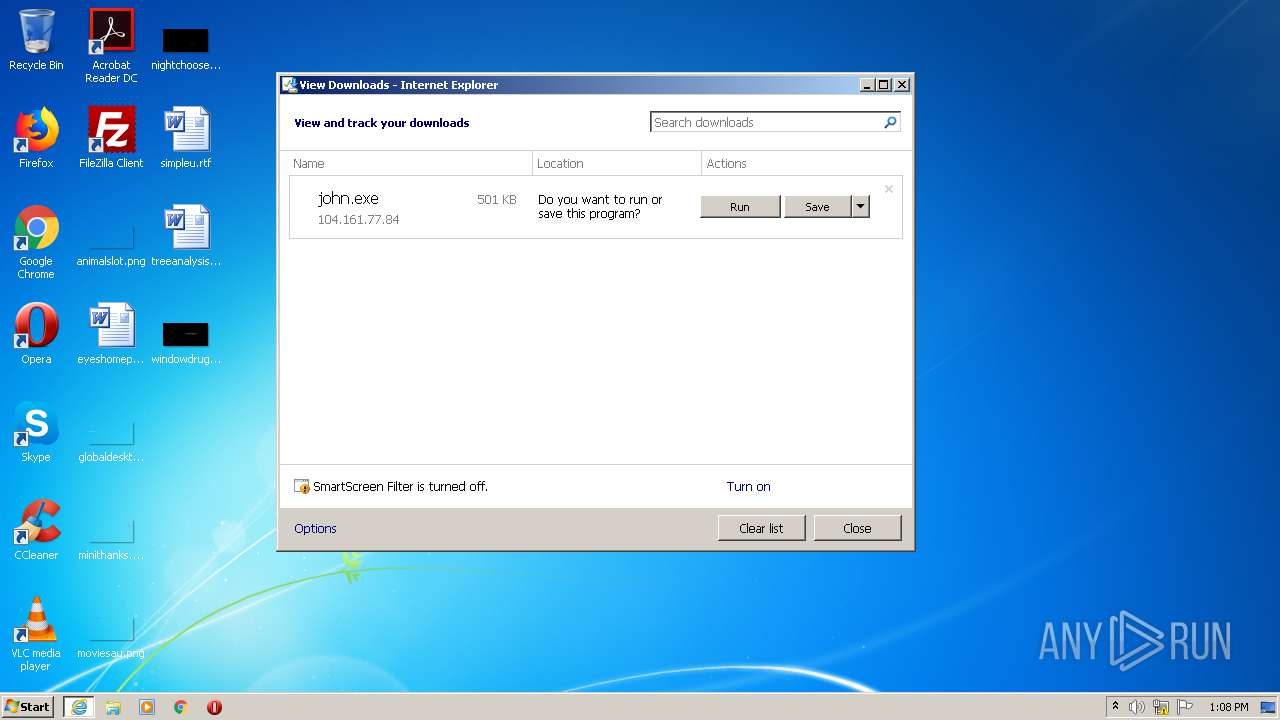
| URL: | http://104.161.77.84:444/john.exe |
| Full analysis: | https://app.any.run/tasks/c6cd799a-d45b-4e8e-b505-4d82552bec27 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | September 30, 2020, 12:08:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B4DBFBBEF70E821FB68FDAE950EE331E |
| SHA1: | 17A7F44C7A5EA565951F1D2FB708F3947251C53E |
| SHA256: | D6D6DB309A13D375592B1E0F87EE542EC781AFD5A23E2EA4AF978C7E2997A41A |
| SSDEEP: | 3:N1KtjX3uWgA:Cd+e |
MALICIOUS
Application was dropped or rewritten from another process
- john.exe (PID: 464)
FORMBOOK was detected
- explorer.exe (PID: 252)
Connects to CnC server
- explorer.exe (PID: 252)
SUSPICIOUS
Starts Internet Explorer
- explorer.exe (PID: 252)
Starts CMD.EXE for commands execution
- msdt.exe (PID: 2228)
Executable content was dropped or overwritten
- iexplore.exe (PID: 2560)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2560)
Reads Internet Cache Settings
- iexplore.exe (PID: 2500)
- iexplore.exe (PID: 2560)
Application launched itself
- iexplore.exe (PID: 2560)
Creates files in the user directory
- iexplore.exe (PID: 2560)
Reads settings of System Certificates
- iexplore.exe (PID: 2560)
Manual execution by user
- msdt.exe (PID: 2228)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2560)
Changes settings of System certificates
- iexplore.exe (PID: 2560)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
7
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 464 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\john.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\john.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2228 | "C:\Windows\System32\msdt.exe" | C:\Windows\System32\msdt.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2500 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2560 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2560 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://104.161.77.84:444/john.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2872 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | john.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 2936 | /c del "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\System32\cmd.exe | — | msdt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 131
Read events
1 053
Write events
76
Delete events
2
Modification events
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1930528190 | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30840610 | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2560) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
1
Suspicious files
10
Text files
3
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2500 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\john[1].exe | — | |
MD5:— | SHA256:— | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab29D0.tmp | — | |
MD5:— | SHA256:— | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar29D1.tmp | — | |
MD5:— | SHA256:— | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\ver2A11.tmp | — | |
MD5:— | SHA256:— | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\33CW68ED.txt | — | |
MD5:— | SHA256:— | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\AEWGB776.txt | — | |
MD5:— | SHA256:— | |||
| 2500 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\john.exe.793w7wd.partial | — | |
MD5:— | SHA256:— | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF80CC9D0D7CF63FA1.TMP | — | |
MD5:— | SHA256:— | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\john.exe.793w7wd.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\OTN6SOYE.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
39
DNS requests
20
Threats
58
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
252 | explorer.exe | GET | — | 69.172.201.153:80 | http://www.lightningbike.com/p980/?tXO0M08=FBKeSvp7onQKV7b9tHve3dSlExSIKs0hA7E01+iJ3AKnr6MyQ30O9/TUQmlG+/Ie9c5gGQ==&CTRL=ctYpLnzpaLcluBS | US | — | — | malicious |
2560 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2500 | iexplore.exe | GET | 200 | 104.161.77.84:444 | http://104.161.77.84:444/john.exe | US | executable | 501 Kb | suspicious |
252 | explorer.exe | GET | — | 34.102.136.180:80 | http://www.huntconsultant.com/p980/?tXO0M08=6CHzOIsBMaCsXJ3h+ZgOiZtst4QvrSCTIUtmDkn0A+tvz+PfaMwH0lBBdsgYQk8w4Kp2Rw==&CTRL=ctYpLnzpaLcluBS | US | — | — | whitelisted |
252 | explorer.exe | GET | 403 | 34.102.136.180:80 | http://www.huntconsultant.com/p980/?tXO0M08=6CHzOIsBMaCsXJ3h+ZgOiZtst4QvrSCTIUtmDkn0A+tvz+PfaMwH0lBBdsgYQk8w4Kp2Rw==&CTRL=ctYpLnzpaLcluBS | US | html | 275 b | whitelisted |
252 | explorer.exe | GET | 404 | 213.133.104.4:80 | http://www.attorneysiraq.com/p980/?tXO0M08=tYqSCMCJ6LFscm4s53os8Hrep7E2wdPn4ybGh9GaTDrTWHoVHvE63WO0kkUHu/rWIrCBjg==&CTRL=ctYpLnzpaLcluBS | DE | html | 267 b | malicious |
252 | explorer.exe | GET | — | 160.153.136.3:80 | http://www.knightsbridgehouse.com/p980/?tXO0M08=fyoDuifQhdZZRl7DxOqSWc1mjJu8Ki9OS5kWewfN9TiPpJHrL2zQ/CWSZAS9Wet7fZbQvg==&CTRL=ctYpLnzpaLcluBS | US | — | — | malicious |
252 | explorer.exe | GET | 403 | 34.102.136.180:80 | http://www.outthecancersurvey.net/p980/?tXO0M08=+UGxd3kJPDMtukD9iz+qY8kHlppX2iSMMRTGi8SHGh6Y+ujoFZyObrHyhbLGEGC8Ftsdqw==&CTRL=ctYpLnzpaLcluBS | US | html | 275 b | whitelisted |
252 | explorer.exe | GET | 403 | 34.98.99.30:80 | http://www.easysuperapp.com/p980/?tXO0M08=BSn40O5VgnjNebUHz93I31wzMhQRArzTbdmyLPL/PKK0Hxs6adjxJ6DKZd66duY6BV0oWQ==&CTRL=ctYpLnzpaLcluBS | US | html | 275 b | whitelisted |
1052 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2560 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2500 | iexplore.exe | 104.161.77.84:444 | — | Input Output Flood LLC | US | suspicious |
2560 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1052 | svchost.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2560 | iexplore.exe | 204.79.197.200:443 | ieonline.microsoft.com | Microsoft Corporation | US | whitelisted |
252 | explorer.exe | 46.23.69.44:80 | www.bigbucks4you.com | UK-2 Limited | GB | malicious |
252 | explorer.exe | 34.102.136.180:80 | www.huntconsultant.com | — | US | whitelisted |
252 | explorer.exe | 192.0.78.24:80 | www.cafebachthao.com | Automattic, Inc | US | malicious |
252 | explorer.exe | 45.142.156.48:80 | www.5918199.com | — | — | malicious |
252 | explorer.exe | 160.153.136.3:80 | www.knightsbridgehouse.com | GoDaddy.com, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
www.bigbucks4you.com |
| malicious |
www.huntconsultant.com |
| whitelisted |
www.cafebachthao.com |
| malicious |
www.5918199.com |
| malicious |
www.attorneysiraq.com |
| malicious |
www.knightsbridgehouse.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2500 | iexplore.exe | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
2500 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
252 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
252 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
252 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
252 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
252 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
252 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
252 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
252 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
28 ETPRO signatures available at the full report