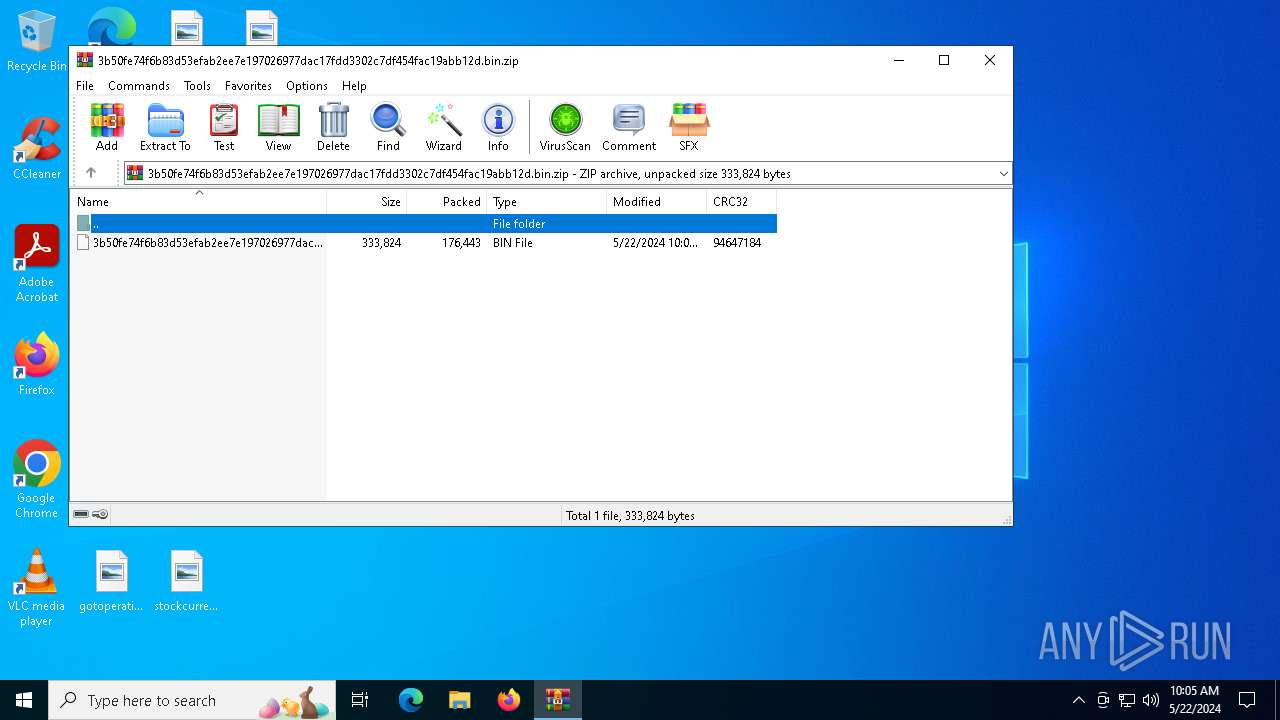
| File name: | 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.zip |
| Full analysis: | https://app.any.run/tasks/08944d07-920c-4607-aee7-3298d3caf649 |
| Verdict: | Malicious activity |
| Threats: | Fabookie is an infostealer malware that was first observed as early as October 2021. The threat is known for targeting account credentials of Facebook users. The collected information is then sold by the attackers to other criminals. Fabookie is often distributed via loaders such as SmokeLoader. |
| Analysis date: | May 22, 2024, 10:05:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
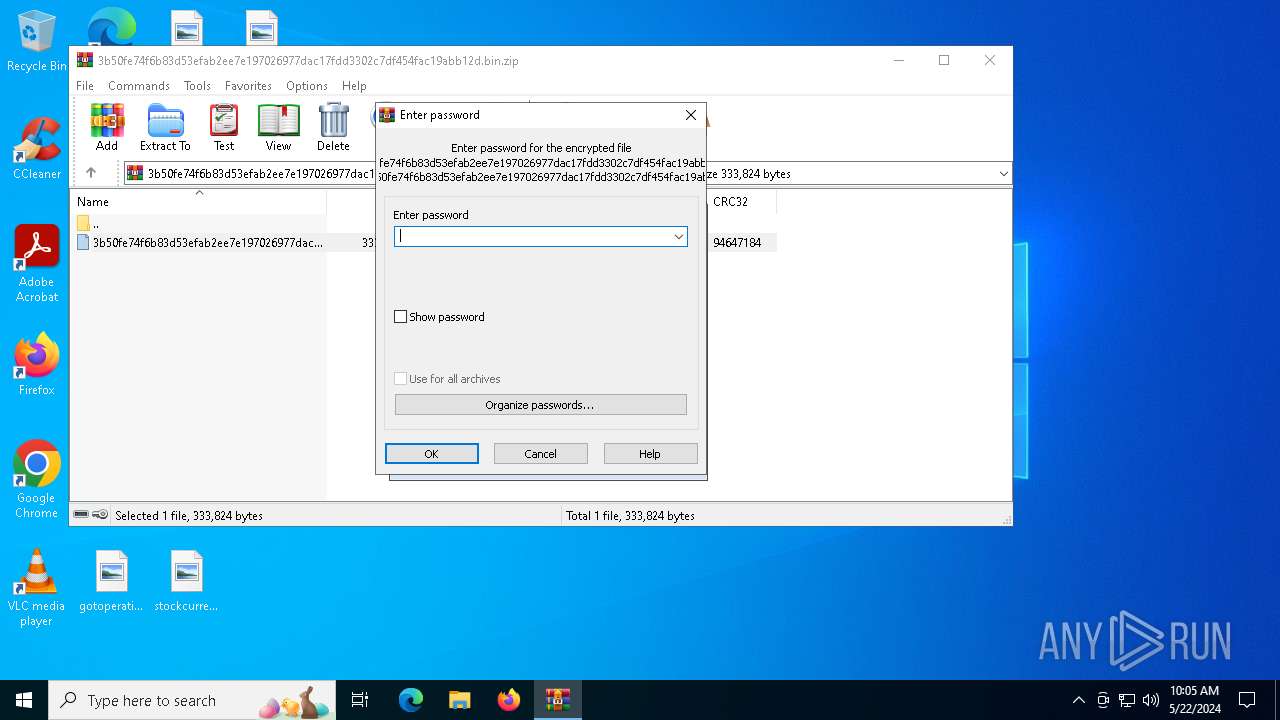
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | FC7CC4028B5BB9C5D5EA4D731803BC87 |
| SHA1: | 8E67A7365378B049CA42990B6EFB5AE4560C7750 |
| SHA256: | D705BB73BFA982782031FE88B19F1D1AEBF340A6CF206B2A203B90071169D440 |
| SSDEEP: | 6144:KLQM6JPBRaTNYfRhtcn51+0WiChi8pW46yjviHyuh:KkPBATm57y1+ji38s46yjaSuh |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6444)
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
Scans artifacts that could help determine the target
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
Creates a writable file in the system directory
- svchost.exe (PID: 6732)
- svchost.exe (PID: 6644)
SUSPICIOUS
Reads security settings of Internet Explorer
- TextInputHost.exe (PID: 6928)
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 7052)
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
Reads the date of Windows installation
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 7052)
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
Application launched itself
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 7052)
- svchost.exe (PID: 6596)
Executable content was dropped or overwritten
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 6196)
Starts CMD.EXE for commands execution
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 6196)
Process drops legitimate windows executable
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
Executes as Windows Service
- wmpnetwk.exe (PID: 5952)
- wmixedwk.exe (PID: 5380)
Creates file in the systems drive root
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
- cmd.exe (PID: 6620)
Executing commands from a ".bat" file
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
Starts SC.EXE for service management
- cmd.exe (PID: 6448)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 6620)
Process requests binary or script from the Internet
- WINWORD.EXE (PID: 1012)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6444)
Reads the computer name
- TextInputHost.exe (PID: 6928)
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 7052)
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
- wmpnetwk.exe (PID: 5952)
Checks supported languages
- TextInputHost.exe (PID: 6928)
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 7052)
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
- wmpnetwk.exe (PID: 5952)
- wmixedwk.exe (PID: 5380)
Checks proxy server information
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 7052)
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
Manual execution by a user
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 7052)
- mspaint.exe (PID: 1676)
- WINWORD.EXE (PID: 1012)
Creates files or folders in the user directory
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 7052)
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
Process checks computer location settings
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 7052)
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
Creates files in the program directory
- svchost.exe (PID: 6596)
- SearchIndexer.exe (PID: 6820)
- svchost.exe (PID: 6624)
- 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe (PID: 6236)
- svchost.exe (PID: 6732)
- svchost.exe (PID: 6644)
Executes as Windows Service
- SearchIndexer.exe (PID: 6820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:05:22 10:04:46 |
| ZipCRC: | 0x94647184 |
| ZipCompressedSize: | 176443 |
| ZipUncompressedSize: | 333824 |
| ZipFileName: | 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin |
Total processes
155
Monitored processes
24
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1012 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\responserentals.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1676 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\societysec.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3396 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "5E15320E-8C56-474C-BF94-433574EEEF5D" "9B45096D-6E7E-42F1-8260-664BE4FD90A4" "1012" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 4148 | takeown /f "C:\Program Files\Windows Media Player\wmpnetwk.exe" | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4480 | ping 127.0.0.1 -n 3 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4484 | sc create "Accecss Auto Connetcion Manager" binPath= "C:\Program Files\Windows Media Player\wmixedwk.exe" START= auto DISPLAYNAME= "WebServer" TYPE= own | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5108 | icacls "C:\Program Files\Windows Media Player\wmpnetwk.exe" /grant administrators:F | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5380 | "C:\Program Files\Windows Media Player\wmixedwk.exe" | C:\Program Files\Windows Media Player\wmixedwk.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Antimalware Service Executable Exit code: 0 Version: 4.3.9600.16384 (winblue_rtm.130821-1623) Modules
| |||||||||||||||
| 5952 | "C:\Program Files\Windows Media Player\wmpnetwk.exe" | C:\Program Files\Windows Media Player\wmpnetwk.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Antimalware Service Executable Exit code: 0 Version: 4.3.9600.16384 (winblue_rtm.130821-1623) Modules
| |||||||||||||||
| 6196 | "C:\Windows\System32\cmd.exe" cmd /c takeown /f "C:\Program Files\Windows Media Player\wmpnetwk.exe" && icacls "C:\Program Files\Windows Media Player\wmpnetwk.exe" /grant administrators:F | C:\Windows\System32\cmd.exe | — | 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
30 398
Read events
29 935
Write events
408
Delete events
55
Modification events
| (PID) Process: | (6444) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6444) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6444) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6444) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.zip | |||
| (PID) Process: | (6444) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6444) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6444) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6444) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6444) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6444) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
5
Suspicious files
34
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6236 | 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\aaaaaaaa[1].jpg | — | |
MD5:— | SHA256:— | |||
| 6236 | 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe | C:\Program Files\Windows Media Player\mpsvc.dll | — | |
MD5:— | SHA256:— | |||
| 6236 | 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe | C:\Program Files\Windows Media Player\wmpnetwk.exe | — | |
MD5:— | SHA256:— | |||
| 6820 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\Windows.edb | — | |
MD5:— | SHA256:— | |||
| 6444 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6444.15250\3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin | executable | |
MD5:A59664F37C25EDAA69C39A65490ED3A9 | SHA256:3B50FE74F6B83D53EFAB2EE7E197026977DAC17FDD3302C7DF454FAC19ABB12D | |||
| 6236 | 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\xxxxxxxx[1].jpg | image | |
MD5:3200DC4E4F84ECA82267063AA1055D0C | SHA256:60EB602D492C656CBCC7BDB8A2520BE9815C4A5F1E21D0435CC2B60819970240 | |||
| 7052 | 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\xxxxxxxx[1].jpg | image | |
MD5:3200DC4E4F84ECA82267063AA1055D0C | SHA256:60EB602D492C656CBCC7BDB8A2520BE9815C4A5F1E21D0435CC2B60819970240 | |||
| 1012 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:764BE25B93441A1C2532D7C862EF9721 | SHA256:3E011D2D16AC79D92340A41FE42FEE7EF274A0A468FE00E2BB382E679B1AC438 | |||
| 1012 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json | — | |
MD5:— | SHA256:— | |||
| 1012 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\5475cb191e478c39370a215b2da98a37e9dc813d.tbres | binary | |
MD5:71CA4EFA71AE0A9C0D55467625630164 | SHA256:8134F276C6D260312B8774EADEE45601C707C92FA50110E36205ECA07325BA9D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
74
TCP/UDP connections
67
DNS requests
27
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.100.146.17:443 | https://r.bing.com/rb/17/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DygxeIQBhwGKAYEBe369AcABMbABMcMB&or=w | unknown | — | 21.3 Kb | unknown |
— | — | GET | 200 | 95.100.146.17:443 | https://r.bing.com/rb/1a/cir3,ortl,cc,nc/oT6Um3bDKq3bSDJ4e0e-YJ5MXCI.css?bu=B68CP54ChwFZWbkC&or=w | unknown | — | 5.88 Kb | unknown |
7052 | 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe | GET | 200 | 103.146.158.221:80 | http://sta.alie3ksgee.com/xxxxxxxx.jpg | unknown | — | — | unknown |
6236 | 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe | GET | 200 | 103.146.158.221:80 | http://sta.alie3ksgee.com/xxxxxxxx.jpg | unknown | — | — | unknown |
— | — | GET | 200 | 95.100.146.35:443 | https://r.bing.com/rb/3J/ortl,cc,nc/4-xJy3tX6bM2BGl5zKioiEcQ1TU.css?bu=A4gCjAKPAg&or=w | unknown | — | 15.5 Kb | unknown |
6236 | 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe | GET | 200 | 103.146.158.221:80 | http://sta.alie3ksgee.com/aaaaaaaa.jpg | unknown | — | — | unknown |
— | — | GET | 200 | 95.100.146.35:443 | https://r.bing.com/rb/6t/cir3,ortl,cc,nc/nKv8Dr5AaiEnGKVhQG5dLl1N7PA.css?bu=MbEKqwq3CqsKmwurCqELqwqpC6sKsAurCrYLqwq8C6sKwgurCskKqwrPCqsKwwqrCqsKkgurCt4KqwrkCqsK2AqrCuoK9Ar3CqsKqwqPC_0KqwqDC4YLqwrsC6sKyAurCpoM&or=w | unknown | — | 443 Kb | unknown |
— | — | GET | 200 | 95.100.146.34:443 | https://r.bing.com/rb/6t/ortl,cc,nc/JmfAIE20nOCyQ3TY7bnLsgT0ICc.css?bu=CYcMqwqMDKsKkAyrCqsKqwqrCg&or=w | unknown | — | 428 Kb | unknown |
— | — | GET | 200 | 95.100.146.18:443 | https://r.bing.com/rb/6t/ortl,cc,nc/QNBBNqWD9F_Blep-UqQSqnMp-FI.css?bu=AasK&or=w | unknown | — | 6 b | unknown |
4680 | SearchApp.exe | GET | 200 | 95.100.146.8:443 | https://r.bing.com/rp/1Sd5265G8OlnRColAI8O_SxSQ1Q.br.js | unknown | text | 123 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4364 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
1324 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 184.86.251.27:443 | — | Akamai International B.V. | DE | unknown |
5140 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3396 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4680 | SearchApp.exe | 184.86.251.9:443 | — | Akamai International B.V. | DE | unknown |
7052 | 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe | 103.146.158.221:80 | sta.alie3ksgee.com | YISU CLOUD LTD | HK | unknown |
5456 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
sta.alie3ksgee.com |
| unknown |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
cl.alie3ksgff.com |
| unknown |
myxqbh.top |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7052 | 3b50fe74f6b83d53efab2ee7e197026977dac17fdd3302c7df454fac19abb12d.bin.exe | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] Suspicious User Agent HTTPREAD |
— | — | A Network Trojan was detected | PAYLOAD [ANY.RUN] Win32/Fabookie Jpeg Embeded Payload |
— | — | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] Suspicious User Agent HTTPREAD |
— | — | A Network Trojan was detected | PAYLOAD [ANY.RUN] Win32/Fabookie Jpeg Embeded Payload |
2184 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|