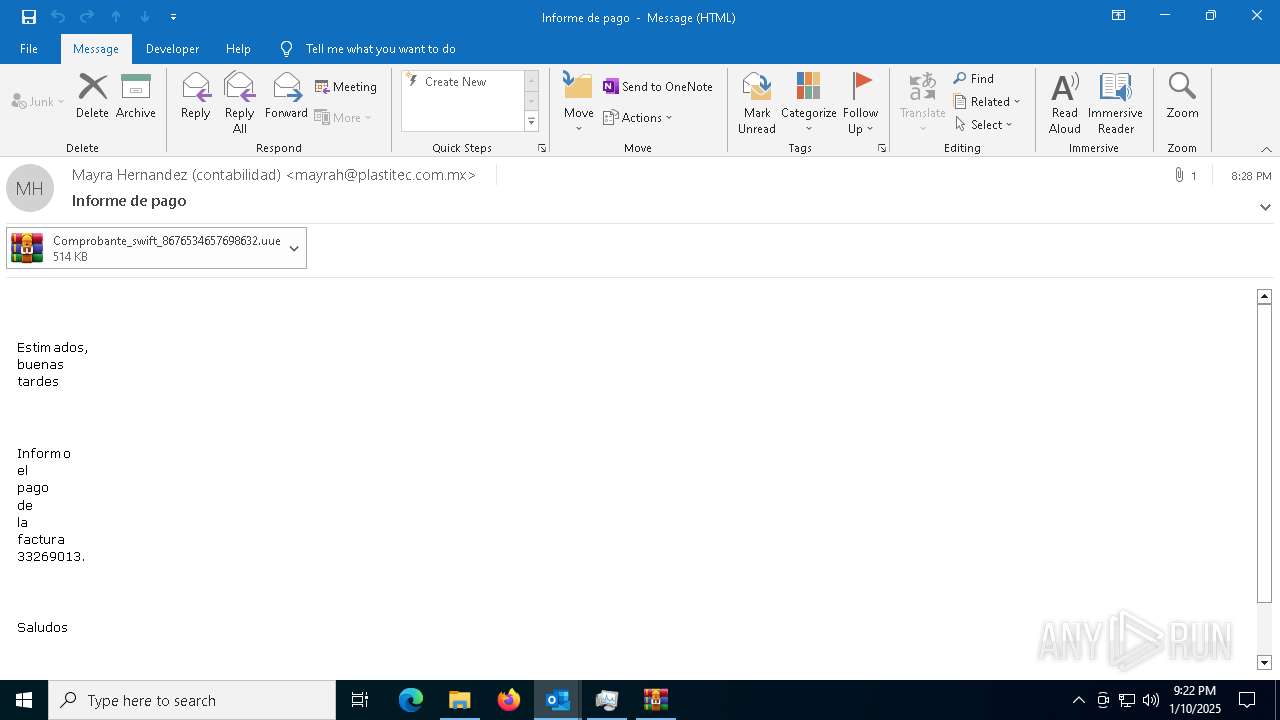
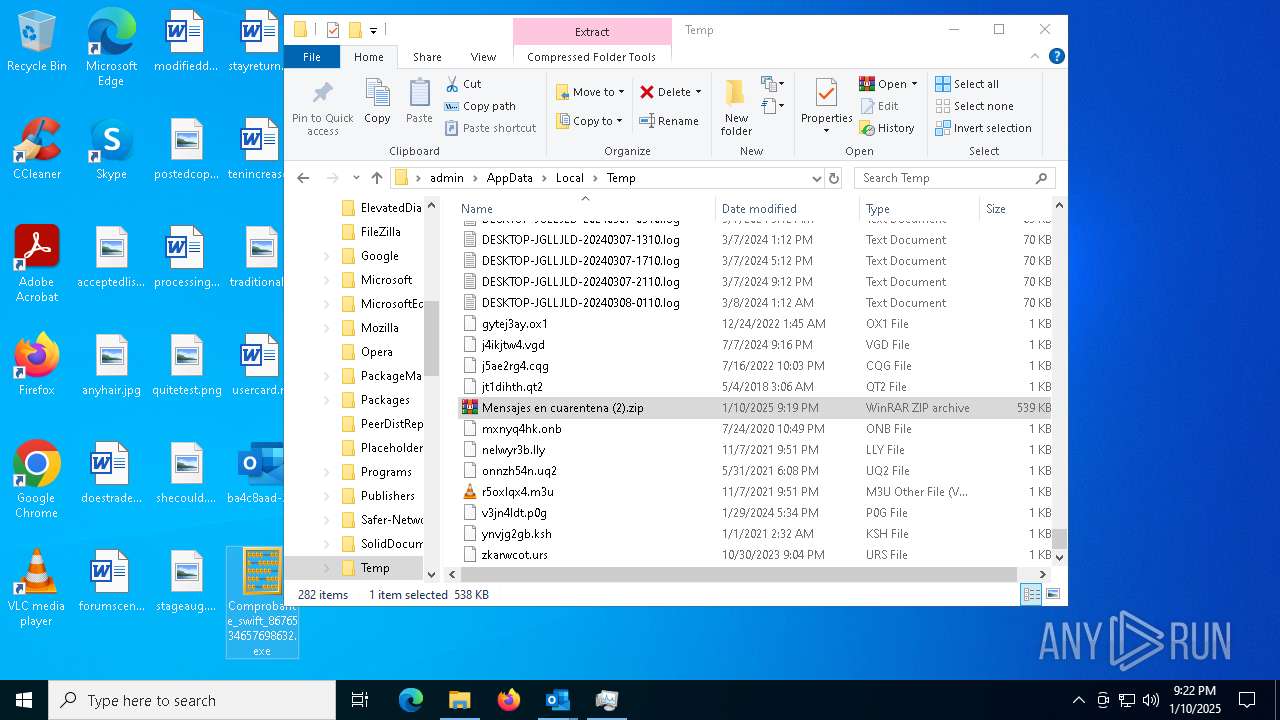
- Comprobante_swift_8676534657698632.exe (PID: 6012)
- Comprobante_swift_8676534657698632.exe (PID: 6776)
- Comprobante_swift_8676534657698632.exe (PID: 2672)
- Comprobante_swift_8676534657698632.exe (PID: 1080)
- Comprobante_swift_8676534657698632.exe (PID: 6424)
- Comprobante_swift_8676534657698632.exe (PID: 188)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 6328)
- RegAsm.exe (PID: 7020)
- RegAsm.exe (PID: 1760)
- RegAsm.exe (PID: 432)
- RegAsm.exe (PID: 7136)
Steals credentials from Web Browsers
- RegAsm.exe (PID: 6328)
- RegAsm.exe (PID: 7020)
- RegAsm.exe (PID: 1760)
- RegAsm.exe (PID: 432)
- RegAsm.exe (PID: 7136)
AGENTTESLA has been detected (SURICATA)
- RegAsm.exe (PID: 6328)
- RegAsm.exe (PID: 7020)
- RegAsm.exe (PID: 1760)
- RegAsm.exe (PID: 432)
- RegAsm.exe (PID: 7136)
Connects to the CnC server
- RegAsm.exe (PID: 6328)
- RegAsm.exe (PID: 7020)
- RegAsm.exe (PID: 1760)
- RegAsm.exe (PID: 432)
- RegAsm.exe (PID: 7136)
AGENTTESLA has been detected (YARA)
- RegAsm.exe (PID: 6328)
- RegAsm.exe (PID: 1760)
- RegAsm.exe (PID: 7020)
- RegAsm.exe (PID: 432)
- RegAsm.exe (PID: 7136)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6556)
- WinRAR.exe (PID: 5564)
- WinRAR.exe (PID: 7152)
Reads Microsoft Outlook installation path
- WinRAR.exe (PID: 6556)
- WinRAR.exe (PID: 7152)
Checks for external IP
- svchost.exe (PID: 2192)
- RegAsm.exe (PID: 6328)
- RegAsm.exe (PID: 7020)
- RegAsm.exe (PID: 1760)
- RegAsm.exe (PID: 432)
- RegAsm.exe (PID: 7136)
Connects to unusual port
- RegAsm.exe (PID: 6328)
- RegAsm.exe (PID: 7020)
- RegAsm.exe (PID: 1760)
- RegAsm.exe (PID: 432)
- RegAsm.exe (PID: 7136)
Connects to FTP
- RegAsm.exe (PID: 6328)
- RegAsm.exe (PID: 7020)
- RegAsm.exe (PID: 1760)
- RegAsm.exe (PID: 432)
- RegAsm.exe (PID: 7136)
INFO
The sample compiled with german language support
- WinRAR.exe (PID: 6556)
- OUTLOOK.EXE (PID: 6784)
- WinRAR.exe (PID: 5564)
- WinRAR.exe (PID: 5964)
- WinRAR.exe (PID: 7152)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6556)
The process uses the downloaded file
- WinRAR.exe (PID: 6556)
- WinRAR.exe (PID: 5564)
- OUTLOOK.EXE (PID: 6784)
- WinRAR.exe (PID: 7152)
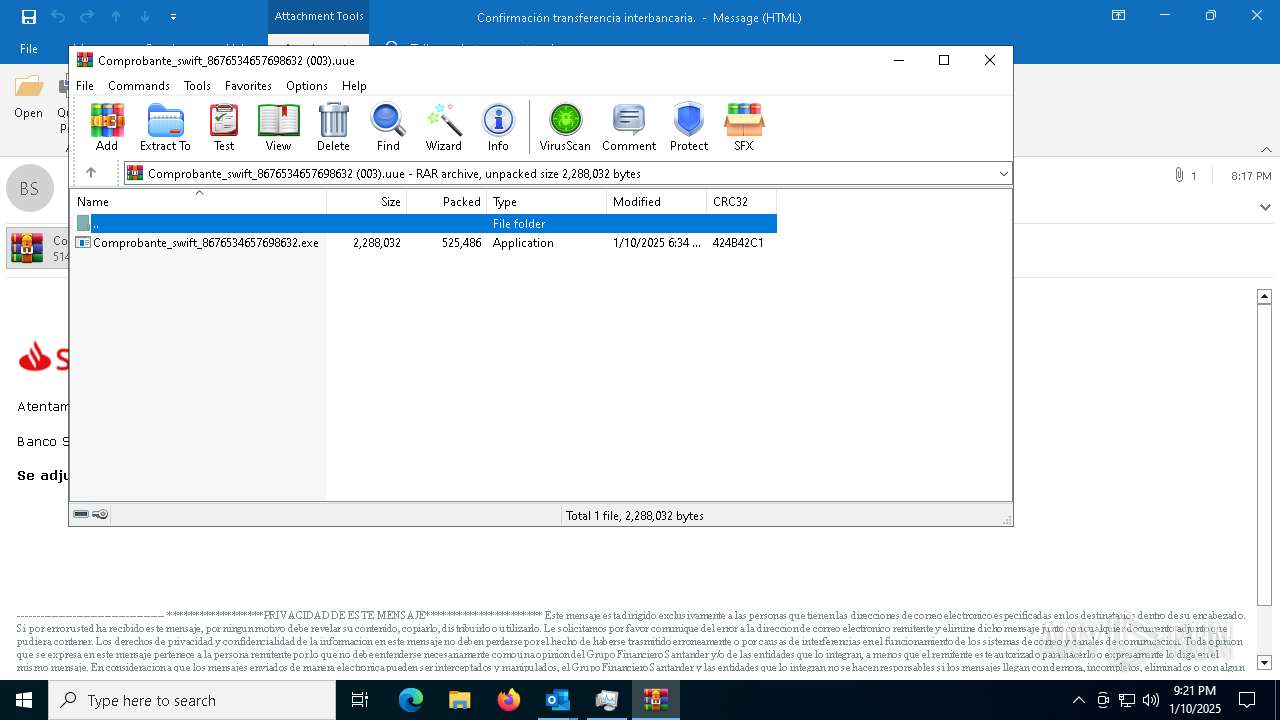
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5564)
- WinRAR.exe (PID: 5964)
Reads the computer name
- Comprobante_swift_8676534657698632.exe (PID: 6012)
- RegAsm.exe (PID: 6328)
- Comprobante_swift_8676534657698632.exe (PID: 1080)
- RegAsm.exe (PID: 432)
- Comprobante_swift_8676534657698632.exe (PID: 188)
- RegAsm.exe (PID: 6684)
Checks supported languages
- Comprobante_swift_8676534657698632.exe (PID: 6012)
- RegAsm.exe (PID: 6328)
- Comprobante_swift_8676534657698632.exe (PID: 6776)
- Comprobante_swift_8676534657698632.exe (PID: 2672)
- RegAsm.exe (PID: 1760)
- RegAsm.exe (PID: 432)
- Comprobante_swift_8676534657698632.exe (PID: 6424)
- RegAsm.exe (PID: 7136)
- Comprobante_swift_8676534657698632.exe (PID: 188)
- RegAsm.exe (PID: 6684)
Reads the machine GUID from the registry
- Comprobante_swift_8676534657698632.exe (PID: 6012)
- RegAsm.exe (PID: 6328)
- Comprobante_swift_8676534657698632.exe (PID: 6776)
- RegAsm.exe (PID: 7020)
- RegAsm.exe (PID: 1760)
- Comprobante_swift_8676534657698632.exe (PID: 1080)
- RegAsm.exe (PID: 7136)
- Comprobante_swift_8676534657698632.exe (PID: 188)
Disables trace logs
- RegAsm.exe (PID: 6328)
- RegAsm.exe (PID: 1760)
- RegAsm.exe (PID: 7136)
Checks proxy server information
- RegAsm.exe (PID: 6328)
- RegAsm.exe (PID: 1760)
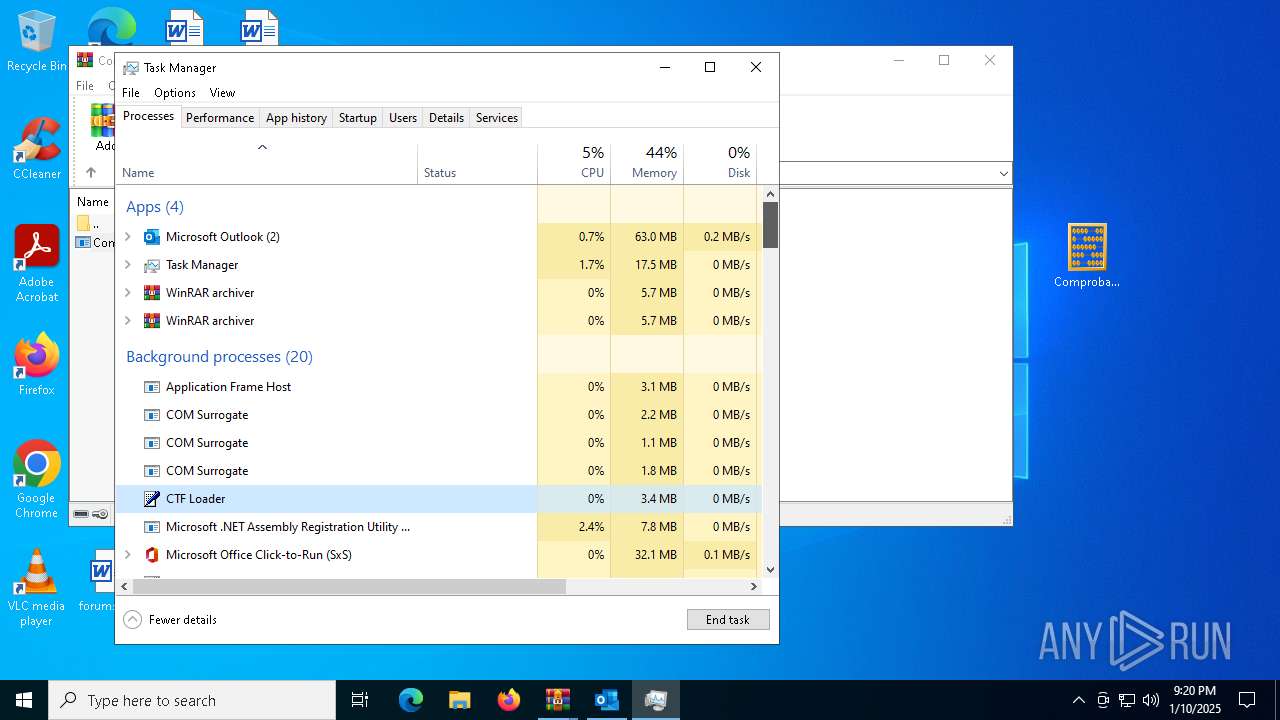
Manual execution by a user
- Comprobante_swift_8676534657698632.exe (PID: 6776)
- Taskmgr.exe (PID: 5604)
- Comprobante_swift_8676534657698632.exe (PID: 2672)
- Taskmgr.exe (PID: 1596)
- OUTLOOK.EXE (PID: 1140)
- Comprobante_swift_8676534657698632.exe (PID: 1080)
- WinRAR.exe (PID: 7152)
- Comprobante_swift_8676534657698632.exe (PID: 6424)
- Comprobante_swift_8676534657698632.exe (PID: 188)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 45 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:10 20:57:50 |
| ZipCRC: | 0x6f56136e |
| ZipCompressedSize: | 4294967295 |
| ZipUncompressedSize: | 4294967295 |
| ZipFileName: | ea537a0d-4c76-43cd-40d8-08dd31b81a2e/34a3e8c0-6921-02e0-b21e-bc1f8571e6fd.eml |
Total processes
159
Monitored processes
30
Malicious processes
14
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Users\admin\Desktop\Comprobante_swift_8676534657698632.exe" | C:\Users\admin\Desktop\Comprobante_swift_8676534657698632.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 432 | "C:\WINDOWS\Microsoft.NET\Framework\v4.0.30319\regasm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | Comprobante_swift_8676534657698632.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1080 | "C:\Users\admin\Desktop\Comprobante_swift_8676534657698632.exe" | C:\Users\admin\Desktop\Comprobante_swift_8676534657698632.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
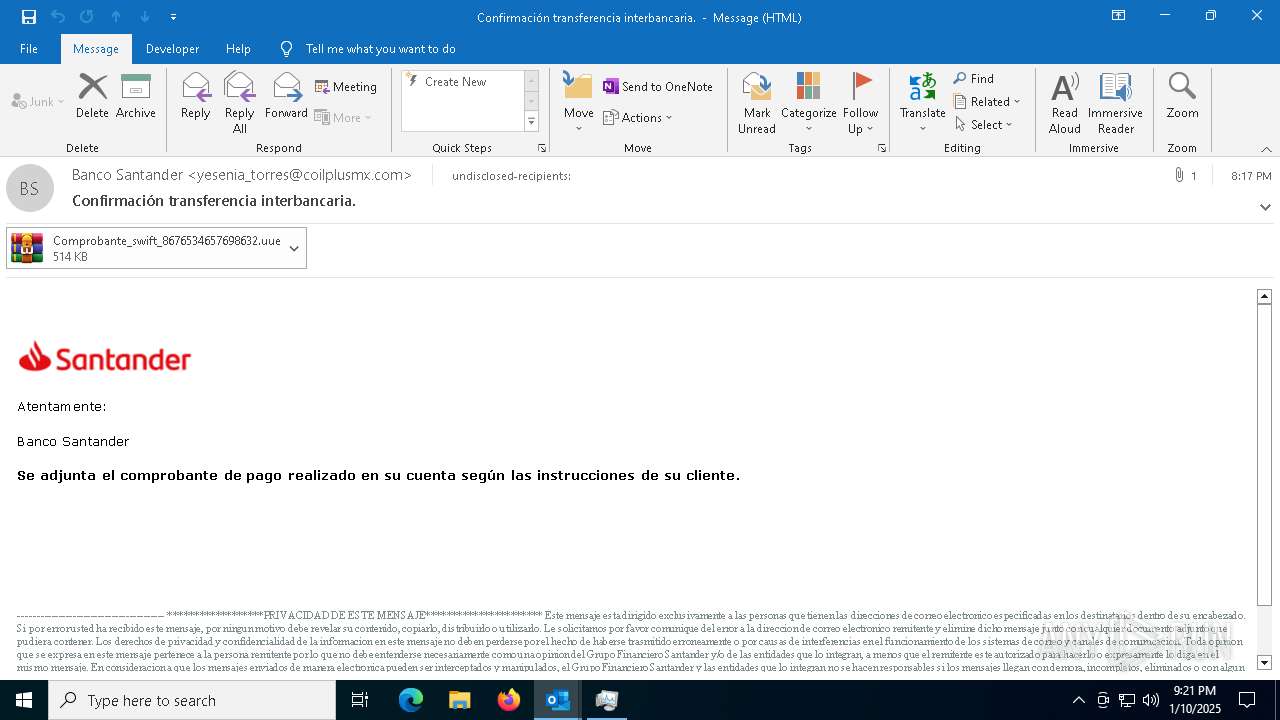
| 1140 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\ba4c8aad-21d0-eb22-a40e-31dc691af764.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1596 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | "C:\WINDOWS\Microsoft.NET\Framework\v4.0.30319\regasm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | Comprobante_swift_8676534657698632.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1760 | "C:\WINDOWS\Microsoft.NET\Framework\v4.0.30319\regasm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | Comprobante_swift_8676534657698632.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2672 | "C:\Users\admin\Desktop\Comprobante_swift_8676534657698632.exe" | C:\Users\admin\Desktop\Comprobante_swift_8676534657698632.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2736 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Rar$DIb7152.46837\34a3e8c0-6921-02e0-b21e-bc1f8571e6fd.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
30 599
Read events
29 252
Write events
1 176
Delete events
171
Modification events
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Mensajes en cuarentena (2).zip | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6556) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6784) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (6784) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common |
| Operation: | write | Name: | SessionId |
Value: 8DBDFDC70036DA44988D72D67514C191 | |||
Executable files
3
Suspicious files
22
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6784 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 6556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb6556.26634\34a3e8c0-6921-02e0-b21e-bc1f8571e6fd.eml | binary | |
MD5:6358B582F0250F9A07FC4121E9E2DAB8 | SHA256:14D2CD178F3180E95EEE7949E9E61DC45B7224E5CA2D704E5C59DE8D45DFB2FE | |||
| 6784 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\916AC5B3-FF76-420B-A366-FF6ABA25CE5D | xml | |
MD5:FA909E27BCF04A6098C56E8BD55484EC | SHA256:4968E5A831C79316394603409697B3C6AA92B36F9DE2D31D1202A43E99550D24 | |||
| 6556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb6556.26634\34a3e8c0-6921-02e0-b21e-bc1f8571e6fd.eml:OECustomProperty | binary | |
MD5:D651CE128A7834CA1ED398336D085042 | SHA256:1F000015313DDB29B0B81FC8229958A625236C93CAEACE0E94F54520E5D39B2B | |||
| 6784 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:2406D6C215D2203F3FE97D33E1F66F57 | SHA256:29812EDF9F7BDBB24C48E758C461B3A9C77CE46632696F84646D85BA9825160D | |||
| 6784 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:71A1407A7319F8E35C6B9E7D3DD0E793 | SHA256:616E3E561DBFC729DDC325394F74FA3906C9038956A9A7CCA0E689444A63216E | |||
| 6784 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olk9C24.tmp | binary | |
MD5:13AB33633D1EB79455ABDC598B373402 | SHA256:D7250F51131DD2B8285F2703832879AE3D245721ECB1DE955CD8499BD265F23D | |||
| 6784 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:AB0AE6594E31622A1E7CB63DEC4F926C | SHA256:2E46ED781493A2811F73D75173C0C8C16C01C7F6ED590772613E56D1824032D7 | |||
| 6784 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:DD159D070F5486E5045A4ECF74DC361F | SHA256:31830E2FD13CF4B1561DCB07D443E2918D633D5C3ECFAAF4AE25D6DFABF676A1 | |||
| 6784 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:96FB7C55659946D88A504895C533F5D2 | SHA256:24103A95A005927A6752555593F8EB40486FC0CDD951C51A172B8B03F35B2377 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
58
DNS requests
31
Threats
51
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.161:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6784 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3688 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6784 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
3692 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6328 | RegAsm.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
3692 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1876 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.161:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 92.123.104.63:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3040 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
6328 | RegAsm.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
6328 | RegAsm.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
6328 | RegAsm.exe | A Network Trojan was detected | ET MALWARE AgentTesla Exfil via FTP |
6328 | RegAsm.exe | Misc activity | INFO [ANY.RUN] FTP protocol command for uploading a file |
6328 | RegAsm.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
6328 | RegAsm.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
7020 | RegAsm.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
7020 | RegAsm.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
10 ETPRO signatures available at the full report