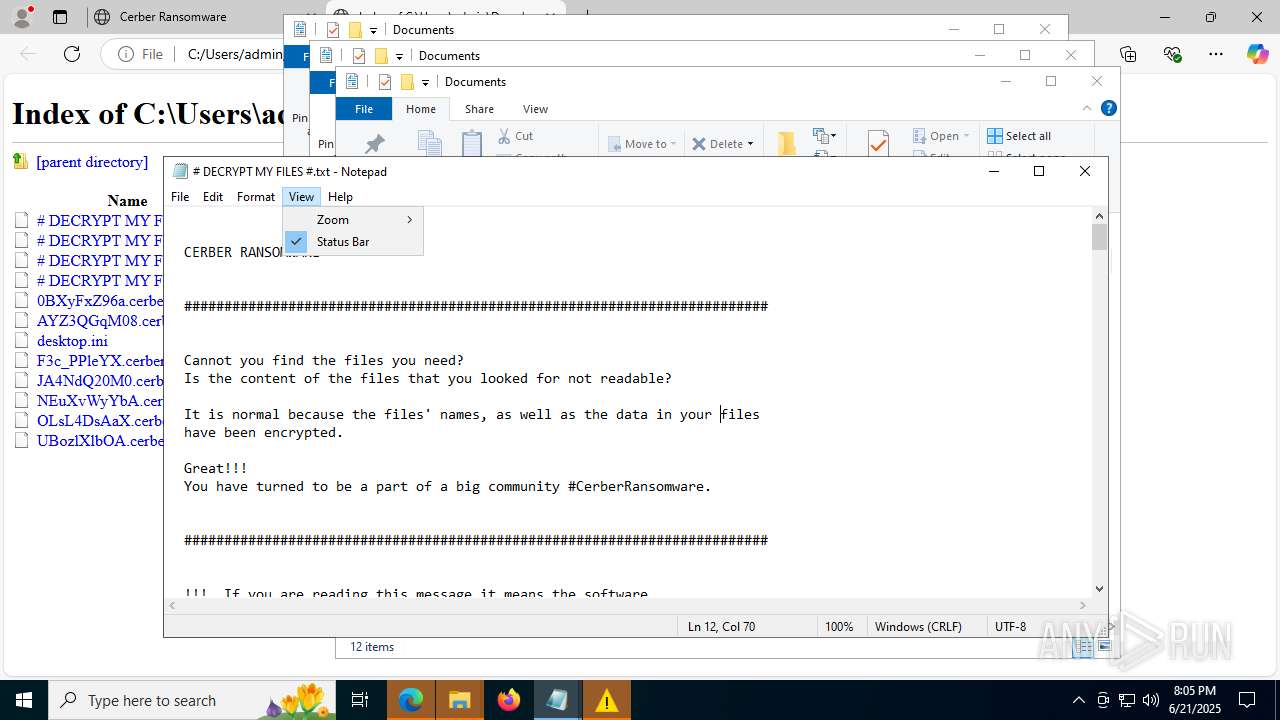
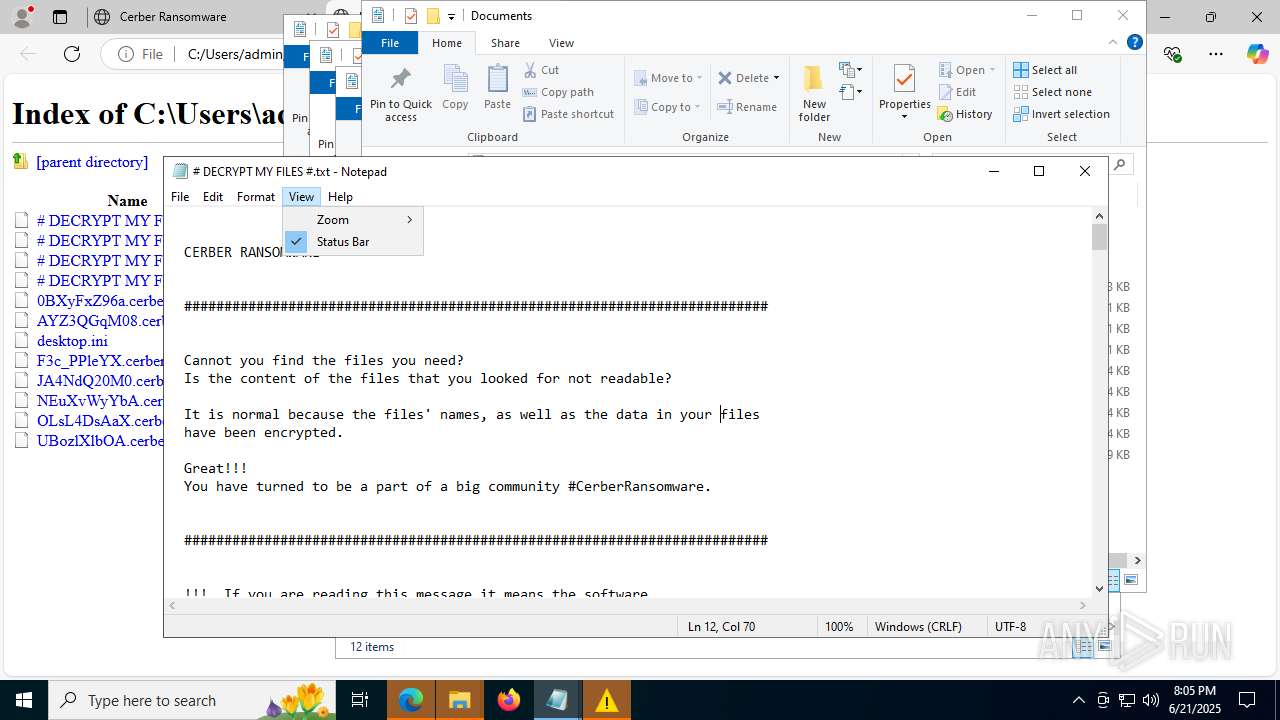
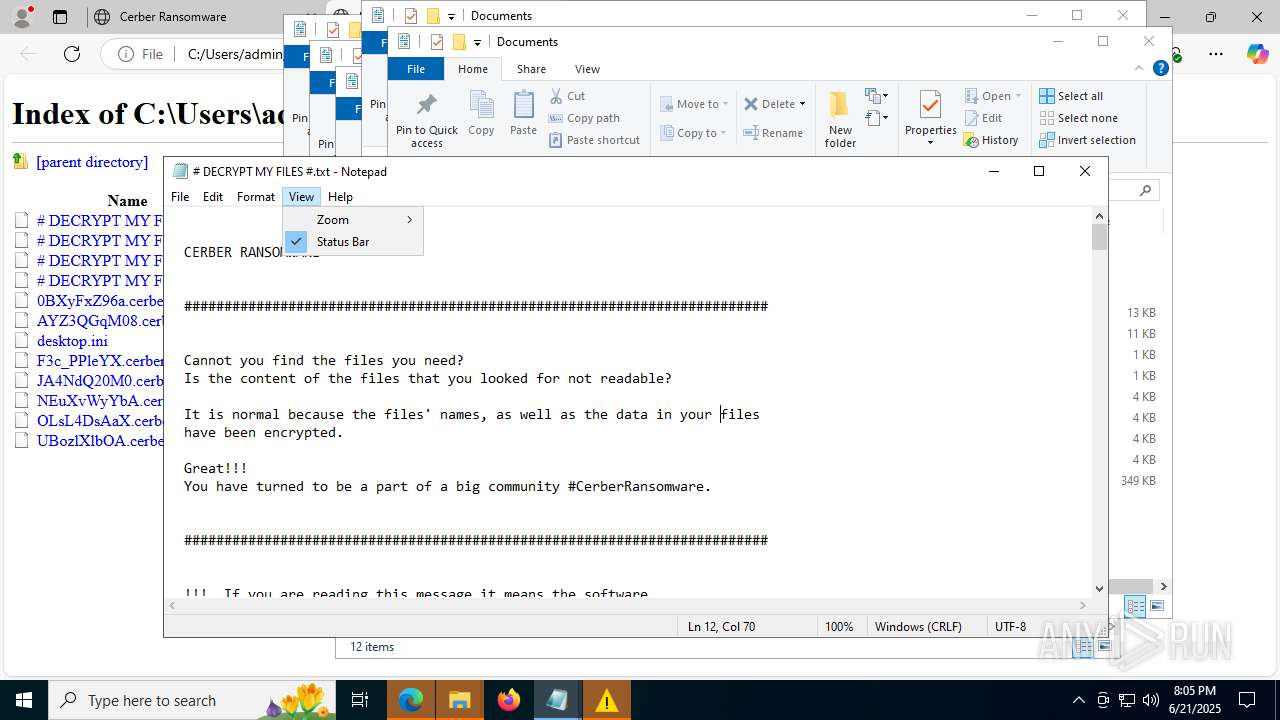
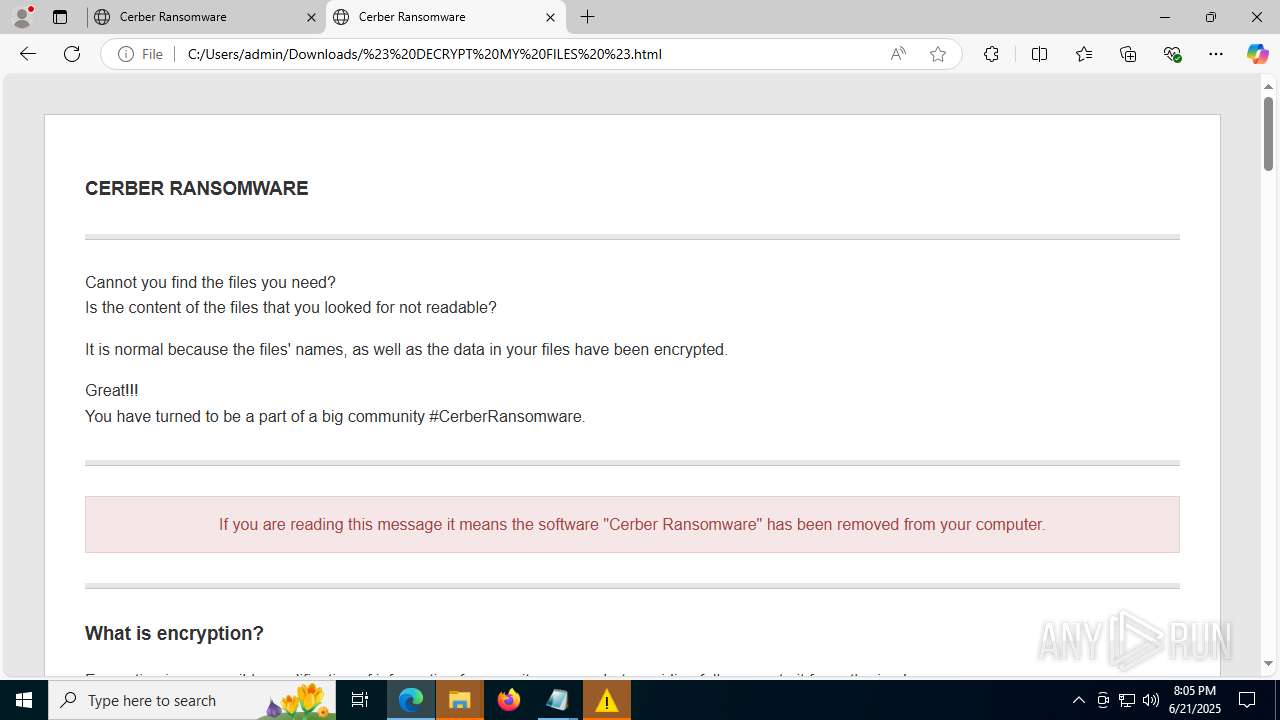
| File name: | 202405274612fbda398e6d7570975a3b122849d8cerber.exe |
| Full analysis: | https://app.any.run/tasks/ea6d22ce-12ad-481a-9dd8-e346e7790d67 |
| Verdict: | Malicious activity |
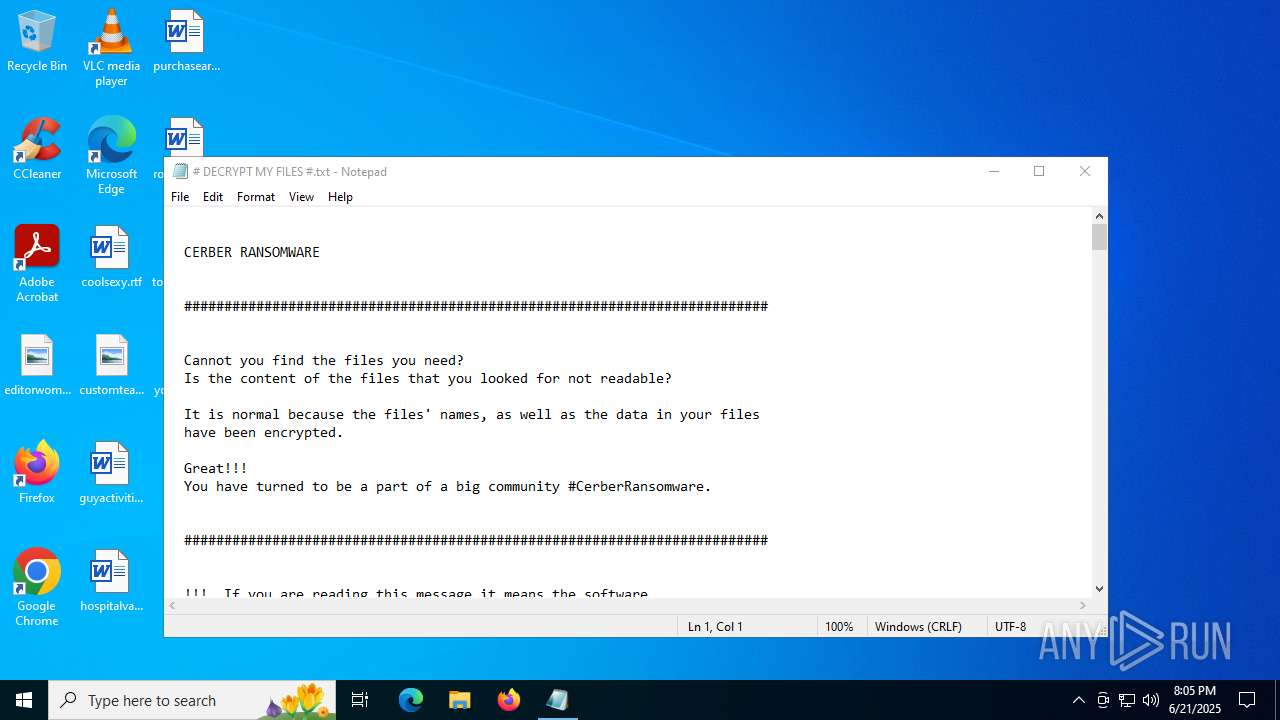
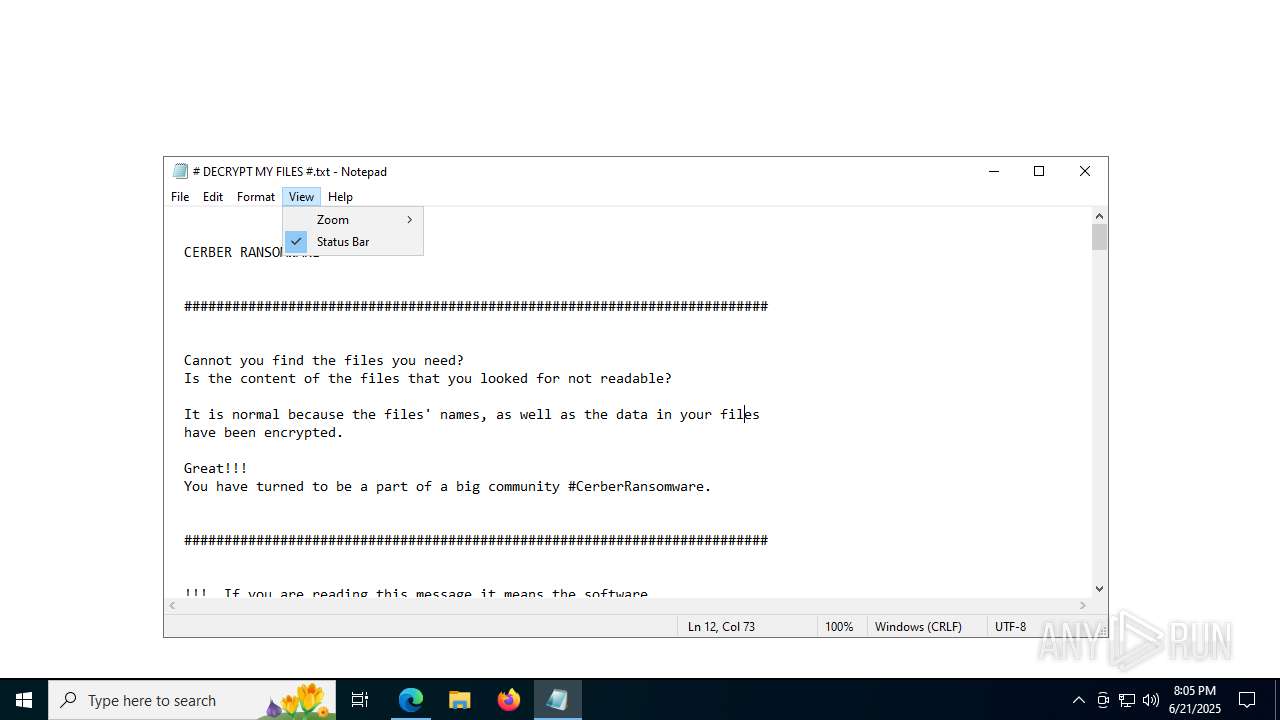
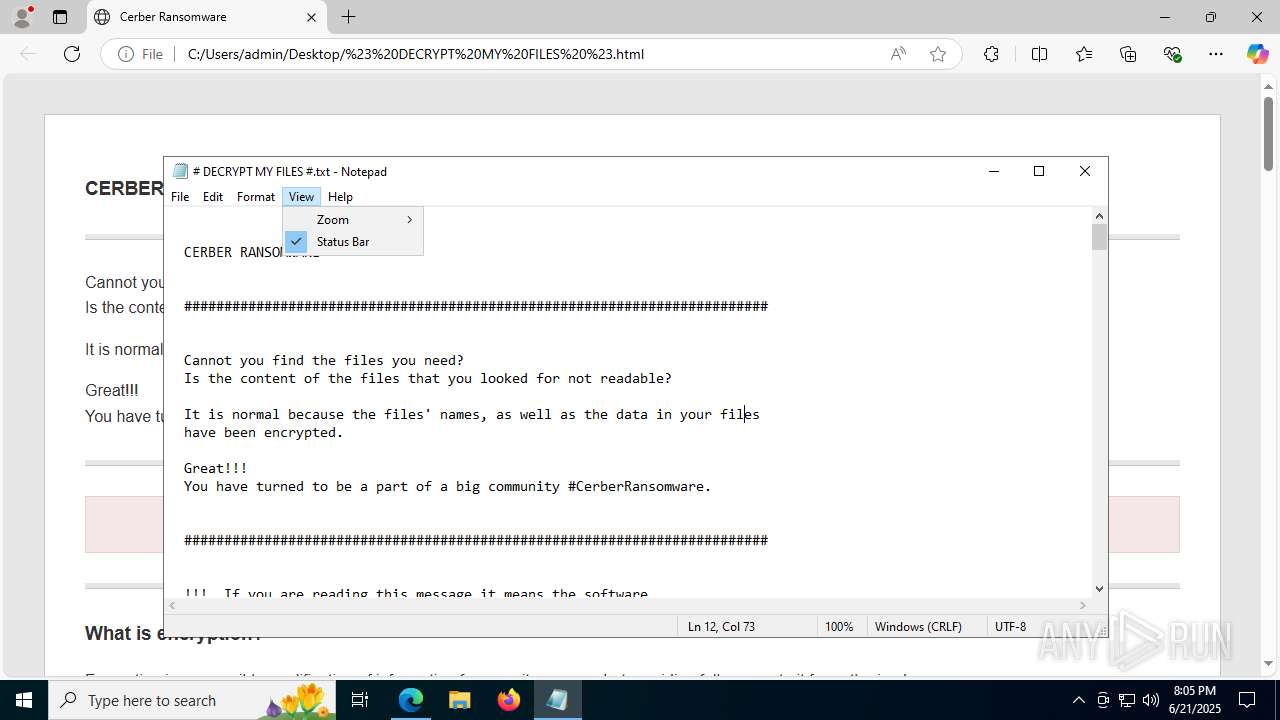
| Threats: | Cerber is a Ransomware-as-a-Service (RaaS) that appeared in 2016, spread quickly and has been evolving since. It became well-known for its file encryption, offline capabilities, and sophisticated evasion techniques. It primarily targets enterprises, financial institutions, and government entities, encrypting their data and demanding ransom payments in Bitcoin. It also targets everyday users encrypting personal files (photos, documents) with the risk of their permanent loss. |
| Analysis date: | June 21, 2025, 20:03:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 4612FBDA398E6D7570975A3B122849D8 |
| SHA1: | 0B044922439DE8838EB6C0DCF604C47DD36DD4DD |
| SHA256: | D7401ACBE93358AF3649A47F80A178DF497F699D8D430B8400B008DEC894B1B9 |
| SSDEEP: | 6144:gjOJQDMwfkHF1qUHyvBKF8+nRbNjb2s/jF9Ev:gBfkl1q2yv4F8+nRJX2H |
MALICIOUS
Changes the autorun value in the registry
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
- dtdump.exe (PID: 6636)
CERBER mutex has been found
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
- dtdump.exe (PID: 6636)
- dtdump.exe (PID: 3092)
- dtdump.exe (PID: 2296)
Create files in the Startup directory
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
The process uses screensaver hijack for persistence
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
- dtdump.exe (PID: 6636)
Starts CMD.EXE for self-deleting
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
- dtdump.exe (PID: 6636)
RANSOMWARE has been detected
- dtdump.exe (PID: 6636)
Deletes shadow copies
- dtdump.exe (PID: 6636)
SUSPICIOUS
Executable content was dropped or overwritten
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
Starts itself from another location
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
Hides command output
- cmd.exe (PID: 6176)
- cmd.exe (PID: 7760)
The executable file from the user directory is run by the CMD process
- dtdump.exe (PID: 6636)
Reads security settings of Internet Explorer
- dtdump.exe (PID: 6636)
- dtdump.exe (PID: 3092)
Starts CMD.EXE for commands execution
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
- dtdump.exe (PID: 3092)
- dtdump.exe (PID: 6636)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6176)
- cmd.exe (PID: 7760)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 6176)
- cmd.exe (PID: 7760)
Possibly a phishing URL contains email has been detected
- msedge.exe (PID: 5504)
- msedge.exe (PID: 356)
- msedge.exe (PID: 2292)
- msedge.exe (PID: 5780)
- iexplore.exe (PID: 6224)
Checks for external IP
- svchost.exe (PID: 2200)
- dtdump.exe (PID: 6636)
Creates file in the systems drive root
- dtdump.exe (PID: 6636)
There is functionality for taking screenshot (YARA)
- dtdump.exe (PID: 6636)
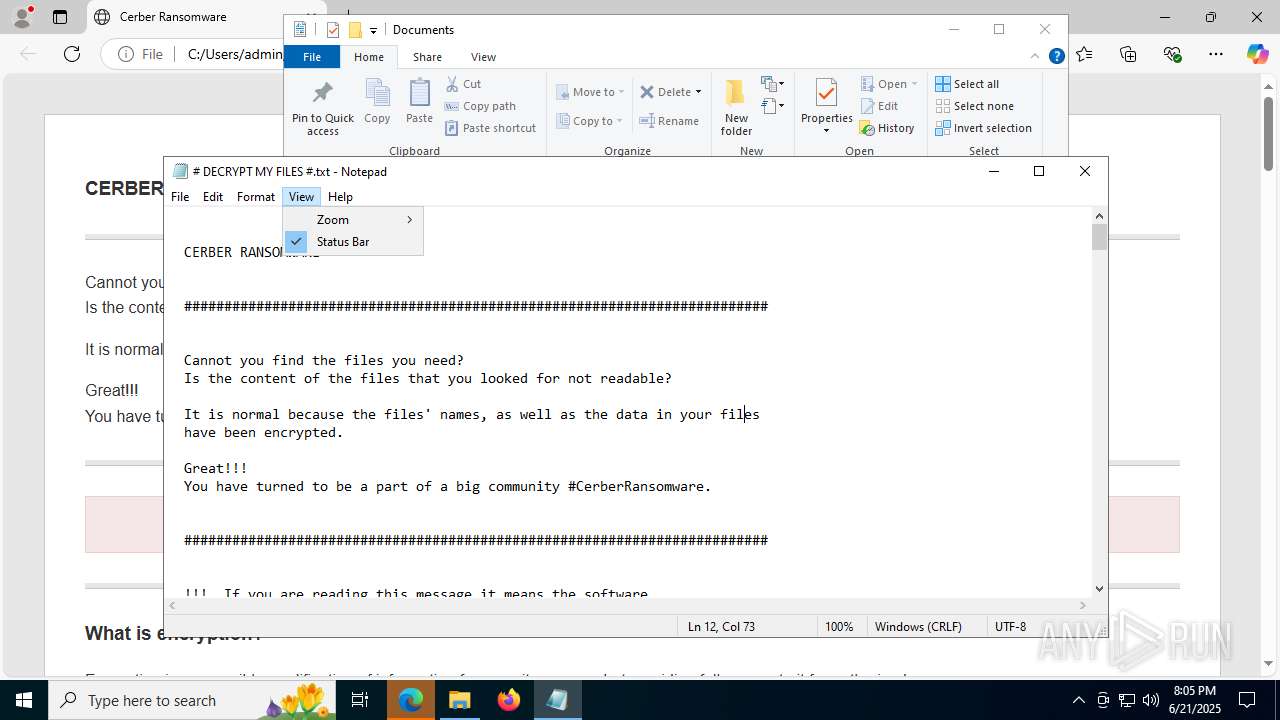
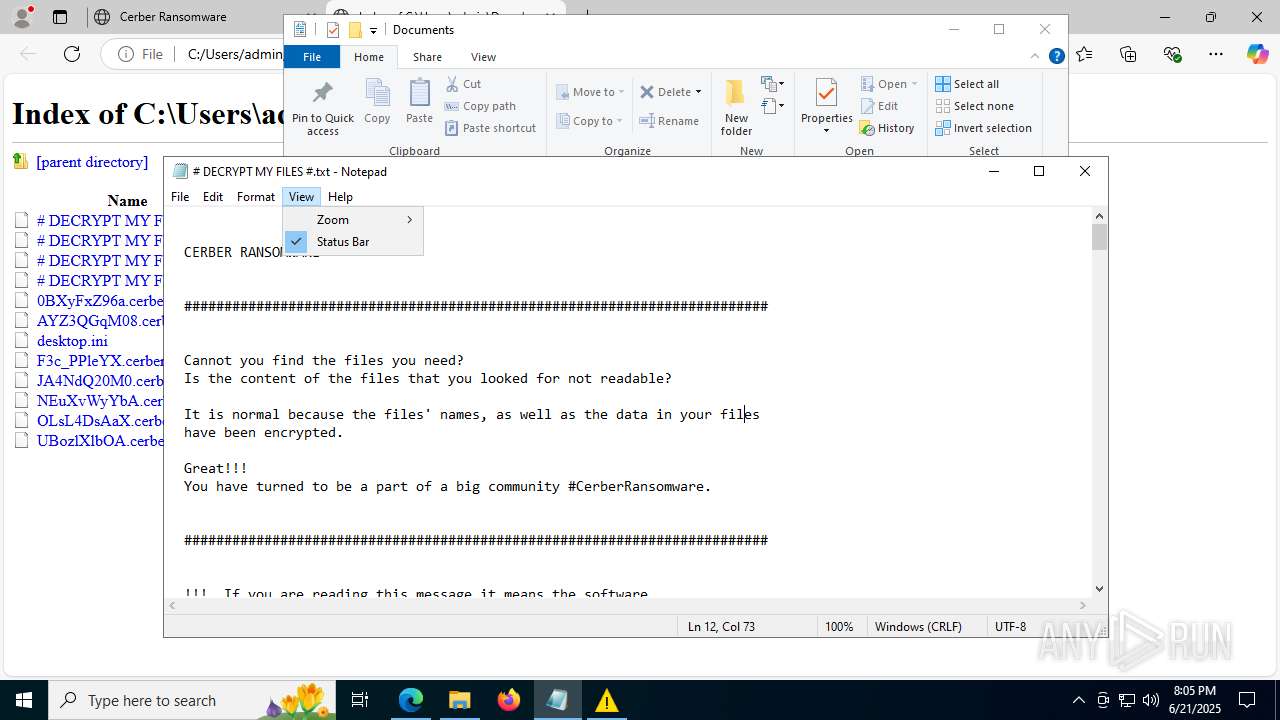
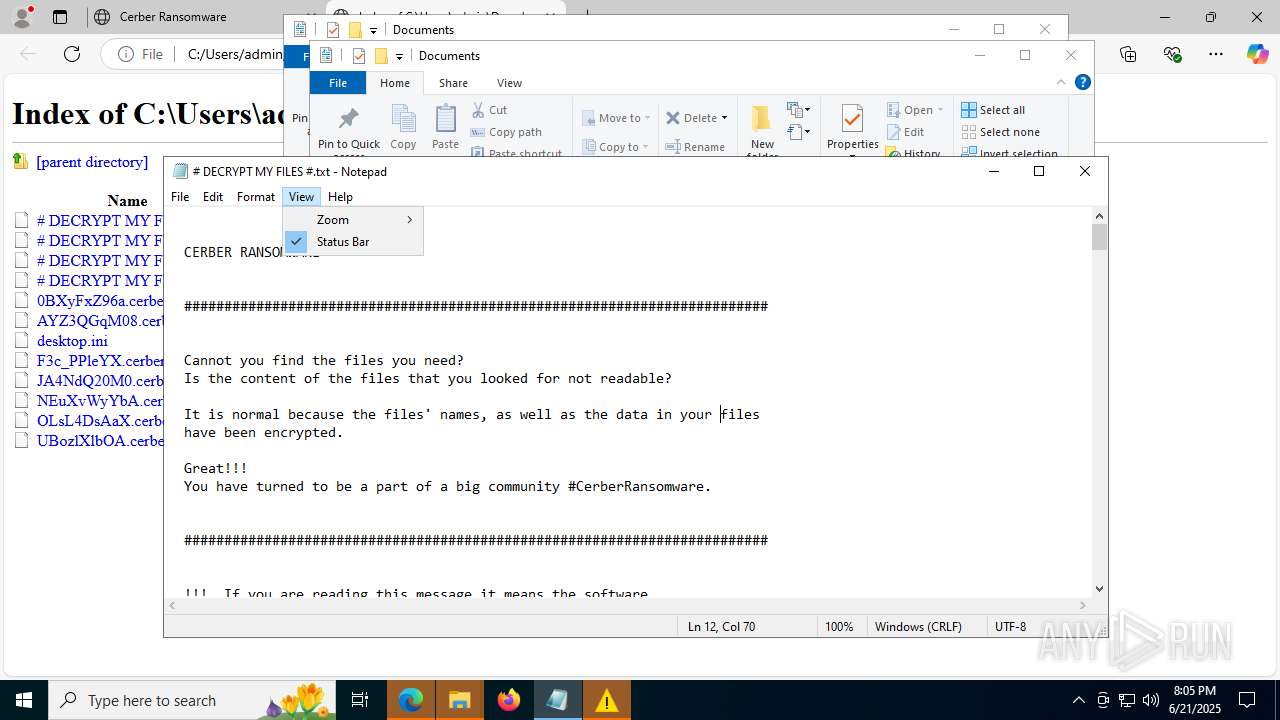
Start notepad (likely ransomware note)
- dtdump.exe (PID: 6636)
Executes as Windows Service
- VSSVC.exe (PID: 5400)
The process executes VB scripts
- dtdump.exe (PID: 6636)
INFO
The sample compiled with russian language support
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
Checks supported languages
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
- dtdump.exe (PID: 3092)
- dtdump.exe (PID: 6636)
- dtdump.exe (PID: 2296)
- identity_helper.exe (PID: 356)
Reads the machine GUID from the registry
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
Creates files or folders in the user directory
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
- dtdump.exe (PID: 6636)
Reads the computer name
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
- dtdump.exe (PID: 3092)
- dtdump.exe (PID: 6636)
- dtdump.exe (PID: 2296)
- identity_helper.exe (PID: 356)
Launching a file from the Startup directory
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
Launching a file from a Registry key
- 202405274612fbda398e6d7570975a3b122849d8cerber.exe (PID: 1068)
- dtdump.exe (PID: 6636)
Process checks whether UAC notifications are on
- dtdump.exe (PID: 3092)
Process checks computer location settings
- dtdump.exe (PID: 6636)
- dtdump.exe (PID: 3092)
Checks proxy server information
- dtdump.exe (PID: 6636)
- slui.exe (PID: 4832)
Manual execution by a user
- dtdump.exe (PID: 2296)
- msedge.exe (PID: 2292)
- rundll32.exe (PID: 3752)
- rundll32.exe (PID: 6104)
- rundll32.exe (PID: 7020)
- iexplore.exe (PID: 6224)
- wscript.exe (PID: 1740)
- rundll32.exe (PID: 7224)
- notepad.exe (PID: 7380)
- rundll32.exe (PID: 7592)
- rundll32.exe (PID: 7456)
- rundll32.exe (PID: 7948)
- rundll32.exe (PID: 7988)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 3624)
- notepad.exe (PID: 332)
- rundll32.exe (PID: 7020)
- notepad.exe (PID: 7380)
Application launched itself
- msedge.exe (PID: 5504)
- msedge.exe (PID: 356)
- msedge.exe (PID: 2292)
- msedge.exe (PID: 2188)
Reads Environment values
- identity_helper.exe (PID: 356)
Reads the software policy settings
- slui.exe (PID: 4832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:05:30 07:36:51+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 150016 |
| InitializedDataSize: | 30720 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x52b0 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.2.3.51 |
| ProductVersionNumber: | 3.2.3.51 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Russian |
| CharacterSet: | Unicode |
| Comments: | Выгрузчик Punto Switcher |
| CompanyName: | О ОО Яндекс |
| FileDescription: | Выгрузчик Punto Switcher |
| FileVersion: | 3.2.3.51 |
| InternalName: | Punto Switcher Unloader |
| LegalCopyright: | Copyright 2008-2011 ООО Яндекс |
| LegalTrademarks: | Punto Switcher |
| OriginalFileName: | puntounloader.exe |
| ProductName: | Punto Switcher |
| ProductVersion: | 3.2.3.51 |
Total processes
197
Monitored processes
60
Malicious processes
5
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | vssadmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 332 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\# DECRYPT MY FILES #.txt | C:\Windows\System32\notepad.exe | — | dtdump.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 356 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --edge-skip-compat-layer-relaunch --single-argument C:\Users\admin\Desktop\# DECRYPT MY FILES #.html | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 1 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 356 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5784,i,14207295588287870977,2905952343935511052,262144 --variations-seed-version --mojo-platform-channel-handle=5872 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1068 | "C:\Users\admin\Desktop\202405274612fbda398e6d7570975a3b122849d8cerber.exe" | C:\Users\admin\Desktop\202405274612fbda398e6d7570975a3b122849d8cerber.exe | explorer.exe | ||||||||||||
User: admin Company: О ОО Яндекс Integrity Level: MEDIUM Description: Выгрузчик Punto Switcher Exit code: 0 Version: 3.2.3.51 Modules
| |||||||||||||||
| 1296 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5784,i,14207295588287870977,2905952343935511052,262144 --variations-seed-version --mojo-platform-channel-handle=5872 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1604 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=3724,i,14207295588287870977,2905952343935511052,262144 --variations-seed-version --mojo-platform-channel-handle=4188 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1740 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Downloads\# DECRYPT MY FILES #.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1868 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3616,i,14207295588287870977,2905952343935511052,262144 --variations-seed-version --mojo-platform-channel-handle=3596 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2072 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5092,i,14207295588287870977,2905952343935511052,262144 --variations-seed-version --mojo-platform-channel-handle=3480 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
16 820
Read events
16 536
Write events
280
Delete events
4
Modification events
| (PID) Process: | (1068) 202405274612fbda398e6d7570975a3b122849d8cerber.exe | Key: | HKEY_CURRENT_USER\Printers\Defaults\{4300906E-252F-DD84-8300-59D7201E9E37} |
| Operation: | write | Name: | Component_01 |
Value: 424E4B714A706836377168424B7A642F4A6434497A78655A434571714B653871534942516F6C773766397464314235756B7451444A46556D71314C63356B45364E6C31415747323031464561745345364379674762354A6F4A575576526B726635712B564C30577A46777069714E4B774538667A4444384E584D6A6676392B4C6D5371375458754C576E447A396531656A3764654A41324758374B2F6863516E3042484B7236566A5968373863564B4F4D496677655A3276684F736E4876586474667277734E2B4D3651683145634A674A6C4F486D6B5072733361695346462B72647561596B7072786E6961786C48585A6654527352664F505A53762B64535372365332526275753530464F4A6C716C6676624E70445A497A36783475557A49443065445653686E43704D79636C4B50317A6373517761496236374D326D6C52304A65305935544A683258572F4662453663324447673D3D | |||
| (PID) Process: | (1068) 202405274612fbda398e6d7570975a3b122849d8cerber.exe | Key: | HKEY_CURRENT_USER\Printers\Defaults\{4300906E-252F-DD84-8300-59D7201E9E37} |
| Operation: | write | Name: | Component_00 |
Value: 9A04010126D2D6504002000001000000D4B20F5167B5FD37B3287D35600AFDD93BAB57AB00B2E719AF8F619FAACD8FC67B2BD0EAEAD81610EA254AF559FAC7081212A12ABA561F5964D63508E62207114C8F1A818ED9FD77000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010001 | |||
| (PID) Process: | (1068) 202405274612fbda398e6d7570975a3b122849d8cerber.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | dtdump |
Value: "C:\Users\admin\AppData\Roaming\{CF9A297B-AC74-EC8E-5C44-DEEA0D4DAE71}\dtdump.exe" | |||
| (PID) Process: | (1068) 202405274612fbda398e6d7570975a3b122849d8cerber.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | dtdump |
Value: "C:\Users\admin\AppData\Roaming\{CF9A297B-AC74-EC8E-5C44-DEEA0D4DAE71}\dtdump.exe" | |||
| (PID) Process: | (1068) 202405274612fbda398e6d7570975a3b122849d8cerber.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Command Processor |
| Operation: | write | Name: | AutoRun |
Value: "C:\Users\admin\AppData\Roaming\{CF9A297B-AC74-EC8E-5C44-DEEA0D4DAE71}\dtdump.exe" | |||
| (PID) Process: | (1068) 202405274612fbda398e6d7570975a3b122849d8cerber.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | SCRNSAVE.EXE |
Value: "C:\Users\admin\AppData\Roaming\{CF9A297B-AC74-EC8E-5C44-DEEA0D4DAE71}\dtdump.exe" | |||
| (PID) Process: | (3092) dtdump.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3092) dtdump.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3092) dtdump.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3092) dtdump.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
1
Suspicious files
250
Text files
106
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6636 | dtdump.exe | C:\Users\admin\Documents\# DECRYPT MY FILES #.vbs | text | |
MD5:E885E348F83D97DB3DEB82ED43A64EEB | SHA256:BF4B1B2372317EB80D719B452100E9538EA7D44F5E168A7E59D0AECFEBF5B660 | |||
| 6636 | dtdump.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\json[1].json | binary | |
MD5:1392DA3C9826D1020E5C00625394F223 | SHA256:4488827F93282D80B6A4E6053FDD9C181620E3F0DF6189FC22FF057D0A79FA44 | |||
| 6636 | dtdump.exe | C:\Users\admin\AppData\Roaming\Microsoft\Outlook\Outlook.srs | binary | |
MD5:E9AD5CEF9E2EC65EDCFA4534EE8275C1 | SHA256:1EA15F3322695EFAB519C640CBA6849F3860FD7954CF6912EA97CC7B06E851D9 | |||
| 6636 | dtdump.exe | C:\Users\admin\Documents\# DECRYPT MY FILES #.txt | text | |
MD5:FBD9692354D7F91F7FBC4062106DEF76 | SHA256:EB6023BBB5BEAEB621E177A0BDE1DDCBB5626F02A6AB824B1BB106C9E05FDD96 | |||
| 6636 | dtdump.exe | C:\Users\admin\AppData\Roaming\Microsoft\Outlook\hddfCLqUjW.cerber | binary | |
MD5:3E0CE8071E9BFD447787F04F7C1718E8 | SHA256:616A4E3B67177333E58371310CD9F6550669DD012CD4AF95E4B6102A298B309A | |||
| 6636 | dtdump.exe | C:\Users\admin\AppData\Roaming\Microsoft\Outlook\# DECRYPT MY FILES #.html | html | |
MD5:0B1E9666E65DED8695506891D39E1AA9 | SHA256:BC9E07DCF1DE73C5E2CF1CA6E1DA29A6D271433E532D09791757B7AE14A0F516 | |||
| 6636 | dtdump.exe | C:\Users\admin\Documents\modifiedfeed.rtf | binary | |
MD5:EFD12D9211BF3671E4C32FB41BD52F77 | SHA256:977AD5ABEA2FBEA2C35FBE6BE7CFA38CC36DD5B1983BA68C529800D108C81899 | |||
| 6636 | dtdump.exe | C:\Users\admin\AppData\Roaming\Microsoft\Outlook\Outlook.xml | binary | |
MD5:3E0CE8071E9BFD447787F04F7C1718E8 | SHA256:616A4E3B67177333E58371310CD9F6550669DD012CD4AF95E4B6102A298B309A | |||
| 6636 | dtdump.exe | C:\Users\admin\Documents\# DECRYPT MY FILES #.html | html | |
MD5:0B1E9666E65DED8695506891D39E1AA9 | SHA256:BC9E07DCF1DE73C5E2CF1CA6E1DA29A6D271433E532D09791757B7AE14A0F516 | |||
| 6636 | dtdump.exe | C:\Users\admin\Documents\Q41bX72czZ.cerber | binary | |
MD5:EFD12D9211BF3671E4C32FB41BD52F77 | SHA256:977AD5ABEA2FBEA2C35FBE6BE7CFA38CC36DD5B1983BA68C529800D108C81899 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
10 068
DNS requests
38
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.25.50.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.25.50.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1688 | RUXIMICS.exe | GET | 200 | 184.25.50.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1688 | RUXIMICS.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.131:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 40.126.31.131:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
6636 | dtdump.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io/json | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.69:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1688 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 184.25.50.8:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 184.25.50.8:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1688 | RUXIMICS.exe | 184.25.50.8:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ipinfo.io |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
6636 | dtdump.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ipinfo.io |