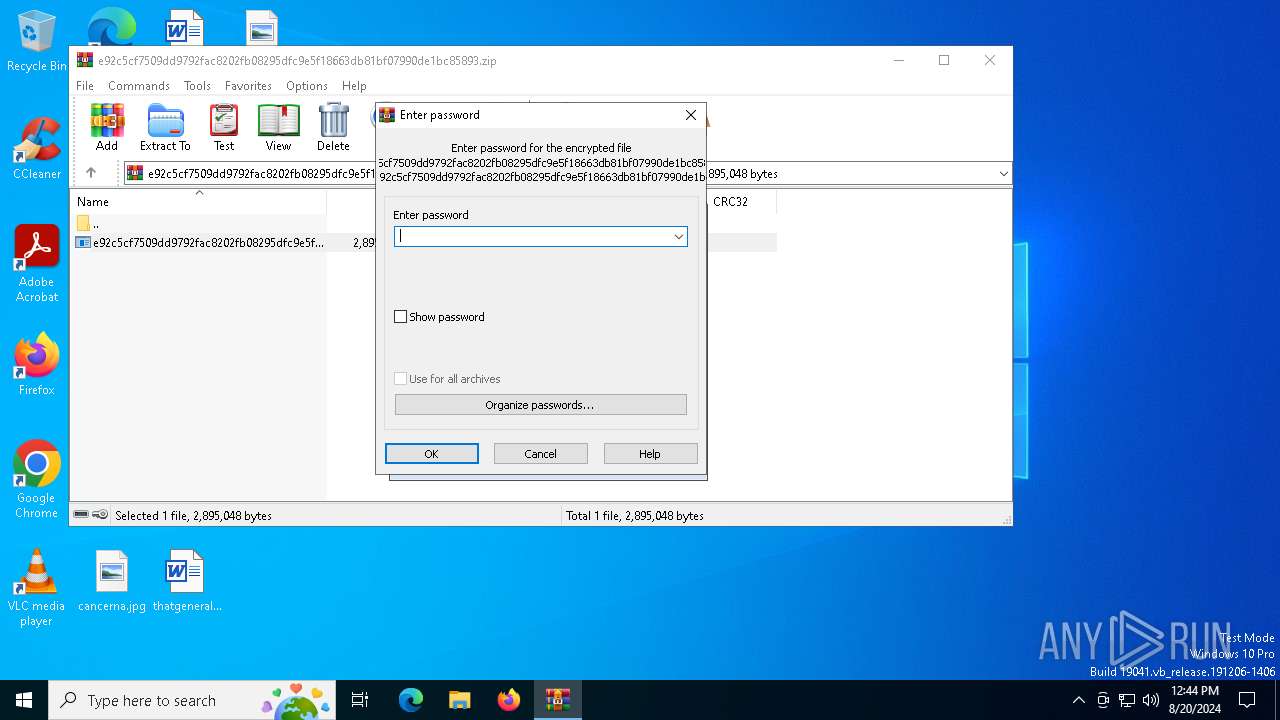
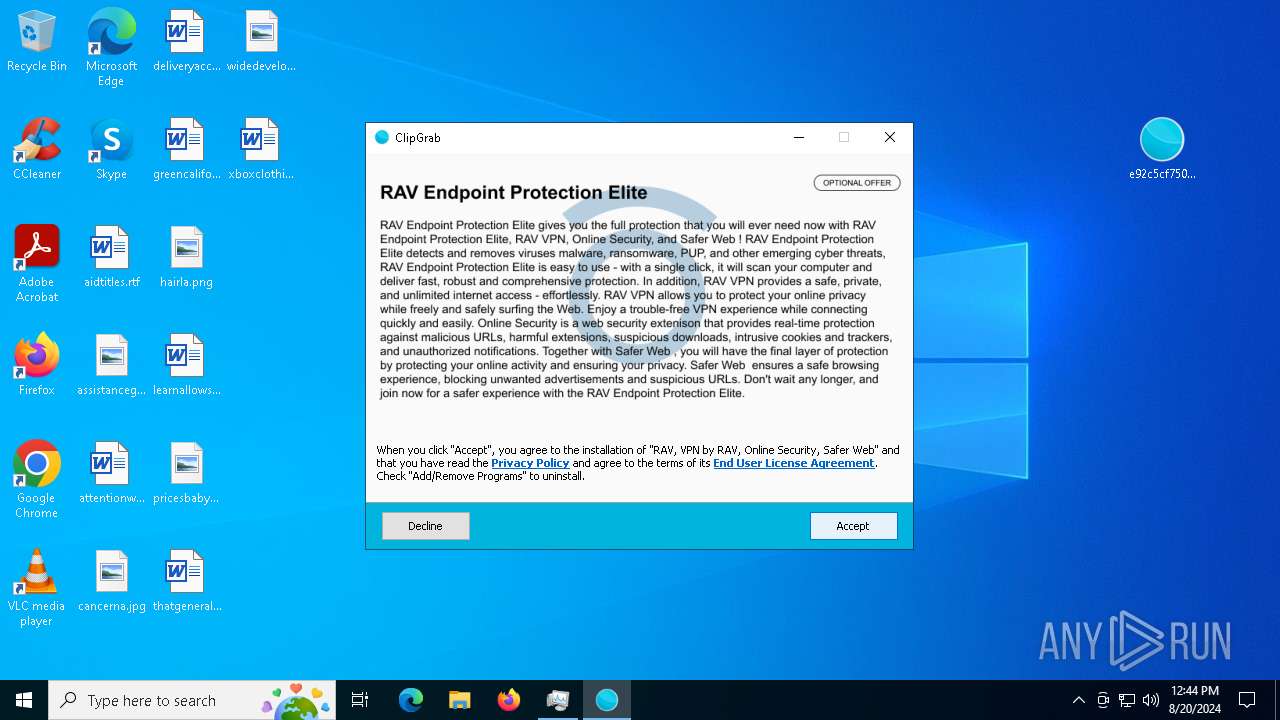
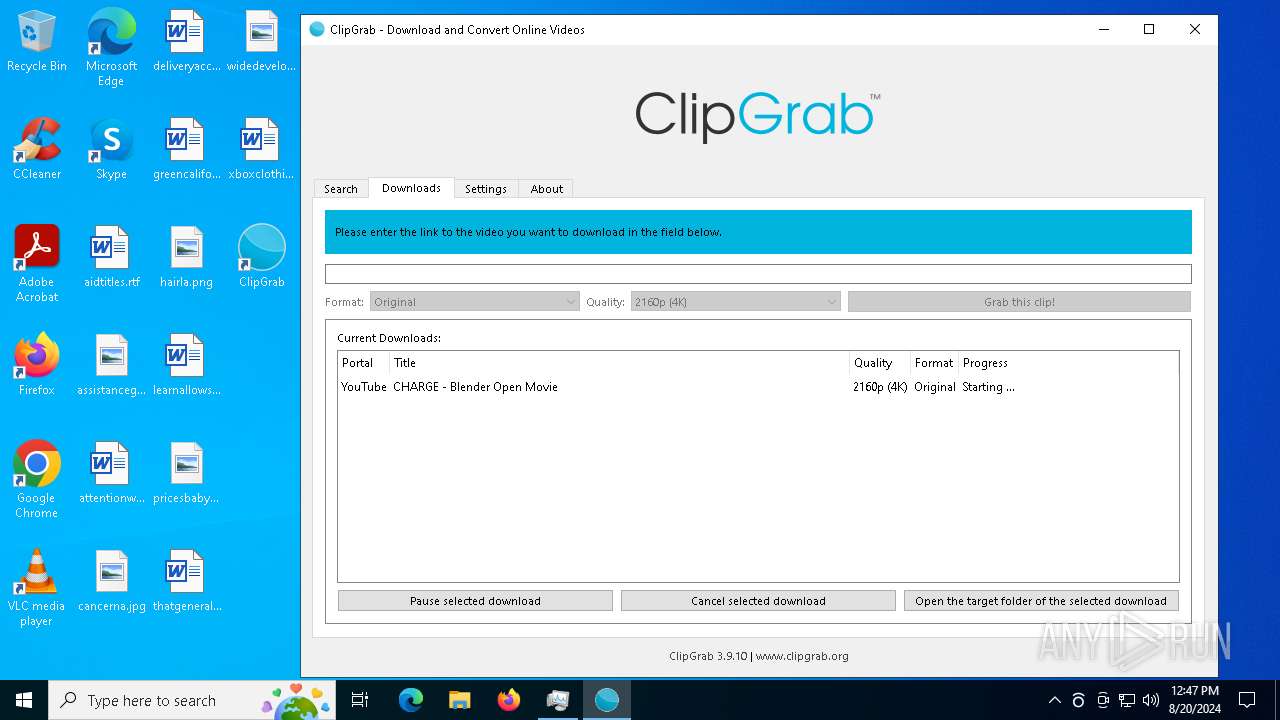
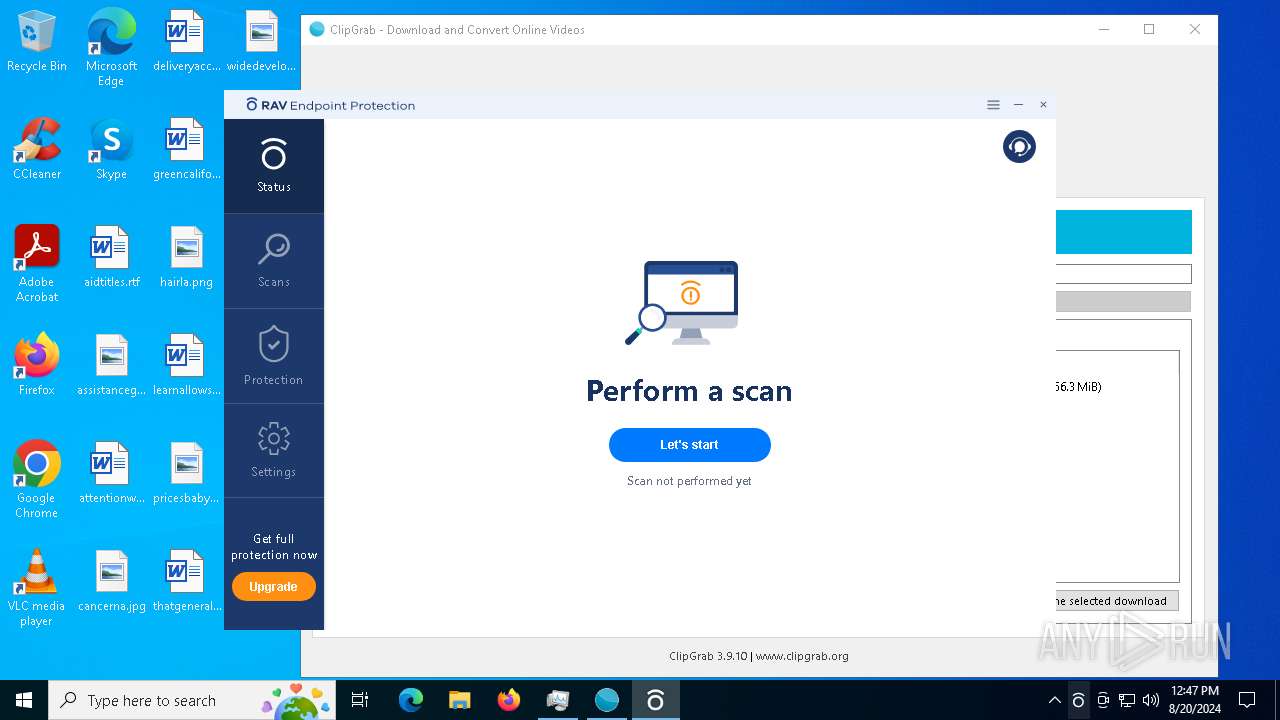
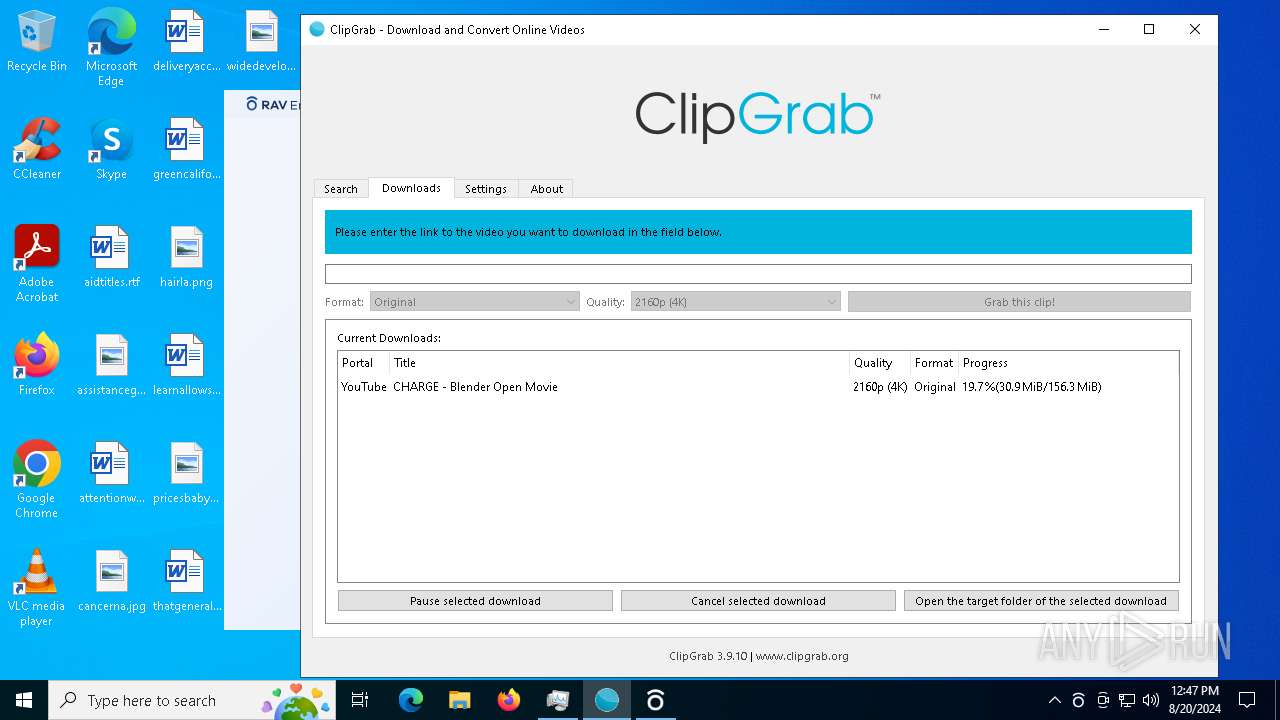
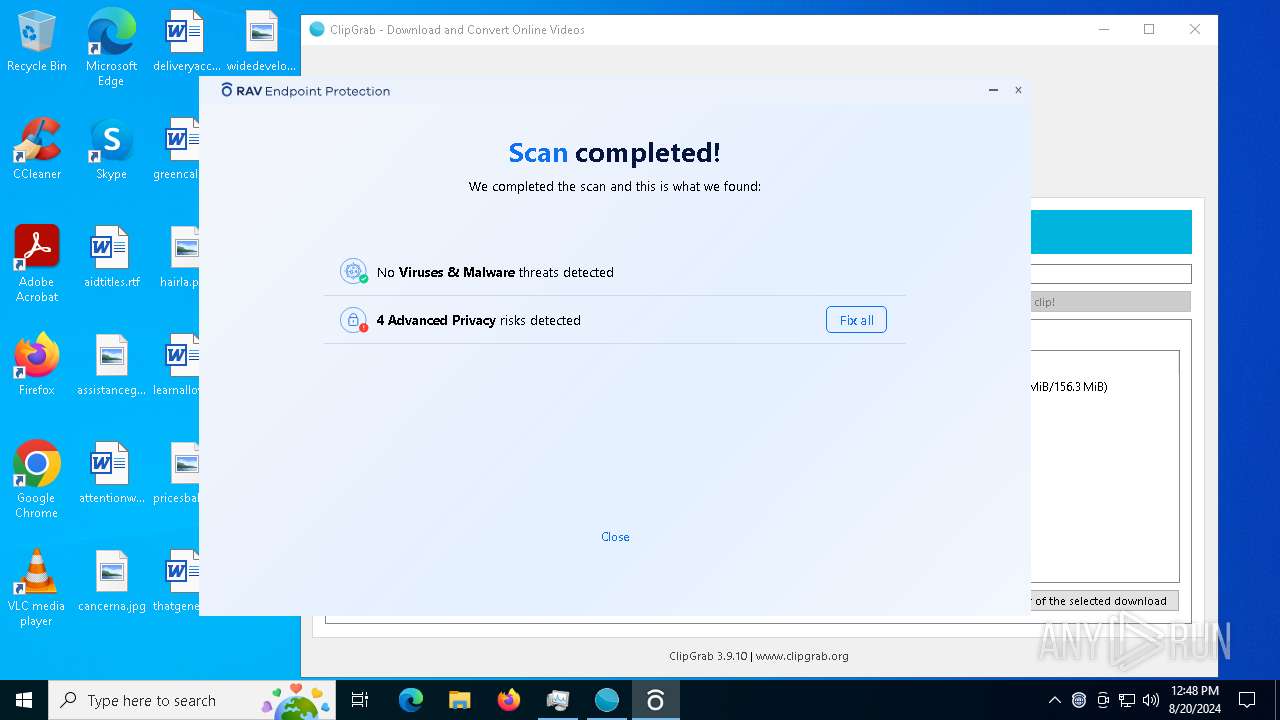
| URL: | https://bazaar.abuse.ch/sample/e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893/ |
| Full analysis: | https://app.any.run/tasks/eb377e1b-f5d6-4e4b-aee9-eec1f52e2474 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | August 20, 2024, 12:43:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 7776CF0AFB535A87BF0E2E520C83DC2A |
| SHA1: | 8EB84EC9B09ECFEAC6705D0FF0381A4D94770966 |
| SHA256: | D6BFBD119CC75EDE793F4ADF37AB61DB2C3FDED5866925D57B85473B47D9B907 |
| SSDEEP: | 3:N8N0uDWWLXHG/VIcIGThCWUdfWxdUjV8BwB:23pWzIGcTd+bUpQi |
MALICIOUS
Actions looks like stealing of personal data
- UnifiedStub-installer.exe (PID: 876)
- rsEngineSvc.exe (PID: 3140)
- rsVPNSvc.exe (PID: 8128)
- rsDNSSvc.exe (PID: 5372)
Changes the autorun value in the registry
- rundll32.exe (PID: 872)
- rundll32.exe (PID: 6104)
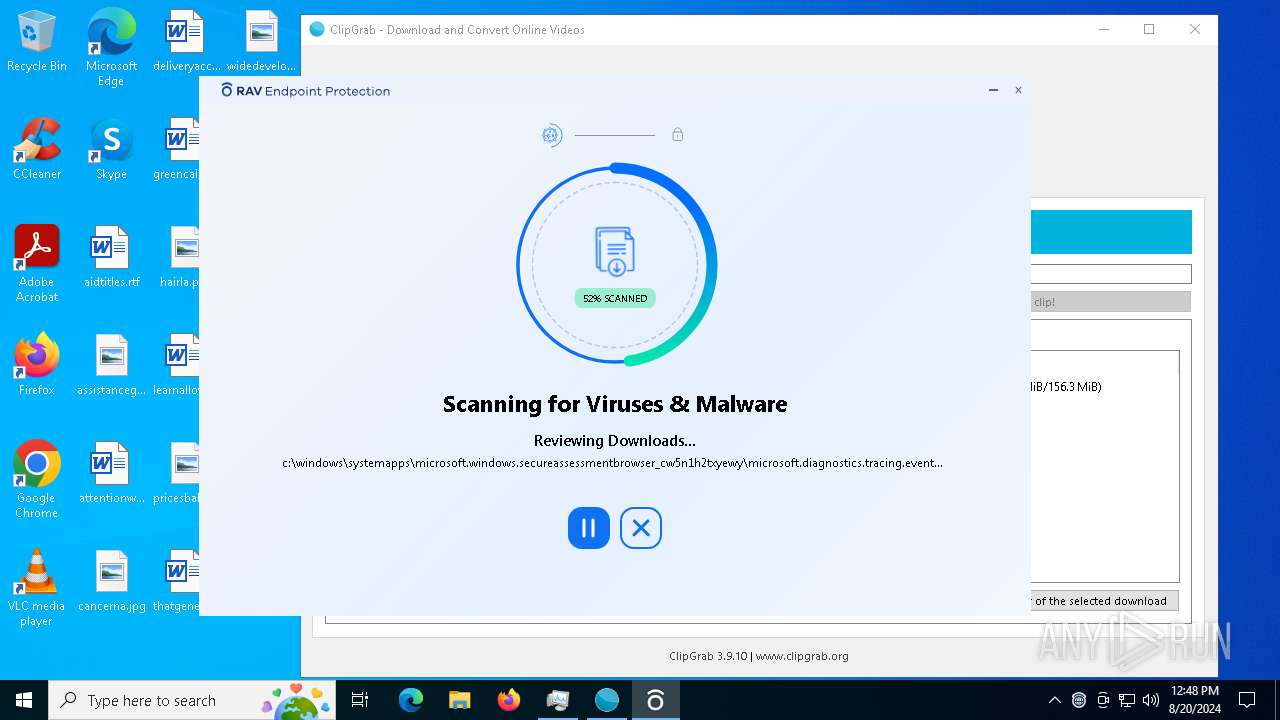
CYBERGATE has been detected (YARA)
- rsEngineSvc.exe (PID: 3140)
Steals credentials from Web Browsers
- rsEngineSvc.exe (PID: 3140)
SUSPICIOUS
Application launched itself
- Taskmgr.exe (PID: 7160)
- rsAppUI.exe (PID: 8168)
- rsAppUI.exe (PID: 4068)
- rsAppUI.exe (PID: 6332)
Executable content was dropped or overwritten
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.tmp (PID: 6832)
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.exe (PID: 4544)
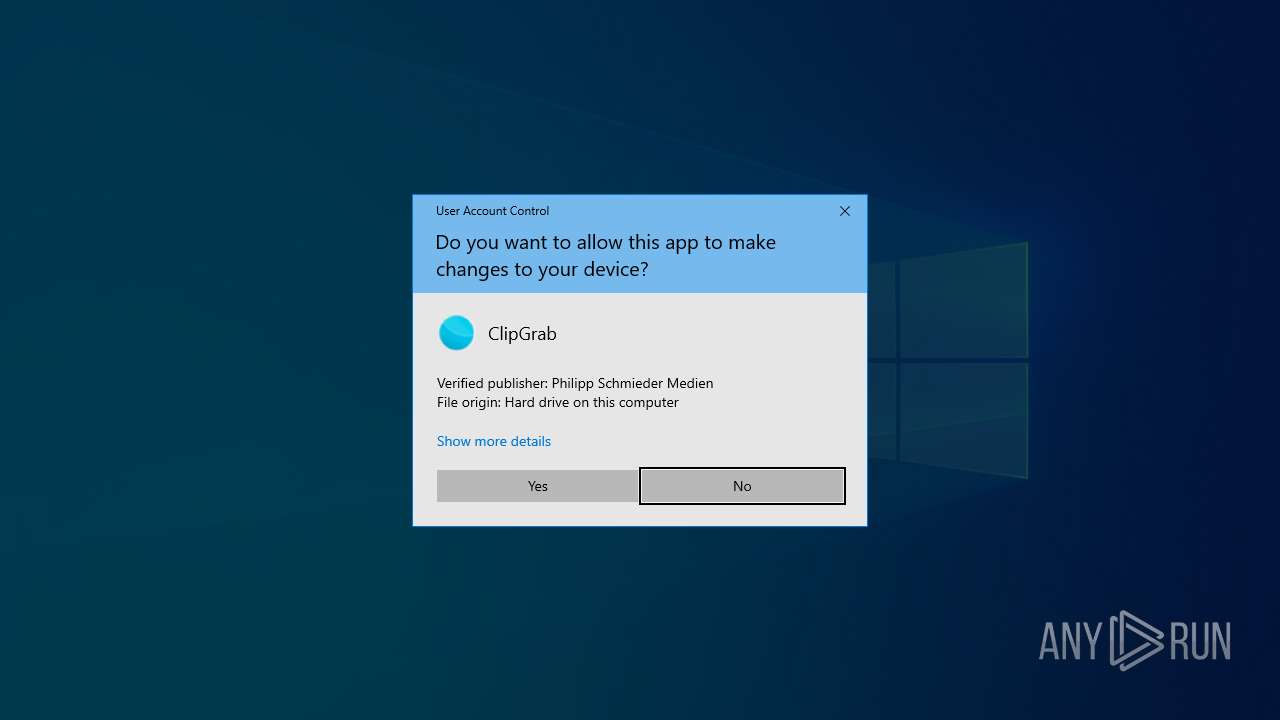
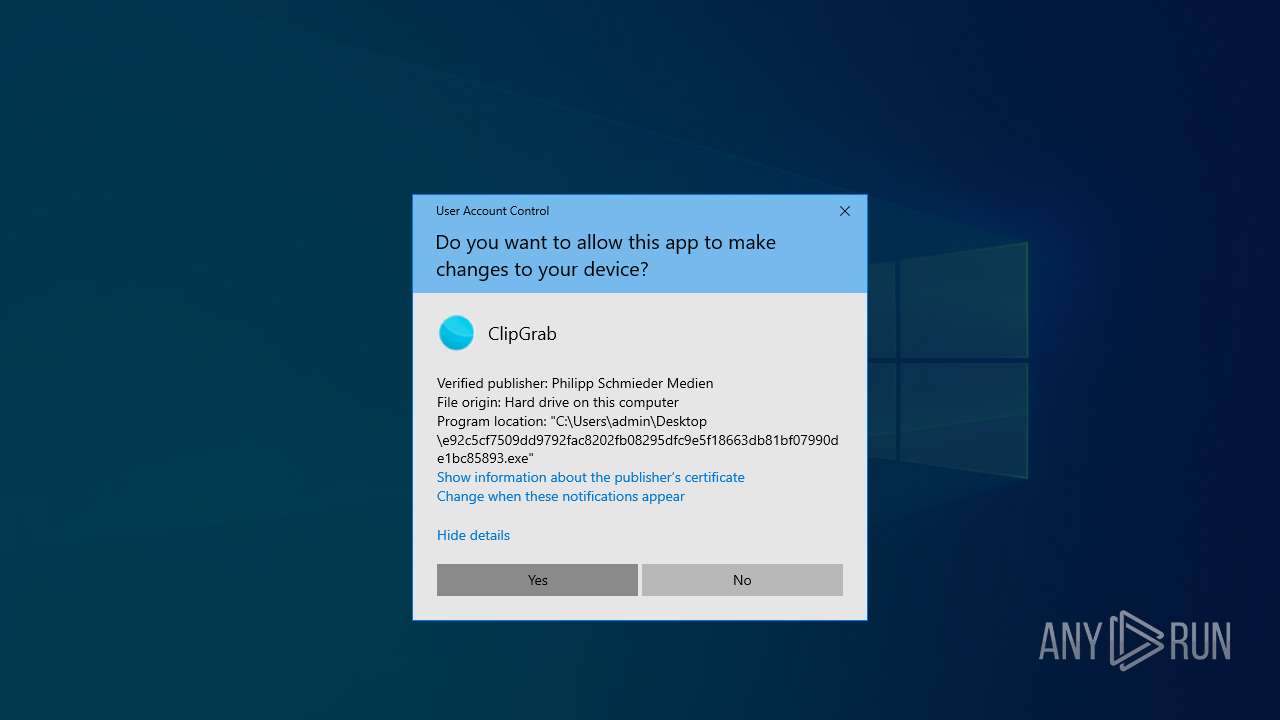
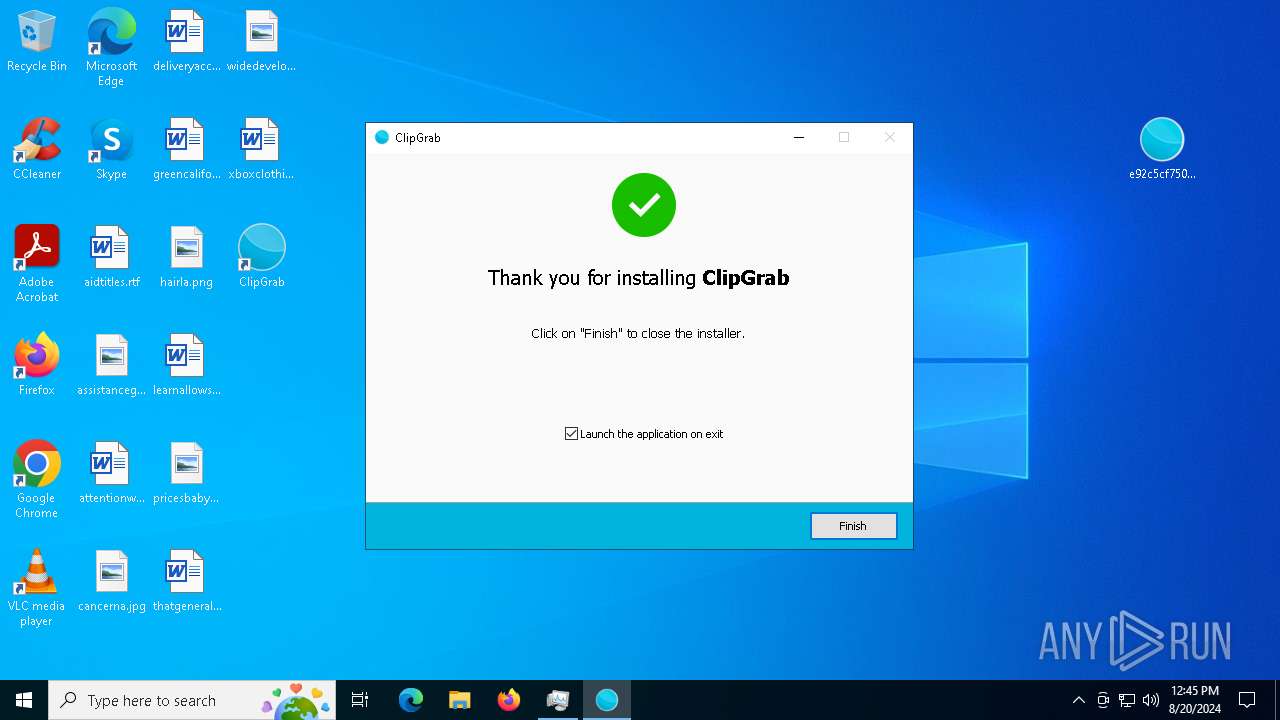
- clipgrab-3.9.10-portable.exe (PID: 6840)
- clipgrab-3.9.10-portable.tmp (PID: 6808)
- vc_redist.x86.exe (PID: 8080)
- vc_redist.x86.exe (PID: 3244)
- prod0.exe (PID: 8112)
- fztqbxpk.exe (PID: 7220)
- UnifiedStub-installer.exe (PID: 876)
Drops the executable file immediately after the start
- clipgrab-3.9.10-portable.exe (PID: 6840)
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.exe (PID: 4544)
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.tmp (PID: 6832)
- vc_redist.x86.exe (PID: 8080)
- clipgrab-3.9.10-portable.tmp (PID: 6808)
- vc_redist.x86.exe (PID: 3244)
- prod0.exe (PID: 8112)
- fztqbxpk.exe (PID: 7220)
- UnifiedStub-installer.exe (PID: 876)
Reads the Windows owner or organization settings
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.tmp (PID: 6832)
- clipgrab-3.9.10-portable.tmp (PID: 6808)
Process drops python dynamic module
- clipgrab-3.9.10-portable.tmp (PID: 6808)
The process drops C-runtime libraries
- clipgrab-3.9.10-portable.tmp (PID: 6808)
- UnifiedStub-installer.exe (PID: 876)
Process drops legitimate windows executable
- clipgrab-3.9.10-portable.tmp (PID: 6808)
- vc_redist.x86.exe (PID: 8080)
- fztqbxpk.exe (PID: 7220)
- UnifiedStub-installer.exe (PID: 876)
Starts a Microsoft application from unusual location
- vc_redist.x86.exe (PID: 8080)
- vc_redist.x86.exe (PID: 3244)
Reads security settings of Internet Explorer
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.tmp (PID: 6832)
- prod0.exe (PID: 8112)
- UnifiedStub-installer.exe (PID: 876)
- rsWSC.exe (PID: 5920)
- rsEngineSvc.exe (PID: 5500)
- rsEDRSvc.exe (PID: 7856)
- rsEngineSvc.exe (PID: 3140)
- clipgrab.exe (PID: 7624)
- rsVPNSvc.exe (PID: 8144)
- rsDNSSvc.exe (PID: 5288)
Reads the date of Windows installation
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.tmp (PID: 6832)
- prod0.exe (PID: 8112)
- rsEDRSvc.exe (PID: 7368)
- rsEngineSvc.exe (PID: 3140)
Searches for installed software
- vc_redist.x86.exe (PID: 3244)
- UnifiedStub-installer.exe (PID: 876)
- rsVPNSvc.exe (PID: 8128)
- rsEngineSvc.exe (PID: 3140)
Creates a software uninstall entry
- UnifiedStub-installer.exe (PID: 876)
Executes as Windows Service
- rsSyncSvc.exe (PID: 7420)
- rsWSC.exe (PID: 1680)
- rsClientSvc.exe (PID: 7352)
- rsEngineSvc.exe (PID: 3140)
- rsEDRSvc.exe (PID: 7368)
- WmiApSrv.exe (PID: 2328)
- rsVPNSvc.exe (PID: 8128)
- rsVPNClientSvc.exe (PID: 6372)
- WmiApSrv.exe (PID: 6360)
- rsDNSClientSvc.exe (PID: 7552)
- rsDNSResolver.exe (PID: 6516)
- rsDNSSvc.exe (PID: 5372)
- WmiApSrv.exe (PID: 8212)
Executes application which crashes
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.tmp (PID: 6832)
Loads Python modules
- python.exe (PID: 4284)
- python.exe (PID: 7268)
- python.exe (PID: 3784)
- python.exe (PID: 4308)
- python.exe (PID: 6648)
- python.exe (PID: 3908)
- python.exe (PID: 2144)
- python.exe (PID: 6816)
- python.exe (PID: 5516)
- python.exe (PID: 6324)
- python.exe (PID: 7500)
- python.exe (PID: 1116)
- python.exe (PID: 7904)
- python.exe (PID: 6748)
- python.exe (PID: 6272)
- python.exe (PID: 8068)
- python.exe (PID: 7856)
- python.exe (PID: 7176)
- python.exe (PID: 7752)
- python.exe (PID: 5724)
- python.exe (PID: 2876)
- python.exe (PID: 7316)
- python.exe (PID: 7080)
Adds/modifies Windows certificates
- clipgrab.exe (PID: 7624)
- UnifiedStub-installer.exe (PID: 876)
- rsWSC.exe (PID: 5920)
- rsEngineSvc.exe (PID: 3140)
The process creates files with name similar to system file names
- UnifiedStub-installer.exe (PID: 876)
Drops a system driver (possible attempt to evade defenses)
- UnifiedStub-installer.exe (PID: 876)
Drops 7-zip archiver for unpacking
- UnifiedStub-installer.exe (PID: 876)
Checks Windows Trust Settings
- UnifiedStub-installer.exe (PID: 876)
- rsWSC.exe (PID: 5920)
- rsEngineSvc.exe (PID: 5500)
- rsEDRSvc.exe (PID: 7856)
- rsWSC.exe (PID: 1680)
- rsEngineSvc.exe (PID: 3140)
- rsEDRSvc.exe (PID: 7368)
- rsVPNSvc.exe (PID: 8144)
- rsDNSSvc.exe (PID: 5288)
Creates or modifies Windows services
- rundll32.exe (PID: 872)
- UnifiedStub-installer.exe (PID: 876)
Creates files in the driver directory
- UnifiedStub-installer.exe (PID: 876)
Uses RUNDLL32.EXE to load library
- UnifiedStub-installer.exe (PID: 876)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- UnifiedStub-installer.exe (PID: 876)
Dropped object may contain URLs of mainers pools
- rsEngineSvc.exe (PID: 3140)
Reads the BIOS version
- rsEDRSvc.exe (PID: 7368)
- rsEngineSvc.exe (PID: 3140)
Process checks is Powershell's Script Block Logging on
- rsEDRSvc.exe (PID: 7368)
The process checks if it is being run in the virtual environment
- rsEngineSvc.exe (PID: 3140)
- rsVPNSvc.exe (PID: 8128)
- rsDNSSvc.exe (PID: 5372)
There is functionality for taking screenshot (YARA)
- rsHelper.exe (PID: 6548)
Read startup parameters
- rsEngineSvc.exe (PID: 3140)
Starts CMD.EXE for commands execution
- rsDNSSvc.exe (PID: 5372)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 7984)
- cmd.exe (PID: 8676)
INFO
Application launched itself
- firefox.exe (PID: 6744)
- firefox.exe (PID: 6764)
Manual execution by a user
- WinRAR.exe (PID: 7192)
- Taskmgr.exe (PID: 7160)
- Taskmgr.exe (PID: 7852)
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.exe (PID: 4544)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7192)
Reads Microsoft Office registry keys
- firefox.exe (PID: 6764)
The process uses the downloaded file
- firefox.exe (PID: 6764)
- WinRAR.exe (PID: 7192)
- rsEngineSvc.exe (PID: 3140)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 7160)
- Taskmgr.exe (PID: 7136)
- runonce.exe (PID: 4760)
- runonce.exe (PID: 5772)
Create files in a temporary directory
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.tmp (PID: 6832)
- clipgrab-3.9.10-portable.exe (PID: 6840)
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.exe (PID: 4544)
- clipgrab-3.9.10-portable.tmp (PID: 6808)
- vc_redist.x86.exe (PID: 3244)
- prod0.exe (PID: 8112)
- fztqbxpk.exe (PID: 7220)
- UnifiedStub-installer.exe (PID: 876)
- rsAppUI.exe (PID: 8168)
- python.exe (PID: 7316)
- rsAppUI.exe (PID: 4068)
- rsEngineSvc.exe (PID: 3140)
- rsAppUI.exe (PID: 6332)
Reads the software policy settings
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.tmp (PID: 6832)
- prod0.exe (PID: 8112)
- UnifiedStub-installer.exe (PID: 876)
- WerFault.exe (PID: 2480)
- clipgrab.exe (PID: 7624)
- WerFault.exe (PID: 6892)
- rsWSC.exe (PID: 5920)
- rsEngineSvc.exe (PID: 5500)
- rsWSC.exe (PID: 1680)
- rsEDRSvc.exe (PID: 7856)
- rsEDRSvc.exe (PID: 7368)
- rsEngineSvc.exe (PID: 3140)
- rsVPNSvc.exe (PID: 8144)
- rsVPNSvc.exe (PID: 8128)
- rsDNSSvc.exe (PID: 5372)
- rsDNSSvc.exe (PID: 5288)
Reads the machine GUID from the registry
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.tmp (PID: 6832)
- prod0.exe (PID: 8112)
- UnifiedStub-installer.exe (PID: 876)
- ffmpeg.exe (PID: 6968)
- clipgrab.exe (PID: 7624)
- ffmpeg.exe (PID: 6604)
- python.exe (PID: 3784)
- python.exe (PID: 4284)
- python.exe (PID: 3908)
- python.exe (PID: 4308)
- python.exe (PID: 6648)
- python.exe (PID: 2144)
- python.exe (PID: 7268)
- python.exe (PID: 6816)
- python.exe (PID: 7500)
- python.exe (PID: 6324)
- python.exe (PID: 1116)
- python.exe (PID: 7904)
- python.exe (PID: 6748)
- python.exe (PID: 8068)
- python.exe (PID: 6272)
- python.exe (PID: 7752)
- python.exe (PID: 7176)
- python.exe (PID: 5724)
- rsWSC.exe (PID: 5920)
- rsWSC.exe (PID: 1680)
- rsEngineSvc.exe (PID: 5500)
- rsEngineSvc.exe (PID: 3140)
- python.exe (PID: 2876)
- rsEDRSvc.exe (PID: 7856)
- rsEDRSvc.exe (PID: 7368)
- rsHelper.exe (PID: 6548)
- python.exe (PID: 7080)
- rsAppUI.exe (PID: 8168)
- ffmpeg.exe (PID: 1108)
- ffmpeg.exe (PID: 6804)
- python.exe (PID: 7316)
- rsVPNSvc.exe (PID: 8128)
- rsVPNSvc.exe (PID: 8144)
- rsAppUI.exe (PID: 4068)
- rsDNSSvc.exe (PID: 5288)
- rsDNSSvc.exe (PID: 5372)
- rsAppUI.exe (PID: 6332)
Checks proxy server information
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.tmp (PID: 6832)
- prod0.exe (PID: 8112)
- UnifiedStub-installer.exe (PID: 876)
- WerFault.exe (PID: 2480)
- WerFault.exe (PID: 6892)
- python.exe (PID: 7176)
- python.exe (PID: 5724)
- rsWSC.exe (PID: 5920)
- python.exe (PID: 2876)
- rsAppUI.exe (PID: 8168)
- python.exe (PID: 7316)
- python.exe (PID: 7080)
- rsAppUI.exe (PID: 4068)
- rsAppUI.exe (PID: 6332)
Reads the computer name
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.tmp (PID: 6832)
- clipgrab-3.9.10-portable.tmp (PID: 6808)
- vc_redist.x86.exe (PID: 3244)
- prod0.exe (PID: 8112)
- UnifiedStub-installer.exe (PID: 876)
- clipgrab.exe (PID: 7624)
- rsSyncSvc.exe (PID: 7420)
- rsSyncSvc.exe (PID: 7888)
- python.exe (PID: 7176)
- python.exe (PID: 5724)
- rsWSC.exe (PID: 5920)
- rsClientSvc.exe (PID: 6804)
- rsWSC.exe (PID: 1680)
- rsClientSvc.exe (PID: 7352)
- rsEngineSvc.exe (PID: 5500)
- rsEngineSvc.exe (PID: 3140)
- rsEDRSvc.exe (PID: 7368)
- python.exe (PID: 2876)
- rsEDRSvc.exe (PID: 7856)
- rsHelper.exe (PID: 6548)
- rsAppUI.exe (PID: 8168)
- rsAppUI.exe (PID: 2232)
- rsAppUI.exe (PID: 8028)
- python.exe (PID: 7316)
- python.exe (PID: 7080)
- rsVPNSvc.exe (PID: 8144)
- rsVPNClientSvc.exe (PID: 7416)
- rsVPNClientSvc.exe (PID: 6372)
- rsVPNSvc.exe (PID: 8128)
- rsAppUI.exe (PID: 4068)
- rsAppUI.exe (PID: 3648)
- rsAppUI.exe (PID: 2820)
- rsDNSClientSvc.exe (PID: 7552)
- rsDNSResolver.exe (PID: 5724)
- rsDNSResolver.exe (PID: 6516)
- rsDNSSvc.exe (PID: 5288)
- rsDNSClientSvc.exe (PID: 1492)
- rsDNSSvc.exe (PID: 5372)
- rsAppUI.exe (PID: 8384)
- rsAppUI.exe (PID: 6332)
- rsAppUI.exe (PID: 8404)
Checks supported languages
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.exe (PID: 4544)
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.tmp (PID: 6832)
- clipgrab-3.9.10-portable.exe (PID: 6840)
- vc_redist.x86.exe (PID: 8080)
- vc_redist.x86.exe (PID: 3244)
- clipgrab-3.9.10-portable.tmp (PID: 6808)
- prod0.exe (PID: 8112)
- fztqbxpk.exe (PID: 7220)
- clipgrab.exe (PID: 7624)
- UnifiedStub-installer.exe (PID: 876)
- ffmpeg.exe (PID: 6604)
- ffmpeg.exe (PID: 6968)
- rsSyncSvc.exe (PID: 7420)
- rsSyncSvc.exe (PID: 7888)
- python.exe (PID: 2144)
- python.exe (PID: 4284)
- python.exe (PID: 3784)
- python.exe (PID: 6648)
- python.exe (PID: 3908)
- python.exe (PID: 4308)
- python.exe (PID: 7268)
- python.exe (PID: 6816)
- python.exe (PID: 5516)
- python.exe (PID: 7500)
- python.exe (PID: 1116)
- python.exe (PID: 7904)
- python.exe (PID: 6324)
- QtWebEngineProcess.exe (PID: 7060)
- QtWebEngineProcess.exe (PID: 400)
- QtWebEngineProcess.exe (PID: 6520)
- python.exe (PID: 6748)
- python.exe (PID: 6272)
- python.exe (PID: 8068)
- python.exe (PID: 7752)
- QtWebEngineProcess.exe (PID: 6808)
- python.exe (PID: 7176)
- python.exe (PID: 7856)
- QtWebEngineProcess.exe (PID: 8044)
- QtWebEngineProcess.exe (PID: 7348)
- python.exe (PID: 5724)
- QtWebEngineProcess.exe (PID: 7232)
- rsWSC.exe (PID: 1680)
- rsClientSvc.exe (PID: 6804)
- rsClientSvc.exe (PID: 7352)
- rsEngineSvc.exe (PID: 5500)
- rsWSC.exe (PID: 5920)
- rsEngineSvc.exe (PID: 3140)
- QtWebEngineProcess.exe (PID: 8128)
- python.exe (PID: 2876)
- rsEDRSvc.exe (PID: 7856)
- rsEDRSvc.exe (PID: 7368)
- rsHelper.exe (PID: 6548)
- EPP.exe (PID: 7700)
- QtWebEngineProcess.exe (PID: 6920)
- rsAppUI.exe (PID: 8168)
- rsAppUI.exe (PID: 8028)
- rsAppUI.exe (PID: 2232)
- rsAppUI.exe (PID: 7828)
- rsLitmus.A.exe (PID: 7412)
- python.exe (PID: 7080)
- rsAppUI.exe (PID: 7940)
- ffmpeg.exe (PID: 1108)
- ffmpeg.exe (PID: 6804)
- python.exe (PID: 7316)
- rsVPNClientSvc.exe (PID: 6372)
- rsVPNSvc.exe (PID: 8128)
- rsVPNClientSvc.exe (PID: 7416)
- rsVPNSvc.exe (PID: 8144)
- rsAppUI.exe (PID: 4068)
- VPN.exe (PID: 7012)
- rsAppUI.exe (PID: 3648)
- rsAppUI.exe (PID: 2820)
- rsAppUI.exe (PID: 5092)
- rsAppUI.exe (PID: 6660)
- rsDNSClientSvc.exe (PID: 1492)
- rsDNSResolver.exe (PID: 5724)
- rsDNSClientSvc.exe (PID: 7552)
- rsDNSResolver.exe (PID: 7008)
- rsDNSResolver.exe (PID: 6516)
- rsDNSSvc.exe (PID: 5288)
- rsDNSSvc.exe (PID: 5372)
- rsAppUI.exe (PID: 6332)
- DNS.exe (PID: 5712)
- rsAppUI.exe (PID: 8384)
- rsAppUI.exe (PID: 8428)
- rsAppUI.exe (PID: 8952)
- rsAppUI.exe (PID: 9016)
- rsAppUI.exe (PID: 8404)
Creates a software uninstall entry
- clipgrab-3.9.10-portable.tmp (PID: 6808)
Creates files in the program directory
- clipgrab-3.9.10-portable.tmp (PID: 6808)
- UnifiedStub-installer.exe (PID: 876)
- rsWSC.exe (PID: 5920)
- rsEngineSvc.exe (PID: 5500)
- rsEngineSvc.exe (PID: 3140)
- rsEDRSvc.exe (PID: 7856)
- rsEDRSvc.exe (PID: 7368)
- rsVPNSvc.exe (PID: 8144)
- rsVPNSvc.exe (PID: 8128)
- rsDNSResolver.exe (PID: 5724)
- rsDNSSvc.exe (PID: 5288)
- rsDNSResolver.exe (PID: 6516)
- rsDNSSvc.exe (PID: 5372)
Process checks computer location settings
- e92c5cf7509dd9792fac8202fb08295dfc9e5f18663db81bf07990de1bc85893.tmp (PID: 6832)
- prod0.exe (PID: 8112)
- QtWebEngineProcess.exe (PID: 400)
- rsAppUI.exe (PID: 8168)
- rsAppUI.exe (PID: 7828)
- rsAppUI.exe (PID: 7940)
- rsVPNSvc.exe (PID: 8128)
- rsAppUI.exe (PID: 6660)
- rsAppUI.exe (PID: 4068)
- rsAppUI.exe (PID: 5092)
- rsAppUI.exe (PID: 8428)
- rsAppUI.exe (PID: 8952)
- rsAppUI.exe (PID: 9016)
- rsAppUI.exe (PID: 6332)
Reads Environment values
- prod0.exe (PID: 8112)
- UnifiedStub-installer.exe (PID: 876)
- rsEngineSvc.exe (PID: 3140)
- rsEDRSvc.exe (PID: 7368)
- rsAppUI.exe (PID: 8168)
- rsVPNSvc.exe (PID: 8128)
- rsAppUI.exe (PID: 4068)
- rsDNSSvc.exe (PID: 5372)
- rsAppUI.exe (PID: 6332)
Disables trace logs
- prod0.exe (PID: 8112)
- UnifiedStub-installer.exe (PID: 876)
- rsEngineSvc.exe (PID: 3140)
- rsEDRSvc.exe (PID: 7368)
- rsVPNSvc.exe (PID: 8128)
- rsDNSSvc.exe (PID: 5372)
Creates files or folders in the user directory
- clipgrab.exe (PID: 7624)
- WerFault.exe (PID: 6892)
- WerFault.exe (PID: 2480)
- UnifiedStub-installer.exe (PID: 876)
- rsWSC.exe (PID: 5920)
- rsEngineSvc.exe (PID: 3140)
- rsAppUI.exe (PID: 8168)
- rsAppUI.exe (PID: 2232)
- rsVPNSvc.exe (PID: 8128)
- rsAppUI.exe (PID: 4068)
- rsAppUI.exe (PID: 2820)
- rsDNSSvc.exe (PID: 5372)
- rsAppUI.exe (PID: 6332)
- rsAppUI.exe (PID: 8404)
Reads the time zone
- QtWebEngineProcess.exe (PID: 400)
- runonce.exe (PID: 4760)
- rsEDRSvc.exe (PID: 7368)
- rsEngineSvc.exe (PID: 3140)
- rsVPNSvc.exe (PID: 8128)
- runonce.exe (PID: 5772)
- rsDNSSvc.exe (PID: 5372)
.NET Reactor protector has been detected
- UnifiedStub-installer.exe (PID: 876)
- rsWSC.exe (PID: 1680)
- rsEngineSvc.exe (PID: 3140)
- rsEDRSvc.exe (PID: 7368)
- rsHelper.exe (PID: 6548)
Reads product name
- rsEDRSvc.exe (PID: 7368)
- rsEngineSvc.exe (PID: 3140)
- rsAppUI.exe (PID: 8168)
- rsAppUI.exe (PID: 4068)
- rsAppUI.exe (PID: 6332)
Reads CPU info
- rsEDRSvc.exe (PID: 7368)
- rsEngineSvc.exe (PID: 3140)
- rsVPNSvc.exe (PID: 8128)
- rsDNSSvc.exe (PID: 5372)
Reads mouse settings
- rsEngineSvc.exe (PID: 3140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
309
Monitored processes
160
Malicious processes
15
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 368 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | python.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 400 | "C:\Program Files (x86)\ClipGrab\QtWebEngineProcess.exe" --type=renderer --no-sandbox --disable-gpu-memory-buffer-video-frames --enable-threaded-compositing --enable-features=AllowContentInitiatedDataUrlNavigations --disable-features=MojoVideoCapture,SurfaceSynchronization,UseModernMediaControls,UseVideoCaptureApiForDevToolsSnapshots --disable-databases --disable-gpu-compositing --service-pipe-token=8383712626691625480 --lang=en-US --webengine-schemes=qrc:sLV --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8383712626691625480 --renderer-client-id=4 --mojo-platform-channel-handle=2856 /prefetch:1 | C:\Program Files (x86)\ClipGrab\QtWebEngineProcess.exe | — | clipgrab.exe | |||||||||||
User: admin Company: The Qt Company Ltd. Integrity Level: HIGH Description: Qt Qtwebengineprocess Version: 5.12.6.0 Modules
| |||||||||||||||
| 460 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | python.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 508 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | python.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | "C:\WINDOWS\system32\rundll32.exe" setupapi.dll,InstallHinfSection DefaultInstall 128 C:\Program Files\ReasonLabs\EPP\x64\rsKernelEngine.inf | C:\Windows\System32\rundll32.exe | UnifiedStub-installer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | .\UnifiedStub-installer.exe /silent | C:\Users\admin\AppData\Local\Temp\7zS43CDC113\UnifiedStub-installer.exe | fztqbxpk.exe | ||||||||||||
User: admin Company: Reason Software Company Inc. Integrity Level: HIGH Description: UnifiedStub Exit code: 0 Version: 6.0.6 Modules
| |||||||||||||||
| 1064 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1108 | ffmpeg -bsfs | C:\Program Files (x86)\ClipGrab\ffmpeg.exe | — | python.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1116 | "C:\Program Files (x86)\ClipGrab\python\python.exe" "" --version | C:\Program Files (x86)\ClipGrab\python\python.exe | — | clipgrab.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: HIGH Description: Python Exit code: 1 Version: 3.8.9 Modules
| |||||||||||||||
| 1116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rsDNSResolver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
205 691
Read events
204 851
Write events
608
Delete events
232
Modification events
| (PID) Process: | (6744) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 873FB5F900000000 | |||
| (PID) Process: | (6764) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 54C2B6F900000000 | |||
| (PID) Process: | (6764) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Progress |
Value: 0 | |||
| (PID) Process: | (6764) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Progress |
Value: 1 | |||
| (PID) Process: | (6764) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Installer\308046B0AF4A39CB |
| Operation: | delete value | Name: | installer.taskbarpin.win10.enabled |
Value: | |||
| (PID) Process: | (6764) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (6764) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (6764) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (6764) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (6764) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
Executable files
1 007
Suspicious files
625
Text files
144
Unknown types
53
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6764 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6764 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6764 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 6764 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6764 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 6764 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:046A14EFA4E7F08F4C3102E8A5BC1FC9 | SHA256:99CBCEAB70F4A4775A40D6BCF385D943B5A4888965F9945499917D400E01D8BF | |||
| 6764 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6764 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6764 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6764 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
107
TCP/UDP connections
262
DNS requests
172
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6764 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6764 | firefox.exe | POST | 200 | 23.53.40.123:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
1168 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6764 | firefox.exe | POST | 200 | 23.53.40.161:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
6764 | firefox.exe | POST | 200 | 23.53.40.161:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
6764 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
6764 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
6764 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
6764 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
6764 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5956 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4760 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6764 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | — | — | unknown |
6764 | firefox.exe | 216.58.212.170:443 | safebrowsing.googleapis.com | — | — | whitelisted |
6764 | firefox.exe | 151.101.66.49:443 | bazaar.abuse.ch | FASTLY | US | unknown |
6764 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
6764 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | — | — | unknown |
6764 | firefox.exe | 216.58.206.35:80 | o.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
bazaar.abuse.ch |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
p2.shared.global.fastly.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
prod.ads.prod.webservices.mozgcp.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2232 | rsAppUI.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |
2232 | rsAppUI.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |
Process | Message |
|---|---|
clipgrab.exe | QObject::connect: signal not found in QTreeView
|
clipgrab.exe | "C:\\Program Files (x86)\\ClipGrab\\python\\python.exe: can't find '__main__' module in ''\r\n"
|
clipgrab.exe | "WARNING: [youtube:tab] Incomplete data received. Retrying (1/3)...\nWARNING: [youtube:tab] Incomplete data received. Retrying (2/3)...\nWARNING: [youtube:tab] Incomplete data received. Retrying (3/3)...\nWARNING: [youtube:tab] Incomplete data received. Giving up after 3 retries\n"
|
clipgrab.exe | ""
|
rsEngineSvc.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\ReasonLabs\EPP\x64\SQLite.Interop.dll"...
|
clipgrab.exe | "WARNING: [youtube:tab] Incomplete data received. Retrying (1/3)...\nWARNING: [youtube:tab] Incomplete data received. Retrying (2/3)...\nWARNING: [youtube:tab] Incomplete data received. Retrying (3/3)...\nWARNING: [youtube:tab] Incomplete data received. Giving up after 3 retries\n"
|
rsEDRSvc.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\ReasonLabs\EDR\x64\SQLite.Interop.dll"...
|
clipgrab.exe | "WARNING: [youtube] Failed to download m3u8 information: HTTP Error 429: Too Many Requests\n"
|
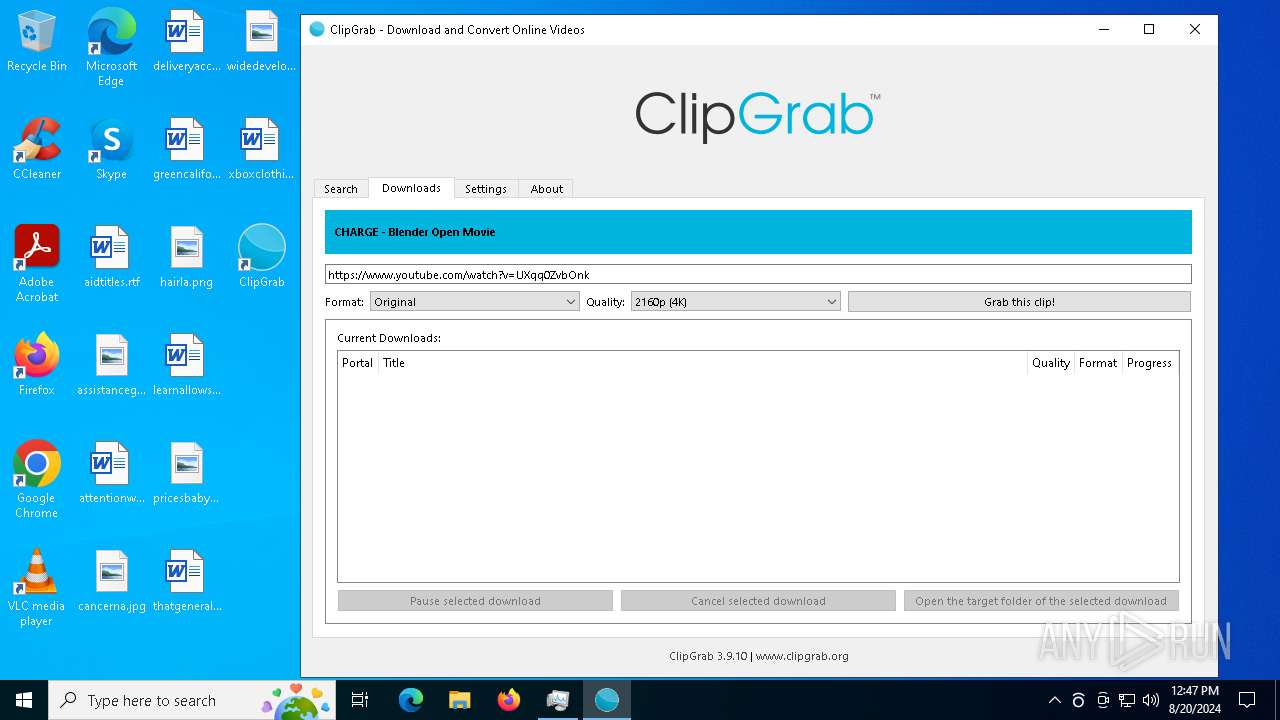
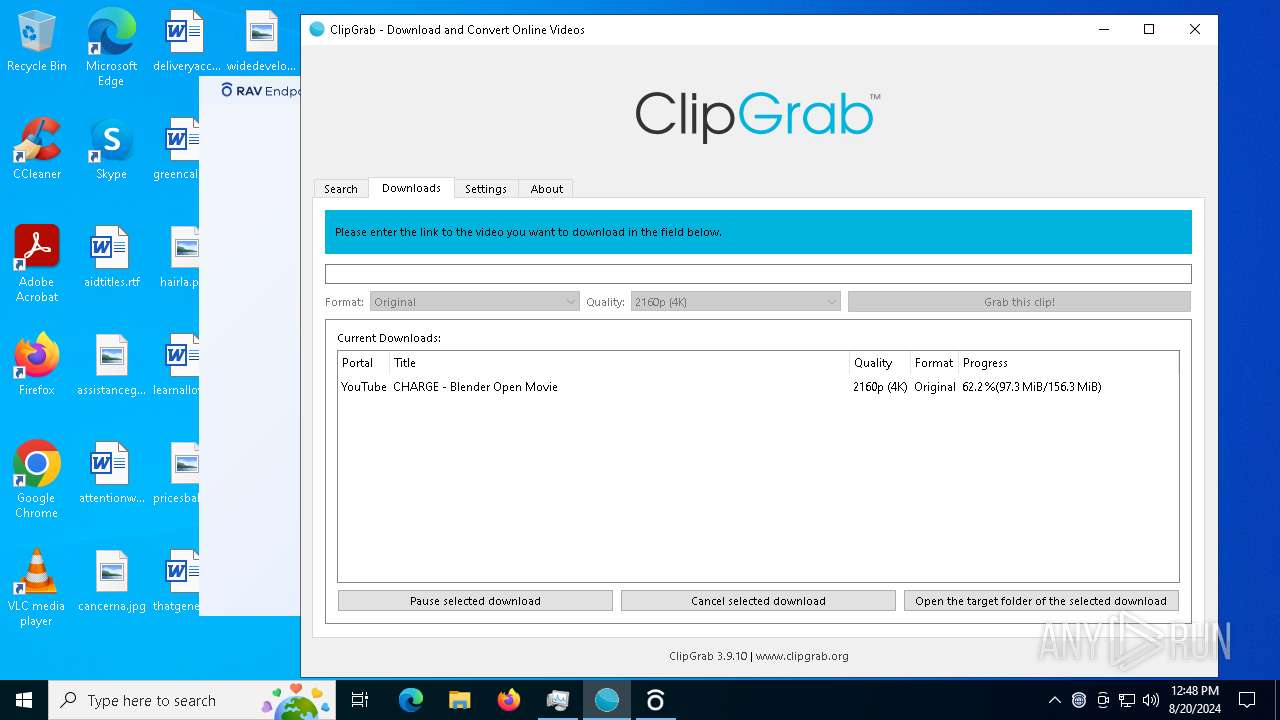
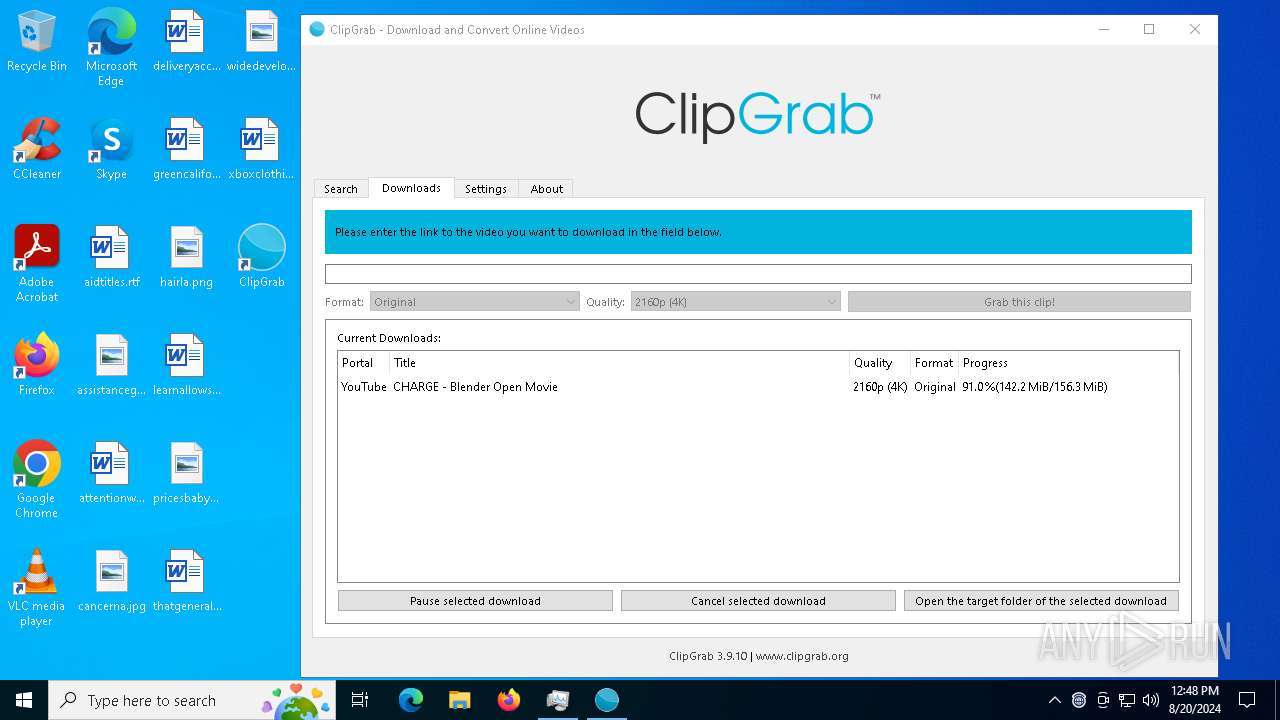
clipgrab.exe | Discovered video: "CHARGE - Blender Open Movie"
|
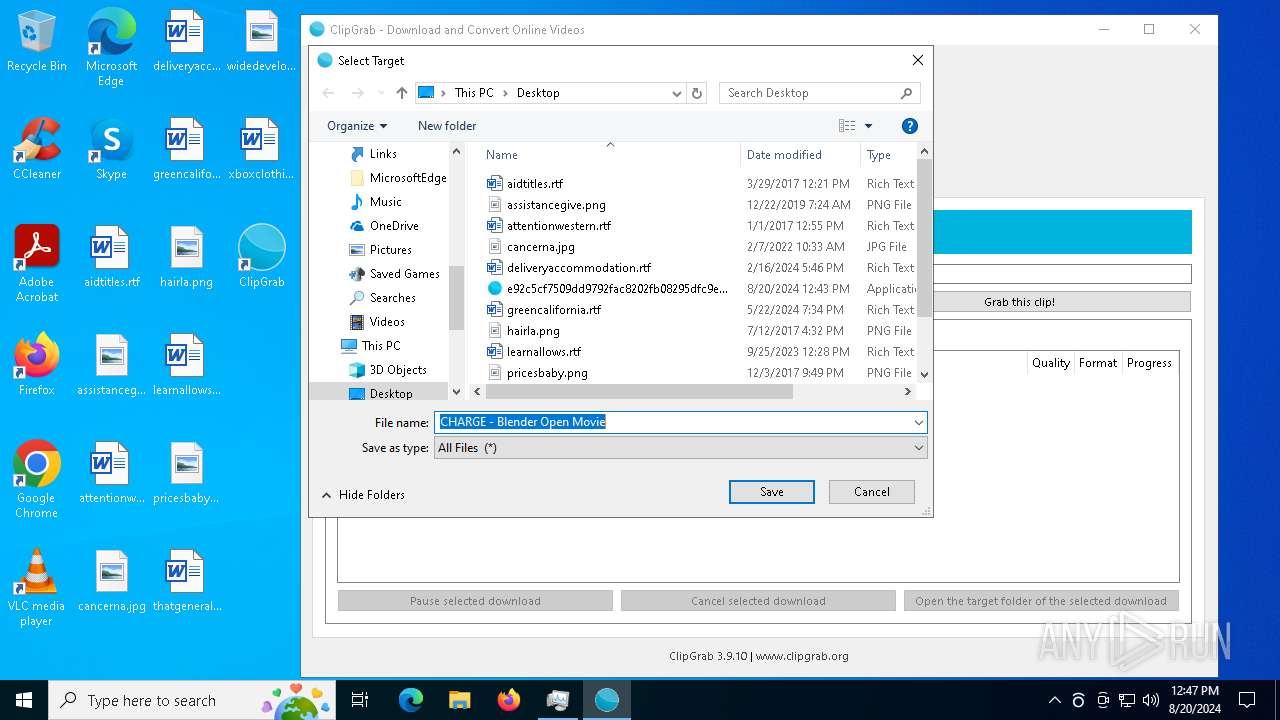
clipgrab.exe | "C:/Users/admin/Desktop" "CHARGE - Blender Open Movie"
|