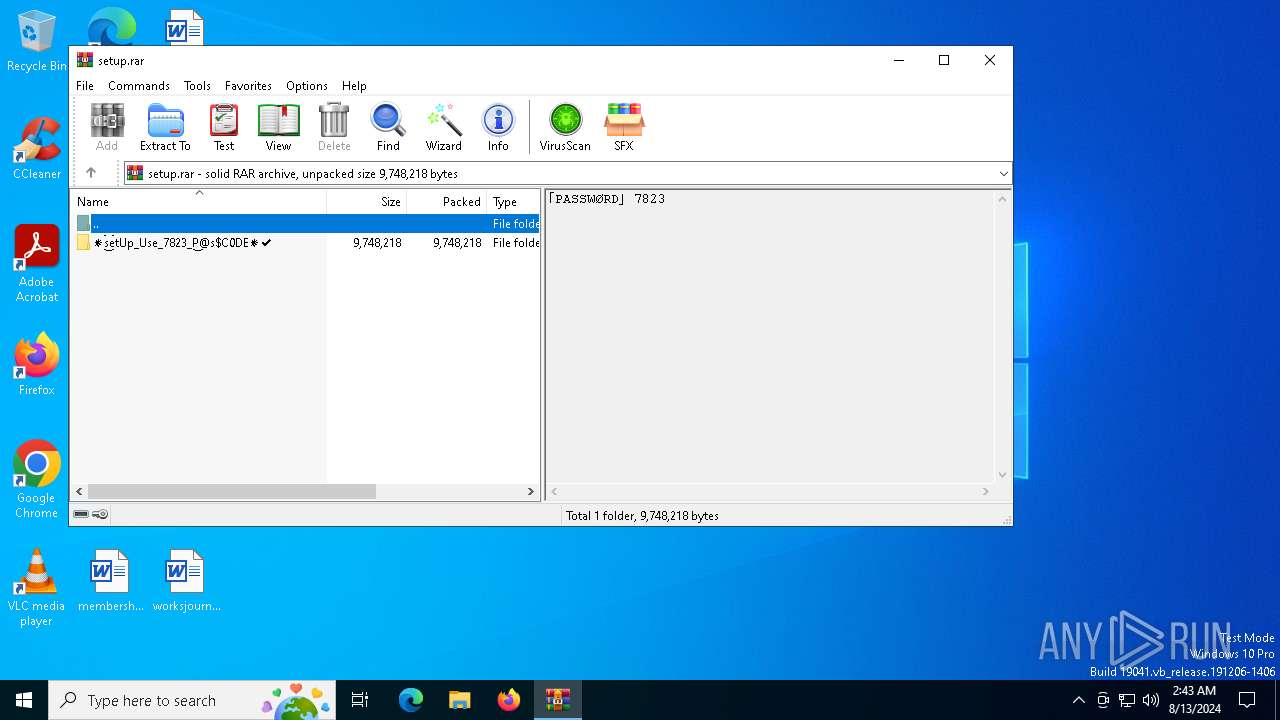
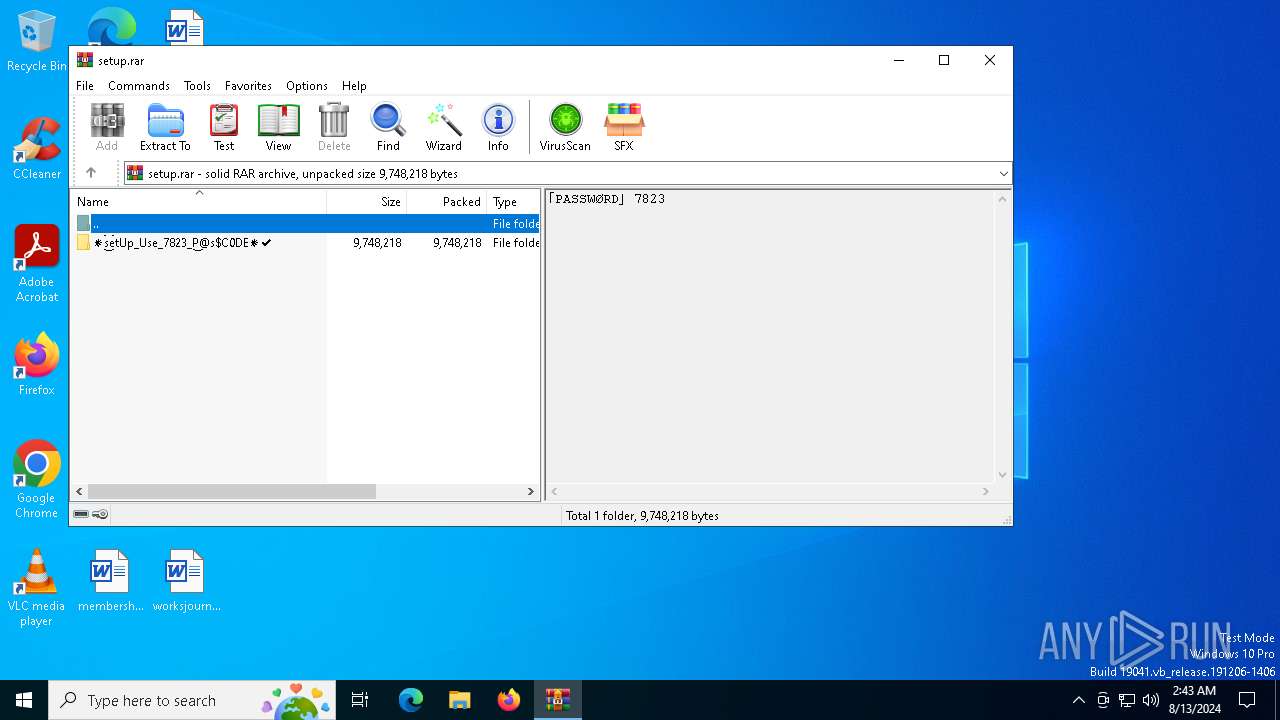
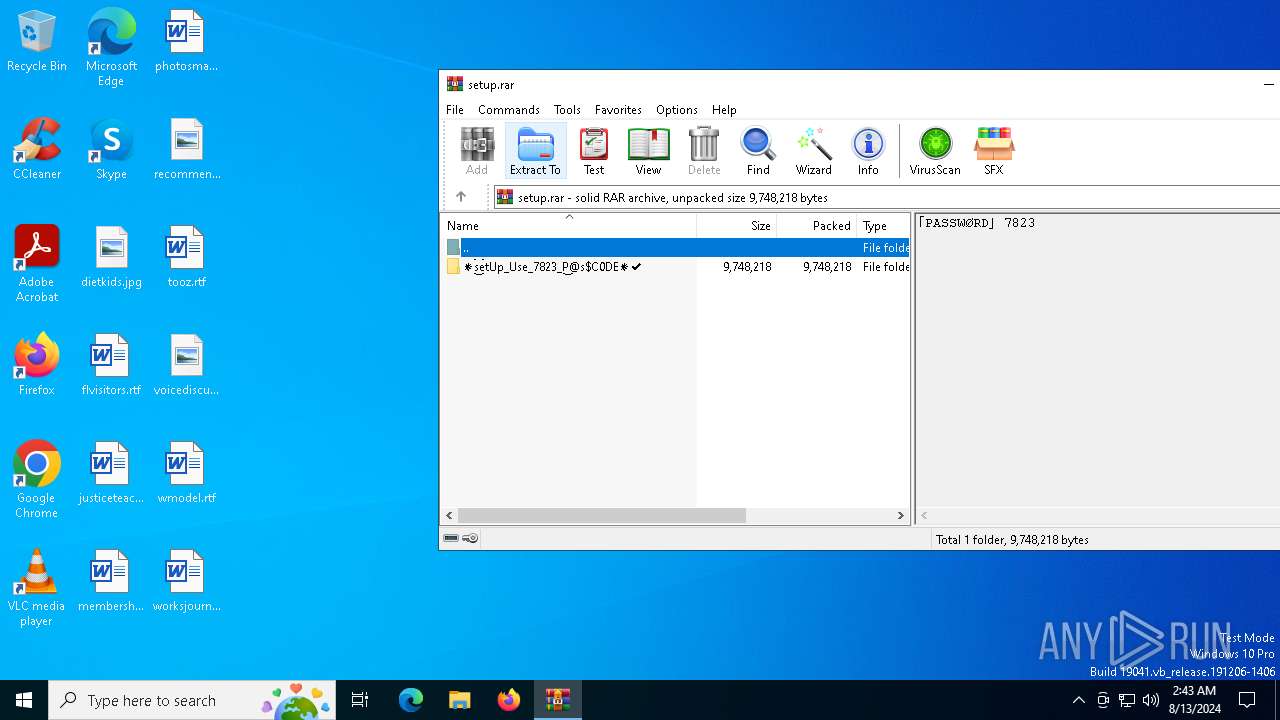
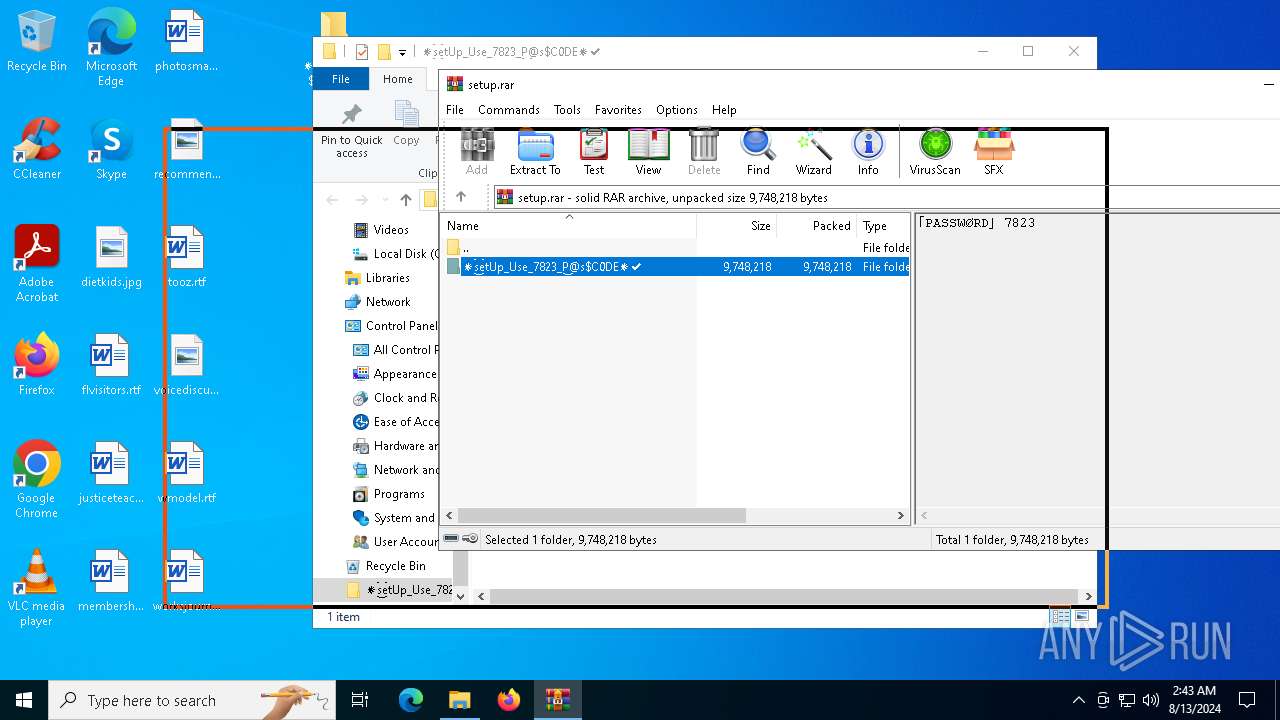
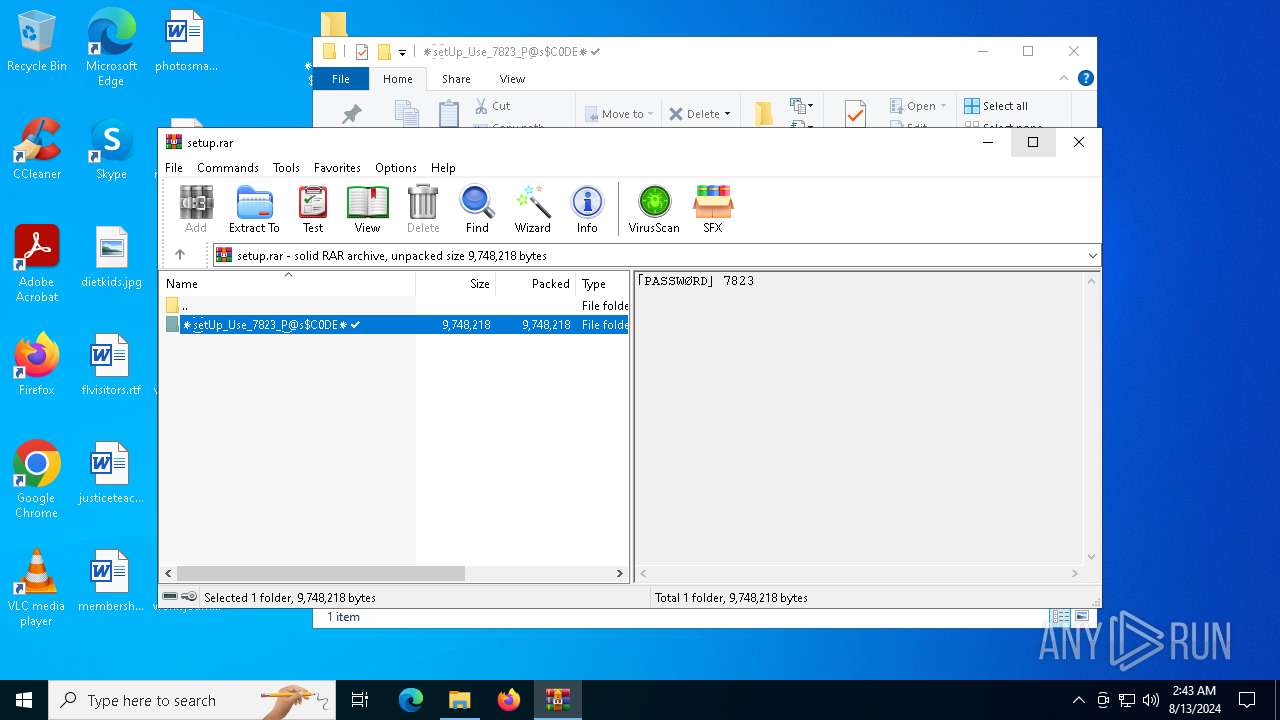
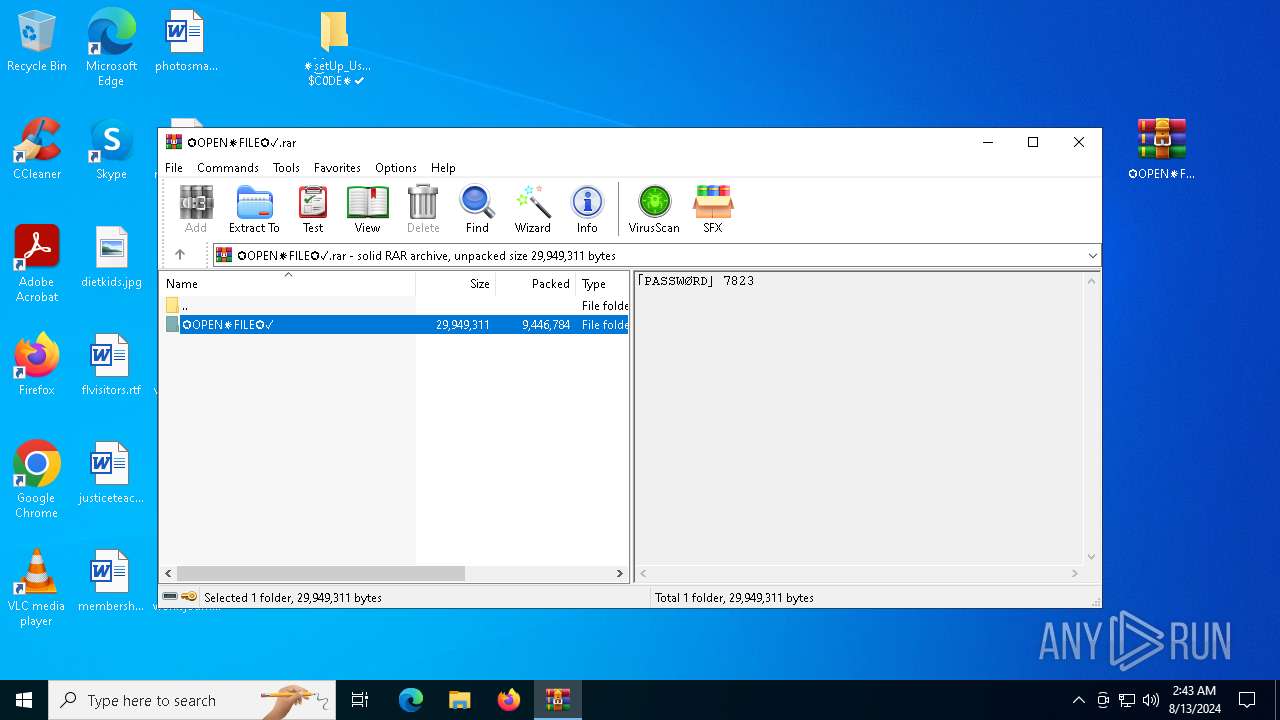
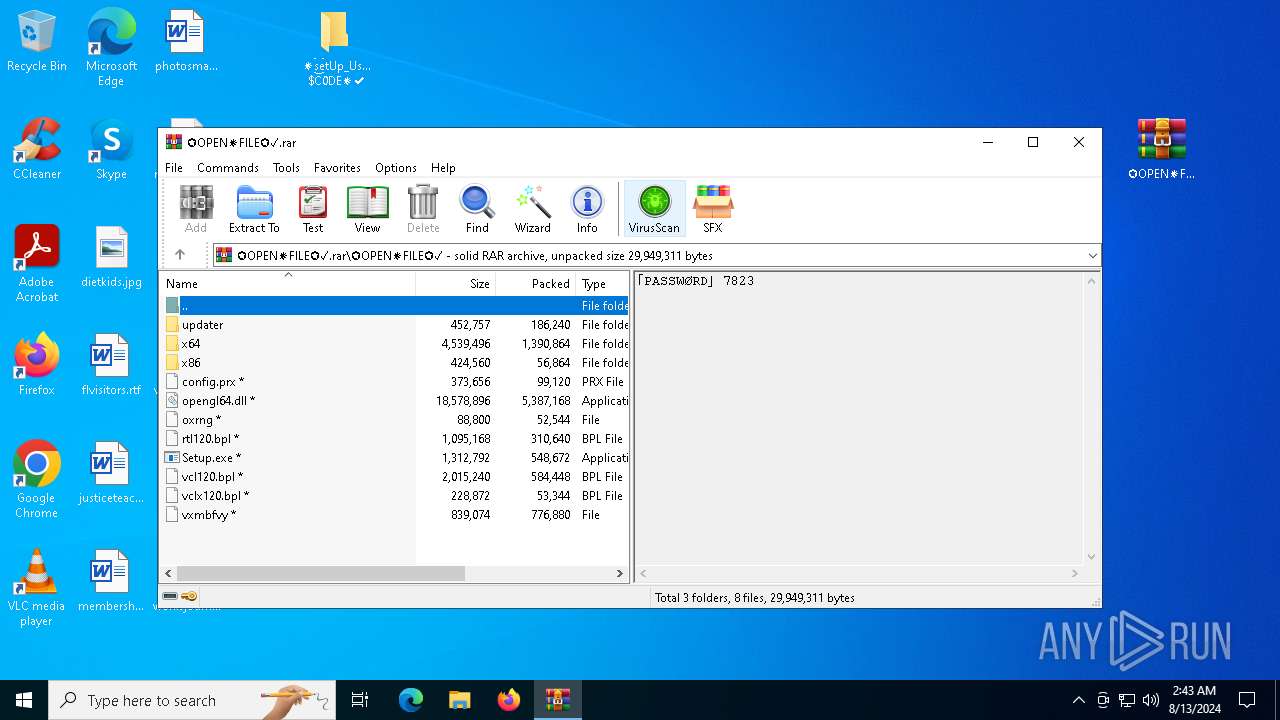
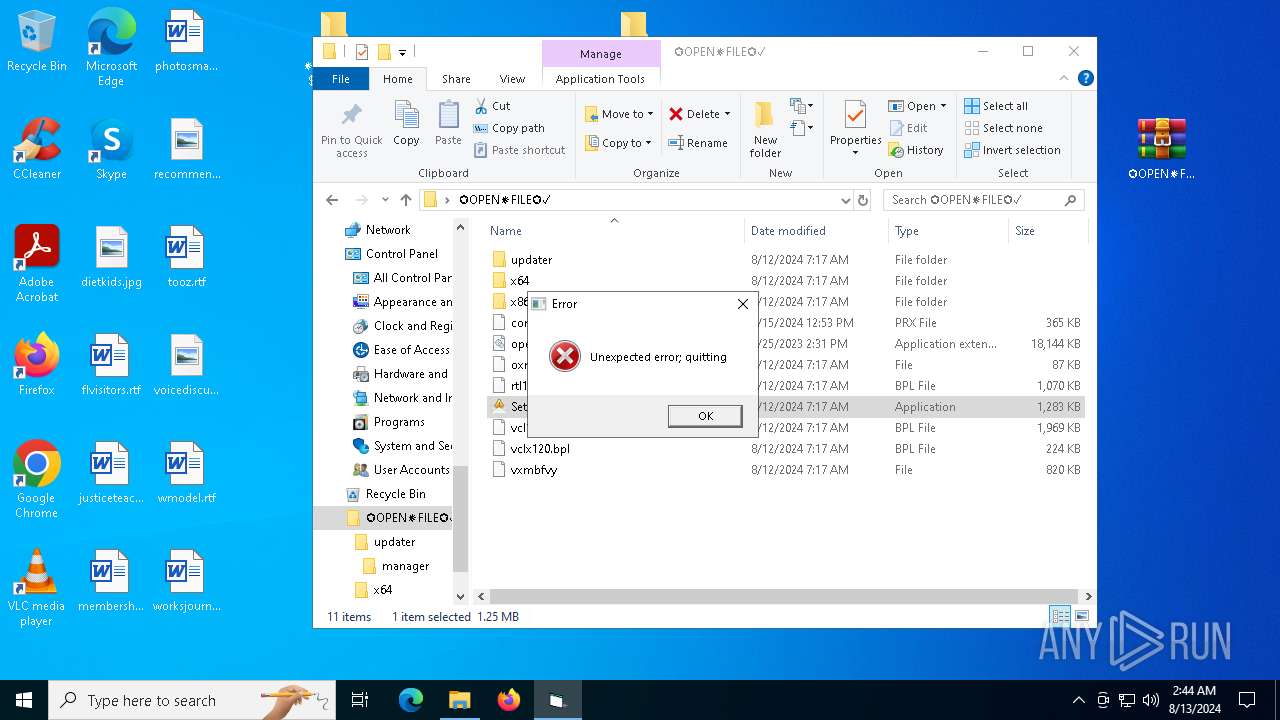
| File name: | setup.rar |
| Full analysis: | https://app.any.run/tasks/93494e45-6162-47c6-93a5-51ac95a2cda1 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | August 13, 2024, 02:43:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | DB7F6A4A1FF1559F216E17EC39A55469 |
| SHA1: | 95B84172E981780910EC516DC9B1A4E4CD5D265C |
| SHA256: | D7A01A07E0B5B58E6736D228194724E7FA7C5B499E84FB6F2022CC7DAF09B815 |
| SSDEEP: | 98304:OfWoynmHGRNUaWk9Wv/+n1TECroOZZHxNi6Ndbc6gXAIPkBdicKR4SxTS05syulV:hntsvWgNYYCAo |
MALICIOUS
LUMMA has been detected (YARA)
- SearchIndexer.exe (PID: 2804)
Bypass execution policy to execute commands
- powershell.exe (PID: 1292)
Changes powershell execution policy (Bypass)
- SearchIndexer.exe (PID: 2804)
Create files in the Startup directory
- C7RGME9OT64JKGXEY.exe (PID: 2796)
Probably downloads file via BitsAdmin (POWERSHELL)
- powershell.exe (PID: 1292)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 2336)
Drops the executable file immediately after the start
- Setup.exe (PID: 3980)
- C7RGME9OT64JKGXEY.exe (PID: 2796)
Executable content was dropped or overwritten
- Setup.exe (PID: 3980)
- SearchIndexer.exe (PID: 2804)
- C7RGME9OT64JKGXEY.exe (PID: 2796)
Starts application with an unusual extension
- Setup.exe (PID: 3980)
Searches for installed software
- SearchIndexer.exe (PID: 2804)
Starts POWERSHELL.EXE for commands execution
- SearchIndexer.exe (PID: 2804)
The process executes Powershell scripts
- SearchIndexer.exe (PID: 2804)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 1292)
Found regular expressions for crypto-addresses (YARA)
- MSBuild.exe (PID: 2648)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 1292)
There is functionality for taking screenshot (YARA)
- C7RGME9OT64JKGXEY.exe (PID: 2796)
Connects to unusual port
- MSBuild.exe (PID: 2648)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2336)
Manual execution by a user
- WinRAR.exe (PID: 2336)
- notepad++.exe (PID: 4100)
- notepad.exe (PID: 6232)
- Setup.exe (PID: 3980)
- mspaint.exe (PID: 3700)
- notepad++.exe (PID: 1184)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6232)
Checks supported languages
- Setup.exe (PID: 3980)
- TextInputHost.exe (PID: 5500)
- StrCmp.exe (PID: 2132)
- more.com (PID: 6808)
- IMVFJYW7N30CL2EQGJ3JJXZK7SVRY55.exe (PID: 6032)
- C7RGME9OT64JKGXEY.exe (PID: 2796)
- MSBuild.exe (PID: 2648)
Reads the computer name
- TextInputHost.exe (PID: 5500)
- Setup.exe (PID: 3980)
- StrCmp.exe (PID: 2132)
- more.com (PID: 6808)
- IMVFJYW7N30CL2EQGJ3JJXZK7SVRY55.exe (PID: 6032)
- C7RGME9OT64JKGXEY.exe (PID: 2796)
Creates files or folders in the user directory
- Setup.exe (PID: 3980)
- C7RGME9OT64JKGXEY.exe (PID: 2796)
Create files in a temporary directory
- Setup.exe (PID: 3980)
- IMVFJYW7N30CL2EQGJ3JJXZK7SVRY55.exe (PID: 6032)
- SearchIndexer.exe (PID: 2804)
- more.com (PID: 6808)
Reads the software policy settings
- SearchIndexer.exe (PID: 2804)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1292)
.NET Reactor protector has been detected
- C7RGME9OT64JKGXEY.exe (PID: 2796)
Creates files in the program directory
- MSBuild.exe (PID: 2648)
Reads the machine GUID from the registry
- C7RGME9OT64JKGXEY.exe (PID: 2796)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1292)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(2804) SearchIndexer.exe
C2 (9)deallerospfosu.shop
writerospzm.shop
celebratioopz.shop
mennyudosirso.shop
complaintsipzzx.shop
languagedscie.shop
bassizcellskz.shop
quialitsuzoxm.shop
monkkerpmzio.shop
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
158
Monitored processes
19
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1184 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\AppData\Local\Temp\e728501e" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 1292 | powershell -exec bypass -f "C:\Users\admin\AppData\Local\Temp\42UWFJFUZQ4VE4KVGK.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | SearchIndexer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1692 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | C:\Users\admin\AppData\Roaming\Wise\XTDHHOMKLQMSHZFLDE\StrCmp.exe | C:\Users\admin\AppData\Roaming\Wise\XTDHHOMKLQMSHZFLDE\StrCmp.exe | — | Setup.exe | |||||||||||
User: admin Company: aaa Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
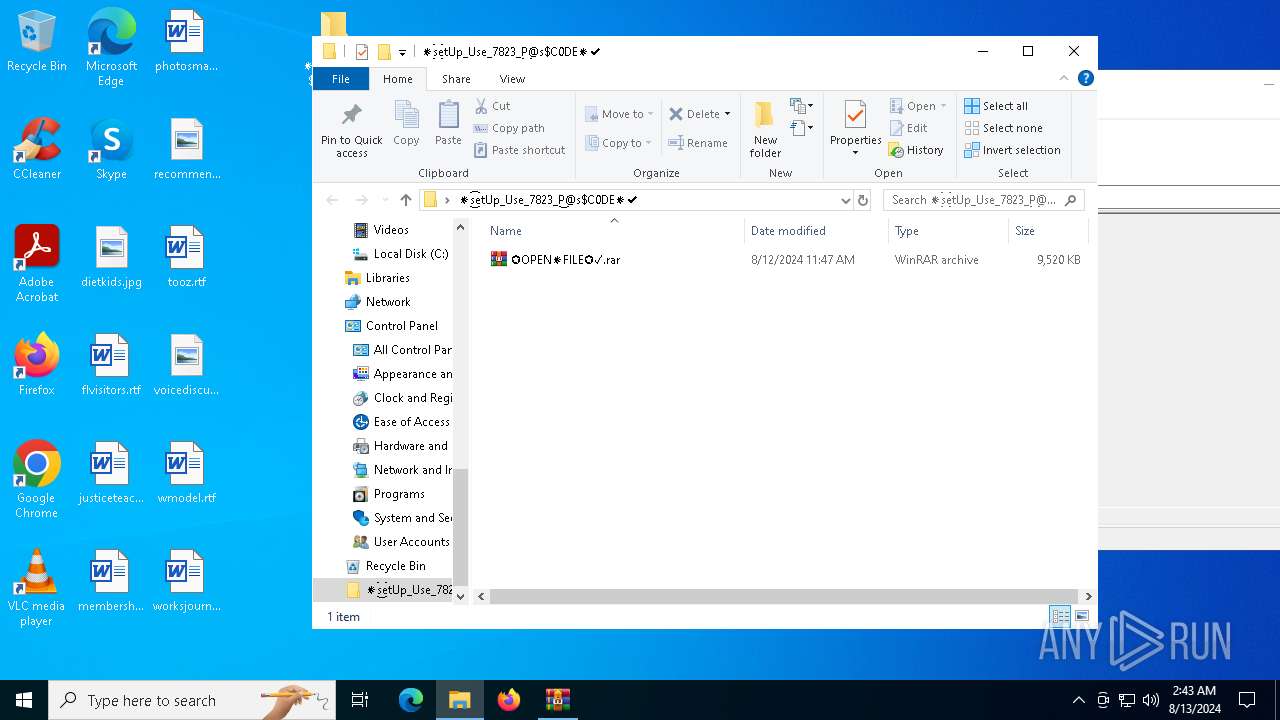
| 2336 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\✪OPEN✵FILE✪✓.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2648 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | C7RGME9OT64JKGXEY.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2796 | "C:\Users\admin\AppData\Local\Temp\C7RGME9OT64JKGXEY.exe" | C:\Users\admin\AppData\Local\Temp\C7RGME9OT64JKGXEY.exe | SearchIndexer.exe | ||||||||||||
User: admin Company: Softinventive Lab Integrity Level: MEDIUM Description: Total Network Inventory Exit code: 4294967295 Version: 4.3.2.4252 Modules
| |||||||||||||||
| 2804 | C:\WINDOWS\SysWOW64\SearchIndexer.exe | C:\Windows\SysWOW64\SearchIndexer.exe | more.com | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Indexer Exit code: 0 Version: 7.0.19041.3758 (WinBuild.160101.0800) Modules
Lumma(PID) Process(2804) SearchIndexer.exe C2 (9)deallerospfosu.shop writerospzm.shop celebratioopz.shop mennyudosirso.shop complaintsipzzx.shop languagedscie.shop bassizcellskz.shop quialitsuzoxm.shop monkkerpmzio.shop | |||||||||||||||
| 3700 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\AppData\Local\Temp\e728501e.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3980 | "C:\Users\admin\Desktop\✪OPEN✵FILE✪✓\Setup.exe" | C:\Users\admin\Desktop\✪OPEN✵FILE✪✓\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: IObit Integrity Level: MEDIUM Description: Send Bug Report Exit code: 1 Version: 10.0.10.101 Modules
| |||||||||||||||
Total events
109 656
Read events
109 576
Write events
79
Delete events
1
Modification events
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\setup.rar | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF960000007F0000005604000068020000 | |||
| (PID) Process: | (6592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
33
Suspicious files
8
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6592 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6592.31710\✵s͜͡etUp_Use_7823_P͜@s$C0DE✵✔\✪OPEN✵FILE✪✓.rar | — | |
MD5:— | SHA256:— | |||
| 2336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2336.34218\✪OPEN✵FILE✪✓\Setup.exe | executable | |
MD5:58717509C1521EACFCC7CDA39E6BD45C | SHA256:D76D0650B630FDB70756A446E0A43672B5DA1C2A74014118B02133923305DA9A | |||
| 2336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2336.34218\✪OPEN✵FILE✪✓\x86\api-ms-win-core-string-l1-1-0.dll | executable | |
MD5:2E5C29FC652F432B89A1AFE187736C4D | SHA256:3807DB7ACF1B40C797E4D4C14A12C3806346AE56B25E205E600BE3E635C18D4F | |||
| 2336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2336.34218\✪OPEN✵FILE✪✓\x86\api-ms-win-core-rtlsupport-l1-1-0.dll | executable | |
MD5:0069FD29263C0DD90314C48BBCE852EF | SHA256:D11093FDC1D5C9213B9B2886CE91DB3DED17EF8DAE1615A8C7FFBC55B8E3F79B | |||
| 2336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2336.34218\✪OPEN✵FILE✪✓\x86\api-ms-win-core-synch-l1-1-0.dll | executable | |
MD5:979C67BA244E5328A1A2E588FF748E86 | SHA256:8BB38A7A59FBAA792B3D5F34F94580429588C8C592929CBD307AFD5579762ABC | |||
| 2336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2336.34218\✪OPEN✵FILE✪✓\x86\api-ms-win-core-processthreads-l1-1-1.dll | executable | |
MD5:29001F316CCFC800E2246743DF9B15B3 | SHA256:E5EA2C21FB225090F7D0DB6C6990D67B1558D8E834E86513BC8BA7A43C4E7B36 | |||
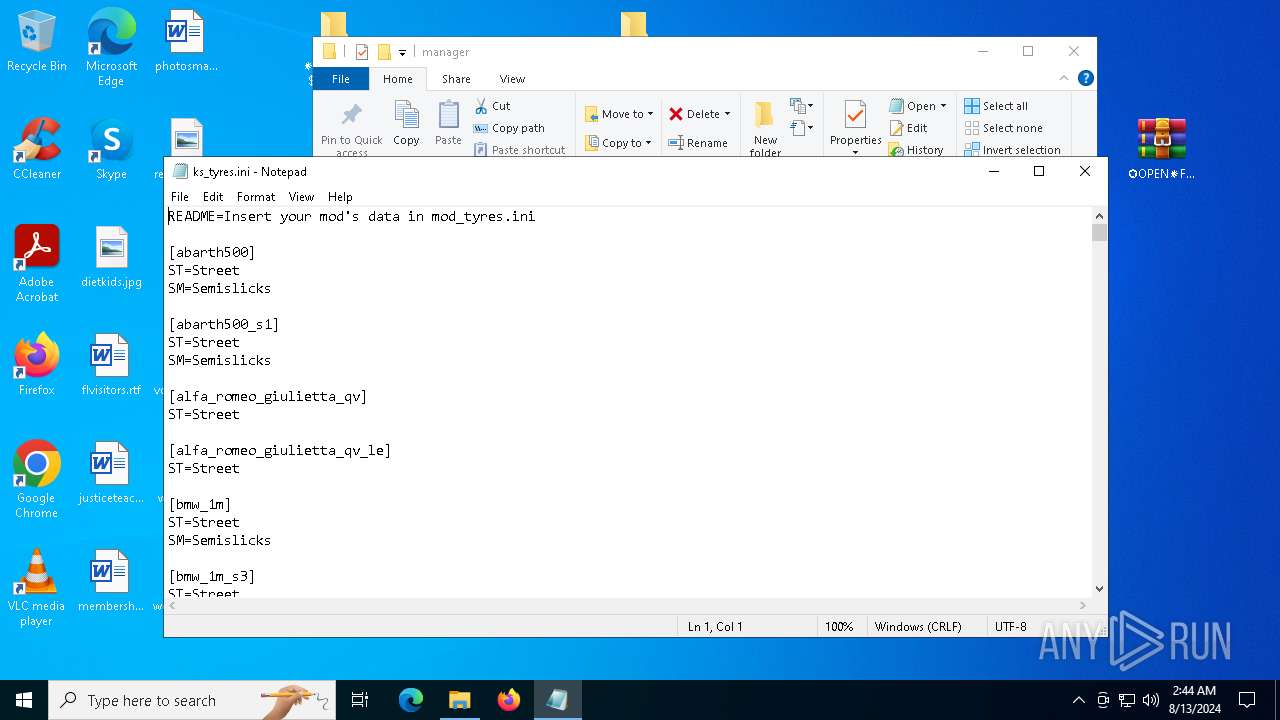
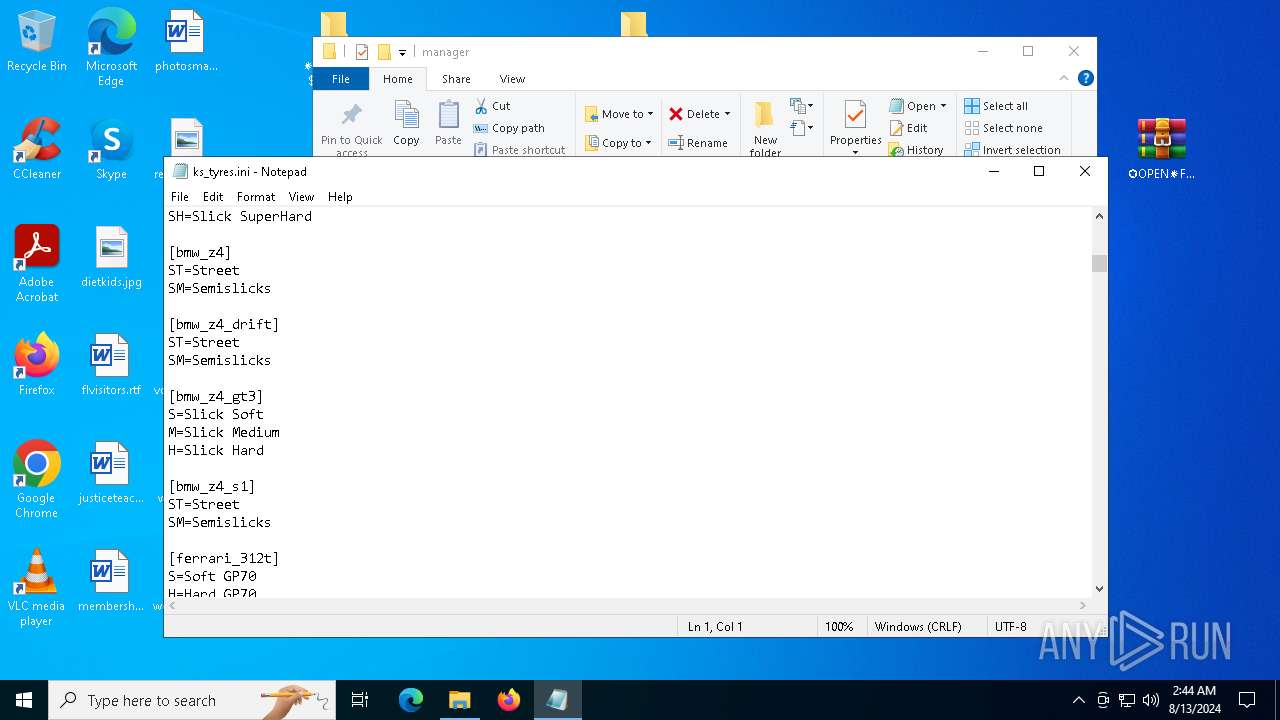
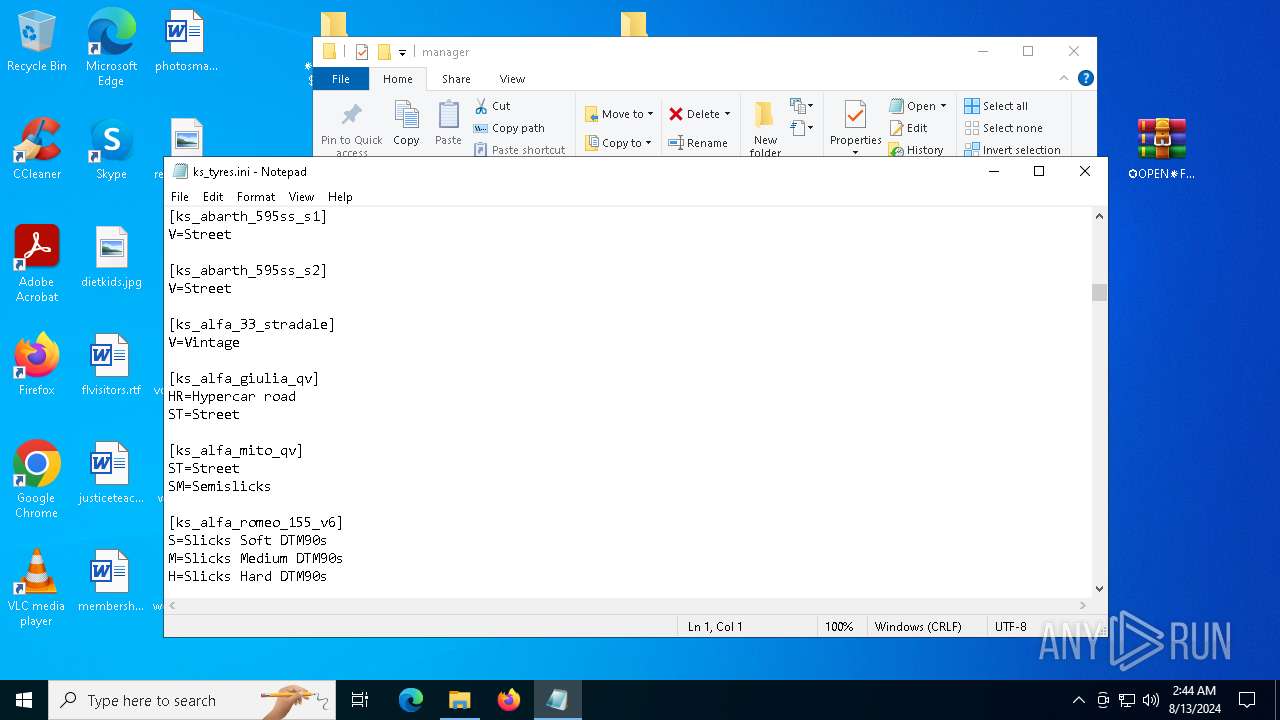
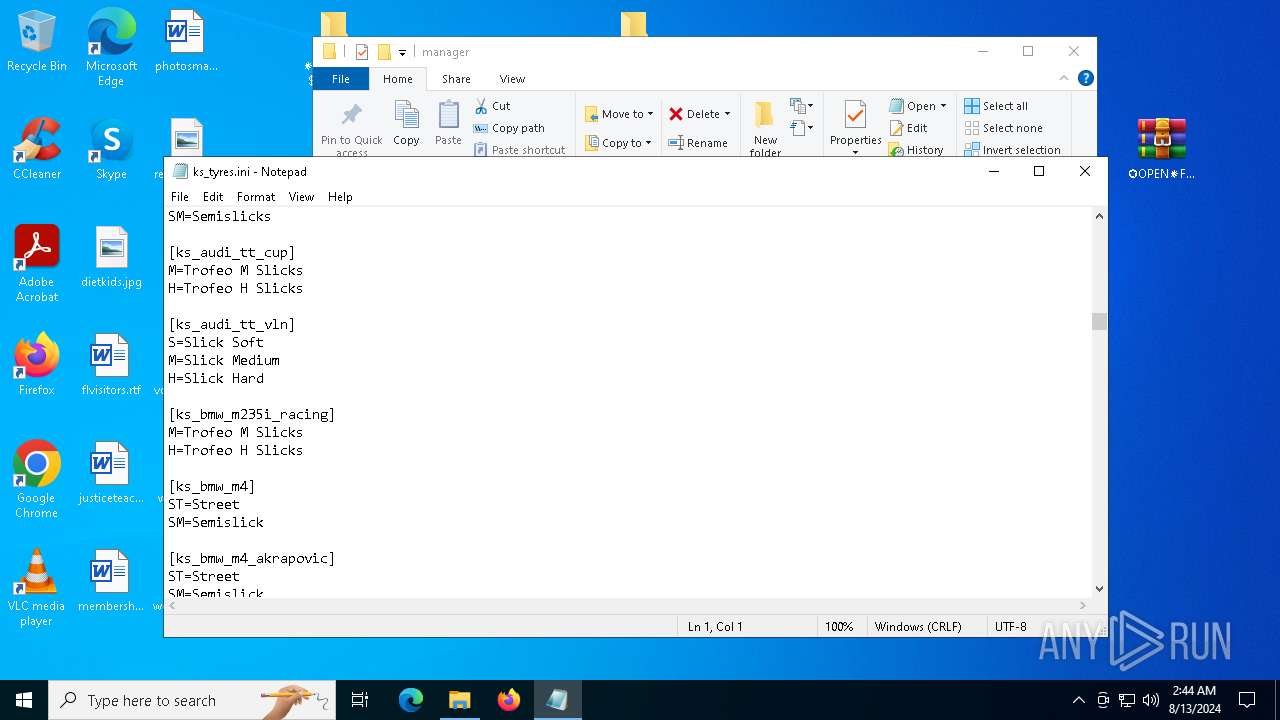
| 2336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2336.34218\✪OPEN✵FILE✪✓\updater\manager\ks_tyres.ini | text | |
MD5:47F6571C7884DA6C743551AC724186D4 | SHA256:894D3C57598ECB22C769CC3EA8219859A95E22740E72394A474012EA2119B3D9 | |||
| 2336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2336.34218\✪OPEN✵FILE✪✓\x86\api-ms-win-core-synch-l1-2-0.dll | executable | |
MD5:659E4FEBC208545A2E23C0C8B881A30D | SHA256:9AC63682E03D55A5D18405D336634AF080DD0003B565D12A39D6D71AAA989F48 | |||
| 2336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2336.34218\✪OPEN✵FILE✪✓\x86\api-ms-win-crt-convert-l1-1-0.dll | executable | |
MD5:3E415147CCD7C712618868BDD7A200CD | SHA256:77B69E829BDC26C7B2474BE6B8A2382345B2957E23046897E40992A8157A7BA1 | |||
| 2336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2336.34218\✪OPEN✵FILE✪✓\x86\api-ms-win-core-util-l1-1-0.dll | executable | |
MD5:C6553959AECD5BAC01C0673CFDF86B68 | SHA256:68BD9C086D210EB14E78F00988BA88CEAF9056C8F10746AB024990F8512A2296 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
699
DNS requests
28
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3160 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3160 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6936 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6964 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
2536 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1076 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3160 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
2804 | SearchIndexer.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|