| File name: | d6a479704bd6b481edc8c53ab9601c34bff8558fb7a90389e7259c879c96d7df |
| Full analysis: | https://app.any.run/tasks/b3d959ab-8d5d-4e82-acde-cf18fa9f2190 |
| Verdict: | Malicious activity |
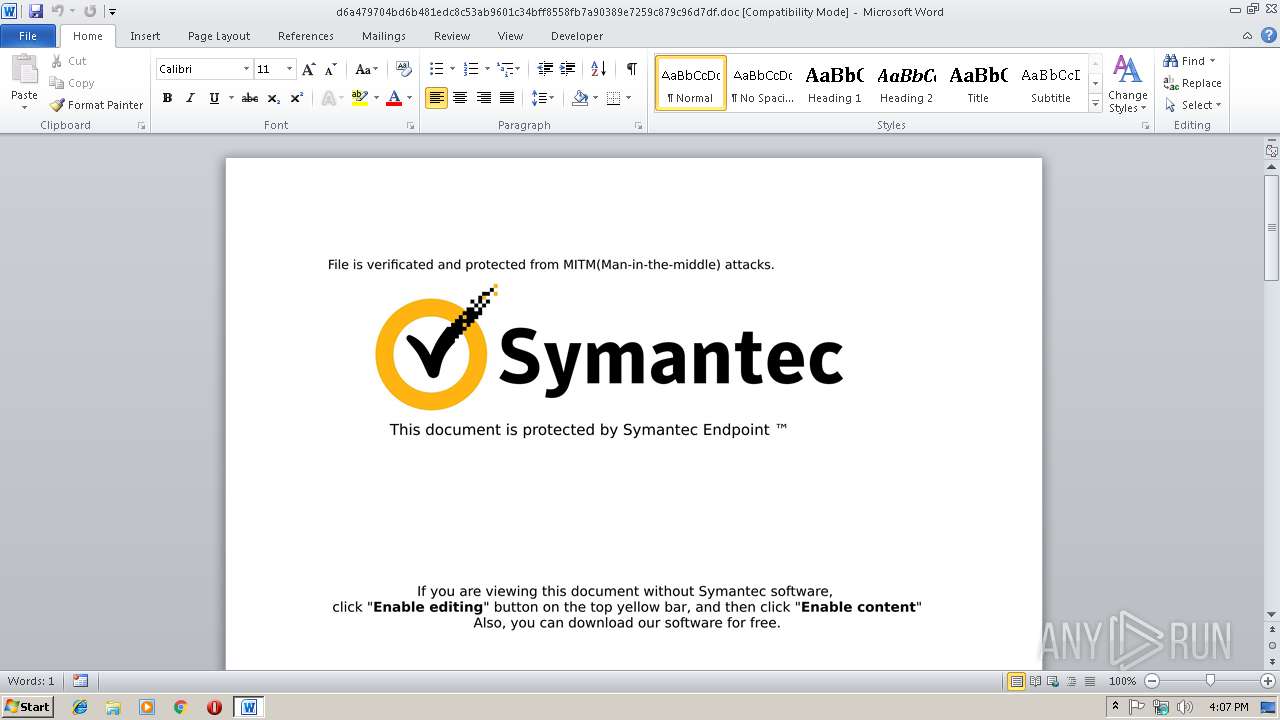
| Threats: | Arkei is a stealer type malware capable of collecting passwords, autosaved forms, cryptocurrency wallet credentials, and files. |
| Analysis date: | December 06, 2018, 16:07:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: Little Pig, Template: Normal.dotm, Last Saved By: Little Pig, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Total Editing Time: 01:00, Create Time/Date: Thu Nov 29 17:41:00 2018, Last Saved Time/Date: Thu Nov 29 17:42:00 2018, Number of Pages: 2, Number of Words: 0, Number of Characters: 3, Security: 0 |
| MD5: | 4B6977F65207F40A703CC3108BD616DA |
| SHA1: | A26152C2CF2E8880D1EC730F574F1D80E329E6FC |
| SHA256: | D6A479704BD6B481EDC8C53AB9601C34BFF8558FB7A90389E7259C879C96D7DF |
| SSDEEP: | 6144:UXA5ivBFLyG4AcLXmeJUguD4Bl7XnpSHLW7W/bMlj:OA5ivOPDRuDm7X8qsb2 |
MALICIOUS
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2972)
Requests a remote executable file from MS Office
- WINWORD.EXE (PID: 2972)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2972)
Application was dropped or rewritten from another process
- ubyj.exe (PID: 1760)
- ubyj.exe (PID: 856)
- UANZQNJNPV.exe (PID: 712)
- UANZQNJNPV.exe (PID: 3600)
ARKEI was detected
- ubyj.exe (PID: 856)
Loads dropped or rewritten executable
- ubyj.exe (PID: 856)
Downloads executable files from the Internet
- ubyj.exe (PID: 856)
Stealing of credential data
- ubyj.exe (PID: 856)
Actions looks like stealing of personal data
- ubyj.exe (PID: 856)
AZORULT was detected
- UANZQNJNPV.exe (PID: 3600)
Connects to CnC server
- UANZQNJNPV.exe (PID: 3600)
SUSPICIOUS
Unusual connect from Microsoft Office
- WINWORD.EXE (PID: 2972)
Creates files in the program directory
- ubyj.exe (PID: 856)
Reads the cookies of Mozilla Firefox
- ubyj.exe (PID: 856)
Reads the cookies of Google Chrome
- ubyj.exe (PID: 856)
Executable content was dropped or overwritten
- ubyj.exe (PID: 856)
Creates files in the user directory
- ubyj.exe (PID: 856)
Starts itself from another location
- ubyj.exe (PID: 856)
Starts CMD.EXE for commands execution
- ubyj.exe (PID: 856)
Connects to server without host name
- UANZQNJNPV.exe (PID: 3600)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3216)
Checks for external IP
- ubyj.exe (PID: 856)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2972)
Creates files in the user directory
- WINWORD.EXE (PID: 2972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (80) |
|---|
EXIF
FlashPix
| Author: | Little Pig |
|---|---|
| Template: | Normal.dotm |
| LastModifiedBy: | Little Pig |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 1.0 minutes |
| CreateDate: | 2018:11:29 17:41:00 |
| ModifyDate: | 2018:11:29 17:42:00 |
| Pages: | 2 |
| Words: | - |
| Characters: | 3 |
| Security: | None |
| CodePage: | Unicode (UTF-8) |
| Company: | Microsoft |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 3 |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | - |
| CompObjUserType: | - |
Total processes
39
Monitored processes
7
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 712 | "C:\ProgramData\UANZQNJNPV.exe" | C:\ProgramData\UANZQNJNPV.exe | — | ubyj.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 856 | C:\Users\Public\ubyj.exe | C:\Users\Public\ubyj.exe | ubyj.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1760 | C:\Users\Public\ubyj.exe | C:\Users\Public\ubyj.exe | — | WINWORD.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2416 | taskkill /im ubyj.exe /f | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2972 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\d6a479704bd6b481edc8c53ab9601c34bff8558fb7a90389e7259c879c96d7df.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3216 | "C:\Windows\System32\cmd.exe" /c taskkill /im ubyj.exe /f & erase C:\Users\Public\ubyj.exe & exit | C:\Windows\System32\cmd.exe | — | ubyj.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3600 | "C:\ProgramData\UANZQNJNPV.exe" | C:\ProgramData\UANZQNJNPV.exe | UANZQNJNPV.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 166
Read events
799
Write events
362
Delete events
5
Modification events
| (PID) Process: | (2972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 7h? |
Value: 37683F009C0B0000010000000000000000000000 | |||
| (PID) Process: | (2972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2972) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1300627479 | |||
| (PID) Process: | (2972) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1300627600 | |||
| (PID) Process: | (2972) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1300627601 | |||
| (PID) Process: | (2972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 9C0B0000E05BA2D67D8DD40100000000 | |||
| (PID) Process: | (2972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | .j? |
Value: 2E6A3F009C0B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | .j? |
Value: 2E6A3F009C0B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
16
Suspicious files
1
Text files
13
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2972 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA888.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 856 | ubyj.exe | C:\ProgramData\EZSFTVFMC4137HO8J9HP\c-shm | — | |
MD5:— | SHA256:— | |||
| 856 | ubyj.exe | C:\ProgramData\EZSFTVFMC4137HO8J9HP\history | — | |
MD5:— | SHA256:— | |||
| 2972 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\AU3_EXE[1].exe | executable | |
MD5:— | SHA256:— | |||
| 856 | ubyj.exe | C:\ProgramData\EZSFTVFMC4137HO8J9HP\history-shm | — | |
MD5:— | SHA256:— | |||
| 2972 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$a479704bd6b481edc8c53ab9601c34bff8558fb7a90389e7259c879c96d7df.doc | pgc | |
MD5:— | SHA256:— | |||
| 856 | ubyj.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\msvcp140[1].dll | executable | |
MD5:109F0F02FD37C84BFC7508D4227D7ED5 | SHA256:334E69AC9367F708CE601A6F490FF227D6C20636DA5222F148B25831D22E13D4 | |||
| 2972 | WINWORD.EXE | C:\Users\Public\ubyj.exe | executable | |
MD5:— | SHA256:— | |||
| 856 | ubyj.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2YPIJ90\freebl3[1].dll | executable | |
MD5:EF2834AC4EE7D6724F255BEAF527E635 | SHA256:A770ECBA3B08BBABD0A567FC978E50615F8B346709F8EB3CFACF3FAAB24090BA | |||
| 2972 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
6
DNS requests
4
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | ubyj.exe | POST | 200 | 79.143.28.114:80 | http://benderio.com/ | RU | text | 94 b | malicious |
856 | ubyj.exe | POST | 200 | 79.143.28.114:80 | http://benderio.com/169 | RU | text | 156 b | malicious |
856 | ubyj.exe | GET | 200 | 79.143.28.114:80 | http://benderio.com/mozglue.dll | RU | executable | 133 Kb | malicious |
856 | ubyj.exe | GET | 200 | 79.143.28.114:80 | http://benderio.com/vcruntime140.dll | RU | executable | 81.8 Kb | malicious |
856 | ubyj.exe | POST | 200 | 185.194.141.58:80 | http://ip-api.com/line/ | DE | text | 115 b | malicious |
856 | ubyj.exe | GET | 200 | 79.143.28.114:80 | http://benderio.com/freebl3.dll | RU | executable | 326 Kb | malicious |
856 | ubyj.exe | GET | 200 | 79.143.28.114:80 | http://benderio.com/msvcp140.dll | RU | executable | 429 Kb | malicious |
856 | ubyj.exe | GET | 200 | 79.143.28.114:80 | http://benderio.com/nss3.dll | RU | executable | 1.19 Mb | malicious |
2972 | WINWORD.EXE | GET | 200 | 122.10.96.66:80 | http://linyidyhg.com/data/cache/listcache/ae/c5/3b/AU3_EXE.exe | HK | executable | 697 Kb | suspicious |
3600 | UANZQNJNPV.exe | POST | — | 185.198.57.181:80 | http://185.198.57.181/index.php | NL | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3600 | UANZQNJNPV.exe | 185.198.57.181:80 | — | Host Sailor Ltd. | NL | malicious |
856 | ubyj.exe | 185.194.141.58:80 | ip-api.com | netcup GmbH | DE | unknown |
2972 | WINWORD.EXE | 122.10.96.66:80 | linyidyhg.com | Hutchison Global Communications | HK | suspicious |
856 | ubyj.exe | 79.143.28.114:80 | benderio.com | Frame Design Ltd | RU | malicious |
856 | ubyj.exe | 91.194.60.236:80 | www.bsprotection.fr | Octopuce s.a.r.l. | FR | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
linyidyhg.com |
| suspicious |
benderio.com |
| malicious |
ip-api.com |
| malicious |
www.bsprotection.fr |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2972 | WINWORD.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
856 | ubyj.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.PWS.Stealer.23869 (Arkei) |
856 | ubyj.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
856 | ubyj.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.PWS.Stealer.23869 (Arkei) |
856 | ubyj.exe | A Network Trojan was detected | MALWARE [PTsecurity] Nocturnal Stealer |
856 | ubyj.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
856 | ubyj.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.PWS.Stealer.23869 (Arkei) |
856 | ubyj.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3600 | UANZQNJNPV.exe | A Network Trojan was detected | MALWARE [PTsecurity] AZORult HTTP Header |
3600 | UANZQNJNPV.exe | A Network Trojan was detected | MALWARE [PTsecurity] AZORult Request |
4 ETPRO signatures available at the full report